当前位置:网站首页>Mysql--- query the top 5 students
Mysql--- query the top 5 students
2022-07-06 00:57:00 【The evening wind blows】
List of articles
demand : The query result is top 5 Students of
After getting the demand , First analyze the requirements , Find out the screening conditions
One 、Mysql Inquire about
1、 The most basic query
select * from table where name="panpan"
2、 Check before 5 name
stay mysql Top of the filtered data in , You can use keywords :limit
select * from table where name="panpan" limit 1
explain : The name in the query table is panpan The first record
3、 Under what conditions , The demand is to screen by achievements , You can use order by Sort filter
select * from table where order by grade
Two 、 Query application
Query after merging :
select * from score order by grade limit 5
explain : Query to score Exterior and interior grade , With grade Screening , Before extraction 5 Bar record
边栏推荐
- golang mqtt/stomp/nats/amqp
- BiShe - College Student Association Management System Based on SSM
- The growth path of test / development programmers, the problem of thinking about the overall situation
- Spark AQE
- Dynamic programming -- linear DP
- Intensive learning weekly, issue 52: depth cuprl, distspectrl & double deep q-network
- [simple implementation of file IO]
- How spark gets columns in dataframe --column, $, column, apply
- Cloud guide DNS, knowledge popularization and classroom notes
- Illustrated network: the principle behind TCP three-time handshake, why can't two-time handshake?
猜你喜欢
How to make your own robot
Recursive method to realize the insertion operation in binary search tree
![[groovy] JSON serialization (convert class objects to JSON strings | convert using jsonbuilder | convert using jsonoutput | format JSON strings for output)](/img/52/021931181ad3f4bef271b4e98105c2.jpg)
[groovy] JSON serialization (convert class objects to JSON strings | convert using jsonbuilder | convert using jsonoutput | format JSON strings for output)
Differences between standard library functions and operators
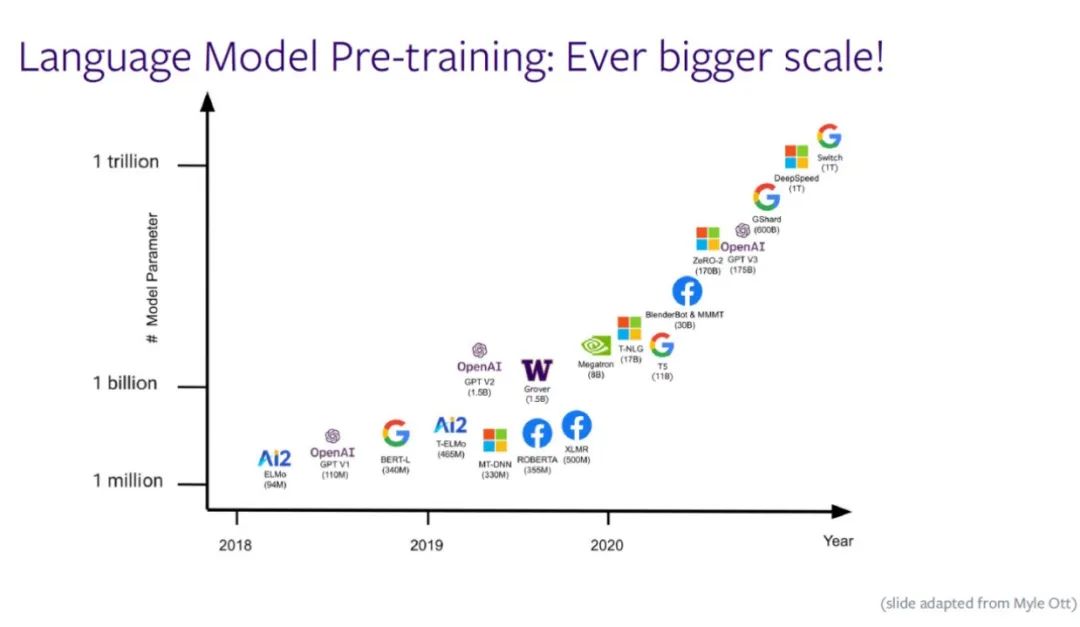
Meta AI西雅图研究负责人Luke Zettlemoyer | 万亿参数后,大模型会持续增长吗?
Spark AQE
Five challenges of ads-npu chip architecture design

Spark AQE

cf:C. The Third Problem【关于排列这件事】

Questions about database: (5) query the barcode, location and reader number of each book in the inventory table
随机推荐
Five challenges of ads-npu chip architecture design
MYSQL---查询成绩为前5名的学生
[groovy] JSON string deserialization (use jsonslurper to deserialize JSON strings | construct related classes according to the map set)
猿桌派第三季开播在即,打开出海浪潮下的开发者新视野
Spark AQE
孤勇者
CTF daily question day44 rot
Spark AQE
Logstash clear sincedb_ Path upload records and retransmit log data
A preliminary study of geojson
synchronized 和 ReentrantLock
Spark DF adds a column
MCU realizes OTA online upgrade process through UART
[groovy] JSON serialization (jsonbuilder builder | generates JSON string with root node name | generates JSON string without root node name)
After Luke zettlemoyer, head of meta AI Seattle research | trillion parameters, will the large model continue to grow?
cf:D. Insert a Progression【关于数组中的插入 + 绝对值的性质 + 贪心一头一尾最值】
Promise
Recoverable fuse characteristic test
devkit入门
在产业互联网时代,将会凭借大的产业范畴,实现足够多的发展