当前位置:网站首页>Knowledge Points for Network Planning Designers' Morning Questions in November 2021 (Part 1)
Knowledge Points for Network Planning Designers' Morning Questions in November 2021 (Part 1)
2022-08-05 00:45:00 【GE_1001】
1. Cybersecurity review is a work carried out in accordance with the National Security Law of the People's Republic of China and the Cybersecurity Law of the People's Republic of China.
2. Integrity means that information can only be modified by those who are allowed, and it can be judged whether it has been tampered with.At the same time, a system should also operate according to its original specified functions and not be manipulated by unauthorized persons.
3. Denial of service is to use a large number of legitimate requests to occupy a large number of network resources in order to achieve the purpose of paralyzing the network and equipment.
4. Service flow analysis is to conduct long-term monitoring of the system and use statistical analysis methods to study parameters such as communication frequency, communication time flow, and changes in the total amount of communication, and find valuable information and laws.
5. The advantage of the incremental model is that it is easy to understand and has low management costs; it reduces user requirements changes; it emphasizes early stage planning and requirements investigation and product testing in development; the cost and time for delivering the first version are relatively small.The disadvantage is that the configuration is complex and the initial changes are not planned well, which will lead to unstable subsequent increments.
6. The sequence data type represents several ordered data.Sequence data types in python language are divided into immutable sequence data types and mutable sequence data types.Immutable sequences include strings, tuples, byte strings, and ranges; mutable sequences include lists and byte arrays.
7. Availability is the percentage of time a system can operate normally.Often expressed in terms of the length of time between failures or the speed at which the system can return to normal in the event of a failure.
8. In the three-tier C/S software architecture: the presentation layer belongs to the user interface part and is responsible for the dialogue function between the user and the application; the functional layer is equivalent to the ontology of the application and is responsible for specific business processing logic; the data layer is theThe database management system is responsible for managing the reading and writing of database data.
9. When the switch processes the data frames that cannot be found, in order to avoid the purpose of data forwarding, it forwards to all ports.The switch adds the corresponding MAC address entry by reading the source address in the input frame.The MAC address entry of the switch changes dynamically.
10.1000BASE-T is a full-duplex network using four twisted pairs, each pair of which transmits bidirectionally.1000BASE-T supports Category 5e or Category 5 twisted pair with better performance.1000BASE-TX uses four twisted pairs, two of which transmit and two receive.1000BASE-TX can only support six types of twisted pair.The encoding technology used by 1000BASE-TX is PAM5.
11. Unnumbered frame (U frame).This frame can realize link control and connection management.The frame can be divided into command and response frame for transmitting information; command and response frame for link recovery; command and response frame for setting data transmission mode; other command and response frame.Contains the SABME frame for establishing the connection and the UA frame for acknowledging the command from the secondary station to the primary station.
12. In the HDLC frame structure, 01111110 is considered to be the frame boundary.In order to avoid the 01111110 sequence appearing in the frame to be treated as a boundary field, HDLC adopts the zero-bit padding method to prevent 6 consecutive 1s from appearing in a frame.
13. Head Length (IHL).This field is 4 bits long.The unit that represents the number is 32 bits, that is, 4 bytes.The commonly used value is 5, which is also the minimum value, indicating that the header is 20 bytes; the maximum value that can be taken is 15 (1111 in binary), indicating that the header is 60 bytes.
14.ADSL adopts echo cancellation (EC technology) technology, and its uplink and downlink channel frequencies can partially overlap.
15. Spanning Tree Protocol (STP) is a link management protocol that provides path redundancy for the network while preventing loops.
- There are many ways of data exchange in communication network, mainly divided into circuit switching, message switching, packet switching and cell switching.The switching method adopted by the core of the Internet network is packet switching.
17. The virtual circuit establishes a logical connection before transmitting the packet. Since the physical link connecting the source host and the destination host already exists, there is no need to actually establish a physical link, but a connection must be established.
18.SDH frame structure consists of the following three parts:
(1) Section overhead, including regeneration section overhead and multiplex section overhead.The function of segment overhead is to ensure that the information payload is normal bytes for network operation, management, and maintenance.
(2) Management unit pointer: Point to the exact position of the first byte of the information payload within the frame.
(3) Information payload: store all kinds of information to be transmitted.
19. In BGP, the adjacent connection between two routers is called a peer connection, and the two routers are peers with each other.If the router peers are in the same AS, they are called IBGP peers; otherwise, they are called EBGP peers.
By default, the routers inside the AS establish BGP peering in pairs.
20. The Traceroute command uses the ICMP protocol to locate all routers on the path between the client and the destination.The client directly sends an ICMP echo request packet, and the TTL of the first request is 1,
The TTL of the second request is 2, and then increments until the 30th; the intermediate router sendsReturns an ICMP TTL-expired packet.When the server receives an echo request, it will send an ICMP echo reply packet to the client.
边栏推荐
- ora-00604 ora-02429
- 僵尸进程和孤儿进程
- SV class virtual method of polymorphism
- TinyMCE disable escape
- 码率vs.分辨率,哪一个更重要?
- gorm joint table query - actual combat
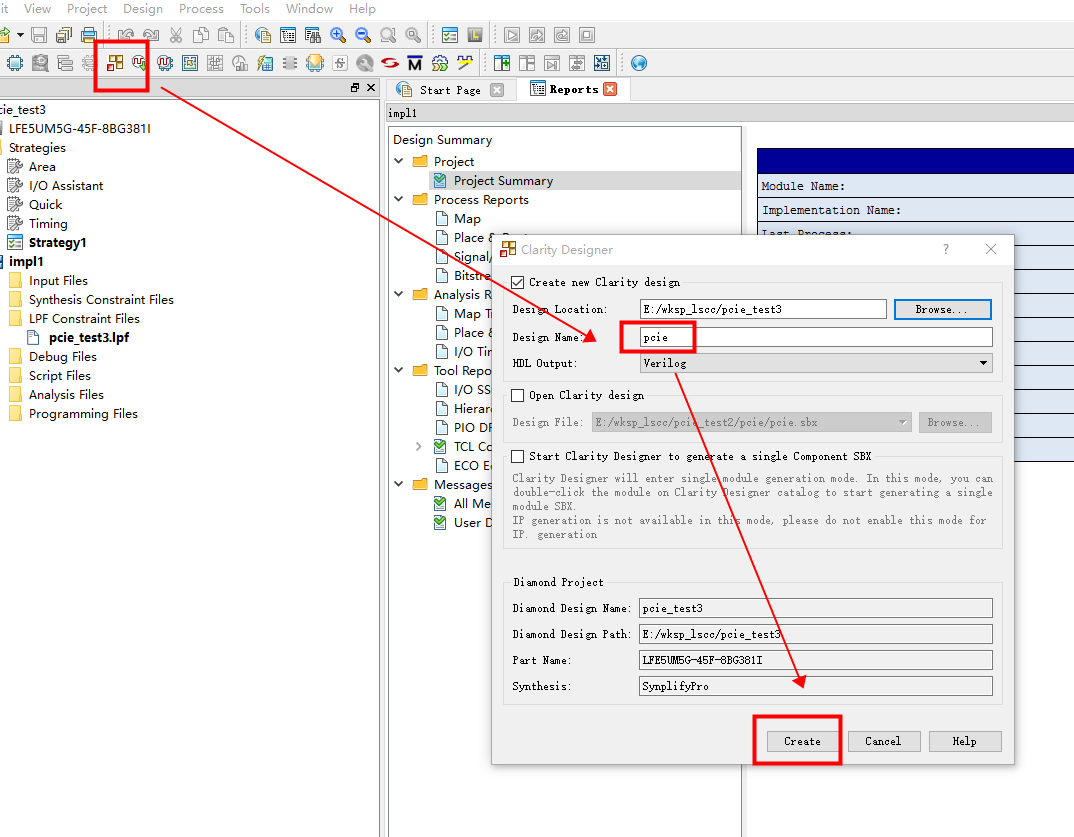
- Lattice PCIe 学习 1
- [230] Execute command error after connecting to Redis MISCONF Redis is configured to save RDB snapshots
- 2022杭电多校第三场 K题 Taxi
- LiveVideoStackCon 2022 Shanghai Station opens tomorrow!
猜你喜欢
随机推荐
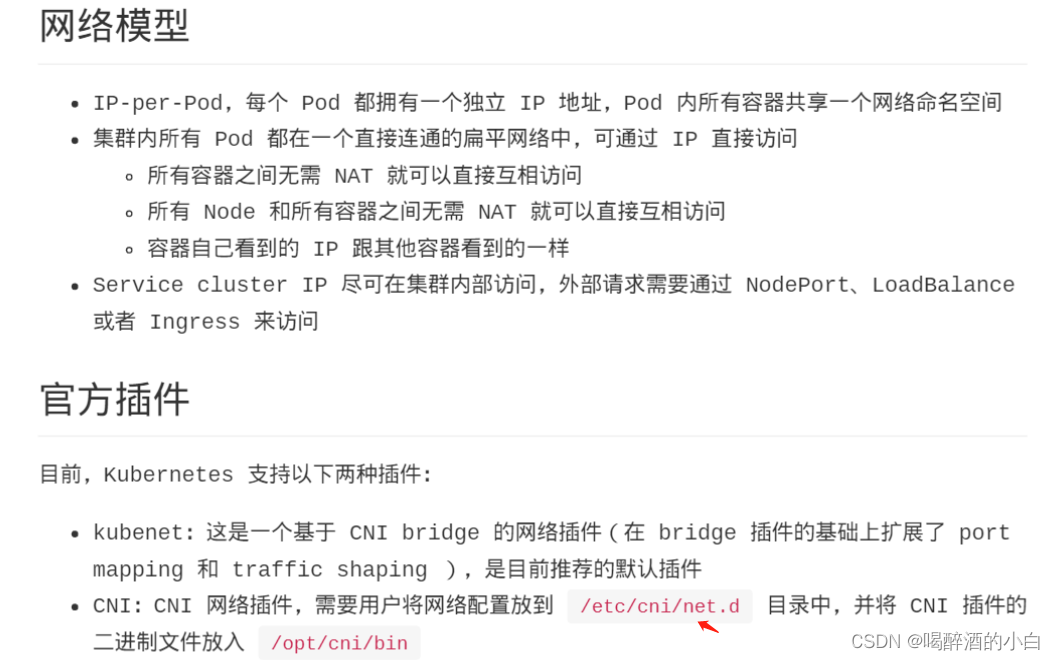
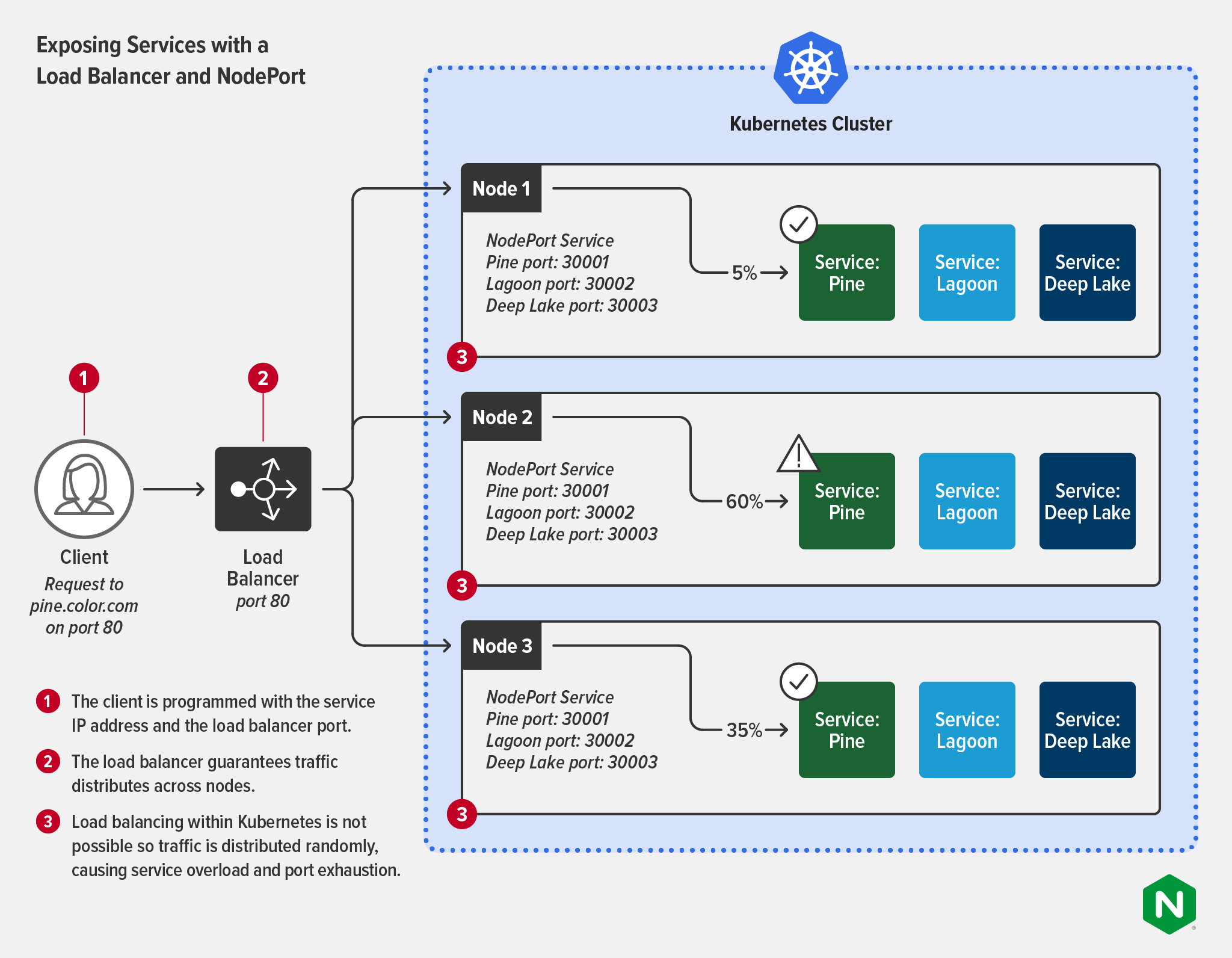
Getting Started with Kubernetes Networking
Software Testing Interview Questions: Qualifying Criteria for Software Acceptance Testing?
### Error querying database. Cause: com.mysql.jdbc.exceptions.jdbc4.MySQLNonTransientConnectionExcep
5. PCIe official example
Kubernetes 网络入门
QSunSync Qiniu cloud file synchronization tool, batch upload
Helm Chart
Software Testing Interview Questions: What do test cases usually include?
【FreeRTOS】FreeRTOS与stm32内置堆栈的占用情况
软件测试面试题:关于自动化测试工具?
gorm joint table query - actual combat
tiup update
软件测试面试题:软件测试类型都有哪些?
面试汇总:为何大厂面试官总问 Framework 的底层原理?
GCC:编译时库路径和运行时库路径
如何用 Solidity 创建一个“Hello World”智能合约
If capturable=False, state_steps should not be CUDA tensors
2022牛客多校训练第二场 J题 Link with Arithmetic Progression
Will domestic websites use Hong Kong servers be blocked?
tiup status