当前位置:网站首页>生成随机密码/验证码
生成随机密码/验证码
2022-07-06 09:28:00 【梦想身高1米8】
// len,随机长度
const randomAuthorizeCode = (len) => {
// seed,随机范围
var seed = ['A', 'B', 'C', 'D', 'E', 'F', 'G', 'H', 'I', 'J', 'K', 'L', 'M', 'N', 'O', 'P', 'Q', 'R', 'S', 'T', 'U', 'V', 'W', 'X', 'Y', 'Z',
'a', 'b', 'c', 'd', 'e', 'f', 'g', 'h', 'i', 'j', 'k', 'm', 'n', 'o', 'p', 'q', 'r', 's', 't', 'u', 'v', 'w', 'x', 'y', 'z',
'0', '1', '2', '3', '4', '5', '6', '7', '8', '9'];
let r = ''
// random随机选中
for (let i = 0; i < len; i++) {
let t = Math.round(Math.random() * (seed.length - 1));
r += seed[t];
}
return r;
}
边栏推荐
- TCP's three handshakes and four waves
- QT实现窗口渐变消失QPropertyAnimation+进度条
- Nodejs+vue online fresh flower shop sales information system express+mysql
- Penetration test 2 --- XSS, CSRF, file upload, file inclusion, deserialization vulnerability
- 860. Lemonade change
- C language learning notes
- Is the sanic asynchronous framework really so strong? Find truth in practice
- Penetration test (7) -- vulnerability scanning tool Nessus
- Nodejs crawler
- Programmers, what are your skills in code writing?
猜你喜欢

Information security - Epic vulnerability log4j vulnerability mechanism and preventive measures
![[exercise-5] (UVA 839) not so mobile (balance)](/img/8e/48dcf75f7347b36301df6fc129c09d.png)
[exercise-5] (UVA 839) not so mobile (balance)
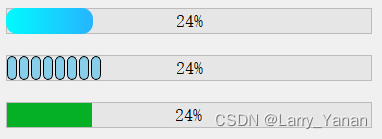
QT实现窗口渐变消失QPropertyAnimation+进度条
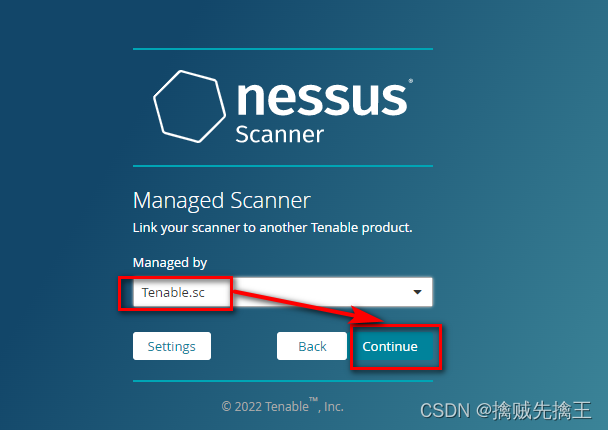
Penetration test (7) -- vulnerability scanning tool Nessus

409. Longest palindrome

Information security - threat detection engine - common rule engine base performance comparison
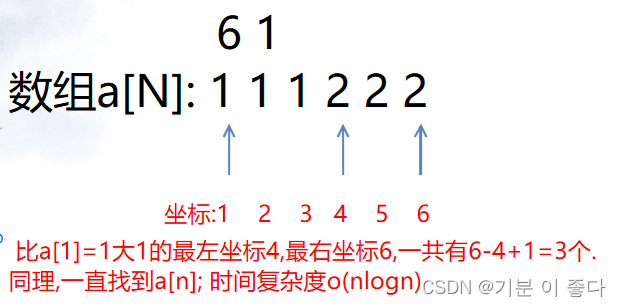
Luogu P1102 A-B number pair (dichotomy, map, double pointer)

Penetration test (2) -- penetration test system, target, GoogleHacking, Kali tool
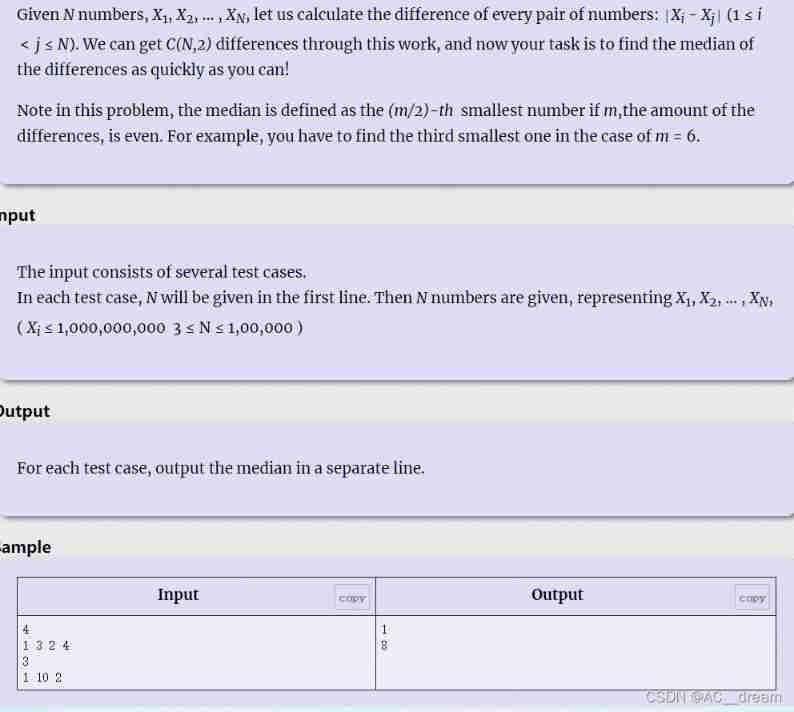
(POJ - 3579) median (two points)

The concept of C language array
随机推荐
Maximum product (greedy)
【练习-11】4 Values whose Sum is 0(和为0的4个值)
The most complete programming language online API document
Penetration test 2 --- XSS, CSRF, file upload, file inclusion, deserialization vulnerability
[exercise-1] (UVA 673) parentheses balance/ balanced brackets (stack)
[exercise-3] (UVA 442) matrix chain multiplication
New to redis
Codeforces Round #799 (Div. 4)A~H
C language is the watershed between low-level and high-level
Information security - Analysis of security orchestration automation and response (soar) technology
Information security - threat detection - detailed design of NAT log access threat detection platform
921. Minimum additions to make parentheses valid
socket通讯
Penetration test (1) -- necessary tools, navigation
最全编程语言在线 API 文档
(POJ - 3579) median (two points)
The concept of C language array
Truck History
[exercise 4-1] cake distribution
PySide6 信号、槽