当前位置:网站首页>49 pictures and 26 questions explain in detail what is WiFi?
49 pictures and 26 questions explain in detail what is WiFi?
2022-07-05 04:33:00 【Network technology platform】
When the New Year's day , Take my uncle's WiFi It's done . In fact, the problems found , It's not even WiFi problem , however WiFi Indeed, every household has . It's estimated that your little friends at home , Some relatives will ask you to help with WiFi , Actually WiFi The content of the content is relatively simple , Just the speed of upgrading wireless products , Compared with wired network, it is much faster , But everything is the same , Now let's talk about what is WiFi ?
1、 What is? CSMA/CA ?
For Ethernet CSMA/CD For transmission control , and IEEE 802.11 Of WLAN It's using CSMA/CA .
CSMA/CD , Full name Carrier Sense Multiple Access with Collision Detection , namely Carrier sense multiple access / Conflict detection protocol .
Carrier sense ( Carrier Sense ), It refers to that each device in the network before sending data , Confirm whether there is data transmission on the line . If there is data transmission , Do not send data ; If there is no data transmission , Send data now .
Multiple access ( Multiple Access ), It refers to all devices on the network sending and receiving data , Use the same line together , And the data sent is broadcast .
Collision detection ( Collision Detection ), It refers to the device sending data frames at the same time , You must also monitor the line , Determine whether there is a conflict . in other words , At the same time , Is there any other device sending data frames .
The conflict domain of Ethernet refers to data transmission , Conflict detected , When a conflict occurs, wait for a random period of time to send again . And in the WLAN in , If other devices are sending data , Then after the device is sent , Wait a random time , Continue sending data . This is it. Conflict avoidance ( CA ,Collision Avoidance ). Because the data is sent directly after the other party's equipment , It may also cause wireless transmission conflicts .
Ethernet , The transmission medium is network cable or optical fiber , It can detect the occurrence of conflicts through electrical signals . But because the wireless network will not produce electrical signals , So you need to use CSMA/CA To replace CSMA/CD .
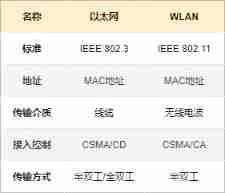
2、WLAN What makes up ?
STA , Full name Station , namely The workstation , Refers to a wireless terminal equipped with a wireless network card , such as : mobile phone 、 Computer, etc. .

AP , Full name Wireless Access Point , namely wireless AP , Used to connect STA And network equipment of wired network .

IBSS , Full name Independent Basic Service Set , namely Independent basic service set , Contains one or more STA Wireless networks for , It's also called ad-hoc Wireless network , cannot access DS The mode used when .

BSS , Full name Basic Service Set , That is, the basic service set , By a AP And one or more STA Wireless network .BSS All of the inside STA Communication is through AP complete ,AP It can not only connect to the wired network , You can also do it in STA and Other STA or DS Bridge between nodes .
ESS , Full name Extended Service Set , That is, extend the service set , Connected to the same wired network 、 Two or more AP form , Similar to the concept of a subnet .
DS , Full name Distribution System , That is, the distribution system , Make different BSS Internal AP adopt DS interconnection ,STA Can be from a BSS Move to another BSS .AP It can be wireless interconnection , It can also be wired interconnection , Usually wired interconnection is used .DS yes BSS The basis of logical connection between , Give Way STA stay BSS Can realize roaming .
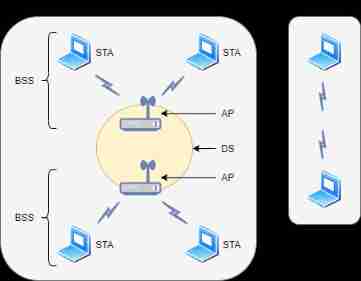
3、WLAN There are several topologies ?
WLAN There are two topologies , One is the direct interconnection between terminals ad-hoc Pattern , The other is through AP Infrastructure mode connecting wired network .
ad-hoc Pattern , Full name ad-hoc mode , namely IEEE 802.11 The development of wireless network BSS , On two STA Direct wireless communication between , And form a network , Also known as point-to-point network mode . Usually, laptops and printers are connected wirelessly or multiple game consoles are online for wartime use . The terminal is generally configured with a wireless network card . In this mode , The terminal cannot be connected to the Internet .
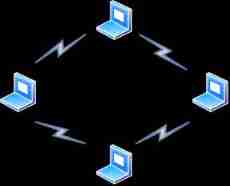
Infrastructure model , Full name Infrastructure Mode , Refer to 802.11 The development of wireless network BSS Formal networking , Usually by AP Use when connecting to the Internet . In this mode , Except for STA Outside , There needs to be AP To connect to the Internet .
4、 What is? AP ?
Wired network connects the terminal and switch through wired cables , Form a network . In the infrastructure mode of wireless network , Through a process called AP The equipment , Connect multiple terminals to the wired network .AP Also called access point , Access points are often RJ-45 Network interface , Used to connect to switches or routers , Thus, the terminal of wireless network can access wired network or Internet .
5、WLAN What are the standards ?
Like Ethernet ,WLAN There are also Standards IEEE Made by the organization . Ethernet standards are collectively referred to as IEEE 802.3 , and WLAN Standards are collectively referred to as 802.11 .
and IEEE 802.3 equally ,IEEE 802.11 Between the physical layer and the data link layer MAC Sublayer . Defined WLAN Which frequency band and modulation mode are used , How much transmission rate and other transmission standards , Security is also defined 、QoS 、 Management and other related contents .
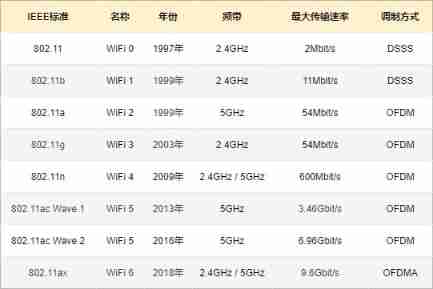
All of these are 802.11 Transmission standards , There are other types of Standards .
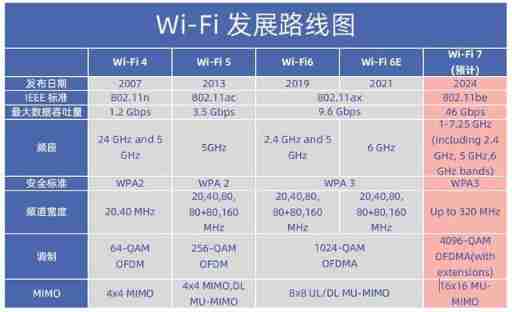
IEEE 802.11n
IEEE 802.11n Previous standards are rare , I won't introduce it here .IEEE 802.11n , Also known as WiFi 4 , Standard in 2009 The formulation was completed in , The maximum transmission rate is 600 Mbit/s , Use MIMO Multi channel technology greatly improves the transmission rate . Can also be downward compatible IEEE 802.11a 、IEEE 802.11b 、IEEE 802.11g .
IEEE 802.11ac
IEEE 802.11ac , Also known as WiFi 5 , There are two versions , Namely :Wave 1 、Wave 2 . The difference is that Wave 1 Use 80 Mhz Bandwidth sum SU-MIMO technology , The maximum transmission rate is 3.46 Gbit/s . and Wave 2 It's using 160 Mhz Bandwidth sum DL MU-MIMO technology , The maximum transmission rate is 6.93 Gbit/s . The frequency band and modulation mode are the same .
IEEE 802.11ax
IEEE 802.11ax , Also known as WiFi 6 , Standard in 2018 The formulation was completed in , The maximum transmission rate is 9.6 Gbit/s .WiFi 6 Support at the same time 2.4G and 5G Frequency band , Complete coverage of low-speed and high-speed equipment , More coverage . Support WPA 3 Security protocols , Wireless network is more secure . Support TWT technology , It can save more electricity . To put it simply , It's faster 、 Lower latency 、 Lower capacity 、 More secure 、 More power saving .
6、 What is? WiFi ?
WiFi Is based on IEEE 802.11 The standard 、 Brand certification of products from different manufacturers . Since there are IEEE 802.11 Standard , Why do we have to WiFi authentication ? This is because IEEE 802.11 The time period for the launch of formal standards is long , Wireless networks are developing rapidly , Manufacturers can't wait for official standards , I formed WiFi union , And complete the certification of interconnection .
actually , Not every IEEE 802.11 Products have been applied WiFi Certification of the Alliance , So lacking WiFi Certified products , Not necessarily compatible WiFi equipment . But after WiFi The certification STA or AP Can be barrier free interconnection .
In hotels or public places , Often see “ free WiFi surf the internet ” The logo of , This means AP It's passed WiFi authentication . Besides computers and mobile phones , Home appliances and game consoles can also be completed WiFi authentication .
WiFi It also defines similar WPA This wireless encryption related standards .

7、 What is Association ?
Use WLAN The terminal of should pass AP Complete wireless connection , To connect to the Internet or wired network .
Wireless terminal connection AP The process is called relation ( Association ).
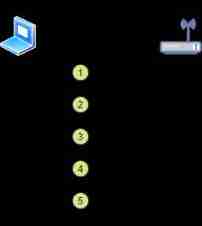
STA It can be different from the connection AP , But at the same time , Can only be connected to one AP On .AP Will send regularly beacon frame ,STA according to beacon The content of the frame , obtain AP Of SSID Information 、 Supported wireless transmission rate , And wireless channel and other information .
STA In the process of Association , Will send to AP send out Association request Data frame ,AP Upon receipt of the request , As to the STA Returns Correlation response Data frame .
STA Will confirm AP The status code sent , If it is “ successful ” , Indicates that the connection is successful , If other information is returned , Indicates that the association failed .STA Upon receipt of “ successful ” At the same time , There will also be a Association ID( AID ) Identification number of .
WLAN Certification process , It happens before the correlation process .
8、 What is the data frame like ?
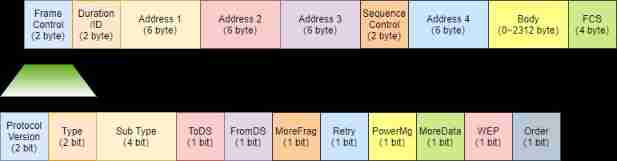
IEEE 802.11 Of MAC Data frame The field information of is as follows :
Protocol Version : Protocol version , Express IEEE 802.11 Version of protocol .
Type : type , Indicates the function of the data frame , There are control frames 、 Manage frames 、 There are three kinds of data frames .
Subtype : subtypes , Each data frame has multiple subtypes , Implement specific functions .
To DS and From DS :DS Refers to distributed systems , Using and AP Associated with STA Type of data frame transmitted between . The value is 1 when , Indicates that the sending source is AP , The value is 0 when , Indicates that the sending source is STA .
More Frag : After dividing the upper layer into groups , When sending, use . The value is 1 when , Indicates that there are subsequent fragmented data frames . The value is 0 when , Indicates that the current data frame is the last fragment , Or there is no fragmented data frame .
Retry : Indicates whether to resend the data frame . The value is 1 when , Indicates that the data frame is sent again . The value is 0 when , Indicates that this data frame will not be sent .
More Data : Indicates whether there are subsequent packets . The value is 1 when , Indicates that there are subsequent groups .
WEP : Indicates whether to proceed with WEP encryption . The value is 1 when , Indicates encryption .
Order : The value is 1 when , Indicates that the data frame is strictly in accordance with strictly ordered( Send receive sequence cannot be replaced ) Send according to the standard .
IEEE 802.11 The data frames of can be divided into three categories :
- Manage frames ( Managed Frame )
1、 Broadcasting wireless signals beacon frame , By default , Every time 100 millisecond AP Broadcast once .
2、 Authentication uses authentication frames :AP and STA When it comes to information interaction , Associated frame used .
Control frame ( Control Frame )
Data frame ( Data Frame )
Usually the data frame Address 1 Indicates the destination address ,Address 2 Represents the source address ,Address 3 Express BSSID Information .
9、 What are the access control functions of Wireless Networks ?
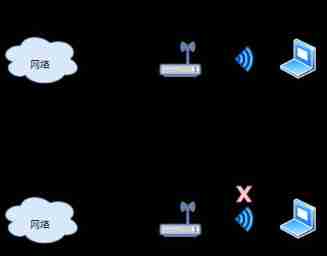
Because radio waves are invisible , There will be strange users without permission , Unauthorized access AP The use happens . As long as the wireless signal can reach the range , And know SSID ,STA You can talk to AP Association . In order to prevent unknown people from using , have access to ESSID hide Function and MAC Address filtering function .
ESSID hide
SSID Information is made up of AP Of beacon Frames are broadcast regularly .STA adopt beacon Frame to confirm with that SSID Connect . however , Only where wireless signals can reach , Anyone can go through beacon frame , Use STA Search for SSID Information and connection .
To guard against such risks , Can be used without sending beacon The frame of ESSID hide function .STA It needs to be obtained through other ways SSID Information , And in STA Configure accordingly , So as to hide the network connection .
however , because SSID In the spread of Wireless Networks , No encryption , When there is STA Use this hidden SSID Connect AP when , You can get the information of this wireless network through the wireless monitoring tool SSID , therefore ESSI Hidden functions are not very safe countermeasures .
MAC Address filtering
stay AP Allow associated MAC Address list , Only those in the list STA To connect to the wireless network , Prevent other STA Access AP , This method is called MAC Address filtering or MAC Address the authentication .
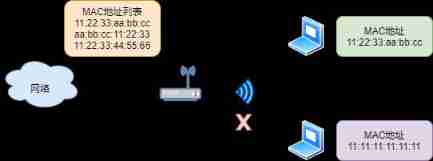
In addition to the AP Set the outer , You can also use RADIUS Server settings allow access MAC Address information , At the same time of certification MAC Address filtering . however ,MAC Addresses can also be disguised and pretended by tools , You can access WLAN Of MAC Address monitoring , Get specific MAC Address information , So this is not a perfect security strategy .
10、 What authentication functions does the wireless network have ?
stay AP Upper use ESSID Hide and MAC Address filtering function , Can not completely prevent malicious access , In order to completely prevent malicious users from accessing the wireless network , Need to be certified .
IEEE 802.11 At first, there are two authentication methods : Open systems certification 、 Shared key authentication .
Open systems certification
Develop system certification ( Open System Authentication ) no need STA Enter authentication information such as user name and password , You can go to AP Send an authentication request .AP Able to receive all access authentication requests , in other words , No matter who you are, you can communicate with AP On the correlation . Usually used for public WiFi , combination Portal Certified or VPN To complete the permission control of users' access to the network .
Shared key authentication
Shared key authentication ( Shared Key Authentication ) be used for AP and STA Conduct wireless encrypted communication . Use WEP or WPA When encrypting Standards ,AP and STA Configure the same password in advance , With this password, the wireless communication link can be established . This password is called Pre shared key ( pre-shared key ), Do not know the pre shared key STA , It is impossible to do so. AP Associated .
IEEE 802.1X
IEEE 802.1X User authentication and access control protocol , It is quoted from the wired network .
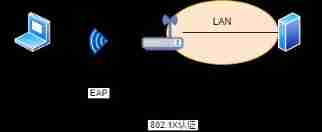
IEEE 802.1X It was carried out by Authentication client 、 Access equipment 、 Authentication server Three parts . The terminal requesting authentication is called Authentication client , Connected to the terminal AP 、 Switches and other network devices are called Access equipment . The authentication method is used EAP , The client initiates an authentication request , The access device will send the received EAP The message is encapsulated into RADIUS Data frame , Forward to the authentication server , When the authentication server completes the authentication , The access device will notify the client and regard the client as the client with successful authentication , After that, the data frames sent by the client will be forwarded to the LAN or the Internet .
The authentication information is the user name 、 password 、 One of the ways is digital certificate , The corresponding authentication protocols are EAP-MD5 、EAP-TLS 、EAP-TTLS And so on .
11、 What encryption functions does the wireless network have ?
Radio waves transmitted in the air , As long as it is within the coverage , Can be received by anyone , Plus WLAN Data analysis tools , Malicious users can eavesdrop on the communication content of the wireless network .
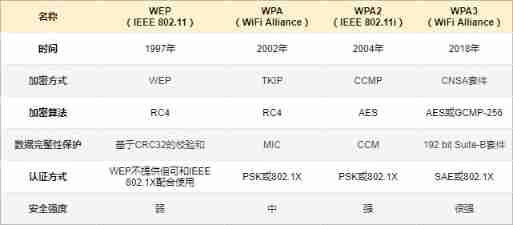
In order to prevent wireless communication from being eavesdropped and tampered , In the process of wireless communication , Encrypt information .WLAN Encryption has WEP 、WPA 、WPA2 、WPA3 Equal standard .
WEP
WEP , Full name Wired Equivalent Privacy , That is, Wired Equivalent confidentiality .WEP Encryption is the first technology used in wireless encryption , be based on RC4 The key of the algorithm encrypts the data , This key is called WEP key .
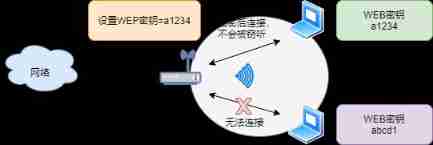
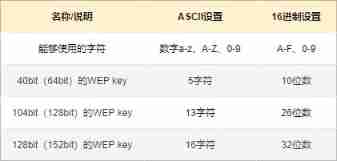
WEP There are three encryption methods :40 bit The length of the key and 24 bit The initial vector value of length consists of 64 bit Long encryption ,104 bit The length of the key and 24 bit The initial vector value of length consists of 128 bit Long encryption ,128 bit The length of the key and 24 bit The initial vector value of length consists of 152 bit Long encryption . The shorter the key length , The shorter the cracking time , It's not used much now .
WPA
WEP It's too fragile , So it was formulated WPA , Full name WiFi Protected Access , namely WiFi Protect access .
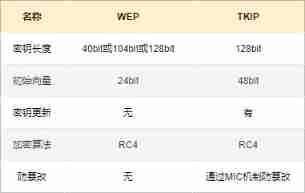
WPA hold SSID and WEP The key is encrypted together , And it can automatically update the user authentication function and key on a regular basis TKIP .
WPA There are two patterns : Personal mode and Business model .
Personal mode Of WPA Mainly for family and personal use , It's also called WPA-PSK ,AP and STA Use the same Pre shared key ( PSK ).
Business model Of WPA Mainly used in enterprises , Added IEEE 802.1X Authentication server , Different users use different user names and passwords to connect to the wireless network .
WPA2
WPA2 Is the new generation WPA standard , use AES encryption algorithm .AES Commonly used in IPsec and SSL In the agreement , Than RC4 It's more secure .AES The supported length is 128 bit 、196 bit 、256 bit The key of ,WPA2 Use one of the 128 bit Length type .WPA2 Compatible with the previous generation WPA , Support WPA2 Devices and only support WPA Your device can also communicate .AES A similar TKIP The agreement CCMP , among CBC-MAC It is password segment connection / Message authentication code means .
AP Encryption settings of can be selected WPA-PSK( TKIP )、WPA-PSK( AES )、WPA2-PSK( TKIP ) or WPA2-PSK( AES ).
WPA3
2017 year 10 month ,802.11 In the agreement 13 Year of WPA2 The encryption was completely cracked .2018 year 6 month 26 Japan ,WiFi Alliance announcement WPA3 The agreement has been finalized , This is a WiFi New standards for connectivity .
WPA3 stay WPA2 New functions are added on the basis of , Simplify WiFi Safety assurance methods 、 Achieve more reliable authentication , Improve the strength of data encryption . be-all WPA3 All networks must be protected by management frames PMF , Ensure data security .
according to WiFi Different uses and security requirements of the network ,WPA3 It is divided into WPA3 Personal Edition 、WPA3 Enterprise Edition , namely WPA3-SAE and WPA3-802.1X .WPA3 It provides additional functions for different networks :WPA3 Personal Edition enhances the protection of password security , and WPA3 Users of Enterprise Edition can choose more advanced security protocols , Protect sensitive data .
- WPA3 Personal Edition
contrast WPA2 Personal Edition ,WPA3 Personal edition can provide more reliable password based authentication . This is because WPA3 The personal version uses a more secure protocol : Peer entities validate at the same time SAE( Simultaneous Authentication of Equals ).SAE To replace the WPA2 Personal version of PSK authentication , It can effectively resist offline dictionary attacks , Increase the difficulty of violent cracking .SAE Be able to provide forward confidentiality , Even if the attacker knows the password in the network , You can't decrypt the traffic obtained , Greatly improved WPA3 Personal network security .WPA3 The personal version only supports AES encryption .
SAE stay WPA/WPA2-PSK The original four handshakes were added SAE handshake , In essence, it is for dynamic negotiation of paired master keys PMK .WPA/WPA2-PSK Of PMK Only with SSID It's about pre shared keys , and SAE Dynamic random variables are introduced , For each negotiation PMK It's all different , Improved security .
- WPA3 Enterprise Edition
Enterprises 、 Governments and financial institutions can adopt WPA3 Enterprise Edition .WPA3 The enterprise edition is based on WPA2 Enterprise Edition , Provide an optional mode :WPA3-Enterprise 192bit , The advantages of this model are :
Data protection : Use 192 Bit Suite-B Security Suites , Increase the length of the key .
Key protection : Use HMAC-SHA-384 stay 4 The second handshake phase exports the key .
Flow protection : Use Galois counter mode protocol GCMP-256( Galois Counter Mode Protocol ) Protect the wireless traffic after users go online .
Frame protection : Use GMAC-256( GCMP Galois message authentication code ,Galois Message Authentication Code ) Protect multicast management frame .
WPA2 The enterprise edition supports a variety of EAP Way of authentication , however WPA3 Enterprise edition only supports EAP-TLS The way .
12、 What is fat AP ?
Able to perform wireless control and security management functions by oneself AP be called fat AP . Through one or more AP When building a wireless network , Often use fat AP , Simple configuration , It's cheap . There are several AP In our network environment , If you want to modify parameters such as security policy , You need to configure one by one .
13、 What is thin AP ?
When deploying wireless networks in large-scale office areas , Need to be managed AP The quantity is very large , Not suitable for single AP Manage alone . In this case ,AP Keep only the most basic configuration , Security policy and other parameters are uniformly configured and managed through the wireless controller , This kind of AP It's called Thin AP .
AP Support CAPWAP , You can connect to the wireless controller through this Protocol ,AP Just finish MAC Management and data frame control , Authentication and security functions are all left to wireless control .
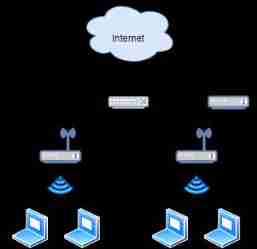
14、 What is wireless bridging ?
Between buildings that cannot be wired 、 Between sites that are physically far away , Can pass Wireless bridge Make a wireless connection . Wireless bridging is through wireless connection , Wired offline networking .
When the communication distance is long , Directional antennas are needed to enhance the radio wave intensity in a particular direction .
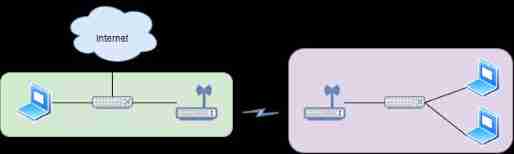
15、 What is wireless relay ?
AP Connect the wireless interface as STA , Connect other AP Released SSID .AP Connect the wireless interface to release the same SSID , Give Way STA Access , This is it. Wireless relay . By connecting the repeater , take STA The received data is forwarded to have the same SSID Of AP , Can expand the scope of Wireless Networks . After the primary repeater is connected , Network throughput will be halved .
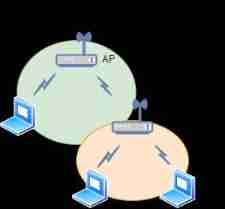
16、 What is the maximum speed of the wireless network ?
Both wireless networks and wired networks have theoretical maximum speeds , such as : Common Ethernet 10Gbit/s and WiFi 6 Of 9.6Gbit/s , These are for data communication , The limit rate of transmission .
Due to the use of CSMA/CA Conflict avoidance agreement , There is a waiting time for data to be sent . therefore ,WiFi 6 The maximum theoretical rate of is 9.6Gbit/s , The maximum speed may be less than 80% .
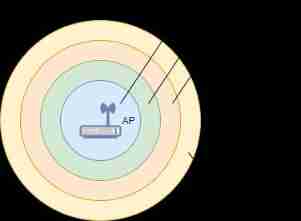
17、 Is the speed of wireless network related to distance ?
STA The maximum distance radius that can communicate is called Coverage . according to STA and AP Different distances , The maximum speed will also be different , leave AP The farther , The greater the communication delay , The lower the data transmission rate . When there are no obstacles , The coverage of wireless network is concentric distribution .
18、 Different WLAN What is the standard rate ?
IEEE 802.11a/b/g Use OFDM The modulation mode provides eight data transmission rates ,DSSS The modulation mode provides four rates .

19、IEEE 802.11n How many speeds are there ?
IEEE 802.11n Use OFDM Modulation mode , Modulation mode and symbol rate can be matched , Definition 0 ~ 31 individual MCS Indexes , Every MCS Indexes have a data transfer rate .
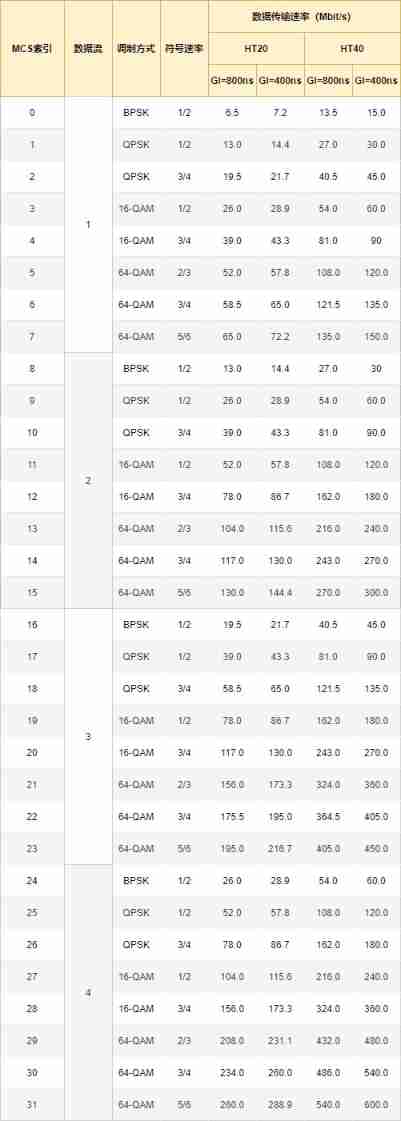
The data transmission rate depends on the channel bandwidth and Protection interval ( GI ) The combination of , At every MCS There are four modes in .
Use 20MHz The channel bandwidth of is called HT20 Pattern , Use 40MHz The channel bandwidth of is called HT40 Pattern .
MIMO Technology can divide data into multiple Data flow ( stream ), Each independent data stream is transmitted simultaneously by multiple antennas using the same frequency band . stay HT40 Mode time , A single data stream has 150Mbit/s The throughput of , stay IEEE 802.11n In the standard , Up to four data streams , Theoretically largest 600Mbit/s Data transfer rate of .
stay HT20 In mode , The largest single data flow is 75Mbit/s The throughput of . Use 2.4GHz Band time , If each channel uses 20MHz The bandwidth of the , At most three channels work at the same time , If you use 40MHz The bandwidth of the , There is only one available channel , So in 2.4GHz In band , Hardly use HT40 Pattern .
Protection interval stay 800ns On the basis of , Added... Again 400ns .
20、 What is spatial data flow ?
MIMO Multiple wireless communication channels using antennas , Let the rate rise sharply . In space , Multiple independent antennas will send wireless signals with the same frequency at the same time , Each same frequency signal is called Spatial data flow . Each spatial data stream is divided by the transmitting antenna , Finally, it reaches multiple receiving antennas .
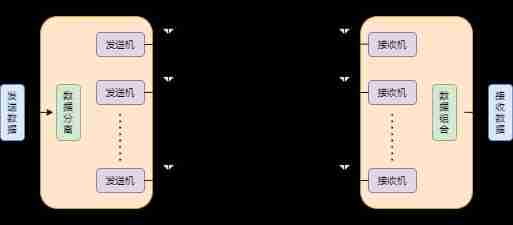
The sender uses Spatial coding ( STC ) Send the signal in time and space restructuring , Form a parallel transmission signal , And then through M Antennas send communication waves . The receiver passes N Antennas receive multipath radio waves , Also use Space time decoding ( STD ), Separate the signal Combine , So that all signals can be successfully received .
stay multipath In transit , By using multiple paths , It can be compared with the number of antennas ( Spatial data flow ) Form proportional , To improve the transmission speed of wireless data .
21、AP How many antennas are there ?
Support 802.11n The standard AP There are multiple antennas . The number of spatial streams also depends on the number of antennas , Usually use a × b :c or a × b Express AP Number of antennas .a Express Transmit antenna Or the number of wireless signals sent ,b Express receiving antenna Or the number of wireless signals received ,c Indicates available Maximum number of spatial streams . such as , current WiFi 6 AP , That is to say 802.11ax The standard AP , The biggest support 8 × 8 :8 The number of , Express 8 Root transmit antenna and 8 Composed of four receiving antennas , Use 8 Space streams for wireless data transmission .

22、WiFi 5 What is the maximum speed of ?
WiFi 5 , That is to say 802.11ac standard . contrast 802.11n ,WiFi 5 There are mainly four aspects of improvement : Wider bandwidth binding 、 More spatial flow 、 More advanced modulation technology 、 More flexible MIMO Mechanism .
Channel binding :802.11n Channel binding technology is introduced , It's two 20MHz The channels are bundled together . and WiFi 5 Able to support 160MHz Channel of , That is, binding 8 Channels . If 802.11a/b/g If it's a single lane , and 802.11n It's two lanes , arrival WiFi 5 It will reach eight lanes .

Eight data streams :WiFi 5 Continue to use 802.11n Of MIMO technology , Adopt multi antenna technology , Without consuming more bandwidth and increasing transmission power consumption , Increase data throughput . More antenna designs , Data can be spread over multiple antennas , Let every Hz More data transferred , It also increases reliability . If channel binding increases the number of lanes in a road , that MIMO Technology is to increase the number of roads , Greatly improve the bearing capacity of the road , You can pass more traffic .
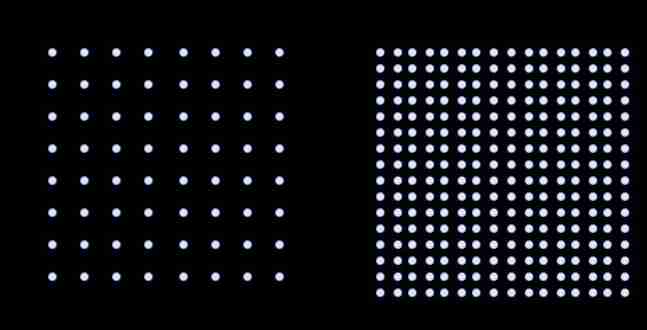
256QAM Modulation technology : In terms of signal modulation ,802.11n Is to use 64QAM , and WiFi 5 It is achieved. 256QAM .QAM The transmitted signal set is generally represented by constellation , Each constellation point corresponds to a signal , The more constellation points , The greater the amount of information transmitted , Common forms are 16QAM 、64QAM 、256QAM ,WiFi 5 The protocol standard is 256QAM , Therefore, the amount of data carried by a single carrier can reach 8bit , and 802.11n It can only reach 6bit .
Multi user MIMO( MU-MIMO ): Multi user MIMO Technology can improve single AP Number of wireless access terminals , Alleviate the problem of high-density deployment .802.11n In technology , At the same time MIMO Only single users are allowed to use , and WiFi 5 It can support multiple users MIMO, This means a single 802.11ac Of AP Different data streams can be transmitted to two or more devices .
WiFi 5 When calculating the maximum rate , Use 160MHz Pattern 、 256-QAM Modulation mode 、400ns The protection interval of ,WiFi 5 The flow rate of a single line can reach 866.7 Mbit/s, Eight flow rates are as high as 6.9Gbit/s.
23、WiFi 6 What is the maximum speed of ?
WiFi 6 , In fact, that is 802.11ax standard . contrast WiFi 5 ,WiFi 6 The improvement of is more complete band coverage 、 Higher order modulation 、 More comprehensive MU-MIMO 、 introduce OFDMA technology 、 newly added TWT Mechanism .
Support at the same time 2.4GHz and 5GHz Frequency band :WiFi5 Only support 5G Frequency band , although 5G Rich frequency band resources , But the penetration is poor , When the signal coverage is weak . and WiFi 6 Support at the same time 2.4GHz and 5GHz Frequency band ,2.4G Better signal coverage , Complete coverage of low-speed and high-speed equipment .
High level debugging mode :WiFi 6 Support 1024-QAM , higher than WiFi 5 Of 256-QAM , The amount of data carried by a single carrier can reach 10bit, It means higher data transmission rate .

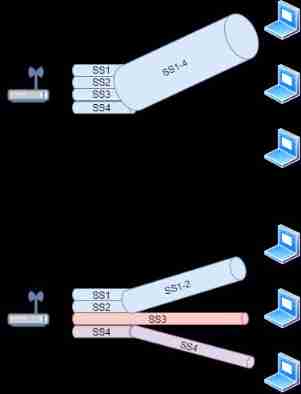
complete MU-MIMO :WiFi 5 introduce MU-MIMO function , But it supports data download , When uploading data, I still walk SU-MIMO . and WiFi6 It's a full version MU-MIMO function , Support data uplink and downlink .8 × 8 MU-MIMO , It means that up to eight terminals can be supported to transmit data at the same time . although AP Multiple terminals can be accessed , But it didn't use MU-MIMO Before technology , They send and receive data one by one ,AP Only one terminal can transmit data at a time , Only the time interval is milliseconds , We can't perceive it .WiFi 6 In the real sense, eight terminals transmit data at the same time , Suitable for high-density wireless network scenarios .
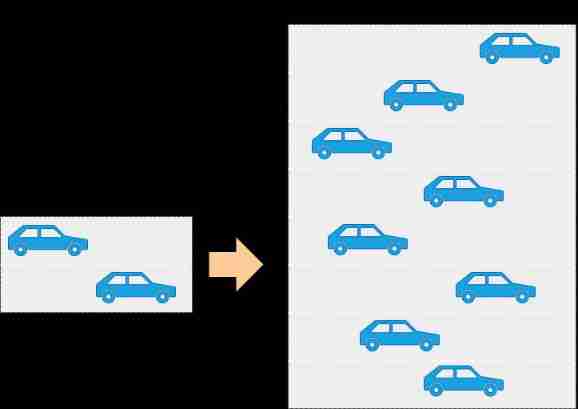
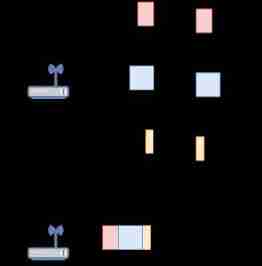
OFDMA technology :WiFi6 In OFDM Add multiple access based on ( Multi user ) technology , Thus evolved into OFDMA . actually OFDMA Redesign the frame structure , Subdivide into several resource units , Serve multiple users .
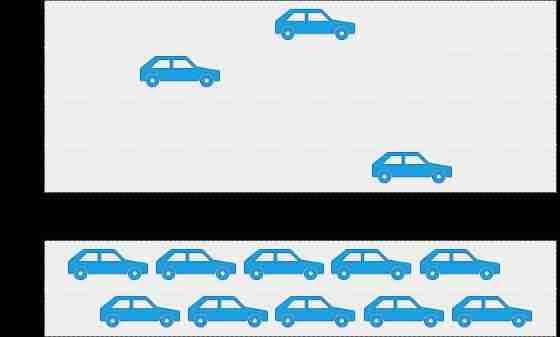
With 20MHz Take channel as an example , stay OFDM programme ( namely WiFi 4/WiFi 5 ) Every frame in the is composed of 52 Data subcarriers , But because this frame only serves one terminal . The transmitted packet is too small ( Like chat records ). Empty subcarriers cannot be allocated to other terminals .
And in the OFDMA programme ( namely WiFi 6 ) Every frame in the is composed of 234 Data subcarriers , Every time 26 The subcarrier is defined as a RU( Resource unit ), Every RU It can serve a terminal , Simply divide , Each frame can be divided into 9 Share , At most, it can be 9 User services .
It's most convenient and intuitive to explain this technology with the goods from trucks .OFDM Technology is to deliver trucks for every customer . No matter how much goods , A single trip , This inevitably leads to the phenomenon of empty trucks . and OFDMA Technology will ship multiple orders together , Let the truck go on the road as full as possible , The transportation efficiency is greatly improved .
Not only that ,WiFi6 Next OFDMA and MU-MIMO The effect of can be superimposed . The two show a complementary relationship ,OFDMA It is suitable for parallel transmission of small packets to improve channel utilization and transmission efficiency . and MU-MIMO It is suitable for parallel transmission of large data packets , Improve the effective bandwidth of single user , It can also reduce the delay .
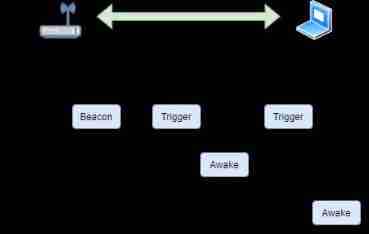
TWT Mechanism :WiFi 6 Joined the TWT Mechanism ( Target Wake Time ).TWT The mechanism is specially set for low-speed devices such as smart homes . For example, configuration 2.4GHz Frequency band 、20MHz Band WiFi terminal .AP It will automatically generate a wake-up time for data exchange , When the network data transmission is not high , Wake up these low-speed devices in turn for data exchange , For example, download the latest database 、 Upload generated data and other operations . In this way, slow devices no longer occupy bandwidth for a long time , It can effectively avoid network congestion . This is also a technical means to optimize the network bandwidth utilization .
WiFi 6 When calculating the maximum rate , Use 160MHz Pattern 、1024-QAM Modulation mode 、800ns The protection interval of ,WiFi 6 The flow rate of a single line can reach 1.2 Gbit/s, Eight flow rates are as high as 9.6Gbit/s.

24、 What is interference ?
Wireless interference The dictionary explanation of is , When two waves of the same kind meet at some point , Then the amplitude of this point is the phenomenon of the sum of the amplitudes of two waves .
During electrical transmission , Will produce electromagnetic waves , But unexpected electromagnetic waves appear , Is the reason for the interference phenomenon . For example, the sudden thunder , It will cause noise in the radio .

In wireless communication , Radio waves of different frequencies , Each has its own transmission path , Send and receive data on each transmission path , This transmission path is called channel ( channel ).
Within the reach of electromagnetic waves , A multiple AP Communicate in the same channel , Will send interference . Thunder and lightning 、 Electromagnetic wave of microwave oven , If and AP The electromagnetic waves of coincide , Will destroy the transmitted data , Result in failure to communicate , This also belongs to interference phenomenon .
It is difficult to prevent the influence of electromagnetic waves such as thunder , But avoid coming from others AP Interference of , You can also modify the channel configuration .
25、WLAN How many channels ?
WLAN In the standard , Use 2.4GHz and 5GHz Frequency band , Each frequency band has multiple channels . Set up AP when , To prevent interference , You need to put the same channel AP Isolate .
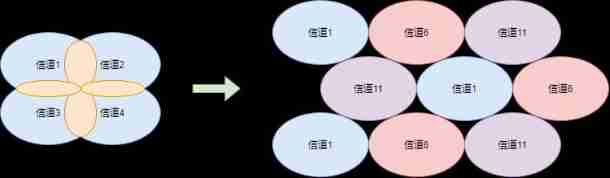
All over the world WiFi 2.4G and 5G The channels are not exactly the same , Now let's take a look at China WLAN What are the channels ?
2.4G channel
WLAN Of 2.4G The channel bandwidth is 83.5MHz , The frequency range is 2.4 ~ 2.4835 GHz , Actually, it is divided into 14 Channels , China uses the front 13 Channels , The channel number is 1 ~ 13 . The effective width of each channel is 20 MHz , And then there is 2MHz Forced isolation band of , Similar to the separation belt on the highway . For the center frequency is 2412 MHz Channel of 1 , The frequency range is 2401 ~ 2423 MHz .
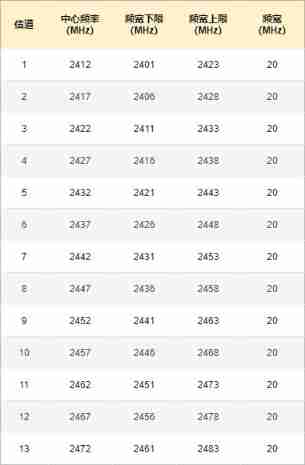
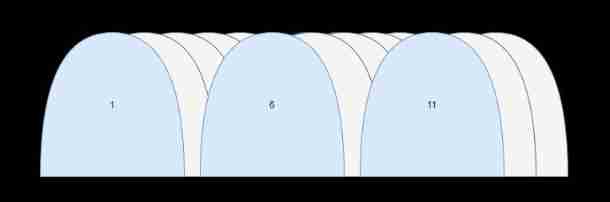
But that's not to say , Just choose a different digital channel , There must be no interference . channel 1 Frequency of use and channel 2 ~5 There is some overlap , Therefore, interference will still occur . So it looks like , The channel combination that will definitely not cause interference is 1 、6 、11 . You can also think about , What other channel combinations will not cause interference ?
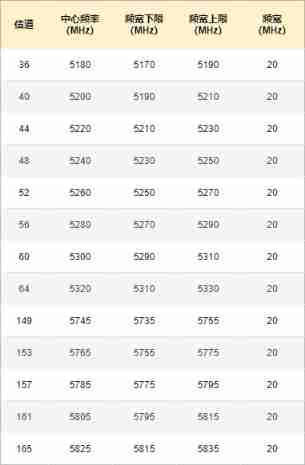
5G channel
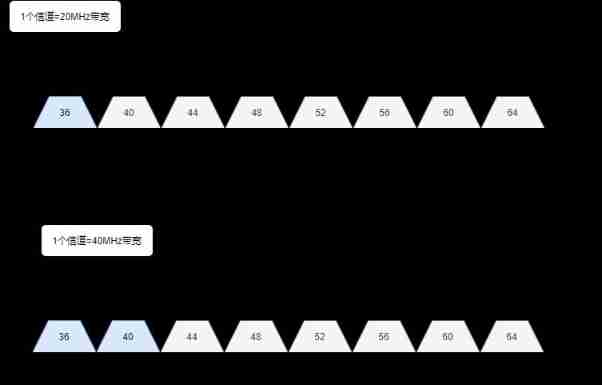
WLAN Of 5G The channel bandwidth resources are richer , Is the total 700MHz The bandwidth of , The frequency range is 5.15 ~ 5.85 GHz , There are... In China 13 individual 20MHz channel , The channel number is 36 、40 、44 、48 、52 、56 、60 、64 、149 、153 、157 、161 、165 , And all channels are Mutual interference Of , You can use it directly .
from 802.11n Start , Adjacent channels can be used at the same time , form 40MHz 、80MHz 、160MHz Bandwidth for data transmission .
26、AP What is the maximum coverage of ?
WLAN In communication , Leave AP How far can we still communicate ? The answer depends on the antenna . Antennas are used for different purposes , Divided into different categories .
According to the horizontal pattern characteristics , Can be divided into Omnidirectional antenna 、 Directional antenna 、 Smart antenna .
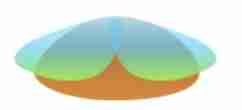
Omnidirectional antenna The radio wave energy radiated in all directions in the horizontal plane is the same , But the radio wave energy radiated in different directions in the vertical plane is different . Pattern radiation is similar to incandescent lamp radiation visible light , Horizontally 360 Degrees of radiation .

Directional antenna The radio wave energy radiated in all directions in the horizontal plane and the vertical plane is different . Pattern radiation is similar to flashlight radiation visible light , Directional radiation in a certain direction , With the same RF energy, it can achieve a longer coverage distance , But at the expense of other regional coverage .

Smart antenna There are multiple directional radiations and 1 An omnidirectional radiation mode . The antenna receives the signal transmitted by the terminal in omnidirectional mode ; The smart antenna algorithm judges the location of the terminal according to the received signal , And control CPU Send the control signal to select the directional radiation mode with the maximum radiation direction pointing to the terminal .
According to the polarization mode , It can be divided into single polarization antenna and dual polarization antenna . Both single polarization and dual polarization are linear polarization in nature , There are usually horizontal polarization and vertical polarization .
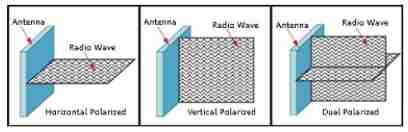
Monopolar antenna : receive 、 Transmission is two separate antennas , An antenna contains only one polarization mode . Wireless signal is horizontal transmission, horizontal reception or vertical transmission, vertical reception . Therefore, more installation space and maintenance workload are required .
Dual polarized antenna : receive 、 Transmission is an antenna , An antenna contains two polarization modes, vertical and horizontal .
In the communication distance of wireless network , The indoor coverage range is generally between tens of meters and 100 meters , The outdoor coverage can reach hundreds of meters .

Conclusion
WiFi High popularity , It has great commercial value , The time for the launch of new standards is also getting faster . It's still WiFi 6 The promotion stage of ,2022 year 1 month WiFi The alliance has already announced Wi-Fi 6 Of the 2 Version of the standard , It improves the uplink and all supported bands ( 2.4GHz、5GHz and 6GHz ) Power management for . Even in WiFi 7 When the standards have not been unified , MediaTek conducted the first WiFi 7 Live demonstration of Technology .
however , Don't ignore the actual use of Wireless Networks , The rate should be negotiated symmetrically . Yes WiFi 6 Of AP , And support is needed WiFi 6 Of STA , To negotiate WiFi 6 High rate , This is really used WiFi 6 . If you take one WiFi 5 Of STA Connect WiFi 6 Of AP , Finally, we can only negotiate WiFi 5 Rate , Can't play WiFi 6 The function of . friends , You all use it now WiFi A few ah ? Welcome to leave a message , Talk about practical WiFi Experience !
43528)]
Conclusion
WiFi High popularity , It has great commercial value , The time for the launch of new standards is also getting faster . It's still WiFi 6 The promotion stage of ,2022 year 1 month WiFi The alliance has already announced Wi-Fi 6 Of the 2 Version of the standard , It improves the uplink and all supported bands ( 2.4GHz、5GHz and 6GHz ) Power management for . Even in WiFi 7 When the standards have not been unified , MediaTek conducted the first WiFi 7 Live demonstration of Technology .
[ Outside the chain picture transfer in …(img-syYTTSpF-1644766743528)]
however , Don't ignore the actual use of Wireless Networks , The rate should be negotiated symmetrically . Yes WiFi 6 Of AP , And support is needed WiFi 6 Of STA , To negotiate WiFi 6 High rate , This is really used WiFi 6 . If you take one WiFi 5 Of STA Connect WiFi 6 Of AP , Finally, we can only negotiate WiFi 5 Rate , Can't play WiFi 6 The function of . friends , You all use it now WiFi A few ah ? Welcome to leave a message , Talk about practical WiFi Experience !
Official account : Network technology platform , reply “ Information ” Get video 、 Training course 、 Experimental Manual 、 e-book .
边栏推荐
- A solution to the problem that variables cannot change dynamically when debugging in keil5
- Aperçu en direct | Services de conteneurs ACK flexible Prediction Best Practices
- Decryption function calculates "task state and lifecycle management" of asynchronous task capability
- 这是一个不确定的时代
- Threejs Internet of things, 3D visualization of farms (II)
- 网络安全-记录web漏洞修复
- Neural networks and deep learning Chapter 6: Circular neural networks reading questions
- 线上故障突突突?如何紧急诊断、排查与恢复
- Raki's notes on reading paper: soft gazetteers for low resource named entity recognition
- QT Bluetooth: a class for searching Bluetooth devices -- qbluetooth devicediscoveryagent
猜你喜欢

首席信息官如何利用业务分析构建业务价值?
Qt蓝牙:搜索蓝牙设备的类——QBluetoothDeviceDiscoveryAgent
程序员应该怎么学数学
![[popular science] basic knowledge of thermal design: heat dissipation analysis of 5g optical devices](/img/45/380e739f5eed33626c363756f814d3.png)
[popular science] basic knowledge of thermal design: heat dissipation analysis of 5g optical devices
level17
C26451: arithmetic overflow: use the operator * on a 4-byte value, and then convert the result to an 8-byte value. To avoid overflow, cast the value to wide type before calling the operator * (io.2)
![[finebi] the process of making custom maps using finebi](/img/3a/d638dbac6a26c37087ec9550c35e63.png)
[finebi] the process of making custom maps using finebi

直播預告 | 容器服務 ACK 彈性預測最佳實踐

2022-2028 global and Chinese virtual data storage Market Research Report
蛇形矩阵
随机推荐
Neural networks and deep learning Chapter 2: machine learning overview reading questions
蛇形矩阵
About the prompt loading after appscan is opened: guilogic, it keeps loading and gets stuck. My personal solution. (it may be the first solution available in the whole network at present)
PHP reads the INI file and writes the modified content
Function (error prone)
WeNet:面向工业落地的E2E语音识别工具
User behavior collection platform
A solution to the problem that variables cannot change dynamically when debugging in keil5
【虛幻引擎UE】實現UE5像素流部署僅需六步操作少走彎路!(4.26和4.27原理類似)
TPG x AIDU|AI领军人才招募计划进行中!
Common features of ES6
函数(基本:参数,返回值)
Neural networks and deep learning Chapter 5: convolutional neural networks reading questions
Aperçu en direct | Services de conteneurs ACK flexible Prediction Best Practices
介绍汉明距离及计算示例
Threejs Internet of things, 3D visualization of farms (I)
Uncover the seven quirky brain circuits necessary for technology leaders
2022-2028 global and Chinese FPGA prototype system Market Research Report
Serpentine matrix
Observable time series data downsampling practice in Prometheus