当前位置:网站首页>Simple process of penetration test
Simple process of penetration test
2022-07-05 13:54:00 【Cwxh0125】
Simple process
One . information gathering
nslookup whois
Two . Scan for leaks
namp=IP Range port 80 (iss,apache, What website )
Advanced scanning : Such as iss Loophole Scanning for website vulnerabilities
3、 ... and . Exploit
Four . Raise the right (shell Environmental Science , Desktop Environment , Highest authority ))
Manually test port number open : talent IP Address Test port
5、 ... and . Destroy the bodies
6、 ... and . leave oneself a way out
7、 ... and . Penetration test report
Practice
Open two virtual machines
win2003 The server 10.1.1.2
winxp staff 10.1.1.1
use xp attack 2003
First, two virtual machines should be able to communicate To configure IP In the same LAN
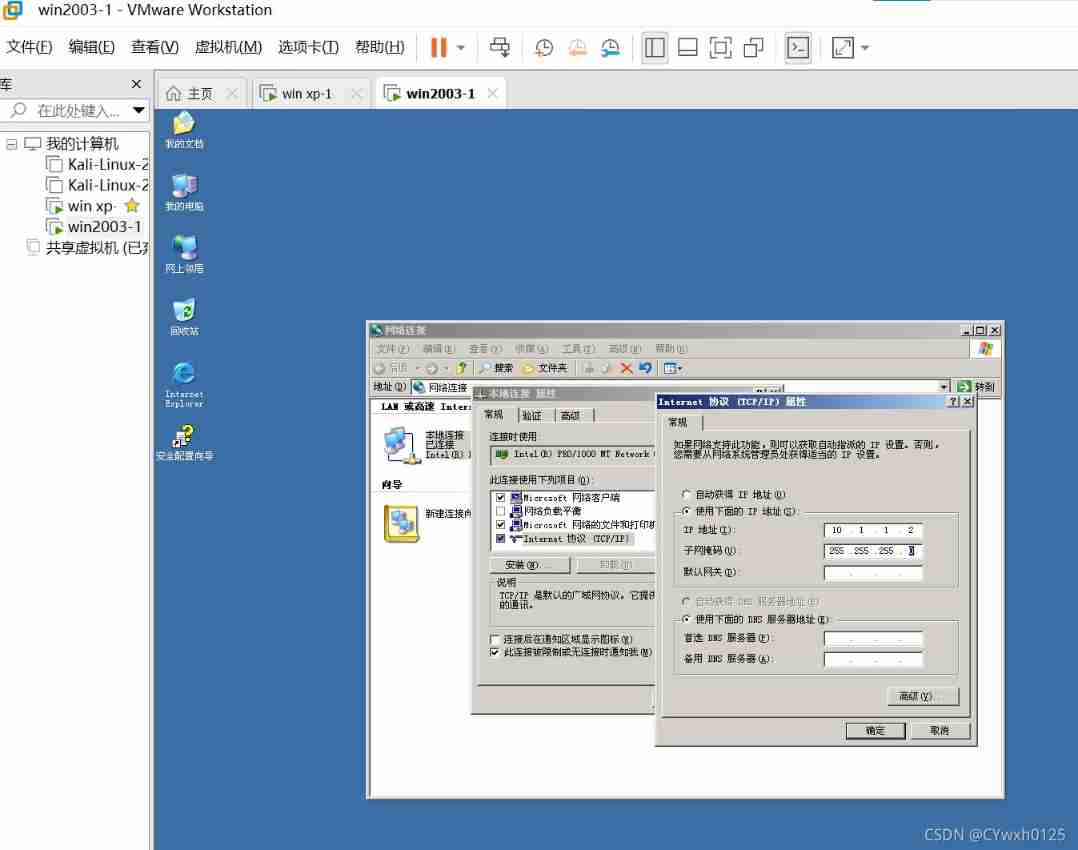
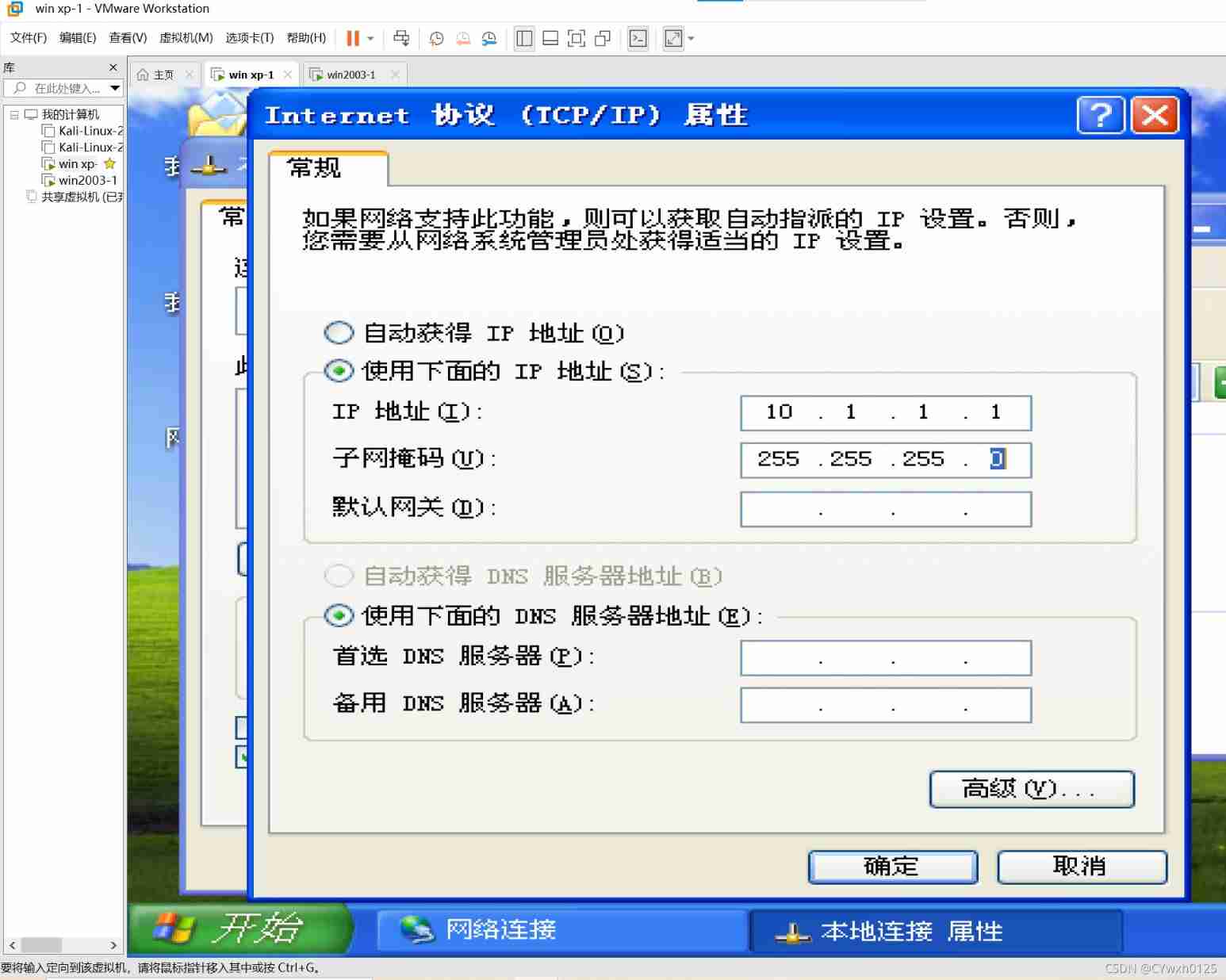
After the configuration is completed, try xp On ping once 2003 ping success
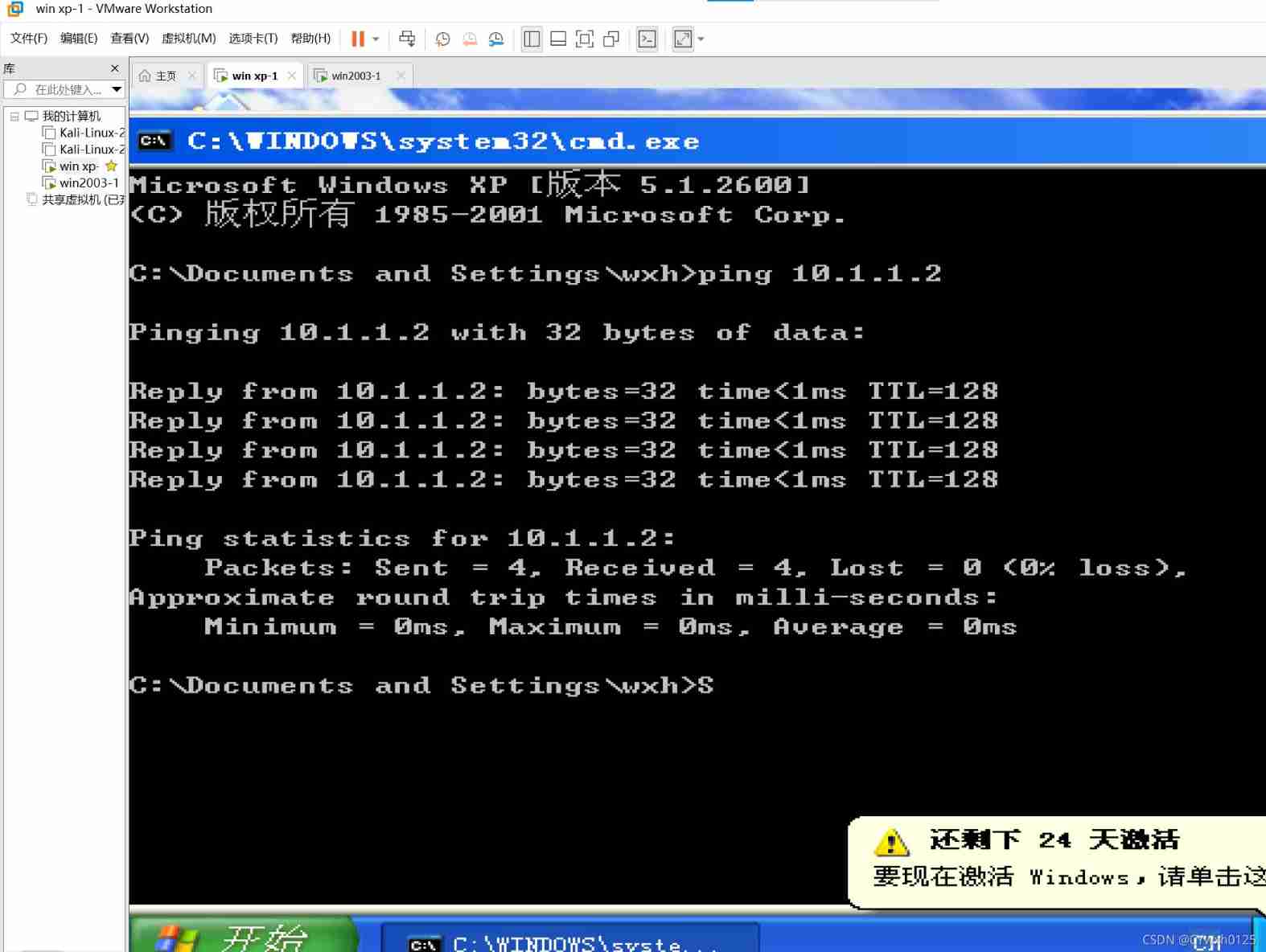
Next The attack
attack 445 attack ( Shared port )
First step : Port scanning
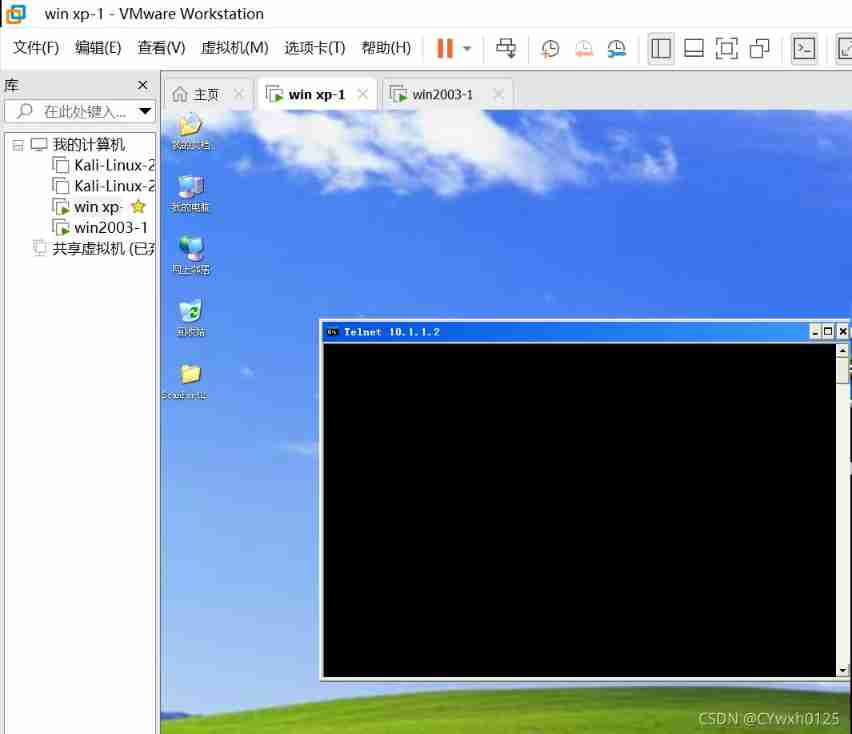
Manual scanning
telnet IP port The following situations represent that the corresponding port is open 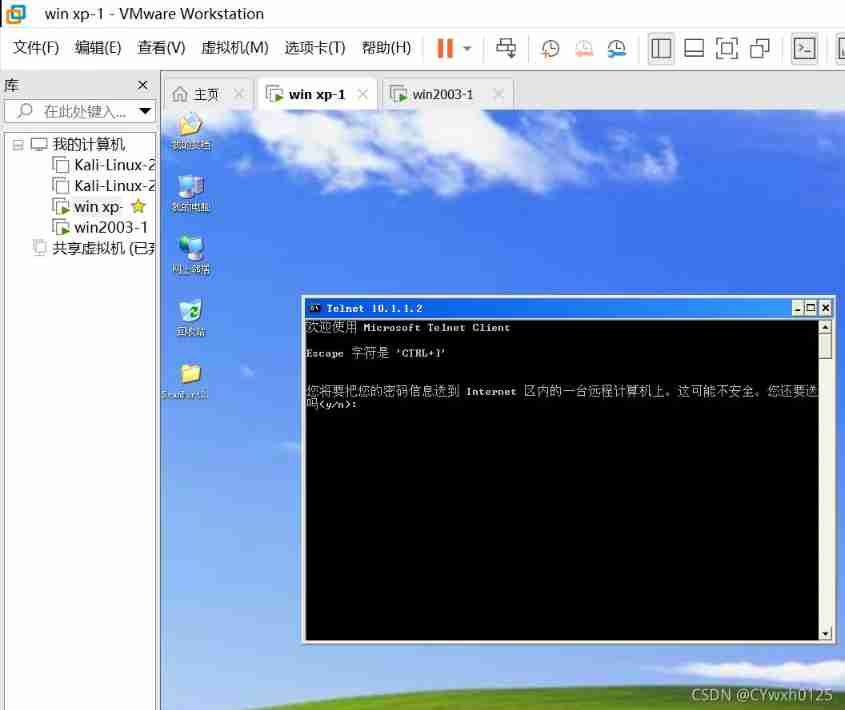
Automatic scanning Use scanport
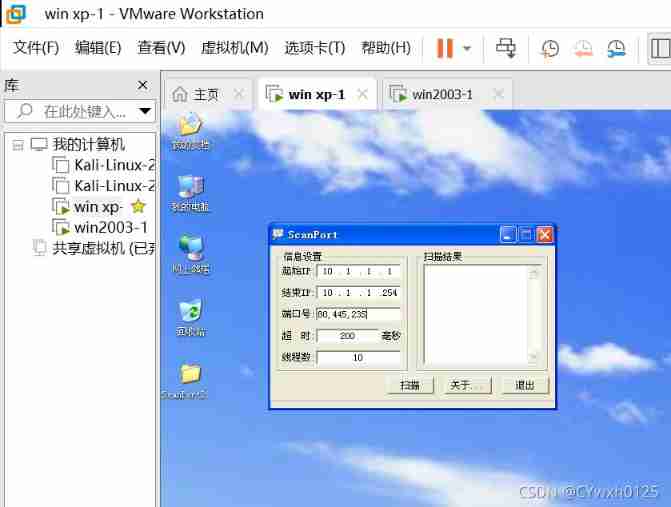
You can see xp and 2003 Both virtual machines are turned on 445 port

445 One of the exploits ipc$:
net use Used to connect your computer to shared resources ( Establish disk mapping ), Or disconnect the computer from shared resources ( Delete disk mapping ), When using this command without options , It lists the computer connections .
1) Make an empty connection :
net use \\IP\ipc$ "" /user:"" ( Be sure to pay attention to : This line of command contains 3 A space )
2) Establish a non empty connection :
net use \\IP\ipc$ " password " /user:" user name " ( There are also 3 A space )
3) Map default share :
net use z: \\IP\c$ " password " /user:" user name " ( You can put the other party's c The disk maps to its own z disc , And so on )
If you've established a goal ipc$, You can use IP+ Disk character +$ visit , Specific commands net use z: \\IP\c$
4) Delete one ipc$ Connect
net use \\IP\ipc$ /del
5) Delete shared mapping
net use c: /del Delete mapped c disc , And so on
net use * /del Delete all , There will be a prompt to press y confirm
3 View the shared resources of the remote host ( But you don't see the default share )
net view \\IP
Brutally crack the system password 445
Using tools ntscan
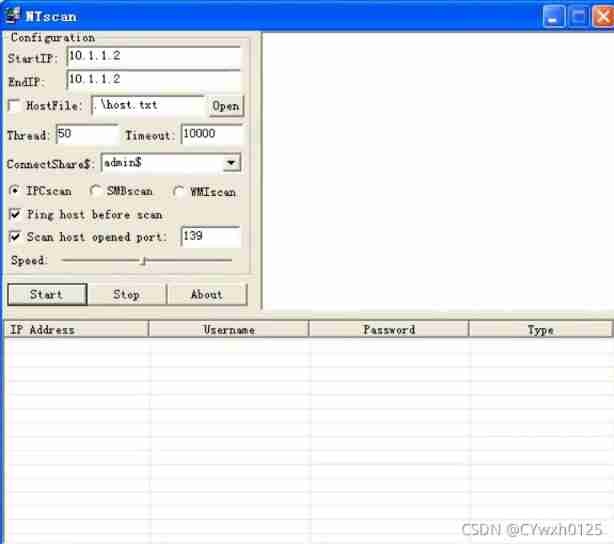
take user And the password burst out You can go through net use \\IP\ipc$ " password " /user:" user name " To make a connection
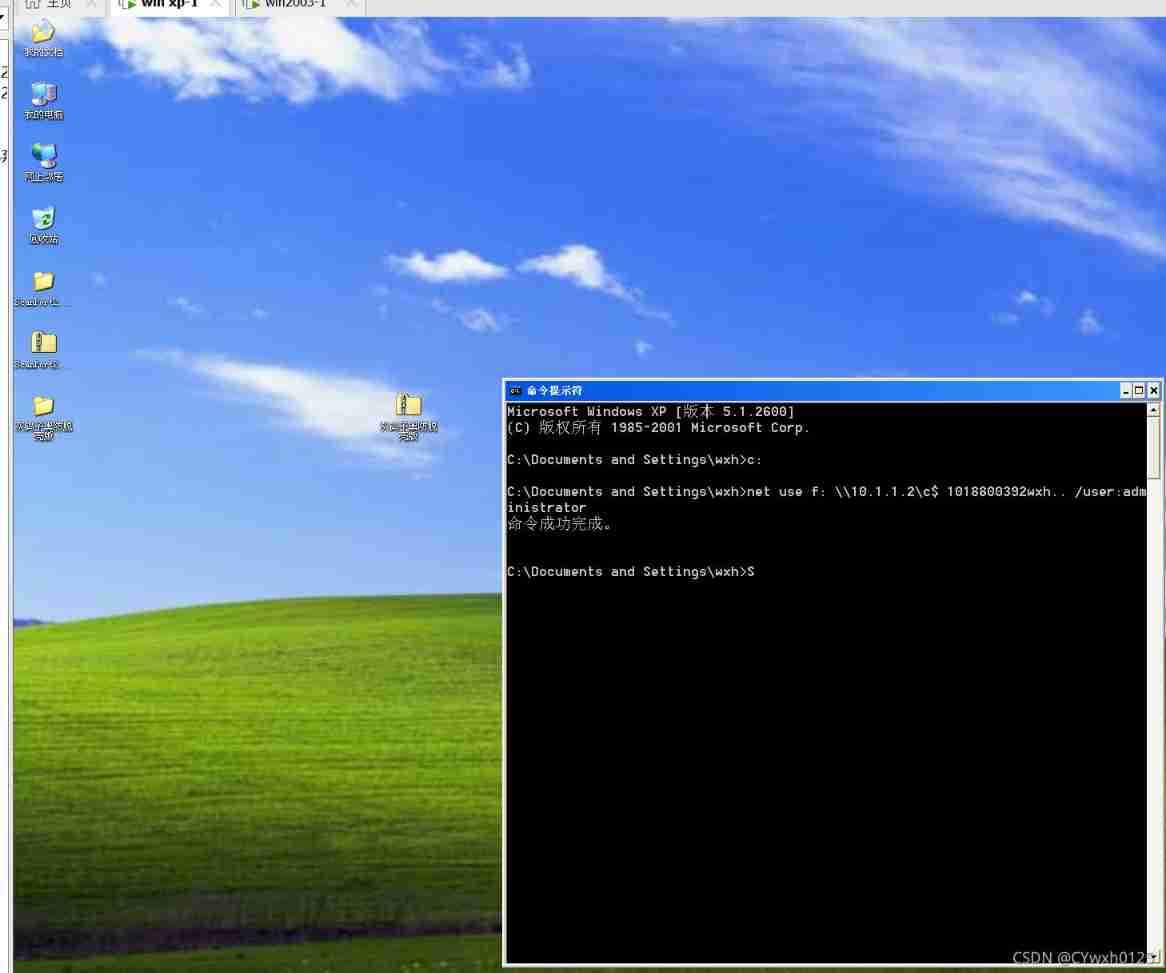
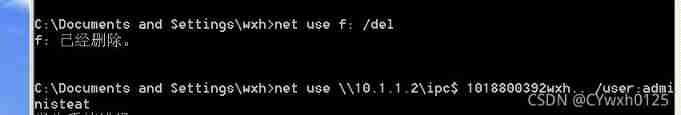
After successful connection, the back door can be left
Make a Trojan
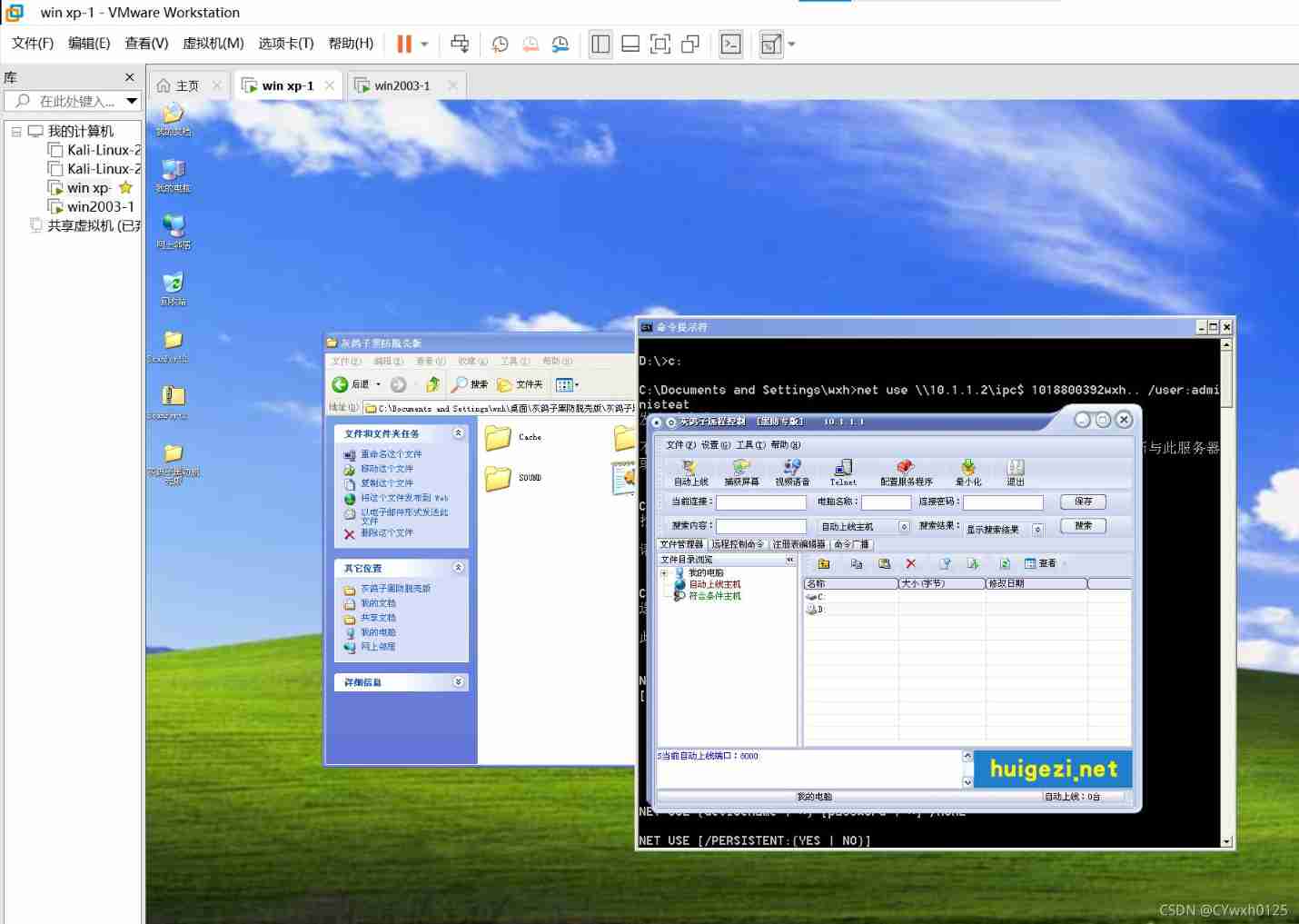
copy Implant Trojans
边栏推荐
- Kotlin协程利用CoroutineContext实现网络请求失败后重试逻辑
- How to apply the updated fluent 3.0 to applet development
- web3.eth. Filter related
- How to deal with the Yellow Icon during the installation of wampserver
- 【云资源】云资源安全管理用什么软件好?为什么?
- laravel-dompdf导出pdf,中文乱码问题解决
- Catch all asynchronous artifact completable future
- matlab学习2022.7.4
- PHP character capture notes 2020-09-14
- MySQL if else use case use
猜你喜欢

Summit review | baowanda - an integrated data security protection system driven by compliance and security

荐号 | 有趣的人都在看什么?

【华南理工大学】考研初试复试资料分享
![[js] basic syntax - for loop](/img/7f/6ddc47c062caa7d39538f88e12b1a0.jpg)
[js] basic syntax - for loop

Catch all asynchronous artifact completable future

【公开课预告】:视频质量评价基础与实践
Win10 - lightweight gadget
![UE source code reading [1]--- starting with problems delayed rendering in UE](/img/fa/f33242b01e4da973fa36c2c6f23db6.png)
UE source code reading [1]--- starting with problems delayed rendering in UE
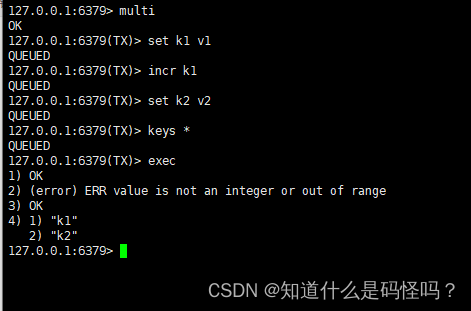
redis6事务和锁机制
zabbix 监控
随机推荐
ETCD数据库源码分析——rawnode简单封装
搭建一个仪式感点满的网站,并内网穿透发布到公网 2/2
Liar report query collection network PHP source code
About the problem and solution of 403 error in wampserver
MySQL if else use case use
Attack and defense world web WP
Summit review | baowanda - an integrated data security protection system driven by compliance and security
Routing in laravel framework
瑞能实业IPO被终止:年营收4.47亿 曾拟募资3.76亿
Solve the problem of "unable to open source file" xx.h "in the custom header file on vs from the source
Can graduate students not learn English? As long as the score of postgraduate entrance examination English or CET-6 is high!
aspx 简单的用户登录
ELFK部署
Brief introduction to revolutionary neural networks
Redis6 master-slave replication and clustering
面试官灵魂拷问:为什么代码规范要求 SQL 语句不要过多的 join?
Controller in laravel framework
2022建筑焊工(建筑特殊工种)特种作业证考试题库及在线模拟考试
如何把大的‘tar‘存档文件分割成特定大小的多个文件
Multi person cooperation project to see how many lines of code each person has written