当前位置:网站首页>Redis string type
Redis string type
2022-07-06 01:40:00 【Freezing point contract】
String type :string
- String yes Redis Most basic types , You can understand that Memcached As like as two peas , One key Corresponding to one value;
- String Type is binary safe , signify Redis Of string Can contain any data . such as jpg Picture or serialized object
- String The type is Redis Basic data types , One Redis Middle string value At most 512M
Common commands
Add key value pair
set <key> <value>obtain key Corresponding value
get <key>Will specify value Append to original value At the end of
append <key> <value>obtain value The length of
strlen <key>Only when key When it doesn't exist key Add
setnx <key> <value>take key Increase the value of the number stored in 1, Can only operate on numeric values , If it is empty , The new value added is 1
incr <key>take key The number stored in minus 1, Can only operate on numeric values , If it is empty , The new value added is -1
decr <key>take key The numerical value stored in the custom step size increases or decreases
incrby <key> <step> decrby <key> <step>
The concept of atomic operation
- Atomic operations are operations that are not interrupted by the thread scheduling mechanism , Once this operation begins , It runs until the end , There won't be any context switch ( Switch to another thread )
- In a single thread , Operations that can be performed in a single instruction can be considered as " Atomic manipulation ", Because interrupts can only occur between instructions
- In multithreading , Can't be used by other processes ( Threads ) The interrupted operation is called atomic operation
- Redis The atomicity of a single command is mainly due to Redis The single thread
String batch operation command
At the same time for multiple key Set the value
mset <key1> <value1> <key2> <value2> ...Get multiple at the same time value
mget <key1> <key2> ...Set up multiple value, And key non-existent ( Atomicity : One existence fails )
msetnx <key1> <value1> <key2> <value2> ...
Other commands
Get substring , From the index start To stop( Left and right closed )
getrang <key> <start> <stop>Use... From the specified index location value Covering substring
setrang <key> <index> <value>Set the expiration time while setting the key value pair ( Company :s)
setex <key> <time> <value>To old change new ( Read original value , And write )
getset <key> <value>
String data structure
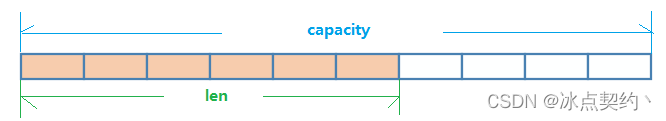
- String The data structure of is a simple dynamic string (Simple Dynamic String, abbreviation SDS). Is a string that can be modified , The internal structure is similar to Java Of ArrayList, Reduce the frequent allocation of memory by pre allocating redundant space
- Space actually allocated internally for the current string capacity Generally higher than the actual string length len. When the string length is less than 1M when , Expansion is to double the existing space , If exceeded 1M, When expanding, it will only expand more at one time 1M Space . Note that the maximum string length is 512M
边栏推荐
- Electrical data | IEEE118 (including wind and solar energy)
- yii中console方法调用,yii console定时任务
- False breakthroughs in the trend of London Silver
- Card 4G industrial router charging pile intelligent cabinet private network video monitoring 4G to Ethernet to WiFi wired network speed test software and hardware customization
- ClickOnce 不支持请求执行级别“requireAdministrator”
- 竞赛题 2022-6-26
- Basic operations of databases and tables ----- unique constraints
- Cookie concept, basic use, principle, details and Chinese transmission
- 2022年PMP项目管理考试敏捷知识点(8)
- Huawei converged VLAN principle and configuration
猜你喜欢

General operation method of spot Silver
MATLB | real time opportunity constrained decision making and its application in power system
Alibaba-Canal使用详解(排坑版)_MySQL与ES数据同步
Huawei Hrbrid interface and VLAN division based on IP
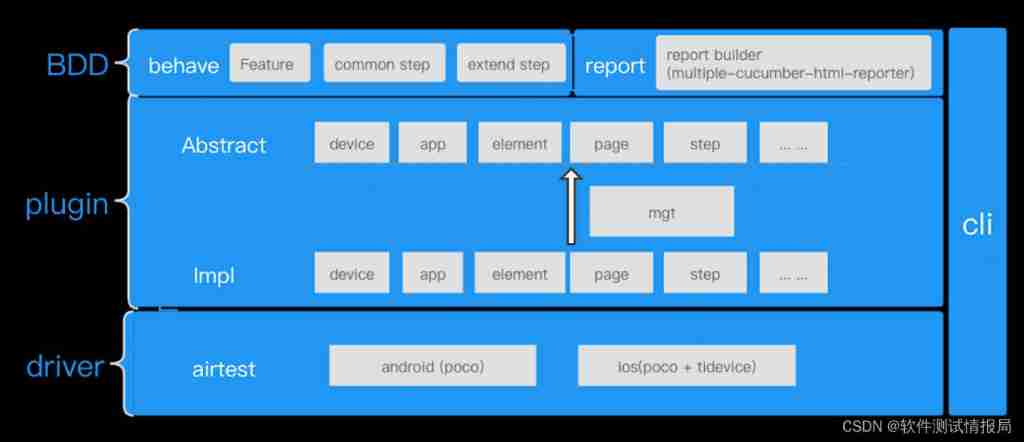
Open source | Ctrip ticket BDD UI testing framework flybirds

Initialize MySQL database when docker container starts

How to see the K-line chart of gold price trend?
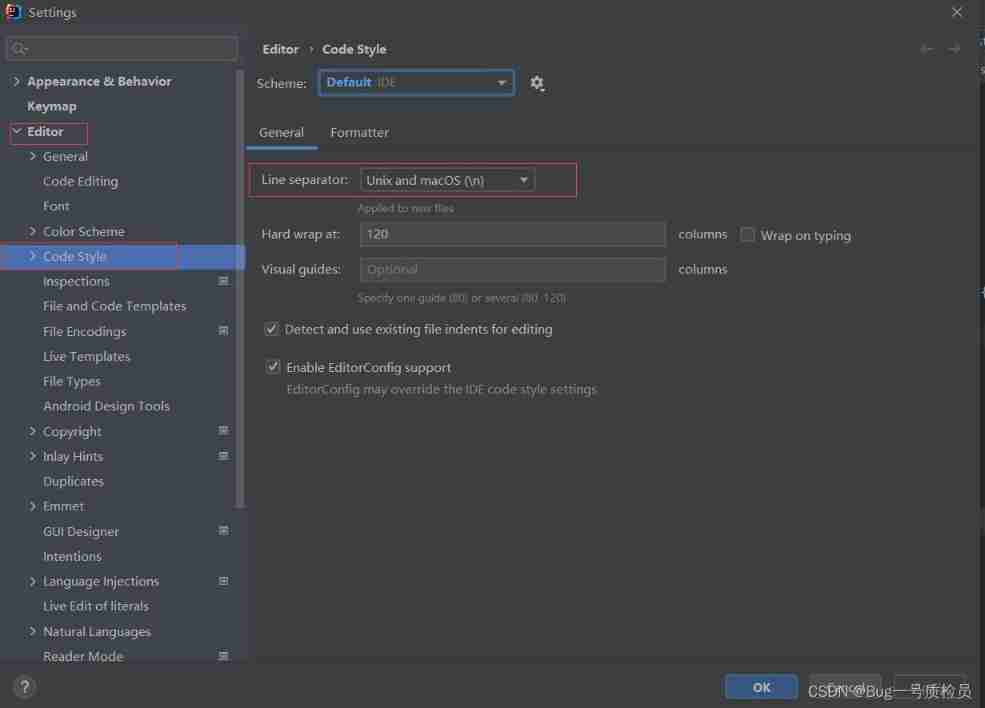
Idea sets the default line break for global newly created files
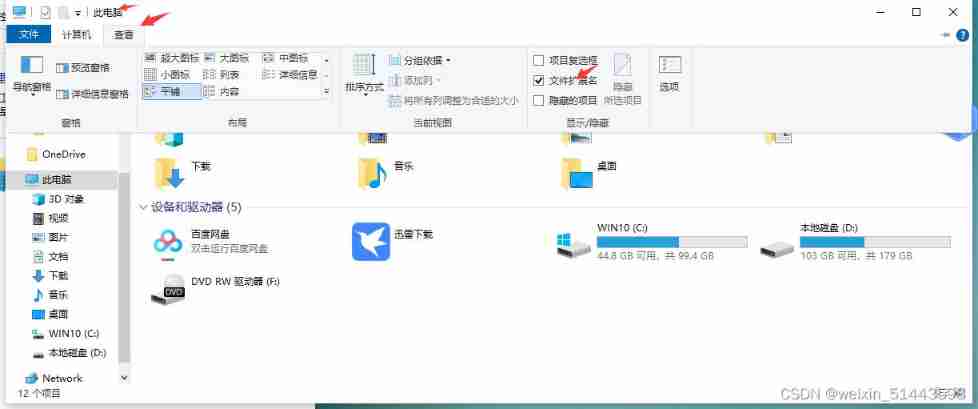
Win10 add file extension
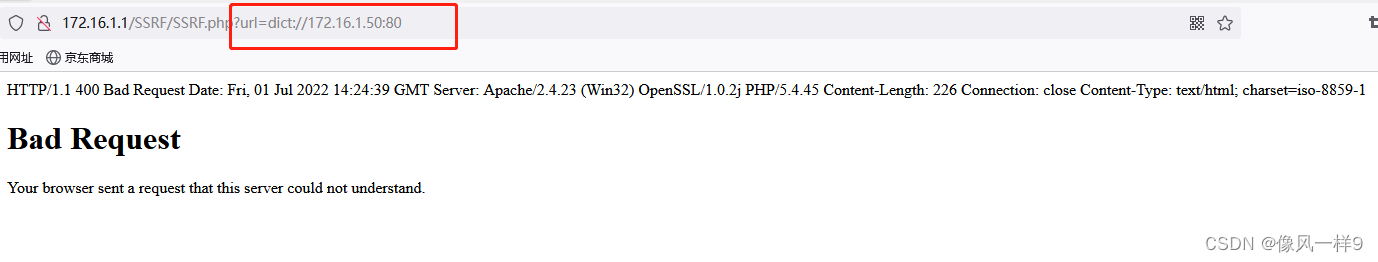
【SSRF-01】服务器端请求伪造漏洞原理及利用实例
随机推荐
Cookie concept, basic use, principle, details and Chinese transmission
Basic process and testing idea of interface automation
Leetcode3. Implement strstr()
You are using pip version 21.1.1; however, version 22.0.3 is available. You should consider upgradin
Leetcode sword finger offer 59 - ii Maximum value of queue
ORA-00030
How to see the K-line chart of gold price trend?
National intangible cultural heritage inheritor HD Wang's shadow digital collection of "Four Beauties" made an amazing debut!
037 PHP login, registration, message, personal Center Design
Cadre du Paddle: aperçu du paddlelnp [bibliothèque de développement pour le traitement du langage naturel des rames volantes]
Numpy array index slice
[solved] how to generate a beautiful static document description page
Leetcode skimming questions_ Sum of squares
Docker compose configures MySQL and realizes remote connection
Unity VR resource flash surface in scene
MCU lightweight system core
How does Huawei enable debug and how to make an image port
dried food! Accelerating sparse neural network through hardware and software co design
Force buckle 1020 Number of enclaves
Kubernetes stateless application expansion and contraction capacity