当前位置:网站首页>[interview arrangement] 0211 game engine server
[interview arrangement] 0211 game engine server
2022-07-07 22:17:00 【r1ch4rd】
List of articles
Self introduction.
Project introduction
C++
Principle and process of realizing polymorphism
1) When the compiler finds a virtual function in the base class , A virtual table is automatically generated for each class containing virtual functions , The table is a one-dimensional array , The virtual table holds the entry address of the virtual function
2) The compiler holds a virtual table pointer in the first four bytes of each object , namely vptr, Points to the virtual table of the class to which the object belongs . At tectonic time , Initialize the virtual pointer according to the type of the object vptr, So that vptr Point to the correct virtual table , So when you call a virtual function , You can find the right function
3) The so-called right time , When a derived class defines an object , The program will automatically call the constructor , Create a virtual table in the constructor and initialize the virtual table . When constructing subclass objects , The constructor of the parent class will be called first , here , The compiler only “ I saw it ” Parent class , And initialize the virtual table pointer for the parent object , Let it point to the virtual table of the parent class ; When calling the constructor of a subclass , Initialize virtual table pointer for subclass object , Let it point to the virtual table of subclasses
4) When the derived class does not override the virtual function of the base class , The virtual table pointer of the derived class points to the virtual table of the base class ; When a derived class rewrites a virtual function of a base class , The virtual table pointer of a derived class points to its own virtual table ; When a derived class has its own virtual function , Add the virtual function address to your own virtual table
So the base class pointer to the derived class at run time , Can be derived according to the virtual function rewriting dynamic call , So as to realize polymorphism .
Can a constructor be a virtual function ? Why? ?
(1) When creating an object, you need to determine the type of object , Virtual functions are dynamically typed at run time . When constructing an object , Because the object has not been created successfully , The compiler cannot know the actual type of the object
(2) Virtual function table pointer is required for calling virtual function vptr, The pointer is stored in the memory space of the object , If the constructor is declared a virtual function , So since the object has not been created , There is no memory space yet , There is no virtual function table vtable The address is used to call the dummy function
(3) The function of a virtual function is to become the member function of the subclass when it is called through the pointer or reference of the parent class . The constructor is called automatically when the object is created , It's impossible to call... Through a parent class or reference , Therefore, it is stipulated that the constructor cannot be a virtual function
C++ Memory space
- Stack
- Store local variables 、 Function parameter
- High efficiency but limited capacity
- Pile up
- Dynamic application for storage , Namely new Allocated memory
- Free storage area
- Between heap 、 Between stacks
- overall situation / Static storage area
- Store global variables and static variables
- Constant storage area
- Placement does not allow modification of constant data
- Code section
- Binary code for storing execution code
- Stack
new and malloc difference
- new Failure to allocate memory is thrown
bad_allocabnormal ,malloc Go straight back to null - new Memory allocation is dynamically computed , Allocate in free storage ; and malloc You need to specify the size , Allocate memory on the heap
- new/delete It's the operator , Can overload ;malloc/free yes C Standard library functions , Overloading is not allowed
- new/delete Encapsulates the malloc/free, Except for distribution / Free out of memory , It also calls the constructor / Destructor
- The former returns the pointer type at the time of definition , The latter returns void Type a pointer
- new Failure to allocate memory is thrown
Commonly used STL Introduce the container
map The structure of the underlying implementation
- Red and black trees ,
unordered_mapAt the bottom is the hash table
- Red and black trees ,
Characteristics of the red black tree
- First, satisfy the binary sort tree
- All nodes are either black or red
- The root node must be black
- The children of the red node must be black , But the child nodes of the black node can be black
- From roots to NULL The number of black nodes on any path of leaf nodes is the same
Self balancing strategy of red black tree ?
(1) Color change : The nodes of the red black tree change from red to black or from black to red
(2) left-handed : With A node as a fulcrum ( Rotating fulcrum ), Its right child node becomes the parent of the rotation node , The left child of the right child node becomes the right child of the rotating node , The left child node remains unchanged .
(3) Right hand : With A node as a fulcrum ( Rotating fulcrum ), The left child node becomes the parent node of the rotation node , The right child of the left child node becomes the left child of the rotating node , The right child node remains unchanged .
vector Capacity expansion
- Win+VS 1.5 times Linux+GCC 2 times
C++11 New characteristics
Introduction to smart pointer
How to write a template class
How to calculate the number of bytes of memory aligned structure in memory
computer network
- UDP and TCP difference
1、TCP Connection oriented ( If you want to make a call, dial to establish a connection );UDP It's disconnected , That is, you don't need to establish a connection before sending data
2、TCP Provide reliable service . in other words , adopt TCP Connect the transmitted data , No mistakes , No loss , No repetition , And arrive in order ;UDP Do your best to deliver , That is, there is no guarantee of reliable delivery
3、TCP Byte stream oriented , It's actually TCP Think of data as a stream of unstructured bytes ;UDP It's message oriented
UDP no congestion control , Therefore, the network congestion will not reduce the transmission rate of the source host ( Useful for real-time applications , Such as IP Telephone , Real time video conference, etc )
4、 Every one of them TCP Connections can only be point-to-point ;UDP Support one-to-one , One to many , Many to one and many to many interactive communication
5、TCP First cost 20 byte ;UDP The cost of the first part is small , Only 8 Bytes
6、TCP The logical communication channel of is a full duplex reliable channel ,UDP It's an unreliable channel
7、UDP It's message oriented , The sender's UDP For the messages handed in by the application layer , Do not merge , Do not split , Just add a header on it and give it to the network layer below , On the application layer to UDP How many messages , It sends everything , Send one at a time . And docking with the recipient , Directly remove the head after receiving , Give it to the application layer above to complete the task . therefore , It requires the application layer to control the size of the message
TCP Is oriented to a byte stream , It regards the data handed over by the upper application layer as a unstructured byte stream and sends , It can be imagined in the form of running water , The sender TCP Will put the data into “ Reservoir ”( Buffer zone ), Send when you can send , If you can't send it, just wait TCP The size of each message segment will be determined according to the current network congestion state .
- Four kinds of network programming IO Model
(1) Synchronous blocking IO(Blocking IO): Traditional IO Model .
(2) Synchronous nonblocking IO(Non-blocking IO): Created by default socket It's all blocked , Non blocking IO requirement socket Set to NONBLOCK. Pay attention to what's said here NIO Is not Java Of NIO(New IO) library .
(3)IO Multiplexing (IO Multiplexing): Classic Reactor Design patterns , Sometimes called asynchronous blocking IO,Java Medium Selector and Linux Medium epoll It's all this model .
(4) asynchronous IO(Asynchronous IO): Classic Proactor Design patterns , Also known as asynchronous non blocking IO.
- epoll ,poll and select
select At the bottom is a fd_set Data structure of , It's essentially a long An array of types , Each element in the array corresponds to a file descriptor , Check whether any event occurs by polling all file descriptors .
advantage :
1、 Good portability ;
2、 When the number of connections is small and the connections are very active , Good efficiency, too .shortcoming :
1、 The maximum number of file descriptors that can be monitored is 1024( Because the kernel is written ).
2、 Polling traversal is used to check whether there are events , When there are many file descriptors, it is expensive .- poll and select almost , It's just poll There is no maximum number of file descriptions
- epoll Is a more efficient IO The way of multiplexing , The number of file descriptors it can monitor has exceeded 1024 The limitation of ( One hundred thousand ), At the same time, there is no need to check whether there is an event on the file descriptor through polling and traversal , because epoll_wait What is returned is the file descriptor where the event occurred . It is essentially event driven .
operating system
The difference between multiprocessing and multithreading
- There are multiple threads in the same process , Threads share the memory space of the process
- Each process is the basic unit of resource allocation . The process structure consists of the following parts : Code segment 、 stack segment 、 Data segment . Code snippets are static binary code , Multiple programs can be shared . In fact, after the parent process creates the child process , Father 、 In addition to pid Outside , Almost all parts are almost the same .
pthredandstd::threaddifference- std::thread yes c++ Thread library in standard library , Its significance is that it can cross platform without changing the code
Thread private data
- Private data
- Stack
- state
- register
- Program counter
- Shared data
- Global variables
- Data on heap
- The static variable of the function
- Program code
- Open file
- Private data
gdb debugging
ask
边栏推荐
- MIT6.S081-Lab9 FS [2021Fall]
- 如何实现横版游戏中角色的移动控制
- Win11U盘不显示怎么办?Win11插U盘没反应的解决方法
- OpenGL jobs - shaders
- Time standard library
- Leetcode SQL first day
- Jerry's configuration of TWS cross pairing [article]
- Actual combat: sqlserver 2008 Extended event XML is converted to standard table format [easy to understand]
- #DAYU200体验官#MPPT光伏发电项目 DAYU200、Hi3861、华为云IotDA
- Reinforcement learning - learning notes 9 | multi step TD target
猜你喜欢
【Azure微服务 Service Fabric 】因证书过期导致Service Fabric集群挂掉(升级无法完成,节点不可用)
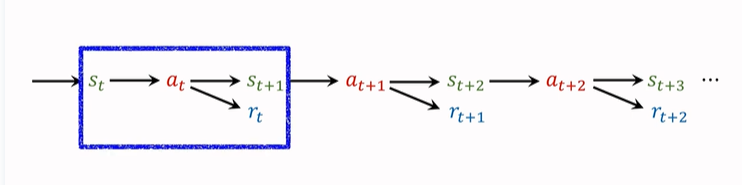
Reinforcement learning - learning notes 9 | multi step TD target
用语雀写文章了,功能真心强大!
PKPM 2020软件安装包下载及安装教程
![Jerry's about TWS channel configuration [chapter]](/img/94/fde5054fc412b786cd9864215e912c.png)
Jerry's about TWS channel configuration [chapter]
Record a garbled code during servlet learning
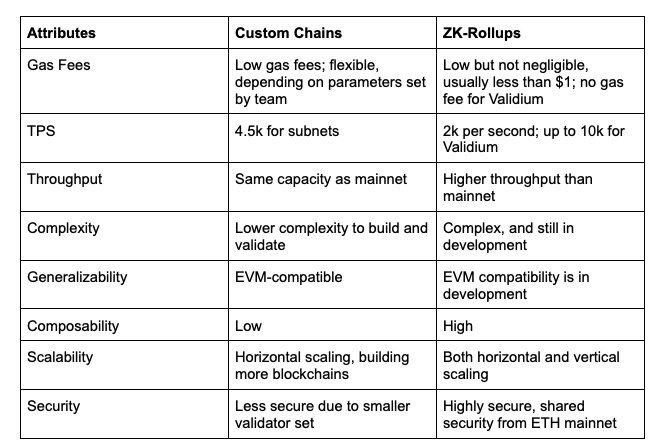
L2: current situation, prospects and pain points of ZK Rollup

Dayu200 experience officer MPPT photovoltaic power generation project dayu200, hi3861, Huawei cloud iotda
How to turn on win11 game mode? How to turn on game mode in win11
![The maximum number of meetings you can attend [greedy + priority queue]](/img/f3/e8e939e0393efc404cc159d7d33364.png)
The maximum number of meetings you can attend [greedy + priority queue]
随机推荐
The function is really powerful!
Ad domain group policy management
Oracle advanced (VI) Oracle expdp/impdp details
Jenkins user rights management
How to quickly check whether the opening area ratio of steel mesh conforms to ipc7525
648. Word replacement
[azure microservice service fabric] how to transfer seed nodes in the service fabric cluster
South China x99 platform chicken blood tutorial
Automatic classification of defective photovoltaic module cells in electronic images
【JDBC Part 1】概述、获取连接、CRUD
How does win11 time display the day of the week? How does win11 display the day of the week today?
Reinforcement learning - learning notes 9 | multi step TD target
OpenGL job - texture
Meta force force meta universe system development fossage model
Redis - basic use (key, string, list, set, Zset, hash, geo, bitmap, hyperloglog, transaction)
【colmap】稀疏重建转为MVSNet格式输入
PKPM 2020软件安装包下载及安装教程
Cv2.resize function reports an error: error: (-215:assertion failed) func= 0 in function ‘cv::hal::resize‘
Code of "digital image processing principle and Practice (matlab version)" part2[easy to understand]
Actual combat: sqlserver 2008 Extended event XML is converted to standard table format [easy to understand]