当前位置:网站首页>Hackmyvm target series (4) -vulny
Hackmyvm target series (4) -vulny
2022-07-06 13:57:00 【The moon should know my meaning】
One 、 information gathering
The old , Let's start with a wave of network segment scanning , Discover the host
nmap -sP 192.168.200.0/24 | grep -i -B 2 virtualbox
Use nmap Scan port , Two ports were found , One 80 port , One 33060( I don't know what it is , No matter it first )
nmap -sC -sV 192.168.200.153 -p-
Visit the home page , However, no useful information was found .

The old , Let's start with a wave of directory scanning , See if you can find any useful information .
Use gobuster Scan the directory .
gobuster dir -u http://192.168.200.153 -w directory-list-2.3-medium.txt -t 30 -x php,html,txt,7z,zip,bak,gz
Found several directories and files , After visiting , Only secret The directory is useful .
Find keywords wordpress, Is this website cms yes wordpress?
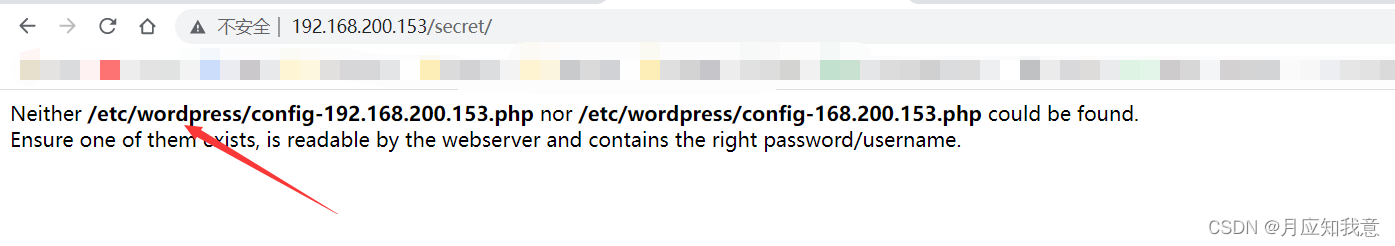
Reuse dirsearch Scan this record and try
dirsearch -u "http://192.168.200.153/secret/" -e php,html,txt,zip,bak,gz,7z -x 404,500-599 -t 50Sure enough wordpress, There are many catalogues .

Visit the following directories one by one to see if there are any gains

Found a compressed file , Download it and see . However, after opening it, I found that I was still too young , I don't understand .

So Baidu took a look , This is a wordpress A plug-in for , There is also an arbitrary file upload vulnerability .

On exploitdb Search the Internet , Found a utilization script . But I always report syntax errors in this script , We won't change , Then we can only find another way .

Two 、 Exploit
Use msf, stay msf The exploitation method of this vulnerability is found above .

Configuration module parameters , Use success , To obtain a web jurisdiction . Use python Get an interactive shell
Use python Get an interactive shell
python3 -c 'import pty; pty.spawn("/bin/bash")'Check the user , Find out besides root One more adrian user
cat /etc/passwdPay attention to this sentence , Mentioned the configuration file and the ability to read accounts and passwords .

Then try reading wordpress Try the configuration file of !
<!-- A picture is missing here , Reading the configuration file, you can see a line of comments -->
Why ! A line of comments is found here , Is this the password of the user above ?
adrian:idrinksomewaterperfect , Successfully switched users !
Get the first flag

3、 ... and 、 Elevated privileges
See if there is any order to raise power !

flock The command can be executed as any user without permission password .
Enter the following command to raise the right
sudo flock -u / /bin/bashperfect , Successfully promoted the permission to root
Get the second flag

边栏推荐
猜你喜欢
随机推荐
Beautified table style
5月27日杂谈
HackMyvm靶机系列(4)-vulny
[the Nine Yang Manual] 2021 Fudan University Applied Statistics real problem + analysis
【Numpy和Pytorch的数据处理】
一段用蜂鸣器编的音乐(成都)
【手撕代码】单例模式及生产者/消费者模式
[dark horse morning post] Shanghai Municipal Bureau of supervision responded that Zhong Xue had a high fever and did not melt; Michael admitted that two batches of pure milk were unqualified; Wechat i
简单理解ES6的Promise
MySQL lock summary (comprehensive and concise + graphic explanation)
PriorityQueue (large root heap / small root heap /topk problem)
Strengthen basic learning records
[面試時]——我如何講清楚TCP實現可靠傳輸的機制
Matlab opens M file garbled solution
Get started with typescript
自定义RPC项目——常见问题及详解(注册中心)
HackMyvm靶机系列(7)-Tron
撲克牌遊戲程序——人機對抗
深度强化文献阅读系列(一):Courier routing and assignment for food delivery service using reinforcement learning
Miscellaneous talk on May 14

![[VMware abnormal problems] problem analysis & Solutions](/img/64/f44864da600b61a1a646a5865a2083.jpg)