当前位置:网站首页>Software testing knowledge reserve: how much do you know about the basic knowledge of "login security"?
Software testing knowledge reserve: how much do you know about the basic knowledge of "login security"?
2022-07-07 06:14:00 【Software testing Fairy】
As a test , Give us a keyword “ Sign in ”, We may think of more user names for use case design 、 Whether the password verification is legal 、 Is it empty 、 Whether it is correct, and so on .

But in today's information age ,“ Login security ” It has been a very popular and common topic , Today, I would like to share with you my personal knowledge about 「 Login security 」 Basic knowledge of .
Concept popularization
Before understanding login security , Let's popularize two basic concepts :“ Storehouse ” and “ Crash Bay ”.
Baidu to the original introduction is :“ Hit the database is a hacker through the collection of Internet users and password information that has been leaked , Generate corresponding dictionary table , After trying to log in other websites in batch , Get a list of users who can log in . And many users use the same account password on different websites , Therefore, hackers can obtain the user's A Website account to try to login B website , This can be interpreted as a collision attack .”
From another angle, you can understand this , Many users' accounts and passwords are aggregated , Formed a “ library ”, Many criminals steal the user's account information , I will try my best to get the real account information of users through various means . This “ Keep trying to get ” Action process of , We can call it “ Collision ”.
There are criminals “ Collision ”, Of course, there are official envoys “ prevent ”, To improve the security of user account information , The programmer ( Just messenger ) When designing login, we will protect the user's account information security layer by layer through a series of means .
Common login security problems
Here, let's popularize the common scenarios that can be determined that the account may be stolen :
1、 The same code & Different accounts , There are many errors ;
2、 Same account number & Different passwords , There are many errors ;
3、 Get SMS verification code frequently .
The above scenarios have two commonalities , Namely “ In a short period of time ” and“ Same device ”, Because hackers or other criminals , When constantly trying to obtain user account and password information, it is basically to try different account and password combinations on the same device in a short time .
Solution
Based on the commonness of the above common login security problems (“ In a short period of time ” and“ Same device ”), There is a corresponding and clear solution :
1、 adopt IP Limit the upper limit of SMS requests for the same user ;
2、 adopt IP Limit the maximum number of password errors for the same user ;
3、 Limit the upper limit of password error of the same user through the account .
Test case design
As a professional tester , Before designing use cases , Besides attention UI Design draft 、 Outside the requirements document , You can also pay attention to the technical documents provided by the development , If conditions permit, we can further understand the corresponding basic implementation principle of development , To some extent, it can help us improve the coverage of our designed test cases , So that we can be more comprehensive 、 More in-depth testing , So as to improve the quality of our products .
From the technical documents developed, we don't need to understand deep technical principles , Just understand the following questions :
1、 How to control login risk ?
2、 After the user's login behavior is judged as a risk , What corresponding measures will be taken ?
3、 After the user's login behavior is judged as a risk , What can be reused ?
4、 Is there any way to appeal ?
Finally, according to the above idea, you can supplement the corresponding functional test cases , Here is a brief list of some test cases :

in addition , While supplementing business test cases , Synchronization can focus on the corresponding interface request specification , In order to get the truth of users as much as possible IP, Interfaces may refer to HTTP Request header specification , Require downstream to transmit through when requesting X_FORWARDED_FOR, To distinguish real users IP.
This can be used as an interface testing concern , Reduce due to IP Risk misjudgment caused by reporting errors , Causes normal users to be unable to use product functions normally .
from HTTP Get the user's authenticity in the request IP There are two ways to address , One is from Remote Address gain , The other is from X-Forward-For gain , But their security and usage scenarios are different , If you want to know more knowledge, you can expand it by yourself according to keywords ~
Learn a little every day , Sooner or later, you can change from a rookie to a big man ~
Last :
You can go to my personal number :atstudy-js, You can get one for free 10G Software Test Engineer interview classic documents . And the corresponding video learning tutorial is free to share ! It includes basic knowledge 、Linux necessary 、Mysql database 、 Caught tools 、 Interface testing tool 、 Test advanced -Python Programming 、Web automated testing 、APP automated testing 、 Interface automation testing 、 Testing advanced continuous integration 、 Test architecture development test framework 、 Performance test, etc .
These test data , For doing 【 software test 】 For our friends, it should be the most comprehensive and complete war preparation warehouse , This warehouse also accompanied me through the most difficult journey , I hope it can help you !
边栏推荐
- JVM监控及诊断工具-命令行篇
- Introduction to the extension implementation of SAP Spartacus checkout process
- Rk3399 platform development series explanation (WiFi) 5.52. Introduction to WiFi framework composition
- Jstat of JVM command: View JVM statistics
- [daily training -- Tencent selected 50] 292 Nim games
- PTA ladder game exercise set l2-004 search tree judgment
- Introduction to yarn (one article is enough)
- PTA 天梯赛练习题集 L2-004 搜索树判断
- How to improve website weight
- Loss function and positive and negative sample allocation in target detection: retinanet and focal loss
猜你喜欢
Dc-7 target
3428. Put apples
【GNN】图解GNN: A gentle introduction(含视频)
yarn入门(一篇就够了)
JVM命令之 jstat:查看JVM統計信息

A very good JVM interview question article (74 questions and answers)
Bypass open_ basedir
深度聚类:将深度表示学习和聚类联合优化
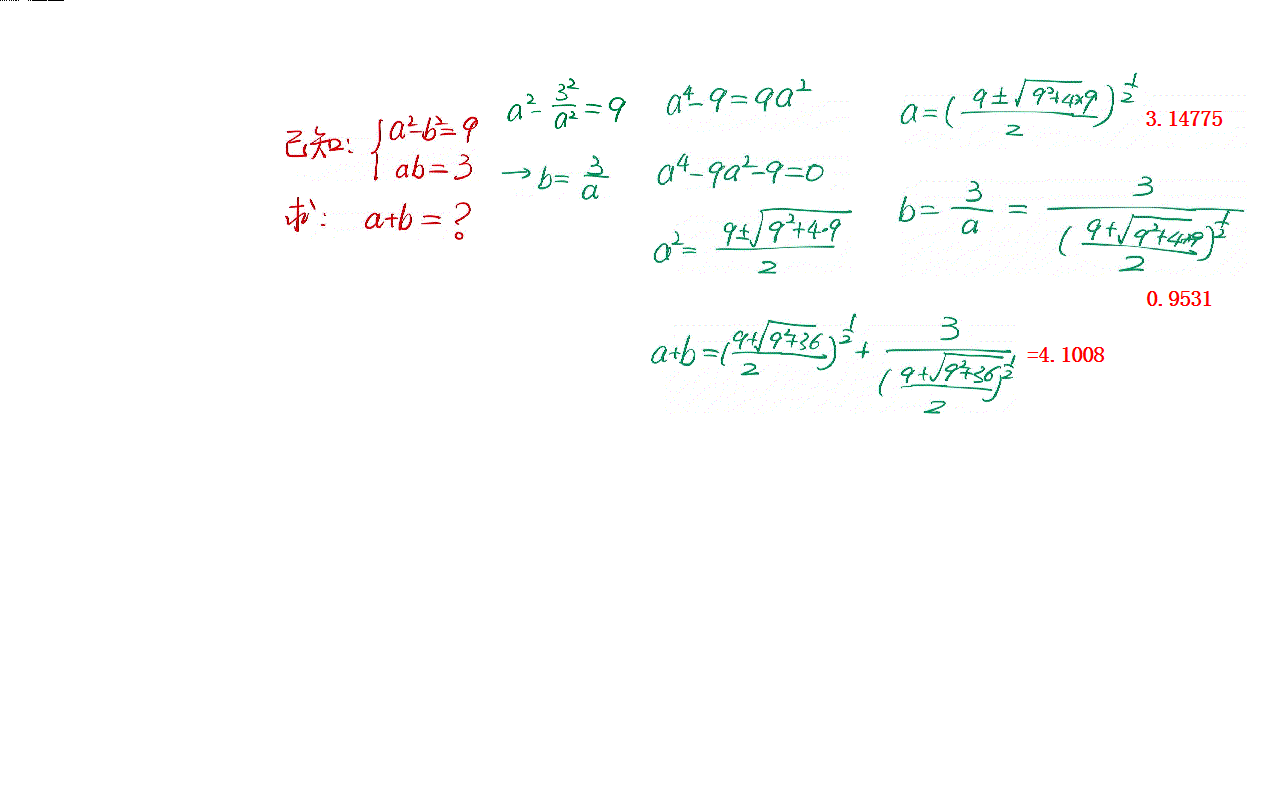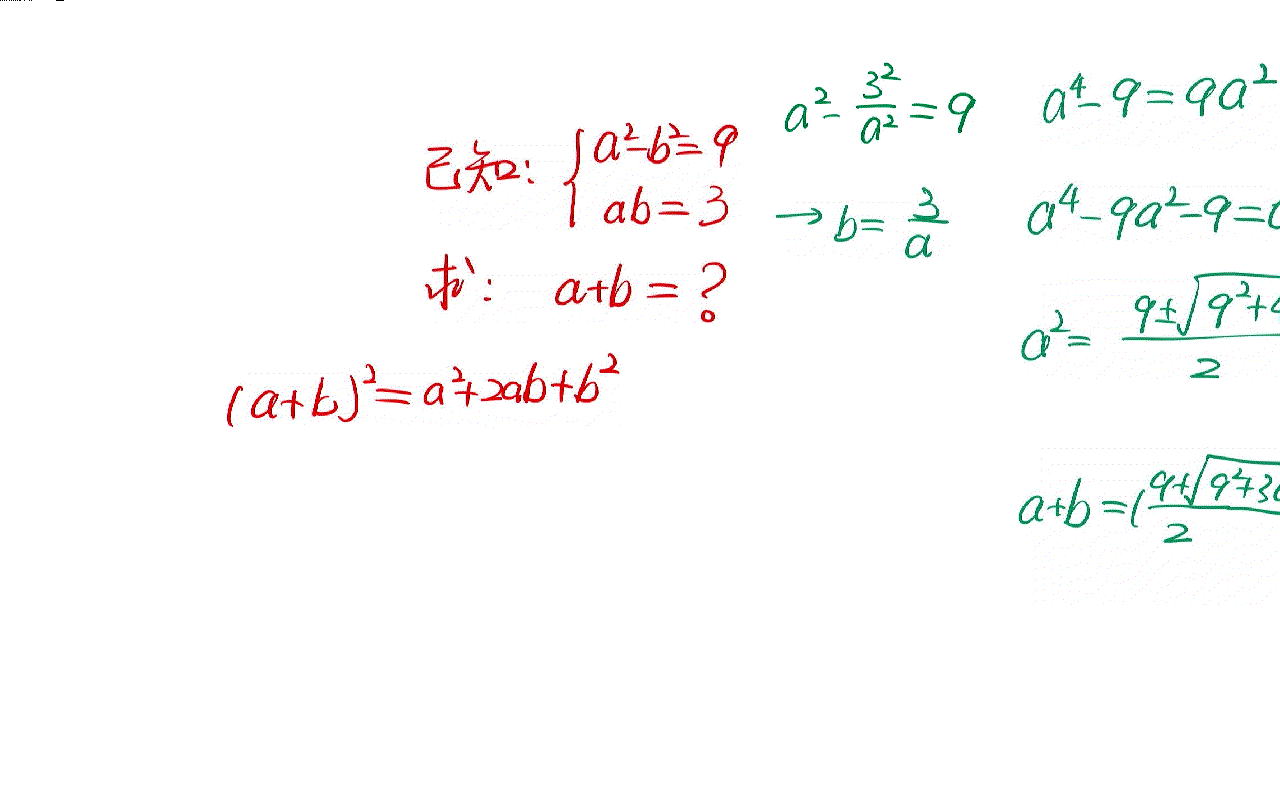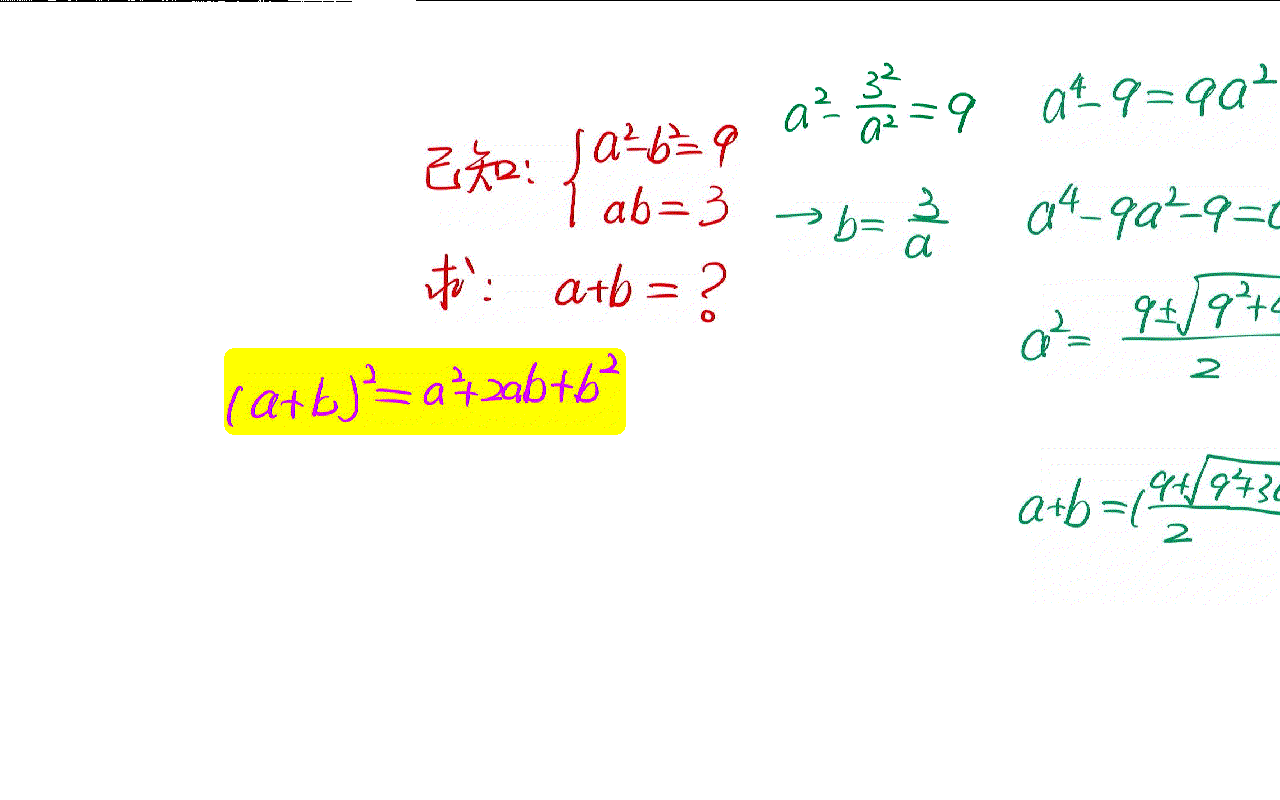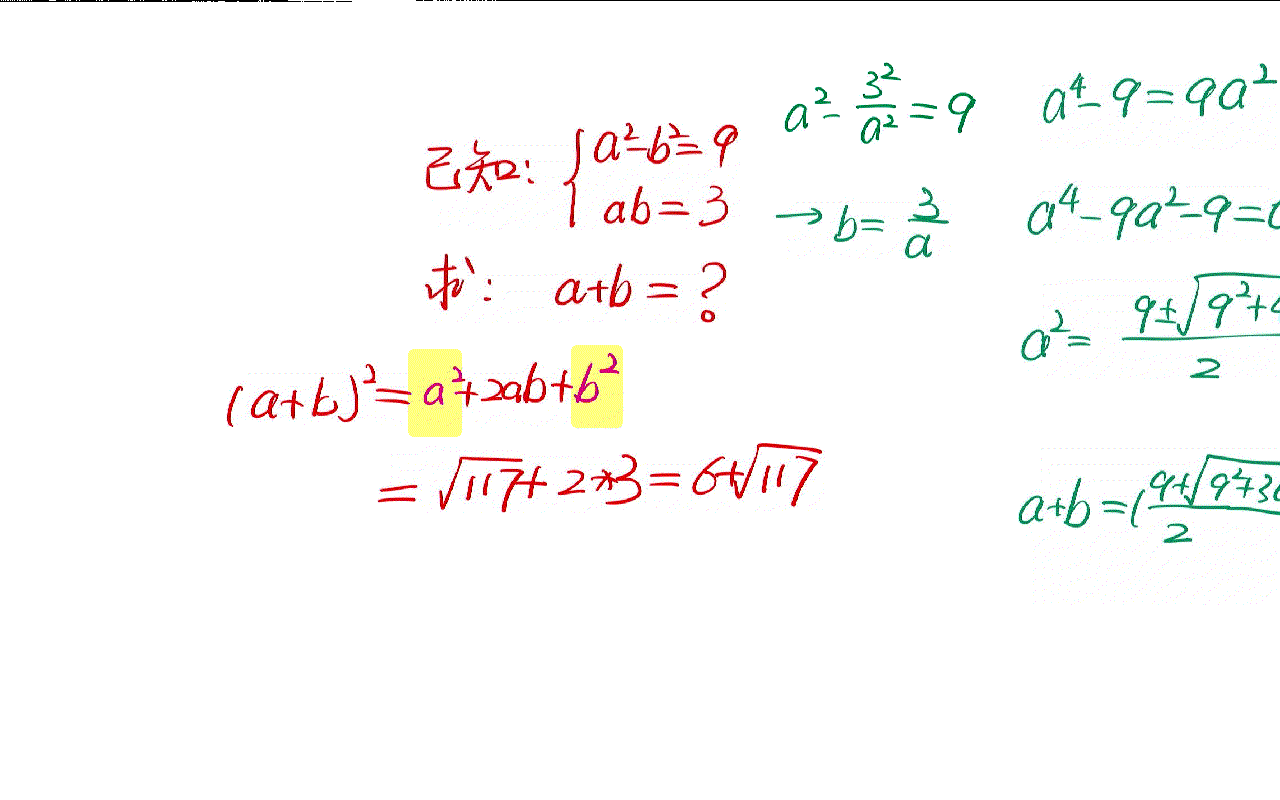
The solution of a simple algebraic problem
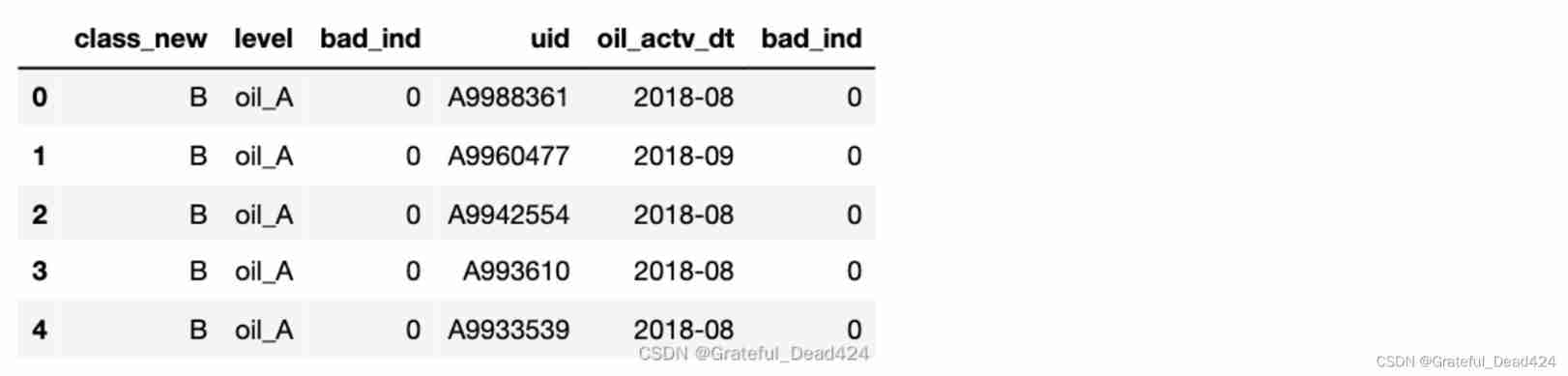
Financial risk control practice - decision tree rule mining template
随机推荐
【SQL实战】一条SQL统计全国各地疫情分布情况
Jcmd of JVM command: multifunctional command line
搞懂fastjson 对泛型的反序列化原理
Subghz, lorawan, Nb IOT, Internet of things
每秒10W次分词搜索,产品经理又提了一个需求!!!(收藏)
jmeter 函数助手 — — 随机值、随机字符串、 固定值随机提取
【FPGA教程案例14】基于vivado核的FIR滤波器设计与实现
C. colonne Swapping [tri + Simulation]
改变ui组件原有样式
Laravel uses Tencent cloud cos5 full tutorial
[InstallShield] Introduction
A very good JVM interview question article (74 questions and answers)
QT console output in GUI applications- Console output in a Qt GUI app?
Convert numbers to string strings (to_string()) convert strings to int sharp tools stoi();
计算模型 FPS
[daily training -- Tencent selected 50] 292 Nim games
Value range of various datetimes in SQL Server 2008
如何在Touch Designer 2022版中设置解决Leap Motion不识别的问题?
3428. Put apples
【FPGA教程案例13】基于vivado核的CIC滤波器设计与实现