当前位置:网站首页>The learning path of a network security mouse - the basic use of nmap
The learning path of a network security mouse - the basic use of nmap
2022-08-02 04:01:00 【Learn Safe Tom Cat】
文章目录
简介
nmap是用来探测计算机网络上的主机和服务的一种安全扫描器.为了绘制网络拓扑图,Nmap的发送特制的数据包到目标主机,然后对返回数据包进行分析.Nmap是一款枚举和测试网络的强大工具.
基础学习
基本操作
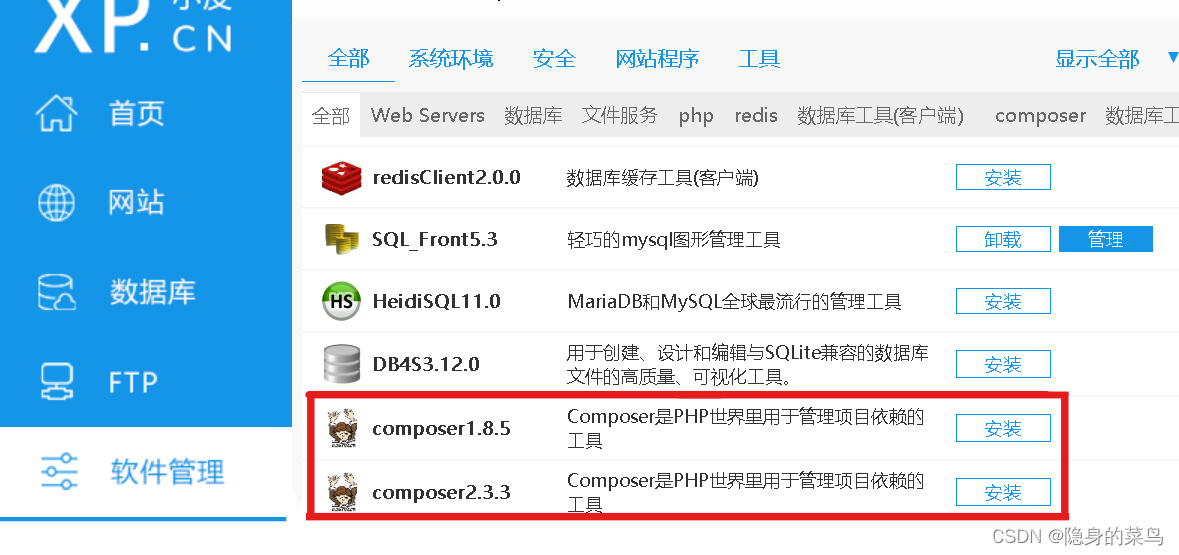
Nmap 192.168.36.131(Here is the target computerIP地址)
NmapThe default is to send onearp的ping数据包,来探测目标主机1-10000Ports open in the range.
Verbose output scan—— V
Nmap -V 192.168.36.131(Here is the target computerIP地址)
Simple scans only describe the output of the replaced results,加上参数-V,The progress of the scan can be seen and the percentage can be seen,It won't be so boring.
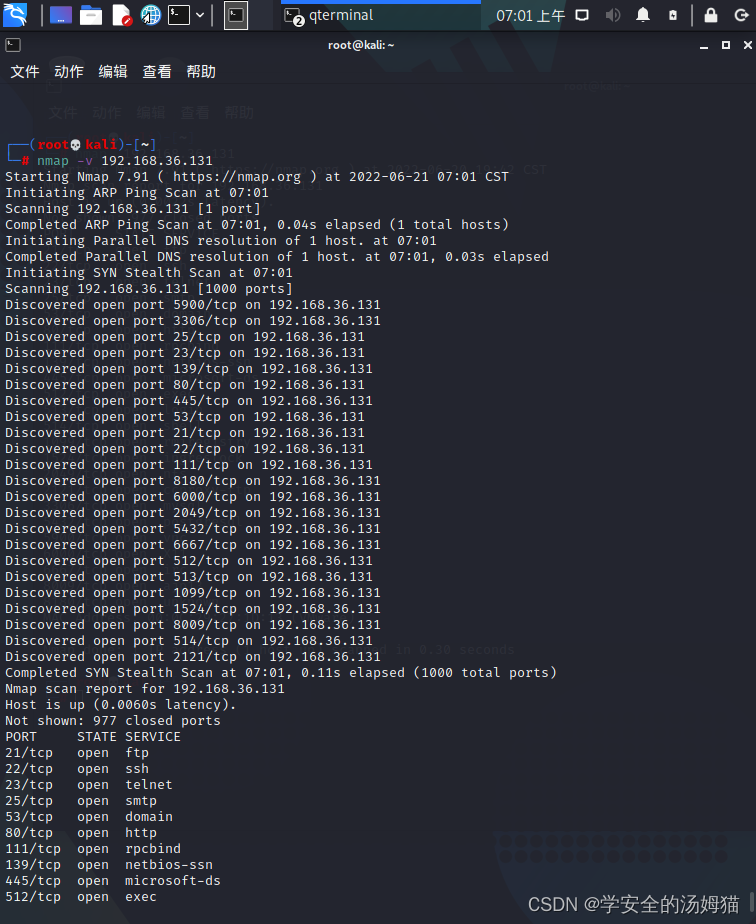
Specify port scans and port range scans——p
Nmap -p- 192.168.36.131(扫描1-65535)
Nmap -p 80,445,8080 192.168.36.131 (仅扫描80,445,8080端口)
NmapThe default is to scan the target machine1-10000端口,通过参数-pCan be the port to set scan

(加-p-和没加-p的区别)
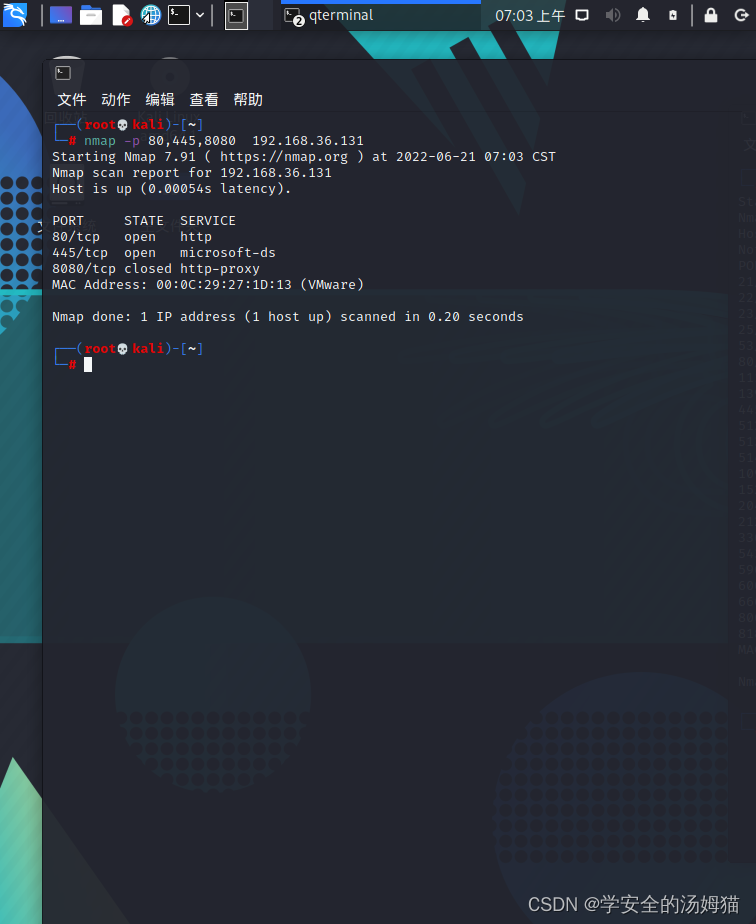
(指定80,445,8080端口)
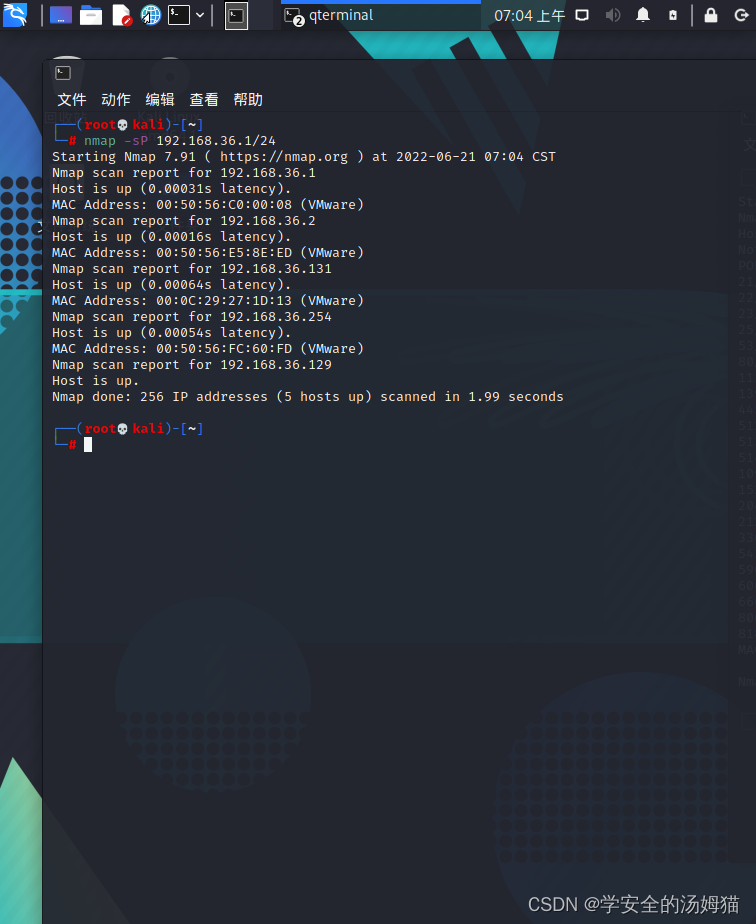
Ping扫描——sP
Nmap -sP 192.168.36.1/24
使用icmppackage to do intranet host discovery
No ping扫描——PN
Nmap -PN 192.168.36.131
使用-PN参数可以绕过ping命令,但是不影响主机的系统的发现.
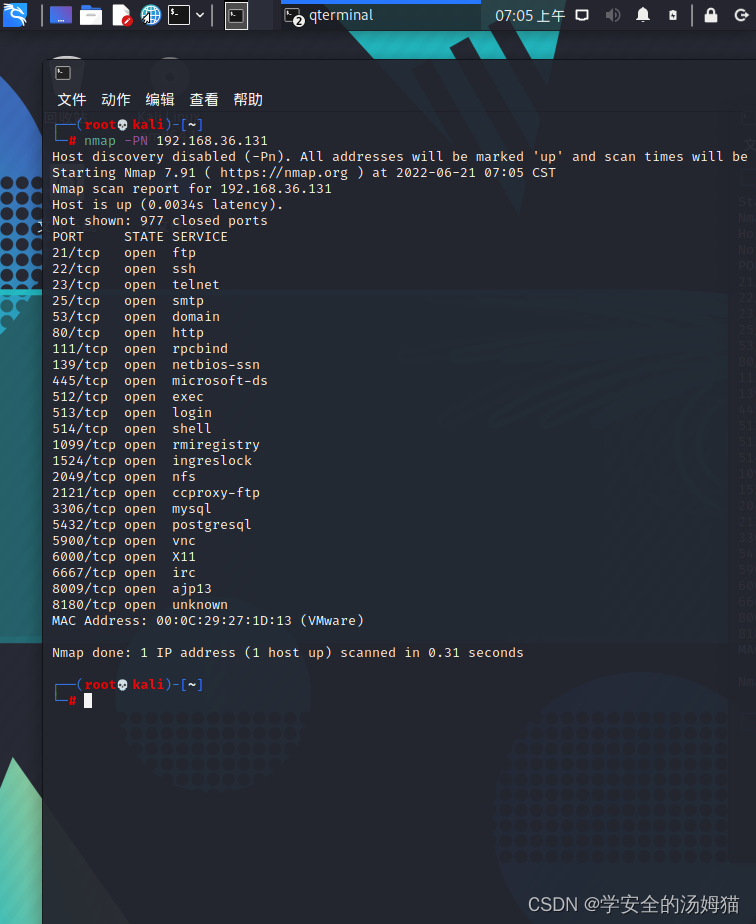
SYN半开放扫描——sS
Nmap -sS 192.168.36.131
Nmap发送SYN包到远程主机,但是它不会产生任何会话.因此不会在目标主机上产生任何日志记录.This also further ensures that ports are not swamped by scanning
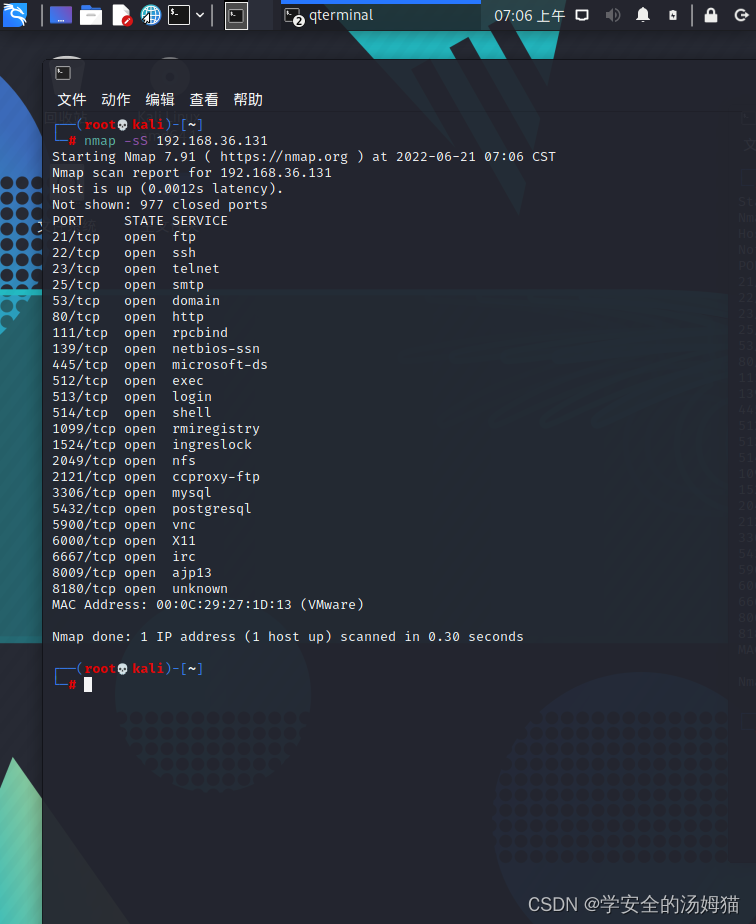
TCP扫描——sT
Nmap -sT 192.168.36.131
使用tcp协议扫描,需要完成三次握手
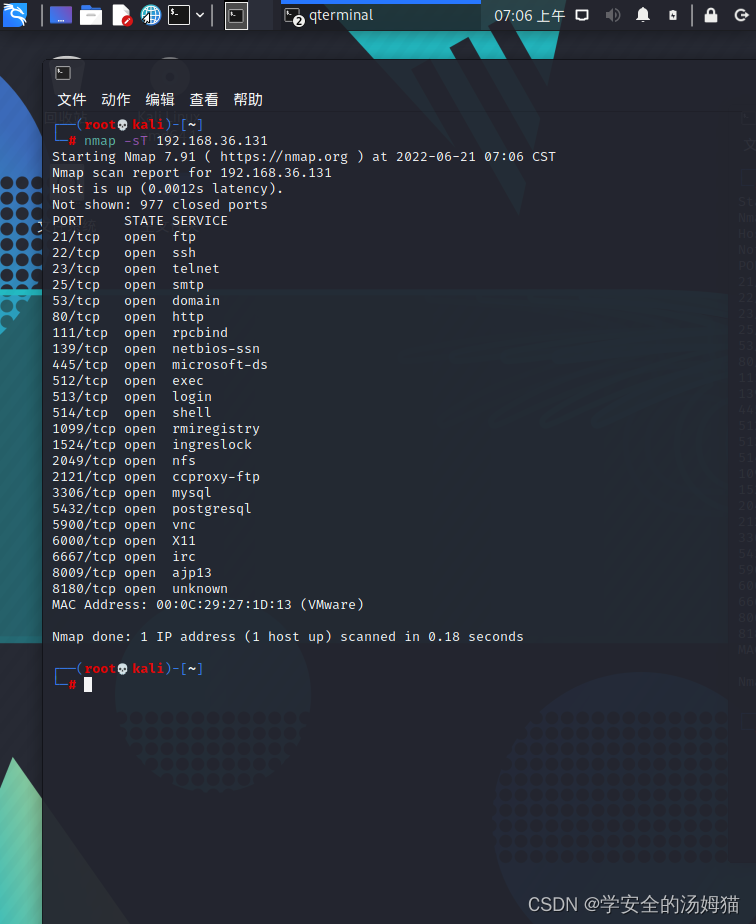
UDP扫描——sU
Nmap -sU -p53 192.168.36.131
这种扫描技术用来寻找目标主机打开的UDP端口
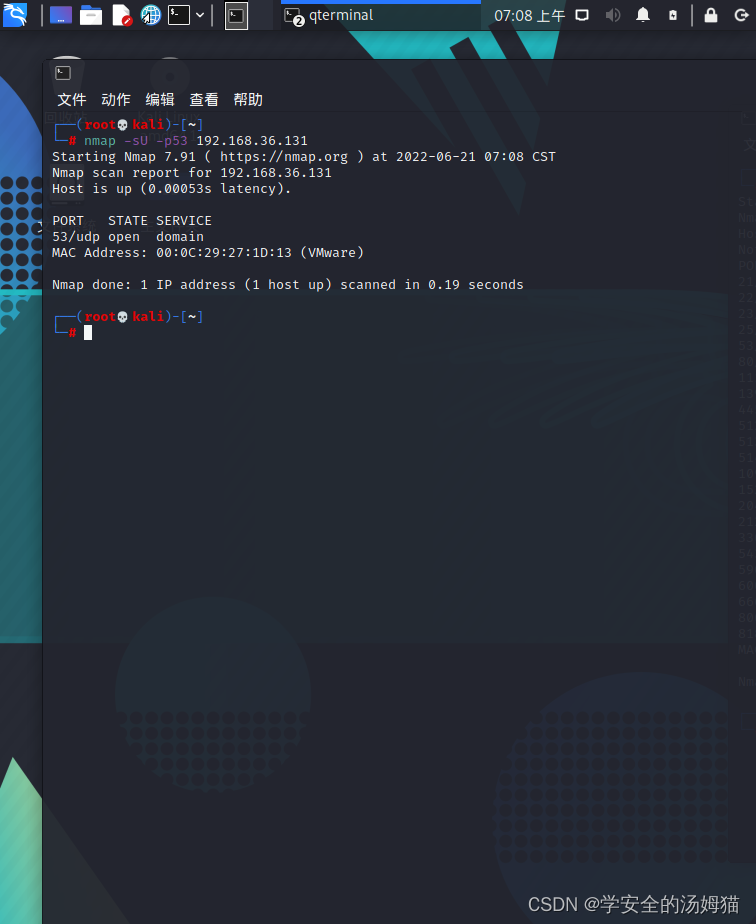
This is because there are many ports on my target machine,If all scans take too long,所以我这里使用-p参数,仅对53端口进行udp扫描
Detection scan for service version numbers——sV
Nmap -sV 192.168.36.131
Used to check the version numbers of hosts and services on the target

操作系统的探测——O
Nmap -O 192.168.36.132
NmapThe system detection technique is very useful in penetration testing to understand the operating system and software of a remote host,Known vulnerabilities are known from the information obtained.

设置时间模板——T
Nmap -T4 192.168.36.131
Nmap提供了6个时间模板,使用时采用-T选项及数字(0 - 5) 或名称.模板名称有paranoid (0)、sneaky (1)、polite (2)、normal(3)、 aggressive (4)和insane (5)
- paranoid、sneaky模式用于IDS躲避
- Polite模式降低了扫描 速度以使用更少的带宽和目标主机资源.
- Normal为默认模式,因此-T3 实际上是未做任何优化.
- Aggressive模式假设用户具有合适及可靠的网络从而加速 扫描
- nsane模式假设用户具有特别快的网络或者愿意为获得速度而牺牲准确性.
这里是引用

综合性扫描——A
Nmap -A -T5 192.168.36.131
Scan the entire contents of the target drone,就是有点费时间,这里我加了-Tparameters to speed up the scan time

内容太多,Not all are put here
网段扫描格式
nmap -sP 192.168.36.1/24 (/扫描C段网络 ,24 代表的24That is, the subnet mask255.255.255.0)
There are actually a lot of spellings here,常用的命令

Here I just recommend using it-sP 进行主机发现,And I just recommend scanningC段的网络,Bparagraph,That speed is not ordinary slow
总结
I'm just talking about some of the parameters I commonly use here,nmap的参数不少,You can continue to dig
The above is my personal understanding,不喜勿喷,Please point out any mistakes.
边栏推荐
猜你喜欢
随机推荐
[symfony/mailer]一个优雅易用的发送邮件类库
3.PHP数据类型、常量、字符串和运算符
(2)Thinkphp6模板引擎**标签
CTF入门之md5
Alfa: 1 vulnhub walkthrough
PHP反序列化漏洞
[sebastian/diff] A historical change extension library for comparing two texts
DarkHole: 2 vulnhub walkthrough
(1) introduction to Thinkphp6, installation view, template rendering, variable assignment
(6) Design of student information management system
[campo/random-user-agent] Randomly fake your User-Agent
Basic use of v-on, parameter passing, modifiers
After the mailbox of the Pagoda Post Office is successfully set up, it can be sent but not received.
php函数漏洞总结
3. PHP data types, constants, strings and operators
vim编辑模式
CTF-网鼎杯往届题目
(2) 顺序结构、对象的布尔值、选择结构、循环结构、列表、字典、元组、集合
PHP入门(自学笔记)
VIKINGS: 1 vulnhub walkthrough




![[league/climate]一个功能健全的命令行功能操作库](/img/ce/39114b1c74af649223db97e5b0e29c.png)