当前位置:网站首页>[the 300th weekly match of leetcode]
[the 300th weekly match of leetcode]
2022-07-06 18:20:00 【ღCauchyོꦿ࿐】
List of articles
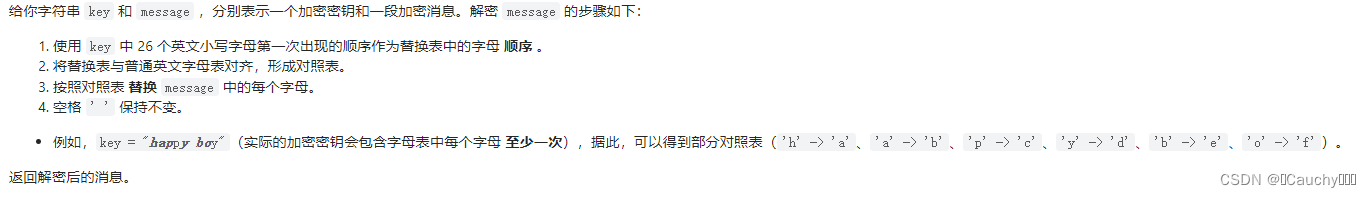
Decrypt the message
subject
Ideas
- simulation , Just mark it .
Code
class Solution {
public:
string decodeMessage(string key, string message) {
string res = "";
int n = key.size();
bool st[26] = {
0};
map<char, int> mp;
int now = 0;
for (int i = 0; i < n; i++) {
if(key[i] == ' ') continue;
if(!st[key[i] - 'a']) {
st[key[i] - 'a'] = true;
mp[key[i]] = now;
now ++;
}
}
for (int i = 0; i < message.size(); i++) {
if(message[i] == ' ') res += ' ';
else {
res += mp[message[i]] + 'a';
}
}
return res;
}
};
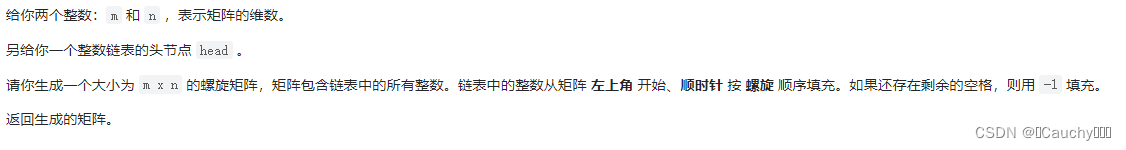
Spiral matrix IV
subject
Ideas
- Set the current direction n o w now now,(0、1、2、3) Corresponding direction array w a l k walk walk.
- Set up, down, left and right (lx、rx、ly、ry) Four borders , Adjust when turning the direction .
Code
class Solution {
public:
vector<vector<int>> spiralMatrix(int m, int n, ListNode* head) {
vector<vector<int>> res(m, vector<int>(n, -1));
ListNode *p = head;
if(p == nullptr) return res;
vector<int> v;
while(p) {
v.push_back(p->val); p = p->next; }
int x = 0, y = -1;
int walk[4][2] = {
0, 1, 1, 0, 0, -1, -1, 0};
int now = 0;
int lx = 0, rx = m - 1, ly = 0, ry = n - 1;
for (int i = 0; i < v.size(); i++) {
int dx = x + walk[now][0], dy = y + walk[now][1];
if(dx > rx || dx < lx || dy > ry || dy < ly) {
if(now == 0) lx += 1;
if(now == 1) ry -= 1;
if(now == 2) rx -= 1;
if(now == 3) ly += 1;
now = (now + 1) % 4;
dx = x + walk[now][0], dy = y + walk[now][1];
}
res[dx][dy] = v[i];
x = dx, y = dy;
}
return res;
}
};
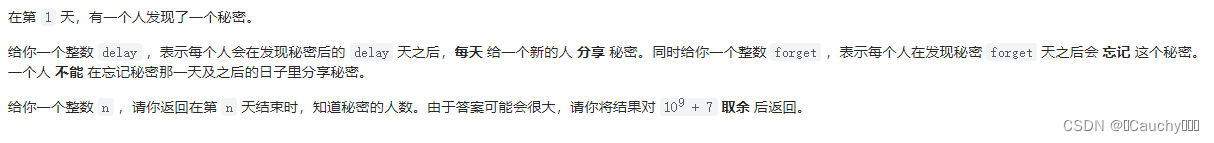
Number of people who know the secret
subject
Ideas
I thought at first , Just take a dynamic array , Simulated deletion 、 The process of adding people . But time , The space cost is bound to be great .
This needs to be optimized :
- It is found that for the i i i God : In the current collection Everyone who can share secrets ( i > = x + d e l a y i>=x+delay i>=x+delay), New people added , Their state ( Time is the beginning i i i God 、delay、forget) All are consistent .( This is equivalent to that we don't need to add everyone one by one , Instead, you can directly replace it with a variable equivalent )
- Find that time is monotonically increasing , Parameters d e l a y 、 f o r g e t delay、forget delay、forget Is constant , Then the latter must be later than the former .
Here I use m a p < i n t , i n t > map<int, int> map<int,int> For storage : The first i i i God , The number of j j j.
Code
class Solution {
public:
constexpr static int mod = 1e9 + 7;
int peopleAwareOfSecret(int n, int delay, int forget) {
map<int, int> mp;
int res = 0;
mp[1] = 1;
for (int i = 2; i <= n; i++) {
int cnt = 0;
for (auto &x: mp) {
int a = x.first, b = x.second;
if(i >= a + forget) {
mp.erase(a); continue; }
if (i >= a + delay) cnt = (cnt + b) % mod;
}
mp.insert({
i, cnt});
}
for (auto &x: mp) res = (res + x.second) % mod;
return res % mod;
}
};
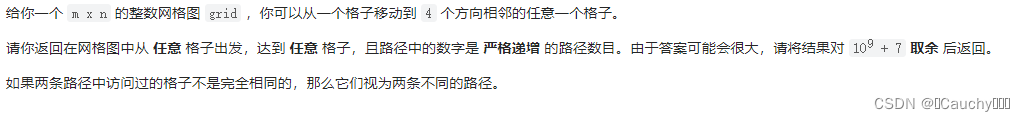
The number of incremental paths in the grid graph
subject
Ideas
- Memory search
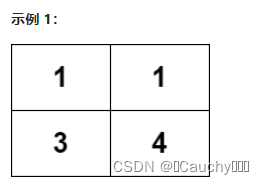
Consider the example illustration
3->4:1
1->3、1->3->4: 2
Adjacent can arrive , State shift d p [ i ] [ j ] = d p [ x ] [ y ] + 1 dp[i][j] = dp[x][y] + 1 dp[i][j]=dp[x][y]+1.
Code
class Solution {
public:
constexpr static int mod = 1e9 + 7;
int n, m;
int walk[4][2] = {
0, 1, 1, 0, 0, -1, -1, 0};
int dfs(int x, int y, vector<vector<int>>& grid, vector<vector<int>>& dp) {
int s = 0;
for (int i = 0; i < 4; i++) {
int dx = x + walk[i][0];
int dy = y + walk[i][1];
if(dx >= n || dx < 0 || dy >= m || dy < 0) continue;
if(grid[x][y] >= grid[dx][dy]) continue;
if(dp[dx][dy]) {
s += dp[dx][dy] + 1; continue; }
s += dfs(dx, dy, grid, dp) + 1;
s %= mod;
}
dp[x][y] = (s + dp[x][y]) % mod;
return dp[x][y];
}
int countPaths(vector<vector<int>>& grid) {
n = grid.size(), m = grid[0].size();
vector<vector<int>> dp(n, vector<int>(m, 0));
for (int i = 0; i < n; i++) {
for (int j = 0; j < m; j++) {
if(!dp[i][j]) {
dfs(i, j, grid, dp);
}
}
}
int res = 0;
for (int i = 0; i < n; i++)
for (int j = 0; j < m; j++)
res = (res + dp[i][j] + 1) % mod;
return res;
}
};
边栏推荐
- 测试1234
- 推荐好用的后台管理脚手架,人人开源
- 78 year old professor Huake has been chasing dreams for 40 years, and the domestic database reaches dreams to sprint for IPO
- Codeforces Round #803 (Div. 2)
- Kill -9 system call used by PID to kill process
- d绑定函数
- 关于这次通信故障,我想多说几句…
- Why does wechat use SQLite to save chat records?
- 文档编辑之markdown语法(typora)
- 重磅硬核 | 一文聊透对象在 JVM 中的内存布局,以及内存对齐和压缩指针的原理及应用
猜你喜欢
Easy to use PDF to SVG program
![Jerry's updated equipment resource document [chapter]](/img/6c/17bd69b34c7b1bae32604977f6bc48.jpg)
Jerry's updated equipment resource document [chapter]
Ms-tct: INRIA & SBU proposed a multi-scale time transformer for motion detection. The effect is SOTA! Open source! (CVPR2022)...
微信为什么使用 SQLite 保存聊天记录?
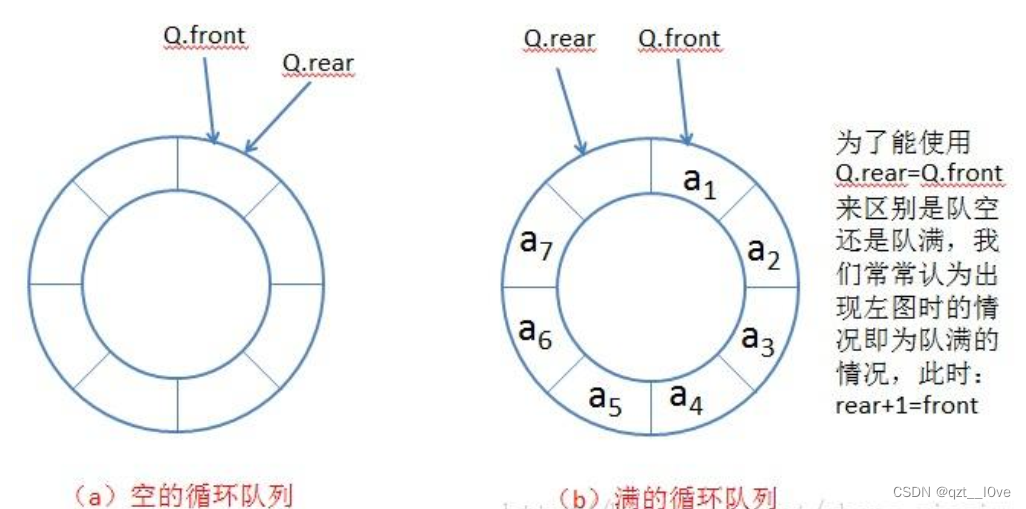
队列的实现
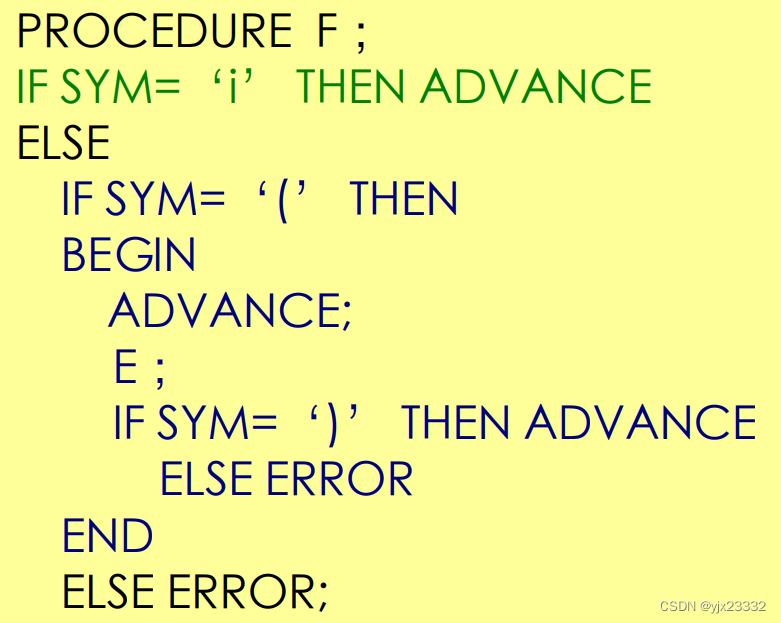
编译原理——自上而下分析与递归下降分析构造(笔记)

SAP Fiori 应用索引大全工具和 SAP Fiori Tools 的使用介绍

F200 - UAV equipped with domestic open source flight control system based on Model Design
Olivetin can safely run shell commands on Web pages (Part 1)
Scratch epidemic isolation and nucleic acid detection Analog Electronics Society graphical programming scratch grade examination level 3 true questions and answers analysis June 2022
随机推荐
Jielizhi obtains the currently used dial information [chapter]
2022暑期项目实训(一)
Recursive way
Maixll-Dock 摄像头使用
首先看K一个难看的数字
Open source and safe "song of ice and fire"
bonecp使用数据源
Jerry is the custom background specified by the currently used dial enable [chapter]
面向程序员的精品开源字体
【Swoole系列2.1】先把Swoole跑起来
Distiller les connaissances du modèle interactif! L'Université de technologie de Chine & meituan propose Virt, qui a à la fois l'efficacité du modèle à deux tours et la performance du modèle interacti
MS-TCT:Inria&SBU提出用于动作检测的多尺度时间Transformer,效果SOTA!已开源!(CVPR2022)...
STM32+ESP8266+MQTT协议连接OneNet物联网平台
The latest financial report release + tmall 618 double top, Nike energy leads the next 50 years
Brief description of SQL optimization problems
简单易用的PDF转SVG程序
Insert dial file of Jerry's watch [chapter]
Cocos2d Lua 越来越小样本 内存游戏
Automatic reservation of air tickets in C language
node の SQLite