当前位置:网站首页>Candy delivery (Mathematics)
Candy delivery (Mathematics)
2022-07-06 16:08:00 【AC__ dream】
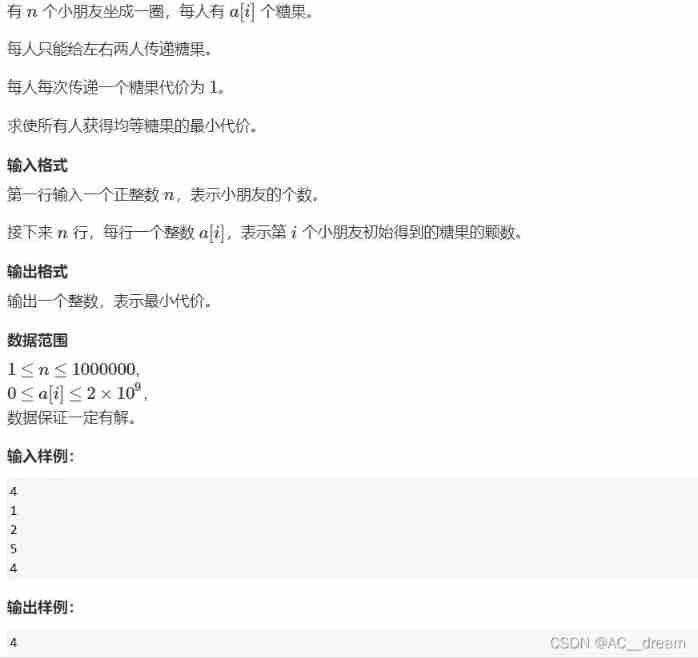
This problem is essentially a mathematical problem , Presuppose xi In the best case i A child gave it to No i-1 The number of sweets for a child (xi A negative number means the i-1 A child gave the first i A child candy ), A special case : When i by 1 when , Default i-1=n, That is to say x1 It means the first one 1 A child gave it to No n The number of sweets for a child . Then our The result is all xi The sum of the absolute values of ( The number of candy delivered is the final price ), The title has given the number of sweets each child had at the beginning ai, Let the number of sweets each child finally gets be mid, So the first i The final number of sweets for children mid Depends on the number of sweets you have at the beginning ai And he gave No i-1 The number of sweets for a child xi And the first i+1 A child gave him the number of sweets xi+1, That is to say mid=ai-xi+x(i+1), Simplify to x(i+1)-xi=mid-ai, From this formula, we can get
(1) x2-x1=mid-a1
(2) x3-x2=mid-a2
……
(n-1) xn-x(n-1)=mid-a(n-1)
Combining the above formulas, we get
(1)+(2) have to x3-x1=2*mid-(a2+a1)
(1)+(2)+(3) have to x4-x1=3*mid-(a3+a2+a1)
……
(1)+(2)+……+(n-1) have to xn-x1=(n-1)*mid-(a(n-1)+a(n-2)+……+a1)
Move the terms of the merged formula to get :
x2=x1-(a1-mid)
x3=x1-((a2+a1)-2*mid)
x4=x1-((a3+a2+a1)-3*mid)
……
xn=x1-((a(n-1)+……+a2+a1)-(n-1)*mid)
Again because x1=x1-0
Our final result is xi The sum of the absolute values of , It's easy to think of the distance formula when you see the formula after the term shift above , So our result is One point to 0,(a1-mid),((a2+a1)-2*mid),……,((a(n-1)+……+a2+a1)-(n-1)*mid) The minimum value of the sum of the distances of these points , This can be transformed into the problem of warehouse location , Directly take a median for calculation , Here is the code :
#include<cstdio>
#include<iostream>
#include<cstring>
#include<vector>
#include<algorithm>
#include<map>
#include<cmath>
#include<queue>
using namespace std;
const int N=1000003;
long long a[N],s[N];
int main()
{
int n;
cin>>n;
for(int i=1;i<=n;i++)
{
scanf("%lld",&a[i]);
s[i]=s[i-1]+a[i];
}
long long mid=s[n]/n;
for(int i=1;i<=n;i++)
s[i]-=i*mid;
sort(s,s+n);
long long ans=0;
for(int i=0;i<n;i++)
ans+=abs(s[i]-s[n/2]);
printf("%lld",ans);
return 0;
}边栏推荐
- [exercise-6] (UVA 725) division = = violence
- E. Breaking the Wall
- [exercise-7] (UVA 10976) fractions again?! (fraction split)
- 渗透测试 ( 2 ) --- 渗透测试系统、靶机、GoogleHacking、kali工具
- JS call camera
- Information security - Analysis of security orchestration automation and response (soar) technology
- Penetration test (2) -- penetration test system, target, GoogleHacking, Kali tool
- 【高老师软件需求分析】20级云班课习题答案合集
- 605. Planting flowers
- 想应聘程序员,您的简历就该这样写【精华总结】
猜你喜欢
【练习-4】(Uva 11988)Broken Keyboard(破损的键盘) ==(链表)
渗透测试 ( 5 ) --- 扫描之王 nmap、渗透测试工具实战技巧合集

1689. Ten - the minimum number of binary numbers
B - 代码派对(女生赛)

Penetration test (2) -- penetration test system, target, GoogleHacking, Kali tool

1005. Maximized array sum after K negations
7-1 懂的都懂 (20 分)
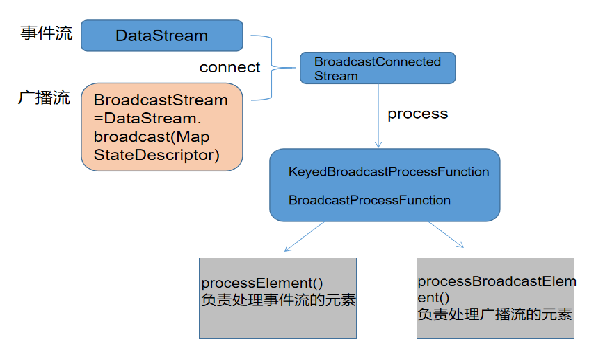
信息安全-威胁检测-flink广播流BroadcastState双流合并应用在过滤安全日志

7-1 understand everything (20 points)

1013. Divide the array into three parts equal to and
随机推荐
Essai de pénétration (1) - - outils nécessaires, navigation
Penetration test (7) -- vulnerability scanning tool Nessus
Gartner:关于零信任网络访问最佳实践的五个建议
Luogu P1102 A-B number pair (dichotomy, map, double pointer)
Research Report on market supply and demand and strategy of China's earth drilling industry
Matlab comprehensive exercise: application in signal and system
渗透测试 ( 7 ) --- 漏洞扫描工具 Nessus
Penetration test (1) -- necessary tools, navigation
渗透测试 ( 8 ) --- Burp Suite Pro 官方文档
Hdu-6025-prime sequence (girls' competition)
Opencv learning log 32 edge extraction
渗透测试 ( 5 ) --- 扫描之王 nmap、渗透测试工具实战技巧合集
Research Report of exterior wall insulation system (ewis) industry - market status analysis and development prospect prediction
Differential (one-dimensional, two-dimensional, three-dimensional) Blue Bridge Cup three body attack
1013. Divide the array into three parts equal to and
Opencv learning log 28 -- detect the red cup cover
Interesting drink
Opencv learning log 26 -- detect circular holes and mark them
Quick to typescript Guide
信息安全-威胁检测引擎-常见规则引擎底座性能比较