当前位置:网站首页>Computing level network notes
Computing level network notes
2022-07-03 09:11:00 【BBQ】
1.URL


The first level domain name is stipulated by international organizations , Just those .
The secondary domain name is applied to the national institution , The largest agent in China is China wanwang ( Artificial application , The only global , Judge the snapper website by this )
The third level domain name is defined by itself
2. Internet access method

ADSL: Find Telecom mobile broadband , Use the telephone line to surf the Internet , Dial-up Internet access



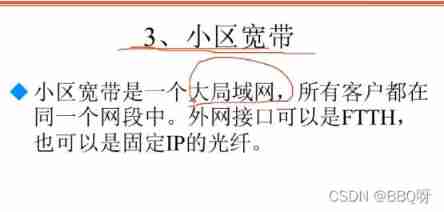
Community broadband : Broadband sharing , Big lan , All information on the Internet is in the LAN , Others can monitor and share through LAN through technical means , Although some have made network segment separation , However, all equipment online information must pass through the general router of the community , In fact, it's still not safe .

3.OSI Of 7 Layer model
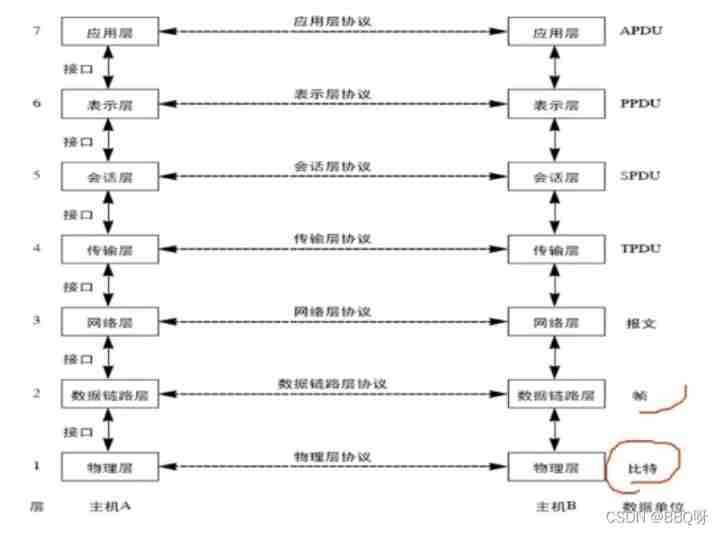
The real data transmission is the lower four layers , A unit with data transmission , The upper three layers are for users to interact ,
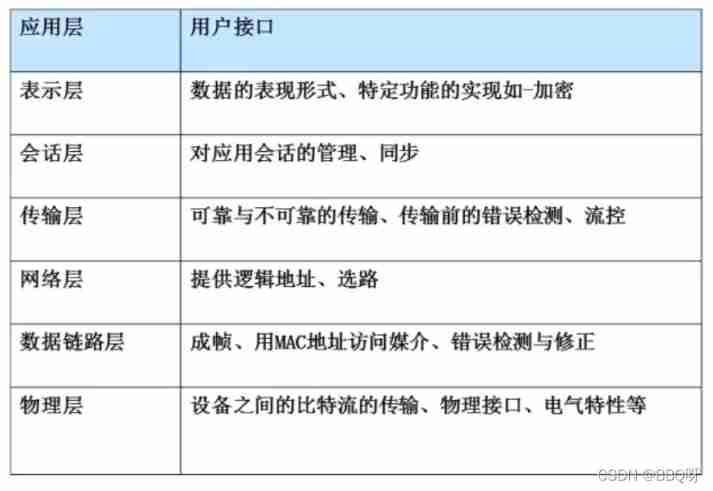
The physical layer : For example, the physical connection between the computer host and the TV screen
Data link layer : The data to be transmitted , Join in MAC Address ( The addresses of the two hosts , For example, each network card comes with one as soon as it leaves the factory MAC Address , LAN internal devices , by MAC Address for transmission )
The network layer : The data to be transmitted , Join in IP Address , Equivalent to the address of a letter .
Transport layer : Determine the transmitted data , Is it transmitted in a reliable or unreliable way ( The distribution corresponds to TCP UDP agreement ), And error checking and flow control . Will add the data to the header , For example, mail delivery , Will be added to the sender's source port , The mail port is 25, Then write the target port of the recipient ,110. The port number is equivalent to the sender and receiver of a letter , Determine which service this letter is sent to , That is, let the receiver know which software is sent to which local machine to process the received data .
The session layer : Determine whether the user has a remote session , Don't pass it down if you don't need it
The presentation layer : Data representation of transmitted data , For example, documents transferred , Conduct ASCII Code said , And compression encryption . The data layer of the receiver , Judge what the received data is , It's documentation , it ASCII Code code
application layer : Interface between user and computing level
4.TCP Four layer model of
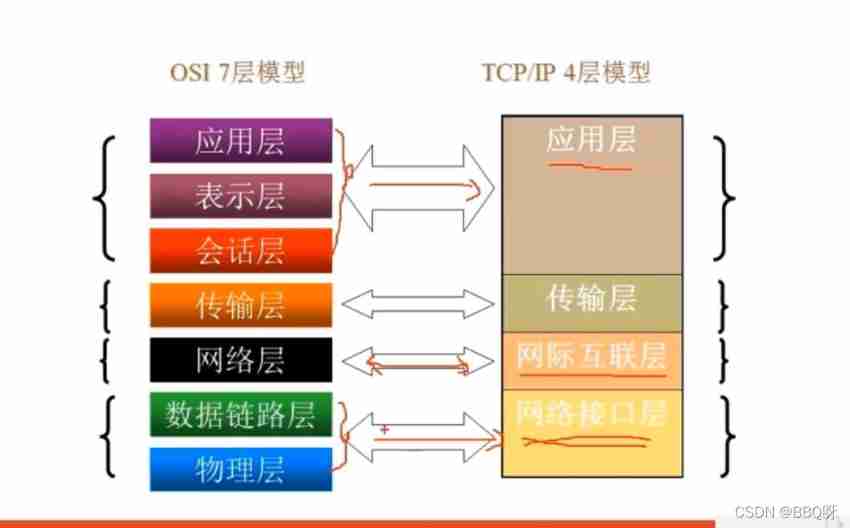
1. Network interface layer

There's a ARP Address resolution protocol , That is, through IP The address can be found MAC Address , This is what the switch does , Learn from everyone MAC Address , And record it in your cache .
2. The network layer

3. Transport layer :

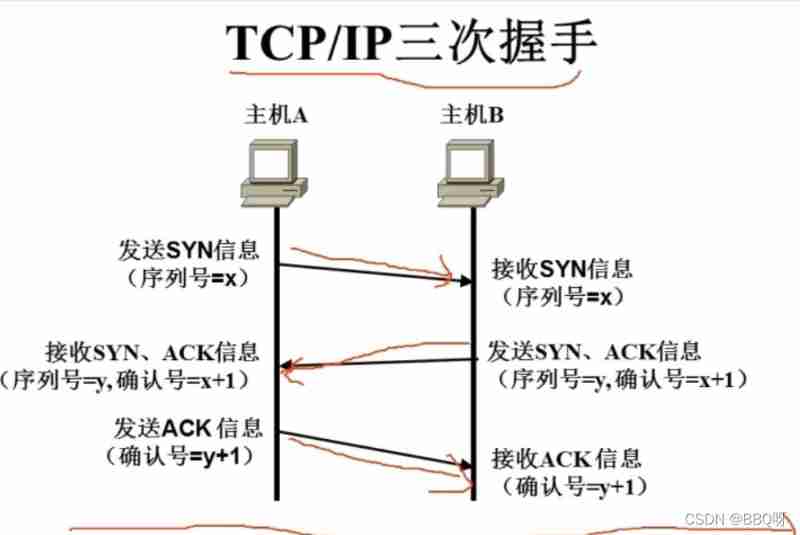
and UDP It's a direct message , Handshake without prior communication , It's like texting , But faster , Occasions with high real-time performance , and TCP It is an occasion requiring high reliability .
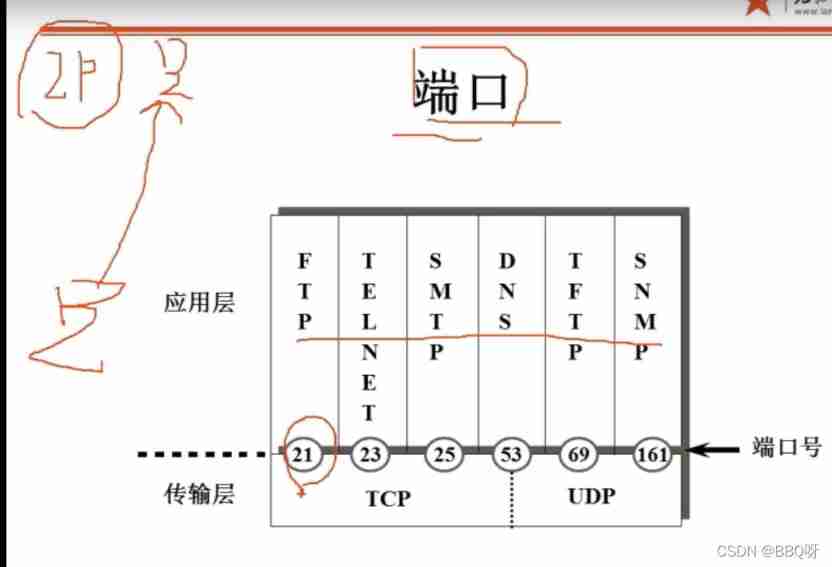
The port number can be changed , But some conventional port numbers remain unchanged . You can check the common ports ( Known as port ) Determine which services the computer has turned on .
4. application layer

5. Data encapsulation process
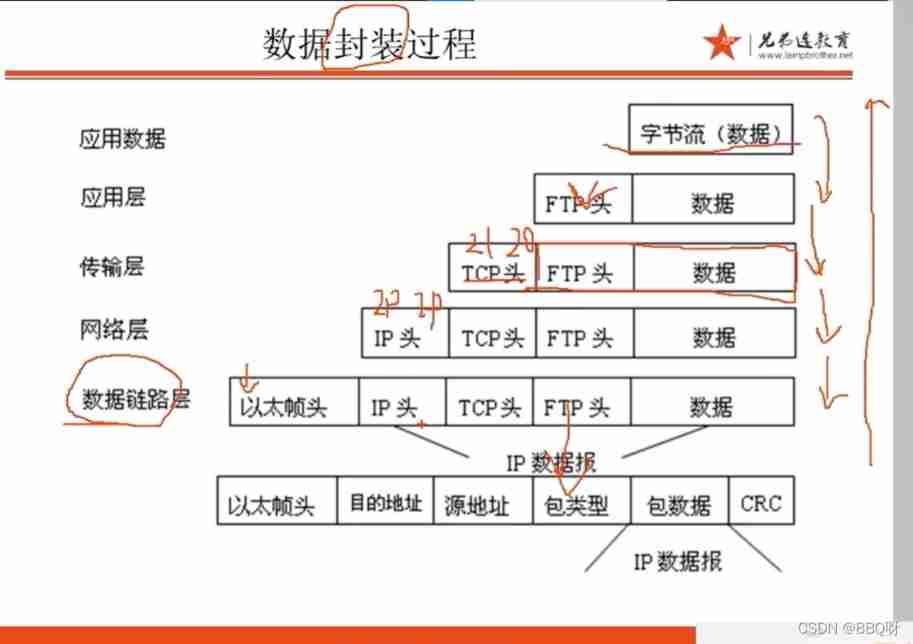
5. Network layer protocols and IP Address partition
1.
2.IP


IP Address range
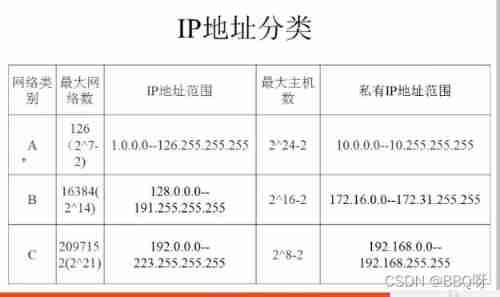
IP The previous number of the address represents the network segment , Only this number is the same , That is, in the same network segment , Only in the LAN can they communicate with each other , Otherwise, the communication between different network segments can only be carried out through the router . But in the same network segment IP Address , As long as you can communicate with each other through a switch .
Ordinary IP You have to buy , You can't just use it , But private IP You can use , And as long as it is in a LAN , Can overlap . But Intranet IP You cannot directly access the public network , Public network IP You can't directly access the intranet .
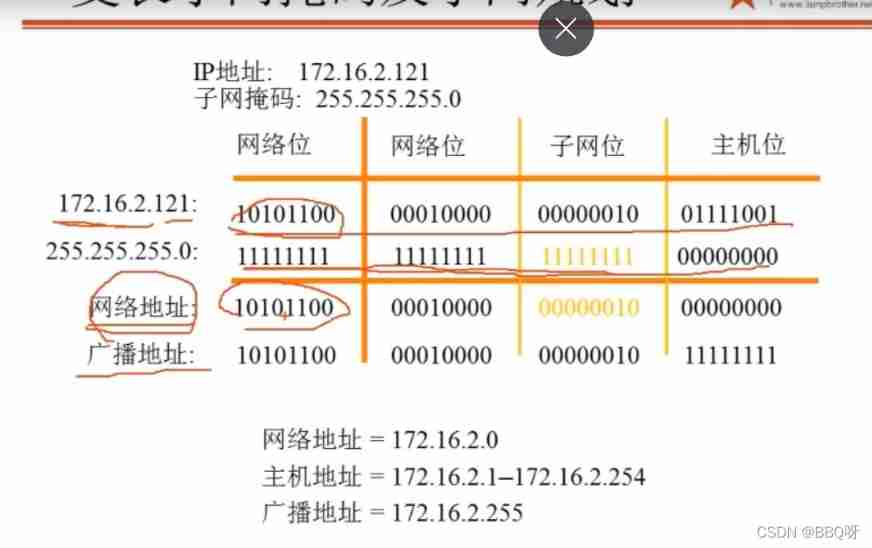
2. Subnet mask

The subnet mask is 1 The bits of represent different network segments , by 0 Represents different hosts
3. Network address and broadcast address
The network address represents the starting address of a network segment , The broadcast address represents the last address of a network segment
4.ICMP agreement

Mainly come Pin
边栏推荐
- How to check whether the disk is in guid format (GPT) or MBR format? Judge whether UEFI mode starts or legacy mode starts?
- 网络安全必会的基础知识
- 【点云处理之论文狂读前沿版10】—— MVTN: Multi-View Transformation Network for 3D Shape Recognition
- 我们有个共同的名字,XX工
- [point cloud processing paper crazy reading classic version 9] - pointwise revolutionary neural networks
- Method of intercepting string in shell
- [point cloud processing paper crazy reading classic version 14] - dynamic graph CNN for learning on point clouds
- 【点云处理之论文狂读经典版11】—— Mining Point Cloud Local Structures by Kernel Correlation and Graph Pooling
- Using variables in sed command
- The "booster" of traditional office mode, Building OA office system, was so simple!
猜你喜欢

On the setting of global variable position in C language

LeetCode 515. 在每个树行中找最大值
LeetCode 871. 最低加油次数

LeetCode 438. 找到字符串中所有字母异位词

Slice and index of array with data type

Markdown learning
![[point cloud processing paper crazy reading classic version 11] - mining point cloud local structures by kernel correlation and graph pooling](/img/40/e0c7bad60b19cafa467c229419ac21.png)
[point cloud processing paper crazy reading classic version 11] - mining point cloud local structures by kernel correlation and graph pooling

2022-1-6 Niuke net brush sword finger offer
Pic16f648a-e/ss PIC16 8-bit microcontroller, 7KB (4kx14)

Sword finger offer II 029 Sorted circular linked list
随机推荐
【点云处理之论文狂读经典版7】—— Dynamic Edge-Conditioned Filters in Convolutional Neural Networks on Graphs
[point cloud processing paper crazy reading frontier version 8] - pointview gcn: 3D shape classification with multi view point clouds
PIC16F648A-E/SS PIC16 8位 微控制器,7KB(4Kx14)
<, < <,>, > > Introduction in shell
Too many open files solution
[point cloud processing paper crazy reading classic version 7] - dynamic edge conditioned filters in revolutionary neural networks on Graphs
Using variables in sed command
Severity code description the project file line prohibits the display of status error c2440 "initialization": unable to convert from "const char [31]" to "char *"
Problems in the implementation of lenet
Methods of using arrays as function parameters in shell
2022-2-14 learning xiangniuke project - generate verification code
Data mining 2021-4-27 class notes
【点云处理之论文狂读经典版14】—— Dynamic Graph CNN for Learning on Point Clouds
树形DP AcWing 285. 没有上司的舞会
樹形DP AcWing 285. 沒有上司的舞會
干货!零售业智能化管理会遇到哪些问题?看懂这篇文章就够了
传统办公模式的“助推器”,搭建OA办公系统,原来就这么简单!
Common DOS commands
AcWing 785. Quick sort (template)
Find the combination number acwing 885 Find the combination number I