当前位置:网站首页>Redis cache breakdown, cache penetration, cache avalanche
Redis cache breakdown, cache penetration, cache avalanche
2022-07-06 03:07:00 【Attacking Xiao Wang 666】
Cache penetration
a large number of key Not in cache , The request goes directly to the database , and key It's not in the database ( Finally back to null, A meaningless query ), If hackers create such a large number of request attacks , Cache penetration may occur
Solution :
1. You can verify at the front end or back end , Filter illegal requests , For example, judge whether the request has been tampered by the summary Algorithm
2. Invalid cache key, Set a shorter effective time ( Not recommended )
3. The bloon filter , A very clever data structure , The concrete realization is :
Store all possible request values in the bloom filter , When requested by the user , First, judge whether the value exists through the bloom filter , If no error message is returned directly .
The process is as follows
When stored , Through multiple hash Function calculation , Then set the corresponding position of the bit array to 1
When comparing , The use of multiple hash The algorithm calculates the request parameters , Judge whether each element at the corresponding position in the digit group is 1, If there is any inconformity, it will be judged as fasle
Of course , Different strings may be hashed out in the same position ( You can appropriately increase the size of the digit group or adjust hash function )
Cache avalanche
It is caused by memory server downtime or simultaneous failure of a large number of hotspot caches at the same time , The request landed in the database
Solution :
1. For server downtime , It can be distributed ( Master-slave ) To improve usability , Or current limiting , Prevent a large number of requests for access at the same time
2. For hotspot cache invalidation , It can be set to never expire ( Not recommended ), Or set the expiration time randomly ( Peak staggering failure )
Cache breakdown
Cache avalanche is aimed at the situation that a large number of caches for different requests are invalidated , Cache breakdown refers to the situation that a large number of requests are the same and the cache fails
Solution :
Hotspot cache does not expire
Use mutexes , Only one request thread can reload the results into the cache after the cache expires , Other threads wait , Finally, query from the cache .
边栏推荐
猜你喜欢
【Kubernetes 系列】一文学会Kubernetes Service安全的暴露应用
My C language learning record (blue bridge) -- under the pointer
深入探究指针及指针类型
![BUUCTF刷题笔记——[极客大挑战 2019]EasySQL 1](/img/37/c38a933ce7fa5d2b8fa597965ffcb2.png)
BUUCTF刷题笔记——[极客大挑战 2019]EasySQL 1
ERA5再分析资料下载攻略
Gifcam v7.0 minimalist GIF animation recording tool Chinese single file version
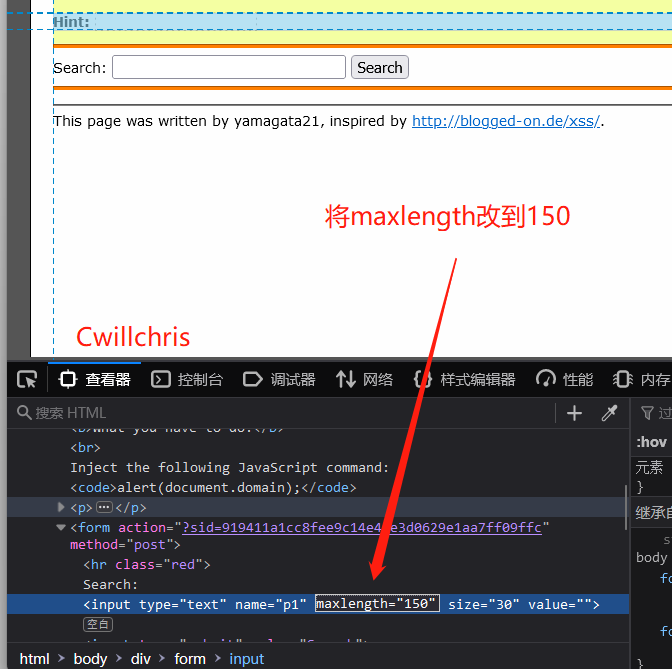
XSS challenges bypass the protection strategy for XSS injection
RobotFramework入门(二)appUI自动化之app启动

C language - Blue Bridge Cup - promised score
JS regular filtering and adding image prefixes in rich text
随机推荐
Inherit day01
Solve 9 with C language × 9 Sudoku (personal test available) (thinking analysis)
Yyds dry inventory comparison of several database storage engines
js 正则过滤和增加富文本中图片前缀
Elimination games
Single instance mode of encapsulating PDO with PHP in spare time
Pat 1046 shortest distance (20 points) simulation
Selenium share
What are the principles of software design (OCP)
【paddle】加载模型权重后预测报错AttributeError: ‘Model‘ object has no attribute ‘_place‘
建模规范:命名规范
tcpdump: no suitable device found
Buuctf question brushing notes - [geek challenge 2019] easysql 1
【Kubernetes 系列】一文學會Kubernetes Service安全的暴露應用
Add one to non negative integers in the array
深度解析链动2+1模式,颠覆传统卖货思维?
全国大学生信息安全赛创新实践赛初赛---misc(永恒的夜)
C language - Blue Bridge Cup - promised score
[matlab] access of variables and files
Daily question brushing plan-2-13 fingertip life