当前位置:网站首页>Alibaba cloud microservices (I) service registry Nacos, rest template and feign client
Alibaba cloud microservices (I) service registry Nacos, rest template and feign client
2022-07-06 13:08:00 【Geometer】
First, let's introduce the concept of service registration
Actually DNS It is a service registration , In microservices . The application instance obtains the information of the service instance through the registry , Use this information to request the parameters they provide
There are ten instances of a service ,client How to know which one to visit ?
Service registration is needed to help us
First deploy a service center locally Nacos:
Start good nacos On the one hand, it can monitor API, On the one hand, there is a console
First, deploy a service End
You can see nacos You can find that the service has been registered to the service center 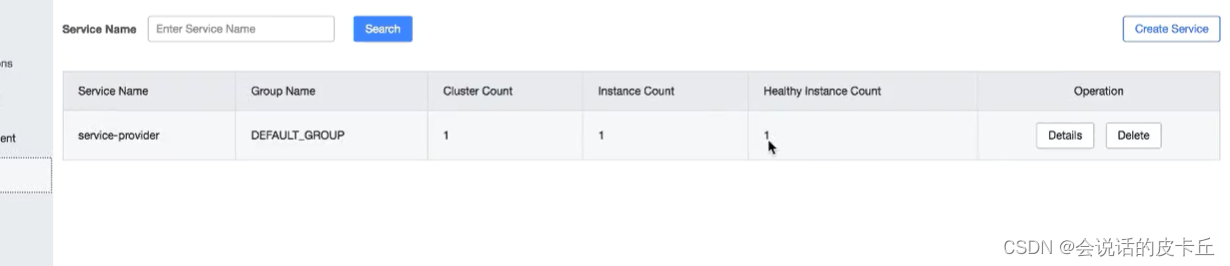
Now deploy Consumer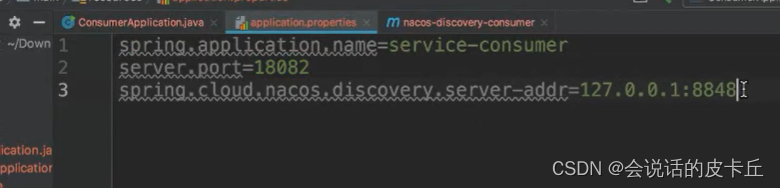
consumer It can be used REST Template and Feign Client To write
Briefly introduce these two gadgets , They are all based on http Protocol to communicate
rest template It needs to be assembled every time url, It is relatively simple to use ,RestTemplate In splicing url When , You can specify ip Address + Port number , You can directly request the interface without going through the service registry ; You can also specify a service name , Request to go to the service registry first ( Such as nacos) Get the corresponding service ip Address + Port number , And then pass by HTTP Forward the request to the corresponding service interface ( need @LoadBalanced)
Feign The underlying implementation of is dynamic agent , Its use is realized through annotations , It is also mapped through the service center 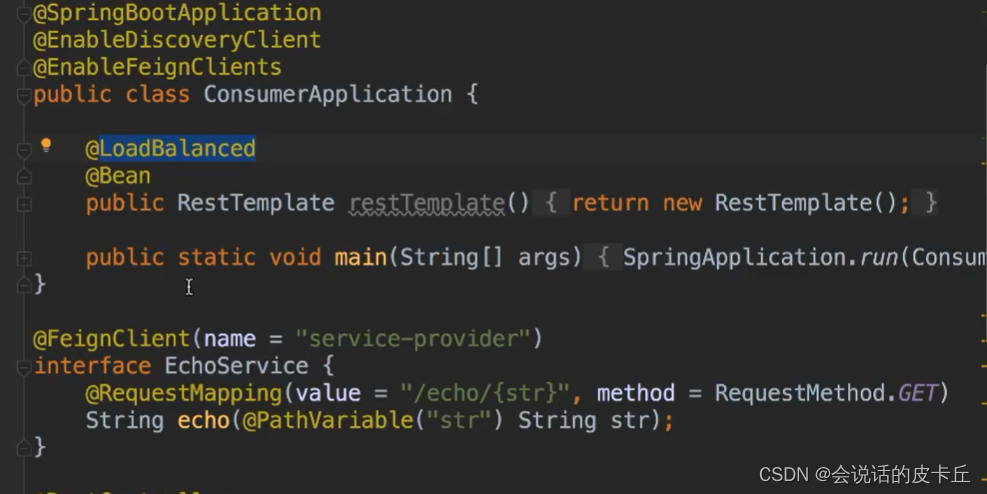
About feigin Use :
1. stay consumer add to @@EnableFeignClients
2. stay consumer add to Feign The interface of ( Use @FeignClient(value = “service-provider”), among value It refers to the services of producers ),producer Is the service that implements this interface
3. stay producer Created in controller Interface , Realization 2 The specific logic of the interface in
4. stay consumer Call in the
边栏推荐
- 十分鐘徹底掌握緩存擊穿、緩存穿透、緩存雪崩
- How do architects draw system architecture blueprints?
- [untitled]
- Record: newinstance() obsolete replacement method
- Introduction pointer notes
- [algorithm] sword finger offer2 golang interview question 1: integer division
- 167. Sum of two numbers II - input ordered array - Double pointers
- Exception: ioexception:stream closed
- First acquaintance with C language (Part 1)
- 十分钟彻底掌握缓存击穿、缓存穿透、缓存雪崩
猜你喜欢
![[algorithm] sword finger offer2 golang interview question 2: binary addition](/img/c2/6f6c3bd4d70252ba73addad6a3a9c1.png)
[algorithm] sword finger offer2 golang interview question 2: binary addition
![Heap sort [handwritten small root heap]](/img/f0/6efda3c6f499a32671a935dd2f21db.png)
Heap sort [handwritten small root heap]
Music playback (toggle & playerprefs)
![[algorithm] sword finger offer2 golang interview question 10: subarray with sum K](/img/63/7422489d09a64ec9f0e79378761bf1.png)
[algorithm] sword finger offer2 golang interview question 10: subarray with sum K
Fgui project packaging and Publishing & importing unity & the way to display the UI
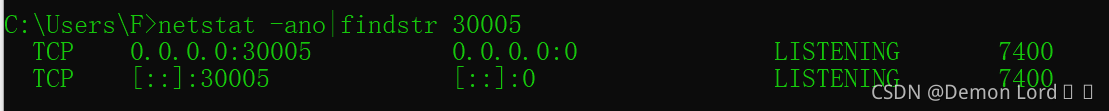
服务未正常关闭导致端口被占用
What are the advantages of using SQL in Excel VBA
【无标题】
Dark chain lock (lca+ difference on tree)
How do architects draw system architecture blueprints?
随机推荐
继承和多态(下)
异常:IOException:Stream Closed
[rtklib] preliminary practice of using robust adaptive Kalman filter under RTK
最短Hamilton路径 (状压DP)
KF UD decomposition pseudo code implementation advanced [2]
抽象类和接口
Branch and loop statements
阿里云微服务(二) 分布式服务配置中心以及Nacos的使用场景及实现介绍
MYSQL索引钟B-TREE ,B+TREE ,HASH索引之间的区别和应用场景
Redis介绍与使用
继承和多态(上)
Usage differences between isempty and isblank
系统设计学习(三)Design Amazon‘s sales rank by category feature
Iterable、Collection、List 的常见方法签名以及含义
Fgui project packaging and Publishing & importing unity & the way to display the UI
First acquaintance with C language (Part 2)
Error: sorting and subscript out of bounds
一文搞定 UDP 和 TCP 高频面试题!
All in one 1405: sum and product of prime numbers
Pride-pppar source code analysis