当前位置:网站首页>Getting started with rce
Getting started with rce
2022-07-05 13:54:00 【Cwxh0125】
brief introduction
Command Injection, Command injection , It means to destroy the structure of command statement by submitting maliciously constructed parameters , So as to achieve the purpose of executing malicious commands .PHP The command injection exploit is PHP One of the common scripting vulnerabilities in applications .
When the application needs to call some external programs to process the content , It will use some functions to execute system commands . Such as PHP Medium system,exec,shell_exec etc. , When the user can control the parameters in the command execution function , Inject malicious system commands into normal commands , Cause command execution attacks . ------------ Training documents
Divided into remote command execution ping And remote code execution evel.
The reason for the vulnerability : There is no input processing at the input port .
Our common router 、 A firewall 、 Intrusion detection and other devices web On the management interface
Case study
With pikachu Two lanes of the shooting range RCE As an example
One .exec"ping"
Generally, users will be provided with a ping Operation of the web Interface , User from web Input target on the interface IP, After submission , The backstage will be right for IP Address once ping test , And return the test results . In fact, this is an interface , It allows attackers to inject operating system commands or code directly into the background server , To control the background system , This is it. RCE Loophole . The specific back-end code is as follows :
$result.=shell_exec('ping '.$ip);// Splice variables directly , I didn't deal with it
Try first ping Baidu
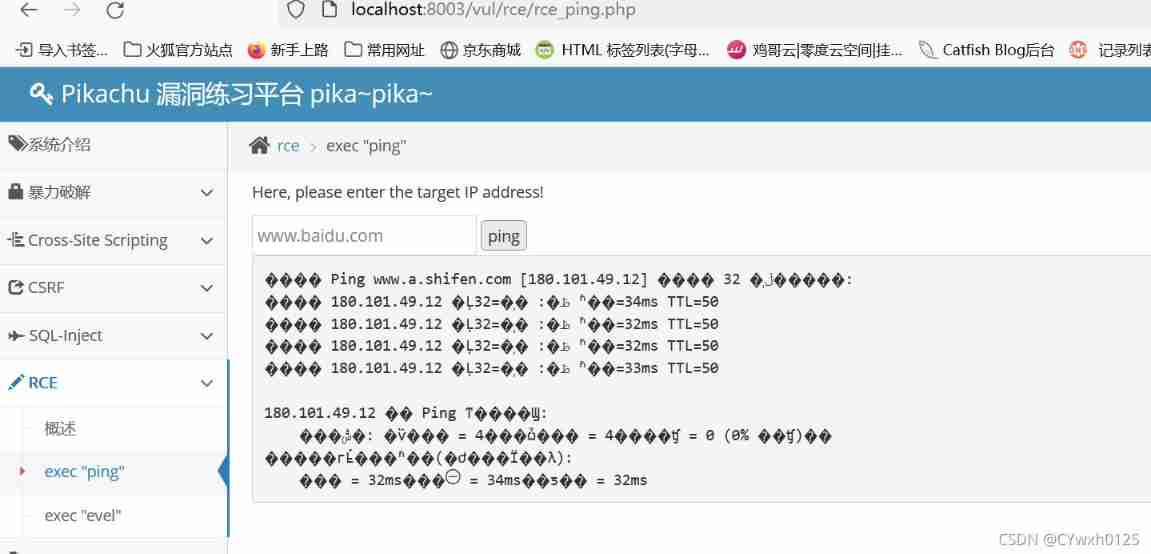
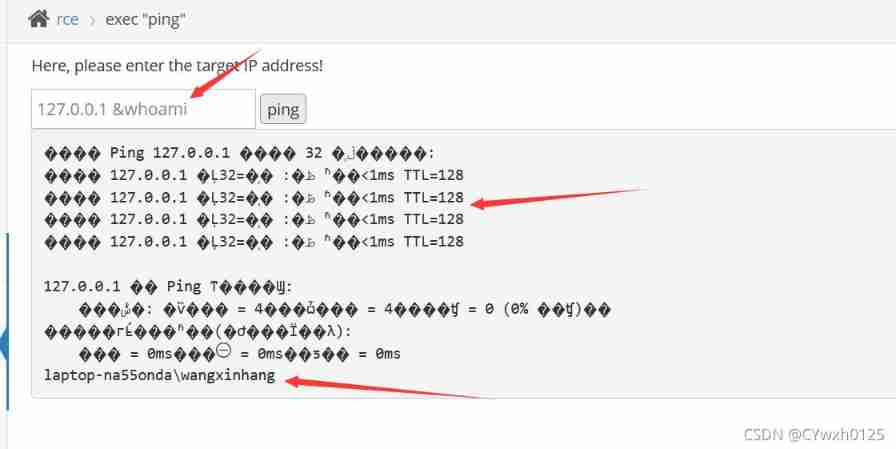
Try splicing at the back
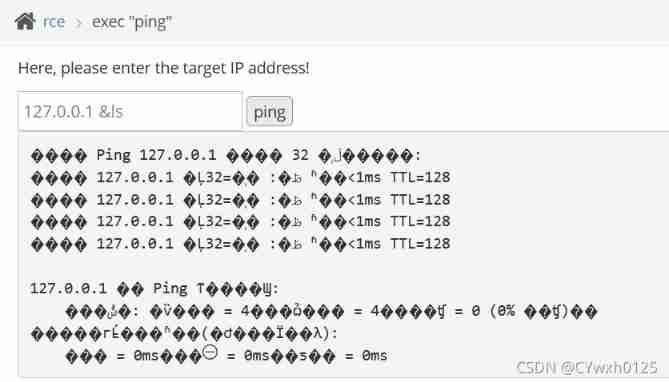
Try to view the directory
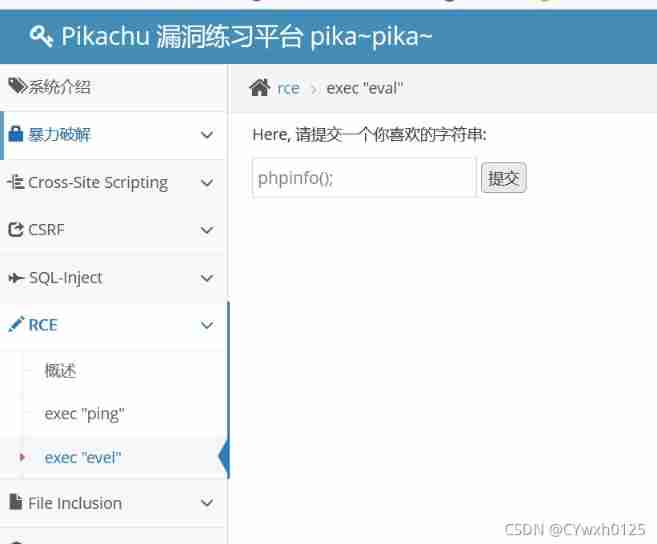
Two .exec"evel"
Back end code :
if(@!eval($_POST['txt']))Submit directly phpinfo();
边栏推荐
- 2022司钻(钻井)考试题库及模拟考试
- Routing in laravel framework
- 嵌入式软件架构设计-消息交互
- About the problem and solution of 403 error in wampserver
- [machine learning notes] how to solve over fitting and under fitting
- Wechat app payment callback processing method PHP logging method, notes. 2020/5/26
- Laravel framework operation error: no application encryption key has been specified
- 鏈錶(簡單)
- 2022 machine fitter (Advanced) test question simulation test question bank simulation test platform operation
- Kotlin协程利用CoroutineContext实现网络请求失败后重试逻辑
猜你喜欢
Brief introduction to revolutionary neural networks
Attack and defense world web WP
Jetpack compose introduction to mastery
::ffff:192.168.31.101 是一个什么地址?

Anchor navigation demo
What are the private addresses
基于微信小程序的订餐系统
uplad_ Labs first three levels
Idea set method annotation and class annotation
Nantong online communication group
随机推荐
Laravel generate entity
Address book (linked list implementation)
Apicloud studio3 WiFi real machine synchronization and WiFi real machine preview instructions
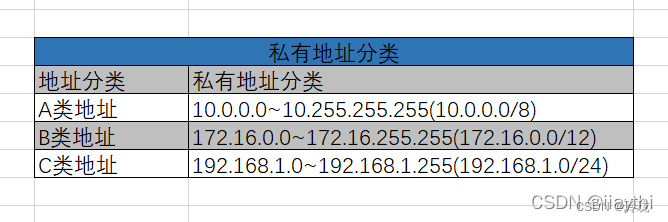
What are the private addresses
Hide Chinese name
Solve the problem of invalid uni app configuration page and tabbar
面试官灵魂拷问:为什么代码规范要求 SQL 语句不要过多的 join?
Require, require in PHP_ once、include、include_ Detailed explanation of the efficiency of repeated introduction of once class library
常见问题之PHP——Fatal error: Allowed memory size of 314572800 bytes exhausted...
【华南理工大学】考研初试复试资料分享
清大科越冲刺科创板:年营收2亿 拟募资7.5亿
2022 machine fitter (Advanced) test question simulation test question bank simulation test platform operation
Scientific running robot pancakeswap clip robot latest detailed tutorial
asp.net 读取txt文件
Jetpack Compose入门到精通
什么叫做信息安全?包含哪些内容?与网络安全有什么区别?
zabbix 监控
Controller in laravel framework
2022建筑焊工(建筑特殊工种)特种作业证考试题库及在线模拟考试
PHP basic syntax