当前位置:网站首页>Method of accessing mobile phone storage location permission under non root condition
Method of accessing mobile phone storage location permission under non root condition
2022-07-06 18:40:00 【Chenfuxu】
1.Manifest Apply for permission to read and write external files
<uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE"/
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/>2. The higher version requires dynamic permission application
int checkReadExternalPermission = checkSelfPermission(Manifest.permission.READ_EXTERNAL_STORAGE);
int checkWriteExternalPermission = checkSelfPermission(Manifest.permission.WRITE_EXTERNAL_STORAGE);
if (checkReadExternalPermission != PackageManager.PERMISSION_GRANTED || checkWriteExternalPermission != PackageManager.PERMISSION_GRANTED) {
requestPermissions(new String[] {Manifest.permission.READ_EXTERNAL_STORAGE, Manifest.permission.WRITE_EXTERNAL_STORAGE}, 0x01);
}3. If an error is reported and the file cannot be accessed , stay application Add
android:requestLegacyExternalStorage="true"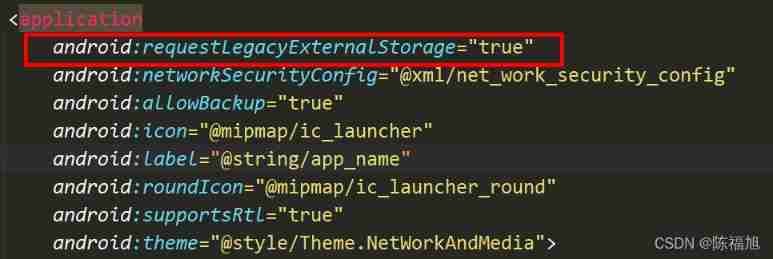
4. Note that sometimes the file cannot be read or written successfully because the file memory is too large
边栏推荐
- UDP protocol: simple because of good nature, it is inevitable to encounter "city can play"
- C#/VB.NET 给PDF文档添加文本/图像水印
- 徐翔妻子应莹回应“股评”:自己写的!
- 当保存参数使用结构体时必备的开发技巧方式
- 爬虫玩得好,牢饭吃到饱?这3条底线千万不能碰!
- Five data structures of redis
- [.Net core] solution to error reporting due to too long request length
- Windows connects redis installed on Linux
- Automatic reservation of air tickets in C language
- Interpreting cloud native technology
猜你喜欢
Recommend easy-to-use backstage management scaffolding, everyone open source
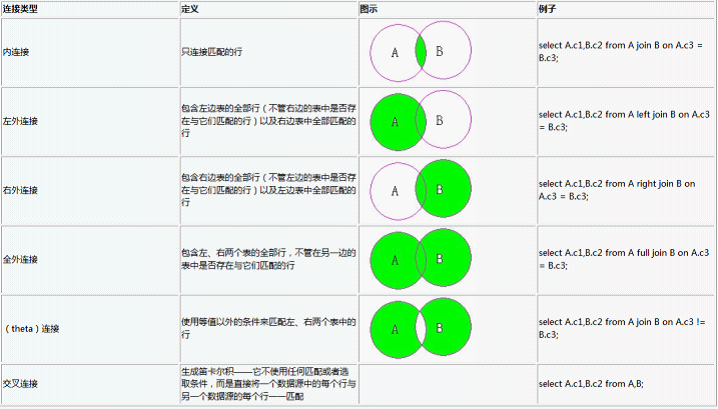
ORACLE进阶(四)表连接讲解
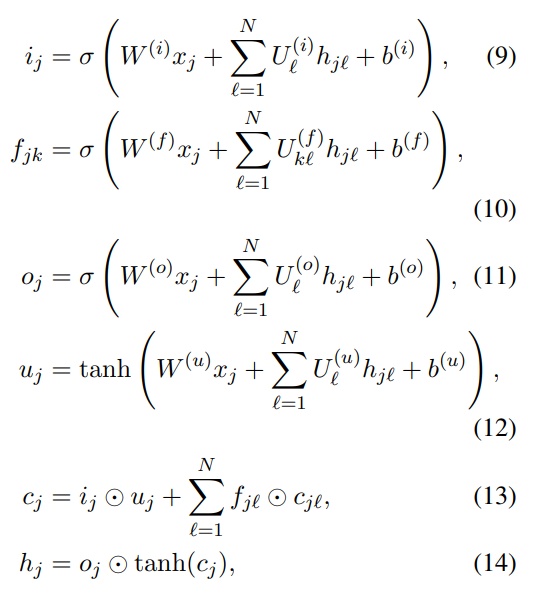
Some understandings of tree LSTM and DGL code implementation
使用cpolar建立一个商业网站(1)
win10系统下插入U盘有声音提示却不显示盘符
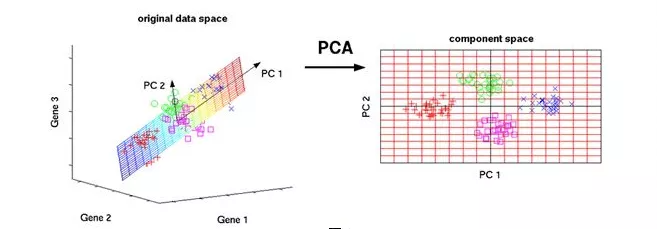
30 minutes to understand PCA principal component analysis

人体骨骼点检测:自顶向下(部分理论)

Summary of performance knowledge points
CSRF vulnerability analysis
Docker安装Redis
随机推荐
【LeetCode第 300 场周赛】
MySQL查询请求的执行过程——底层原理
测试1234
Distill knowledge from the interaction model! China University of science and Technology & meituan proposed virt, which combines the efficiency of the two tower model and the performance of the intera
Collection of penetration test information -- use with nmap and other tools
Self supervised heterogeneous graph neural network with CO comparative learning
重磅硬核 | 一文聊透对象在 JVM 中的内存布局,以及内存对齐和压缩指针的原理及应用
POJ 2208 six lengths of tetrahedron are known, and the volume is calculated
CSRF漏洞分析
SQL injection - access injection, access offset injection
Automatic reservation of air tickets in C language
一种用于夜间和无袖测量血压手臂可穿戴设备【翻译】
Hongke shares | plate by plate ar application in Beijing Winter Olympics
Echart simple component packaging
用于远程医疗的无创、无袖带血压测量【翻译】
Five data structures of redis
Cocos2d Lua 越来越小样本 内存游戏
使用cpolar建立一个商业网站(1)
echart简单组件封装
With the implementation of MapReduce job de emphasis, a variety of output folders