当前位置:网站首页>Nmap: network detection tool and security / port scanner
Nmap: network detection tool and security / port scanner
2022-07-06 01:09:00 【lqonlylove】
One 、 grammar
[email protected]:~$ nmap -help
Nmap 7.80 ( https://nmap.org )
Usage: nmap [Scan Type(s)] [Options] {
target specification}
TARGET SPECIFICATION:
Can pass hostnames, IP addresses, networks, etc.
Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254
-iL <inputfilename>: Input from list of hosts/networks
-iR <num hosts>: Choose random targets
--exclude <host1[,host2][,host3],...>: Exclude hosts/networks
--excludefile <exclude_file>: Exclude list from file
HOST DISCOVERY:
-sL: List Scan - simply list targets to scan
-sn: Ping Scan - disable port scan
-Pn: Treat all hosts as online -- skip host discovery
-PS/PA/PU/PY[portlist]: TCP SYN/ACK, UDP or SCTP discovery to given ports
-PE/PP/PM: ICMP echo, timestamp, and netmask request discovery probes
-PO[protocol list]: IP Protocol Ping
-n/-R: Never do DNS resolution/Always resolve [default: sometimes]
--dns-servers <serv1[,serv2],...>: Specify custom DNS servers
--system-dns: Use OS's DNS resolver --traceroute: Trace hop path to each host SCAN TECHNIQUES: -sS/sT/sA/sW/sM: TCP SYN/Connect()/ACK/Window/Maimon scans -sU: UDP Scan -sN/sF/sX: TCP Null, FIN, and Xmas scans --scanflags <flags>: Customize TCP scan flags -sI <zombie host[:probeport]>: Idle scan -sY/sZ: SCTP INIT/COOKIE-ECHO scans -sO: IP protocol scan -b <FTP relay host>: FTP bounce scan PORT SPECIFICATION AND SCAN ORDER: -p <port ranges>: Only scan specified ports Ex: -p22; -p1-65535; -p U:53,111,137,T:21-25,80,139,8080,S:9 --exclude-ports <port ranges>: Exclude the specified ports from scanning -F: Fast mode - Scan fewer ports than the default scan -r: Scan ports consecutively - don't randomize
--top-ports <number>: Scan <number> most common ports
--port-ratio <ratio>: Scan ports more common than <ratio>
SERVICE/VERSION DETECTION:
-sV: Probe open ports to determine service/version info
--version-intensity <level>: Set from 0 (light) to 9 (try all probes)
--version-light: Limit to most likely probes (intensity 2)
--version-all: Try every single probe (intensity 9)
--version-trace: Show detailed version scan activity (for debugging)
SCRIPT SCAN:
-sC: equivalent to --script=default
--script=<Lua scripts>: <Lua scripts> is a comma separated list of
directories, script-files or script-categories
--script-args=<n1=v1,[n2=v2,...]>: provide arguments to scripts
--script-args-file=filename: provide NSE script args in a file
--script-trace: Show all data sent and received
--script-updatedb: Update the script database.
--script-help=<Lua scripts>: Show help about scripts.
<Lua scripts> is a comma-separated list of script-files or
script-categories.
OS DETECTION:
-O: Enable OS detection
--osscan-limit: Limit OS detection to promising targets
--osscan-guess: Guess OS more aggressively
TIMING AND PERFORMANCE:
Options which take <time> are in seconds, or append 'ms' (milliseconds),
's' (seconds), 'm' (minutes), or 'h' (hours) to the value (e.g. 30m).
-T<0-5>: Set timing template (higher is faster)
--min-hostgroup/max-hostgroup <size>: Parallel host scan group sizes
--min-parallelism/max-parallelism <numprobes>: Probe parallelization
--min-rtt-timeout/max-rtt-timeout/initial-rtt-timeout <time>: Specifies
probe round trip time.
--max-retries <tries>: Caps number of port scan probe retransmissions.
--host-timeout <time>: Give up on target after this long
--scan-delay/--max-scan-delay <time>: Adjust delay between probes
--min-rate <number>: Send packets no slower than <number> per second
--max-rate <number>: Send packets no faster than <number> per second
FIREWALL/IDS EVASION AND SPOOFING:
-f; --mtu <val>: fragment packets (optionally w/given MTU)
-D <decoy1,decoy2[,ME],...>: Cloak a scan with decoys
-S <IP_Address>: Spoof source address
-e <iface>: Use specified interface
-g/--source-port <portnum>: Use given port number
--proxies <url1,[url2],...>: Relay connections through HTTP/SOCKS4 proxies
--data <hex string>: Append a custom payload to sent packets
--data-string <string>: Append a custom ASCII string to sent packets
--data-length <num>: Append random data to sent packets
--ip-options <options>: Send packets with specified ip options
--ttl <val>: Set IP time-to-live field
--spoof-mac <mac address/prefix/vendor name>: Spoof your MAC address
--badsum: Send packets with a bogus TCP/UDP/SCTP checksum
OUTPUT:
-oN/-oX/-oS/-oG <file>: Output scan in normal, XML, s|<rIpt kIddi3,
and Grepable format, respectively, to the given filename.
-oA <basename>: Output in the three major formats at once
-v: Increase verbosity level (use -vv or more for greater effect)
-d: Increase debugging level (use -dd or more for greater effect)
--reason: Display the reason a port is in a particular state
--open: Only show open (or possibly open) ports
--packet-trace: Show all packets sent and received
--iflist: Print host interfaces and routes (for debugging)
--append-output: Append to rather than clobber specified output files
--resume <filename>: Resume an aborted scan
--stylesheet <path/URL>: XSL stylesheet to transform XML output to HTML
--webxml: Reference stylesheet from Nmap.Org for more portable XML
--no-stylesheet: Prevent associating of XSL stylesheet w/XML output
MISC:
-6: Enable IPv6 scanning
-A: Enable OS detection, version detection, script scanning, and traceroute
--datadir <dirname>: Specify custom Nmap data file location
--send-eth/--send-ip: Send using raw ethernet frames or IP packets
--privileged: Assume that the user is fully privileged
--unprivileged: Assume the user lacks raw socket privileges
-V: Print version number
-h: Print this help summary page.
EXAMPLES:
nmap -v -A scanme.nmap.org
nmap -v -sn 192.168.0.0/16 10.0.0.0/8
nmap -v -iR 10000 -Pn -p 80
SEE THE MAN PAGE (https://nmap.org/book/man.html) FOR MORE OPTIONS AND EXAMPLES
[email protected]:~$
Two 、 Parameter description
1、 usage
nmap [Scan Type(s)] [Options] {
target specification}
2、TARGET SPECIFICATION
You can pass the host name ,IP Address , Network, etc .
| Parameters | explain |
|---|---|
| Ex | |
| -iL < inputfilename > | From the host / Input of network list |
| -iR < num hosts > | Choose random targets |
| –exclude <host1[,host2] [,host3],…> | Exclude the host / The Internet |
| –excludefile < exclude_file > | Exclude list from file |
3、HOST DISCOVERY
| Parameters | explain |
|---|---|
| -sL | Just list the targets to scan |
| -sn | Disable port scanning |
| -Pn | Treat all hosts as online – Skip host discovery |
| -PS/PA/PU/PY[portlist] | TCP SYN/ACK、UDP or SCTP Found the given port |
| -PE/PP/PM | ICMP The echo 、 Timestamp and netmask request discovery probe |
| -PO[protocol list] | IP agreement Ping |
| -n/-R | Never execute DNS analysis / Always parse [ Default : Sometimes ] |
| –dns-servers <serv1[,serv2],…> | Specify custom DNS The server |
| –system-dns | Using the operating system DNS Parser |
| –traceroute | Track the hop path to each host |
4、SCAN TECHNIQUES
| Parameters | explain |
|---|---|
| -sS/sT/sA/sW/sM | TCP SYN/Connect()/ACK/Window/Maimon scanning |
| -sU | UDP scanning |
| -sN/sF/sX | TCP Null, FIN, and Xmas scanning |
| –scanflags < flags > | Customize TCP Scan flag |
| -sI <zombie host[:probeport]> | Idle scanning |
| -sY/sZ | SCTP INIT/COOKIE-ECHO scanning |
| -sO | IP Protocol scan |
| -b < FTP relay host > | FTP Bounce scan |
5、PORT SPECIFICATION AND SCAN ORDER
| Parameters | explain |
|---|---|
| -p < port ranges > | Scan only the specified ports |
| –exclude-ports < port ranges > | Exclude the specified port from the scan |
| -F | Fast mode - The number of ports scanned is less than the default scanning |
| -r | Continuous scan port - Don't randomize |
| –top-ports < number > | scanning < number > The most common port |
| –port-ratio < ratio > | Scan port ratio < ratio > |
6、SERVICE/VERSION DETECTION
| Parameters | explain |
|---|---|
| -sV | Probe the open port to determine the service / Version information |
| –version-intensity < level > | from 0( light colour ) Set to 9( Try all probes ) |
| –version-light | Limit to the most likely probe ( Strength 2) |
| –version-all | Try every probe ( Strength 9) |
| –version-trace | Displays detailed version scan activity ( For debugging ) |
7、SCRIPT SCAN
| Parameters | explain |
|---|---|
| -sC | Equivalent to --script=default |
| –script=< Lua scripts > | < Lua scripts > Are comma separated directories 、 List of script files or script categories |
| –script-args=<n1=v1,[n2=v2,…]> | Provide parameters for the script |
| –script-args-file=filename | Provide... In the document NSE Script parameters |
| –script-trace | Display all data sent and received |
| –script-updatedb | Update script database . |
| –script-help=< Lua scripts > | Show help on scripts . |
8、OS DETECTION
| Parameters | explain |
|---|---|
| -O | Enable operating system detection |
| –osscan-limit | Limit operating system detection to promising targets |
| –osscan-guess | Guess more actively about the operating system |
9、TIMING AND PERFORMANCE
Selected options < time > In seconds , Or will "ms"( millisecond )、“s”( second )、“m”( minute ) or "h"( Hours ) Attach to value ( for example 30m) in .
| Parameters | explain |
|---|---|
| -T< 0-5 > | Set the timing template ( The higher, the faster ) |
| –min-hostgroup/max-hostgroup < size > | Parallel host scan group size |
| –min-parallelism/max-parallelism < numprobes > | Probe parallelization |
| –min-rtt-timeout/max-rtt-timeout/initial-rtt-timeout < time > | Specify probe round trip time . |
| –max-retries < tries > | The upper limit number of port scan probe retransmissions . |
| –host-timeout < time > | Give up your goal after such a long time |
| –scan-delay/–max-scan-delay < time > | Adjust the delay between probes |
| –min-rate < number > | The sending speed is not lower than < number > Packets per second |
| –max-rate < number > | The speed of sending packets should not exceed < number > Per second |
10、FIREWALL/IDS EVASION AND SPOOFING
| Parameters | explain |
|---|---|
| -f; --mtu < val > | Fragmented packet ( Optional MTU) |
| -D <decoy1,decoy2[,ME],…> | Cover the scan with bait |
| -S < IP_Address > | Spoofing source address |
| -e < iface > | Use the specified interface |
| -g/–source-port < portnum > | Use the given port number |
| –proxies <url1,[url2],…> | adopt HTTP/SOCKS4 The agent makes relay connection |
| –data < hex string > | Attach the custom payload to the sent packet |
| –data-string < string > | Will customize ASCII The string is appended to the sent packet |
| –data-length < num > | Attach random data to the sent packet |
| –ip-options < options > | Send with specified IP Option packet |
| –ttl < val > | Set up IP Time to live field |
| –spoof-mac <mac address/prefix/vendor name> | Deceive your MAC Address |
| –badsum | Using fake TCP/UDP/SCTP Check and send packets |
11、OUTPUT
| Parameters | explain |
|---|---|
| -oN/-oX/-oS/-oG < file > | Scan as normal 、XML、s|<rIpt kIddi3 and Grepable Format output to the given file name . |
| -oA < basename > | Output in three main formats at the same time |
| -v | Increase the level of detail ( Use -vv Or more for greater effect ) |
| -d | Improve debugging level ( Use -dd Or more for greater effect ) |
| –reason | Shows why the port is in a particular state |
| –open | Only show open ( Or maybe open ) The port of |
| –packet-trace | Displays all packets sent and received |
| –iflist | Print host interface and routing ( For debugging ) |
| –append-output | Append to the specified output file instead of blocking the specified output file |
| –resume < filename > | Resume aborted scan |
| –stylesheet <path/URL> | Is used to XML The output is converted to HTML Of XSL Style sheets |
| –webxml | quote Nmap.Org The style sheet of , For more portable XML |
| –no-stylesheet | Prevent association with XML Output XSL Style sheets |
12、MISC
| Parameters | explain |
|---|---|
| -6 | Enable IPv6 scanning |
| -A | Enable operating system detection 、 Version checking 、 Scripts scan and track routes |
| –datadir < dirname > | Specify custom Nmap Data file location |
| –send-eth/–send-ip | Use the original Ethernet frame or IP Packet sending |
| –privileged | Assume that the user has full privileges |
| –unprivileged | Assume that the user lacks raw socket permissions |
| -V | Print version number |
| -h | Print this help summary page . |
13、EXAMPLES
nmap -v -A scanme.nmap.org
nmap -v -sn 192.168.0.0/16 10.0.0.0/8
nmap -v -iR 10000 -Pn -p 80
3、 ... and 、man nmap
To be completed
边栏推荐
- [day 30] given an integer n, find the sum of its factors
- Study diary: February 13, 2022
- Fibonacci number
- After Luke zettlemoyer, head of meta AI Seattle research | trillion parameters, will the large model continue to grow?
- Programmer growth Chapter 9: precautions in real projects
- VMware Tools安装报错:无法自动安装VSock驱动程序
- Five challenges of ads-npu chip architecture design
- Differences between standard library functions and operators
- 《强化学习周刊》第52期:Depth-CUPRL、DistSPECTRL & Double Deep Q-Network
- Three methods of script about login and cookies
猜你喜欢
《强化学习周刊》第52期:Depth-CUPRL、DistSPECTRL & Double Deep Q-Network
BiShe - College Student Association Management System Based on SSM
Building core knowledge points
Dedecms plug-in free SEO plug-in summary
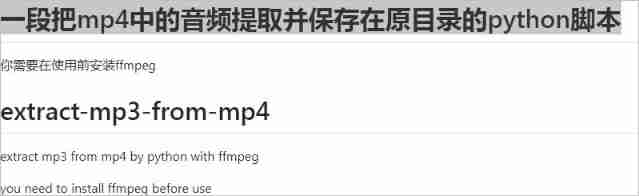
How to extract MP3 audio from MP4 video files?
![[groovy] JSON serialization (convert class objects to JSON strings | convert using jsonbuilder | convert using jsonoutput | format JSON strings for output)](/img/52/021931181ad3f4bef271b4e98105c2.jpg)
[groovy] JSON serialization (convert class objects to JSON strings | convert using jsonbuilder | convert using jsonoutput | format JSON strings for output)
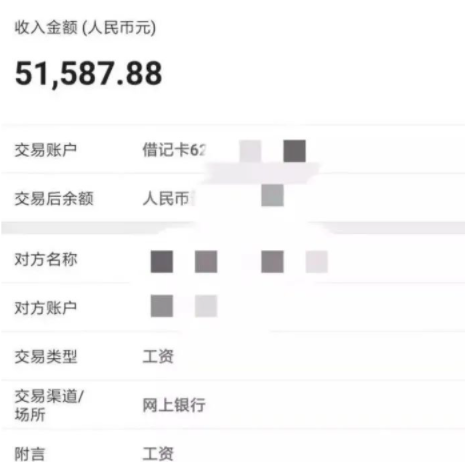
95后CV工程师晒出工资单,狠补了这个,真香...
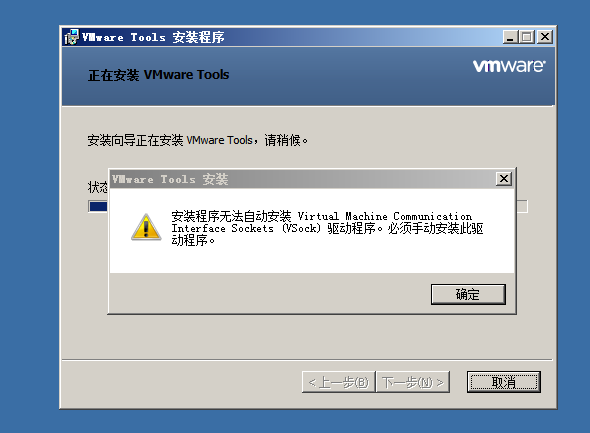
VMware Tools安装报错:无法自动安装VSock驱动程序
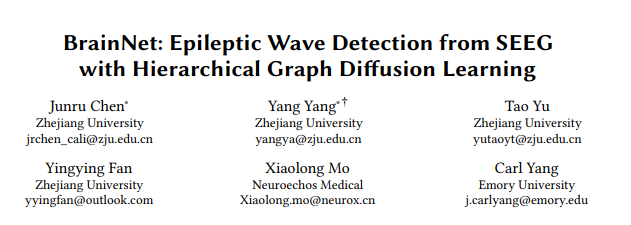
KDD 2022 | 脑电AI助力癫痫疾病诊断
基于DVWA的文件上传漏洞测试
随机推荐
C language programming (Chapter 6 functions)
面试必刷算法TOP101之回溯篇 TOP34
Questions about database: (5) query the barcode, location and reader number of each book in the inventory table
[groovy] compile time meta programming (AST syntax tree conversion with annotations | define annotations and use groovyasttransformationclass to indicate ast conversion interface | ast conversion inte
Arduino hexapod robot
Curlpost PHP
Xunrui CMS plug-in automatically collects fake original free plug-ins
直播系统代码,自定义软键盘样式:字母、数字、标点三种切换
Zhuhai laboratory ventilation system construction and installation instructions
视频直播源码,实现本地存储搜索历史记录
程序员成长第九篇:真实项目中的注意事项
Keepalive component cache does not take effect
关于softmax函数的见解
可恢复保险丝特性测试
Daily practice - February 13, 2022
Use of crawler manual 02 requests
猿桌派第三季开播在即,打开出海浪潮下的开发者新视野
有谁知道 达梦数据库表的列的数据类型 精度怎么修改呀
Some features of ECMAScript
Promise