当前位置:网站首页>FTP server, ssh server (super brief)
FTP server, ssh server (super brief)
2022-07-06 01:55:00 【-Joucy-】
FTP The server 、SSH The server ( Super simple )
One 、FTP The server
reflection : How to transfer documents to Ubuntu On a host ?
1、U Disk copy
2、 Network transmission (FTP、SFTP)File upload and download :
client FileZilla(Windows)
The server vsftpd(Ubuntu)
Two 、SSH The server
Use SSH agreement , Can achieve :
1、 Remote terminal
2、 File transferThe specific methods
1、 Use Xshell Remote login
2、 Use Xftp Transfer files
边栏推荐
- [understanding of opportunity-39]: Guiguzi - Chapter 5 flying clamp - warning 2: there are six types of praise. Be careful to enjoy praise as fish enjoy bait.
- 安装Redis
- [技术发展-28]:信息通信网大全、新的技术形态、信息通信行业高质量发展概览
- Reasonable and sensible
- 【Flask】获取请求信息、重定向、错误处理
- 1. Introduction to basic functions of power query
- NLP fourth paradigm: overview of prompt [pre train, prompt, predict] [Liu Pengfei]
- Computer graduation design PHP college student human resources job recruitment network
- internship:项目代码所涉及陌生注解及其作用
- Redis守护进程无法停止解决方案
猜你喜欢
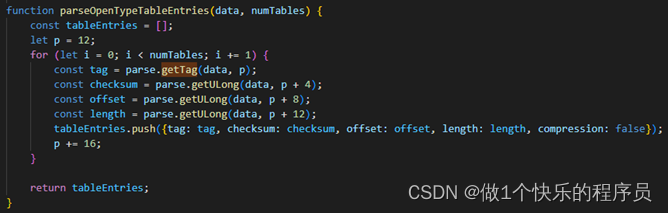
Extracting key information from TrueType font files
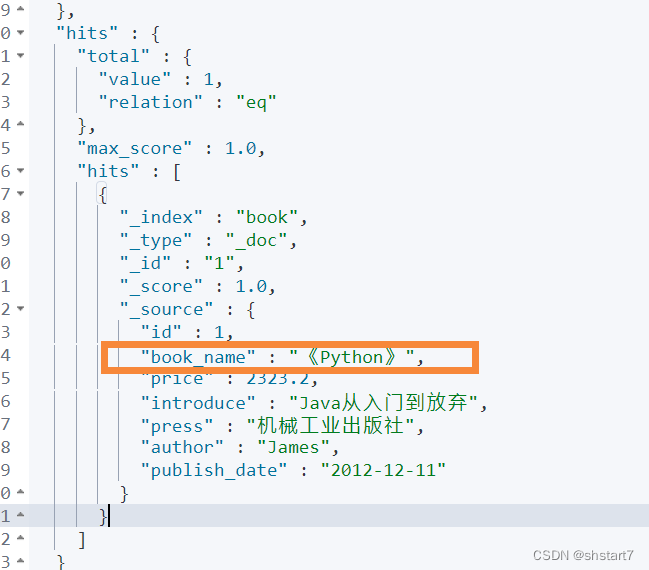
Alibaba canal usage details (pit draining version)_ MySQL and ES data synchronization

02. Go language development environment configuration
PHP campus movie website system for computer graduation design
![[机缘参悟-39]:鬼谷子-第五飞箝篇 - 警示之二:赞美的六种类型,谨防享受赞美快感如同鱼儿享受诱饵。](/img/3c/ec97abfabecb3f0c821beb6cfe2983.jpg)
[机缘参悟-39]:鬼谷子-第五飞箝篇 - 警示之二:赞美的六种类型,谨防享受赞美快感如同鱼儿享受诱饵。
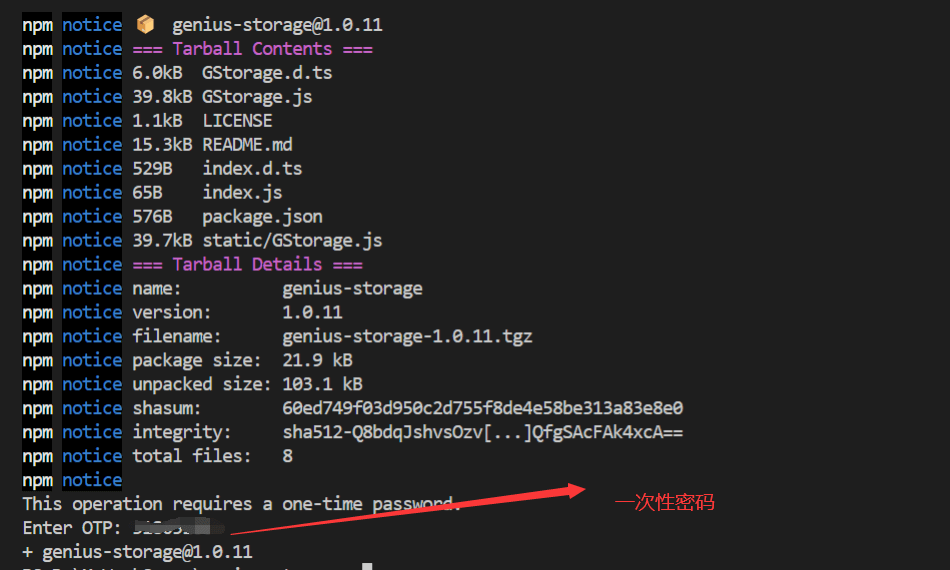
Publish your own toolkit notes using NPM
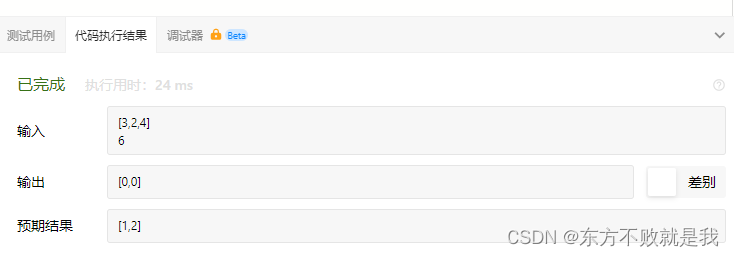
leetcode-两数之和
C web page open WinForm exe
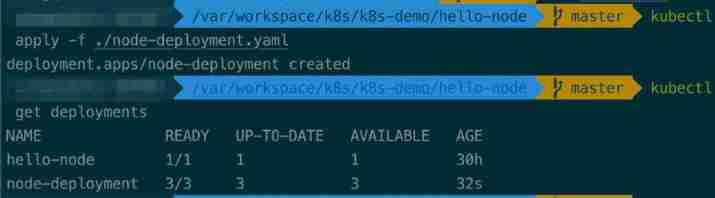
Kubernetes stateless application expansion and contraction capacity

02.Go语言开发环境配置
随机推荐
Format code_ What does formatting code mean
Redis守护进程无法停止解决方案
Redis list
Cookie concept, basic use, principle, details and Chinese transmission
Force buckle 9 palindromes
Pangolin Library: subgraph
2022年PMP项目管理考试敏捷知识点(8)
selenium 元素定位(2)
[flask] response, session and message flashing
leetcode3、实现 strStr()
[flask] obtain request information, redirect and error handling
genius-storage使用文档,一个浏览器缓存工具
Sword finger offer 12 Path in matrix
安装Redis
Basic operations of databases and tables ----- primary key constraints
UE4 unreal engine, editor basic application, usage skills (IV)
Blue Bridge Cup embedded_ STM32 learning_ Key_ Explain in detail
selenium 等待方式
Comments on flowable source code (XXXV) timer activation process definition processor, process instance migration job processor
How to get all sequences in Oracle database- How can I get all sequences in an Oracle database?