当前位置:网站首页>860. Lemonade change
860. Lemonade change
2022-07-06 16:08:00 【mrbone9】
Address :
Power button  https://leetcode-cn.com/problems/lemonade-change/
https://leetcode-cn.com/problems/lemonade-change/
subject :
On the lemonade stand , The price of each lemonade is 5 dollar . Customers line up to buy your products ,( By bill bills The order of payment ) Buy one cup at a time .
Each customer only buys a glass of lemonade , Then pay you 5 dollar 、10 US dollars or 20 dollar . You have to give every customer the right change , That is to say, the net transaction is that every customer pays you 5 dollar .
Be careful , You didn't have any change at first .
Give you an array of integers bills , among bills[i] It's No i A customer paid the bill . If you can give every customer the right change , return true , Otherwise return to false .
Example 1:
| Input :bills = [5,5,5,10,20] Output :true explain : front 3 There are customers , We charge in order 3 Zhang 5 Dollar bills . The first 4 There are customers , We take one 10 Dollar bills , And return it 5 dollar . The first 5 There are customers , Let's return one 10 A dollar bill and a 5 Dollar bills . Because all customers get the right change , So we output true. |
Example 2:
| Input :bills = [5,5,10,10,20] Output :false explain : front 2 There are customers , We charge in order 2 Zhang 5 Dollar bills . For the next 2 Customers , We take one 10 Dollar bills , And return it 5 dollar . For the last customer , We can't return 15 dollar , Because we only have two 10 Dollar bills . Because not every customer gets the right change , So the answer is false. |
Example 3:
| Input :bills = [5,5,10] Output :true |
Example 4:
| Input :bills = [10,10] Output :false |
Tips :
| 1 <= bills.length <= 105 bills[i] No 5 Namely 10 or 20 |
source : Power button (LeetCode)
link :https://leetcode-cn.com/problems/lemonade-change
Copyright belongs to the network . For commercial reprint, please contact the official authority , Non-commercial reprint please indicate the source .
Ideas :
The cashier's idea is ok , Cash register yes 3 Lattice , Separately put 5,10,20
No money at work , The lattice is empty , Normal business is ok , No advance payment
Method 1 、 Count array
It is not strictly a counting array operation , It's similar
bool lemonadeChange(int* bills, int billsSize){
int count[3] = {0};
for(int i=0; i<billsSize; i++)
{
if(bills[i] == 5)
count[0]++;
else if(bills[i] == 10)
{
if(count[0] != 0)
{
count[0]--;
count[1]++;
}
else
return false;
}
else if(bills[i] == 20)
{
if(count[1] != 0)
{
count[1]--;
if(count[0] != 0)
{
count[0]--;
count[2]++;
}
else
return false;
}
else
{
if(count[0] >= 3)
{
count[0] -= 3;
count[2]++;
}
else
return false;
}
}
}
return true;
}边栏推荐
- Alice and Bob (2021 Niuke summer multi school training camp 1)
- Luogu P1102 A-B number pair (dichotomy, map, double pointer)
- Common configuration files of SSM framework
- Shell Scripting
- STM32 how to use stlink download program: light LED running light (Library version)
- 【高老师软件需求分析】20级云班课习题答案合集
- Alice and Bob (2021牛客暑期多校训练营1)
- E. Breaking the Wall
- 【练习-6】(PTA)分而治之
- MySQL授予用户指定内容的操作权限
猜你喜欢
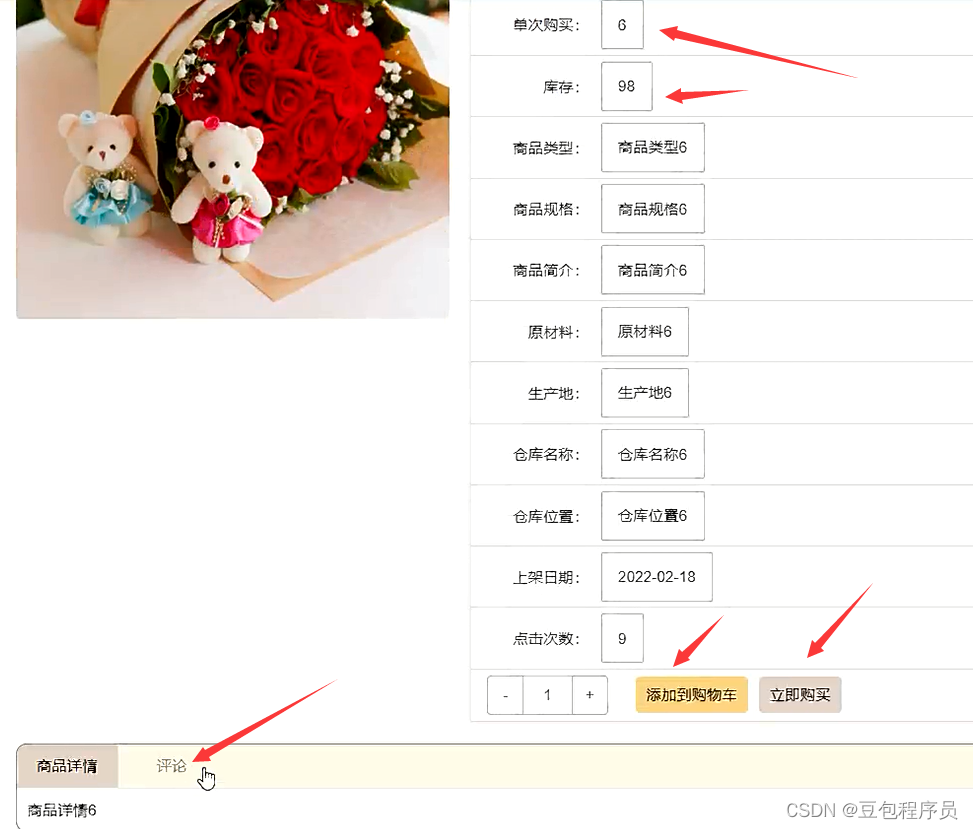
Nodejs+vue online fresh flower shop sales information system express+mysql
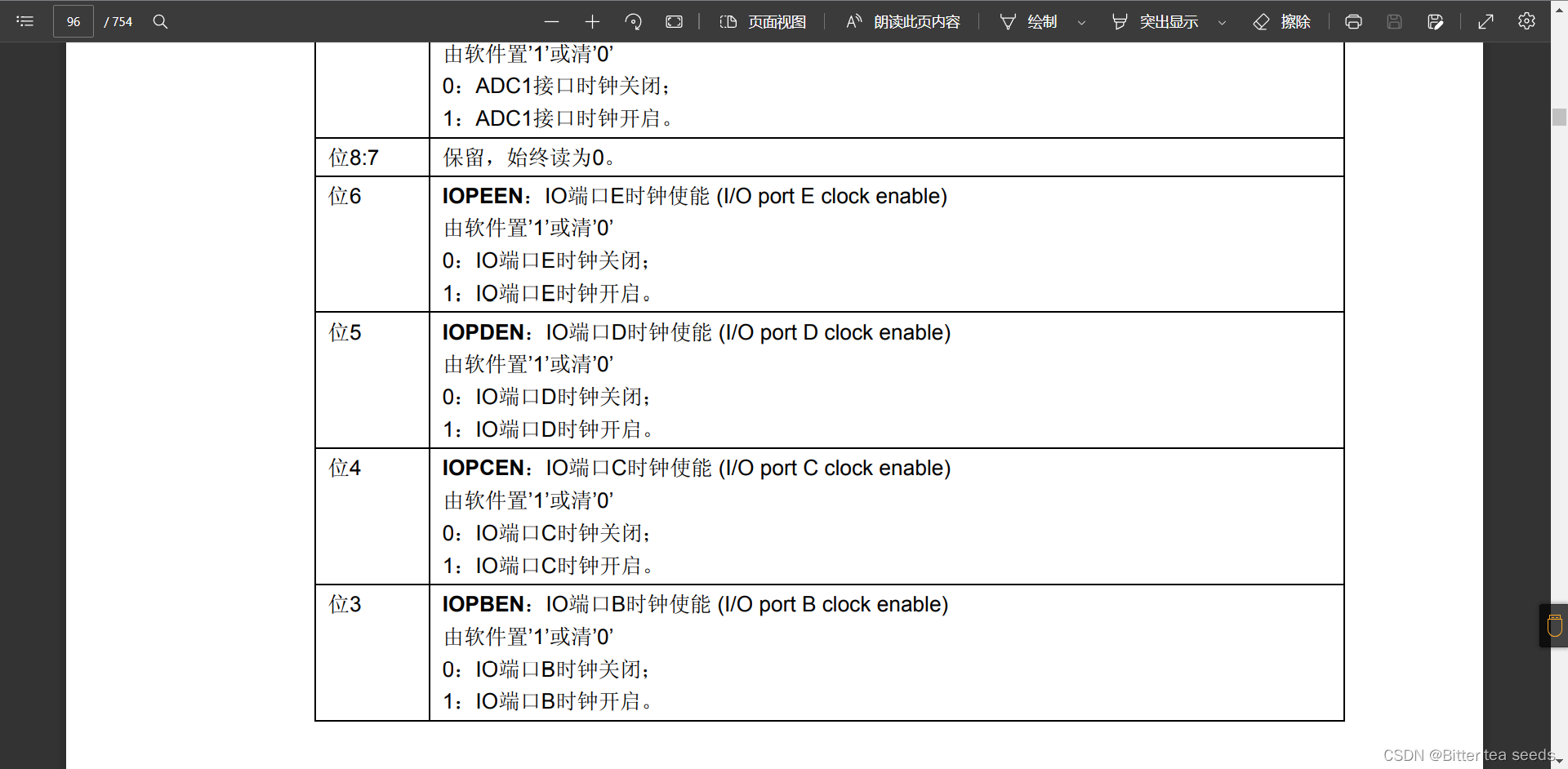
STM32 learning record: LED light flashes (register version)

Information security - threat detection engine - common rule engine base performance comparison
C language is the watershed between low-level and high-level
Basic Q & A of introductory C language
![[analysis of teacher Gao's software needs] collection of exercises and answers for level 20 cloud class](/img/3b/dc43564a36f82e73826b08f39c935e.png)
[analysis of teacher Gao's software needs] collection of exercises and answers for level 20 cloud class

Programmers, what are your skills in code writing?
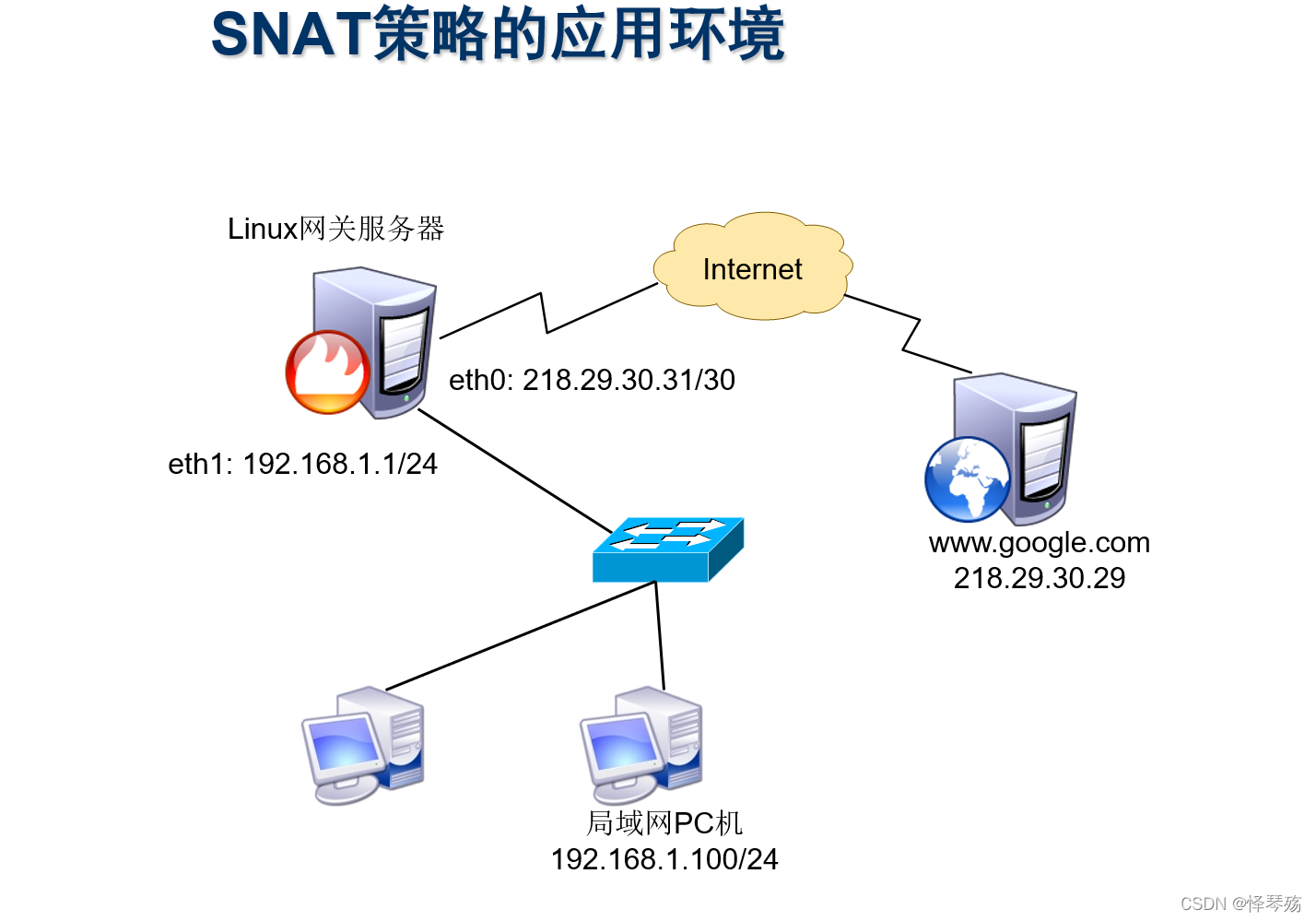
信息安全-威胁检测-NAT日志接入威胁检测平台详细设计

信息安全-史诗级漏洞Log4j的漏洞机理和防范措施
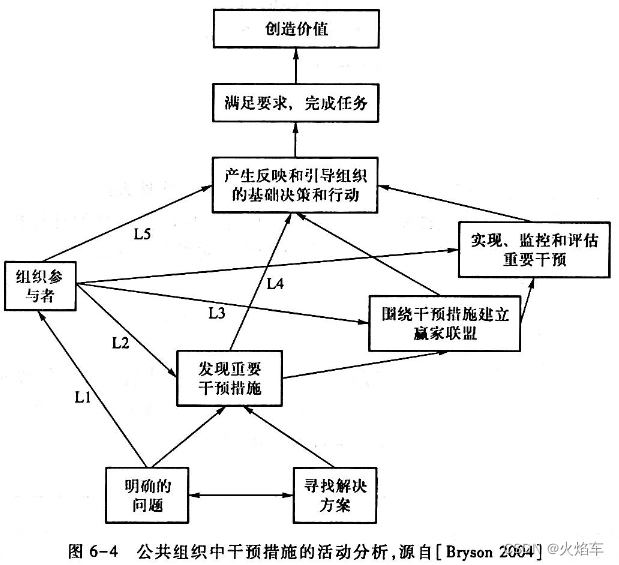
【高老师软件需求分析】20级云班课习题答案合集
随机推荐
C language is the watershed between low-level and high-level
[exercise-3] (UVA 442) matrix chain multiplication
Research Report on market supply and demand and strategy of China's earth drilling industry
【练习-4】(Uva 11988)Broken Keyboard(破损的键盘) ==(链表)
[exercise-9] Zombie's Treasury test
Write web games in C language
Nodejs+vue online fresh flower shop sales information system express+mysql
Quick to typescript Guide
C basic grammar
7-1 懂的都懂 (20 分)
Interesting drink
New to redis
TCP's three handshakes and four waves
[exercise 4-1] cake distribution
Penetration testing (5) -- a collection of practical skills of scanning King nmap and penetration testing tools
渗透测试 ( 3 ) --- Metasploit Framework ( MSF )
Flink 使用之 CEP
E. Breaking the Wall
【练习-2】(Uva 712) S-Trees (S树)
[exercise-4] (UVA 11988) broken keyboard = = (linked list)