当前位置:网站首页>Network Security Learning - Information Collection
Network Security Learning - Information Collection
2022-07-07 04:23:00 【haoaaao】
/**cdn Bypass 7. information gathering ——CDN Bypass technology · Language sparrow
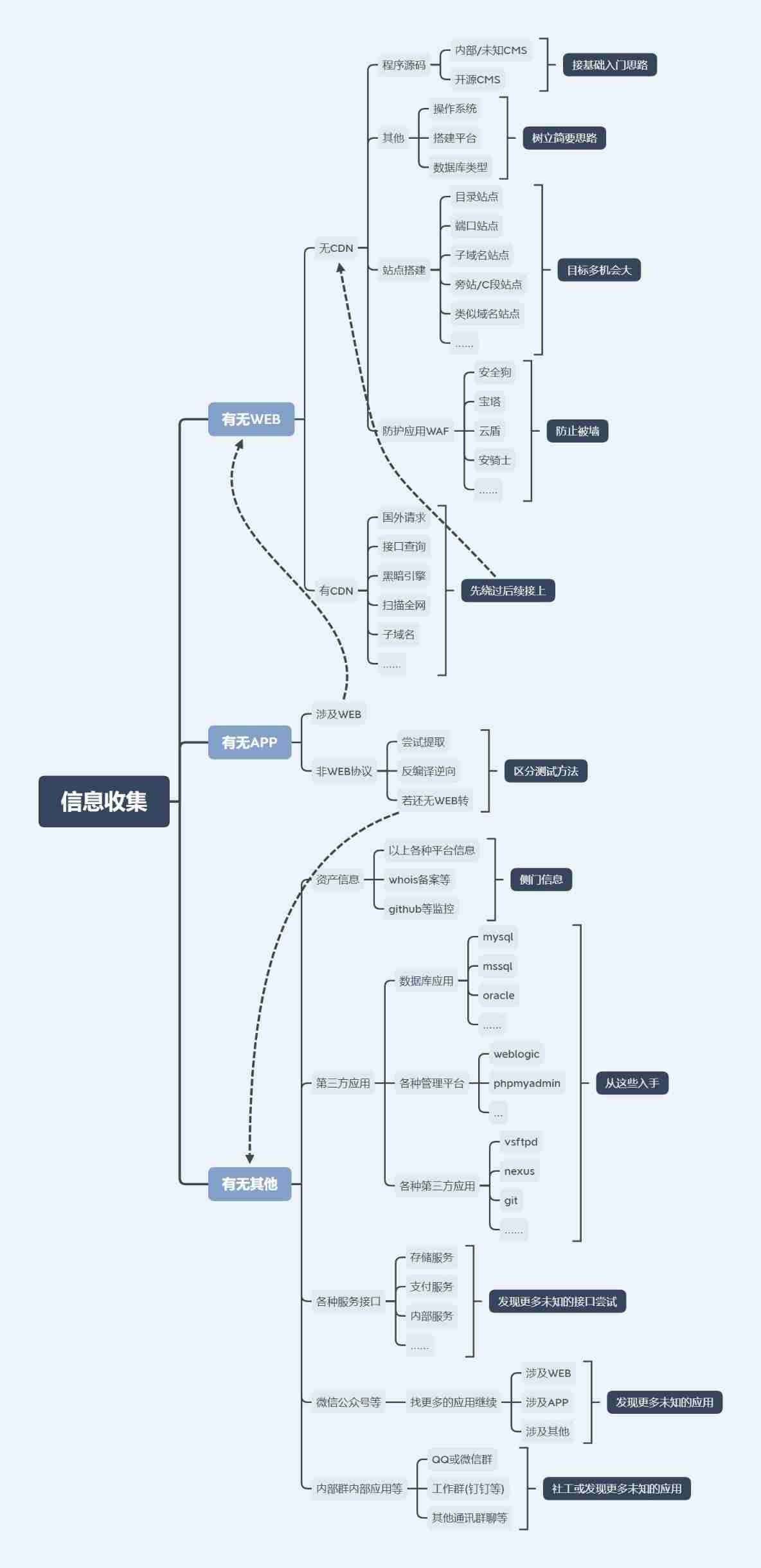
One 、 framework 、 build 、waf
1、 Site construction type :
(1) Directory site construction :
Same website , But in different directories , Building source code is also different , But a problem with one website will affect the other website .
Such as

Probe : Yujian and other directory scanning tools can find
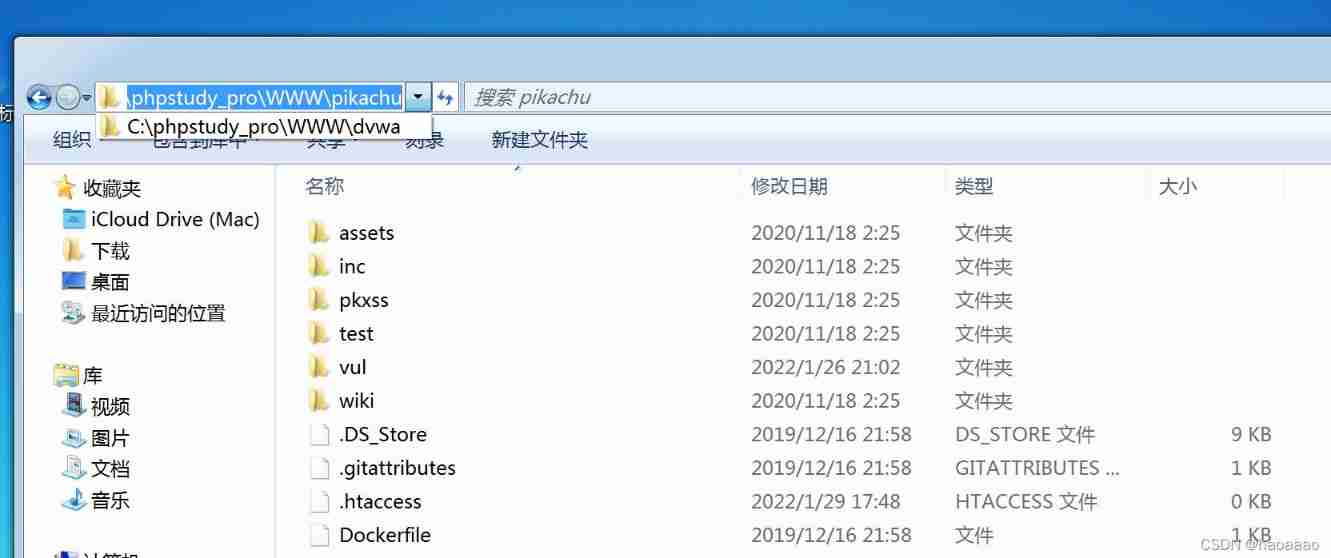
(2) Port class site
The website is located on the same server , But ports are different , For example, those target aircrafts built in practice ,dvwa yes 8023 port ,pikachu yes 8022 port
nmap Port scanning 、 Surf the Internet query
(3) Sub domain name class site
Search the subdomain name online ip,ip Different does not belong to the same server .
(4) Similar domain name sites
The domain name suffix is different , Such as .com and .cn, But from the same server or company .
(5) sidenote 、c Segment site
/** Excerpt from : 8. information gathering —— Site construction and WAF · Language sparrow **/
1) sidenote
Marginal note is an intrusion method , Literally, it means -" Inject... From the side ", Exploit the vulnerabilities of different websites on the same host to get webshell, Thus, the physical path of the user exposed by the program or service on the host can be used for intrusion . Different sites on the same server . Two or more websites are placed on the same server , One of the websites is the target .
Implementable premise :
There are multiple site servers ;
www.a.com( The goal is )
www.b.com
........
Stand alone site server
2)c paragraph
Different servers and different sites in the same network segment . The website has one or more sites , Through the server IP Address of the network segment to test .
192.168.1.1
www.a.com( The goal is )
www.b.com
........
192.168.1.101
www.a.com
www.b.com
........
By querying the network segment 1-254, To get 101 Network segment server permissions , The test method of implementing intranet security through the target host of the same network segment of the server , To obtain the permission of the specified web server .
(6) Build software
Such as phpstudy、 Pagoda and other building software ; f12 View site information , Generally, software with complete information is built , Such as : Apache/2.4.41(win32)OpenSSL/1.1.1c mod_fcgid/2.3.9a;
Similar building software usually has a default account password or security settings , Such as :/phpmyadmin Catalog
2、WAF
(1) brief introduction ( Baidu Encyclopedia )
Web Application protection system ( Also known as : Website Application level intrusion prevention system . english :Web Application Firewall, abbreviation : WAF). utilize The international A generally accepted saying :Web application A firewall It's through the execution of a series of HTTP/HTTPS Of The security policy Come for Web An application that provides protection ;
Web Application protection system (Web Application Firewall, abbreviation :WAF) It represents a new kind of information security technology , To solve the problem that traditional devices such as firewalls are helpless Web Application security issues . Unlike traditional firewalls ,WAF Working in the application layer , So right. Web Application protection has inherent technical advantages . Based on the Web Apply a deep understanding of business and logic ,WAF from Web All kinds of requests from application clients are used for content detection and verification , Ensure its security and legitimacy , Block illegal requests in real time , So as to effectively protect all kinds of websites .
(2) How to quickly identify waf:wafw00f
1)wafw00f Download and install :
github Address :https://github.com/EnableSecurity/wafw00f
kali Bring their own wafw00f:
a、 Start command :wafw00f -l
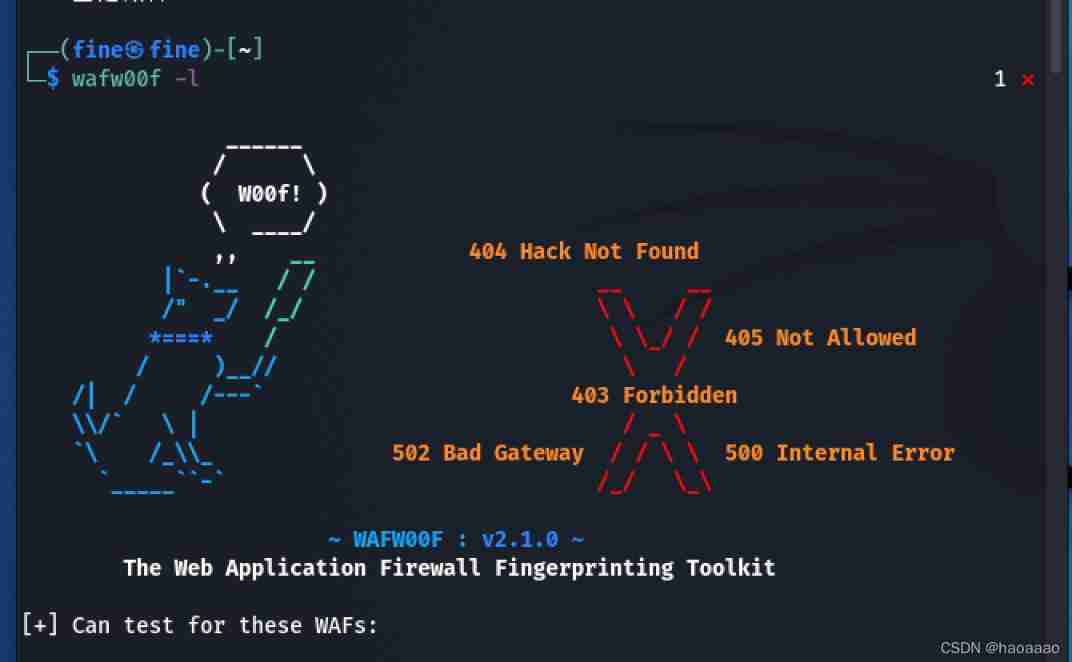
b、 Use command :wafw00f domain name /ip
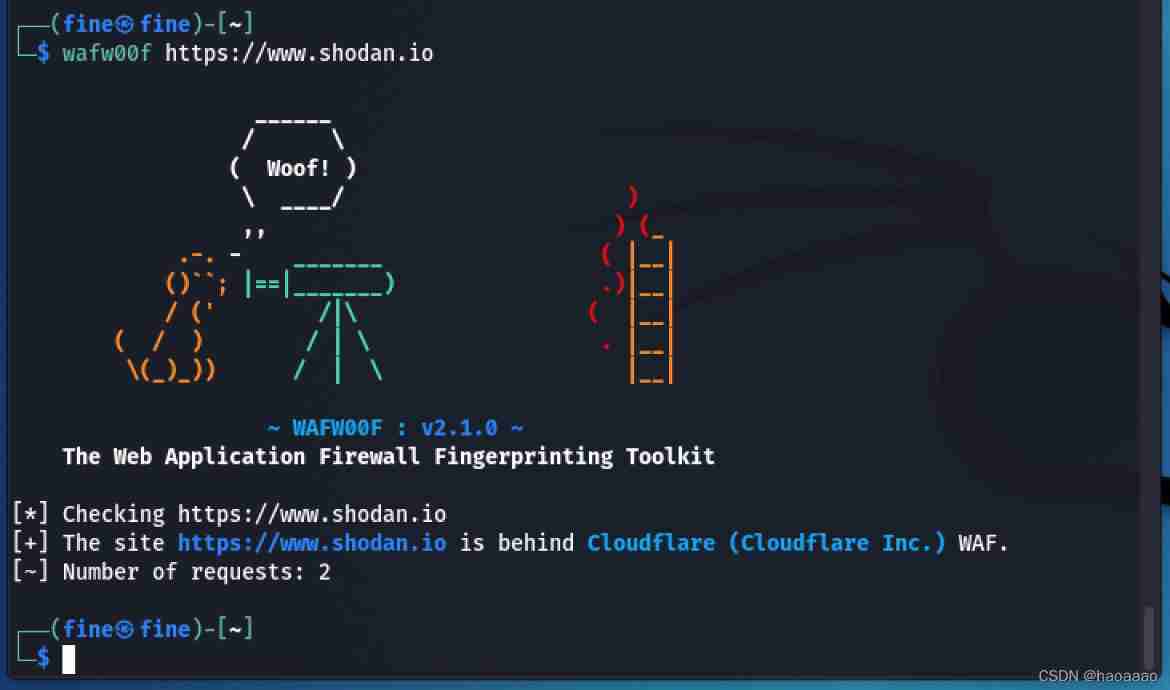
2)sqlmap:
command :python sqlmap.py -u “url” --identify-waf
Two 、app And other assets
1、app Extraction, bag capturing and subsequent cooperation
(1) some apk One click extraction decompilation
A big hole is missing for installation and use :
(2) Use burp History catches more url
2、 some ip nothing web Third party testing ideas under the framework
(1) Random scanning of various ports
nmap、 Search engine (shodan、 Zhong Kui's eyes 、fofa.info etc. )
/** Friends, yuan fofa By b Station a live broadcast to * standing , Leading to fofa It was hacked by the Ministry of industry and information technology and can't be used ***/
eg:
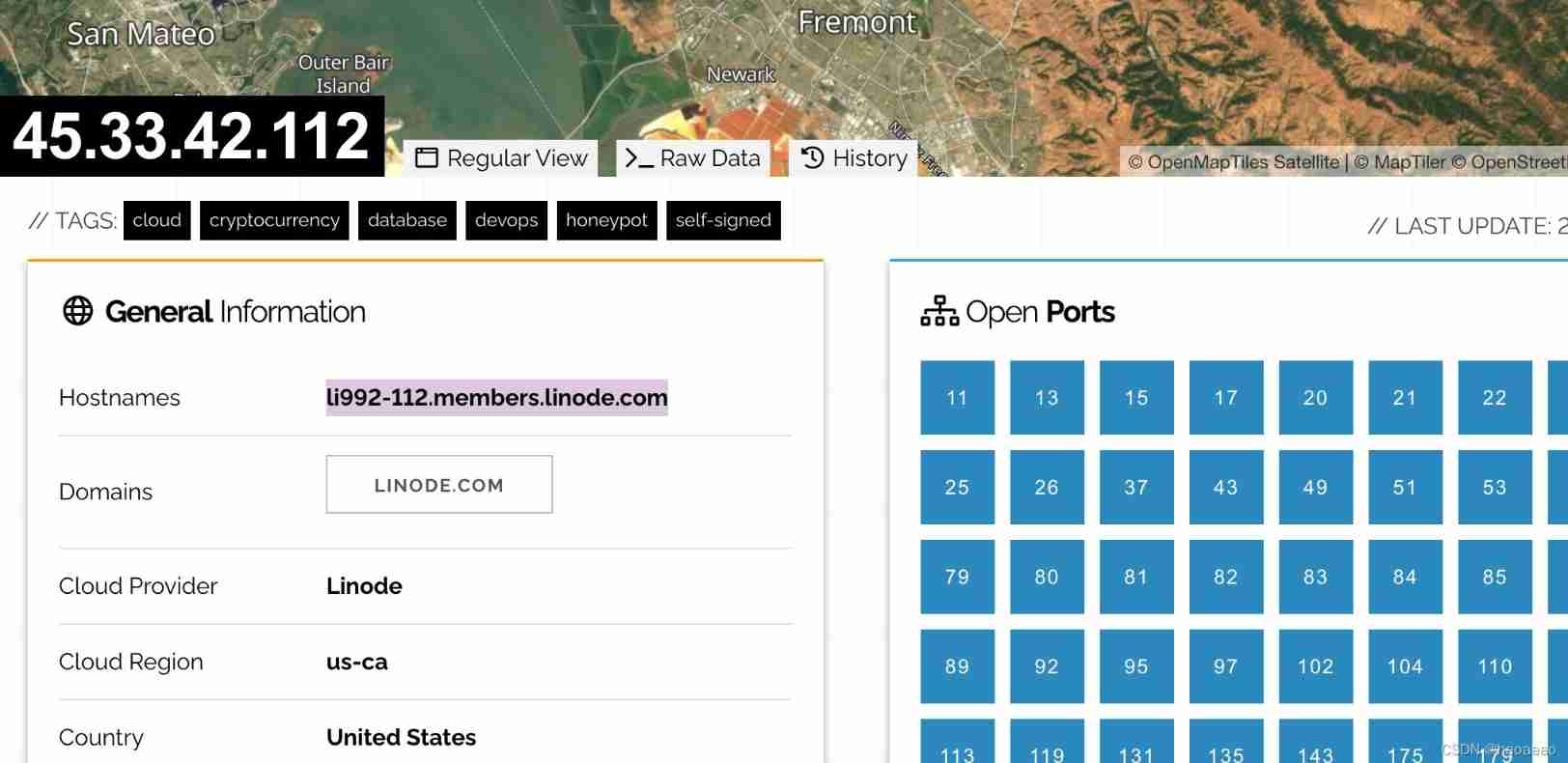
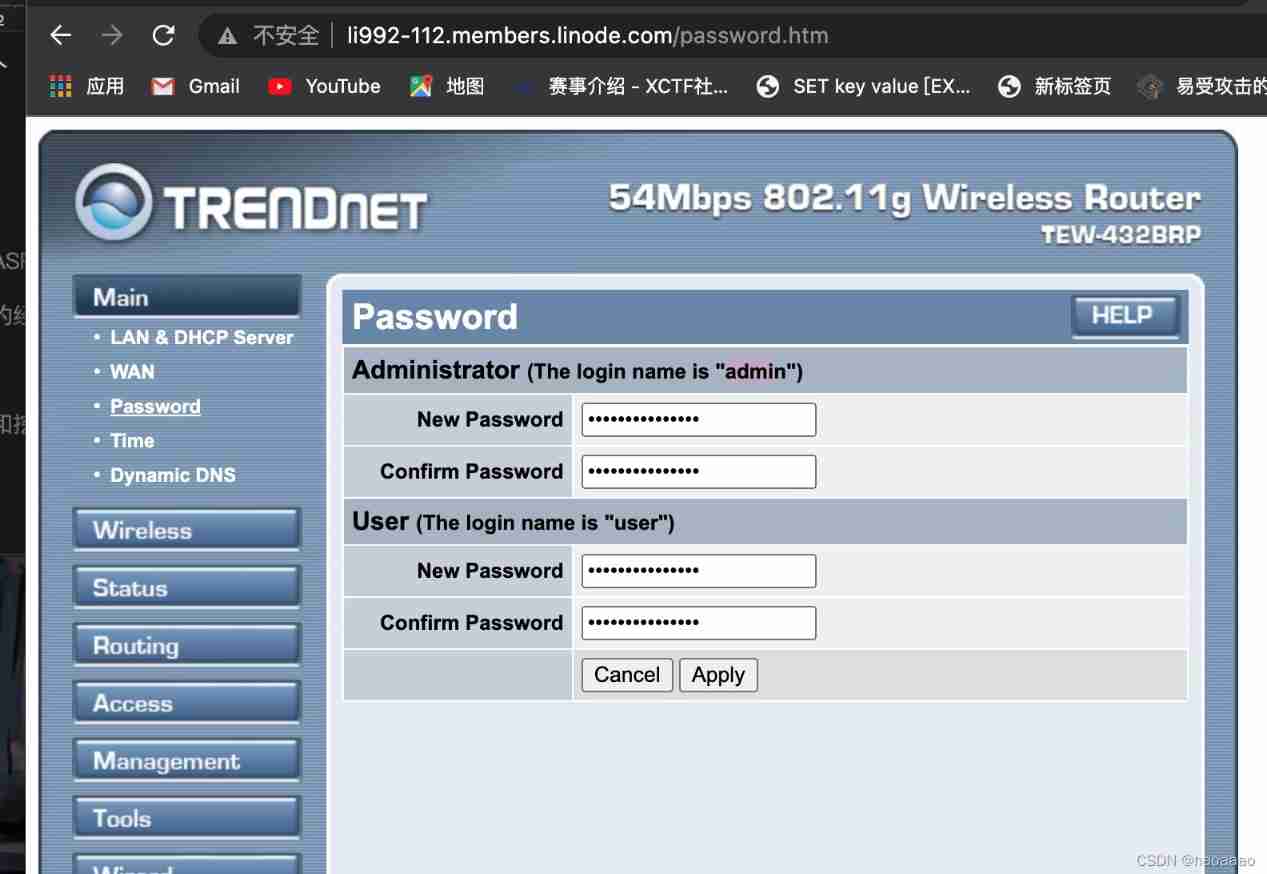
(2) Various interfaces are scanned randomly
(3) Various interface tests
3、 example ( A pyramid selling website )
(1) Check out the website
(2) Collect all kinds of information :
1) Search domain name , Check various ports
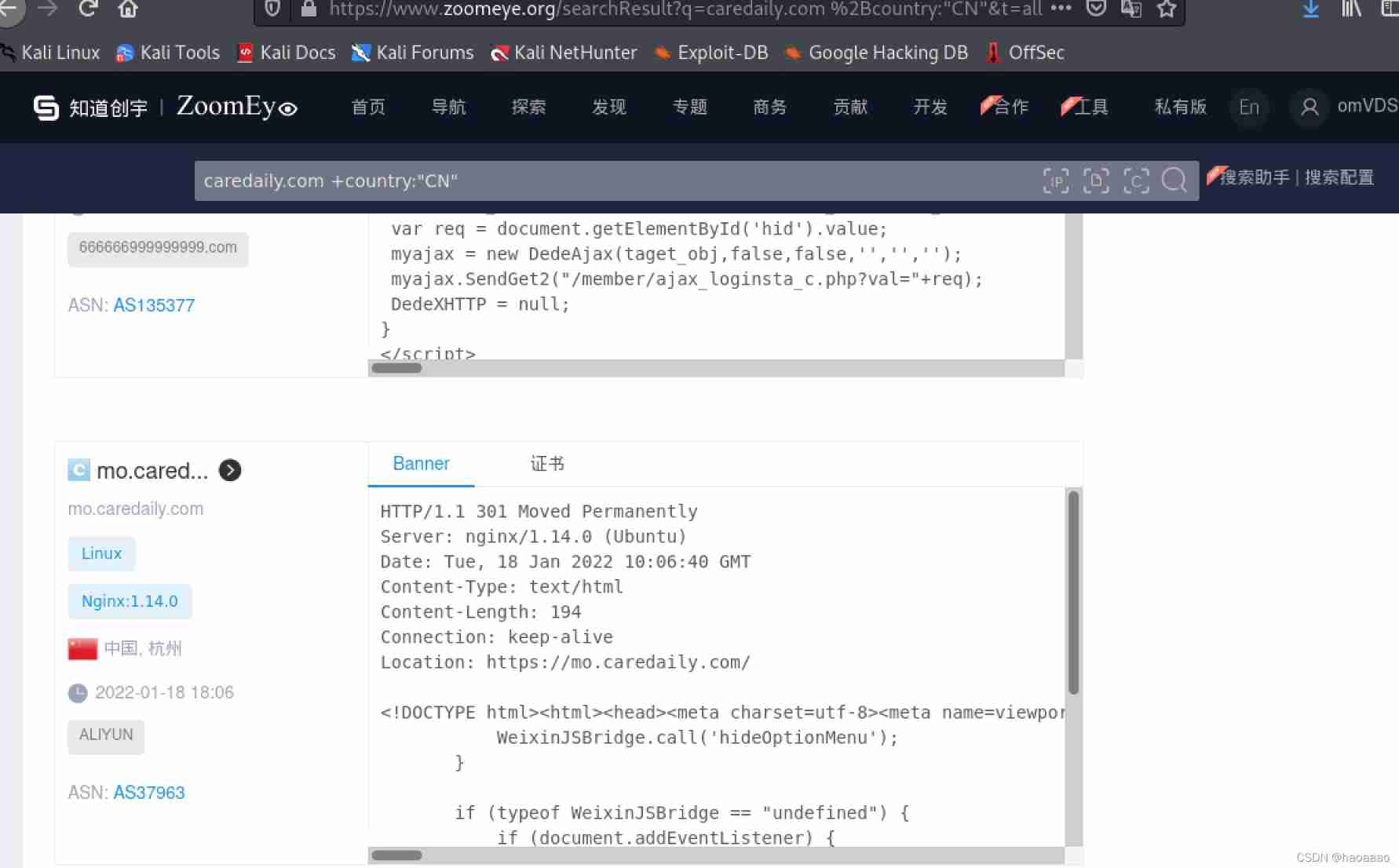
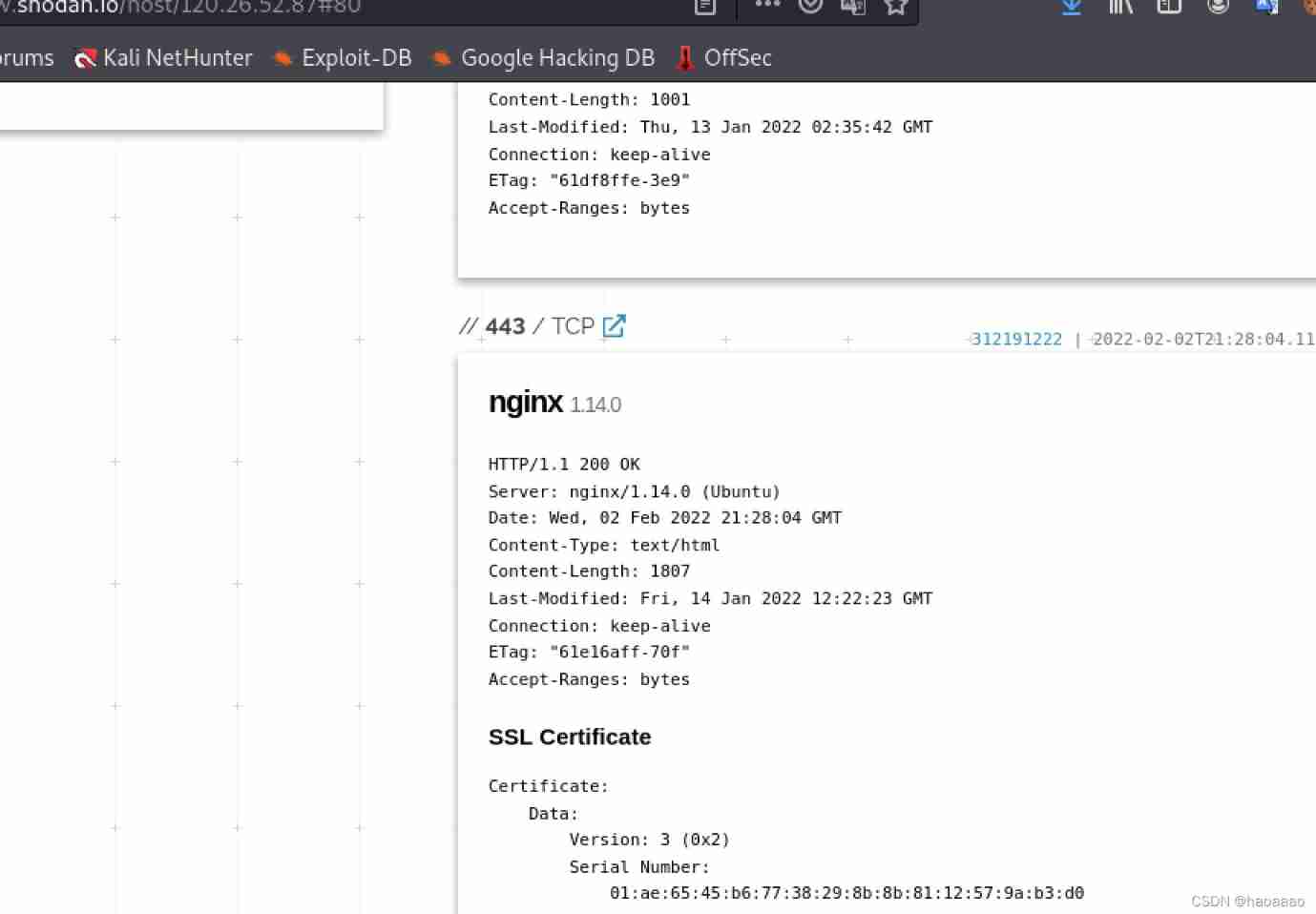
Find login port
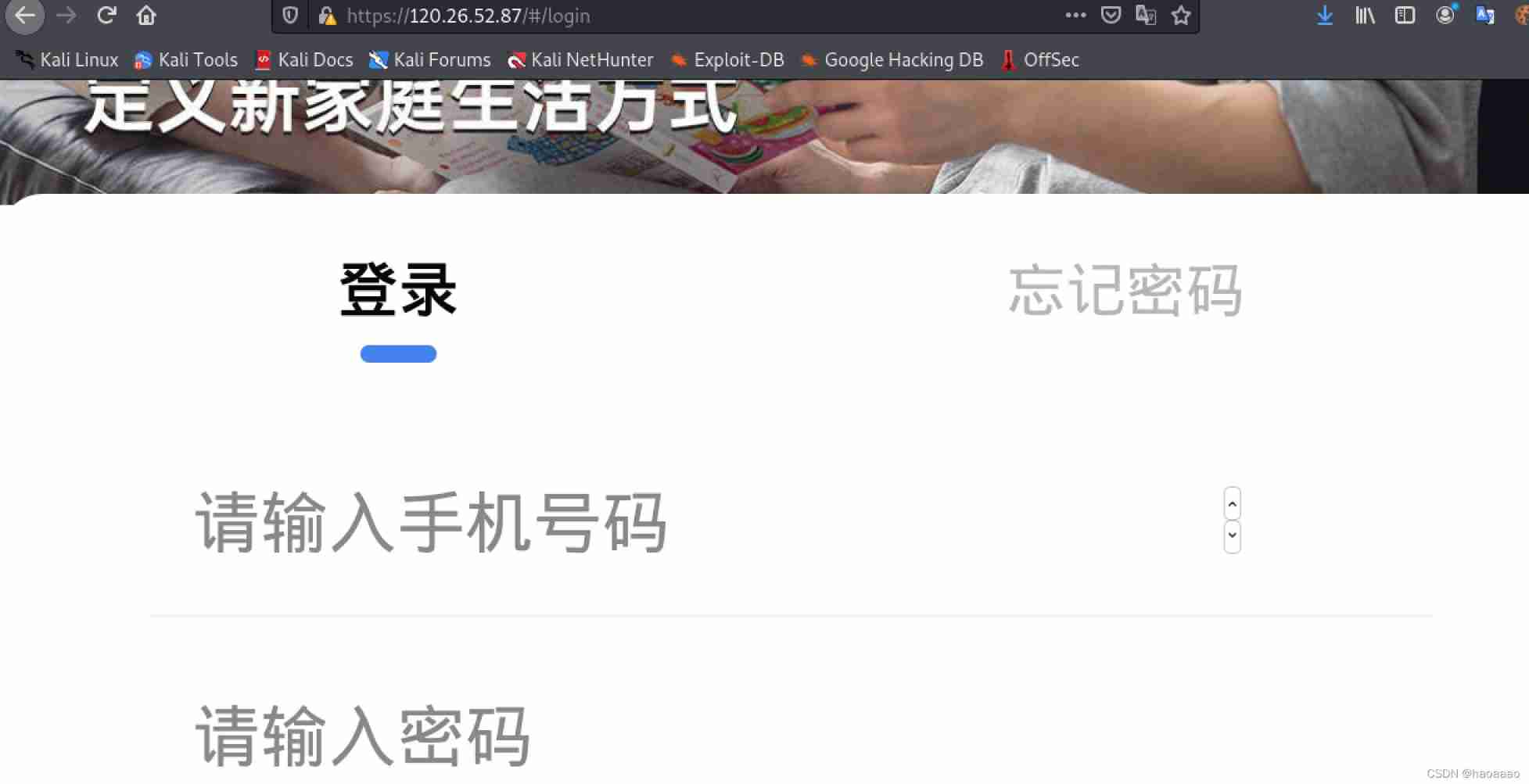
2)ping The website finds the truth ip
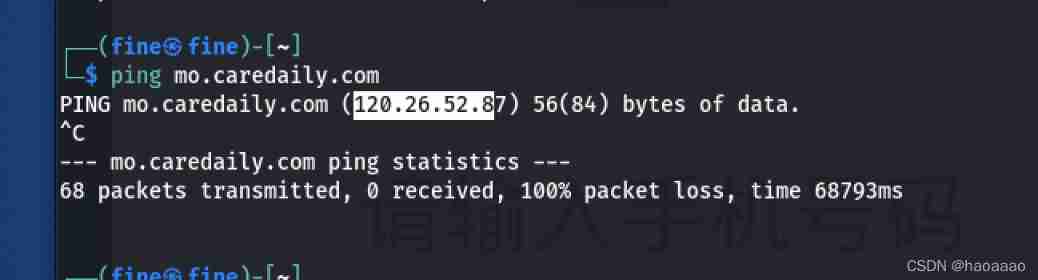
Subdomain query
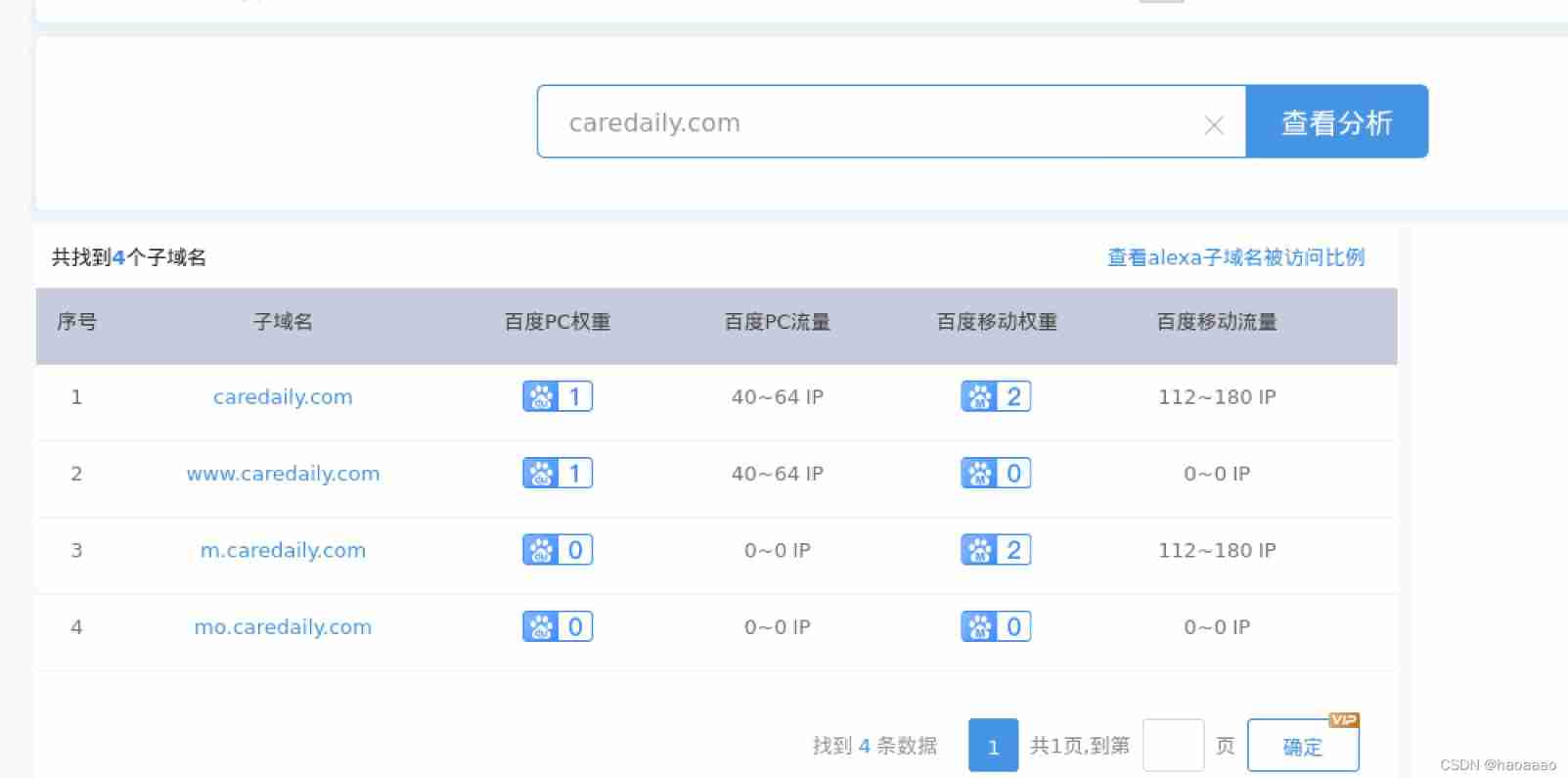
Marginal query
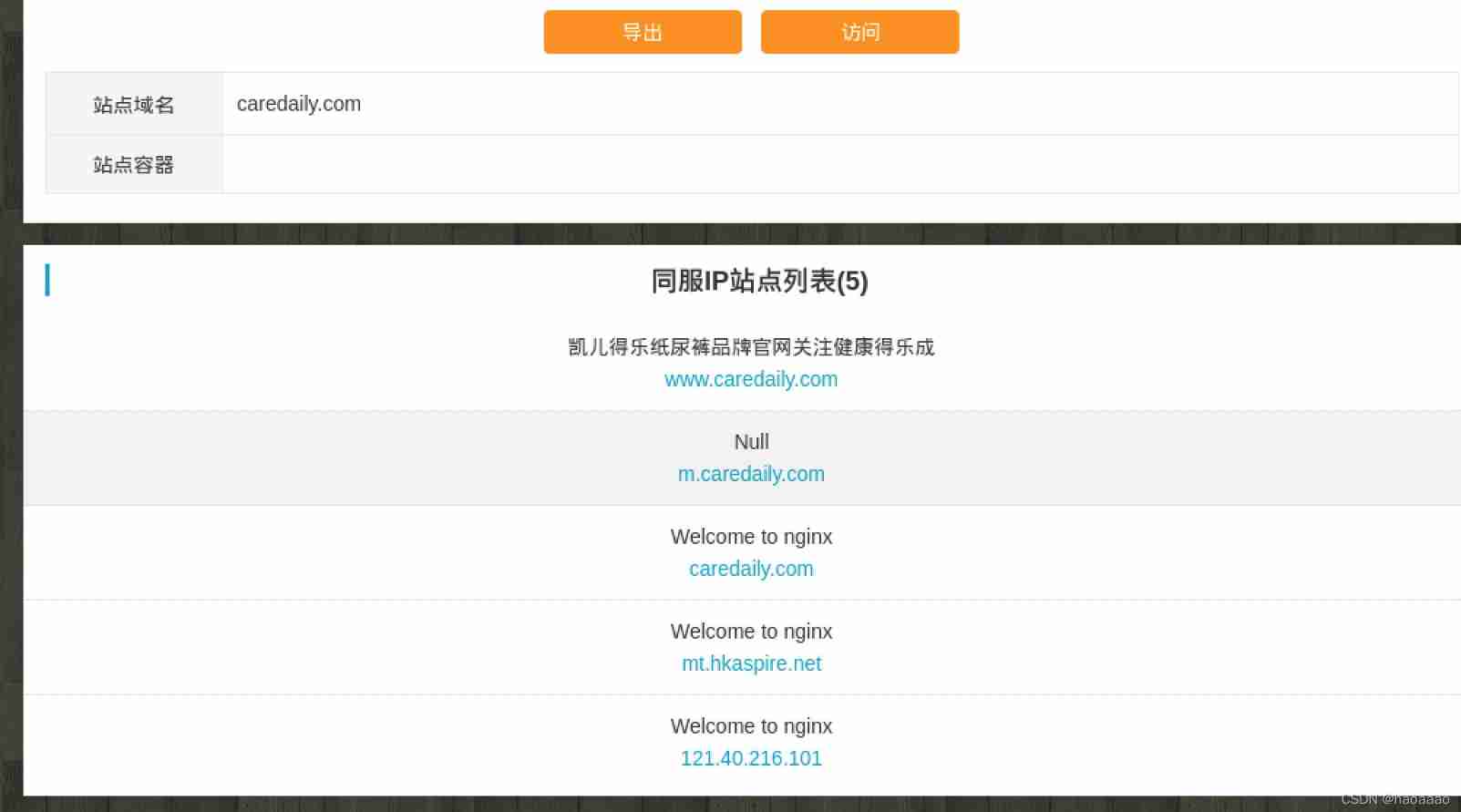
3) Record query
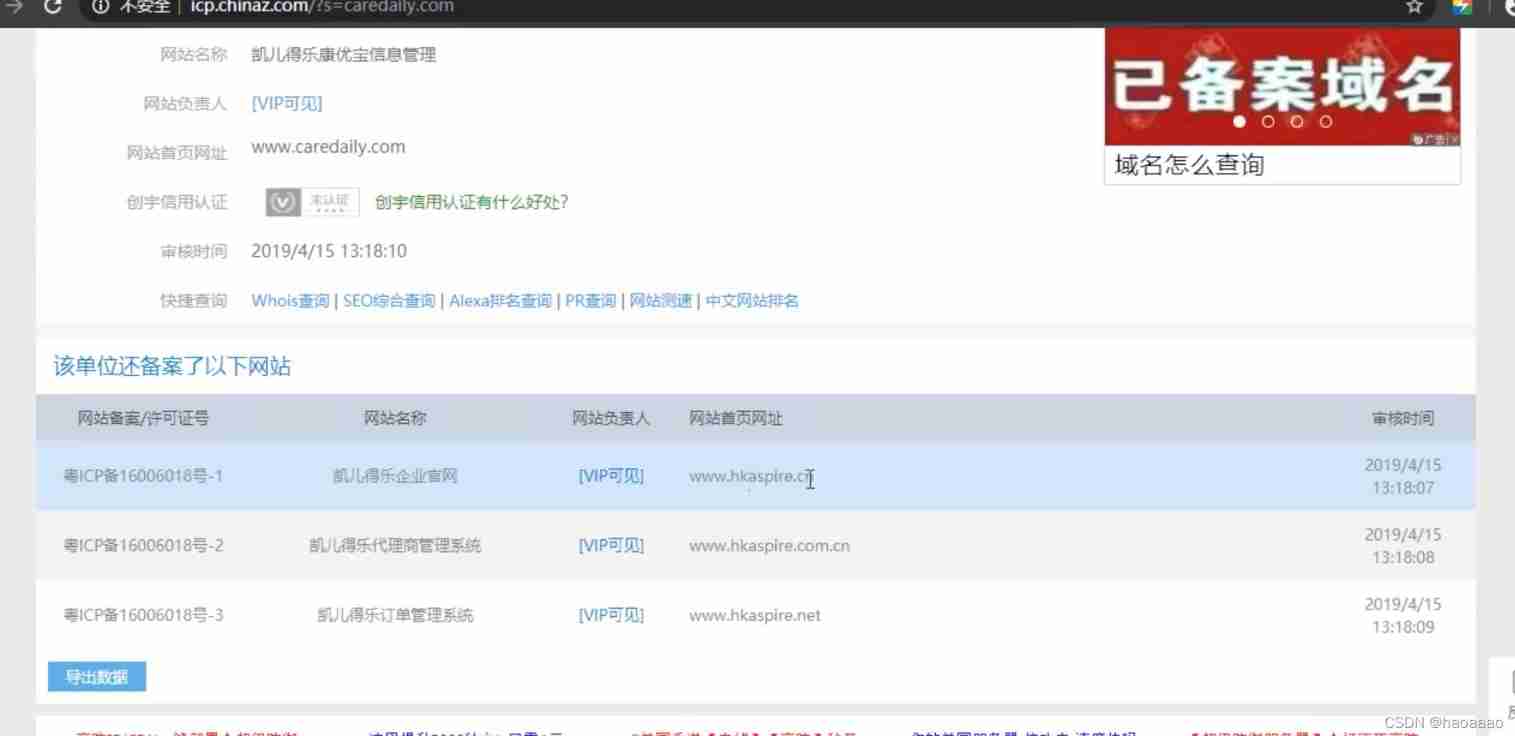

3、 ... and 、 Asset monitoring expansion
1、POC、EXP、Payload And Shellcode
(1) POC: Full name ' Proof of Concept ', chinese ' Proof of concept ' , It often refers to a piece of code that proves a vulnerability .
EXP: Full name ' Exploit ', chinese ' utilize ', It refers to the action of using system vulnerability to attack .
Payload: chinese ' Payload ', Success exploit after , Code or instruction actually executed in the target system .
Shellcode: Simple translation ' shell Code ', yes Payload A kind of , Because of its positive establishment / reverse shell And get the name .
(2)POC Is used to prove the existence of vulnerabilities ,EXP Is used to exploit vulnerabilities , The two are usually not in the same category , Or say ,PoC It's usually harmless ,Exp Usually harmful , With POC, Only then EXP.
Payload There are many kinds of , It can be Shellcode, It can also be a system command directly . The same Payload Can be used for multiple vulnerabilities , But each vulnerability has its own EXP, In other words, there is no universal EXP.
Shellcode There are many kinds , Including positive , In reverse , even to the extent that meterpreter.
Shellcode And Shellshcok Is not a ,Shellshock especially 14 Discovered in 2003 Shellshock Loophole .
2、github monitor

3、 Various collections
4、 demonstration : Monitor the latest EXP Release and others
(1) The code is as follows :
#Title: wechat push CVE-2020
#Date: 2020-5-9
#Exploit Author: weixiao9188
#Version: 4.0
#Tested on: Linux,windows
#cd /root/sh/git/ && nohup python3 /root/sh/git/git.py &
#coding:UTF-8
import requests
import json
import time
import os
import pandas as pd
time_sleep = 60 # every other 20 Climb once a second
while(True):
headers1 = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko)Chrome/70.0.3538.25 Safari/537.36 Core/1.70.3741.400 QQBrowser/10.5.3863.400"}
# Judge whether the file exists
datas = []
response1=None
response2=None
if os.path.exists("olddata.csv"):
# If the file exists, each crawl 10 individual
df = pd.read_csv("olddata.csv", header=None)
datas = df.where(df.notnull(),None).values.tolist()# In the extracted data nan Turn into None
requests.packages.urllib3.disable_warnings()
response1 = requests.get(url="https://api.github.com/search/repositories?q=CVE2020&sort=updated&per_page=10",headers=headers1,verify=False)
response2 = requests.get(url="https://api.github.com/search/repositories?q=RCE&ssort=updated&per_page=10",headers=headers1,verify=False)
else:
# There is no crawling all
datas = []
requests.packages.urllib3.disable_warnings()
response1 = requests.get(url="https://api.github.com/search/repositories?q=CVE2020&sort=updated&order=desc",headers=headers1,verify=False)
response2 = requests.get(url="https://api.github.com/search/repositories?q=RCE&ssort=updated&order=desc",headers=headers1,verify=False)
data1 = json.loads(response1.text)
data2 = json.loads(response2.text)
for j in [data1["items"],data2["items"]]:
for i in j:
s = {"name":i['name'],"html":i['html_url'],"description":i['description']}
s1 =[i['name'],i['html_url'],i['description']]
if s1 not in datas:
#print(s1)
#print(datas)
params = {
"text":s["name"],
"desp":" link :"+str(s["html"])+"\n brief introduction "+str(s["description"])
}
print(" The current push is "+str(s)+"\n")
#print(params)
requests.packages.urllib3.disable_warnings()
requests.get("https://sct.ftqq.com/SCT120223TgU9or8Qt2deaV50HnarzVRBN.send",params=params,headers=headers1,timeout=10,verify=False)
time.sleep(1) # Prevent pushing too hard
print(" Push complete \n")
datas.append(s1)
else:
pass
print(" Data already in !")
pd.DataFrame(datas).to_csv("olddata.csv",header=None,index=None)
time.sleep(time_sleep)
(2) step :
1) stay sct.ftqq.com Scan wechat account , obtain sendkey:
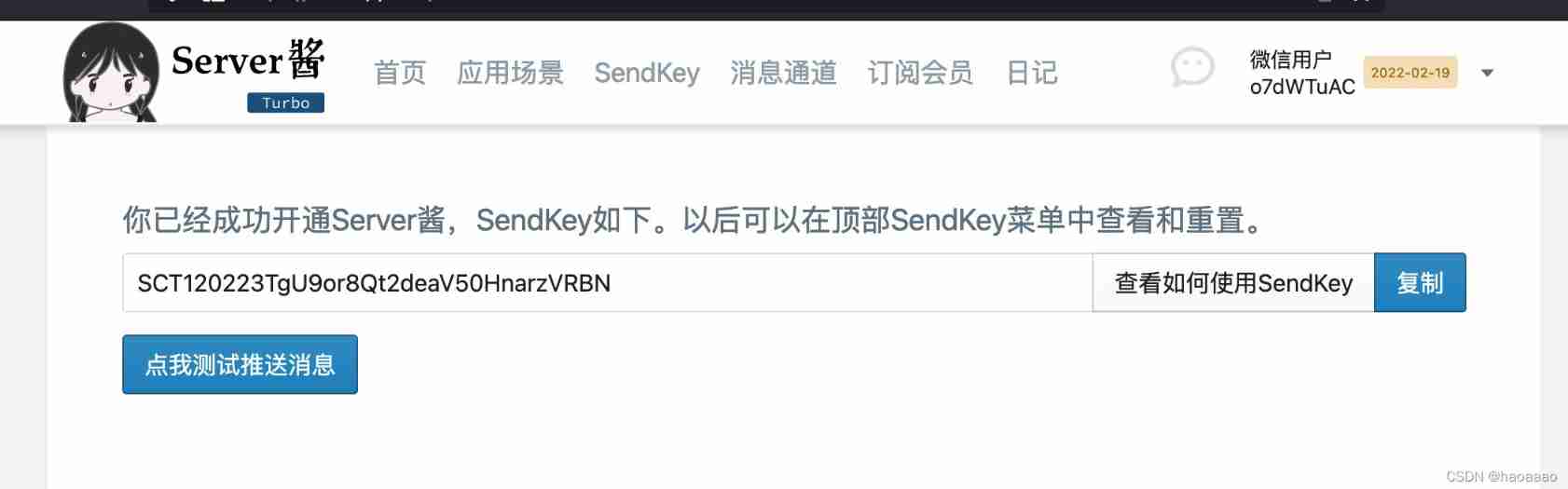
2) take sendkey Copy value to requests.get here :
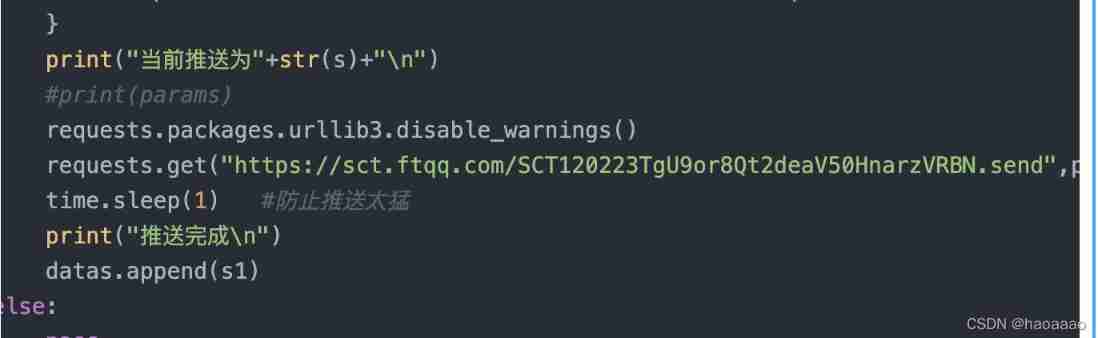
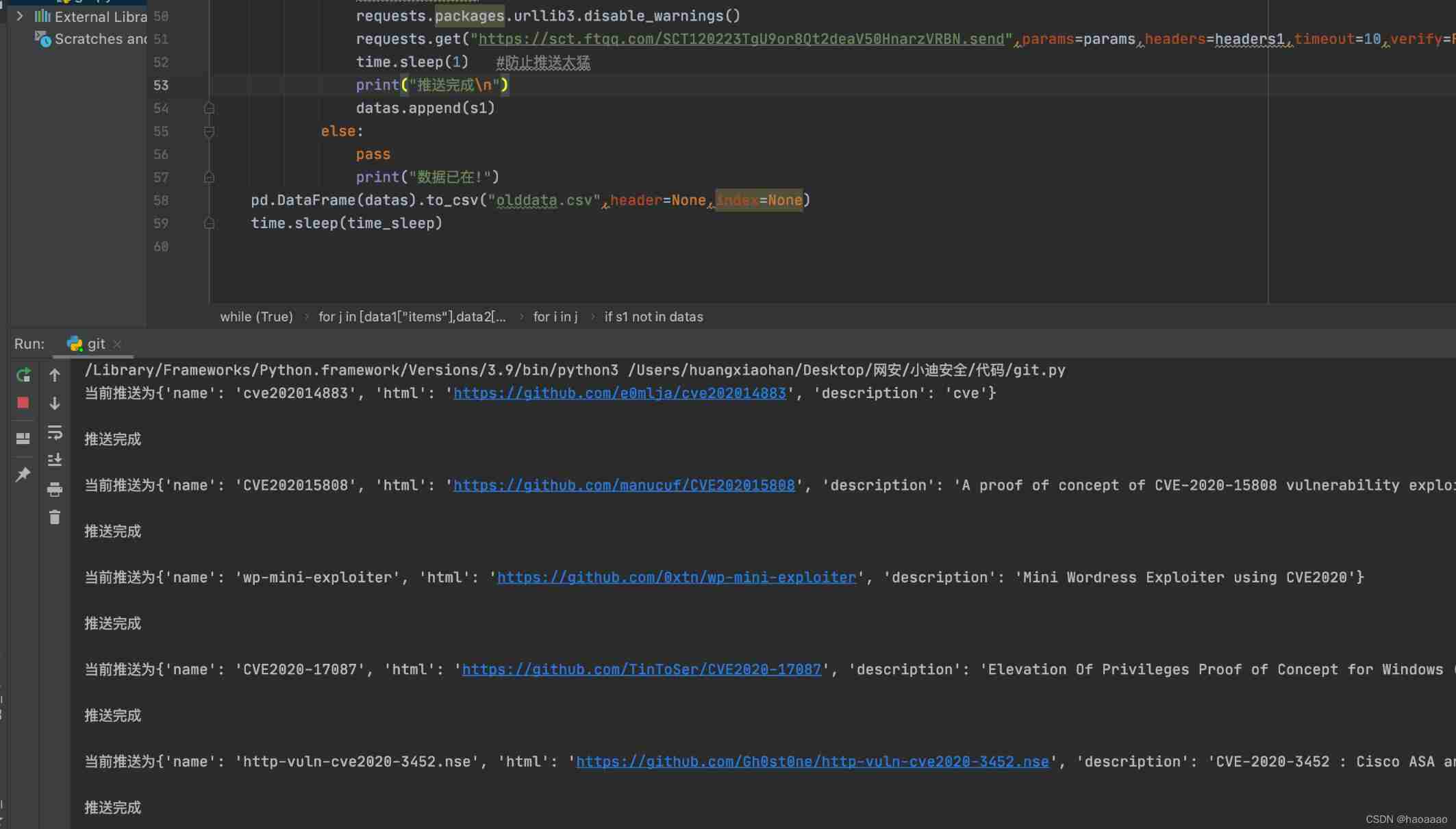
3) Execution results :
边栏推荐
- Some common software related
- Unity3d can change colors and display samples in a building GL material
- [team learning] [34 issues] scratch (Level 2)
- [written to the person who first published the paper] common problems in writing comprehensive scientific and Technological Papers
- leetcode 53. Maximum subarray maximum subarray sum (medium)
- 中青杯2022A题高校数学建模竞赛与课程教育思路分析
- [on automation experience] the growth path of automated testing
- ESG全球领导者峰会|英特尔王锐:以科技之力应对全球气候挑战
- Analysis on the thinking of college mathematical modeling competition and curriculum education of the 2022a question of the China Youth Cup
- [multi threading exercise] write a multi threading example of the producer consumer model.
猜你喜欢
2022 electrician cup question B analysis of emergency materials distribution under 5g network environment
Simple implementation of AVL tree insertion and verification operations
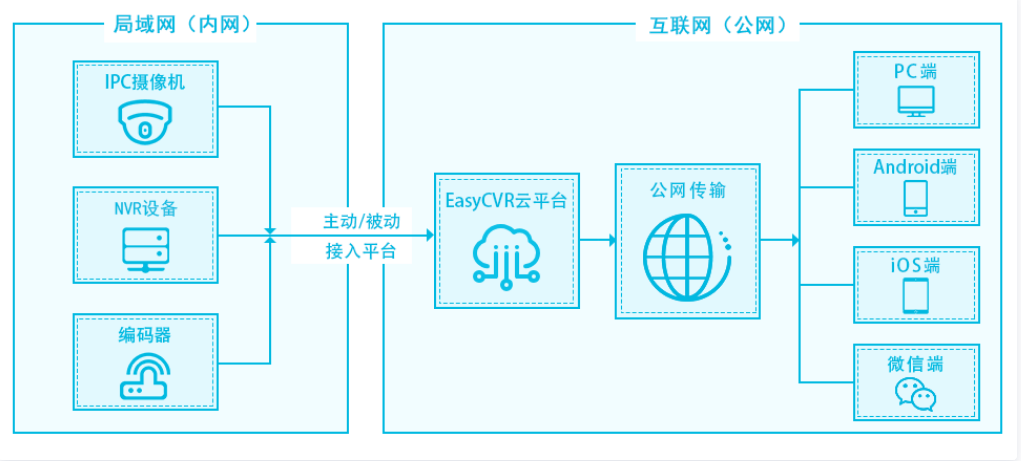
Optimization of channel status offline of other server devices caused by easycvr cluster restart
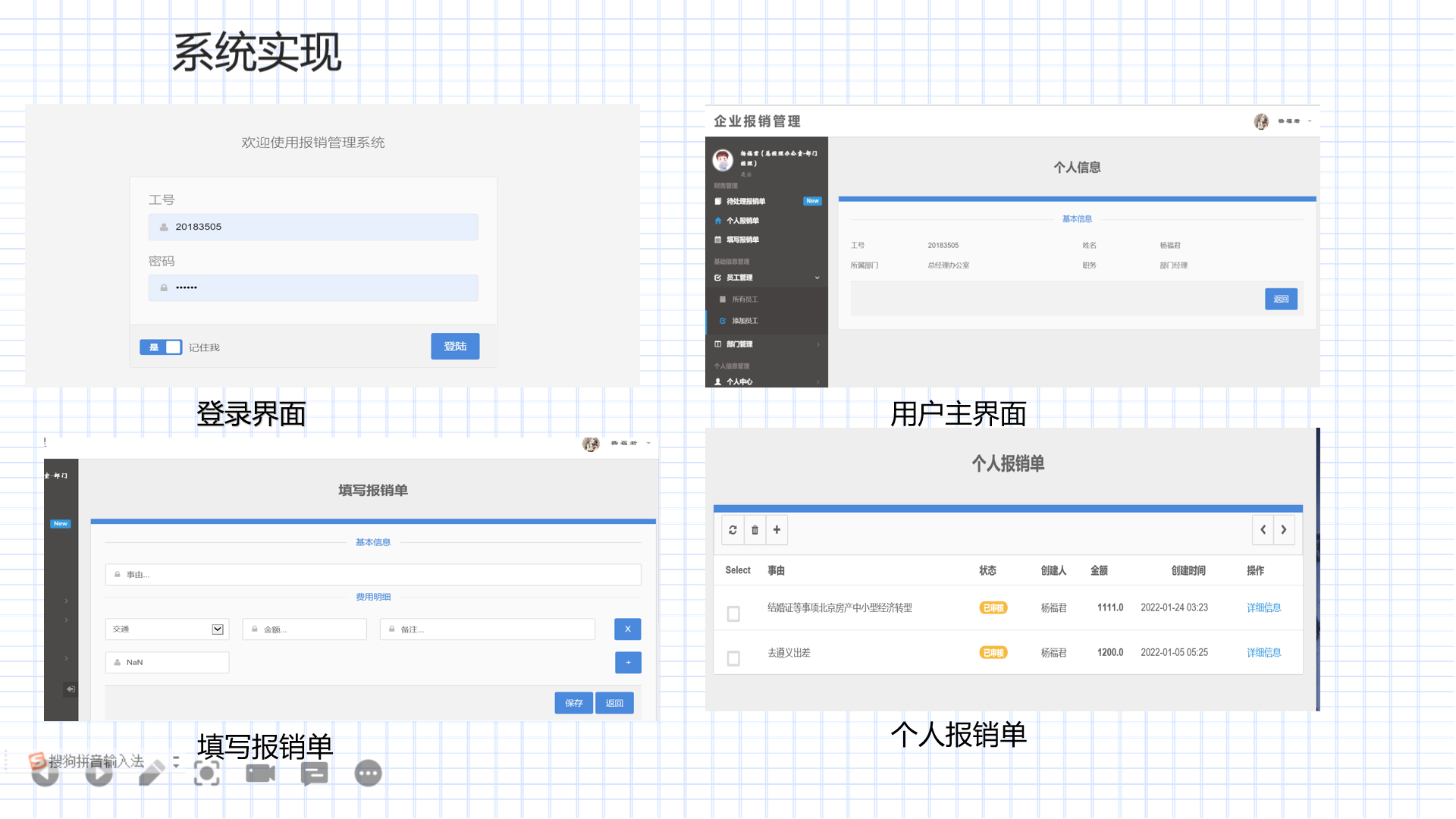
SSM+JSP实现企业管理系统(OA管理系统源码+数据库+文档+PPT)
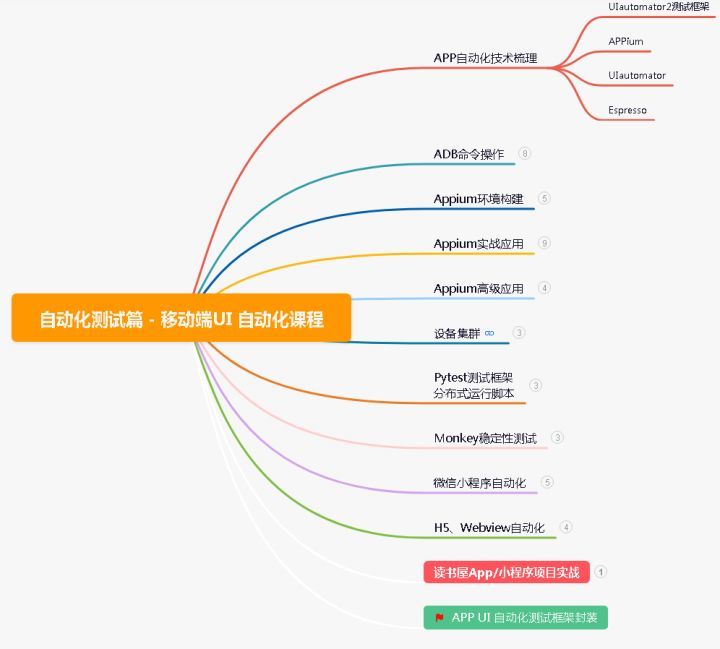
Five years of automated testing, and finally into the ByteDance, the annual salary of 30W is not out of reach
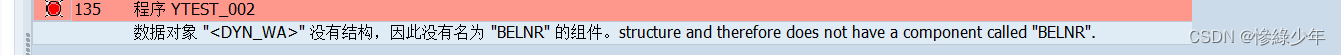
ABAP 动态内表分组循环
![[team learning] [34 issues] scratch (Level 2)](/img/29/8383d753eedcffd874bc3f0194152a.jpg)
[team learning] [34 issues] scratch (Level 2)
各路行业大佬称赞的跨架构开发“神器”,你get同款了吗?

EasyCVR平台接入RTMP协议,接口调用提示获取录像错误该如何解决?
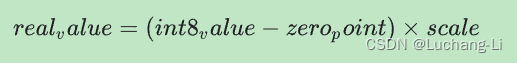
Tflite model transformation and quantification
随机推荐
[OA] excel document generator: openpyxl module
[untitled]
easyui出口excel无法下载框弹出的办法来解决
C # use Siemens S7 protocol to read and write PLC DB block
True global ventures' newly established $146million follow-up fund was closed, of which the general partner subscribed $62million to invest in Web3 winners in the later stage
Redis source code learning (31), dictionary learning, dict.c (1)
Use facet to record operation log
Food Chem|深度学习根据成分声明准确预测食品类别和营养成分
Implementation of map and set
EasyCVR视频广场点击播放时,主菜单高亮效果消失问题的修复
什么是 CGI,什么是 IIS,什么是VPS「建议收藏」
The most complete learning rate adjustment strategy in history LR_ scheduler
One of oscp tools: dirsearch usage Encyclopedia
[team learning] [34 sessions] Alibaba cloud Tianchi online programming training camp
【刷题记录】2. 两数相加
Win11控制面板快捷键 Win11打开控制面板的多种方法
True Global Ventures新成立的1.46亿美元后续基金关账,其中普通合伙人认缴6,200万美元以对后期阶段的Web3赢家进行投资
機器人(自動化)課程的持續學習-2022-
Formation continue en robotique (automatisation) - 2022 -
MySQL data loss, analyze binlog log file