当前位置:网站首页>Common DOS commands
Common DOS commands
2022-07-06 12:15:00 【Boy ~ no talent】
dir: List the current list file (directory)
md: Create directory (make directory)
rd: Delete directory (remove directory)
cd: Change the current path (change directory)
cd…:
cd\: Go back to the root
del: Delete file
copy: Copy file
ren: rename (rename)
type: According to the content
format: format
exit: sign out dos Command line
DOS Commands are not case sensitive , such as C Discoid Program Files, stay dos Commands can be used "program files" Instead of , English quotation marks are added because there is a space in the middle of the name ( That is, more than one word ), This point is often ignored by beginners .
Common commands :
(1) View directory contents command DIR
(2) Specify the executable search directory PATH
(3) Create directory command MD
(4) Open the specified directory command CD
(5) Delete the currently specified subdirectory command RD
(6) Change the current drive letter command C:
(7) File copy command COPY
(8) Display text file content command TYPE
(9) Change file name command REN
(10) Delete file command DEL
(11) Clear screen command CLS
DOS Command special command
Repeat the last command you entered , have access to F3 Key to complete , meanwhile DOS There is a doskey Command recorder for , Execute... On the command line doskey After that, the following functions can be realized :
1、 up arrow "↑" And the down arrow "↓"----- Looking back at the last command executed
2、“Ctrl+C” Key combination or "Break" key ----- Interrupt operation
3、 The mouse operation " Mark " ----------------- Used to select text
4、 The mouse operation " Paste " ----------------- Used to paste the contents of the clipboard to the prompt
5、"F7" key -------------------------- View and execute used commands
6、"/?" ---------------------------- Specify command help
7、">" And ">>" ---------------------- File redirection
Parameters : command + > + Write path \ file name
example :
echo Welcome to Baidu >d:\1.txt ; Write text to the specified file ( Replace if file exists )
netstat -an >>d:\1.txt ; Write text following the end
DOS Order direct access to
edit
Enter a drive letter directly , Disk character :
Such as direct access to D disc ,D:
DOS Command directory command
( One )md—— Create subdirectories
1. function : Create a new subdirectory
2. type : Internal orders
3. Format :md[ Disk character :][ Pathname ]〈 Subdirectory name 〉
4. Instructions :
(1)“ Disk character ”: Specifies the letter of the disk drive to create the subdirectory , If you omit , Is the current drive ;
(2)“ Pathname ”: The parent directory name of the subdirectory to be created , If it defaults, it will be created in the current directory .
example :(1) stay c Create a file named... Under the root directory of the disk fox A subdirectory ;(2) stay fox Create a subdirectory user subdirectories .
md c:\ fox ( In the current drive c Create subdirectories under disk fox)
md c:\ fox\user ( stay fox Create a subdirectory user subdirectories )
( Two )cd—— Change the current directory
1. function : Change the current directory
3. Format :CD [/D] [drive:][path]
(1) If the path and subdirectory name are omitted, the current directory is displayed ;
(2) If “cd\” Format , Then return to the root directory ;
(3) If “cd…” The format is returned to the upper level directory .
(4) Use /D Command line switch , In addition to changing the current directory of the drive , You can also change the current drive .
example :(1) Enter into user subdirectories ;(2) from user Subdirectories go back to subdirectories ;(3) Go back to the root .
c:>cd fox\user( Get into fox Under subdirectories user subdirectories )
c:\fox\user>cd… ( Return to the upper level root directory , Be careful cd And then there are two dots "…").
c:\fox>cd\ ( Go back to the root )
c:\
( 3、 ... and )rd—— Delete subdirectory command
1. function : Delete subdirectories from the specified disk .
3. Format :rd[ Disk character :][ Pathname ][ Subdirectory name ]
(1) Subdirectory must be empty before deletion , In other words, you need to enter the subdirectory first , Use del( Command to delete files ) Delete the files in its subdirectory , Then go back to the previous Directory , use rd Command to delete the subdirectory itself ;
(2) You cannot delete the root directory and the current directory .
example : Ask for c disc fox Under subdirectories user Subdirectory delete , The operation is as follows :
First step : First the user The files in the subdirectory are deleted ;
c>del c:\fox\user*.* or del c:\fox\user or del c:\fox\user*
( notes : This can only delete files , Still cannot delete user Folder under directory )
The second step , Delete user subdirectories .
c>rd c:\fox\user
( notes : If fox\user There is still a folder under the folder , This step will not work , How to solve it ? In fact, there is no need to bother two steps , Directly c>rd c:\fox\user /s
Add a parameter /s, If you don't want the system to ask whether to delete , You can add another parameter /q).
rd(RMDIR): stay DOS Used to delete a directory in the operating system
RMDIR [/S] [/Q] [drive:]path
RD [/S] [/Q] [drive:]path
Be careful : The following two parameters can only be used in WINXP Upper use ( stay vista In fact, the following two parameters can also be used in the system !)
/S In addition to the catalog itself , All subdirectories and files under the specified directory will also be deleted . Used to delete a tree .
/Q Quiet mode , belt /S No confirmation required to delete tree .
Such as : Delete D The name on the disk is myfile( This folder is empty ) Folder , You can enter rd d:\myfile.
If myfile Non empty , You can enter rd d:\myfile /S d:\myfile Delete myfile Folder and all its subfolders and files .
( Four )dir—— Display disk directory command
DOS Command page and teaching diagram (7 Zhang )
1. function : Displays the contents of the disk directory .
3. Format :dir [ Disk character ][ route ][ file name ][/p][/w][/A[[:] attribute ]][/O[:] Arrange in order ]][/S]
4. Instructions :/p Use ; When there are too many directories to view , It cannot be displayed on one screen, and the screen will scroll up , It's not easy to see , add /p After the parameter , On the screen, it will be displayed in one face at a time 23 Line file information , Then pause , And prompt ;press any key to continue( Press any key to continue )
/w Use : add /w Show only filename , The file size and the date and time of creation are omitted . After adding the parameters , Each line can display five file names .
/A Displays the file with the specified properties .
attribute D Catalog R Read only file H Hidden files A Prepare files for filing
S System files I No content index file L Analytic point - Express “ no ” The prefix of
/O List documents in classification order .
Arrange in order N By name ( Alphabetical order ) S By size ( From small to large ) E By extension ( Alphabetical order )
D By date / Time ( From first to last ) G Group directory takes precedence - Prefix in reverse order
/S Displays the files in the specified directory and all subdirectories .
( 5、 ... and )path—— Path setting command
1. function : Search path for device executable , Only valid for documents .
3. Format :path[ Disk character 1] Catalog [ Pathname 1]{[; Disk character 2:],〈 Directory pathname 2〉…}
(1) When running an executable ,dos Will first search the current directory for the file , If found, run it ; If the file cannot be found , According to path The path set by the command , Search the directory one by one for the file ;
(2)path The path in the command , If there are more than two , The paths are separated by a semicolon “;” separate ;
(3)path There are three ways to use commands :
path[ Disk character 1:][ route 1][ Disk character 2:][ route 2]…( Set the search path for the executable ) path:( Cancel all paths )
path:( Display the currently set path )
( 6、 ... and )tree—— Display disk directory structure command
1. function : Displays all directory paths on the specified drive and all file names under these directories .
2. type : External command
3. Format :tree [ Disk character :][/f][>prn]
(1) Use /f Parameter displays all directories and all files in the directory , When omitted , Show only directories , Do not display files in the directory ;
(2) choose >prn When parameters are , Print out the listed directory and the file name in the directory .
( 7、 ... and )deltree—— Delete entire directory command
1. function : Delete the entire directory and its subordinate subdirectories and files .
3. Format :deltree [ Disk character :]〈 Pathname 〉
4. Instructions : This command can delete the directory and all the files under it in one step 、 subdirectories 、 Delete the subdirectories at the lower level , And no matter the attribute of the file is hidden 、 System or read-only , As long as the file is under the deleted directory ,deltree It's all the same , Delete as you like . Be careful when using !
( 8、 ... and )tasklist—— Show process
1. function : Show the whole process of the computer , Same as task manager .
3. Format :tasklist
4. Instructions : function cmd tasklist
DOS Command disk command
( One )format—— Disk format command
1. function : Format the disk , Divide tracks and sectors ; At the same time, check whether there are defective tracks on the whole disk , Mark the bad track ; Establish directory area and file allocation table , Make the disk ready to receive dos To prepare .
3. Format :format〈 Disk character :〉[/s][/4][/q]
(1) The drive letter after the command cannot be defaulted , If you format the hard disk , You will be prompted as follows :warning:all data on non
——removable disk
drive c:will be lost !
proceed with format (y/n)?
( Warning : All the data is in c On the disk , Will be lost , Are you sure you want to continue formatting ?{y( determine )/n( no )})
(2) If the floppy disk is formatted , You will be prompted as follows :insert new diskette for drive a;
and press enter when ready…
( stay a Insert a new disk into the drive , Press enter when you are ready ).
(3) choose [/s] Parameters , Will put dos System files io.sys、msdos.sys And command Copy to disk , Make this disk available as dos Startup disk . If not /s Parameters , Then the formatted disk can only read and write information , It cannot be used as a startup disk ;
(4) choose [/4] Parameters , stay 1.2mb High density floppy drive 360kb Low density disk ;
(5) choose [/q] Parameters , Quick format , This parameter does not redistribute the tracks and sectors of the disk , Only the disk root directory can be 、 Clear the file allocation table and boot sector to blank , therefore , Faster formatting .
(6) choose [/u] Parameters , Indicates unconditional formatting , That is, destroy all data on the original disk . No addition /u, Is a security format , At this time, first create a mirror image file to save the original fat Table and root directory , Use... If necessary unformat Restore the original data .
( Two )unformat Redo format command
1. function : Recover the disk that lost data due to format error operation .
3. Format :unformat〈 Disk character 〉[/l][/u][/p][/test]
4. Instructions : Used to be “ Non destructive ” Formatted disk recovery . The deleted file or subdirectory under the root directory and the system sector of the disk ( Include fat、 root directory 、boot Sector and hard disk partition table ) When damaged , It can also be used. unformat To rescue .
(1) choose /l Parameter lists the subdirectory names found 、 File name 、 Approximate date and other information , But not really unformat Work .
(2) choose /p Parameters will be displayed in the report on the screen ( contain /l Information generated by the parameter ) It is also sent to the printer . The runtime screen will show :“print out will
be sent to lpt1”
(3) choose /test Parameters are only simulated (test) Do not do the real write action . Using this parameter, the screen displays :“simulation only”
(4) choose /u Parameters do not use mirror Image file data , Directly according to the status of the disk unformat.
(5) choose /psrtn; Repair the hard disk partition table .
If you add... After the drive letter /p、/l、/test One of , Are equivalent to using /u Parameters ,unformat Meeting “ hypothesis ” There is no disk at this time mirror Image file .
Be careful :unformat For just format Of disks , Can completely recover , but format After that, if other data is written , be unformat You can't completely save the data .unformat It's not everything , Due to the use unformat Will rebuild fat With the root directory , So it also has high risk , Improper operation may enlarge the loss , If only a few files or subdirectories are deleted by mistake , Just use undelete That's enough .
( 3、 ... and )chkdsk—— Check the current state of the disk command
1. function : Display disk status 、 Memory state and the number of discontinuities in the specified file under the specified path .
3. Format :chkdsk [ Disk character :][ route ][ file name ][/f][/v]
(1) choose [ file name ] Parameters , The disk occupied by the file is displayed ;
(2) choose [/f] Parameters , Correct logical errors found on the specified disk ;
(3) choose [/v] Parameters , Display all files and paths on the disk .
( Four )diskcopy—— Full disk copy command
1. function : Copy a floppy disk in exactly the same format and content .
3. Format :diskcopy[ Disk character 1:][ Disk character 2:]
(1) If the destination floppy disk is not formatted , The system will automatically select format when copying .
(2) If the original file on the target floppy disk , Then all will be lost after copying .
(3) In the case of single drive replication , The system will prompt to replace the source disk and target disk in time , Please distinguish the source disk from the target disk during operation .
( 5、 ... and )label—— Create disk volume label command
1. function : establish 、 change 、 Delete disk volume label .
3. Format :label[ Disk character :][ Volume label ]
(1) The volume label name is the volume label name to be created , If this parameter is defaulted , Then the system prompts you to type in the volume label or asks you whether to delete the original volume label ;
(2) The volume label name is defined by 1 to 11 Characters make up .
( 6、 ... and )vol—— Display disk volume label command
1. function : View the disk volume label .
3. Format :vol[ Disk character :]
4. Instructions : Omit the drive letter , Displays the current drive volume label .
( 7、 ... and )scandisk—— testing 、 Repair disk command
1. function : Check the disk's fat surface 、 Directory structure 、 Is there a problem with the file system , And the detected problems can be repaired .
3. Format :scandisk[ Disk character 1:]{[ Disk character 2:]…}[/all]
(1)scandisk Suitable for hard disk and floppy disk , You can specify more than one disk at a time or choose [/all] Parameter specifies all disks ;
(2) It can automatically detect the cross connection in the disk 、 Logical errors such as missing clusters and directory structures , And fix it .
( 8、 ... and )defrag—— Defragment disk command
1.. function : Defragment the disk , Eliminate disk fragmentation .
3. Format :defrag[ Disk character :][/f]
4. Instructions : choose /f Parameters , Remove the fragments that exist on the disk in the file , And adjust the arrangement of disk files , Make sure there are no gaps between the files . So as to speed up the reading speed and save disk space .
( Nine )sys—— System copy command
1. function : Put... On the current drive dos System files io.sys,msdos.sys and command To the specified drive .
3. Format :sys[ Disk character :]
* Instructions : If there is not enough free space on the disk to store system files , Prompt :no room for on destination disk.
DOS Command file command
( One )copy File copy command
1. function : Copy one or more files to the specified disk .
3. Format :copy [ Source disk ][ route ]( The source file name ) [ Target disk ][ route ]( Destination filename )
(1)copy It's a file to file way to copy data , The destination disk must be formatted before copying ;
(2) In the process of copying , The old file with the same file name on the target disk will be replaced by the source file ;
(3) When copying files , You must first make sure that the target disk has enough space , Otherwise ;insufficient Error messages for , Prompt: insufficient disk space ;
(4) Wildcards are allowed in file names “*”“?”, Multiple files can be copied at the same time ;
(5)copy The source file name in the command must indicate , Don't omit .
(6) Replication time , The destination file name can be the same as the source file name , Referred to as “ Copy with the same name ” In this case, the target file name can be omitted ;
(7) Replication time , The destination file name can also be different from the source file name , Referred to as “ Synonymous copy ”, here , The destination file name cannot be omitted ;
(8) Replication time , You can also combine several files into one file , be called “ Merge copies ”, The format is as follows :copy;[ Source disk ][ route ]〈 The source file name 1〉+〈 The source file name 2〉…[ Target disk ][ route ]〈 Destination filename 〉;
(9) utilize copy command , You can also enter data from the keyboard to create a file , The format is as follows :copy con [ Disk character :][ route ]〈 file name 〉;
After editing ,Ctrl+Z Save editor .
(10) Be careful :copy The format of the command , There must be a space between the source file name and the destination file name !
( Two )xcopy—— Directory copy command
1. function : Copy the specified directory and all the files under the directory together with the directory structure .
3. Format :xcopy [ Source disk :]〈 Source pathname 〉[ Target drive letter :][ Target pathname ][/s][/v][/e]
(1)xcopy yes copy An extension of , You can copy the specified directory with the file and directory structure , But you can't copy hidden files and system files ;
(2) Source drive letter when using 、 Source destination pathname 、 Specify at least one source file name ;
(3) choose /s All the files in the source directory and its subdirectories are copy. Unless specified /e Parameters , otherwise /s You don't copy empty directories , If not specified /s Parameters , be xcopy Copy only the files in the source directory itself , It does not involve subdirectories under it ;
(4) choose /v When parameters are , Compare the copied sectors , But the speed will decrease .
( 3、 ... and )type—— Display file content command
1. function : Show ascii The contents of the code file .
2. type : Internal orders .
3. Format :type[ Disk character :][ route ]〈 file name 〉
(1) Show by ascii A text file composed of codes , Yes .exe or .com Files with extensions such as , The content displayed is unreadable , No practical significance ;
(2) This command can only display the contents of one file at a time , You cannot use wildcards ;
(3) If the file has an extension , The extension must be written ;
(4) When the file is long , When one screen cannot be displayed , It can be displayed in the following format ;type[ Disk character :][ route ]〈 file name 〉|more,more Commands for split screen display , After using some parameters, it will pause when the screen is full , Pressing any key will continue to display .
(5) If you need to print out the contents of the document , The following format can be used :
type[ Disk character :][ route ]〈 file name 〉,>prn
here , The printer should be online .
( Four )ren—— File rename command
1. function : Change file name
3. Format :ren[ Disk character :][ route ]〈 Old filename 〉〈 New file name 〉
(1) The new file name cannot be preceded by a drive letter or path , Because this command can only change the file name of files on the same disk ;
(2) Wildcards are allowed to change a set of file names or extensions .
( 5、 ... and )fc—— File compare command
1. function : Compare the similarities and differences of documents , And list the differences .
3. Format :fc[ Disk character :][ Pathname ]〈 file name 〉[ Disk character :][ Pathname ][ file name ][/a][/c][/n]
(1) choose /a Parameters , by ascii Code comparison mode ;
(2) choose /b Parameters , Binary comparison mode ;
(3) choose /c Parameters , Treat upper and lower case characters as the same characters .
(4) choose /n Parameters , stay ascii Code comparison , Display the line number of the difference .
( 6、 ... and )attrib—— Modify file properties command
1. function : Modify the properties of the specified file .( For file attributes, see 2.5.4( Two ) Document properties section )
2. type : External command .
3. Format :attrib[ file name ][r][—r][a][—a][h][—h][—s]
(1) choose r Parameters , Make the specified file read-only , So that the file can only be read , Unable to write data or delete ; choose —r Parameters , Remove read-only attributes ;
(2) choose a Parameters , Set the file to file attribute ; choose —a Parameters , Remove file attributes ; (3) choose h Parameters , Reconcile files to implicit attributes ; choose —h Parameters , Remove hidden attributes ;
(4) choose s Parameters , Set the file to system properties ; choose —s Parameters , Remove system attributes ; (5) choose /s Parameters , Set all subdirectories and under the current directory .
( 7、 ... and )del—— Delete file command
1. function : Delete the specified file .
3. Format :del[ Disk character :][ route ]〈 file name 〉[/p]
(1) choose /p Parameters , Before deleting, the system asks whether to delete the file , If you don't use this parameter , Automatically delete ;
(2) This command cannot delete files with implicit or read-only properties ;
(3) Wildcards can be used in file names ;
(4) To delete all files on the disk (del*·* or del·), Will prompt :(arey ou sure?)( Are you sure? ?) If you answer y, Then delete , answer n, Then cancel the deletion .
( 8、 ... and )undelete—— Resume delete command
1. function : Restore the wrongly deleted command
3. Format :undelete[ Disk character :][ Pathname ]〈 file name 〉[/dos][/list][/all]
4. Instructions : Use undelete have access to “*” and “?” wildcard .
(1) choose /dos Parameter to recover the file according to the residual records in the directory . Because when the file is deleted , The first character of the file name recorded in the directory will be changed to e5,dos That is, according to e5 And its subsequent characters to find the file to be restored , therefore ,undelete The user will be asked to enter a character , In order to complete the file name . But this character does not have to be the same as the original , Just meet dos File name rule of .
(2) choose /list only “ List ” Files that meet the specified conditions are not restored , So it will not affect the contents of the disk .
(3) choose /all Automatically recover fully recoverable files , Instead of asking users one by one , When using this parameter , if undelete Use the residual records in the directory to recover the files , Then a character will be automatically selected to complete the file name , And make it different from the existing file name , The preferred order of selected characters is :#%——0000123456789a~z.
undelete It also has the function of establishing protective measures for documents , It is beyond the scope of this course , Please refer to the related dos manual .
DOS Command other commands
( One )cls—— Clear screen command
1 function : Clear all displays on the screen , Place the cursor in the upper left corner of the screen .
2 type : Internal orders
3 Format :cls
( Two )ver View system version number command
1 function : Displays the current system version number
3 Format :ver
( 3、 ... and )date Date setting command
1 function : Set or display the system date .
3 Format :date[mm——dd——yy]
4 Instructions :
(1) Omit [mm——dd——yy] Displays the system date and prompts for a new date , If you don't modify it, you can press enter directly ,[mm——dd——yy] by “ The moon —— Day by day —— Every year ” Format ;
(2) When the machine starts , There are automatic file processing (autoexec.bat) Be performed , The system will not prompt for the system date . otherwise , Prompt for a new date and time .
( Four )time System clock setting command
1 function : Sets or displays the system time period .
3 Format :time[hh:mm:ss:xx]
( 5、 ... and )mem View current memory status command
1 function : Displays the current memory usage
2 type : External command
3 Format :mem[/c][/f][/m][/p]
(1) choose /c Parameters list the general memory loaded and cmb The length of each document , It also shows the usage of memory space and the maximum available space ;
(2) choose /f Parameters list the size of bytes remaining in the current general memory and umb Available area and size ;
(3) choose /m The parameter shows the address of the memory used by the module 、 Size and module nature ;
(4) choose /p The parameter specifies that when the output exceeds one screen , Pause for users to view .
( 6、 ... and )msg Display system information command :
1 function : Displays the status of the system's hardware and operating system .
3 Format :msg[/s]
(1) choose /i When parameters are , Do not detect hardware ;
(2) choose /b When parameters are , Start in black and white msg;
(3) choose /s When parameters are , Show concise system reports .
DOS command ping command
about windows Next ping I believe you are familiar with the order , But can put ping There are not many people who give full play to their functions , Of course, I'm not saying that I can make ping Make the most of , I just use it a lot ping This tool , Also summed up some small experience , Now share with you .
reference ping Help instructions for commands , Use ping Skills available when ,ping Only in installation tcp/ip The agreement can only be used later :
ping [-t] [-a] [-n count] [-l length] [-f] [-i ttl] [-v tos] [-r count] [-s count] [[-j computer-list] | [-k computer-list]] [-wz timeout] destination-list
options:
-t ping the specified host until stopped to see statistics and continue - type control-break;to stop - type control-c.
Ceaseless ping Local host , Until you press control-c.
There's nothing special about this feature , But it can be used with other parameters , It will be mentioned below .
net use \ip\ipc$ " " /user:" " establish ipc Empty link
net use \ip\ipc$ “ password ” /user:“ user name ” establish ipc Non empty Links
net use h: \ip\c$ “ password ” /user:“ user name ” Directly log in and map each other c: Go to the local for h:
net use h: \ip\c$ Log in and map each other c: Go to the local for h:
net use \ip\ipc$ /del Delete ipc link
net use h: /del Delete the mapping object to the local as h: Mapping
net user user name password /add Build users
net user guest /active:yes Activate guest user
net user See which users
net user Account name View account properties
net localgroup ***istrators user name /add hold “ user ” Add to administrator to have administrator rights , Be careful :***istrator After add s In the plural
net start See what services are turned on net start service name Opening service ;( Such as :net start telnet,
net start schedule)net stop service name Stop a service
net time \ The goal is ip Check each other's time
net time \ The goal is ip /set Set the local computer time and “ The goal is ip” Time synchronization of the host , Add parameters /yes The confirmation can be cancelled
net view Check which shares are enabled in the local area network
net view \ip Check which shares are enabled in the other party's LAN
net config Display system network settings
net logoff Disconnected shares
net pause service name Suspend a service
net send ip “ Text information ” Send messages to each other
net ver The type of network connection and information being used in the LAN
net share View locally enabled shares
net share ipc$ Turn on ipc$ share
net share ipc$ /del Delete ipc$ share
net share c$ /del Delete c: share
net user guest 12345 use guest After the user logs in, change the password to 12345net password password Change system login password
netstat -a See which ports are open , Commonly used
netstat -annetstat -n View the network connection of the port , Commonly used
netstat -annetstat -v View work in progress
netstat -p The name of the agreement example :netstat -p tcp/ip Check the usage of a protocol ( see tcp/ip Protocol usage )
netstat -s View all protocol usage in use
nbtstat -a ip other party 136 To 139 If one of the ports is open , You can check the user name of the other party's recent login (03 The former is the user name )- Be careful : Parameters -a Use capital letters
tracert - Parameters ip( Or computer name ) Trace route ( Data packets ), Parameters :“-w Numbers ” Used to set the timeout interval .
ping ip( Or domain name ) Send the default size to the opposite host 32 Bytes of data , Parameters :“-l[ Space ] Packet size ”;“-n Number of data sent ”;“-t” Means always ping.
ping -t -l 65500 ip Death ping( Send greater than 64k The documents are not always ping It's death ping)
ipconfig (winipcfg) be used for windows nt And xp(windows 95 98) View local ip Address ,
ipconfig The available parameters “/all” Display all configuration information
tlist -t Show processes in a tree row list ( Additional tools for the system , There is no installation by default , In the installation directory support/tools In the folder )
kill -f Process name Add -f Parameter to force the end of a process ( Additional tools for the system , There is no installation by default , In the installation directory support/tools In the folder )
del -f File name plus -f Parameter to delete the read-only file ,/ar、/ah、/as、/aa Delete read-only 、 hide 、 System 、 Archive file ,/a-r、/a-h、/a-s、/a-a Means delete except read-only 、 hide 、 System 、 Files other than Archives . for example “del/ar .” Delete all read-only files in the current directory ,“del/a-s .” Delete all files except system files in the current directory
DOS command shutdown
The order is as follows :
shutdown.exe -a Cancel shutdown
shutdown.exe -s To turn it off
shutdown.exe -f Forcibly close the application .
shutdown.exe -m \ Computer name Control remote computer .
shutdown.exe -i Display a graphical user interface , But it has to be Shutdown The first parameter of .
shutdown.exe -l Logout the current user .
shutdown.exe -r Shut down and restart .
shutdown.exe -t Time Set shutdown countdown .
shutdown.exe -c" The message content " Enter the message content in the shutdown dialog box ( You can't go beyond 127 Characters ).
For example, your computer should be in 24:00 To turn it off , You can choose “ Start → function ”, Input “at 24:00 Shutdown -s”, such , here we are 24 spot , The computer will appear “ System shutdown ” Dialog box , The default is 30 Seconds and prompts you to save your work . If you want to turn it off in a countdown , You can enter “Shutdown.exe -s -t 7200”, It means 120 Turn off automatically in minutes ,“7200” representative 120 minute .
If you want to cancel , You can enter “shutdown -a”. In addition, enter “shutdown -i”, You can open the set auto shutdown dialog box , Set up automatic shutdown .
Give Way Windows 2000 The same effect can be achieved , You can put Shutdown.exe Copy to the system directory System32 Next
eg:shutdown.exe -s -m \z20235
Of course, you can also put shutdown And at Life is used together to shut down regularly , It will be more accurate , Format :at Shut down time shutdown Options
example :at 12:45 shutdown -s -t 20 Is to let the machine in 12:45 To turn it off , And count down 20 second . It should be noted that it must be opened before using “Task Scheduler” service .
DOS Command basic command
DOS command ping
It is used to check whether the network is smooth or the network connection speed . As an administrator or hacker living on the Internet ,ping Command is the first thing that must be mastered DOS command , The principle it uses is : Machines on the Internet have a unique identity IP Address , We give the target IP Address to send a packet , The other party will return a packet of the same size , According to the returned packets, we can determine the existence of the target host , The operating system of the target host can be preliminarily determined . Let's take a look at some of its common operations . Let's see the help first , stay DOS In the window, type :ping /? enter ,. Help screen shown . Here it is , We only need to master some basic and useful parameters ( The same below ).
-t It means that we will keep on going to the target IP Send packet , Until we force it to stop . Just imagine , If you use 100M Broadband access to , And the goal IP yes 56K My kitten , Then it won't be long , The goal is IP Just because I can't bear so much data, I'm offline , ha-ha , An attack is so simple to implement .
-l Define the size of the packets sent , The default is 32 byte , We can use it to define as much as 65500 byte . Combined with the above introduction -t Parameters used together , It will have a better effect .
-n Define to target IP Number of packets sent , The default is 3 Time . If the network is slow ,3 It's a waste of time for us , Because now our goal is just to judge the target IP Whether there is , Then define it as once .
Explain , If -t Parameters and -n Parameters used together ,ping The command is based on the parameters that follow , such as “ping IP -t -n 3”, Although used -t Parameters , But not all the time ping down , It's just ping 3 Time . in addition ,ping Orders don't have to be ping IP, It can also be direct ping Host domain name , So you can get the host's IP.
DOS command nbtstat
The command uses TCP/IP Upper NetBIOS Show protocol statistics and current TCP/IP Connect , Use this command to get the remote host's NETBIOS Information , For example, user name 、 Working group 、 NIC MAC Address, etc . Here we need to know a few basic parameters .
-a Use this parameter , As long as you know the machine name of the remote host , You can get it NETBIOS Information ( The same below ).
-A This parameter can also get the remote host's NETBIOS Information , But you need to know it IP.
-n List the NETBIOS Information .
When you get the other person's IP Or the machine name , You can use nbtstat Order to get more information about each other , This in turn increases the insurance factor for our invasion .
DOS command netstat
This is a command to check the status of the network , Easy to operate and powerful .
-a Check all open ports on the local machine , Can effectively discover and prevent Trojans , You can know the service information of the machine , Pictured 4.
Here we can see that the local machine is open FTP service 、Telnet service 、 The mail service 、WEB Service etc. . usage :netstat -a IP.
-r List current routing information , Tell us the gateway of the local machine 、 Subnet mask and other information . usage :netstat -r IP.
DOS command tracert
Track route information , Use this command to find out all the ways the data is transferred from the local machine to the target host , This is very helpful for us to understand the network layout and structure . Pictured 5.
The data is transferred from the local machine to 192.168.0.1 On the machine , There's no transit in the middle , The two machines are in the same LAN . usage :tracert IP.
DOS command net
This command is one of the most important network commands , You must have a thorough grasp of the usage of each of its subcommands , Because it's so powerful ad locum , We focus on a few commonly used subcommands .
net view
Use this command to view all the shared resources of the remote host . The command format is net view \IP.
net use
Map a shared resource of a remote host to a local drive letter , The graphic interface is easy to use . The command format is net use x: \IP\sharename. The above one means to 192.168.0.5IP Your share is named magic The directory of is mapped to local Z disc . The following represents and 192.168.0.7 establish IPC$ Connect (net use KaTeX parse error: Undefined control sequence: \IPC at position 7: ">\\IP\̲I̲P̲C̲ “password” /user:“name”),
Established IPC$ After connection , ha-ha , You can upload files :copy nc.exe KaTeX parse error: Undefined control sequence: \admin at position 16: ">\\192.168.0.7\̲a̲d̲m̲i̲n̲, Indicates that the local directory nc.exe To the remote host , Combined with other DOS The command can realize the intrusion .
net start
Use it to start a service on a remote host . When you establish a connection with the remote host , If you find that any of its services are not started , And what do you want to do with this service ? Just use this command to start . usage :net start servername, Pictured 9, Successfully started telnet service .
net stop
After the intrusion, it was found that a service of the remote host was in the way , What do I do ? Use this command to stop ok 了 , Usage and net start Same as .
net user
Check account related information , Include new account 、 Delete account 、 View specific accounts 、 Activate account 、 Account disable etc . It's good for our invasion , The most important , It provides the premise for us to clone accounts . Type... Without parameters net user, Can view all users , Include disabled . Here are the details .
1,net user abcd 1234 /add, Create a new user name of abcd, The password for 1234 Account for , The default is user The group members .
2,net user abcd /del, Set the user name to abcd Users delete .
3,net user abcd /active:no, Set the user name to abcd Disabled by .
4,net user abcd /active:yes, The activation user name is abcd Users of .
5,net user abcd, Check that the user name is abcd Of users
net localgroup View all the information and actions related to user groups . Type... Without parameters net localgroup That is, all current user groups are listed . During the invasion , We usually use it to promote an account to administrator Group account , In this way, we can use this account to control the whole remote host .
net time
This command can view the current time of the remote host . If your goal is just to enter the remote host , Then maybe you can't use this command . But the simple invasion succeeded , Is it just a look ? We need further penetration . Even the current time of the remote host needs to be known , Because using time and other means ( I'll talk about it later ) It can realize the timing start of a command and program , Lay the foundation for our further invasion . usage :net time \IP.
DOS command at
The function of this command is to arrange to execute a specific command and program on a specific date or time ( know net time It's important ?). When we know the current time of the remote host , You can use this command to make it at a later time ( such as 2 Minutes later ) Execute a program and command . usage :at time command \computer.
It means that 6 spot 55 time-sharing , Let the name be a-01 Your computer is turned on telnet service ( here net start telnet That is to open. telnet Commands for services ).
DOS command ftp
First type... On the command line ftp enter , appear ftp Prompt , You can type in “help” To see the help ( whatever DOS Command can use this method to view its help ).
The first is the landing process , That's what we need open 了 , Directly in ftp At the prompt of “open host IP ftp port ” You can enter. , Generally, the default port is 21, Don't write . Then it is to enter a legal user name and password to log in , It's anonymous ftp As an example to introduce .
The username and password are both ftp, The password is not shown . When prompted **** logged in when , It means the landing is successful . Because it's anonymous , So the user shows Anonymous. Next, I will introduce the usage of specific commands .
dir Follow DOS command , Files used to view the server , Hit it directly dir enter , You can see this ftp Files on the server .
cd Enter a folder .
get Download files to local machine .
put Upload files to remote server . It depends on the distance ftp Whether the server has given you writable permission , If possible , ha-ha , What should I do I don't want to say much about it , Let's play freely .
delete Delete remote ftp Files on the server . It must also ensure that you have writable rights .
bye Exit the current connection .
quit ditto .
DOS command telnet
Powerful remote login command , Almost all intruders like to use it , To test that . Why? ? It's easy to operate , Just like using your own machine , As long as you are familiar with DOS command , In success with administrator After the identity is connected to the remote machine , You can use it to ** Everything I want to do . Here is how to use it , First type. telnet enter , Retype help Check out its help .
Then type at the prompt open IP enter , The landing window appears , Let you enter a valid user name and password , Any password entered here is not shown .
When the user name and password are entered correctly, it is successfully established telnet Connect , At this time, you have the same permissions as this user on the remote host , utilize DOS Command will do what you want . Here I use the super administrator permission to log in .
DOS Command character application
DOS Command list symbol
【~】
① stay for Indicates the use of enhanced variable extensions .
② stay %var:~n,m% Represents a string that uses an extended environment variable to specify a location .
③ stay set/a Represents a unary operator , Invert the operand bit by bit .
【!】
① stay set /a Unary operator in , Express logical not . such as set /a a=!0, At this time a It means logic 1.
【@】
① Hide the echo of the command line itself , Commonly used in batch processing .
【$】
① stay findstr The command indicates the end of a line .
② stay prompt In the order , Means to escape the following characters ( Symbolization or effect ).
【%】
① stay set /a Binary operator in , Means arithmetic remainder .
② In the command line environment , stay for command in front , Followed by a character ( It could be letters 、 Numbers or some specific characters ), It means to specify a cycle or traverse the index variable .
③ In batch , Followed by a number, it refers to the specified parameters during the current execution of this batch .
④ In other cases ,% Will be removed ( The batch ) Or keep it ( Command line )
【^】
① Cancel the escape function of specific characters , such as & | > < ! " etc. , But does not include %. For example, some special characters should be displayed on the screen , such as > >> | ^ &; When you wait for the sign , You can add a Symbol to show this The following characters ,^ Is to display a ,^| Is to display a | Character ;
② stay set/a Binary operator in , Means bitwise XOR .
③ stay findstr/r Of [] Indicates that the specified character set does not match .
【&;】
① Command concatenation character . For example, I want to execute two commands simultaneously on a line of text , You can use it &; Command connects these two commands .
② stay set/a Middle is bitwise AND .
【*】
① Represents any arbitrary character , It's what we usually say " wildcard "; Such as in c Find the root directory of the disk c All text files in the root directory (.txt), Then you can enter the command "dir c:*.txt".
② stay set /a Binary operator in , It means arithmetic multiplication .
③ stay findstr/r Middle means to match the previous character multiple times .
【-】
① Range indicator , For example, find the date ,for In the order tokens This character can be used in operation .
② stay findstr/r Connecting two characters in indicates the matching range .
③ - Follow some orders / The latter indicates the switch in reverse .
④ stay set /a in :
1. It means a negative number .
2. Represents arithmetic subtraction .
【+】
① Mainly in the copy It will be used in the command , It means merging many files into one file , It's about this + Character .
② stay set/a Binary operator in , It means arithmetic addition .
【:】
① Label locator , Indicates that the following string is labeled , It can be used as goto The object of command . For example, the batch file defines a ":begin" label , use "goto begin" The command can go to ":begin" After the tag, execute the batch command .
② stay %var:string1=string2% Separate the variable name and the replaced string relationship .
【|】
① Pipe, , That is, the output of the previous command , As input for the next command ."dir /a/b |more" It can be displayed screen by screen dir The information output by the command .
② stay set/a Binary operator in , It's bitwise OR .
③ Indicate the front and back switches in the help document 、 Options or parameters are optional .
【/】
① Represents the following characters ( strand ) It is the function switch of the command ( Options ). such as "dir /s/b/a-d" Express "dir" Different parameters specified by the command .
② stay set/a Middle means division .
【>;】
① Command redirector ,
echo Tangshan flavor is not strong Welcome >d:\1.txt ; Write text to the specified file ( Replace if file exists )
② stay findstr/r Middle represents the right boundary of the matching word , Need to match escape character \ Use .
【<;】
① Take the contents of the file after it as the input of the command before it .
② stay findstr/r Middle represents the left boundary of the matching word , Need to match escape character \ Use .
【=】
① Assignment symbol , For assignment of variables . such as "set a=windows" Means to "windows" This string is assigned to the variable "a".
② stay set/a Means arithmetic operation , such as "set /a x=5-6*5".
【\】
① This "" Symbols in some cases , Represents the root directory of the current path . For example, the current directory is c:\windows\system32 Next , So you "dir “ Words , It's equivalent to "dir c:”.
② stay findstr/r Represents the regular escape character .
【,】
① stay set /a The delimiter that represents a continuous expression in .
② Split elements in some commands .
【.】
① At the end of the path \ Follow closely or appear alone :
One . Represents the current directory .
Two . Represents the directory above .
② When it appears in the file name in the path :
Last one . Indicates the separation between the main file name and the extended file name .
【?】
① stay findstr/r Means that an arbitrary character is matched at this position .
② In the path, it means that any character is collocated at this position .
③ Keep up with the / After that, it means to get the help document of the command .
DOS Command multiple symbols
【&&;】
① Connect two commands , When &&; When the previous order was successful , To perform &&; Later orders .
【||】
① Connect two commands , When || When the previous command fails , To perform || Later orders .
【>&;】
① Write the output of one handle to the input of another .
【<&;】
① Read input from one handle and write it to another handle output .
【%%】
① Two consecutive % Indicates that it is separated into a %.
② In batch , stay for Of the statement in Before clause , For two consecutive % Followed by a character ( It could be letters 、 Numbers and some specific characters ), Means to specify a cycle
Loop or traverse index variables .
③ In batch , stay for In the sentence , Use with in The same string as the previously specified indicator variable , Refers to the index variable .
【>>;】
① Command redirector , Append the output of the previous command to the back .
Parameters : command + >> + Write path \ file name
netstat -an >>d:\1.txt ; Namely follow ‘1.txt’ Continue writing at the end of ‘netstat -an’ Command output result
② stay set /a Binary operator in , Indicates a logical shift to the right .
【==】
① stay if Judge in command == Whether the elements on both sides are the same .
【<<;】
① stay set /a Binary operator in , Indicates a logical shift left .
【+=】
① stay set /a Binary operator in . for example set /a a+=b It means that you will a add b The result of is assigned to a.
【-=】
① stay set /a Binary operator in . for example set /a a-=b It means that you will a subtract b The result of is assigned to a.
【*=】
① stay set /a Binary operator in . for example set /a a*=b It means that you will a multiply b The result of is assigned to a.
【/=】
① stay set /a Binary operator in . for example set /a a/=b It means that you will a add b The result of is assigned to a.
【%=】
① stay set /a Binary operator in . for example set /a a%=b It means that you will a Divide b The remainder of is assigned to a.
notes : The command line can be used directly set /a a%=b , It can be used in batch processing set /a a%%=b.
【^=】
① stay set /a Binary operator in . for example set /a a"^="b It means that you will a And b Assign a value to a.
notes : here “^=” Quotation marks are used to prevent ^ escaped , The same below .
【&=】
① stay set /a Binary operator in . for example set /a a"&="b It means that you will a And b The result of bitwise and is assigned to a.
【|=】
① stay set /a Binary operator in . for example set /a a"|="b It means that you will a And b The result of bitwise or is assigned to a.
【<<=】
① stay set /a Binary operator in . for example set /a a"<<="b It means that you will a Move left according to position b The result of bit is assigned to a.
【>>=】
① stay set /a Binary operator in . for example set /a a">>="b It means that you will a Right shift to position b The result of bit is assigned to a.
【<;】
① stay findstr Represents the beginning of a word in a general expression of .
【>;】
① stay findstr Represents the end of a word in a general expression of .
【!!】
① When variable delay is enabled , Use !! Expand the variable name to indicate the reference to the variable value .
【’ '】
① stay for/f Means to execute their contents as a command line and analyze their output .
② stay for/f "usebackq" Means to analyze the strings they contain as strings .
【()】
① The command contains or has priority delimiters , such as for The command needs this (), We can still do that if,echo Wait for the command to see its figure .
② stay set /a Represents the grouping of expressions .
【" "】
① Delimiter , We often use "“ To enclose the path , Some commands also need ” " Symbol .
② stay for/f Analyze the contents that represent them as strings .
③ stay for/f "usebackq" Indicate that the contents they contain are regarded as file paths and analyze the contents of their files .
④ In other cases, it means that the content is a complete string , Among them >;、>>;、<;、&;、|、 Spaces and so on are no longer escaped .
【】
① stay for/f Indicates that the content contained in them is executed as a command line and its output is analyzed .
【[ ]】
① Indicate the switch in the help document 、 Options or parameters are optional .
② stay findstr /r Means to match according to the specified character set
Hold down shift You can input a small amount of capital letters ,?+? Key means to press and hold the previous key first , Press the second key at the same time .
ctrl+sc or ctrl+num lock Pause to observe the screen display , Press once to continue .
ctrl+c or ctrl+break Terminate program operation , Back to the operating system .
DOS Command program process
ntsd It's a piece. dos command , The function is used to end some dead processes that can't be ended under normal circumstances .
Usage is to open cmd After entering the following command, you can end the process :
Method 1 : Take advantage of the progress of PID The end of the process
Command format :ntsd -c q -p pid
Example command :ntsd -c q -p 1332 ( end explorer.exe process )
A detailed explanation of the example :explorer.exe Of pid by 1332, But how to get the pid Well ? stay CMD The input TASKLIST You can get the... Of all processes in the current task manager PID
Method 2 : Use the process name to end the process
Command format :ntsd -c q -pn ***.exe (***.exe Is the process name ,exe Can't save )
Example command :ntsd -c q -pn explorer.exe
The other can end the process DOS Orders and taskkill:
Command format :taskkill /pid 1234 /f ( The same effect can be achieved .)
If the above cannot satisfy your thirst for knowledge , And then there is :
ntsd Detailed explanation
There are some high-level processes ,tskill and taskkill It may not end , Then we have a more powerful tool , That's the system debug
Class ntsd. Accurately speaking ,ntsd It's a
System debugging tools , Only for system development level administrators , But it's still cool for us to kill the process . Basically except WINDOWS system
Manage your own process ,ntsd Can be killed .
Of course , There are some rootkit Level super Trojan , There's nothing I can do about it , Fortunately, there are still few such bull level Trojans .
NTSD When the debugger starts, it requires the user to specify a process to connect . Use TLIST or PVIEWER, You can get an existing
Process of process ID, Then type. NTSD -p pid To debug this process .NTSD The command line uses the following syntax :
NTSD [options] imagefile
among ,imagefile Is the name of the image to debug ,options Is one of the following options :
Option description -2 Open a new window for debugging character mode applications -d Redirect the output to the debug terminal -g Make the execution automatic
Cross the first breakpoint -G send NTSD Exit immediately when the subroutine terminates o Enable debugging of multiple processes , The default value is a derived from the debugger
A process -p Specify debugging by process ID Identified process -v Produces detailed output
for example , hypothesis inetinfo.exe The process of ID by 104. Typing the following command will NTSD The debugger is connected to inetinfo process
(IIS).
NTSD -p 104
You can also use NTSD Start a new process to debug . for example ,NTSD notepad.exe Will start a new notepad.exe Into the
cheng , And connect to it .
Once connected to a process , You can view the stack with various commands 、 To set breakpoints 、 Dump memory , wait .
Meaning of order ~ Show a list of all threads KB Displays the stack trace of the current thread ~*KB Display stack tracks of all threads R Show the current
Register output of frame U Disassemble the code and display the procedure name and offset D Dump memory BP To set breakpoints BC Clear one or more breakpoints BD Disable one or more breakpoints BE Enable one or more breakpoints BL List one or more breakpoints
individual opinion , A very important parameter is -v Parameters , We can find which connection library files are attached under a process through it .
There are many viruses , Trojan horse , Or malware , They all like to make themselves into dynamic libraries , Then register in the loading library list of the normal program of the system , reach
To hide your purpose .
First we need to set up ntsd Output redirection for , It is best to redirect to a text file , It is convenient for us to analyze and study .
c:>set _NT_DEBUG_LOG_FILE_APPEND=c:\pdw.txt
Be careful , Although the output is redirected , But our output will continue to be displayed on the screen , And will enter debug Pattern , We use -c
q Parameters , We can avoid this problem .
c:>ntsd -c q -v notepad.exe
Now our pdw.txt In file , You can see notepad.exe Debug information for file .
ntsd Kill the process with the following parameters .
c:>ntsd -c q -p PID As long as you can provide the process PID, Then you can kill the process .
We know ,Windows The task manager of is a useful tool for us to know which programs are running on the current computer , So how to open this task manager ? In practice, there are usually two methods : First, press on the keyboard Ctrl+Alt+Del You can open the task manager ; Second, move the mouse to the blank space on the taskbar , Right click → Select task manager to open Task Manager . however , Sometimes after a computer virus , The virus will disable the task manager , What to do at this time ? Please look down .
At this time, we need to adopt a more professional method to open the task manager , That is, use the command prompt , Here is how to use the command prompt to open the task manager , And how to use commands to shut down related processes .
1、 Use the command prompt (cmd) Open the task manager to view the process method
Start → function →cmd, Then enter... In the command prompt window Tasklist You can view the current process of the computer .
2、 Use the command prompt (cmd) The method of terminating a process
Here we use the method of example to illustrate the problem , If you want to abort the Notepad process in the current process notepad.exe, You can use the following commands :
taskkill /f /im notepad.exe
If you know the process to be terminated pid value ( Through the task manager, you can see the pid value ), For example 100, You can use the following commands :
ntsd -c q -p 100 perhaps taskkill /f /pid 100
边栏推荐
- Pytoch temperature prediction
- I2C总线时序详解
- Analysis of charging architecture of glory magic 3pro
- RT-Thread 线程的时间片轮询调度
- Pytoch implements simple linear regression demo
- MP3mini播放模块arduino<DFRobotDFPlayerMini.h>函数详解
- arduino UNO R3的寄存器写法(1)-----引脚电平状态变化
- JS 函数提升和var变量的声明提升
- FreeRTOS 任务函数里面的死循环
- [esp32 learning-2] esp32 address mapping
猜你喜欢
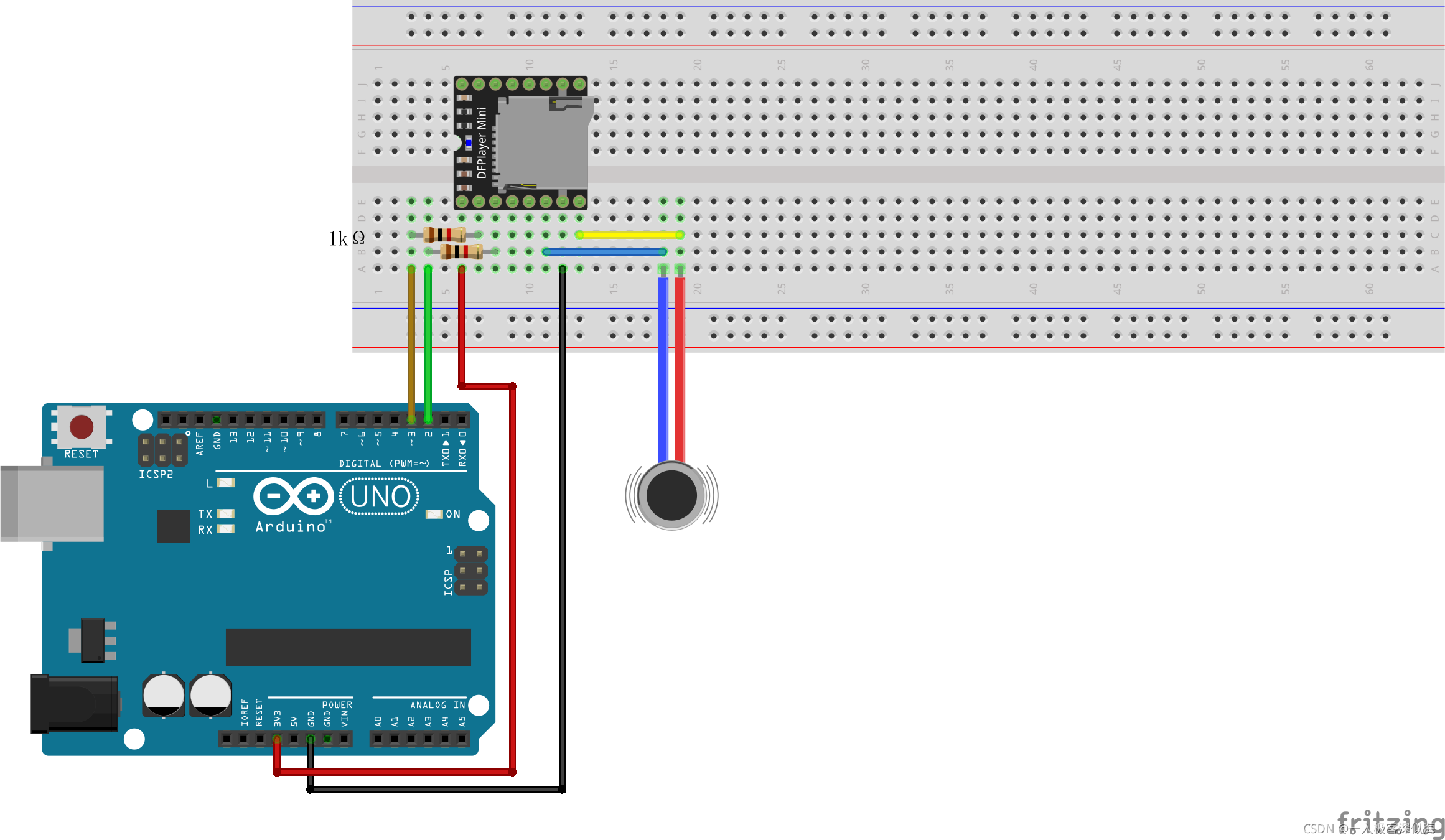
Mp3mini playback module Arduino < dfrobotdfplayermini H> function explanation
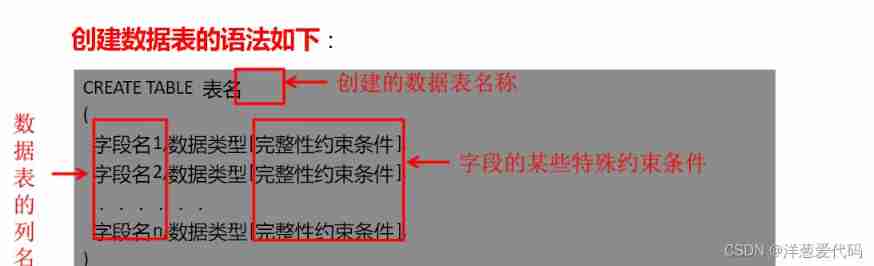
Basic operations of databases and tables ----- creating data tables
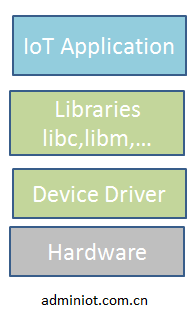
IOT system framework learning
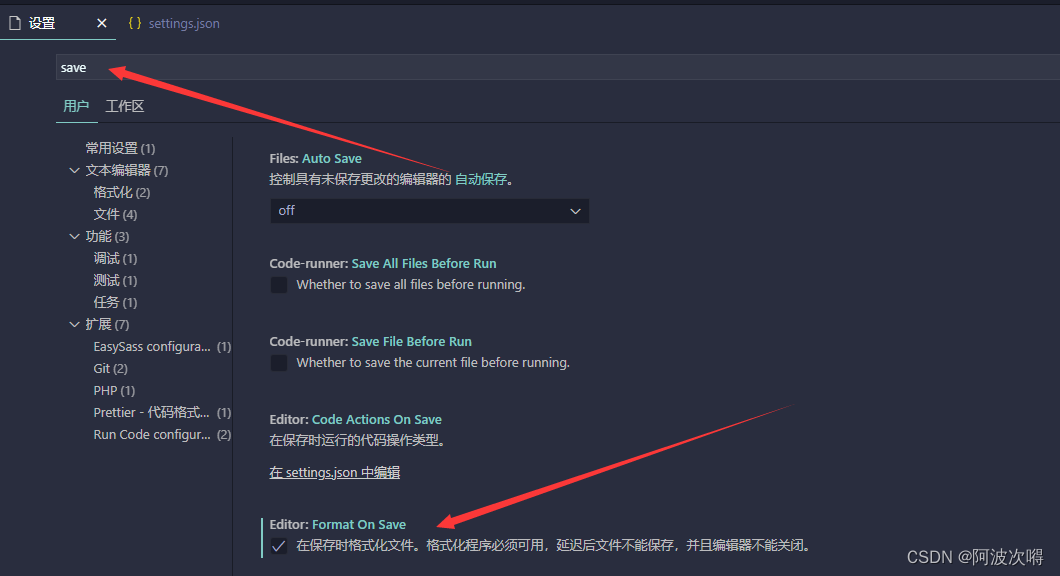
VSCode基础配置
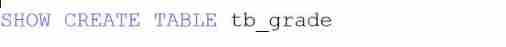
Basic operations of databases and tables ----- view data tables
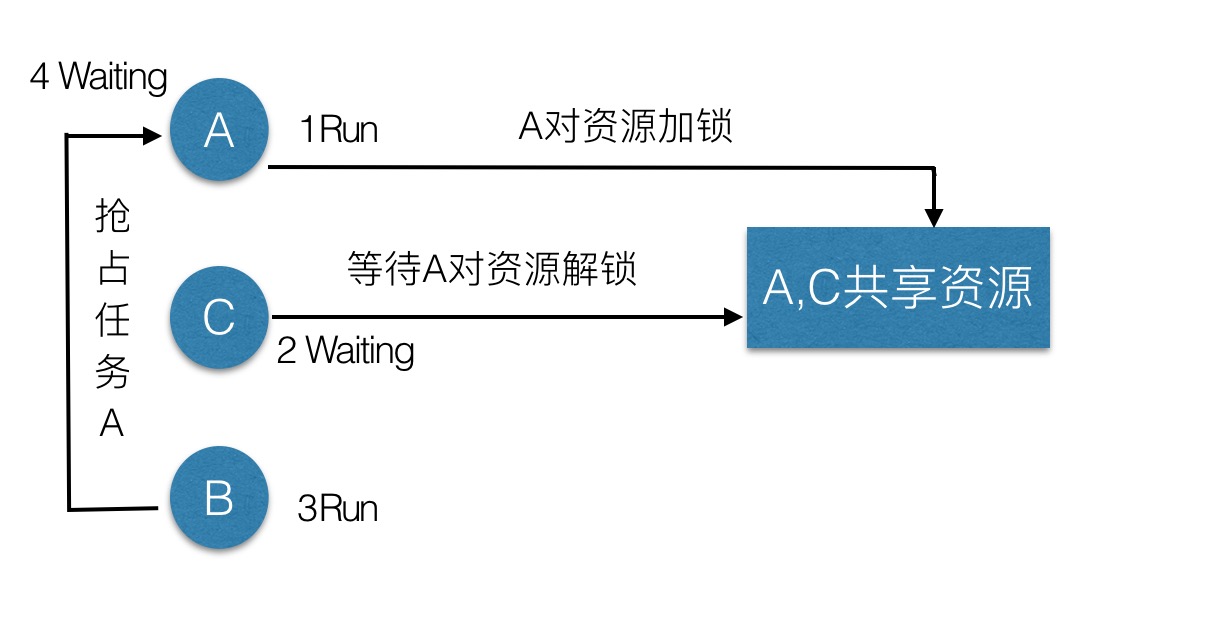
Priority inversion and deadlock
ESP8266使用arduino连接阿里云物联网

RT-Thread API参考手册

Basic knowledge of lithium battery
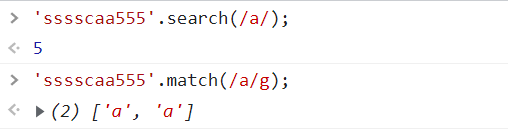
JS regular expression basic knowledge learning
随机推荐
Esp8266 connects to onenet cloud platform (mqtt) through Arduino IDE
Générateur d'identification distribué basé sur redis
电商数据分析--薪资预测(线性回归)
The first simple case of GNN: Cora classification
Gallery's image browsing and component learning
Priority inversion and deadlock
基于Redis的分布式ID生成器
Dead loop in FreeRTOS task function
Symbolic representation of functions in deep learning papers
RuntimeError: cuDNN error: CUDNN_STATUS_NOT_INITIALIZED
ESP学习问题记录
Missing value filling in data analysis (focus on multiple interpolation method, miseforest)
C语言回调函数【C语言】
ESP8266通过arduino IED连接巴法云(TCP创客云)
RuntimeError: cuDNN error: CUDNN_ STATUS_ NOT_ INITIALIZED
VSCode基础配置
Esp8266 connects to bafayun (TCP maker cloud) through Arduino IED
Unit test - unittest framework
uCOS-III 的特点、任务状态、启动
Kaggle竞赛-Two Sigma Connect: Rental Listing Inquiries