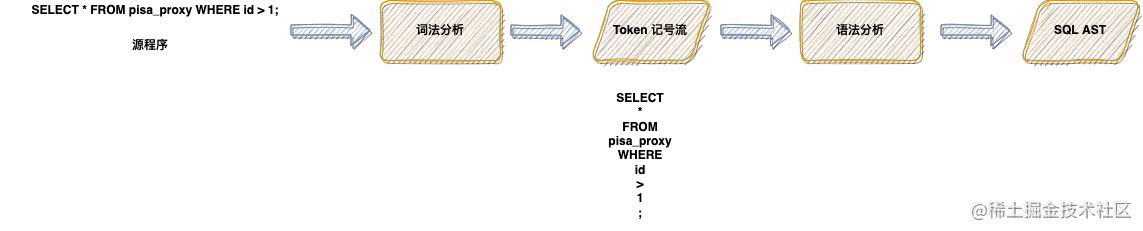
当前位置:网站首页>Jenkins user rights management
Jenkins user rights management
2022-07-07 21:25:00 【Cloud computing security】

Jenkins edition :2.332.3
Catalog
One 、 Installing a plug-in
1.1 install
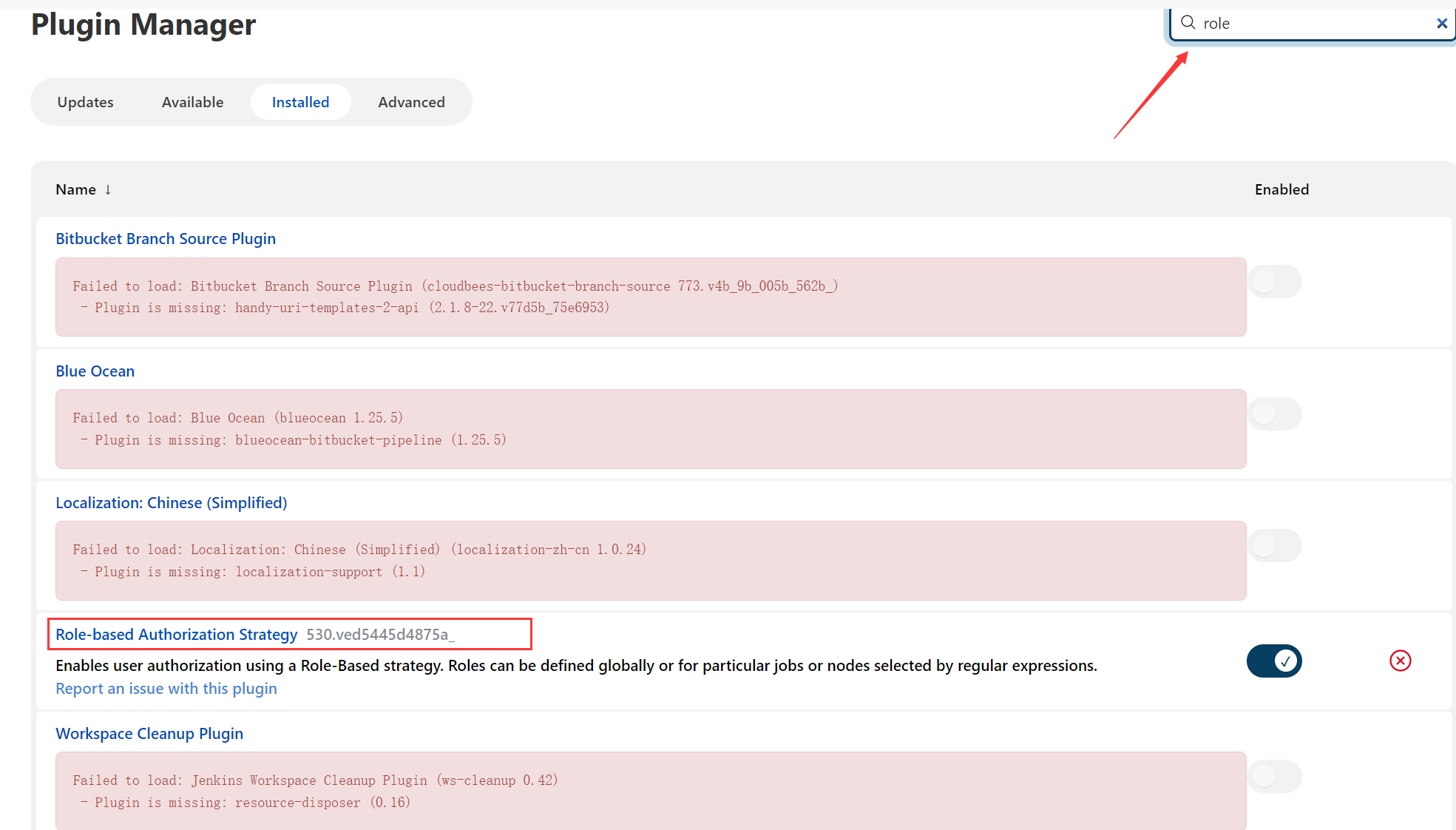
stay Jenkins Install the plug-in in the management plug-in of
Input Role You can find it , As shown in the figure below, I have already installed .
1.2 To configure
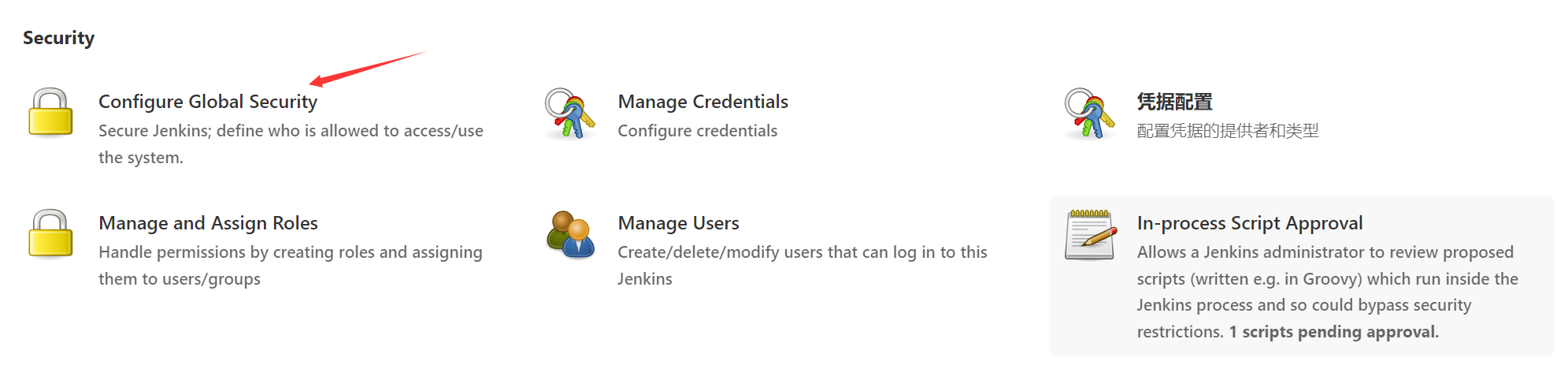
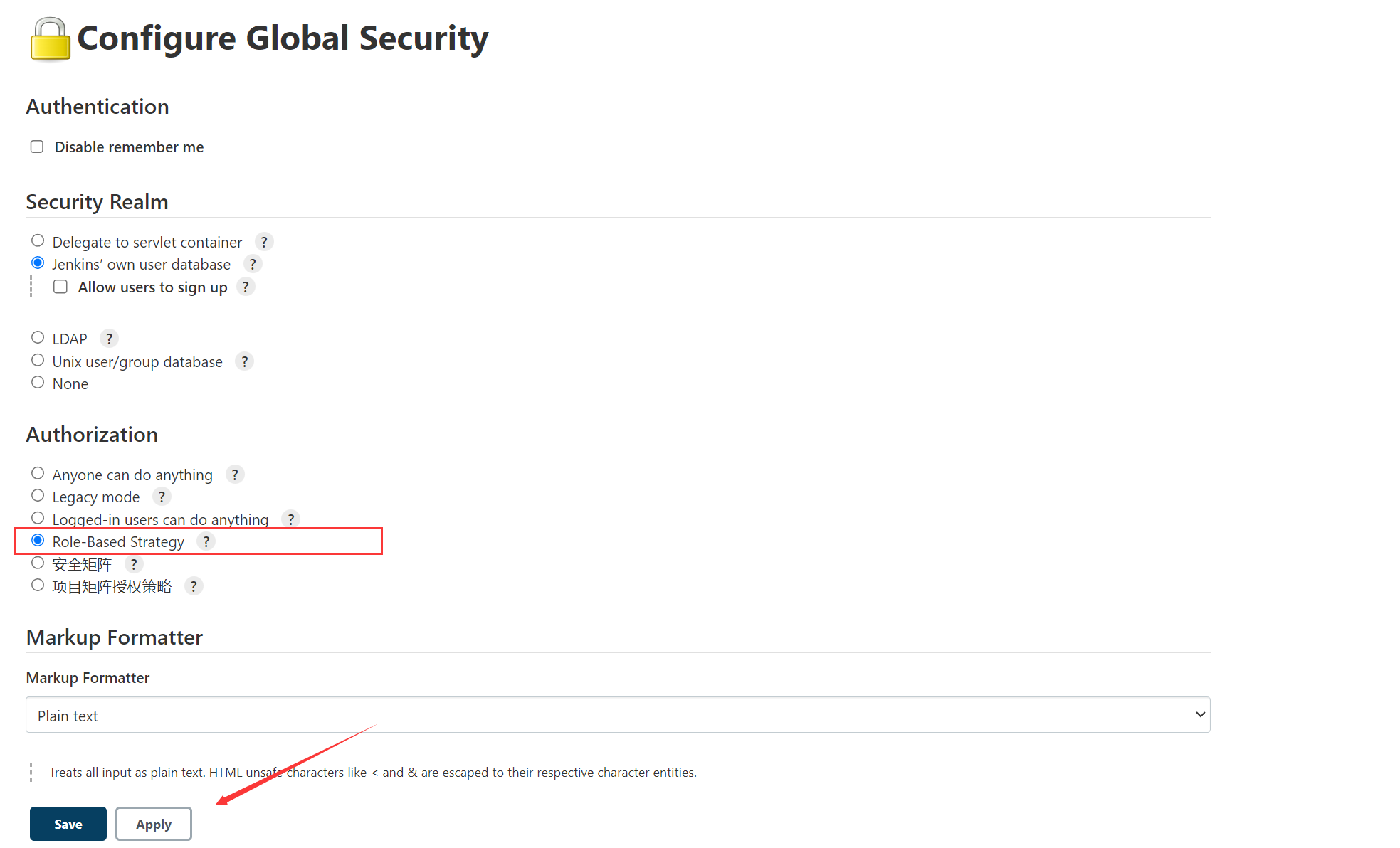
Click on Configure Global Security Enter the configuration
1、 stay Jenkins The following icons are found in the settings
2、 Select the plug-in just installed as my user permission
Two 、 Create the role
2.1 Plug in features
stay Jenkins Found under settings Manage and Assign Roles And click into
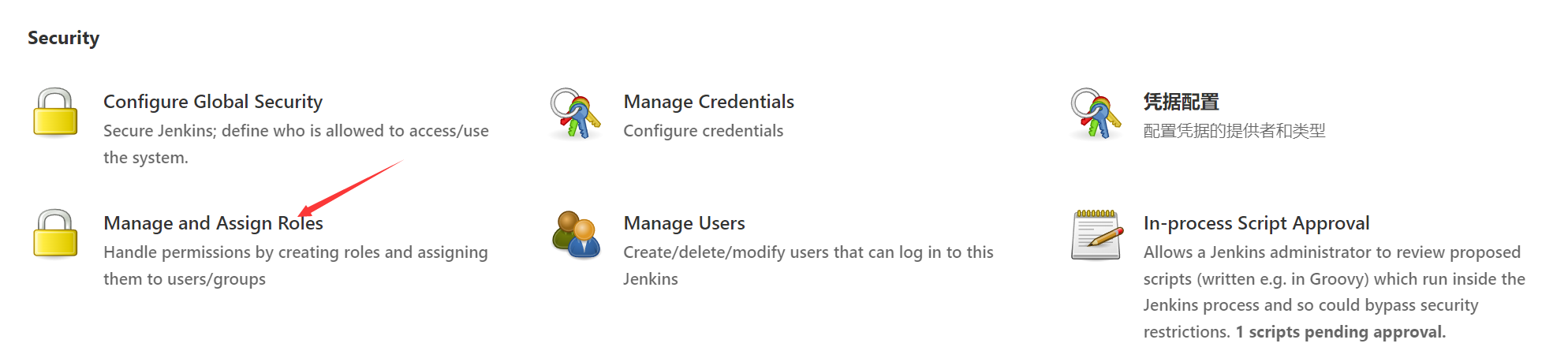
The main function :

2.2 Role management
1、 Click on the image above Manage Roles Enter role management
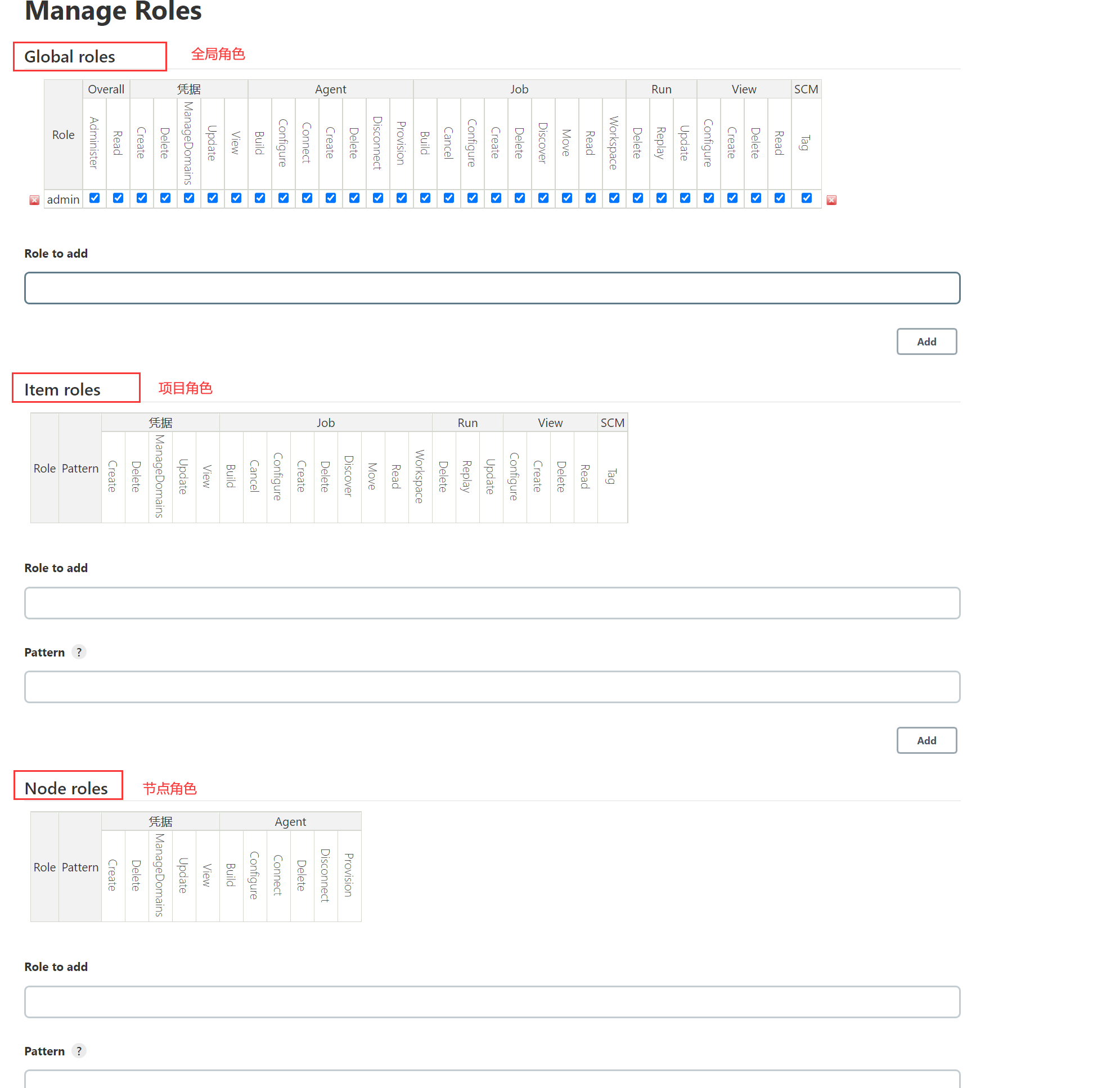
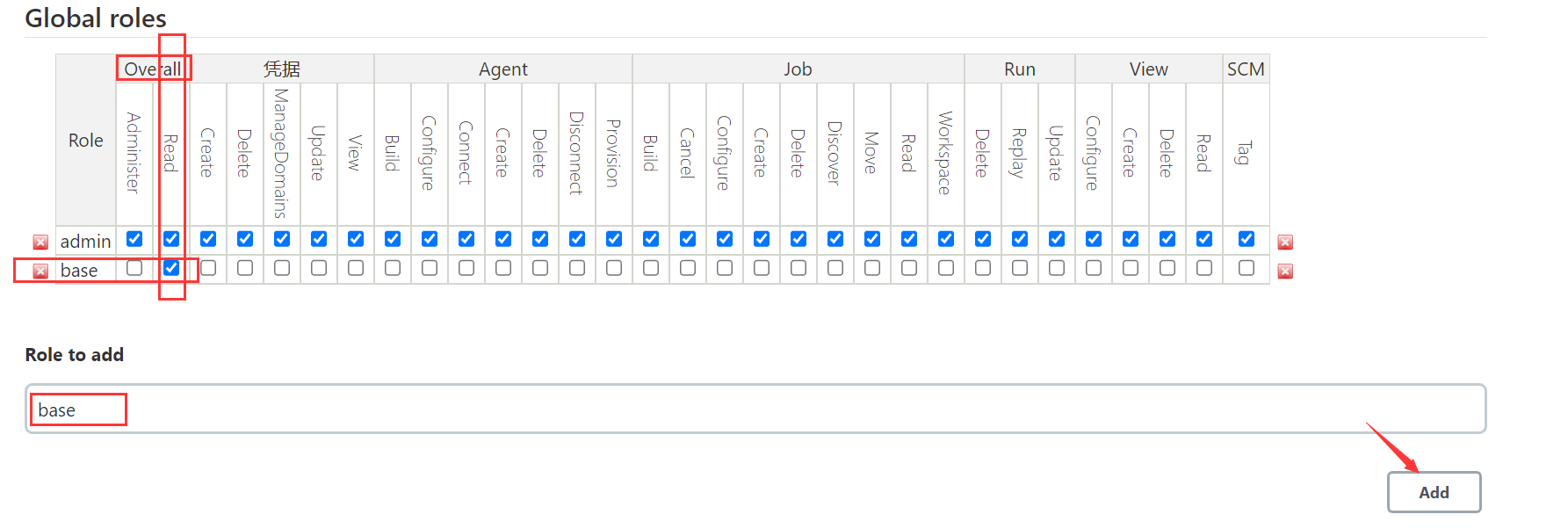
2、 Create a global role
Create a file called base The global role of , This role can be used as the basic permission of all users , That is, all ordinary users have basic permissions , And give the character Overall Under the Read jurisdiction .
 3、 Create project roles
3、 Create project roles
Create a file called shop Project role of ,Pattern For filtering or matching regular expression items ,cms.* Said to cms The first item will be matched to , After setting up , Assign corresponding permissions to the project role .
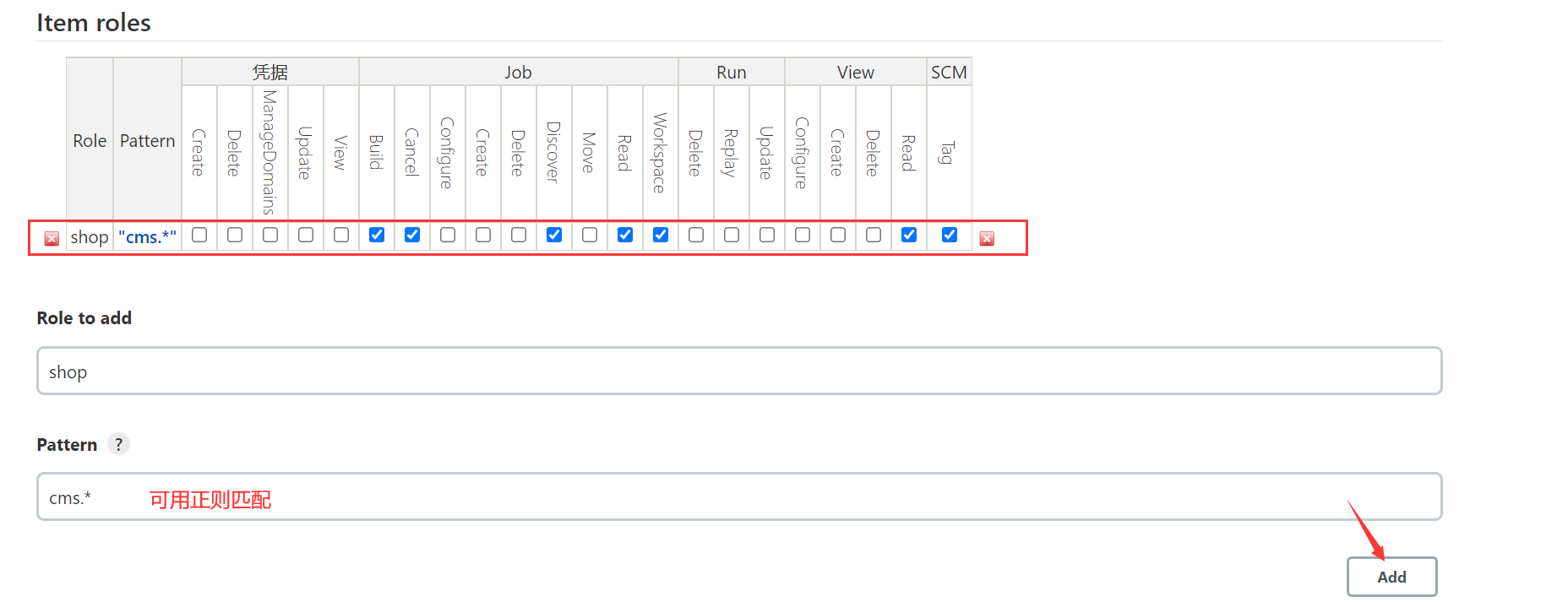
Pattern Can match the job (job)、 agent (agents)、 Folder (folders) And other project keywords and types .
The format is :jobs, agents, folders, etc If there are more than one , Use commas in English "," Just separate .
4、 Create node roles
Node role is mainly used for master-slave Jenkins When the deployment , Configure node permissions .
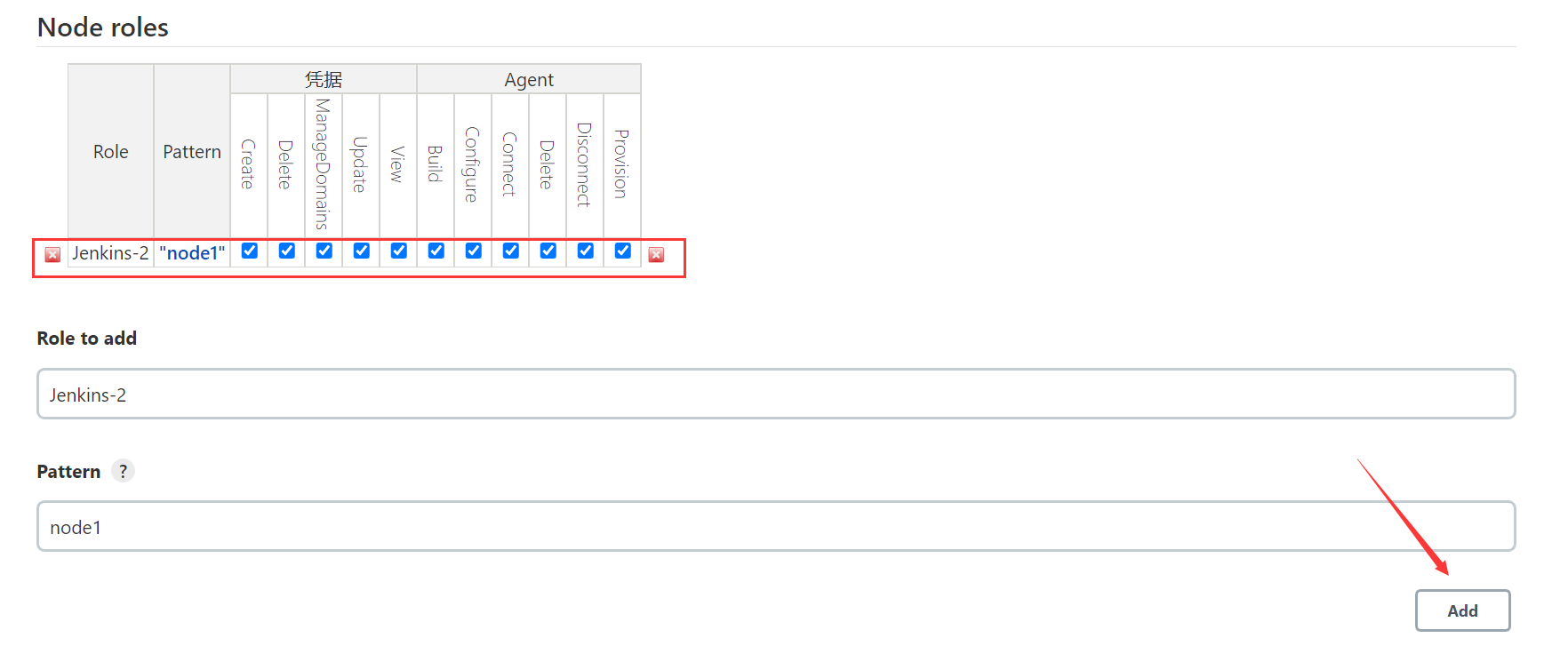
2.3 Role assignment
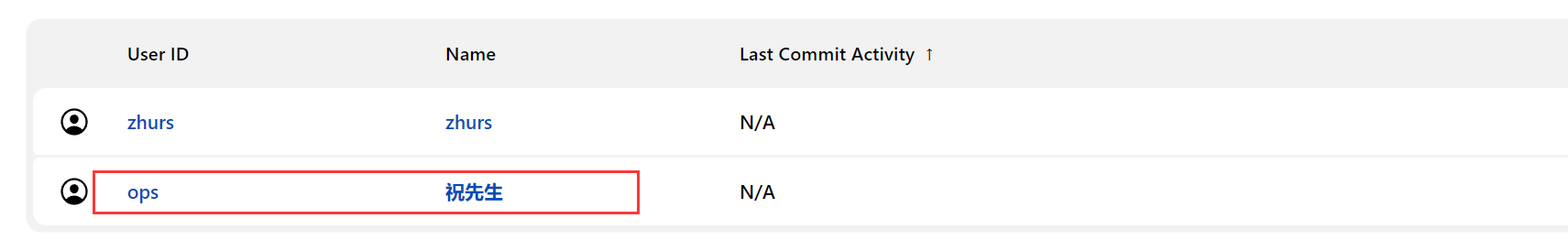
1、 Create user
2、 Click on Assign Roles Assign permissions to users
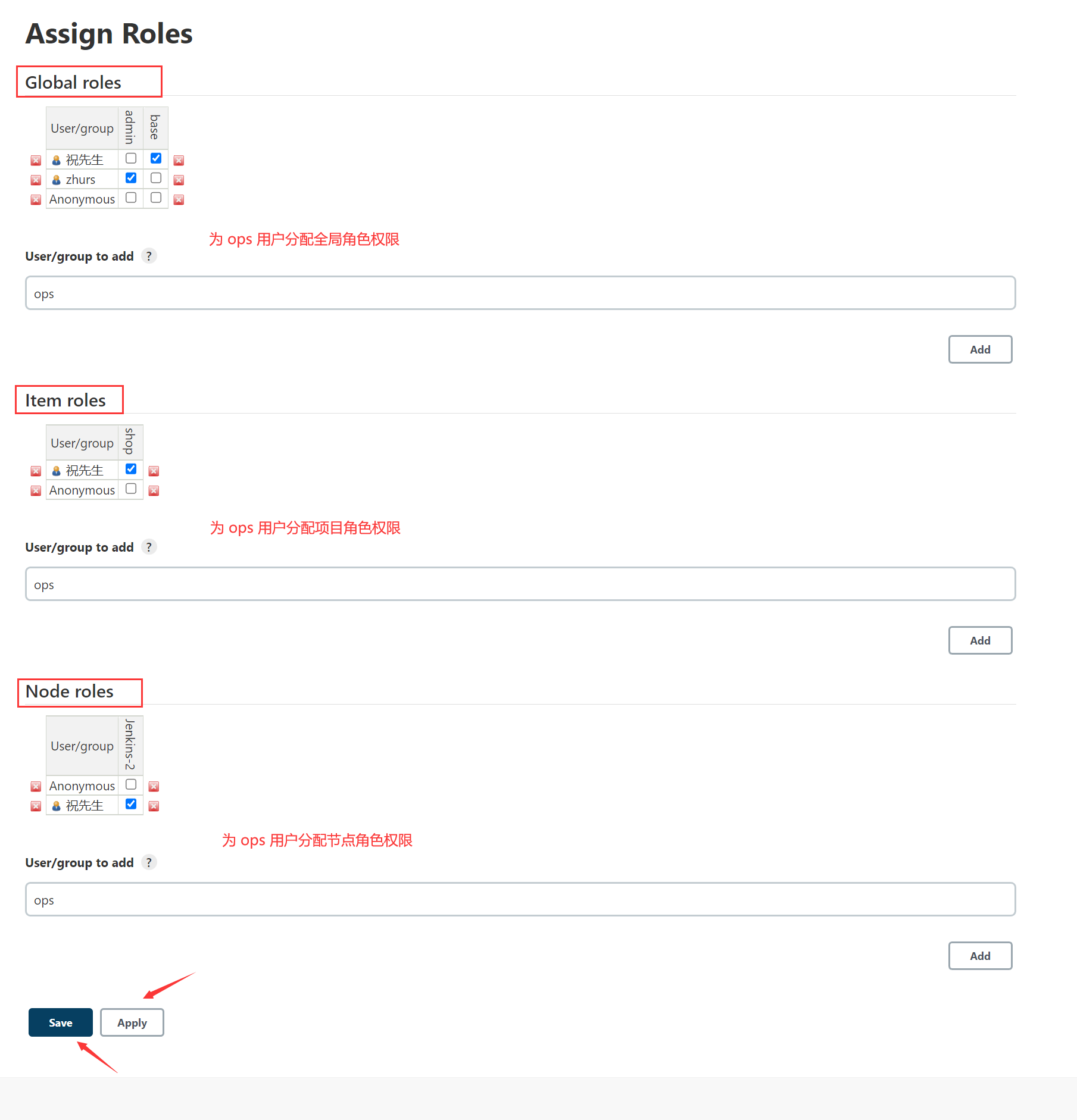
Follow the project role permissions configured above ,ops Users can only match with cms The opening project , He can't see other projects , Next, we will verify .
3、ops User login authentication
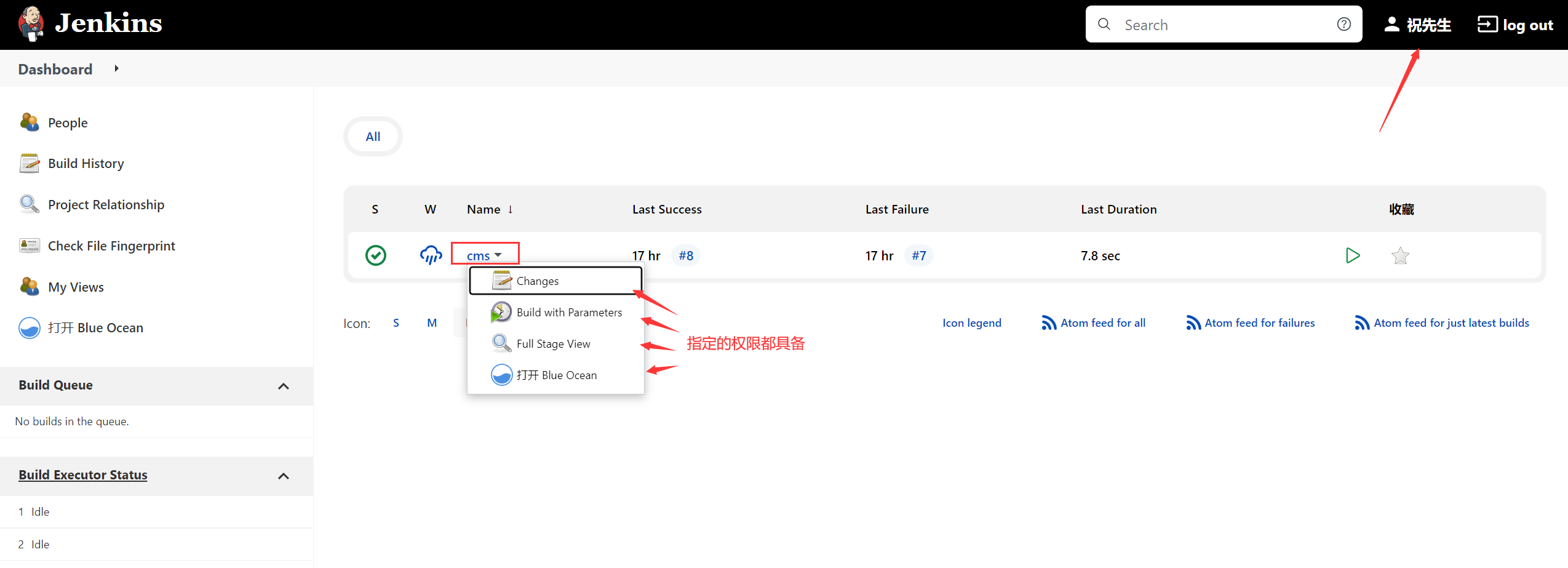
thus ,Jenkins User permissions are set !
边栏推荐
- C language helps you understand pointers from multiple perspectives (1. Character pointers 2. Array pointers and pointer arrays, array parameter passing and pointer parameter passing 3. Function point
- [200 opencv routines] 223 Polygon fitting for feature extraction (cv.approxpolydp)
- How to meet the dual needs of security and confidentiality of medical devices?
- Codeforces 474 F. Ant colony
- Is it safe to open an account of BOC shares in kainiu in 2022?
- Is private equity legal in China? Is it safe?
- Demon daddy A3 stage near normal speed speech flow initial contact
- Details of C language integer and floating-point data storage in memory (including details of original code, inverse code, complement, size end storage, etc.)
- 万字总结数据存储,三大知识点
- Codeforces 474 F. Ant colony
猜你喜欢

程序猿赚的那点钱算个P啊!

How does codesonar help UAVs find software defects?
Lex & yacc of Pisa proxy SQL parsing
AADL inspector fault tree safety analysis module

Goal: do not exclude yaml syntax. Try to get started quickly
Virtual machine network configuration in VMWare
![Is embedded system really safe? [how does onespin comprehensively solve the IC integrity problem for the development team]](/img/af/61b384b1b6ba46aa1a6011f8a30085.png)
Is embedded system really safe? [how does onespin comprehensively solve the IC integrity problem for the development team]

【OpenCV 例程200篇】223. 特征提取之多边形拟合(cv.approxPolyDP)
Mysql子查询关键字的使用方式(exists)
H3C s7000/s7500e/10500 series post stack BFD detection configuration method
随机推荐
DataTable数据转换为实体
Implementation of mahout Pearson correlation
【C语言】指针进阶---指针你真的学懂了吗?
Make this crmeb single merchant wechat mall system popular, so easy to use!
Demon daddy B3 read extensively in a small amount, and completed 20000 vocabulary+
Devil daddy B1 hearing the last barrier, break through with all his strength
Implement secondary index with Gaussian redis
Small guide for rapid formation of manipulator (11): standard nomenclature of coordinate system
Is it safe to open an account of BOC shares in kainiu in 2022?
现在网上开户安全么?想知道我现在在南宁,到哪里开户比较好?
Codeforces round 275 (Div. 2) C – diverse permutation (construction) [easy to understand]
Introduction to referer and referer policy
MySQL storage expression error
国家正规的股票交易app有哪些?使用安不安全
华泰证券可以做到万一佣金吗,万一开户安全嘛
恶魔奶爸 A0 英文零基础的自我提升路
恶魔奶爸 A1 语音听力初挑战
寫一下跳錶
Cantata9.0 | new features
SQL注入报错注入函数图文详解