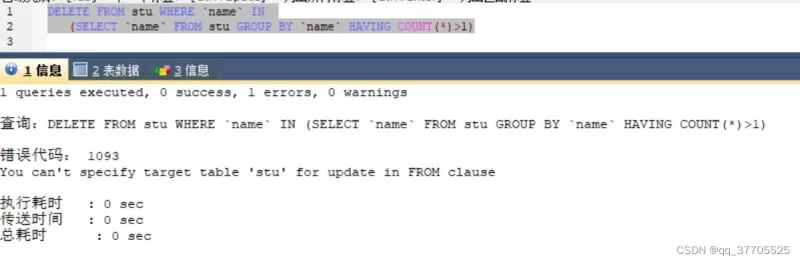
当前位置:网站首页>Humi analysis: the integrated application of industrial Internet identity analysis and enterprise information system
Humi analysis: the integrated application of industrial Internet identity analysis and enterprise information system
2022-07-05 17:29:00 【yansunxer】
Industrial Internet as a new industrial ecosystem 、 Key infrastructure and new application models , Through man 、 machine 、 The overall interconnection of things , Achieve total elements 、 Whole industry chain 、 Full connection of the whole value chain , We will accelerate the transformation and upgrading of traditional industries 、 It has strongly supported the digital transformation of the real economy 、 Accelerated the process of China's fourth industrial revolution .
Identity resolution system is one of the important infrastructure of industrial Internet , It is to realize the industrial Internet across countries 、 regional 、 industry 、 The key basic system of enterprise interconnection . There are a variety of industrial Internet identity resolution technologies in the world , Mainstream technologies include code (Handle)、 Object identifier (OID)、 Unified identification of Internet of things (Ecode) code 、 International article code (GS1) etc. . Due to the relatively late start of industrial Internet identity resolution technology in China , Lack of mature construction experience , The relevant standard system is still improving , There is an urgent need for specific application scenarios of industrial Internet 、 Complex process flow and other specific application design , Construction is safe and efficient 、 Highly available identification resolution system .
6 month 21 Japan , Regional finals of the first China Industrial Internet logo innovation and application competition ( Western Division ) Successfully held in Chongqing . At the scene of the final , Suddenly, the analysis is finished “ Identify data interaction middleware and resource pool ”、“ Chain ” Take the initiative to mark the project work display and on-site defense , The characteristics of the project are elaborated within the specified time 、 Technical advantages, business scenarios and other information .
This project will build identification data interaction middleware and resource pool Services , Provide multi-source data collection 、 Heterogeneous data cleaning and transformation 、 Master data standardization 、 Cross platform information interaction and other service capabilities , Realize the integration and sharing of data resources under different network protocol hardware and operating systems , Realize the storage of identification data 、 Access and query 、 Identification data processing 、 Standardization of heterogeneous data , Promote the integration and application of industrial Internet identity analysis and industrial enterprise information system , Greatly improve the management and application capabilities of identification data . Achieve total elements 、 Whole industry chain 、 Full connection of the whole value chain , Promote the formation of a new manufacturing and service system , Optimize the allocation efficiency of resource elements , Give full play to manufacturing equipment 、 The potential of technology and materials , Improve the production efficiency of enterprises , Create differentiated products and provide value-added services .
Active identity can actively initiate a connection to the identity resolution platform , Be able to actively read data , To solve the problem that passive identification needs reading equipment and is easy to be read and tampered . Rapid docking identification analysis system , Reduce R & D investment . Reduce the difficulty of industrial internet terminal access identification system , Realize low-cost equipment access . It can enrich the application scenarios of identification , Eliminate basic business and identification data barriers , Realize the deep integration of logo and business . With the help of the safety features of active identification , Build a complete and trusted data chain from device to identity management service from bottom to top . Ensure the safety of industrial data collection , Realize identity authentication based on identity 、 Data encryption 、 Access control and other purposes .
边栏推荐
- 中国银河证券开户安全吗 开户后多久能买股票
- 漫画:如何实现大整数相乘?(整合版)
- 独立开发,不失为程序员的一条出路
- Debug kernel code through proc interface
- easyNmon使用汇总
- ICML 2022 | meta proposes a robust multi-objective Bayesian optimization method to effectively deal with input noise
- C#实现水晶报表绑定数据并实现打印3-二维码条形码
- 【二叉树】根到叶路径上的不足节点
- [7.7 live broadcast preview] the lecturer of "typical architecture of SaaS cloud native applications" teaches you to easily build cloud native SaaS applications. Once the problem is solved, Huawei's s
- Embedded-c Language-5
猜你喜欢
随机推荐
Using C language to realize palindrome number
普通程序员看代码,顶级程序员看趋势
机器学习02:模型评估
WebApp开发-Google官方教程
Cartoon: a bloody case caused by a math problem
Learn about MySQL transaction isolation level
Is it safe to open futures accounts online? Will there be more liars online? Doesn't feel very reliable?
EasyX second lesson
Three traversal methods of binary tree
Machine learning 02: model evaluation
漫画:寻找股票买入卖出的最佳时机
Rider set the highlighted side of the selected word, remove the warning and suggest highlighting
33:第三章:开发通行证服务:16:使用Redis缓存用户信息;(以减轻数据库的压力)
通过proc接口调试内核代码
Winedt common shortcut key modify shortcut key latex compile button
7.Scala类
The third lesson of EasyX learning
CVPR 2022最佳学生论文:单张图像估计物体在3D空间中的位姿估计
MySQL queries the latest qualified data rows
漫画:寻找无序数组的第k大元素(修订版)