当前位置:网站首页>Xin'an Second Edition: Chapter 12 network security audit technology principle and application learning notes
Xin'an Second Edition: Chapter 12 network security audit technology principle and application learning notes
2022-07-06 17:34:00 【Moon Dream Studio】
One 、 The outline of this chapter requires
12、 Principles and application of network audit technology
12.1 Overview of network security audit
• Network security audit concept • Purpose of network security audit
12.2 Composition and type of network security audit system
• Composition of network security audit system
• Operation mechanism of network security audit system
• Network security audit system type ( Network communication security audit 、 Operating system security audit 、 Database security audit 、 Application system security audit 、 Operation and maintenance safety audit )
12.3 Network security audit mechanism and implementation technology
• Network security audit data collection
• Network traffic data acquisition technology ( Switch port mirroring 、 Network sniffing ) System log data collection technology (Syslog、FTP、SNMP etc. ) Open source tools for network traffic data collection Tepdump Use
• Network audit data analysis technology ( string matching 、 Full text search 、 Data Association 、 Statistical report 、 Visual analysis, etc )
• Network audit data protection technology ( Decentralized management of system users 、 Mandatory access to audit data 、 Audit data encryption 、 Audit data privacy protection 、 Audit data integrity protection 、 Audit data backup )
12.4 Main technical indicators and products of network security audit
• Main technical indicators of network security audit ( Understanding of functional technical indicators 、 Understanding of performance and technical indicators 、 Understanding of safety technical indicators )
• Analysis of working mechanism of network security audit products 、 Understanding of network security audit product standards 、 Applicable scenarios of network security audit products
12.5 Network security audit application
• Network compliance use
• Network electronic forensics
• Network security operation and maintenance guarantee
Two 、 List of important and easy knowledge points in this chapter
12.1 Overview of network security audit
Network security audit refers to the acquisition of information about security related activities of network information systems 、 Record 、 Storage 、 Analysis and utilization of work .</
边栏推荐
- Total / statistics function of MySQL
- mysql的合计/统计函数
- JVM垃圾回收概述
- Interpretation of Flink source code (I): Interpretation of streamgraph source code
- Solr appears write Lock, solrexception: could not get leader props in the log
- [mmdetection] solves the installation problem
- Selenium test of automatic answer runs directly in the browser, just like real users.
- Connect to LAN MySQL
- Virtual machine startup prompt probing EDD (edd=off to disable) error
- Shawshank's sense of redemption
猜你喜欢
Huawei certified cloud computing hica
03 products and promotion developed by individuals - plan service configurator v3.0
Final review of information and network security (based on the key points given by the teacher)
C#版Selenium操作Chrome全屏模式显示(F11)
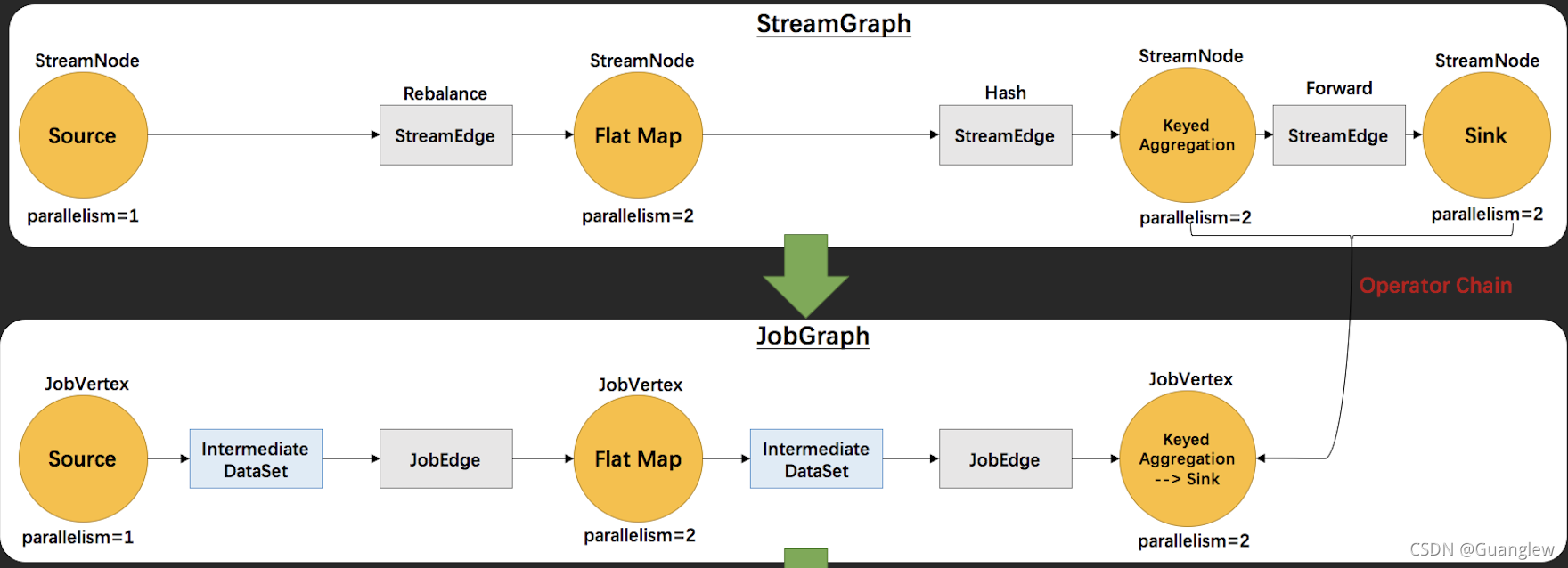
Interpretation of Flink source code (II): Interpretation of jobgraph source code
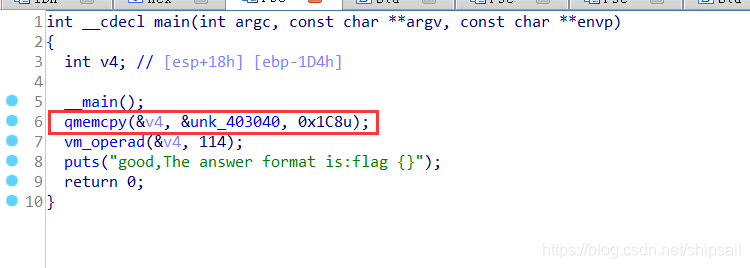
复盘网鼎杯Re-Signal Writeup
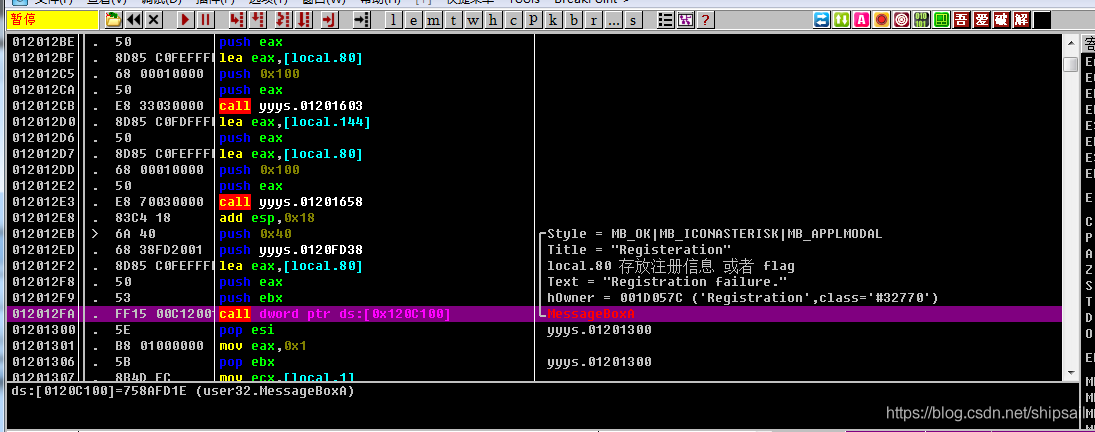
【逆向中级】跃跃欲试
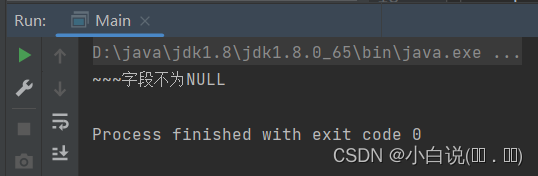
案例:检查空字段【注解+反射+自定义异常】
TCP连接不止用TCP协议沟通

Flink源码解读(二):JobGraph源码解读
随机推荐
Akamai talking about risk control principles and Solutions
Akamai anti confusion
案例:检查空字段【注解+反射+自定义异常】
信息与网络安全期末复习(完整版)
JVM class loading subsystem
Total / statistics function of MySQL
轻量级计划服务工具研发与实践
吴军三部曲见识(四) 大家智慧
自动答题 之 Selenium测试直接运行在浏览器中,就像真正的用户在操作一样。
Flexible report v1.0 (simple version)
mysql的列的数据类型详解
【ASM】字节码操作 ClassWriter 类介绍与使用
Redis quick start
关于Selenium启动Chrome浏览器闪退问题
Programmer orientation problem solving methodology
Redis installation on centos7
Flink analysis (II): analysis of backpressure mechanism
Re signal writeup
[ciscn 2021 South China]rsa writeup
Take you hand-in-hand to do intensive learning experiments -- knock the level in detail