当前位置:网站首页>Analysis of the source code of cocos2d-x for mobile game security (mobile game reverse and protection)
Analysis of the source code of cocos2d-x for mobile game security (mobile game reverse and protection)
2022-07-06 08:31:00 【Game programming】
One 、cocos2d-x Frame structure
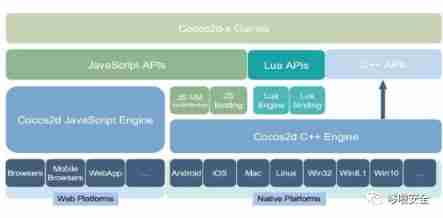
Two 、cocos2d-x Engine architecture
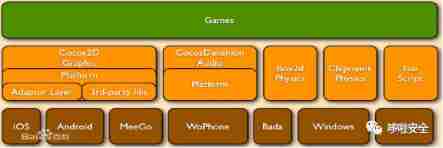
3、 ... and 、cocos2d-x Source structure
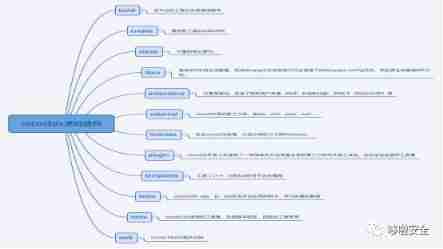
Four 、cocos2d-x The source code parsing
1.luaLoadBuffer Function analysis
cocos2d-x-3.16/cocos/scripting/lua-bindings/manual/CCLuaStack.hcocos2d-x-3.16/cocos/scripting/lua-bindings/manual/CCLuaStack.cpp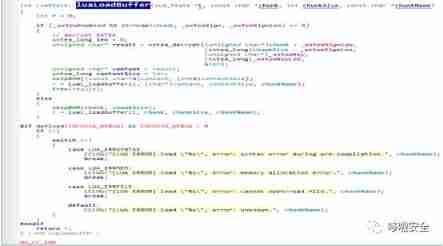
2.applicationDidFinishLaunching Function analysis
cocos2d-x-3.16/tools/simulator/frameworks/runtime-src/Classes/AppDelegate.hcocos2d-x-3.16/tools/simulator/frameworks/runtime-src/Classes/AppDelegate.cpp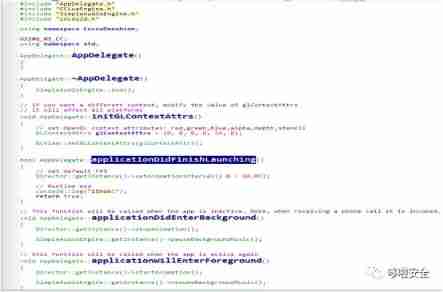
cocos2d-x-3.16/tests/lua-tests/project/Classes/AppDelegate.hcocos2d-x-3.16/tests/lua-tests/project/Classes/AppDelegate.cppcocos2d-x-3.16/templates/cpp-template-default/Classes/AppDelegate.cppcocos2d-x-3.16/templates/js-template-default/frameworks/runtime-src/Classes/AppDelegate.cppcocos2d-x-3.16/templates/lua-template-default/frameworks/runtime-src/Classes/AppDelegate.cppcocos2d-x-3.16/tests/cpp-empty-test/Classes/AppDelegate.cpp 5、 ... and 、 Static analysis so The characteristic function of
1.cocos2d-x lua Version number of
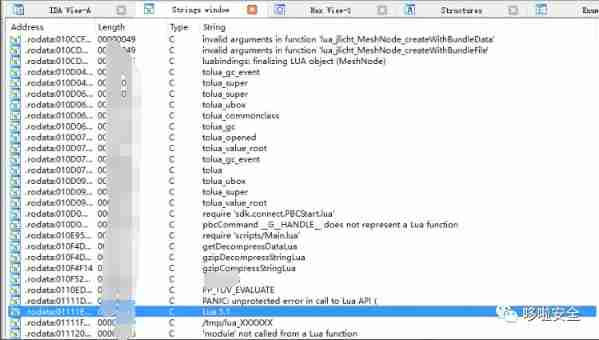
2.cocos2d-x luajit Version number of

3.loadChunksFromZIP function

4.luaLoadChunksFromZIP function

5.luaL_loadbuffer、luaL_loadbufferx、lua_dump function ( Encryption and decryption lua Source code )
(1). stay luaL_loadbuffer Function lua Source code (cocos Engine lua The loader is cocos2dx_lua_loader, In the end, they call luaL_loadbuffer Function to load ,lua The encryption and decryption of the source code are protected by lua_loader Encapsulate the suffix related functions for the loader , Realize to lua File encryption / Decrypt 、 Compress / Decompression and other processing )
(2). At the bottom reader Function lua Source code (lua Engine load lua The bottom layer of the script is to lua_reader function , This function is responsible for the bottom script buff Traverse , So here Hook dump Coming out lua The script is the purest lua Script , All encryption has been removed ( modify lua opcode Or engine logic )( Not enough file information can be obtained at this point ( file name 、buff index etc. ), It needs to be pieced together with the upper function lua Script )
(3). Locate the luaL_loadbuffer function , And then back up , Analyze the decryption process
(4). Pack in App Medium lua The code is usually encrypted , The program is loading lua Decrypt on script ( The key function luaL_loadbuffer ), After decryption, you can get lua Source code . If you get luac Bytecode , It can also be obtained by decompiling lua Source code , The main tools used for decompilation are unluac and luadec51

jlicht_lua_loadercocos2dx_lua_loaderjinit_marker_readerbool AppDelegate::applicationDidFinishLaunching()AppDelegate::applicationDidFinishLaunching(AppDelegate *__hidden this)int LuaStack::luaLoadBuffer(lua_State *L, const char *chunk, int chunkSize, const char *chunkName)cocos2d::CCLuaStack::lua_loadbuffer(lua_State , char const, int, char const*)int luaL_loadbuffer (lua_State *L, const char *buff, size_t sz, const char *name)cocos2d::LuaStack::luaLoadBuffer(lua_State *, char const*, int, char const*)typedef const char * (*lua_Reader) (lua_State *L, void *ud, size_t *sz)typedef int (*lua_Writer) (lua_State *L, const void* p, size_t sz, void* ud)6.applicationDidFinishLaunching、tgaLoadBuffer、loadBinary、loadBreakConfig、loadBottleModel、loadBoxData、ApplicationProtocol function
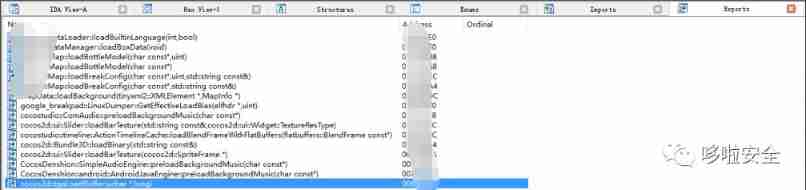
7.initWithImageFile、initWithImageData、initWithImageFile Such as function ( Encrypt and decrypt the resource files of mobile games )
cocos2d::CCImage::initWithImageFile(char const*, cocos2d::CCImage::EImageFormatcocos2d::CCImage::initWithImageData(void *, int, cocos2d::CCImage::EImageFormat, int, int, int)jlicht::Image::initWithImageFile(std::string const&, bool)lua_cocos2dx_Image_initWithImageFile(lua_State *)cocos2d::Image::initWithImageFile(std::string const&)int lua_cocos2dx_Image_initWithImageFile(lua_State* tolua_S)bool initWithImageFile(const char * strPath, EImageFormat imageType = kFmtPng)bool initWithImageData(void * pData, int nDataLen, EImageFormat eFmt = kFmtUnKnown, int nWidth = 0, int nHeight = 0, int nBitsPerComponent = 8)bool Image::initWithImageFile(const std::string& path)bool CCImage::initWithImageFile(const char * strPath, EImageFormat eImgFmt/* = eFmtPng*/)bool js_cocos2dx_Image_initWithImageFile(JSContext *cx, uint32_t argc, jsval *vp)static int tolua_Cocos2d_CCImage_initWithImageFile00(lua_State* tolua_S)static int tolua_Cocos2d_CCImage_initWithImageData00(lua_State* tolua_S) 6、 ... and 、cocos2dx lua On the protection of scripts
1.lua、luac、luaJIT The relationship between the three documents
among lua It's plaintext code , You can open it directly with Notepad ,luac yes lua Compiled bytecode , The file header is 0x1B 0x4C 0x75 0x61 0x51 ,lua The virtual machine can directly parse lua and luac Script files , and luaJIT Is another lua Implementation version of ,JIT Refer to Just-In-Time( Instant parsing run ),luaJIT comparison lua and luac More efficient , The file header is 0x1B 0x4C 0x4A
2. Game manufacturers generally do not directly lua The source script is packaged into App In the release , General pair lua The protection of scripts is generally as follows 3 Kind of , As shown below :
(1).cocos2dx lua Script encryption 、 Decrypt before loading the script
The plan is easy to pass hook cocos Get the key interface of lua Source code
(2). take cocos2dx lua Script compiled into luaJIT Bytecode and encryption packaging
This scheme can better protect lua Source code , Mainly decrypt first and then decompile , Decompilation is mainly through luajit-decomp project , It will be able to luajit The bytecode is decompiled into pseudo lua Code
(3). modify cocos2dx lua In the virtual machine opcode The order of , Instruction extraction, etc
The scheme is mainly modified lua Virtual machine source code , Then, the modified virtual machine will lua Script compiled into luac Bytecode , Achieve protection lua The purpose of the source code . In this case, if you directly use the decompile tool above, you cannot luac Decompiled , It is necessary to analyze the corresponding opcode, And then modify lua Project opcode And recompile to generate decompiler , Can decompile
3.Cocos2d-x about lua Script encryption provides a lightweight solution
7、 ... and 、 Commonly used mobile game reverse analysis tools
bamen.apkGameKiller_v2.3.apkGameGuardian.8.36.1.apkCheat Engine 6.5NET.ReflectorILSpy8、 ... and 、 Reference article
Lua Reverse procedure Luac File format analysis https://www.anquanke.com/post/id/87006Lua Reverse procedure Luac Bytecode and disassembly https://www.anquanke.com/post/id/87262Lua Reverse procedure Luajit File format https://www.anquanke.com/post/id/87281
author : Almond technology station
this paper [ Mobile game safety cocos2d-x Source analysis of ( Reverse and protection of mobile games ) ] Included in Game programming ️ - Cocos, A game development favorite ~
If the picture is not displayed for a long time , Please use Chrome browser .
边栏推荐
- Vocabulary notes for postgraduate entrance examination (3)
- egg. JS project deployment online server
- Migrate data from a tidb cluster to another tidb cluster
- Restore backup data on S3 compatible storage with br
- 个人电脑好用必备软件(使用过)
- How to use information mechanism to realize process mutual exclusion, process synchronization and precursor relationship
- Analysis of pointer and array written test questions
- Bottom up - physical layer
- Summary of phased use of sonic one-stop open source distributed cluster cloud real machine test platform
- 被破解毁掉的国产游戏之光
猜你喜欢
synchronized 解决共享带来的问题
Yyds dry goods inventory three JS source code interpretation eventdispatcher

How to use information mechanism to realize process mutual exclusion, process synchronization and precursor relationship
What is the use of entering the critical point? How to realize STM32 single chip microcomputer?
2022.02.13 - NC001. Reverse linked list
面向个性化需求的在线云数据库混合调优系统 | SIGMOD 2022入选论文解读
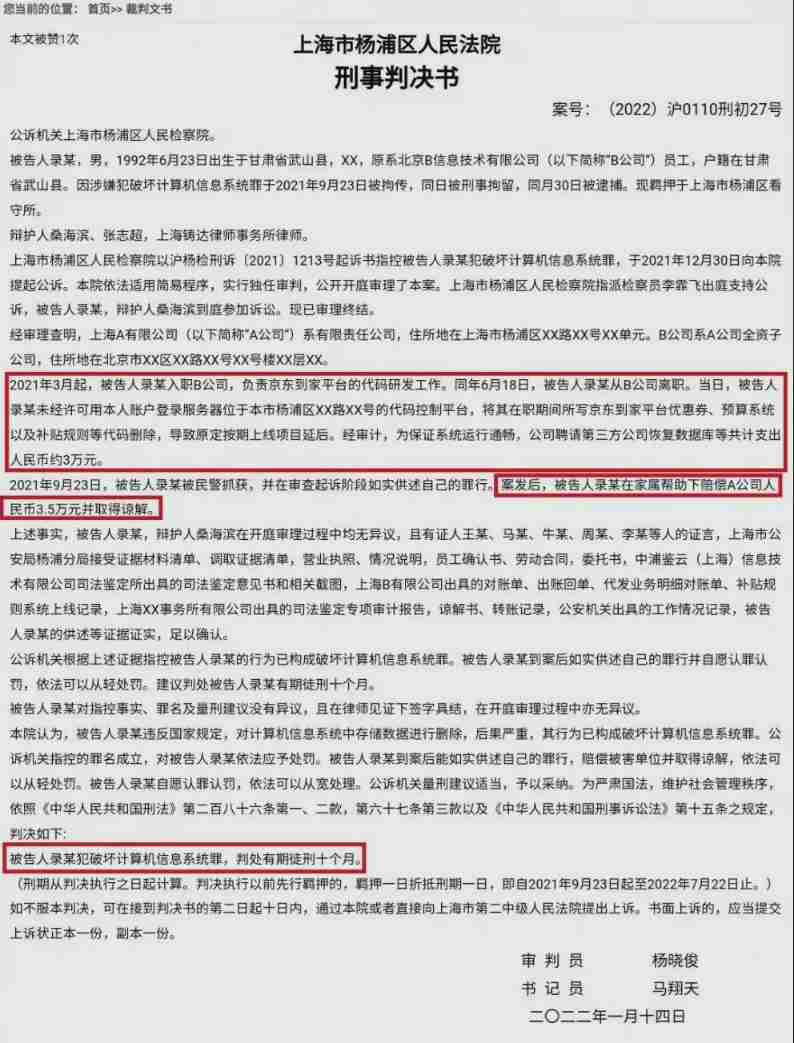
On the day of resignation, jd.com deleted the database and ran away, and the programmer was sentenced
vulnhub hackme: 1
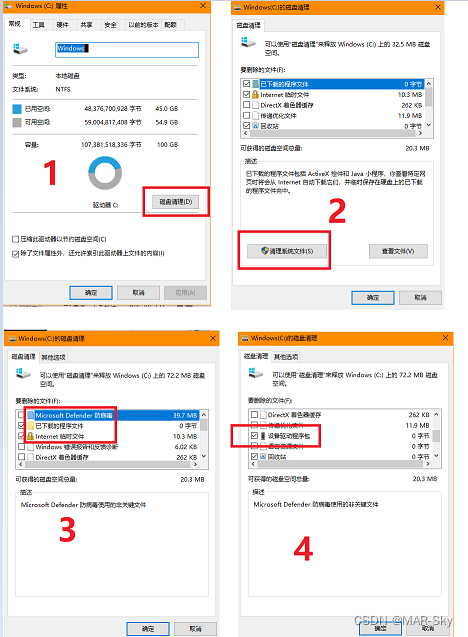
电脑清理,删除的系统文件
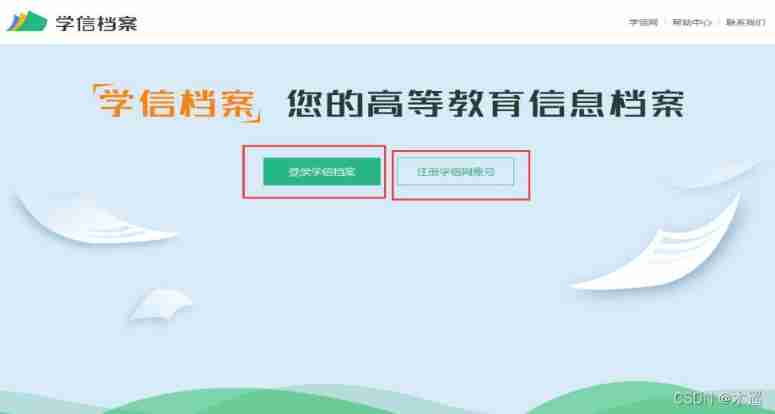
Process of obtaining the electronic version of academic qualifications of xuexin.com
随机推荐
FairGuard游戏加固:游戏出海热潮下,游戏安全面临新挑战
Introduction to backup and recovery Cr
Pyqt5 development tips - obtain Manhattan distance between coordinates
Mobile Test Engineer occupation yyds dry goods inventory
ROS编译 调用第三方动态库(xxx.so)
Ruffian Heng embedded bimonthly, issue 49
个人电脑好用必备软件(使用过)
[MySQL] lock
JS pure function
TiDB备份与恢复简介
【刷题】牛客网面试必刷TOP101
What is CSRF (Cross Site Request Forgery)?
Golang force buckle leetcode 1020 Number of enclaves
2. File operation - write
Leetcode skimming (5.29) hash table
The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
Research and investment forecast report of citronellol industry in China (2022 Edition)
Verrouillage [MySQL]
egg. JS project deployment online server
vulnhub hackme: 1