当前位置:网站首页>10 ways of interface data security assurance
10 ways of interface data security assurance
2022-07-07 03:44:00 【1024 questions】
introduction
1. Data encryption , Prevent the transmission of newspaper messages .
1.1 How to encrypt data ?
1.2 friends , Do you remember https How about the principle of ?
2. Data signature verification
2.1 What is countersigning and signature verification ?
2.2 With https Wait for encrypted data , Why is it necessary to add a signature for verification
3.token Authorization and authentication mechanism
3.1 token Authorized authentication scheme
3.2 How to ensure token The safety of the ?token Hijacked ?
4. Time stamp timestamp Timeout mechanism
5.timestamp+nonce The scheme prevents replay attacks
6. Current limiting mechanism
7. Blacklist mechanism
8. White list mechanism
9. Data desensitization mask
10. Check the validity of data parameters .
introductionIn our daily development , How to ensure the security of interface data ? Personally feel , Interface data security assurance process , Mainly reflected in these aspects : One is the security of data transmission , And the data arrives at the server , How to identify data , The last point is the security of data storage . Today, I want to talk to you about how to ensure the security of interface data 10 A plan .

We all know , Data in the process of network transmission , It's easy to be caught . If you are using http agreement , Because it is transmitted in clear text , Users' data can be easily obtained by others . So we need to encrypt the data .
1.1 How to encrypt data ? Common implementation methods , Is to encrypt key fields . such as , You have a login interface , You can encrypt the password . What encryption algorithm is generally used ? Simple point can use symmetric encryption algorithm ( Such as AES) To encrypt and decrypt , Or hash algorithm processing ( Such as MD5).
What is symmetric encryption : An encryption algorithm that uses the same key for encryption and decryption .

Asymmetric encryption : Asymmetric encryption algorithm requires two keys ( Public key and private key ). Public key and private key exist in pairs , If you encrypt data with a public key , Only the corresponding private key can be decrypted .
A safer way , Is to use asymmetric encryption algorithm ( Such as RSA perhaps SM2), Public key encryption , Private key decryption .

If you want to encrypt all fields , It is generally recommended to use https agreement .https In fact, in the http and tcp Add a layer of encryption between SSL.
Interview is also often asked , as follows :

Client initiated Https request , Connected to the server 443 port .
The server must have a set of digital certificates ( The certificate contains a public key 、 Certification authority 、 Expiration date, etc ).
The server sends its own digital certificate to the client ( The public key is in the certificate , The private key is held by the server ).
After the client receives the digital certificate , Will verify the validity of the certificate . If the certificate is verified , A random symmetric key will be generated , Encrypt with the public key of the certificate .
The client sends the encrypted key of the public key to the server .
After the server receives the ciphertext key sent by the client , Use your previously reserved private key to decrypt it asymmetrically , After decryption, you get the client's key , Then use the client key to encrypt the returned data symmetrically , The data transmitted by maozi are ciphertext .
The server returns the encrypted ciphertext to the client .
When the client receives , Decrypt it symmetrically with your own key , Get the data returned by the server .
Daily business , Data transmission encryption , use https That's all right. , If the safety requirements are high , Such as login and registration , Need to transmit password , The password can be used RSA And so on , Encrypt password . If your business , The security requirements are very high , You can simulate https This process , To message , Do encryption and decryption again .
Data message signature verification , It is a common means to ensure the safety of data transmission , It can ensure that the data will not be tampered with in the transmission process . The enterprise transfer system I used to do , Just use the additional signature to verify the signature .
2.1 What is countersigning and signature verification ? Data signature : use Hash Algorithm ( Such as MD5, perhaps SHA-256) Generate message summary from original request parameters , Then encrypt the digest with the private key , Get the digital signature corresponding to this message sign( This process is countersigning ). Generally speaking , The requestor will send the digital signature and the original message to the receiver .

attestation : The receiver gets the original message and digital signature (sign) after , Use the same Hash Algorithm ( For example, they all use MD5) Generate a summary from the message A. in addition , Decrypt the digital signature with the public key provided by the other party , Get a summary B, contrast A and B Are they the same? , You can know whether the message has been tampered with .

In fact, the additional signature , I understand , The request parameters , According to certain rules , utilize hash Algorithm + The encryption algorithm generates a unique label sign. If the signature is checked , That is to treat the request parameters according to the same rules , Then use the same hash Algorithm , And the corresponding key decryption processing , To compare whether this signature is consistent .
Another example , Some partners achieve this , Set all non empty parameters ( Contains a package AccessKey, Unique developer ID ) In ascending order , Then splice another one SecretKey( This is only used for local encryption , Not participating in network transmission , It is only used as a signature inside ), Get one stringSignTemp Value , Last use MD5 operation , obtain sign.
After the server receives the message , Can check , Only by having a legal identity AccessKey And signature Sign correct , Only then . This solves the problem of authentication and parameter tampering , If the request parameters are hijacked , Because the hijacker can't get SecretKey( For local encryption only , Not participating in network transmission ), He can't forge a legal request
Some friends may have questions , Signature verification is mainly to prevent data from being tampered with during transmission , If it's all used https The next protocol encrypts the data , Why can it be tampered with ? Why is it necessary to add a signature for verification ?
The data was encrypted during transmission , Theoretically , Even if caught , And the data won't be tampered with . however https It's not absolutely safe . You can read this article : terrible , original HTTPS It's no use . There's another point :https The encrypted part is only on the Internet , Then there are many services that jump to each other on the intranet , Countersignature can also be guaranteed here that it will not be tampered with by intermediaries , Therefore, the interface development with high security requirements for general transfer , All need to be signed for verification
Daily development , Our website or APP, They all need users to log in . Then if it is a non login interface , How to ensure safety , How to confirm the user's identity ? have access to token Authorization mechanism .
3.1 token Authorized authentication schemetoken Authorized authentication scheme : The user enters the user name and password on the client , Click to log in , The server will verify the password successfully , A unique value will be returned to the client token, And will token In the form of key value pairs stored in the cache ( It's usually Redis) in . The subsequent client should take this with it for all operations requiring authorization module token, After the server receives the request , to token verification , If token There is , It shows that it is a legal request .
token The login authorization flow chart is as follows :

The user enters the user name and password , Initiate a login request
The server verifies the password , If the verification passes , Generate a globally unique token.
take token Stored in redis in , among key yes token,value yes userId Or user information , Set an expiration time .
Put this token Return to the client
When the user initiates other business requests , You need to bring this token
Background services will uniformly intercept interface requests , Conduct token Validation , And get user information from it , For subsequent business logic . If token non-existent , Indicates that the request is invalid .
How can we guarantee token What about the safety of the company ?
for instance , If I get token, Is it possible to call any interface on the server side ? We can consider from these aspects :
token Set a reasonable period of validity
Use https agreement
token You can encrypt again
If you are accessing sensitive information , Simply add token It's not enough. , Usually, the white list will be configured
Speaking of token, Some friends may think of jwt, namely (JSON Web Token), In fact, it is token A kind of . Interested friends can go to know about it .
4. Time stamp timestamp Timeout mechanism Data is easy to capture , Suppose we use https And countersignature , Even if the middleman catches the data message , It can't see the real data . But some lawbreakers , He doesn't care about the real data , Instead, you get the captured packets directly , Make a malicious request ( such as DOS attack ), To bring down your system .
We can introduce timestamp timeout mechanism , To ensure interface security . Namely : Every time a user requests it, he will bring a timestamp of the current time timestamp, The server receives timestamp after , Decrypt , After passing the examination , Compare with the current time of the server , If the time difference is greater than a certain time ( such as 3 minute ), The request is considered invalid .
The timestamp timeout mechanism is also vulnerable , If it is within the time difference , Replay attacks by hackers , That won't work . have access to timestamp+nonce programme .
nonce Refers to a unique random string , Used to identify each signed request . We can send every request nonce Parameters are stored in a “set aggregate ” in , Or maybe json Format is stored in a database or cache . Each processing HTTP When asked , First of all, judge the nonce Whether the parameter is in the “ aggregate ” in , If there is an illegal request .
However, for servers , Keep forever nonce The price is very high . Can combine timestamp To optimize . because timstamp Parameter for more than 3min Request , It's considered illegal to ask , So we just need to store 3min Of nonce Parametric “ aggregate ” that will do .
If users are real users , He maliciously calls the interface frequently , Want to bring down your system ? In this case, it is necessary to access current limiting .
There are token bucket and leaky bucket algorithms in common use . You can read my article , For the interview : Explanation of classical current limiting algorithm
have access to Guava Of RateLimiter Stand alone current limiting , You can also use Redis Distributed current limitation , You can also use Alibaba open source components sentinel Current limiting . for instance , How many requests can you accept in a minute .
If malicious requests from real users are found , You can set up a blacklist mechanism , Black the user . General situation , There will be some competitors , Or users who are not bad intentions , Want to do your system . therefore , In order to ensure safety , Generally, our business system , There needs to be a blacklist mechanism . For blacklist initiated requests , Just return the error code directly .
8. White list mechanismWith the blacklist mechanism , You can also set up a white name single machine system . The enterprise transfer system I used to be responsible for , If an outside merchant wants to access our system , You need to apply for the online white list in advance . At that time, O & M will apply for IP Internet white list , Only the requests in the white list , To access our transfer system .
9. Data desensitization maskFor passwords , Or cell phone number 、 Sensitive information such as ID card , Generally, desensitization mask is required to display , If it's a password , It also needs to be encrypted and saved to the database .
For mobile phone numbers 、 ID card information , Daily development , When checking logs , What you see should be masked . The purpose is to try not to disclose these user information , Although only development and operation and maintenance can read the log , But it still needs to be prevented , Do masking .
Save the password to the database , We definitely can't directly save in plaintext . The simplest also needs MD5 Deal with it and save it ,Spring Security Medium BCryptPasswordEncoder It's fine too , Its bottom layer is SHA-256 + Random salt + The key encrypts the password , and SHA and MD The series is the same , All are hash Algorithm of abstract class .
Security assurance of interface data , We also need our system , There is a data validity check , Simply put, it is parameter verification , For example, the length of ID card , Length of mobile phone number , Is it a number, etc .
The above is the interface data security guarantee 10 Details of these methods , For more information about interface data security, please pay attention to other relevant articles on software development network !
边栏推荐
- 太方便了,钉钉上就可完成代码发布审批啦!
- 22. (ArcGIS API for JS) ArcGIS API for JS Circle Collection (sketchviewmodel)
- 我的勇敢对线之路--详细阐述,浏览器输入URL发生了什么
- .net中 接口可以有默认实现了
- Stored procedures and functions (MySQL)
- 注意力机制原理
- 22.(arcgis api for js篇)arcgis api for js圆采集(SketchViewModel)
- 23.(arcgis api for js篇)arcgis api for js椭圆采集(SketchViewModel)
- 【安全攻防】序列化與反序列,你了解多少?
- Open3d mesh filtering
猜你喜欢

Create applet from 0
枚举通用接口&枚举使用规范
Set WiFi automatic connection for raspberry pie

24. (ArcGIS API for JS) ArcGIS API for JS point modification point editing (sketchviewmodel)
Construction of Hisilicon universal platform: color space conversion YUV2RGB

哈夫曼树基本概念
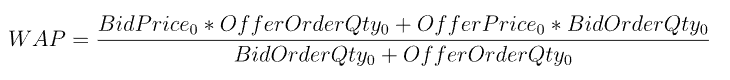
复杂因子计算优化案例:深度不平衡、买卖压力指标、波动率计算
QT 打开文件 使用 QFileDialog 获取文件名称、内容等
Kalman filter-1

A 股指数成分数据 API 数据接口
随机推荐
Graphical tools package yolov5 and generate executable files exe
Mathematical induction and recursion
R数据分析:cox模型如何做预测,高分文章复现
注意力机制原理
Experience design details
QT 项目 表格新建列名称设置 需求练习(找数组消失的数字、最大值)
Flutter3.0, the applet is not only run across mobile applications
接口数据安全保证的10种方式
1200.Minimum Absolute Difference
密码学系列之:在线证书状态协议OCSP详解
PHP lightweight Movie Video Search Player source code
23. (ArcGIS API for JS) ArcGIS API for JS ellipse collection (sketchviewmodel)
VHDL实现任意大小矩阵加法运算
Probability formula
Variables, process control and cursors (MySQL)
Vernacular high concurrency (2)
Ubuntu20 installation redisjson record
PIP download only, not install
Sub pixel corner detection opencv cornersubpix
Tencent cloud native database tdsql-c was selected into the cloud native product catalog of the Academy of communications and communications