当前位置:网站首页>SRC mining ideas and methods
SRC mining ideas and methods
2022-07-06 13:48:00 【One call yyds】
Recently, I found that many small partners who have just come into contact with infiltration do not know the secret of actually digging holes , So I'm going to write some tips for digging holes by myself .
src It is recommended that novices dig holes in the preferred vulnerability box , Because the vulnerability box has a wide range , All domestic sites receive . Compared with other src platform , Mining is very suitable for novices .
Vulnerability mining , Information gathering is important .
Here we will explain with some actual combat .
First of all, let's talk about Google grammar !!!
The following can be done by fofa、 Zhong Kui's eyes 、shodan Wait for cyberspace search engines to search Google Mirror image .
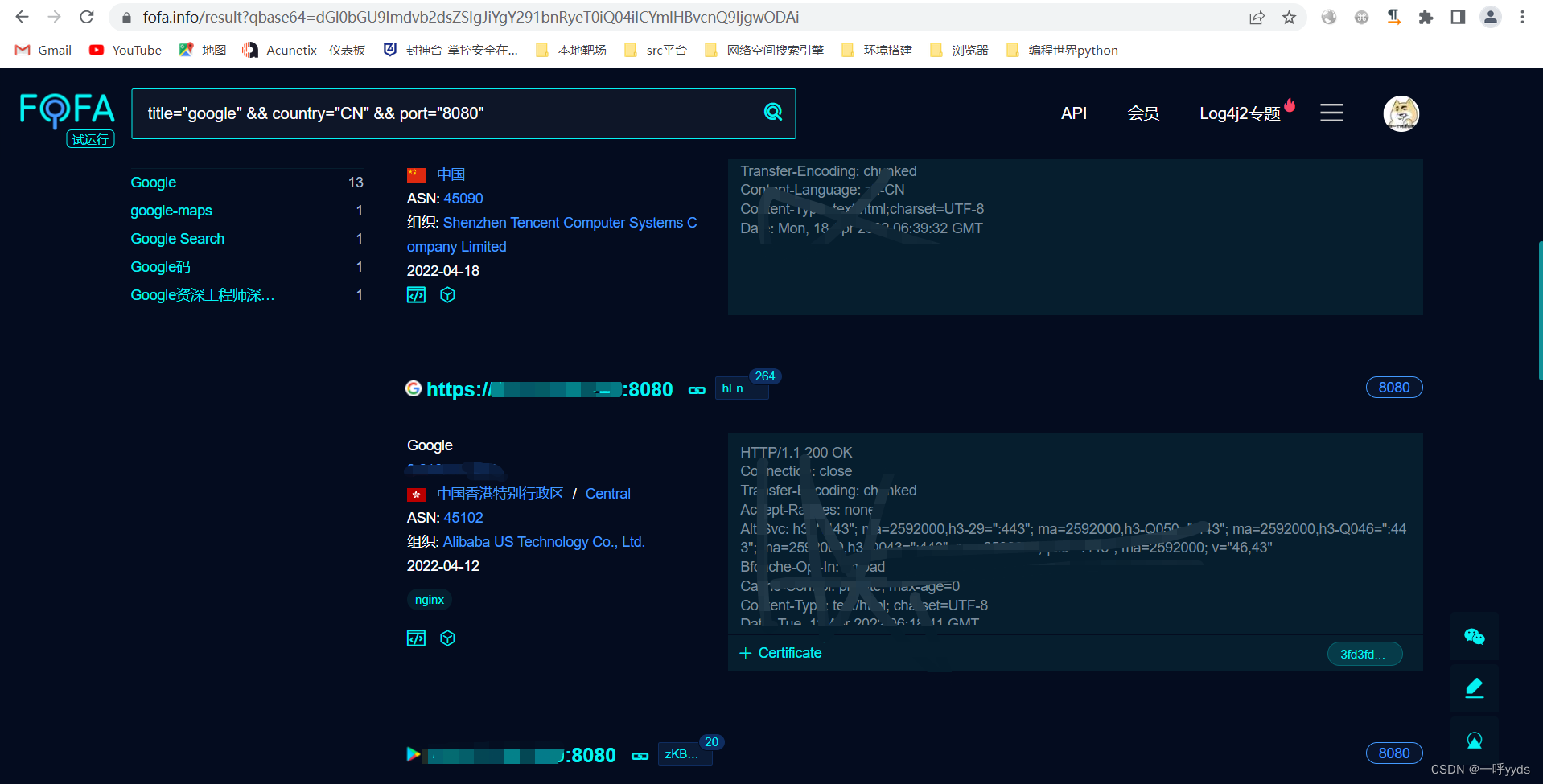
# SQL Injection and hole digging are basically smooth
1. Look for loopholes , Through basic site:、inurl: Google Syntax .
2. Find a site , Various points , Find his injection point .
3. Injection point not found , information gathering .
4. Then there are some column operations .
open Google Mirror image , Enter our Google syntax site:.com company .
In this way, you will get the domain name with .com Is the suffix related company name , The meaning of adding a company after it is to specify the company name for screening .
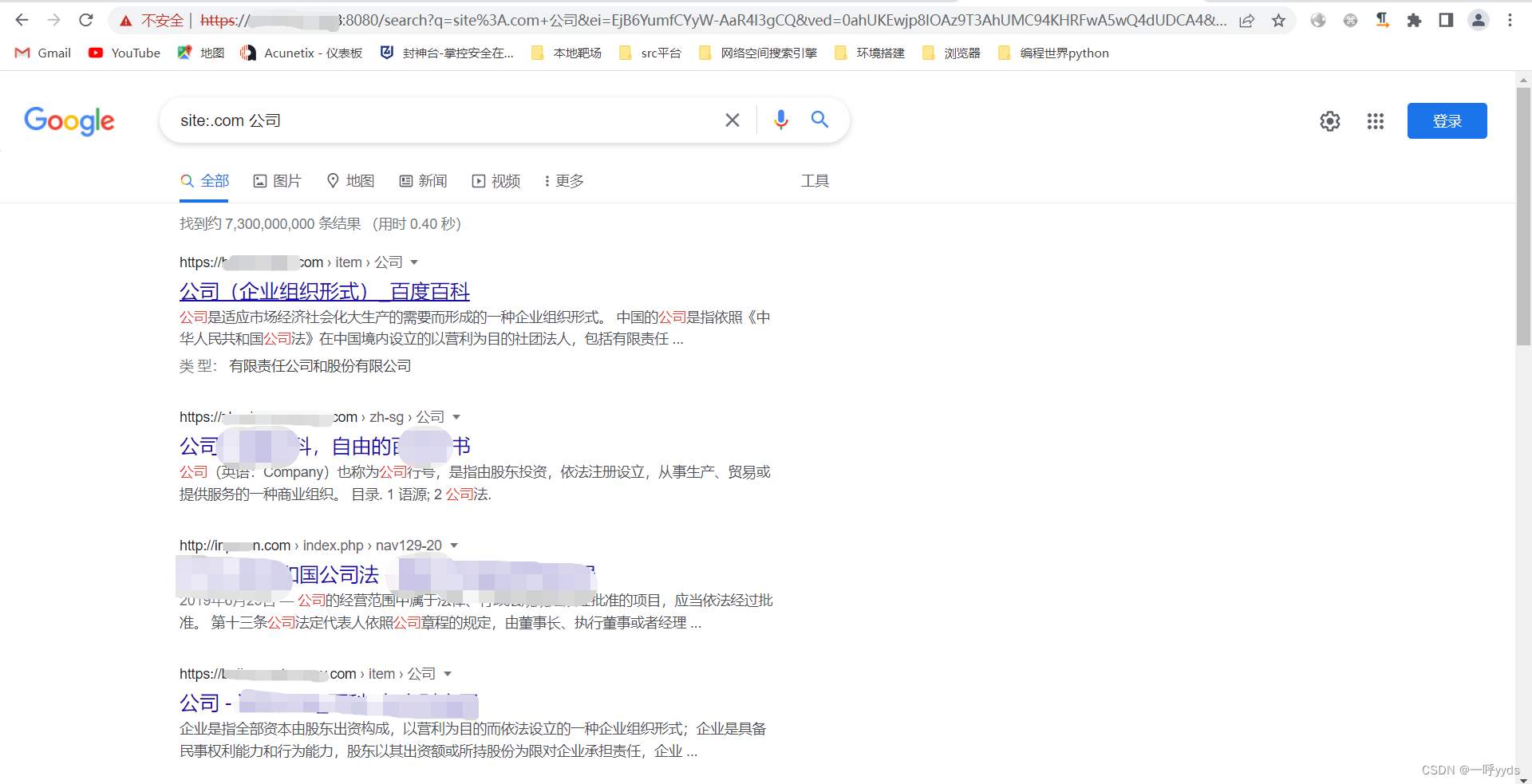
Google Syntax , Search through Google browser :site:.com inurl:php?id=22 company
And here we add php?id=22, Because the core of our injection point is to transmit parameters , Therefore, it will be easier to find loopholes by searching for participants .
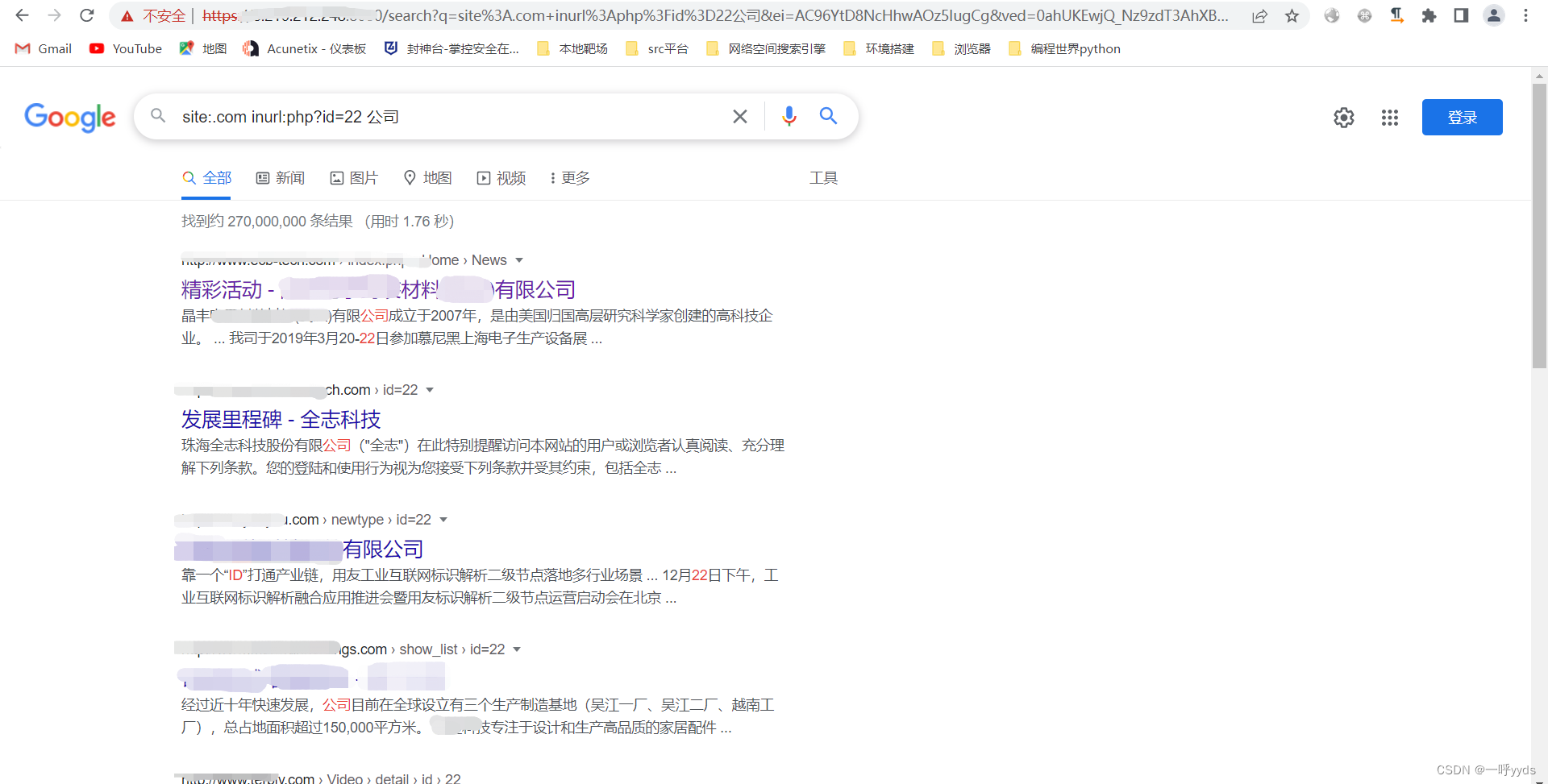
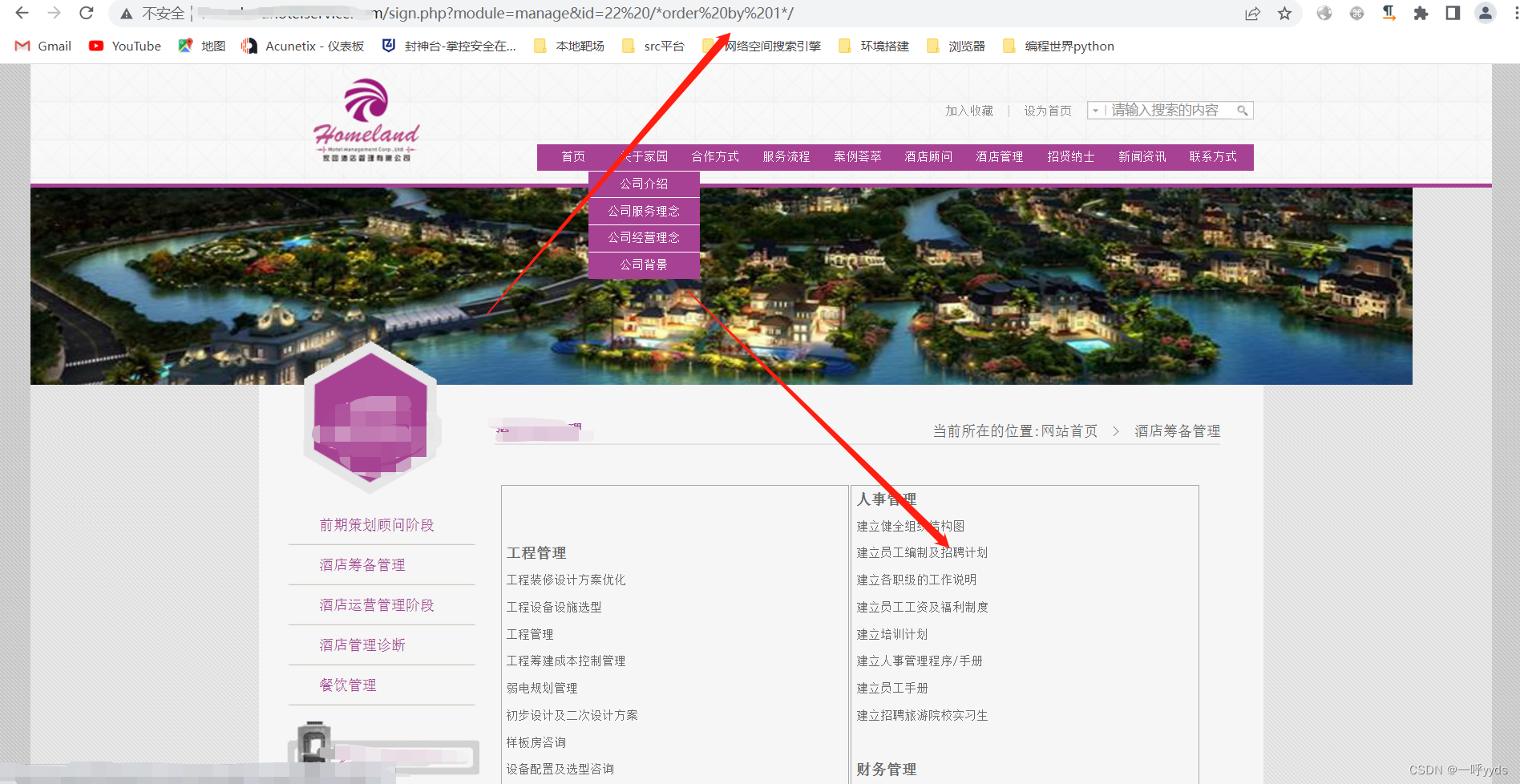
Now we find a website to test .
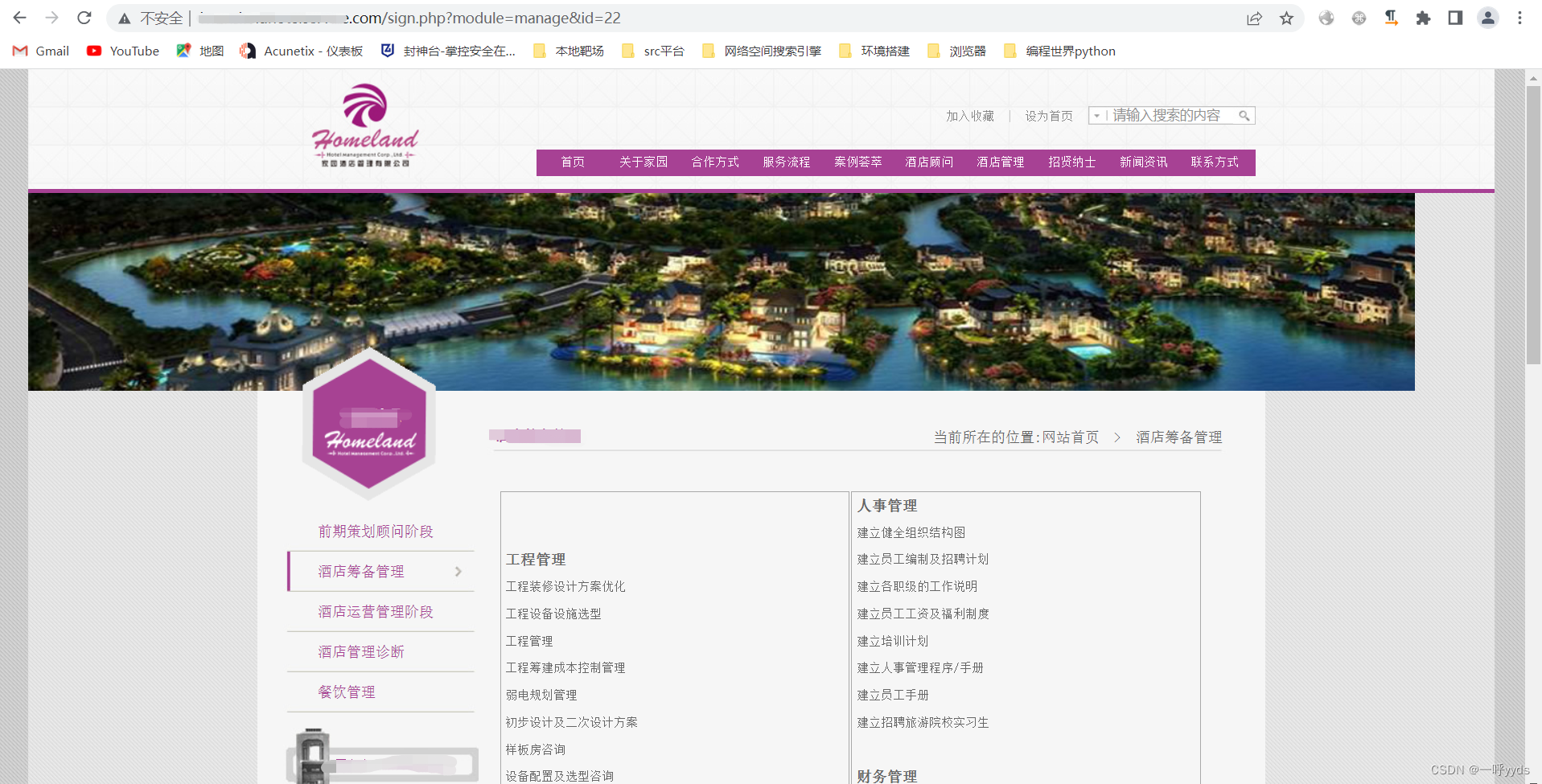
First we enter single quotation marks : ' , Look, the page has changed .
This means that the single quotation mark we entered is executed , There was a misreport . There is a great possibility that SQL Inject .
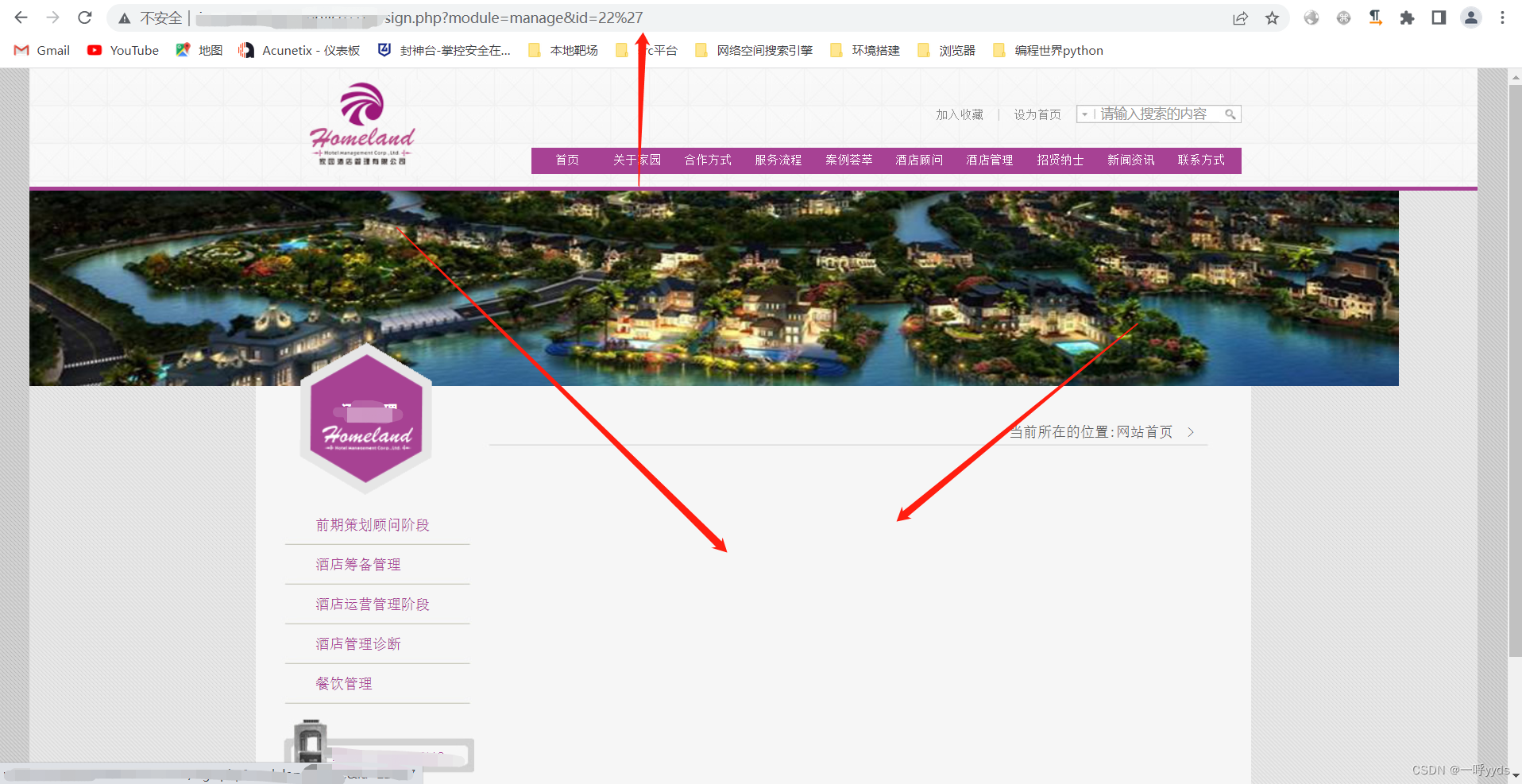
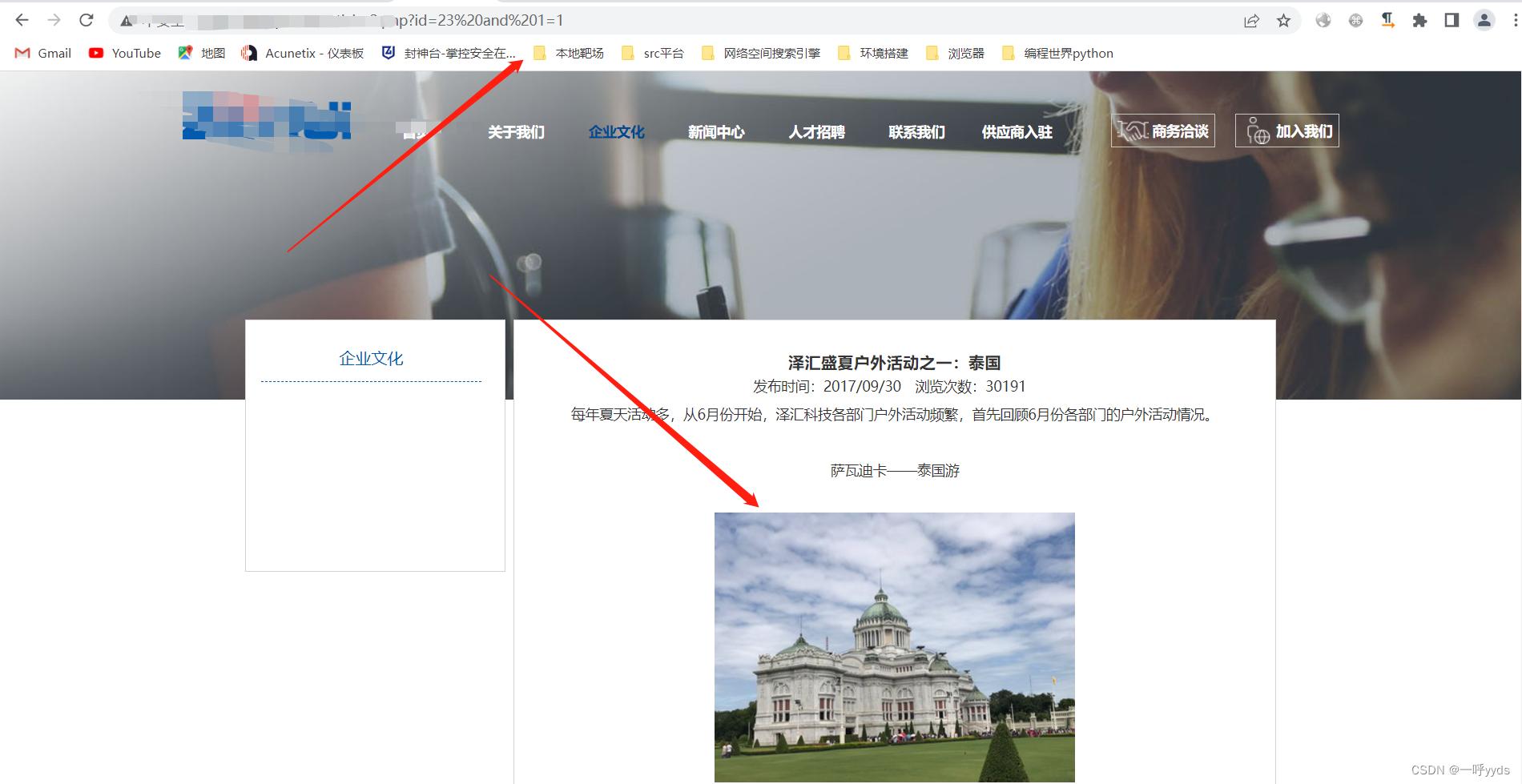
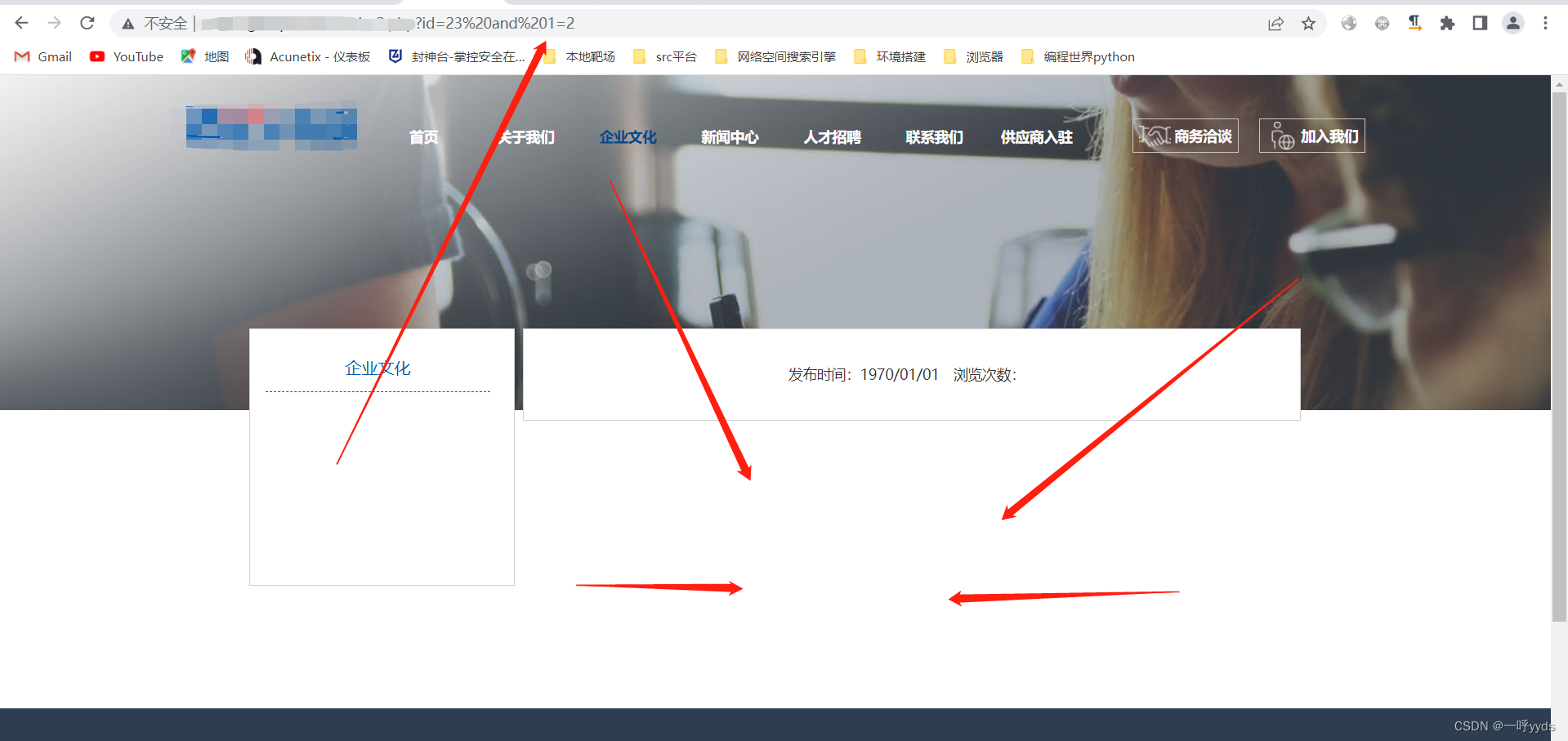
Further use ,and 1=1 && and 1=2, Verify whether the vulnerability exists .
there and 1=1, The page is normal , But in and 1=2 When , The page is echoed normally , Further verify .
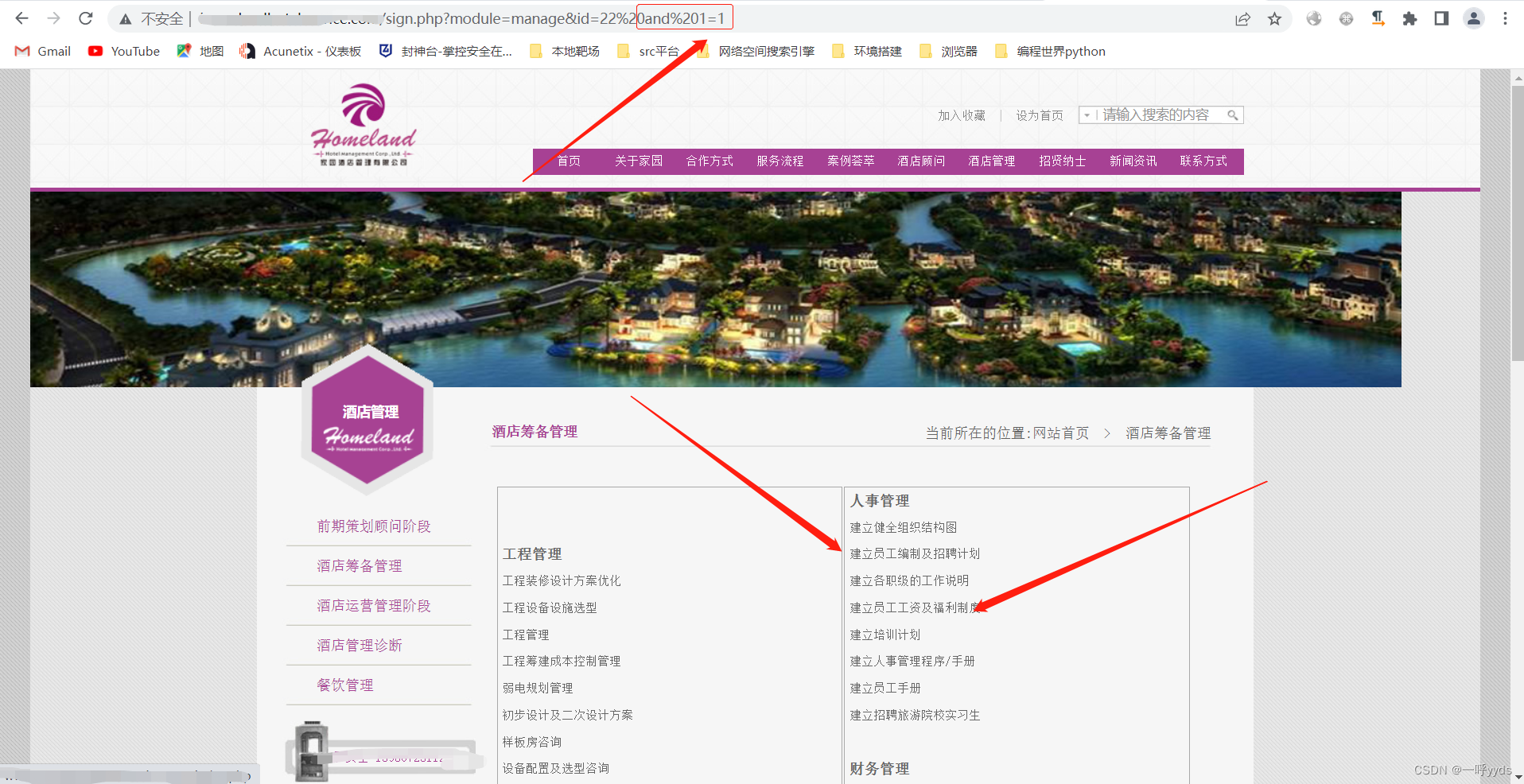
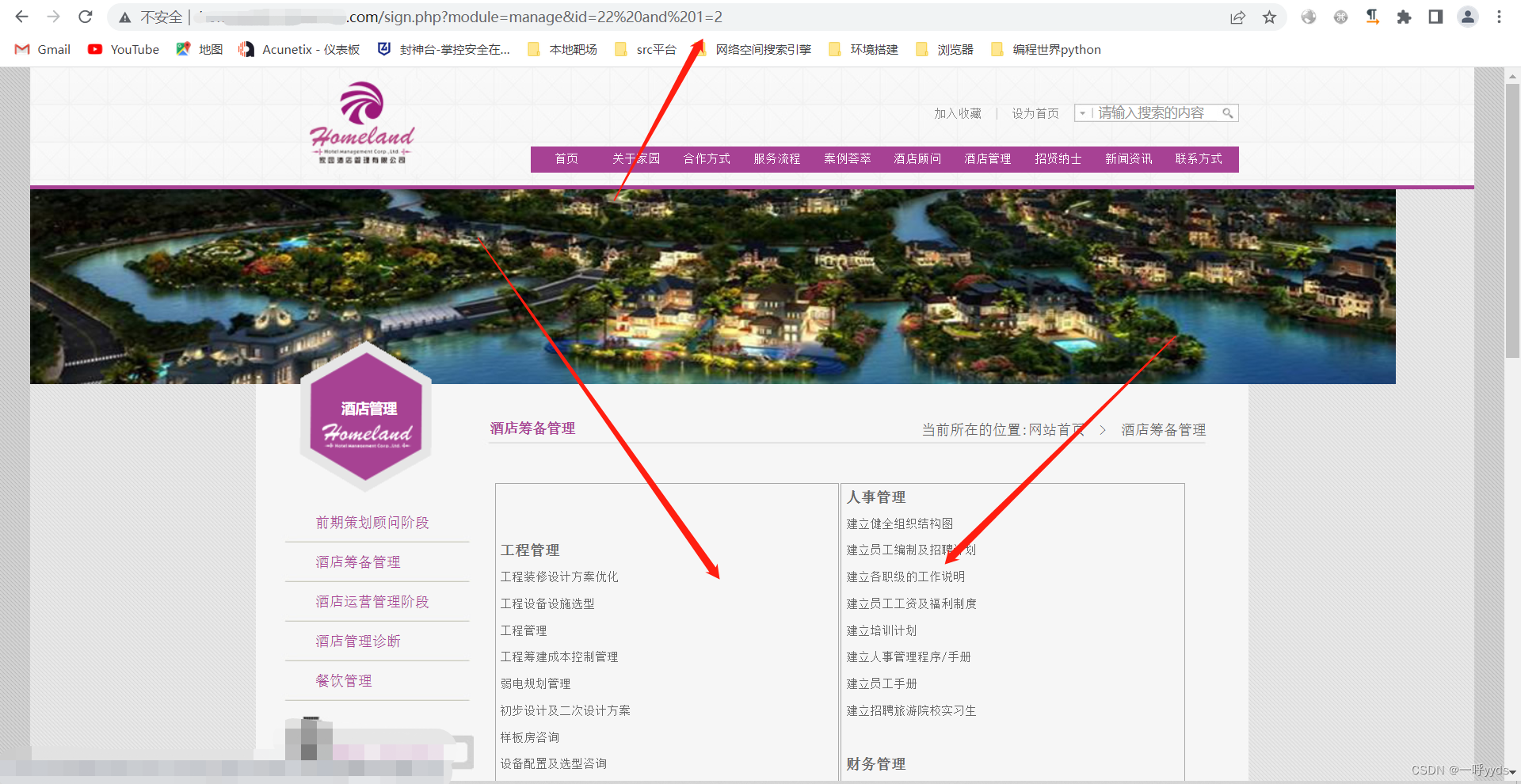
We continue to use SQL Statement function , Come to the conclusion , We were blocked by the website firewall .
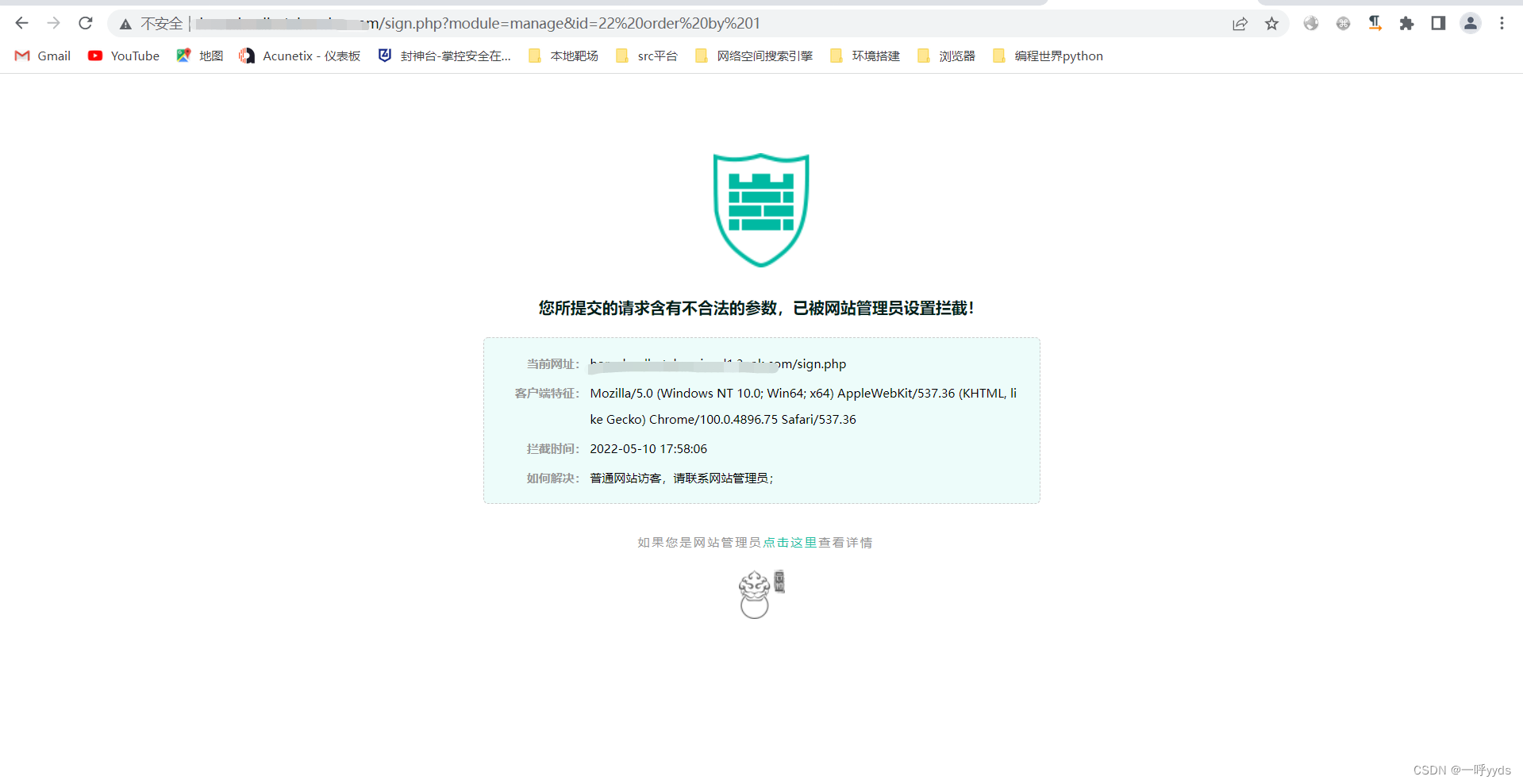
Did not bypass the website firewall , Try the inline annotation method casually here , Execution succeeded . It's too cumbersome to bypass the firewall , I'll do more , For starters , If you encounter a firewall, you can retreat directly .
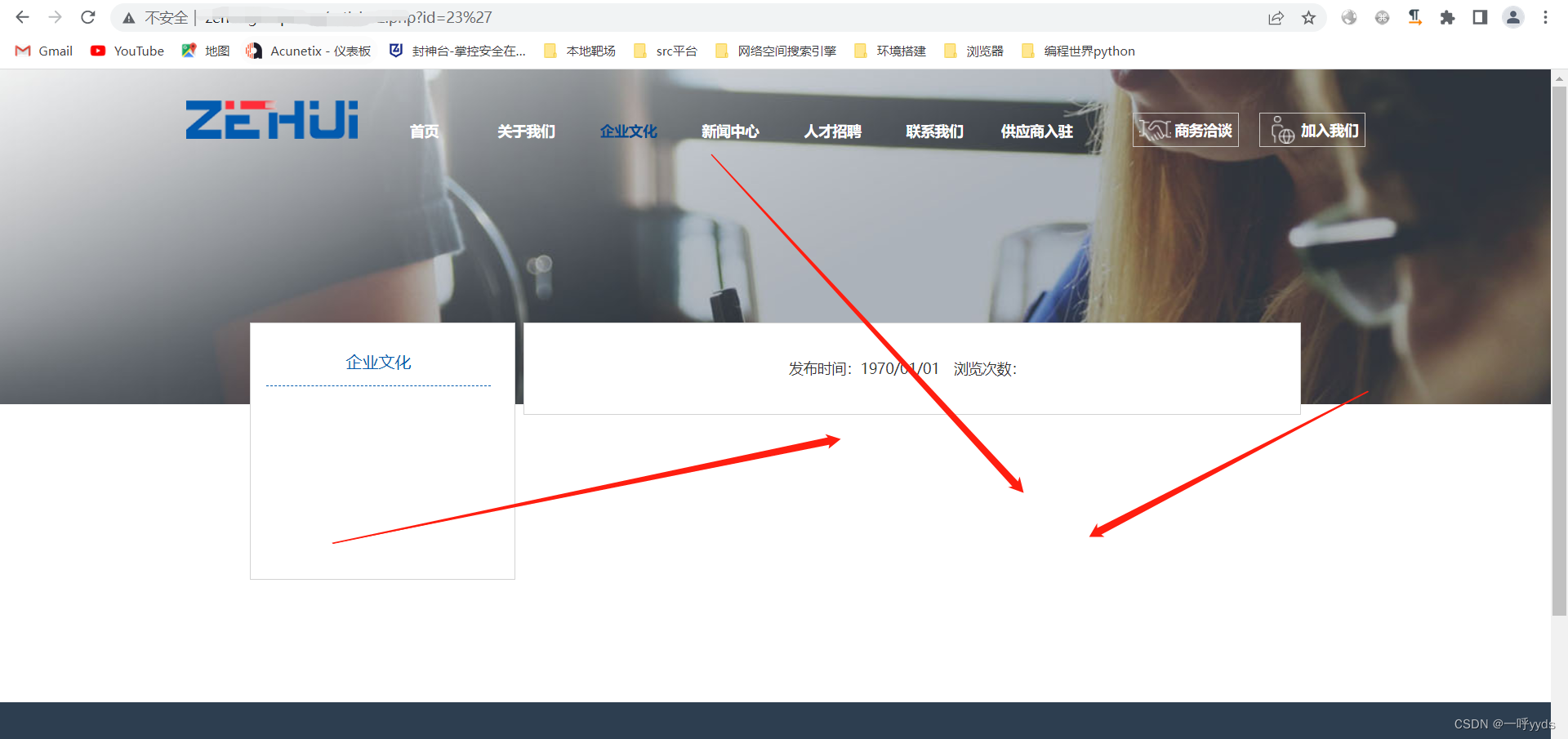
Find a station below , Enter single quotes ', Page exception , We look for input and 1=1 | 1=2, Find out 1=2 abnormal .
It indicates that the function we input is executed by the database , There is SQL Inject .
The vulnerability has been tested , Next, let's see if we can verify the vulnerability . On SQL sentence , We use order by 11 | order by 12.
order by 11 The page is normal , and order by 12 Page exception ( That there is 11 A field ).
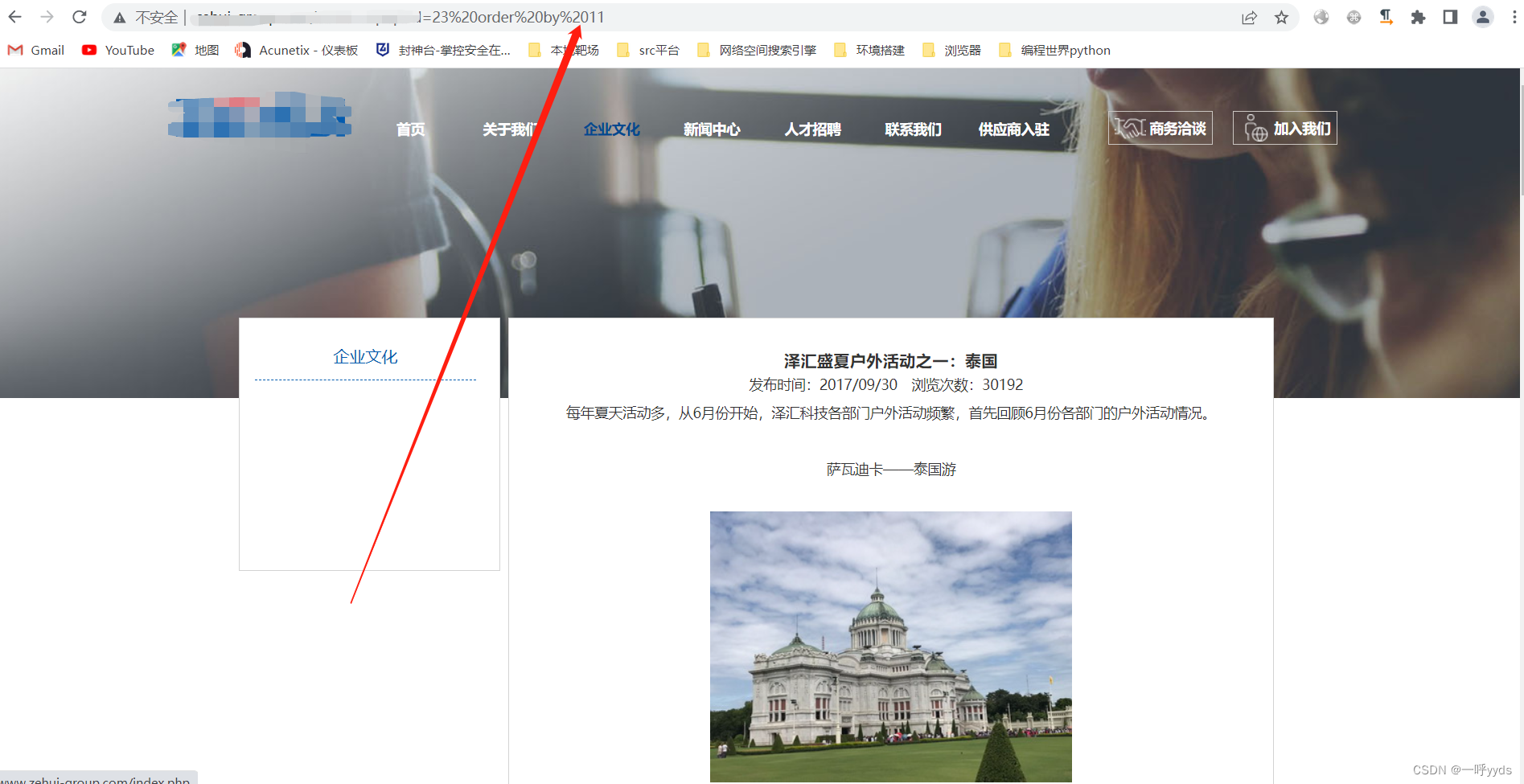
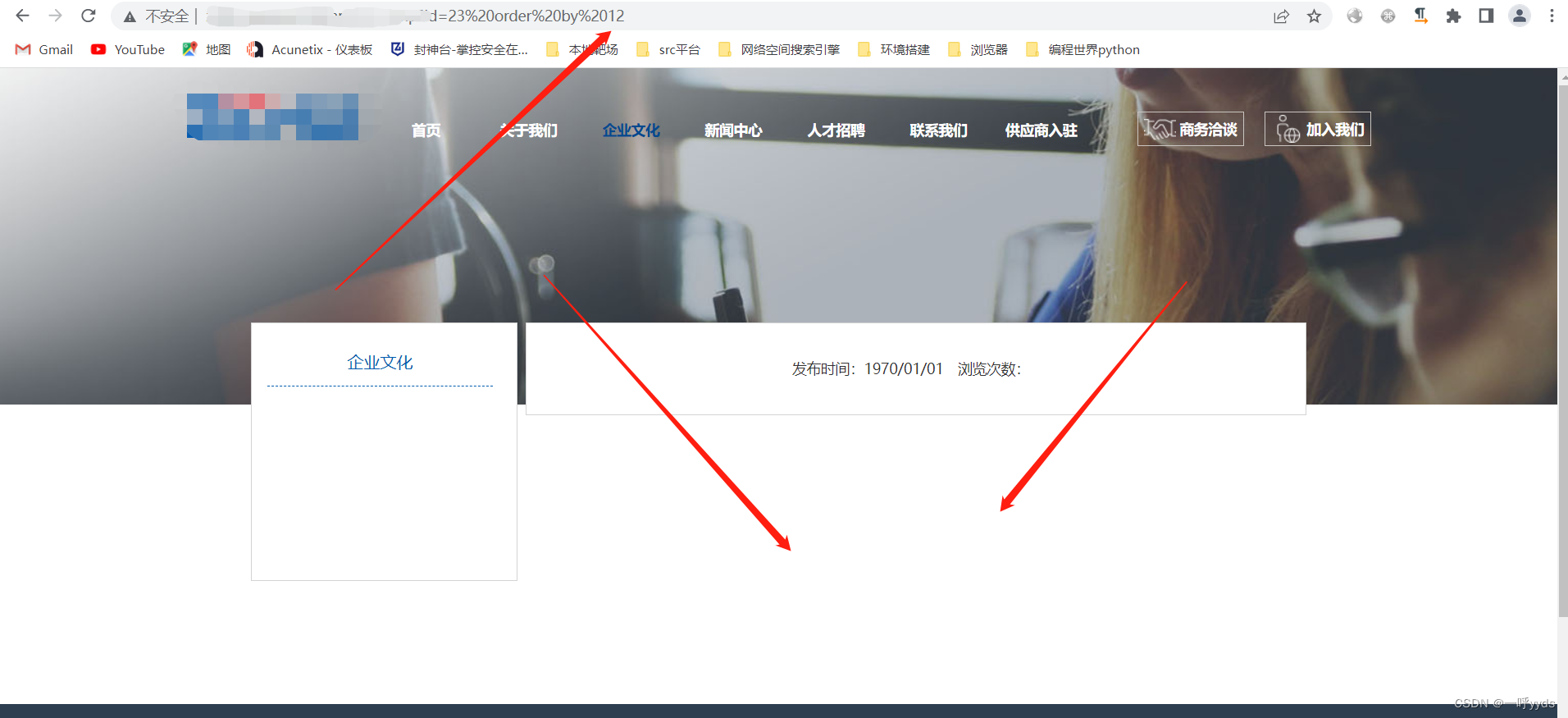
Then we use SQL sentence , It is found that there is a Boolean blind note , Boolean blind note query data is cumbersome , Just throw it here SQLmap ran .
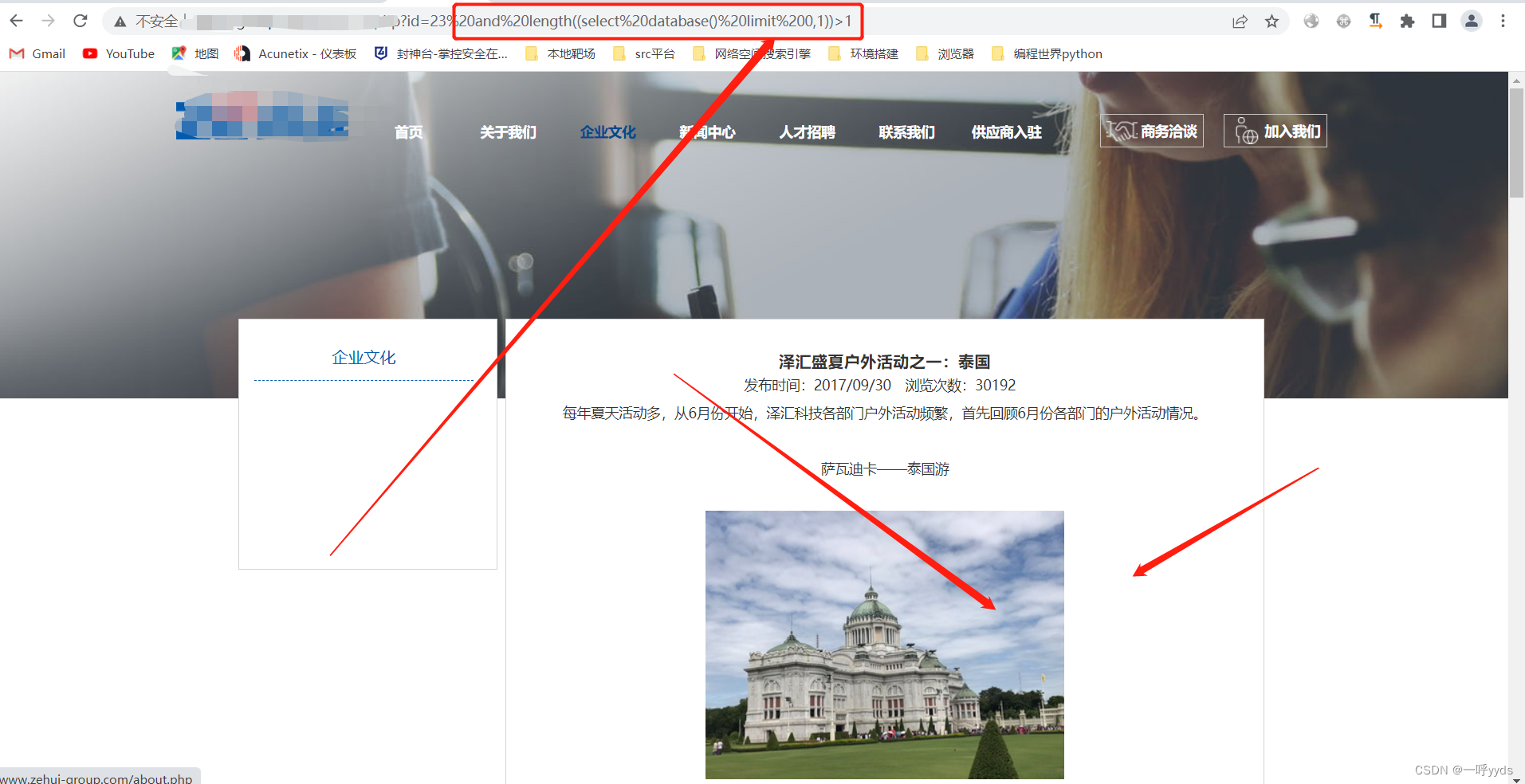
sqlmap command :Python sqlmap.py -u The goal is URL --dbs( Specify the name of the target database ), Finally, the library name is successfully obtained .
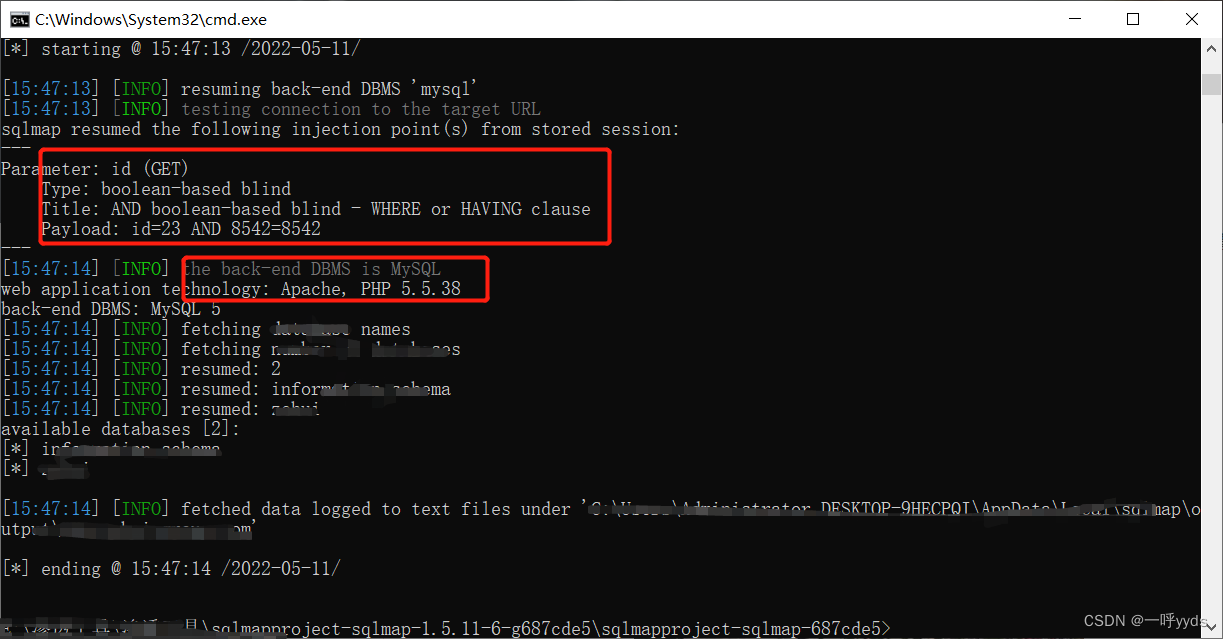
Digging a hole is so easy ,SQL There are still a lot of injections , encounter waf, Those who have ideas can try to bypass .
XSS Loophole
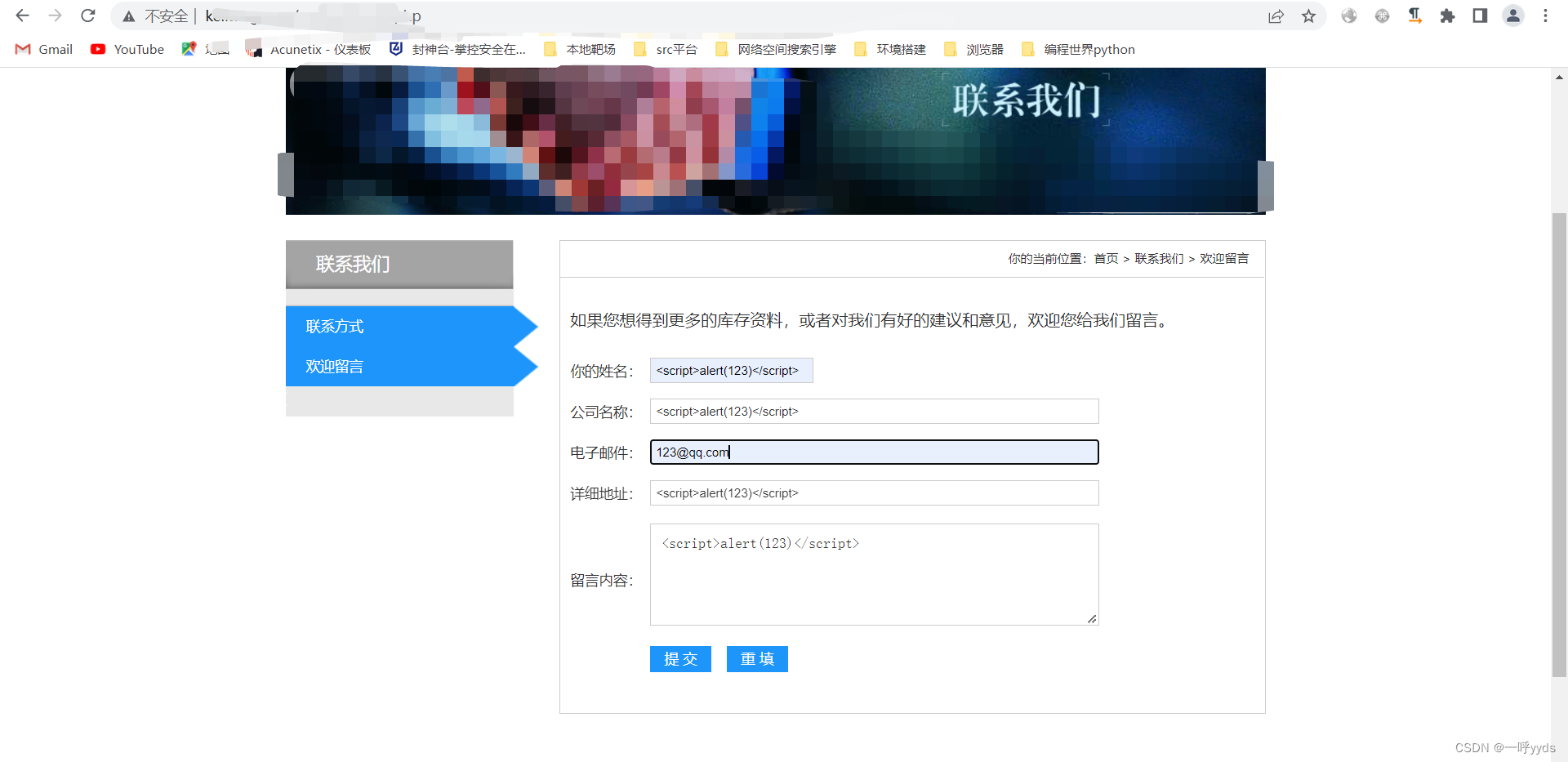
Generally, check whether there is a message board through the searched site , Try blind typing XSS, Generally one XSS Medium risk , Build... Directly xss sentence :<script>alert(1)</script>, Just insert it directly in the box , Pop up and submit directly src The platform is ok .
XSS General message board !!!
Weak password vulnerability mining
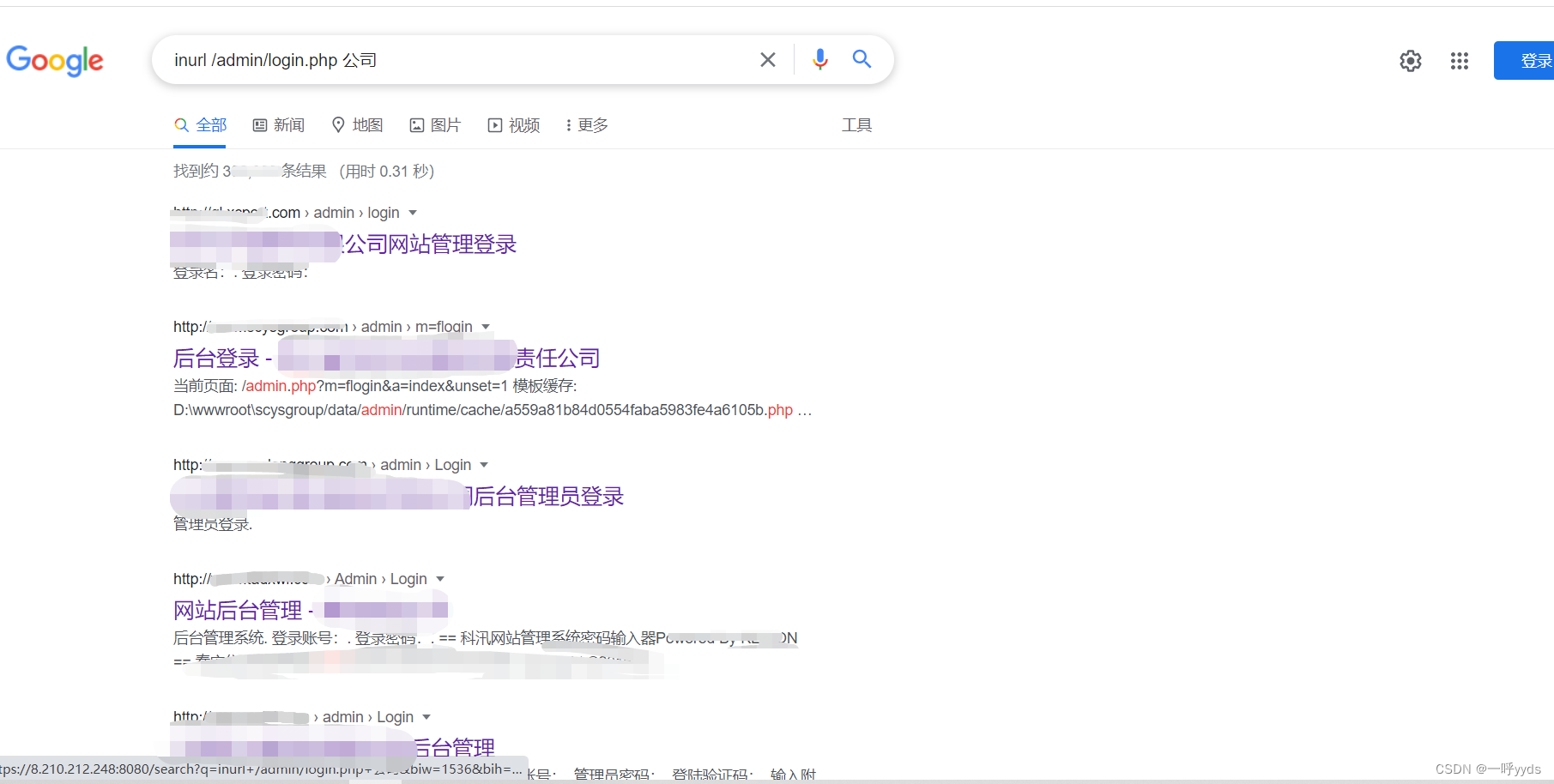
Weak password Google syntax :inurl:admin/login.php company .
In this way, you can search the backstage of many companies .
Entering the background, you can use tools to blast weak passwords in batches , Such as admin/111111 etc. , You can also view js Code to check whether there is an account password .
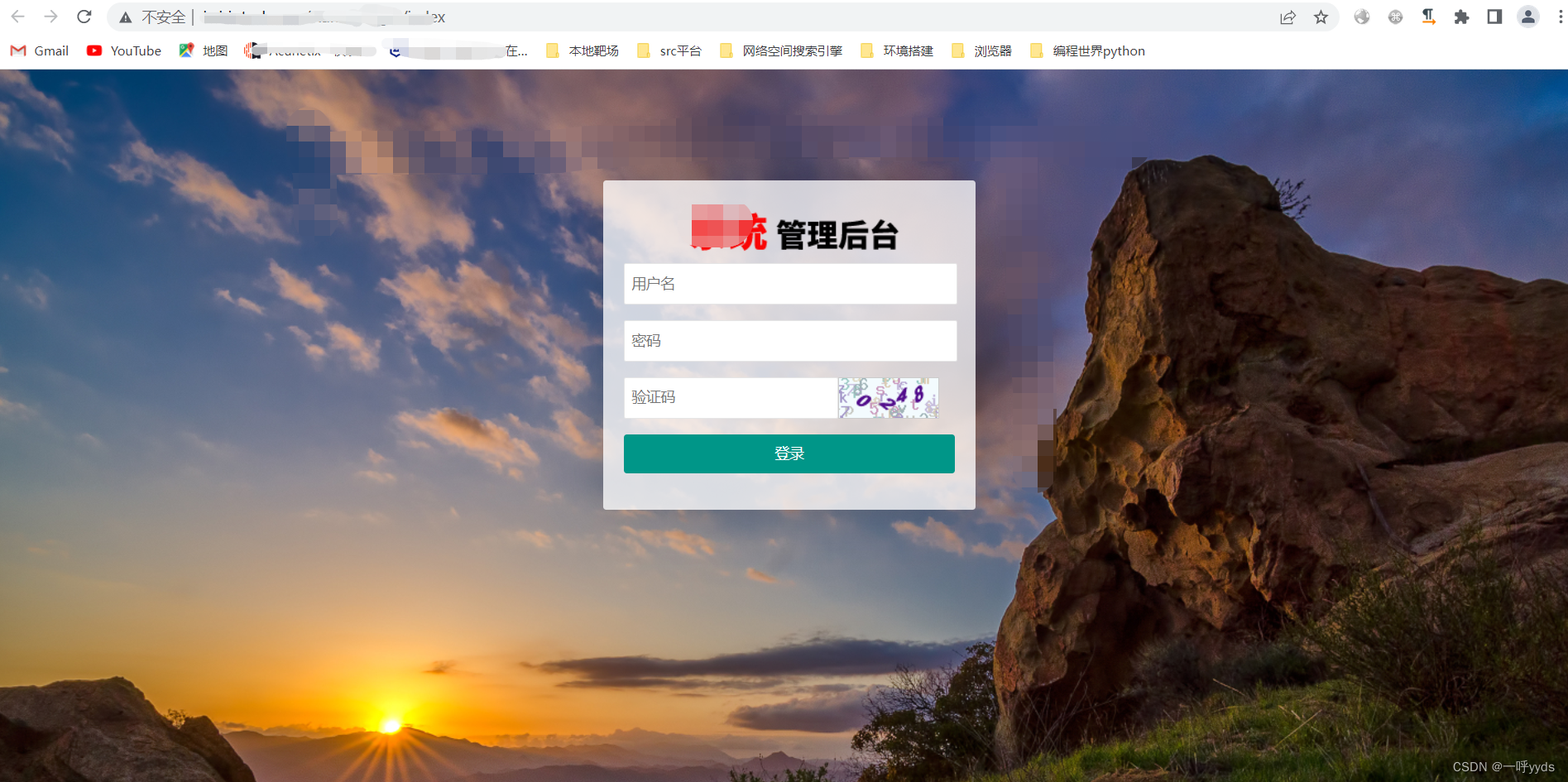
You can use or build your own weak password blasting tool , There are many such tools , I won't elaborate more .
Some verification codes are arranged , There is also a verification code that will not change if you catch the package .
These are all excavations src Compare the recommended vulnerabilities , I wish you all to be on the list as soon as possible !!!
边栏推荐
- 自定义RPC项目——常见问题及详解(注册中心)
- 【毕业季·进击的技术er】再见了,我的学生时代
- 6. Function recursion
- 4.分支语句和循环语句
- Write a program to simulate the traffic lights in real life.
- Wechat applet
- 4.二分查找
- Aurora system model of learning database
- Mode 1 two-way serial communication is adopted between machine a and machine B, and the specific requirements are as follows: (1) the K1 key of machine a can control the ledi of machine B to turn on a
- FAQs and answers to the imitation Niuke technology blog project (I)
猜你喜欢

1.初识C语言(1)

这次,彻底搞清楚MySQL索引

1. First knowledge of C language (1)
Principles, advantages and disadvantages of two persistence mechanisms RDB and AOF of redis
Leetcode. 3. Longest substring without repeated characters - more than 100% solution
C language Getting Started Guide
hashCode()与equals()之间的关系
优先队列PriorityQueue (大根堆/小根堆/TopK问题)
2. C language matrix multiplication
Service ability of Hongmeng harmonyos learning notes to realize cross end communication
随机推荐
1. Preliminary exercises of C language (1)
[the Nine Yang Manual] 2019 Fudan University Applied Statistics real problem + analysis
Detailed explanation of redis' distributed lock principle
优先队列PriorityQueue (大根堆/小根堆/TopK问题)
C语言实现扫雷游戏(完整版)
7-1 输出2到n之间的全部素数(PTA程序设计)
【九阳神功】2021复旦大学应用统计真题+解析
仿牛客技术博客项目常见问题及解答(二)
Leetcode. 3. Longest substring without repeated characters - more than 100% solution
1. First knowledge of C language (1)
实验八 异常处理
Read only error handling
4. Branch statements and loop statements
Why use redis
Using spacedesk to realize any device in the LAN as a computer expansion screen
Safe driving skills on ice and snow roads
The difference between cookies and sessions
7-7 7003 组合锁(PTA程序设计)
C language Getting Started Guide
5月14日杂谈