当前位置:网站首页>CSRF vulnerability analysis
CSRF vulnerability analysis
2022-07-06 18:21:00 【xiaochuhe.】
Warning
Do not Use the content mentioned in this article Breach of law .
this paper No guarantee is given
Catalog
3、 ... and 、 Introduction to the experimental environment
Four 、 Practical vulnerability learning
( One ) be based on Get Formal CSRF attack
( Two ) be based on Post Formal CSRF attack
Experimental environment : Hetian Laboratory
One 、 Preliminary knowledge ——cookie brief introduction
The current mainstream Web Applications are all based on Cookie Way to save the session state , But browsers are introducing Cookie But a very important safety factor was ignored , From WEB The file requests generated by the page will be brought with COOKIE. Just request the domain and Cookie The domain specified by the information is consistent , Whether it's a visit Web page , Or ask for pictures , Text and other resources , Users will bring... When making requests Cookie. The following picture shows the attached message we sent when visiting Baidu homepage Cookie Information :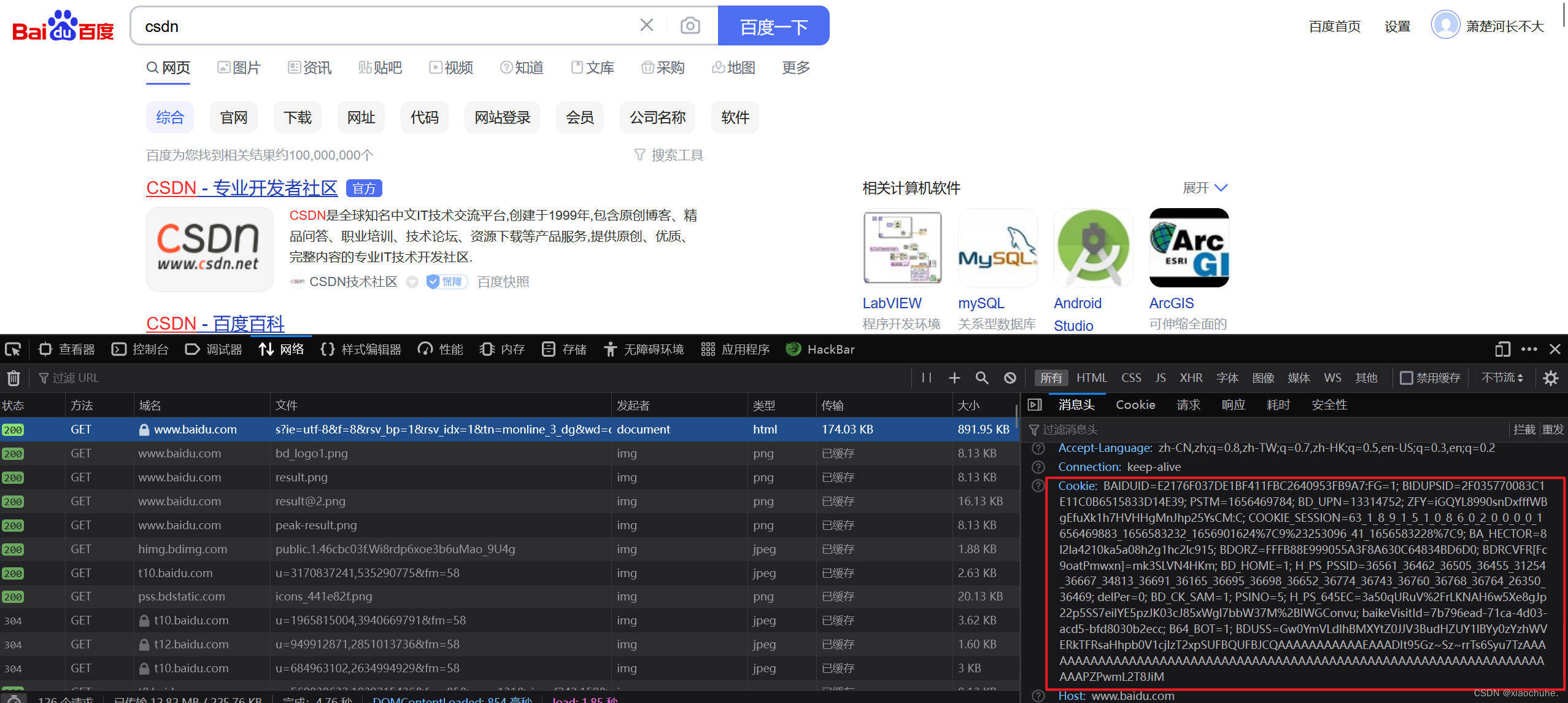
notes :Cookie This feature makes it convenient for users to always visit the website as login , But at the same time , It also facilitates attackers to steal identity information and perform malicious acts .
Two 、 Vulnerability profile
CSRF(Cross-site request forgery) Cross-site request forgery , Also known as “one click attack” perhaps session riding, Commonly abbreviated as CSRF perhaps XSRF, Is a malicious use of the site .CSRF Take advantage of trusted sites by masquerading requests from trusted users . And XSS Compared to attack ,CSRF Attacks are often unpopular ( So there are few resources to guard against it ) And hard to prevent , So it's considered a ratio XSS More dangerous .
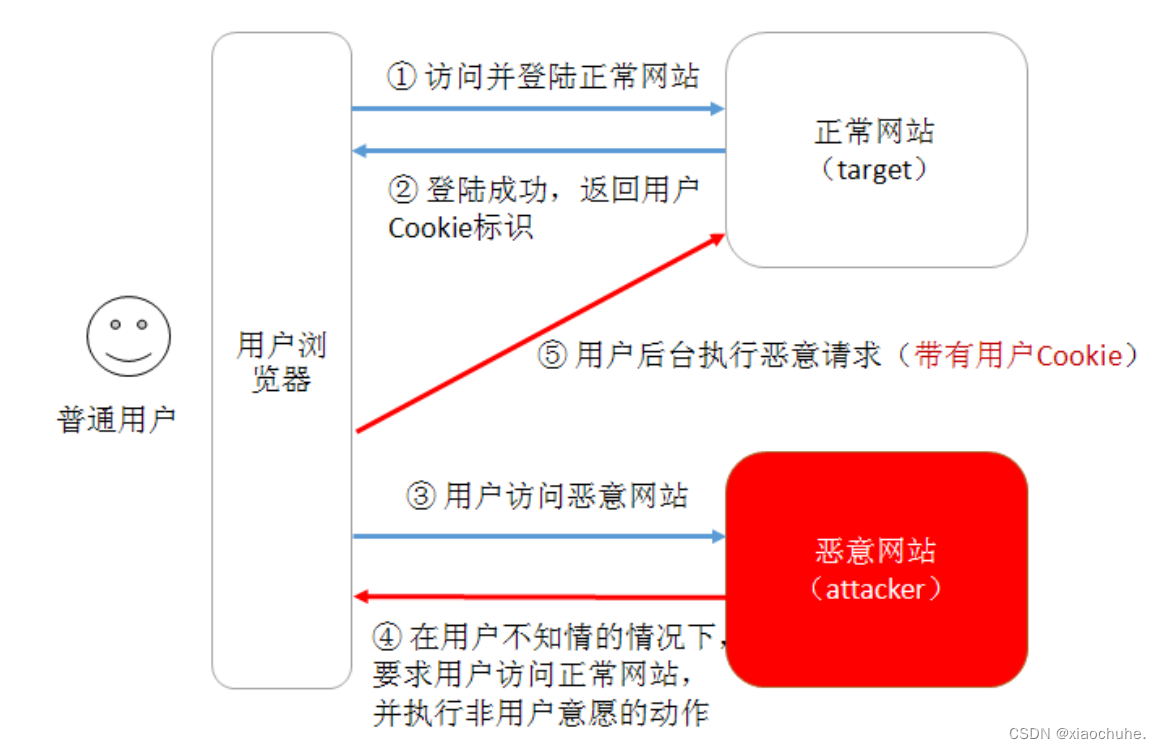
The picture below is a complete CSRF Attack map . The user logged in and visited a normal website , After successful login , The website returns the user's identity Cookie To the user . When a user visits a malicious website , Malicious websites force users to send malicious requests to normal websites . Because the user has a normal website at this time Cookie, So it's equivalent to the attacker stealing the user's identity , To visit the normal ( The goal is ) Website .
Once complete CSRF attack , The victim user needs to complete two steps :
- Log in to the normal website , And build locally Cookie.
- Without quitting the normal website , Visit malicious websites .
3、 ... and 、 Introduction to the experimental environment
A machine deploys a normal website ( Message board ):10.1.1.189
A machine deploys malicious websites :10.1.1.23
Four 、 Practical vulnerability learning
( One ) be based on Get Formal CSRF attack
1. Open the message board , Input user ID admin With the code 123456 Sign in :
2. Click the add message button to enter the message adding page , Press F12 Button opens Chrome Browser debugging tools ( Or open other equivalent Http Debugging software ), Switch to Network Label column , Choose Preserve Log Options , Ready to grab the message packet . Enter the title and content in the input box respectively , Click on add Button . Click... In the debug window ”add.php?title=…” A view of the message request just sent Http Content of agreement , As shown in the figure below :
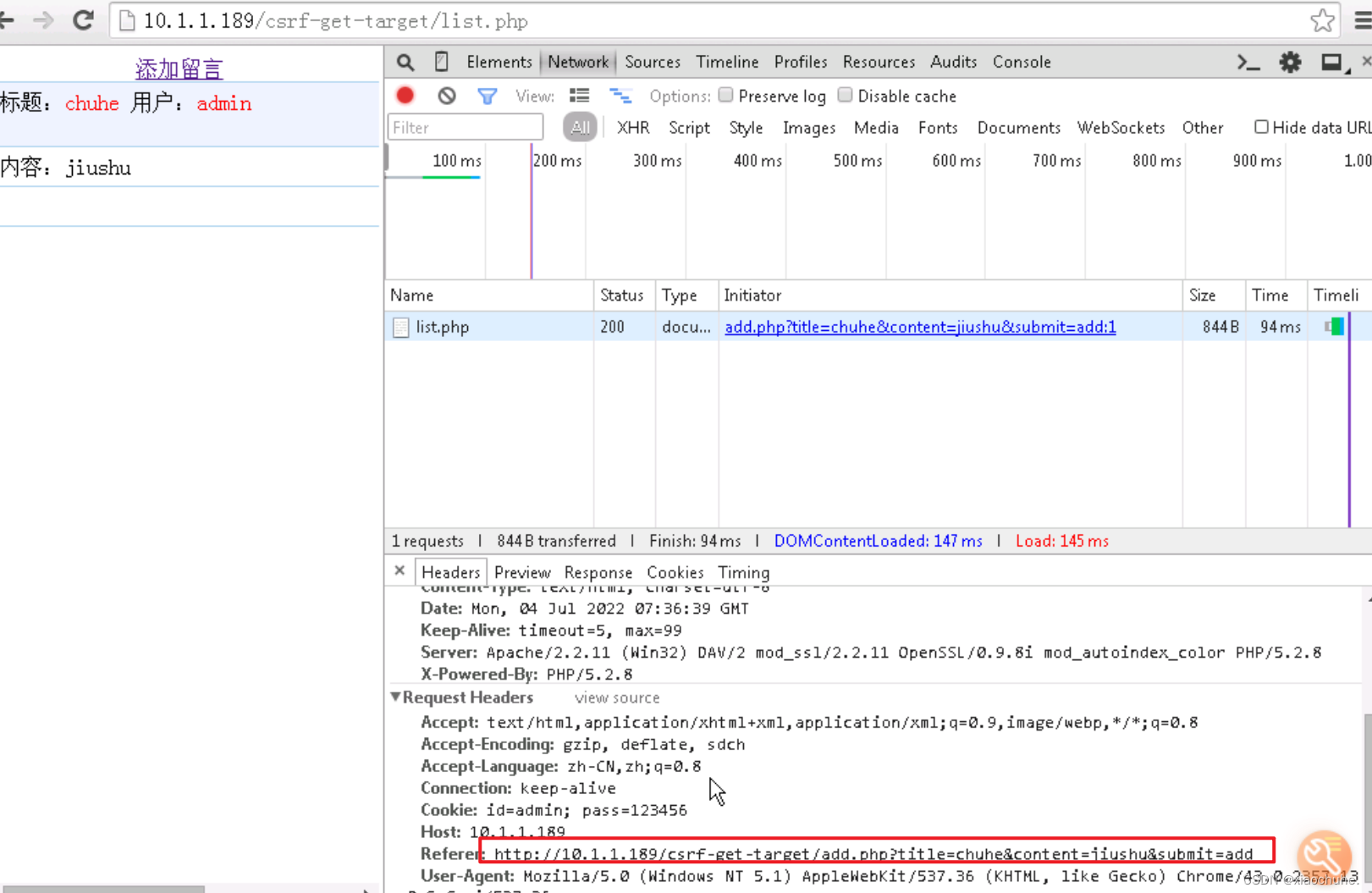
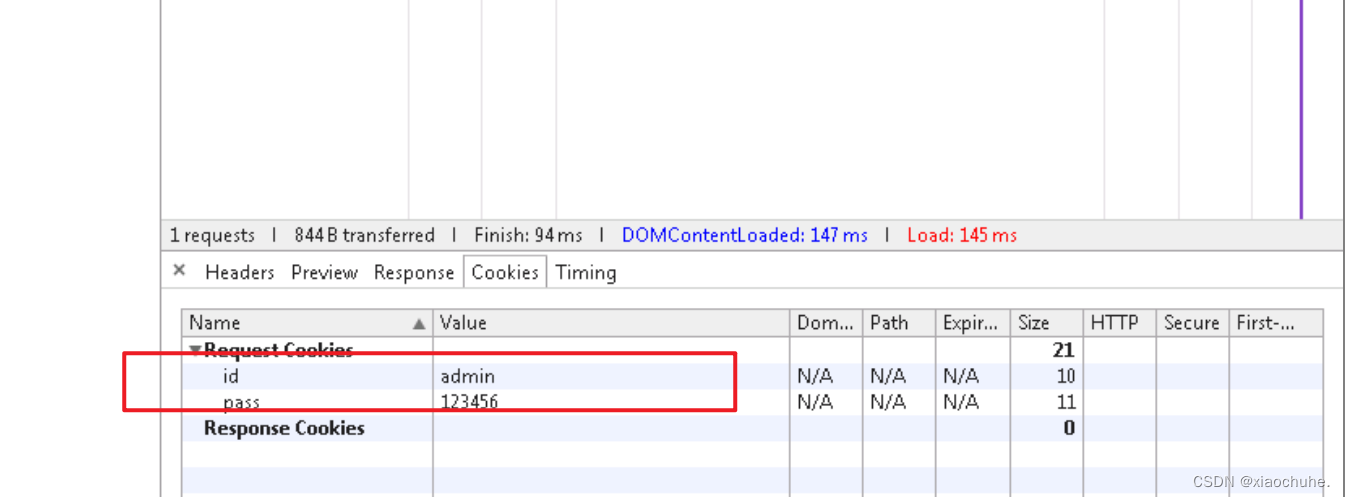
You can see from the screenshot , What we entered in the message board , Attached to the page request address sent to the server , This parameter field is stored in URL The request in is called GET request . That is, the first thing we try is based on GET Request form CSRF attack , Next section will introduce POST Request form CSRF attack . At the same time, we found that users are adding message requests , The user ID is attached Cookie Field . Of course, this is for demonstration , Let's go straight to Plaintext user name and password are regarded as Cookie value .
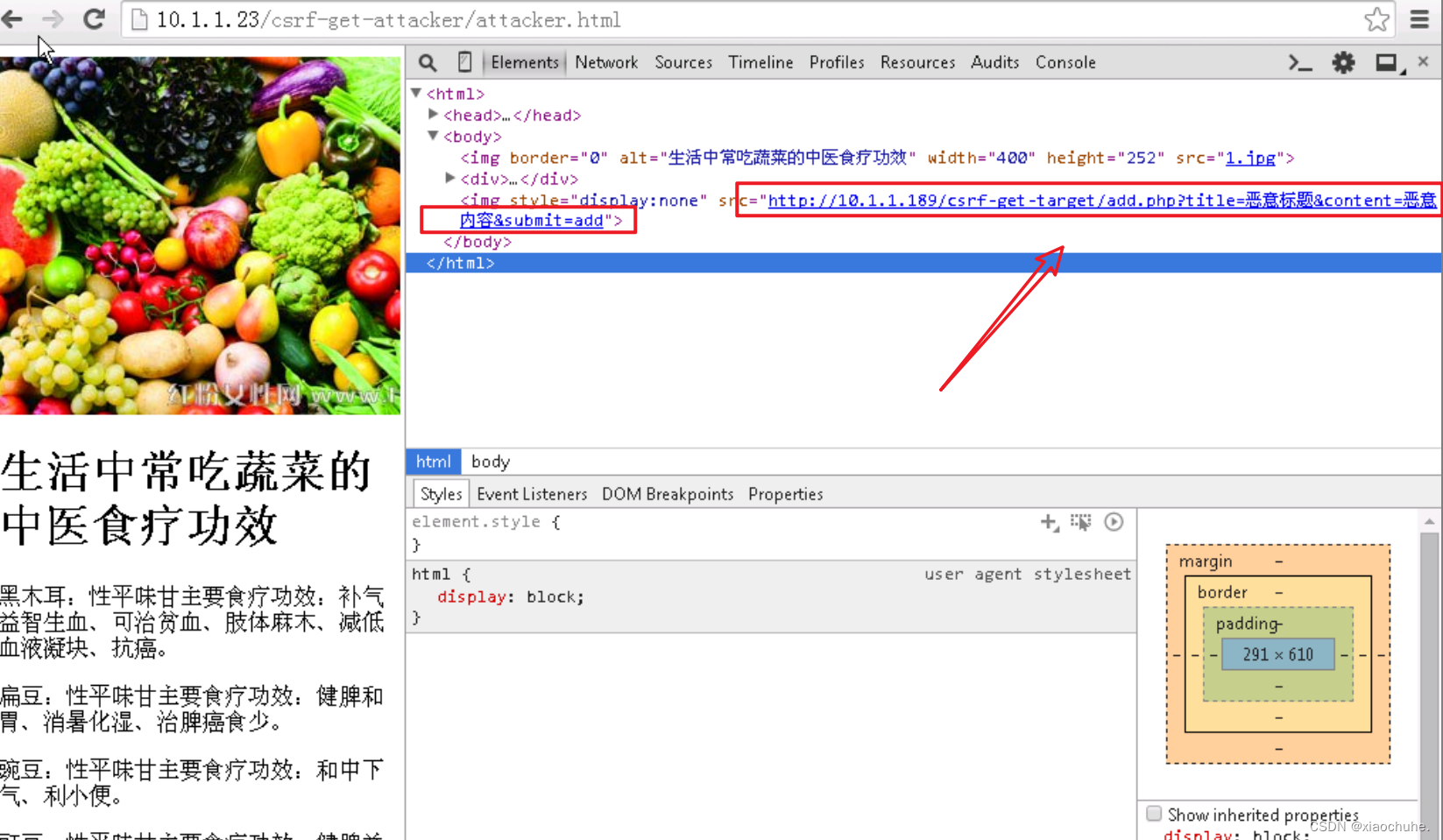
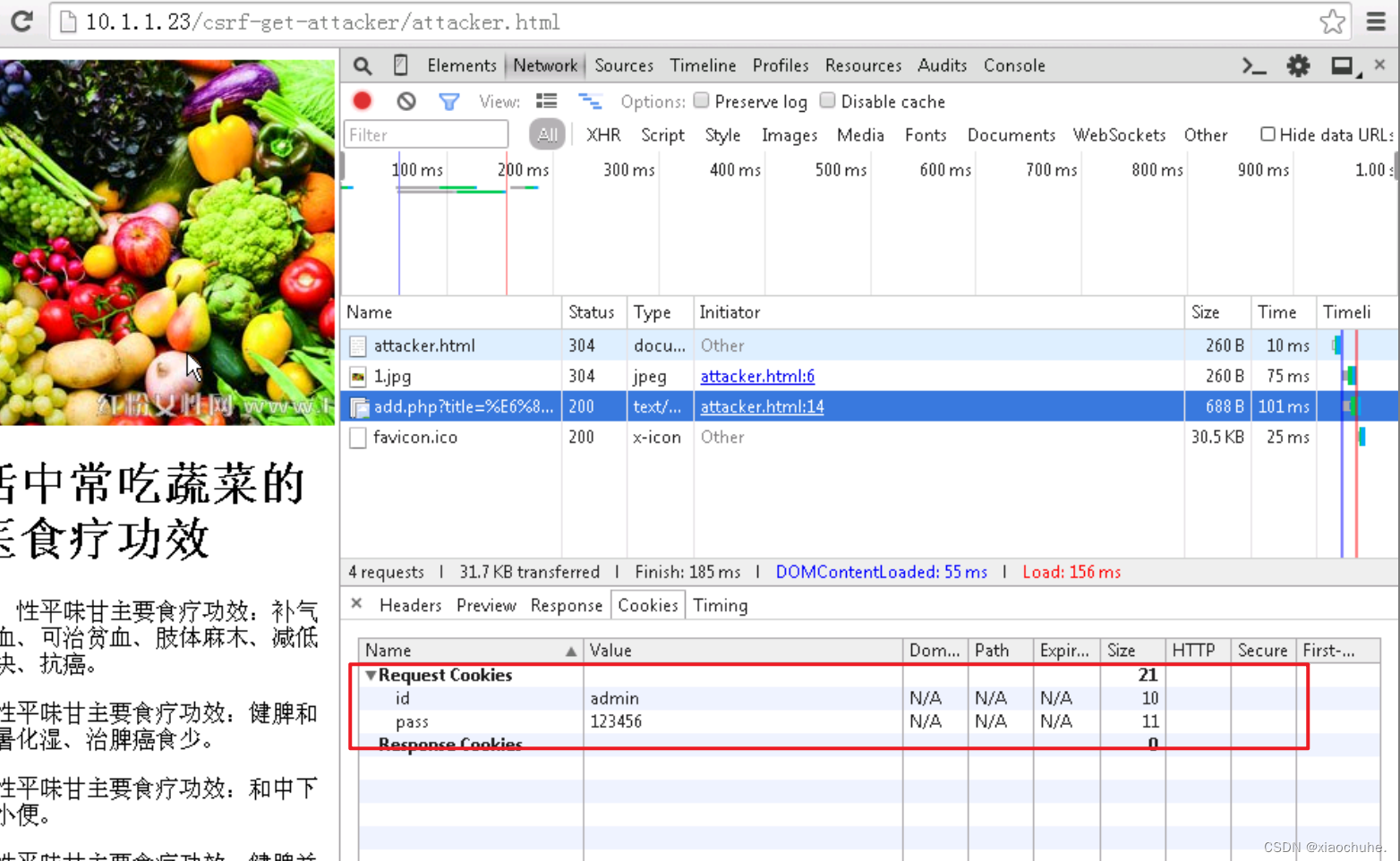
4. Log in to the malicious website and view CSRF Attack effect , The user creates a new tab in the browser , Visit malicious websites : http://10.1.1.23/csrf-get-attacker/attacker.html We found that the malicious website looks like a normal web page , But in fact, malicious websites have issued malicious scripts to users in the background , This script makes use of the information saved in the message board before the user logs in Cookie Information , Pretend to be a user and leave a message on the message board .
 5. Revisit the message board website : http://10.1.1.189/csrf-get-target/list.php I found a malicious message on the message board , As shown in the figure below . The content of this message was just published when our identity was pretended during our login to the malicious website .
5. Revisit the message board website : http://10.1.1.189/csrf-get-target/list.php I found a malicious message on the message board , As shown in the figure below . The content of this message was just published when our identity was pretended during our login to the malicious website .
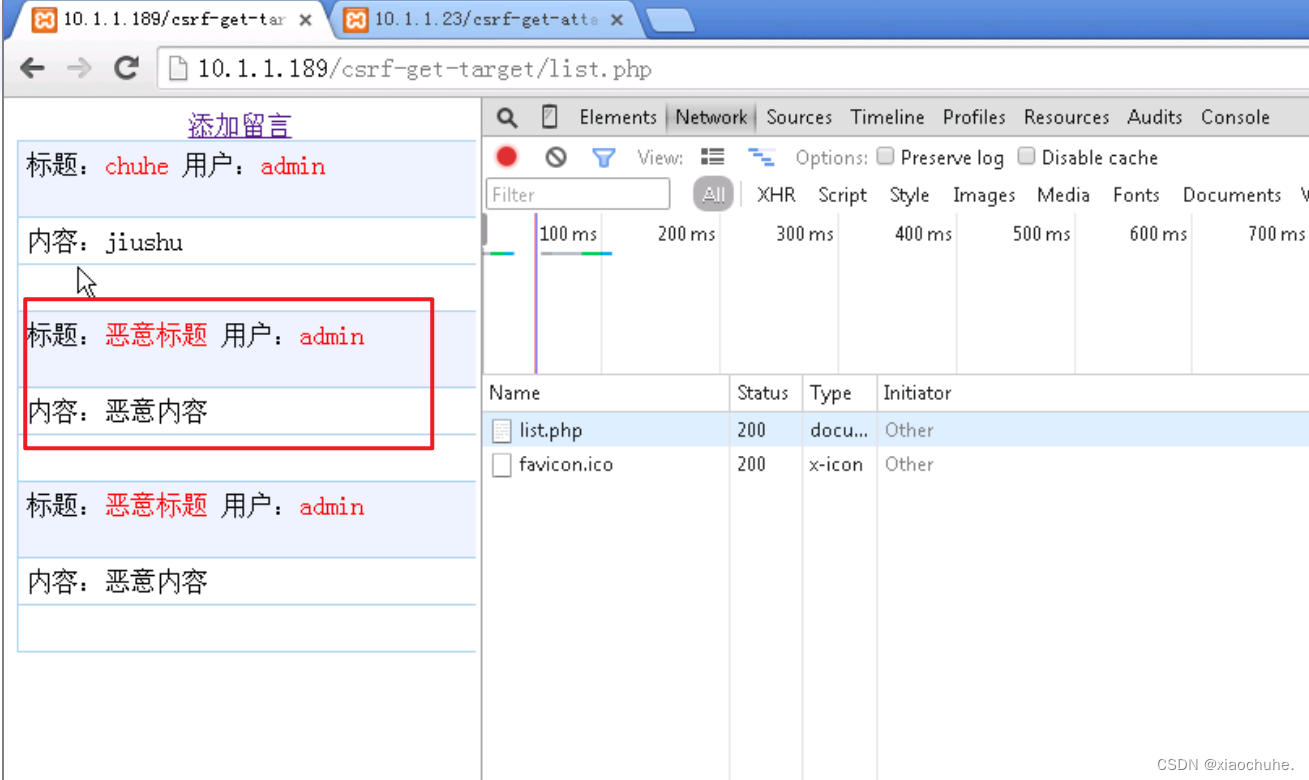
Review malicious website code , understand CSRF Attack principle :
You can see that in the code , The malicious website implanted a <img> label , Because it passes CSS Style set to hidden , So we didn't see the actual label content during the visit . This tag is set by src Address , Sent a malicious message request to the message board website . Because the browser saves our identity on the message board website Cookie, And automatically send Cookie Attached , So the malicious website successfully stole our identity , Completed a malicious message behavior , This is based on GET Requested CSRF The whole process of attack .
( Two ) be based on Post Formal CSRF attack
1. Follow the method in step 1 , Recapture the uploaded packets , Check the message content format :
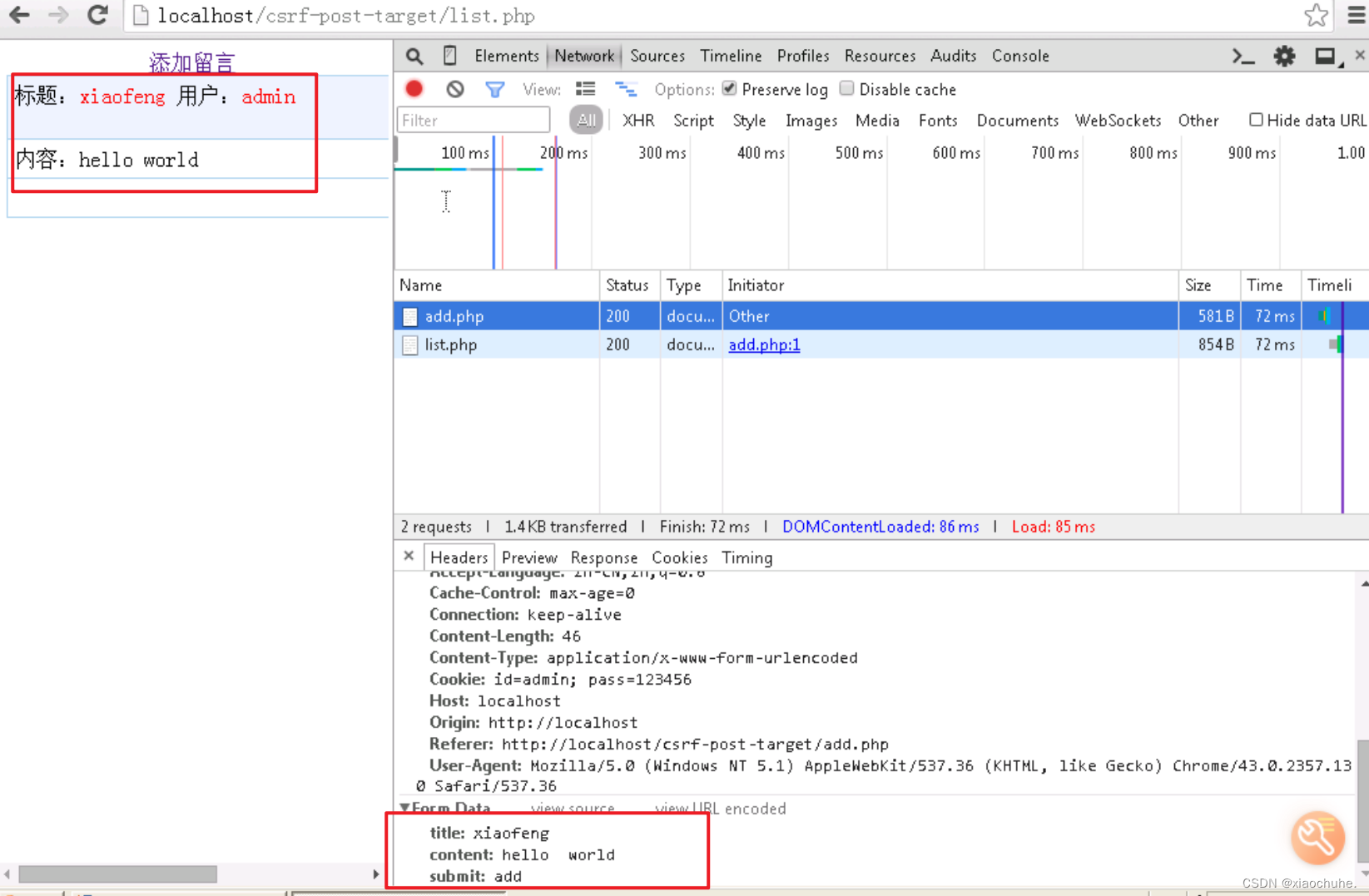
You can see from the screenshot , What we entered in the message board , Attached to HTTP Requested Data Sent to the server in the domain , This parameter field is stored in HTTP Data The request in the domain is called Post request .
2. Create a new tab in the browser , Visit malicious websites :http://10.1.1.23/csrf-post-attacker/attacker.html
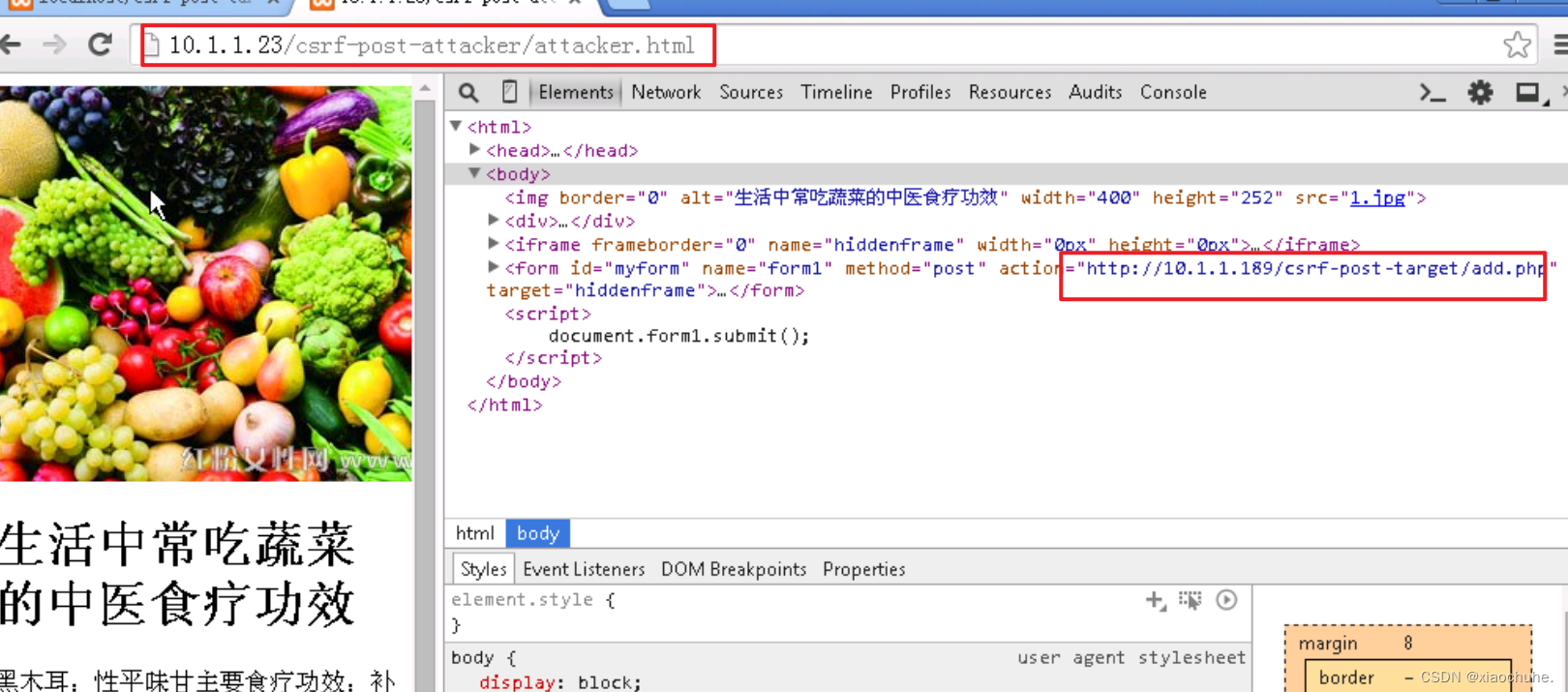
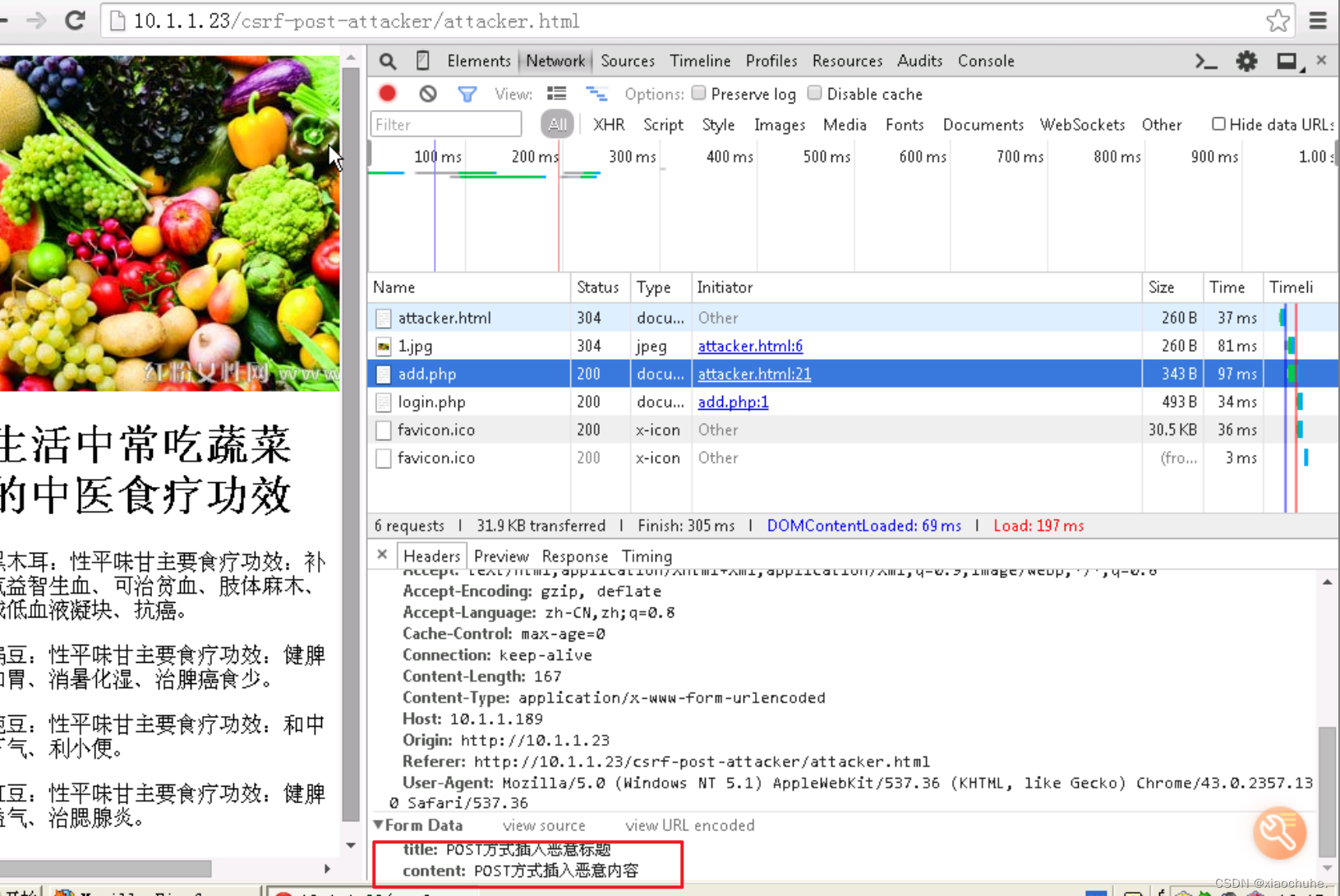
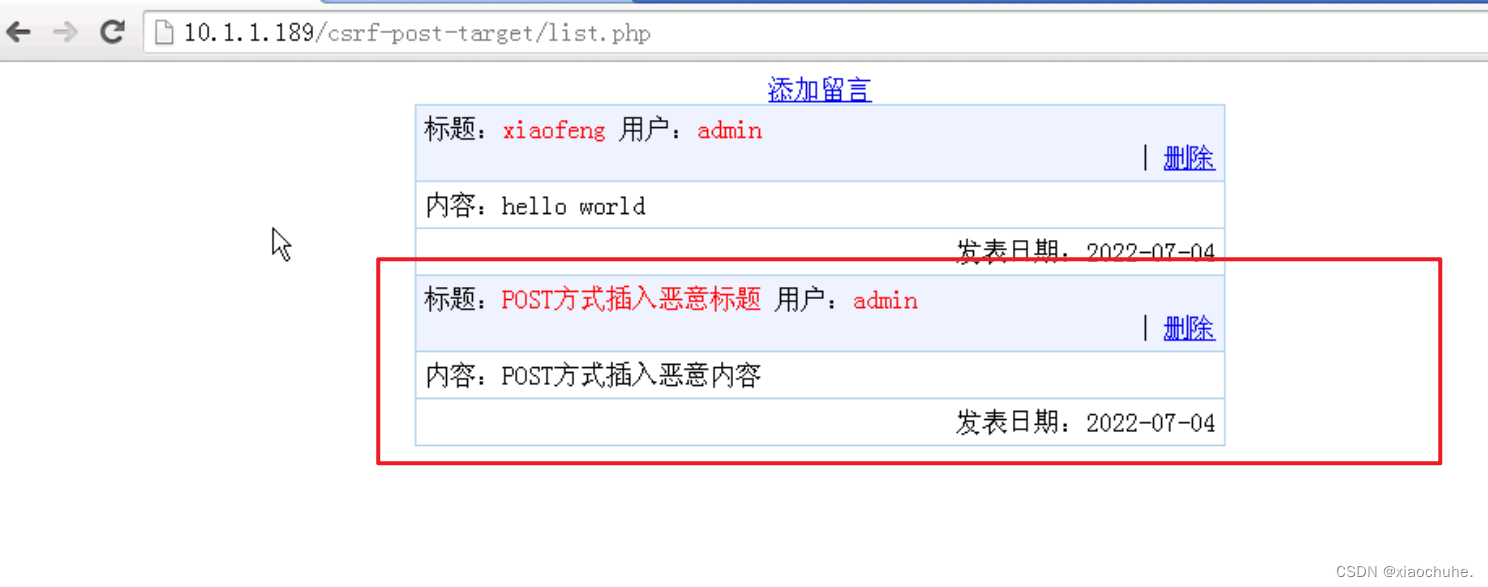 I found a malicious message on the message board . The content of this message was just published when our identity was pretended during our login to the malicious website .
I found a malicious message on the message board . The content of this message was just published when our identity was pretended during our login to the malicious website .
Review malicious website code , understand CSRF Attack principle :
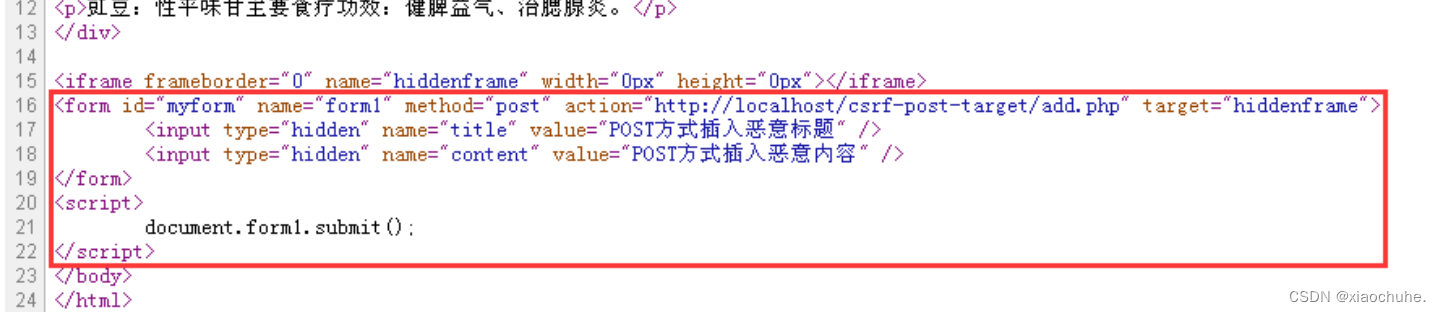
You can see that in the code , The malicious website implanted a form Forms , Of this form action Set as the address of the message website . At the same time, there is another segment implanted Javascript Code , The function of this code is to automatically submit form The form data . such , When the user visits the malicious website , In fact, it passes Post Method sends a malicious message request to the message board .
5、 ... and 、 Bug repair
● Verify requested Referer value , If Referer Is a domain name starting with your own website , It means that the request comes from the website itself , It's legal. . If Referer Is another website domain name or blank , It could be CSRF attack , Then the server should reject the request , However, this method may be bypassed .
● CSRF The attack was successful , It's because an attacker can fake a user's request , thus , To resist CSRF The key to the attack is : Put information in the request that the attacker cannot forge . For example, it can be in HTTP Was added a request in the form of randomly generated parameter token, And verify on the server side token, If not in the request token perhaps token The content of is incorrect , It is considered that the request may be CSRF Attack to reject the request .
Experimental environment : Hetian Laboratory
Reference resources : Hetian network security laboratory - Professional network security \ Network shooting range of information security online experimental service
Warning
Do not Use the content mentioned in this article Breach of law .
this paper No guarantee is given !
边栏推荐
- 第三季百度网盘AI大赛盛夏来袭,寻找热爱AI的你!
- node の SQLite
- Five data structures of redis
- F200 - UAV equipped with domestic open source flight control system based on Model Design
- Redis的五种数据结构
- Jerry's watch reading setting status [chapter]
- Ms-tct: INRIA & SBU proposed a multi-scale time transformer for motion detection. The effect is SOTA! Open source! (CVPR2022)...
- Introduction to the usage of model view delegate principal-agent mechanism in QT
- celery最佳实践
- Implementation of queue
猜你喜欢

Recursive way
30 minutes to understand PCA principal component analysis
【LeetCode第 300 场周赛】
![[Android] kotlin code writing standardization document](/img/d5/53d6a75e87af15799bf7e5d6eb92a5.png)
[Android] kotlin code writing standardization document
Maixll-Dock 摄像头使用
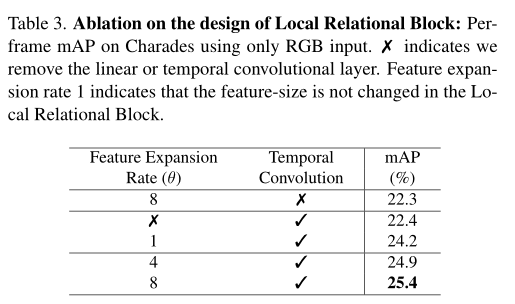
Ms-tct: INRIA & SBU proposed a multi-scale time transformer for motion detection. The effect is SOTA! Open source! (CVPR2022)...

SAP Fiori 应用索引大全工具和 SAP Fiori Tools 的使用介绍

关于这次通信故障,我想多说几句…
![[swoole series 2.1] run the swoole first](/img/cd/88abf7e83e9d9d416051b33263690b.png)
[swoole series 2.1] run the swoole first

2019 Alibaba cluster dataset Usage Summary
随机推荐
Compilation principle - top-down analysis and recursive descent analysis construction (notes)
使用block实现两个页面之间的传统价值观
【Swoole系列2.1】先把Swoole跑起来
Docker安装Redis
C语言高校实验室预约登记系统
带你穿越古罗马,元宇宙巴士来啦 #Invisible Cities
Take you through ancient Rome, the meta universe bus is coming # Invisible Cities
atcoder它A Mountaineer
Comparative examples of C language pointers *p++, * (p++), * ++p, * (++p), (*p) + +, +(*p)
win10系统下插入U盘有声音提示却不显示盘符
微信为什么使用 SQLite 保存聊天记录?
图片缩放中心
The integrated real-time HTAP database stonedb, how to replace MySQL and achieve nearly a hundredfold performance improvement
测试123
Jerry's watch reading setting status [chapter]
C language exchanges two numbers through pointers
Introduction to the usage of model view delegate principal-agent mechanism in QT
Easy to use PDF to SVG program
Tree-LSTM的一些理解以及DGL代码实现
Top command details