当前位置:网站首页>Use byte stream to read Chinese from file to console display
Use byte stream to read Chinese from file to console display
2022-07-05 17:01:00 【Oh-liuxing】
package text;
import java.io.FileInputStream;
import java.io.IOException;
public class FileInputStreamDemo06 {
public static void main(String[] args) throws IOException {
FileInputStream fis = new FileInputStream("D:\\a.txt");
int len;
byte[] bytes = new byte[70];
while ((len = fis.read(bytes)) != -1) {
System.out.print(new String(bytes, 0, len, "gbk"));
}
fis.close();
}
}
Tips :idea By default utf-8 Coded ,utf-8 code 1 Chinese accounts for 3 Bytes ,gbk code 1 Chinese accounts for 2 Bytes . Using byte stream to read Chinese data adopts the method of reading one byte at a time , So what you read is garbled . When we use Notepad to store Chinese, the default is ANSI code , In fact, that is GBK code
边栏推荐
- Precision epidemic prevention has a "sharp weapon" | smart core helps digital sentinels escort the resumption of the city
- 关于new Map( )还有哪些是你不知道的
- Etcd build a highly available etcd cluster
- 【剑指 Offer】61. 扑克牌中的顺子
- "21 days proficient in typescript-3" - install and build a typescript development environment md
- [Jianzhi offer] 61 Shunzi in playing cards
- PHP人才招聘系统开发 源代码 招聘网站源码二次开发
- Global Data Center released DC brain system, enabling intelligent operation and management through science and technology
- Jarvis OJ simple network management protocol
- How does win11 change icons for applications? Win11 method of changing icons for applications
猜你喜欢

【 brosser le titre 】 chemise culturelle de l'usine d'oies
![[729. My Schedule i]](/img/e3/32914227d00cf7595ee850e60f2b72.png)
[729. My Schedule i]
![[729. My schedule I]](/img/e3/32914227d00cf7595ee850e60f2b72.png)
[729. My schedule I]

American chips are no longer proud, and Chinese chips have successfully won the first place in emerging fields
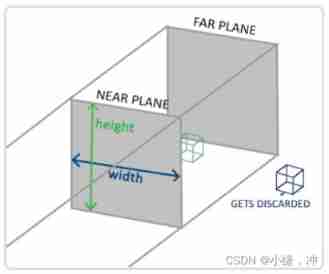
Learnopongl notes (I)
How to set the WiFi password of the router on the computer
WSL2.0安装

二叉树相关OJ题

采用药丸屏的iPhone14或引发中国消费者的热烈抢购
Domestic API management artifact used by the company
随机推荐
Bs-xx-042 implementation of personnel management system based on SSM
Detailed explanation of use scenarios and functions of polar coordinate sector diagram
Sentinel-流量防卫兵
Accès aux données - intégration du cadre d'entité
Practical example of propeller easydl: automatic scratch recognition of industrial parts
Global Data Center released DC brain system, enabling intelligent operation and management through science and technology
Benji Bananas 会员通行证持有人第二季奖励活动更新一览
Jarvis OJ 远程登录协议
[brush title] goose factory shirt problem
微信公众号网页授权登录实现起来如此简单
C# TCP如何设置心跳数据包,才显得优雅呢?
二叉树相关OJ题
DenseNet
关于new Map( )还有哪些是你不知道的
如何安装mysql
How was the middle table destroyed?
为季前卡牌游戏 MotoGP Ignition Champions 做好准备!
Etcd build a highly available etcd cluster
采用药丸屏的iPhone14或引发中国消费者的热烈抢购
网站页面禁止复制内容 JS代码