Preface
lately edusrc New certificate , This cannot be arranged for him .
Set goals
Information collection without words , Open it directly fofa, Use the syntax title="XXX university ", Found a system
See the login box , Maybe everyone will blow up the weak password first , Maybe my face is black , I have never been able to burst out in this way , So I prefer to test unauthorized access , Here I casually input an account number and password
Return to grab the return package of this interface , Back in the bag 500
Here I change it to 200 , Can enter the system , But there is no data information
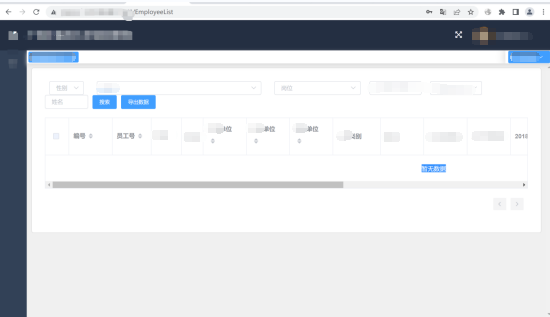
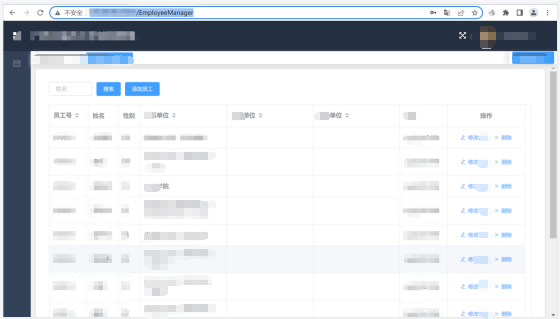
And then I just F12 View the source code , Found a route ,/EmployeeManager, Splice it behind the website
visit
【---- Help network security learn , All the following learning materials are free ! Add vx:yj009991, remarks “ Blog Garden ” obtain !】
① Thinking map of the growth path of Network Security Learning
② 60+ Network security classic common toolkit
③ 100+SRC Vulnerability analysis report
④ 150+ Network security attack and defense technology ebook
⑤ The most authoritative CISSP Certification test guide + Question bank
⑥ super 1800 page CTF Practical skills manual
⑦ A collection of the latest interview questions from Wangan factory ( With answers )
⑧ APP Client security detection guide ( Android +IOS)
Direct unauthorized access , Moderately dangerous , I originally wanted to submit it manually , But look at the certificate exchange conditions , Get two medium risks , It's not to embarrass me , There is no way to continue working overtime , So I used the user name and password I just got to log in
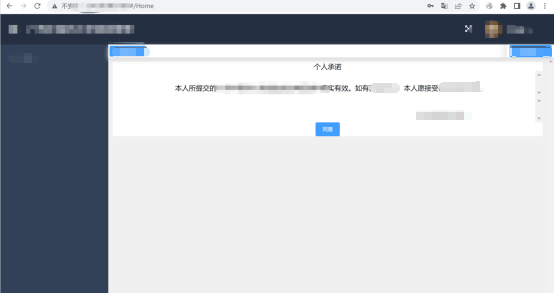
There is a personal commitment after logging in , You need to agree to the next step , Click OK to capture the package
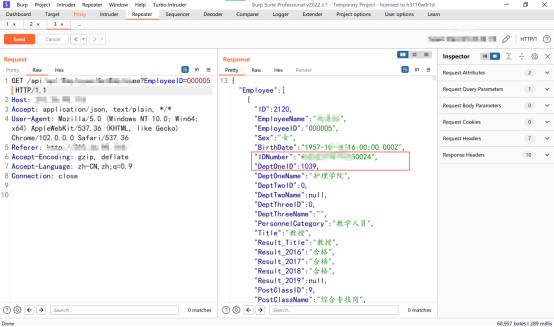
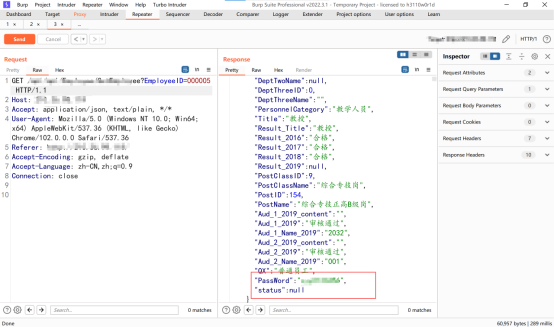
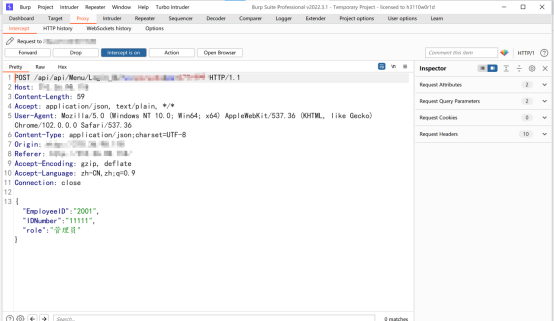
Interface returns the user's sf Certificate and password , And then EmployeeID=000005 Change to 000006
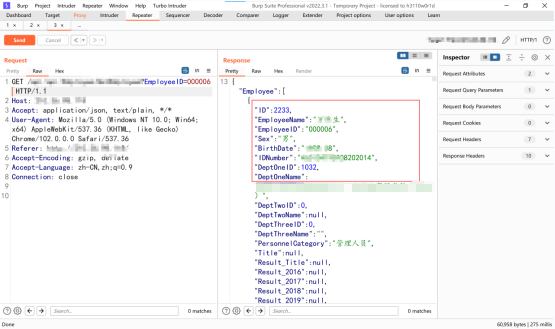
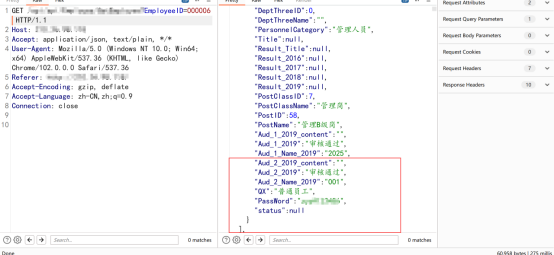
Another level of ultra vires , Leaked user sensitive information , Moderate risk should be stable , Then I noticed that this system distinguishes between the administrator and the ordinary user , A front-end can choose the role type to log in , Then I thought about whether I could log in with the account and password of ordinary users , Then exceed the authority of the administrator , Capture packets when logging in
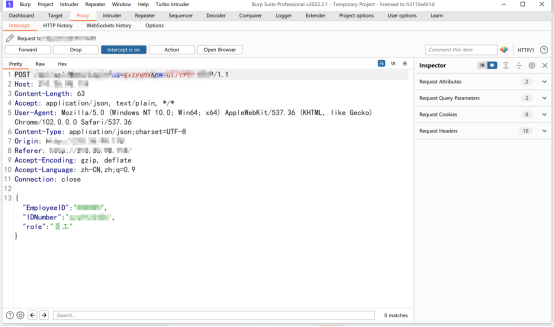
Intercept the return packets of this interface
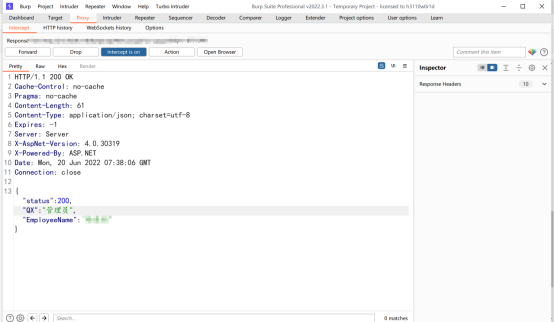
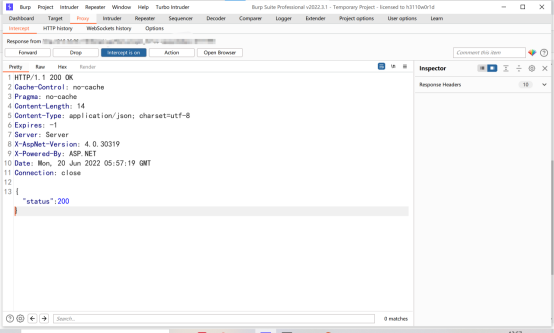
hold QX Change to administrator , And then put the bag
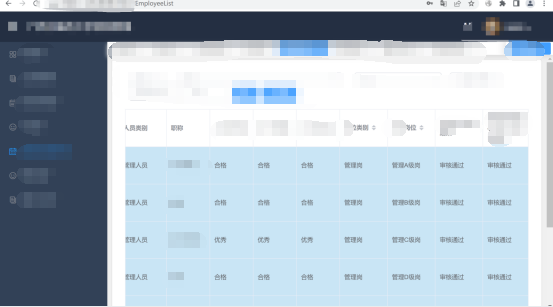
You can see that you have overstepped your authority and become an administrator sf
end
Are very conventional loopholes , The most important thing is to be careful .
More range experiments 、 Network security learning materials , Please click here >>


![C language QQ chat room small project [complete source code]](/img/4e/b3703ac864830d55c824e1b56c8f85.png)