当前位置:网站首页>The differences and connections among cookies, sessions, JWT, and tokens
The differences and connections among cookies, sessions, JWT, and tokens
2022-07-05 06:45:00 【Wei Yunshu】
Cookie、Session、JWT、Token Differences and connections
List of articles
http Stateless request
- Network communication uses http agreement , There is no correlation between each request
Access interface requires authentication
- The back-end interface cannot be exposed to the outside , Only authenticated requests can be accessed , Common authentication methods such as : User name, password 、 SMS verification code , but http It's stateless , Every request requires authentication ;
- You don't want to enter your user name and password every time you send a request , You can put the user name and password in the browser , But once the browser is attacked , All passwords will be revealed ;
Cookie
- There is a store in the browser Cookie The place of ,Cookie It can store <key,value> This key value pair , You can also store the corresponding expiration date , And the corresponding access domain address , When the user accesses the domain name , Just get the corresponding cookie;
- When the user accesses the establishment request with the user name and password for the first time , The server can put the user name and password in cookie among , When the browser is next used , You can log in directly , But this is no different from streaking , It's very unsafe ;
Session
- The server memory stores the client status information , After client access , Create a unique identifier session_id And other corresponding information , Stored locally , And put this session_id Put it in the returned cookie among , Return to browser ; The next time the browser accesses the service , Just take it session_id As identification , Server and storage session_id compare ; When... In the server session_id The expiration date is up , The corresponding expired , If the user exits , In the browser cookie Delete accordingly
JWT
JWT(Json web token) It's made up of three parts :
- Header : describe JWT Metadata . Defines the algorithm to generate the signature and Token The type of .
- Payload( load ): It is used to store the data that needs to be transferred
- Signature( Signature ): Server pass Payload、Header And a key (secret) Use Header The signature algorithm specified in ( The default is HMAC SHA256) Generate .
After the user logs in , Server generation JWT, Put some insensitive information on JWT Of Payload among , Send it back to the user ;
The user will get JWT As your own identity information , Direct login ; But such JWT User controlled , Before it fails , The server has no control permission ;
Token
- A string that does not carry specific information , Store user information in Redis or Mysql Wait in memory ,Token As its key
- The user login , take Token Return to the user , After each login, first pass token Read user information , Then check it ;
Refresh Token
- Token Have time limit ,Refresh Token The actual effect is slightly longer ,Token After the failure , use Refresh Token Refresh Token, keep Token The continuity of
Three questions :
Cookie Store as a client 、session Store as a server , take Session_id As the association between client and server , Client pass Session_id Verify your login status ;Cookie( user name + Encrypted password ) And JWT So like ;Cookie/session And token So like , What is the main difference between them ?
Session Stored in a single server , When users are online at the same time, the amount is ,Session It takes up more memory ; And when the website adopts cluster deployment , Multiple servers need to share user login status . That will Session Put it in mysql Don't you just store it in ?
Cookie There will be cross domain problems ,token There is no cross domain problem , Then why not Cookie As a token The use of ?
边栏推荐
- Orin two brushing methods
- Pycahrm reports an error: indentation error: unindent does not match any outer indentation
- Cloud native related technology learning
- The “mode“ argument must be integer. Received an instance of Object
- Bash exercise 17 writing scripts to install the server side of FRP reverse proxy software
- Speedtree01 generator properties
- LSA Type Explanation - lsa-5 (type 5 LSA - autonomous system external LSA) and lsa-4 (type 4 LSA - ASBR summary LSA) explanation
- [moviepy] unable to find a solution for exe
- 2048 project realization
- [Gaode map POI stepping pit] amap Placesearch cannot be used
猜你喜欢
ollvm编译出现的问题纪录
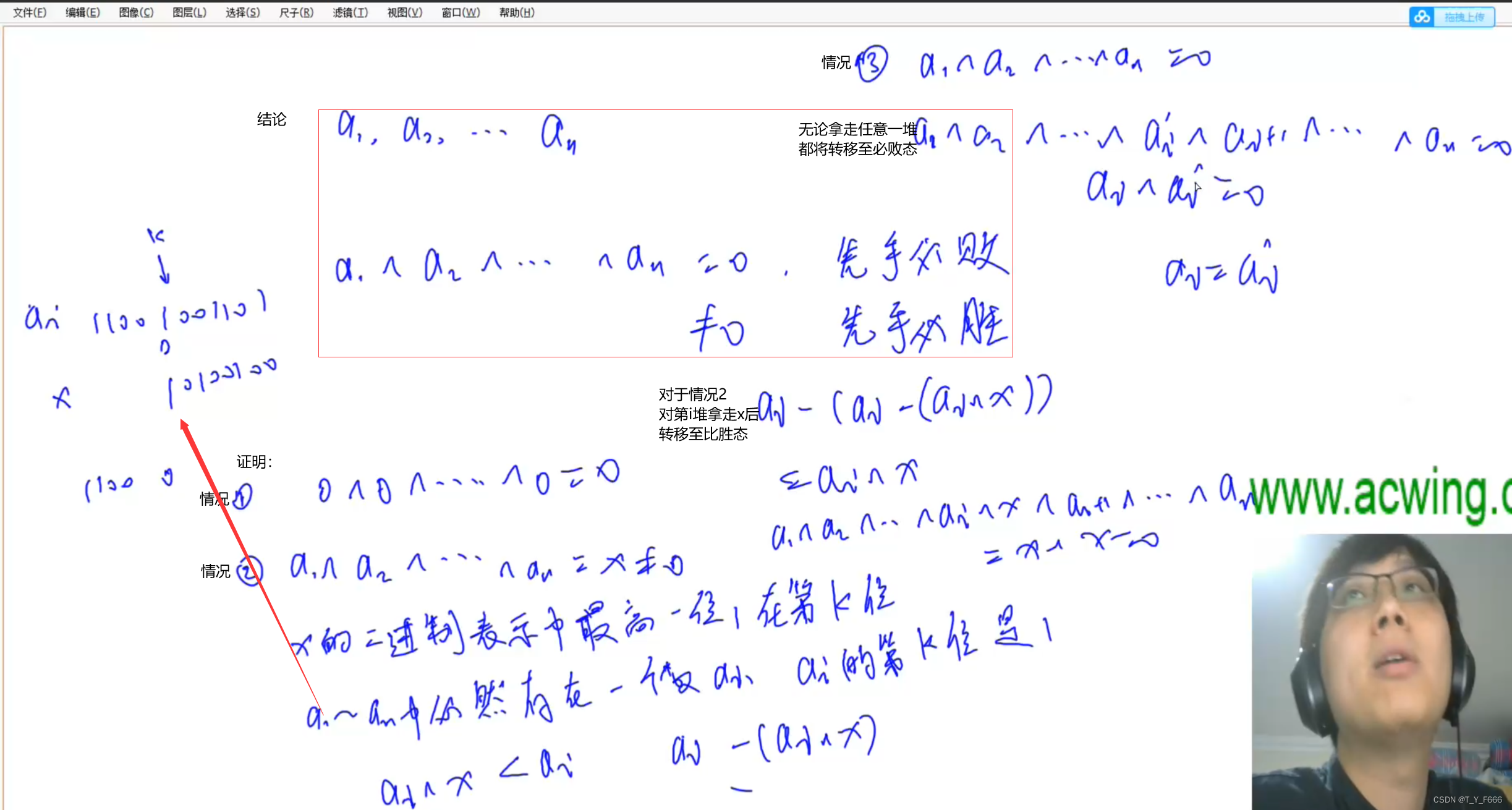
Game theory acwing 891 Nim games

Sorting out the latest Android interview points in 2022 to help you easily win the offer - attached is the summary of Android intermediate and advanced interview questions in 2022
![[wustctf2020] plain_ WP](/img/66/fdf7649359f36444703ff2279562e6.jpg)
[wustctf2020] plain_ WP
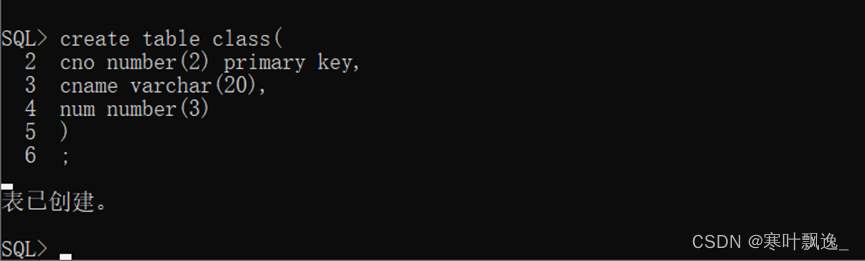
7.Oracle-表结构
20220213-CTF MISC-a_ good_ Idea (use of stegsolve tool) -2017_ Dating_ in_ Singapore

Find the combination number acwing 888 Find the combination number IV
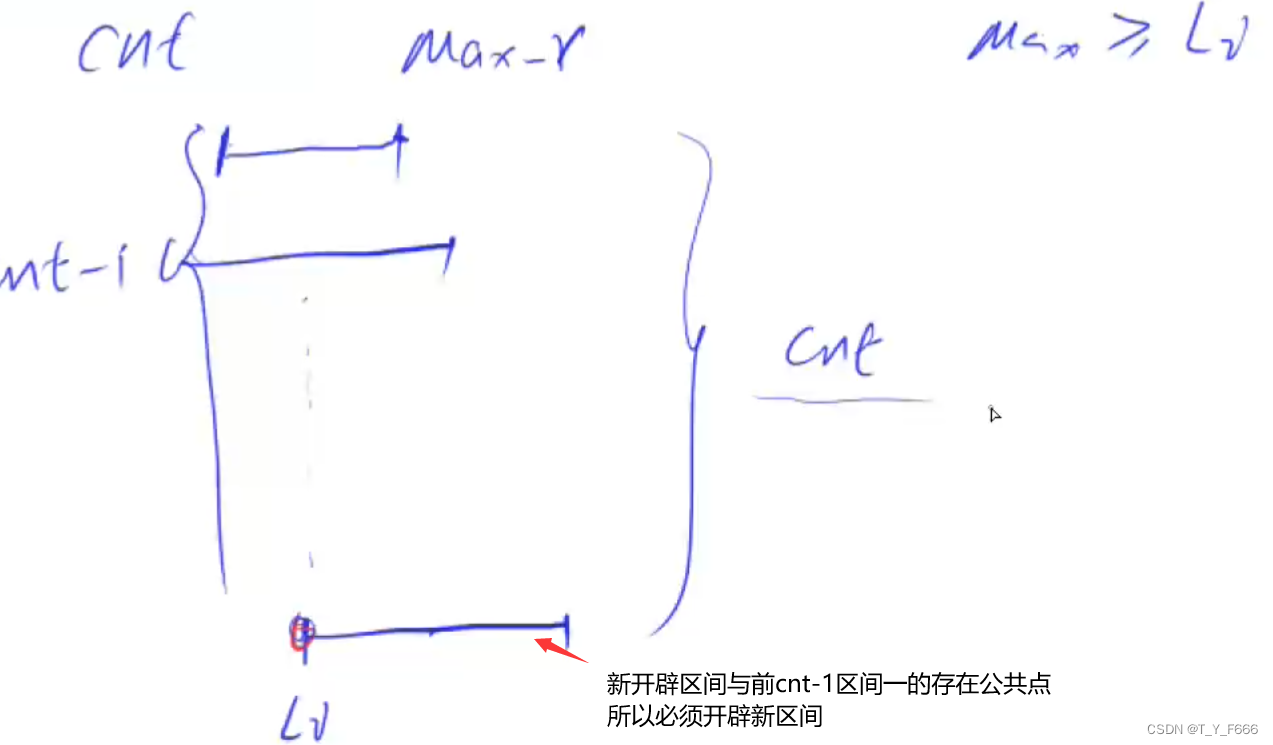
Interval problem acwing 906 Interval grouping
SolidWorks template and design library are convenient for designers to call
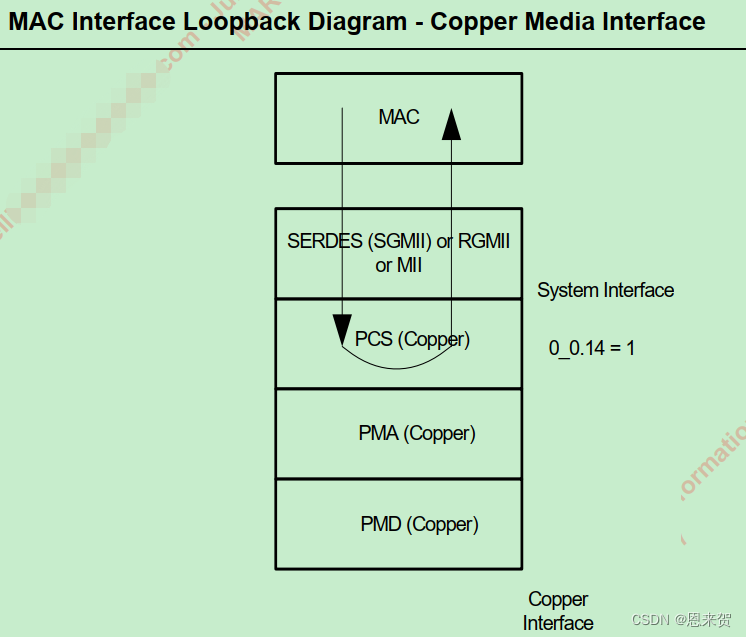
Marvell 88E1515 PHY loopback模式测试
随机推荐
Record of problems in ollvm compilation
H5 module suspension drag effect
2022/6/29-日报
H5内嵌App适配暗黑模式
在新线程中使用Handler
2022-5-the fourth week daily
将webApp或者H5页面打包成App
Edge calculation data sorting
Design specification for mobile folding screen
Cookie、Session、JWT、token四者间的区别与联系
Find the combination number acwing 888 Find the combination number IV
Page type
安装OpenCV--conda建立虚拟环境并在jupyter中添加此环境的kernel
NVM Downloading npm version 6.7.0... Error
如何正确在CSDN问答进行提问
Package webapp or H5 pages into apps
Genesis builds a new generation of credit system
TCP's understanding of three handshakes and four waves
Interval problem acwing 906 Interval grouping
SRE核心体系了解