当前位置:网站首页>A real penetration test
A real penetration test
2022-07-04 07:09:00 【Distant sky】
Summary of the future :
Idle and boring , I came across a website , forehead ... There are many advertisements

A sudden impulse , Casually take the missing scanning tool and sweep it around , Several vulnerabilities were found , All are xss Loophole
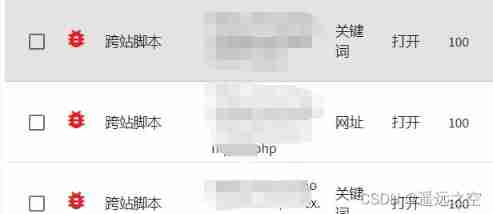
" Test a wave with curiosity , Manually tested payload They all failed , The website "(" ,")" ,"<","> and "alert" Wait until these keywords are filtered out . No way out . Only hard —> Run directly to the dictionary , For xss Vulnerability dictionary payload test .
Finally, a lot of useful things are measured payload

Randomly choose a few tests , Successful pop-up !
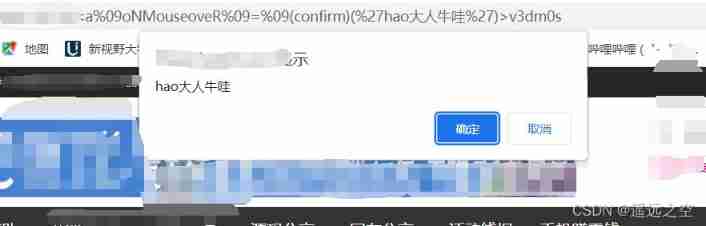
At present, only one vulnerability has been tested , Other vulnerability points have not been tested .
As a student who has studied network security law , Of course, I know that I can't do things that harm others , Especially such a conscientious sharing website , Never destroy .
边栏推荐
- Download address of the official website of national economic industry classification gb/t 4754-2017
- Zhanrui tankbang | jointly build, cooperate and win-win zhanrui core ecology
- notepad++如何统计单词数量
- 关于IDEA如何设置快捷键集
- 果果带你写链表,小学生看了都说好
- Review of enterprise security incidents: how can enterprises do a good job in preventing source code leakage?
- Cochez une colonne d'affichage dans une colonne de tableau connue
- Analysis of tars source code 5
- Computer connects raspberry pie remotely through putty
- Chain ide -- the infrastructure of the metauniverse
猜你喜欢
Vulhub vulnerability recurrence 77_ zabbix
Deep profile data leakage prevention scheme
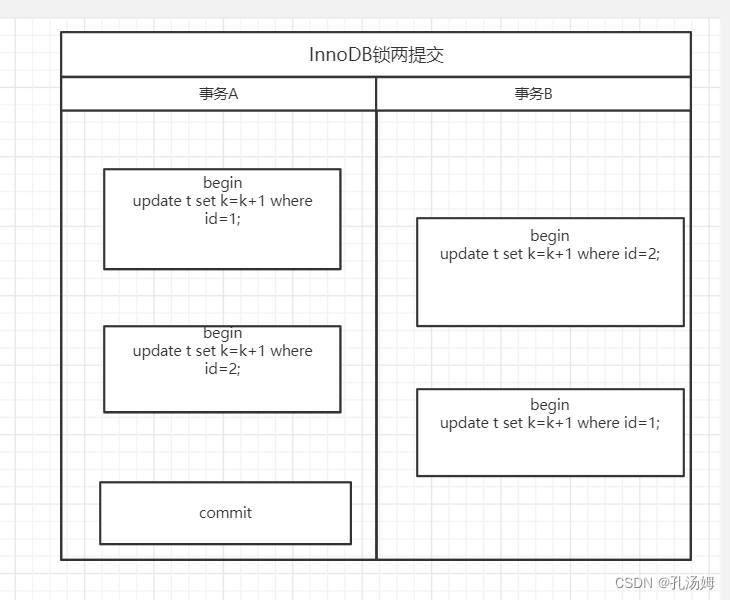
MySQL 45 lecture learning notes (VII) line lock
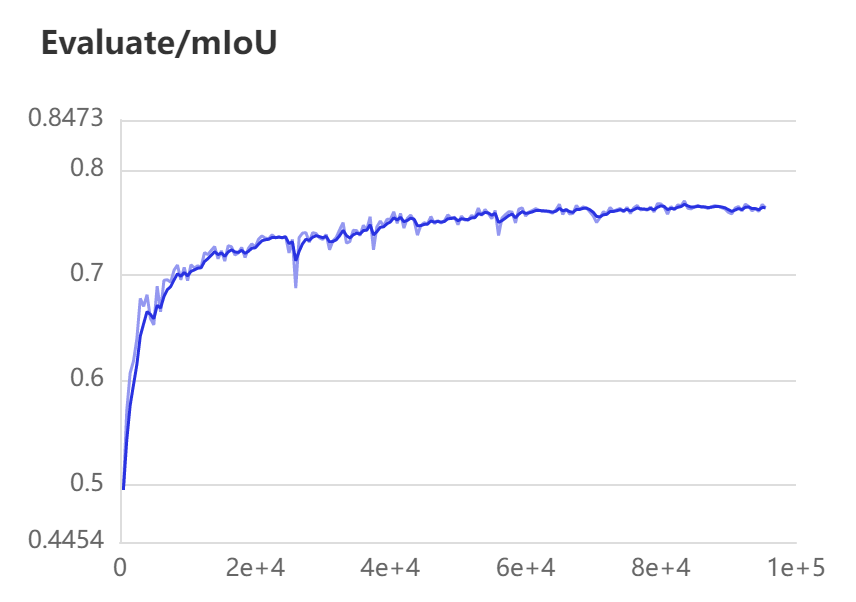
提升复杂场景三维重建精度 | 基于PaddleSeg分割无人机遥感影像
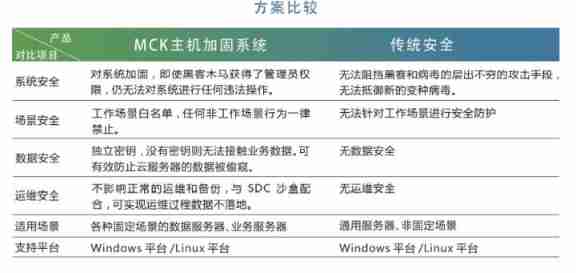
The important role of host reinforcement concept in medical industry
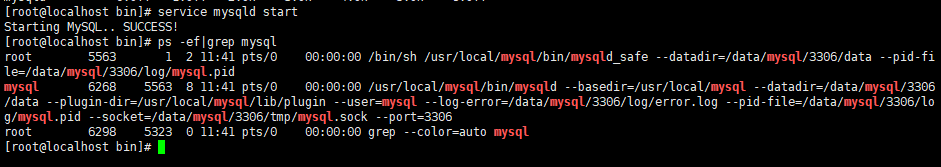
centos8安装mysql.7 无法开机启动
Campus network problems
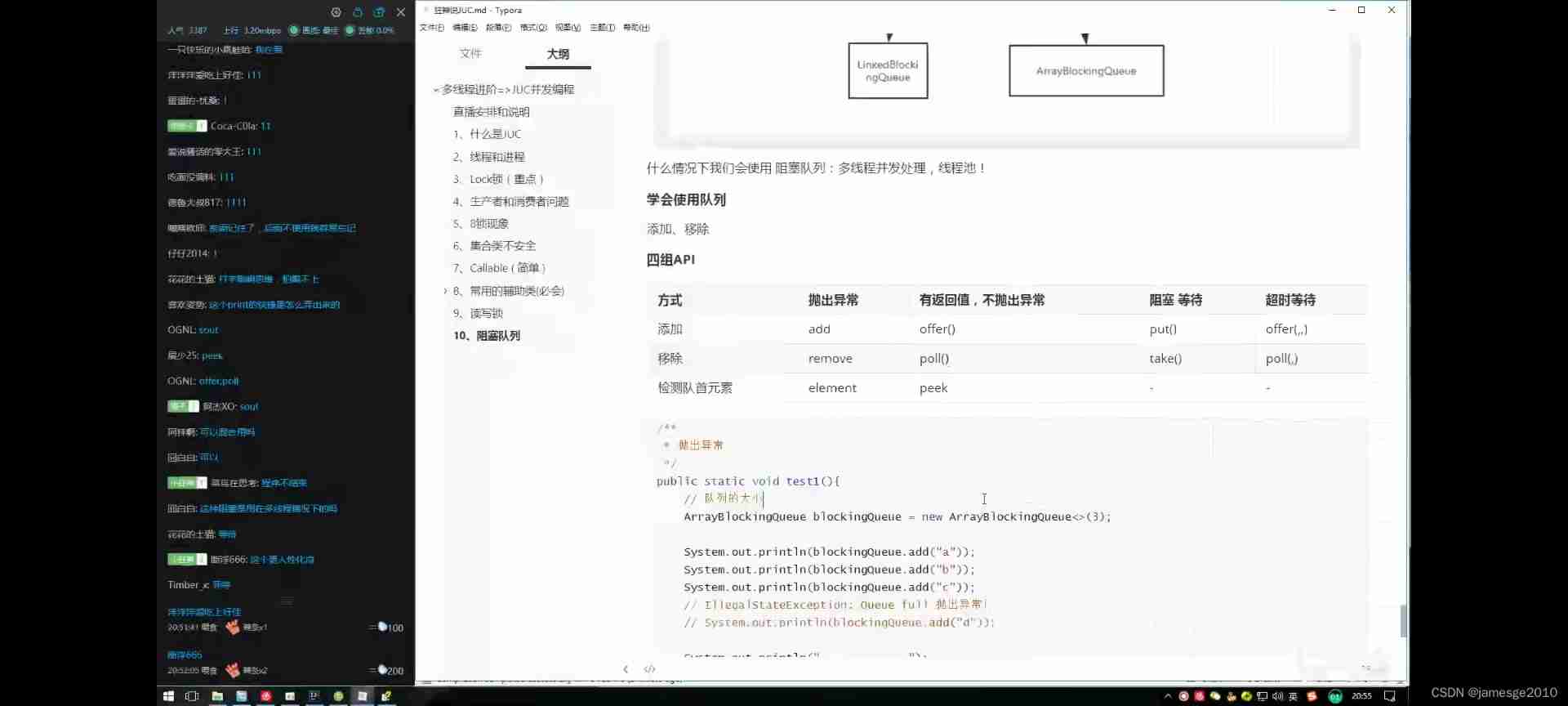
Four sets of APIs for queues
The final week, I split
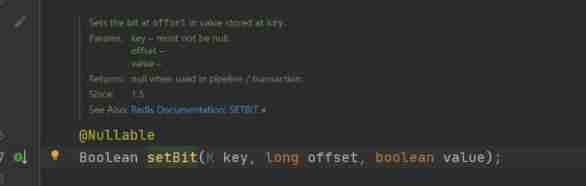
Deep understanding of redis -- a new type of bitmap / hyperloglgo / Geo
随机推荐
Splicing plain text into JSON strings - easy language method
Selection (021) - what is the output of the following code?
The difference between synchronized and lock
Electronic Association C language level 1 35, bank interest
Pangu open source: multi support and promotion, the wave of chip industry
What is the use of cloud redis? How to use cloud redis?
电脑通过Putty远程连接树莓派
大厂技术专家:架构设计中常用的思维模型
Knowledge payment applet dream vending machine V2
[freertos] freertos Learning notes (7) - written freertos bidirectionnel Link LIST / source analysis
uniapp小程序分包
《国民经济行业分类GB/T 4754—2017》官网下载地址
果果带你写链表,小学生看了都说好
Tar source code analysis 9
输入年份、月份,确定天数
Mysql 45讲学习笔记(十二)MySQL会“抖”一下
Cervical vertebra, beriberi
MySQL storage engine
Latex中的单引号,双引号如何输入?
期末周,我裂开