当前位置:网站首页>ISO 26262 - considerations other than requirements based testing
ISO 26262 - considerations other than requirements based testing
2022-07-07 21:18:00 【Maihexong】
 With the development of automatic driving technology , Our travel and transportation have also become more convenient , But at the same time, the safety and reliability of automotive electronic system are also facing unprecedented challenges . Vehicle functional safety standards ISO 26262 In this environment and demand, it came into being , And according to ISO 262626 The demand for software development based on standards is also increasing . In the preparation and design phase , In addition to understanding that dynamic testing should meet ISO 26262 Beyond requirements based testing , What else do we need to know ?
With the development of automatic driving technology , Our travel and transportation have also become more convenient , But at the same time, the safety and reliability of automotive electronic system are also facing unprecedented challenges . Vehicle functional safety standards ISO 26262 In this environment and demand, it came into being , And according to ISO 262626 The demand for software development based on standards is also increasing . In the preparation and design phase , In addition to understanding that dynamic testing should meet ISO 26262 Beyond requirements based testing , What else do we need to know ?
This course will mainly introduce in addition to requirements based testing ,ISO 26262 Requirements in the objectives and test process of unit and integration testing . The course covers how to validate control flow and data flow 、 Equivalent division 、 Boundary value and structured code coverage technology and interface testing 、 Fault injection test and resource usage test technology are combined for application , At the end of the course, we will also share demonstration cases with you .
One 、 Course time :
2020 year 7 month 1 Japan ( Wednesday )【19:30-20:30】
Two 、 The keynote speaker :
As a unit test and integration test expert , For more than 20 years Matt Davis Develop embedded unit and integration test solutions for a large number of customers in business and security critical fields , And recognized by customers all over the world . He has rich experience in software testing , He has made many speeches at international conferences on software certification and standard compliance .
3、 ... and 、 Highlights of the course :
1、 After the course, you can review the recording screen online , Watch review at any time .
2、 Establish an exclusive wechat group , After the course, you can have a long-term interactive discussion .
3、 The courseware materials can be packaged for free .
Four 、 Syllabus :
1、 Evaluate the analysis and verification of control flow and data flow
2、 Compare interface tests , Various techniques of fault injection testing and resource usage testing
3、 The techniques of equivalent division and boundary value analysis are explained , And the testing framework supporting these technologies
4、 It lists some challenges in the application of structured code coverage requirements . It is discussed that using software testing tools should Need confidence and requirements for tool suppliers
5、 A practical demonstration of applying fault injection technology through interface interception test in hardware loop is given .
边栏推荐
- easyui 日期控件清空值
- A brief understanding of the in arc__ bridge、__ bridge_ Retained and__ bridge_ transfer
- object-c编程tips-timer「建议收藏」
- Hoj 2245 planktonic triangle cell (Mathematics)
- DataTable数据转换为实体
- Guava multithreading, futurecallback thread calls are uneven
- Deadlock conditions and preventive treatment [easy to understand]
- SQL注入报错注入函数图文详解
- How to meet the dual needs of security and confidentiality of medical devices?
- Small guide for rapid formation of manipulator (12): inverse kinematics analysis
猜你喜欢
Make this crmeb single merchant wechat mall system popular, so easy to use!
![[paper reading] maps: Multi-Agent Reinforcement Learning Based Portfolio Management System](/img/76/b725788272ba2dcdf866b28cbcc897.jpg)
[paper reading] maps: Multi-Agent Reinforcement Learning Based Portfolio Management System

程序猿赚的那点钱算个P啊!
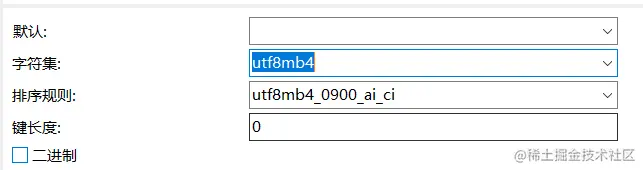
MySQL storage expression error
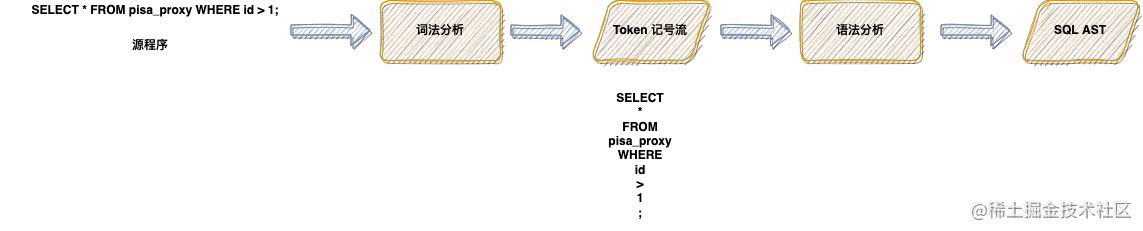
Lex & yacc of Pisa proxy SQL parsing
SQL注入报错注入函数图文详解

How to meet the dual needs of security and confidentiality of medical devices?

Codesonar Webinar
Apifox interface integrated management new artifact

Onespin | solve the problems of hardware Trojan horse and security trust in IC Design
随机推荐
Data sorting in string
Demon daddy guide post - simple version
Phoenix JDBC
【矩阵乘】【NOI 2012】【cogs963】随机数生成器
反诈困境,国有大行如何破局?
Introduction to referer and referer policy
openGl超级宝典学习笔记 (1)第一个三角形「建议收藏」
npm uninstall和rm直接删除的区别
Alibaba cloud award winning experience: how to mount NAS file system through ECS
Codeforces round 275 (Div. 2) C – diverse permutation (construction) [easy to understand]
Default constraint and zero fill constraint of MySQL constraint
论文解读(ValidUtil)《Rethinking the Setting of Semi-supervised Learning on Graphs》
Guava multithreading, futurecallback thread calls are uneven
MinGW MinGW-w64 TDM-GCC等工具链之间的差别与联系「建议收藏」
GridView defines its own time for typesetting "suggestions collection"
FatMouse' Trade (Hangdian 1009)
POJ 3140 contents division "suggestions collection"
Is it safe to open an account online now? I want to know where I can open an account in Nanning now?
How to choose financial products? Novice doesn't know anything
Tensorflow2. How to run under x 1 Code of X