当前位置:网站首页>@Jsonbackreference and @jsonmanagedreference (solve infinite recursion caused by bidirectional references in objects)
@Jsonbackreference and @jsonmanagedreference (solve infinite recursion caused by bidirectional references in objects)
2022-07-06 08:38:00 【XYLANCC】
jackson Medium @JsonBackReference and @JsonManagedReference, as well as @JsonIgnore It is to solve the infinite recursion caused by the existence of two-way references in the object (infinite recursion) problem . These dimensions can be used in attributes or corresponding get、set In the method .
@JsonBackReference and @JsonManagedReference: These two labels are usually used in pairs , Usually used in parent-child relationships [email protected] The attributes of the annotation are serialized (serialization, Convert the object to json data ) when , Will be ignored ( That is... In the result json The data does not contain the content of this attribute )[email protected] The attributes of the annotation are serialized . At serialization ,@JsonBackReference Is equivalent to @JsonIgnore, There can be no @JsonManagedReference. But in deserialization (deserialization, namely json Data to object ) when , without @JsonManagedReference, Will not automatically inject @JsonBackReference The properties of the annotation ( Neglected parent or child ); If there is @JsonManagedReference, Will be automatically injected @JsonBackReference The properties of the annotation .
@JsonIgnore: Ignore an attribute directly , To break infinite recursion , Serialization or deserialization are ignored . Of course, if marked in get、set In the method , Can be controlled separately , Serialization corresponds to get Method , Deserialization corresponds to set Method . In a father son relationship , When deserializing ,@JsonIgnore Ignored attribute values are not automatically injected ( Parent or child ), This is it with @JsonBackReference and @JsonManagedReference The biggest difference .
Sample test code ( Pay attention to the deserialized TreeNode[readValue] Of children Inside parent):
TreeNode.java
import java.util.ArrayList;
import java.util.List;
import org.codehaus.jackson.annotate.JsonBackReference;
import org.codehaus.jackson.annotate.JsonManagedReference;
public class TreeNode {
String name;
@JsonBackReference
// @JsonIgnore
TreeNode parent;
@JsonManagedReference
List<TreeNode> children;
public TreeNode() {
}
public TreeNode(String name) {
this.name = name;
}
public String getName() {
return name;
}
public void setName(String name) {
this.name = name;
}
public TreeNode getParent() {
return parent;
}
public void setParent(TreeNode parent) {
this.parent = parent;
}
public List<TreeNode> getChildren() {
return children;
}
public void setChildren(List<TreeNode> children) {
this.children = children;
}
public void addChild(TreeNode child) {
if (children == null)
children = new ArrayList<TreeNode>();
children.add(child);
}
}
JsonTest.java
Java Code Collection code
import java.io.IOException;
import org.codehaus.jackson.JsonGenerationException;
import org.codehaus.jackson.map.JsonMappingException;
import org.codehaus.jackson.map.ObjectMapper;
import org.junit.AfterClass;
import org.junit.BeforeClass;
import org.junit.Test;
public class JsonTest {
static TreeNode node;
@BeforeClass
public static void setUp() {
TreeNode node1 = new TreeNode("node1");
TreeNode node2 = new TreeNode("node2");
TreeNode node3 = new TreeNode("node3");
TreeNode node4 = new TreeNode("node4");
TreeNode node5 = new TreeNode("node5");
TreeNode node6 = new TreeNode("node6");
node1.addChild(node2);
node2.setParent(node1);
node2.addChild(node3);
node3.setParent(node2);
node2.addChild(node4);
node4.setParent(node2);
node3.addChild(node5);
node5.setParent(node3);
node5.addChild(node6);
node6.setParent(node5);
node = node3;
}
@Test
public void test() throws JsonGenerationException, JsonMappingException, IOException {
ObjectMapper mapper = new ObjectMapper();
String json = mapper.writeValueAsString(node);
System.out.println(json);
TreeNode readValue = mapper.readValue(json, TreeNode.class);
System.out.println(readValue.getName());
}
@AfterClass
public static void tearDown() {
node = null;
}
} 边栏推荐
- The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
- Verrouillage [MySQL]
- Online yaml to CSV tool
- Ruffian Heng embedded bimonthly, issue 49
- Deep learning: derivation of shallow neural networks and deep neural networks
- Function coritization
- The network model established by torch is displayed by torch viz
- sys.argv
- 2022.02.13 - 238. Maximum number of "balloons"
- Mobile phones and computers on the same LAN access each other, IIS settings
猜你喜欢
![Verrouillage [MySQL]](/img/ce/9f8089da60d9b3a3f92a5e4eebfc13.png)
Verrouillage [MySQL]
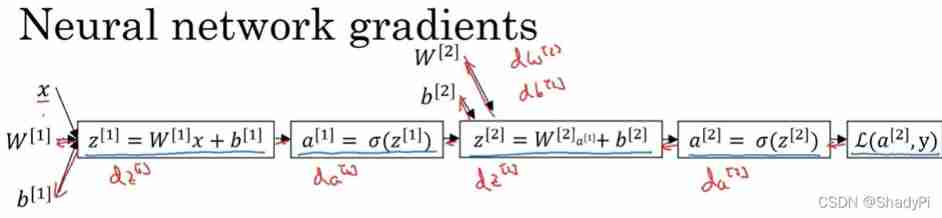
Deep learning: derivation of shallow neural networks and deep neural networks
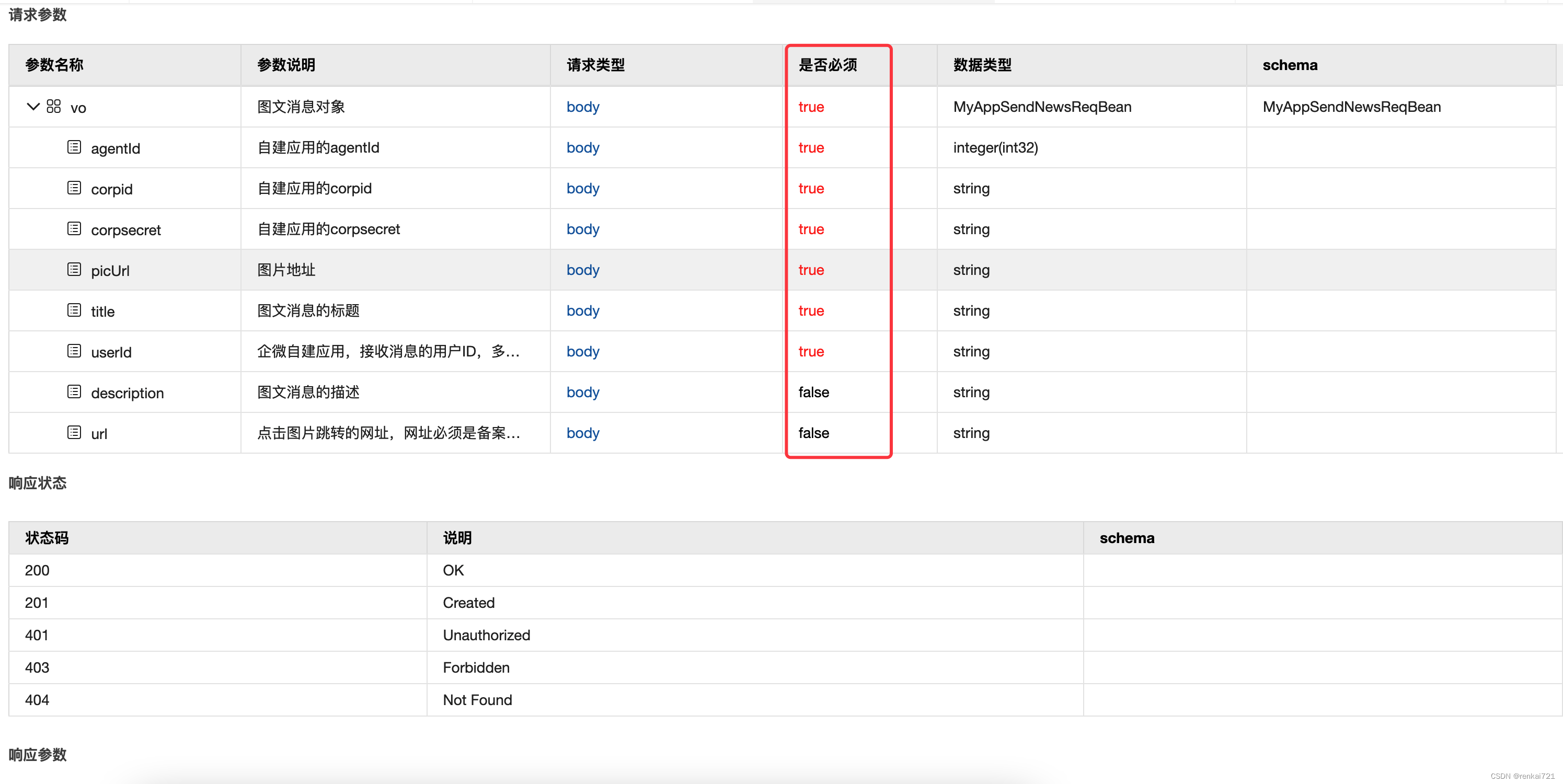
swagger设置字段required必填
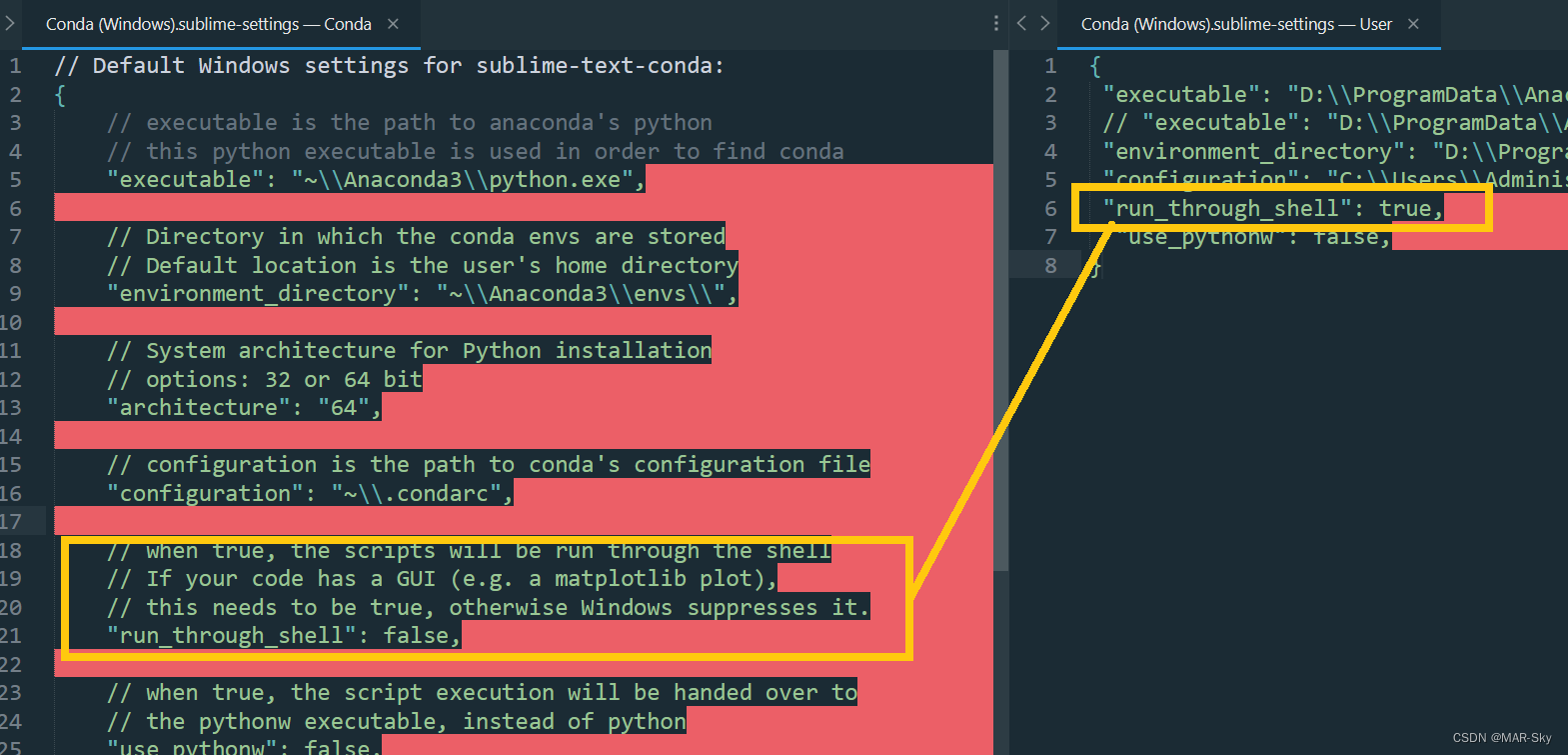
Sublime text in CONDA environment plt Show cannot pop up the problem of displaying pictures

Deep analysis of C language pointer
![[cloud native topic -45]:kubesphere cloud Governance - Introduction and overall architecture of enterprise container platform based on kubernetes](/img/ac/773ce8ee7f380df19edf8373250608.jpg)
[cloud native topic -45]:kubesphere cloud Governance - Introduction and overall architecture of enterprise container platform based on kubernetes
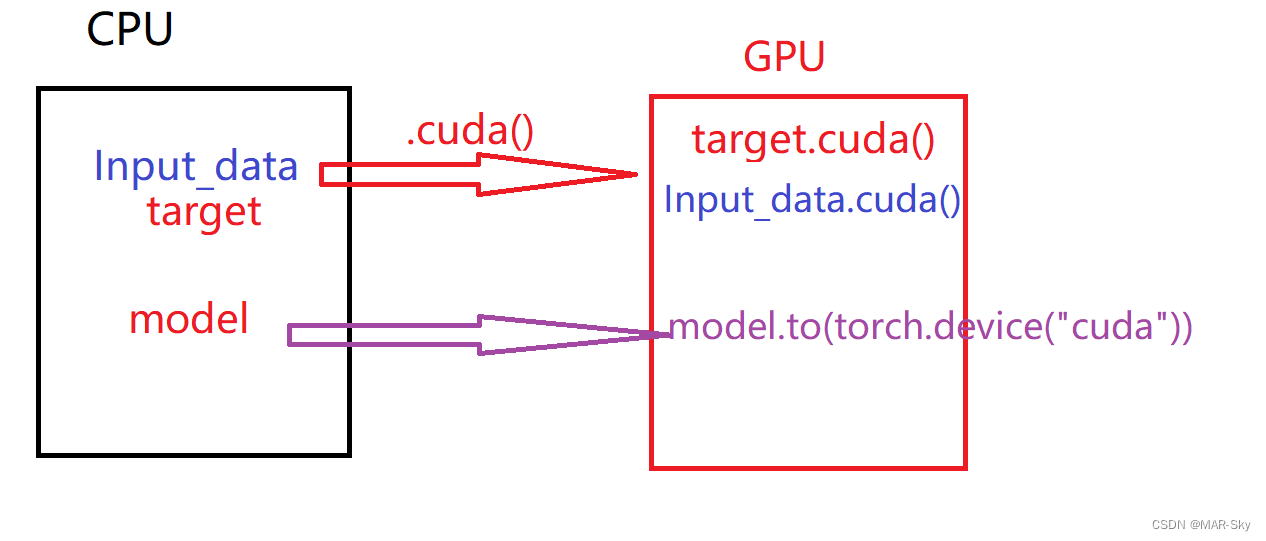
pytorch训练好的模型在加载和保存过程中的问题
C language double pointer -- classic question type
![[MySQL] log](/img/e9/1617122888c096cf6aba2bdb88f0ef.png)
[MySQL] log

The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
随机推荐
VMware 虚拟化集群
同一局域网的手机和电脑相互访问,IIS设置
Unified ordering background interface product description Chinese garbled
LDAP Application Section (4) Jenkins Access
2022.02.13 - NC003. Design LRU cache structure
Computer cleaning, deleted system files
LDAP应用篇(4)Jenkins接入
JS pure function
logback1.3. X configuration details and Practice
View computer devices in LAN
China's high purity aluminum target market status and investment forecast report (2022 Edition)
游戏解包的危害及资源加密的重要性
China high purity silver nitrate Market Research and investment strategy report (2022 Edition)
Zhong Xuegao, who cannot be melted, cannot escape the life cycle of online celebrity products
JS inheritance method
Golang force buckle leetcode 1020 Number of enclaves
Image, CV2 read the conversion and size resize change of numpy array of pictures
C language double pointer -- classic question type
Introduction to the differences between compiler options of GCC dynamic library FPIC and FPIC
[MySQL] log