当前位置:网站首页>LeetCode:39. Combined sum
LeetCode:39. Combined sum
2022-07-06 08:50:00 【Bertil】
To give you one No repeating elements Array of integers for candidates And a target integer target , find candidates You can make the sum of numbers as the target number target Of all Different combinations , And return... As a list . You can press In any order Return these combinations .
candidates Medium The same Numbers can Unlimited repeat selected . If the selected number of at least one number is different , Then the two combinations are different .
For a given input , Guarantee and for target The number of different combinations of is less than 150 individual .
Example 1:
Input :candidates = [2,3,6,7], target = 7
Output :[[2,2,3],[7]]
explain :
2 and 3 Can form a set of candidates ,2 + 2 + 3 = 7 . Be careful 2 You can use it multiple times .
7 Is also a candidate , 7 = 7 .
Only these two combinations .
Example 2:
Input : candidates = [2,3,5], target = 8
Output : [[2,2,2,2],[2,3,3],[3,5]]
Example 3:
Input : candidates = [2], target = 1
Output : []
Tips :
- 1 <= candidates.length <= 30
- 1 <= candidates[i] <= 200
- candidate Every element in is Different from each other
- 1 <= target <= 500
Their thinking
1. Using backtracking ( namely DFS Prune with constraints ): First, ascending the array , Then define recursive functions , But pay attention to : Numbers can be reused , So every recursion , The starting point of incoming is i
2. Use two conditions to prune , Recursive exit :
- Meet the conditions , Copy one into the result array
- The number of remaining targets is less than the current element , The latter elements will only be larger , Abandon this round directly
Backtracking and DFS, The main difference is , The backtracking method does not retain the complete tree structure in the solution process , While depth first search records the complete search tree
Code
/** * @param {number[]} candidates * @param {number} target * @return {number[][]} */
var combinationSum = function(candidates, target) {
const res = [];
// Ascending sort
candidates.sort((a, b) => a - b);
const search = (path, target, start) => {
if (target === 0) {
// Meet the conditions , Copy one into the result array
res.push([...path]);
return;
}
// Note that the starting point is start
for (let i = start; i < candidates.length; i++) {
// The number of remaining targets is less than the current element , The latter elements will only be larger , Abandon this round directly
if (target < candidates[i]) return;
path.push(candidates[i]);
// Numbers can be repeated , So the introduction i
search(path, target - candidates[i], i);
path.pop();
}
};
search([], target, 0);
return res;
};
边栏推荐
- Target detection - pytorch uses mobilenet series (V1, V2, V3) to build yolov4 target detection platform
- LeetCode:124. 二叉树中的最大路径和
- C語言雙指針——經典題型
- sublime text的编写程序时的Tab和空格缩进问题
- 可变长参数
- Variable length parameter
- C language double pointer -- classic question type
- Tcp/ip protocol
- The harm of game unpacking and the importance of resource encryption
- Super efficient! The secret of swagger Yapi
猜你喜欢
目标检测——Pytorch 利用mobilenet系列(v1,v2,v3)搭建yolov4目标检测平台
MYSQL卸载方法与安装方法
Current situation and trend of character animation
Computer cleaning, deleted system files
![[today in history] February 13: the father of transistors was born The 20th anniversary of net; Agile software development manifesto was born](/img/70/d275009134fcbf9ae984c0f278659e.jpg)
[today in history] February 13: the father of transistors was born The 20th anniversary of net; Agile software development manifesto was born
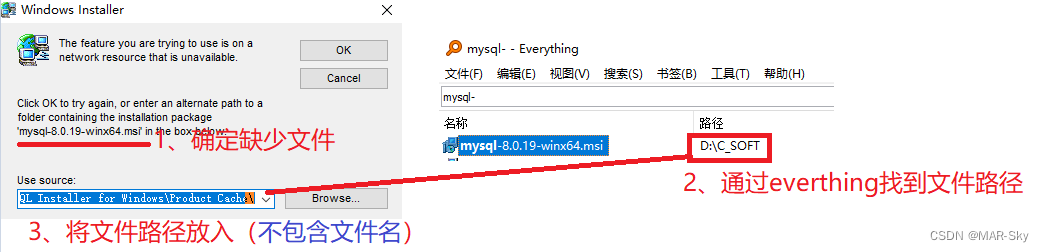
软件卸载时遇到trying to use is on a network resource that is unavailable
可变长参数
企微服务商平台收费接口对接教程
【嵌入式】Cortex M4F DSP库
Using C language to complete a simple calculator (function pointer array and callback function)
随机推荐
Delay initialization and sealing classes
UML diagram memory skills
marathon-envs项目环境配置(强化学习模仿参考动作)
poi追加写EXCEL文件
可变长参数
View computer devices in LAN
@JsonBackReference和@JsonManagedReference(解决对象中存在双向引用导致的无限递归)
Nacos 的安装与服务的注册
Visual implementation and inspection of visdom
R language ggplot2 visualization: place the title of the visualization image in the upper left corner of the image (customize Title position in top left of ggplot2 graph)
opencv+dlib实现给蒙娜丽莎“配”眼镜
ROS compilation calls the third-party dynamic library (xxx.so)
Alibaba cloud server mining virus solution (practiced)
LeetCode:673. 最长递增子序列的个数
深度剖析C语言数据在内存中的存储
Navicat Premium 创建MySql 创建存储过程
【ROS】usb_ Cam camera calibration
如何有效地进行自动化测试?
生成器参数传入参数
Fairguard game reinforcement: under the upsurge of game going to sea, game security is facing new challenges