UP Meta—Web3.0世界创新型元宇宙金融协议

https://img blog.csdnimg.cn/b2a2818a2a124589b06bb27cb3d52891.png 7月4日,IDO全球首发 UP Meta(简称UP)是第一个结合NFT优势致力于建立Web3.0世界的创新型元宇宙金融协议,它使质押收益变得更容易、更高效,并利用协...
2022-07-07 09:58【蜻蜓资讯】
阅读更多112.网络安全渗透测试—[权限提升篇10]—[Windows 2003 LPK.DDL劫持提权&msf本地提权]
![112.网络安全渗透测试—[权限提升篇10]—[Windows 2003 LPK.DDL劫持提权&msf本地提权]](/img/b6/6dfe9be842204567096d1f4292e8e7.png)
我认为,无论是学习安全还是从事安全的人,多多少少都有些许的情怀和使命感 文章目录 一、LPK.DDL劫持提权 LPKDDL 2 1、sethc.exe是什么: 1sethcexe 3 2、lpk.dll出现的背景: 2lpkdll 7 3、Windows查找dll文件的目录顺序: 3Windows...
2022-07-07 09:58【qwsn】
阅读更多110.网络安全渗透测试—[权限提升篇8]—[Windows SqlServer xp_cmdshell存储过程提权]
![110.网络安全渗透测试—[权限提升篇8]—[Windows SqlServer xp_cmdshell存储过程提权]](/img/62/1ec8885aaa2d4dca0e764b73a1e2df.png)
我认为,无论是学习安全还是从事安全的人,多多少少都有些许的情怀和使命感 文章目录 一、Windows Sqlserver xp cmdshell存储过程提权 Windows Sqlserver xp cmdshell 2 1、XP CMDSHELL提权背景: 1XP CMDSHELL 3 2、XP...
2022-07-07 09:58【qwsn】
阅读更多108.网络安全渗透测试—[权限提升篇6]—[Windows内核溢出提权]
![108.网络安全渗透测试—[权限提升篇6]—[Windows内核溢出提权]](/img/c0/8a7b52c46eadd27cf4784ab2f32002.png)
我认为,无论是学习安全还是从事安全的人,多多少少都有些许的情怀和使命感 文章目录 一、Windows IIS6.0溢出提权 Windows IIS60 2 1、Windos提权简介: 1Windos 3 2、程序权限的对比: 2 5 3、 漏洞利用过程: 3 8 (1)实验环境: 1 9 (2)靶...
2022-07-07 09:58【qwsn】
阅读更多powershell cs-UTF-16LE编码上线
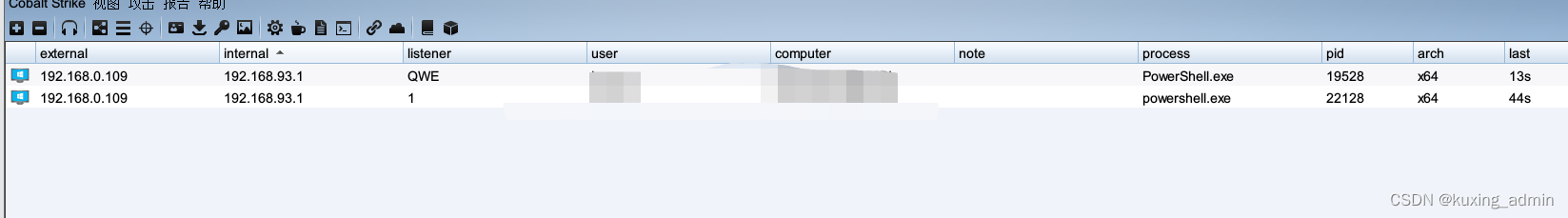
0x01前言 当我们要上线主机的时候,可能会因为你的代码含有木马字符串,导致无法上线 0x02问题 1、 例子 powershell.exe exec bypass encodedCommand ZQBjAGgAbwAgACIAMQAyADMAIgA= https://img blog.csdni...
2022-07-07 09:59【kuxing_admin】
阅读更多Superscalar processor design yaoyongbin Chapter 8 instruction emission excerpt
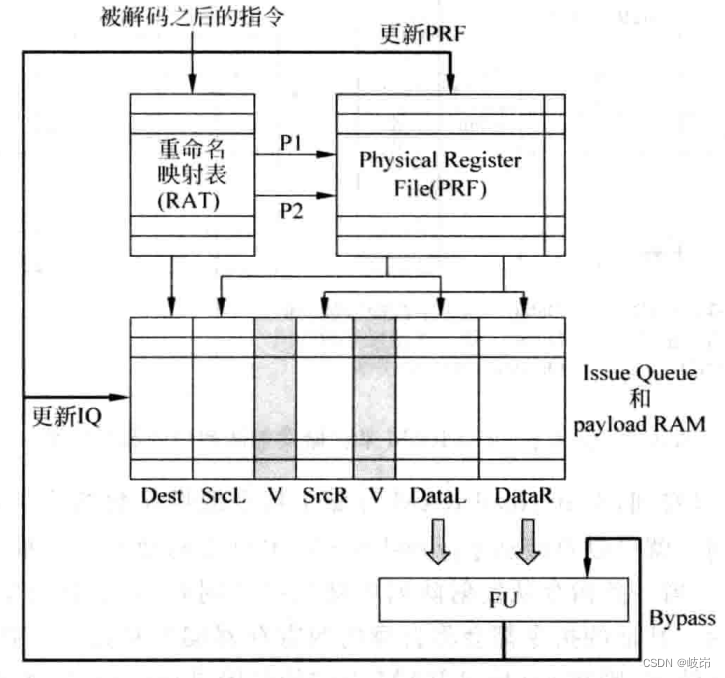
8.1 summary What is launch ? It is to send instructions that meet certain conditions from the transmission queue issue queue Choose from , And sen...
2022-07-07 11:52【Qi Qi】
阅读更多The function of adding @ before the path in C #
Use @ It means no escape The backslash .( Such as r yes Line break ) It is generally expressed in a string : c: windows vscode.exe Have to ...
2022-07-07 11:52【Fog in the sky】
阅读更多[full stack plan - programming language C] basic introductory knowledge
![[full stack plan - programming language C] basic introductory knowledge](/img/6d/555ac6b80b015e0cdfb7ef0a234f9d.png)
List of articles Preface 1 Understanding of editor 13 The process of creating a new project 38 Go over the basics 54 One 、 Input and outpu...
2022-07-07 11:52【Poplar branch】
阅读更多Superscalar processor design yaoyongbin Chapter 10 instruction submission excerpt
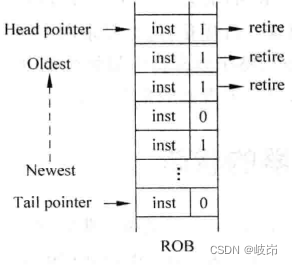
10.1 summary In superscalar processors , When instructions are executed inside the processor , It will not be executed in this strict serial way ....
2022-07-07 11:53【Qi Qi】
阅读更多Superscalar processor design yaoyongbin Chapter 9 instruction execution excerpt
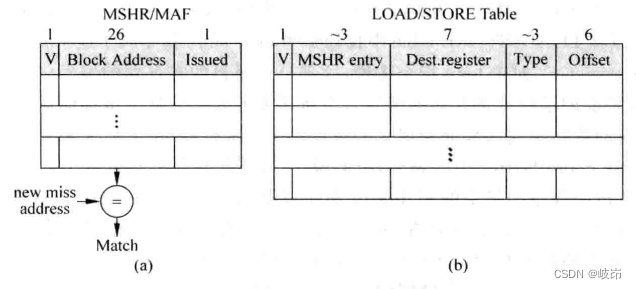
9.1 summary The execution stage is responsible for the execution of instructions , So many things have been done in the previous stage of the asse...
2022-07-07 11:54【Qi Qi】
阅读更多Fleet tutorial 14 basic introduction to listtile (tutorial includes source code)
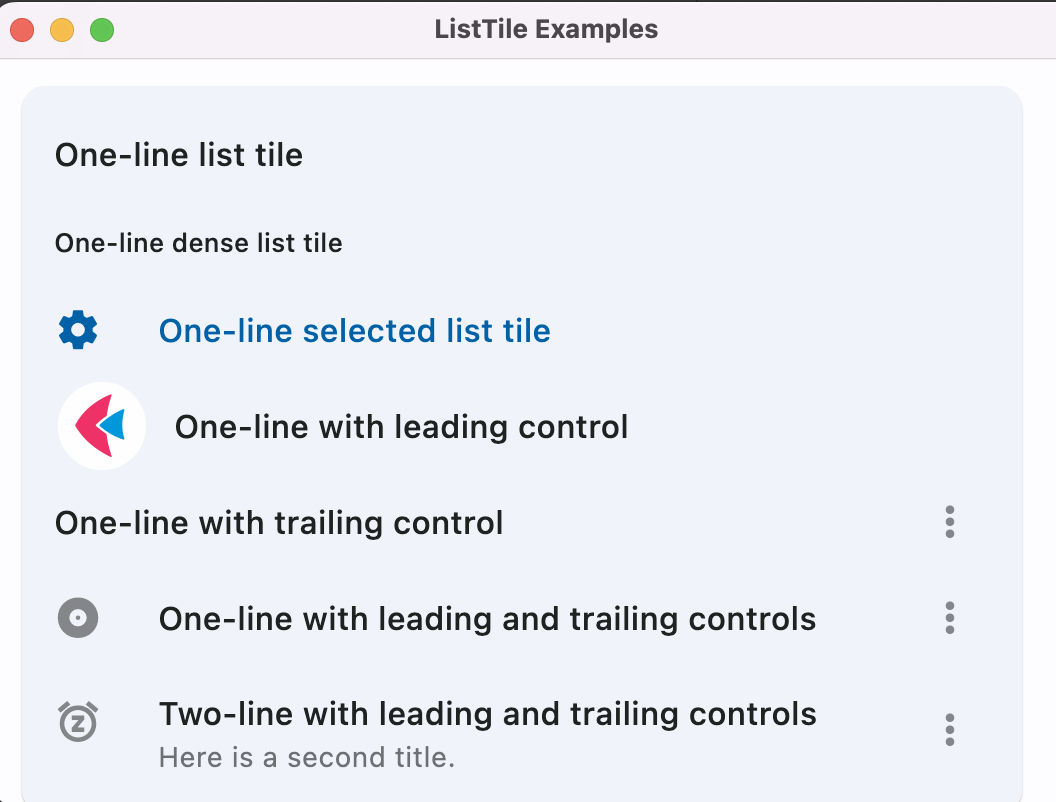
Flet What is it? Flet It's a framework , Make it easy for you to build real-time in your favorite language Web、 Mobile and desktop applications , ...
2022-07-07 11:54【Knowledge fatness】
阅读更多Fleet tutorial 15 introduction to GridView Basics (tutorial includes source code)
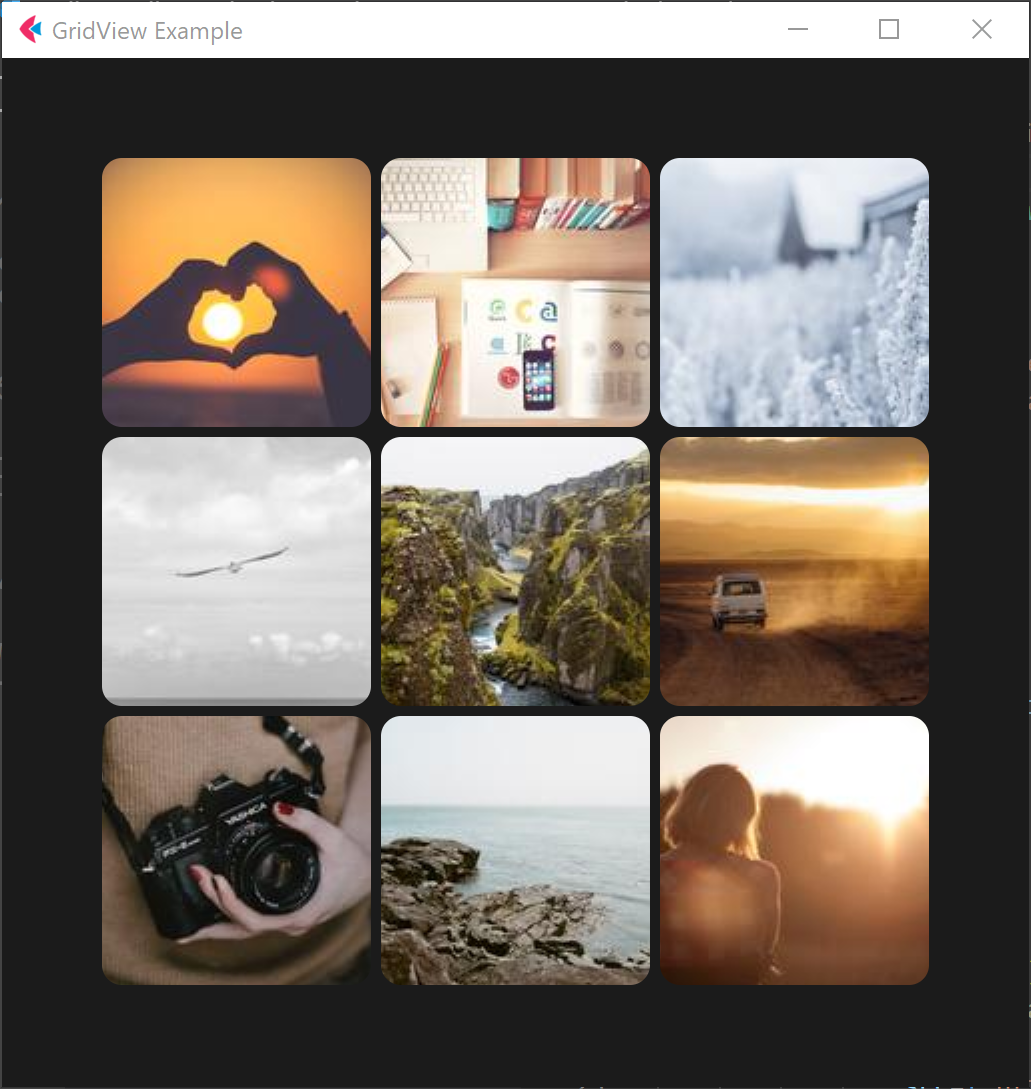
Flet What is it? Flet It's a framework , Make it easy for you to build real-time in your favorite language Web、 Mobile and desktop applications , ...
2022-07-07 11:54【Knowledge fatness】
阅读更多Flet tutorial 17 basic introduction to card components (tutorial includes source code)
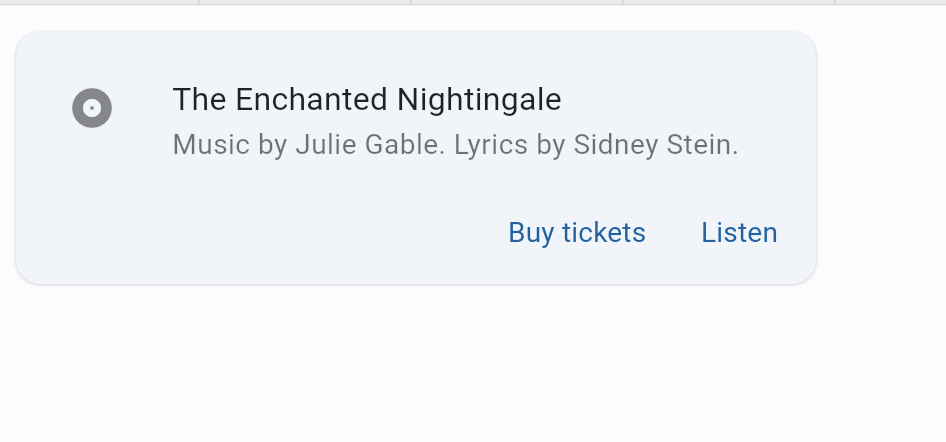
Flet What is it? Flet It's a framework , Make it easy for you to build real-time in your favorite language Web、 Mobile and desktop applications , ...
2022-07-07 11:55【Knowledge fatness】
阅读更多Basic introduction to the 16 tabs tab control in the fleet tutorial (the tutorial includes source code)
Flet What is it? Flet It's a framework , Make it easy for you to build real-time in your favorite language Web、 Mobile and desktop applications , ...
2022-07-07 11:55【Knowledge fatness】
阅读更多[neural network] convolutional neural network CNN [including Matlab source code 1932]
![[neural network] convolutional neural network CNN [including Matlab source code 1932]](/img/65/cf9d0a3f46a581dc8f28de2e28779d.png)
One 、 How to get the code How to get the code 1: The complete code has been uploaded to my resources : 【 neural network 】 Convolutional neural ne...
2022-07-07 11:55【Poseidon light】
阅读更多Common locking table processing methods in Oracle
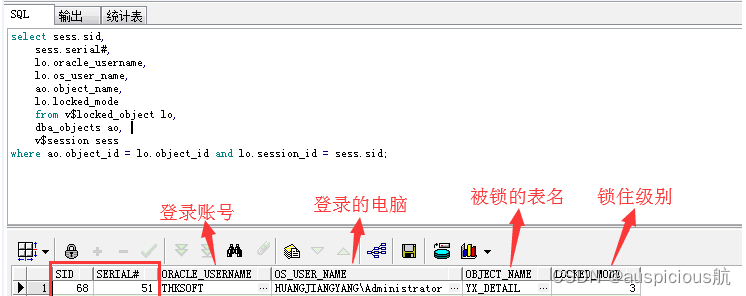
1、 View locked table information select sess.sid,sess.serial/ , lo.oracle username,lo.os user name, ao.object name,lo.locked mode from v$locked objec...
2022-07-07 11:55【Auspicious flight】
阅读更多Detailed explanation of debezium architecture of debezium synchronization
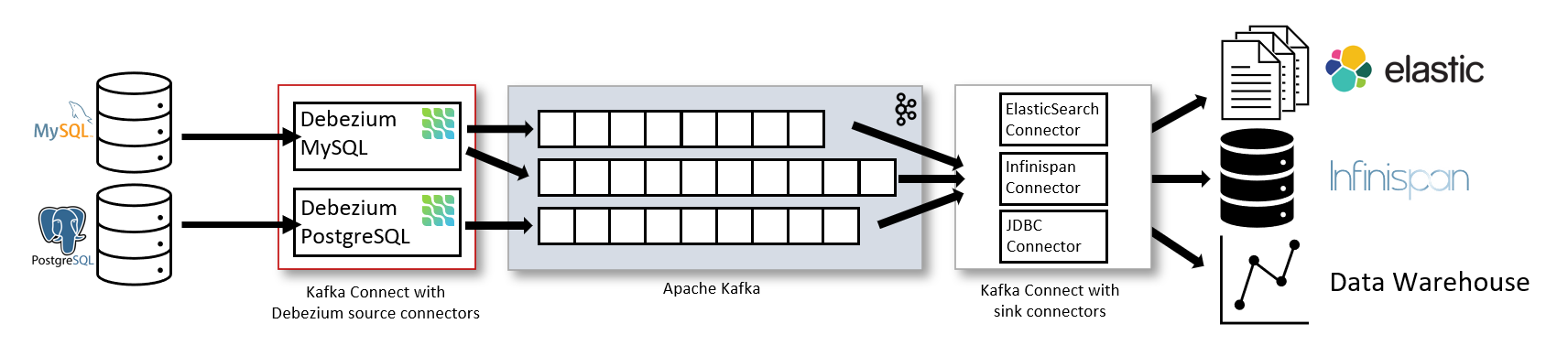
The most common is , You pass Apache Kafka Connect connect 'Kafka Connect' Deploy Debezium .Kafka Connect Is a framework and runtime for imple...
2022-07-07 11:55【Auspicious flight】
阅读更多112. Network security penetration test - [privilege promotion article 10] - [Windows 2003 lpk.ddl hijacking rights lifting & MSF local rights lifting]
![112. Network security penetration test - [privilege promotion article 10] - [Windows 2003 lpk.ddl hijacking rights lifting & MSF local rights lifting]](/img/b6/6dfe9be842204567096d1f4292e8e7.png)
In my submission , Whether studying safety or engaging in safety , More or less, I have some feelings and sense of mission List of articles One ...
2022-07-07 11:56【qwsn】
阅读更多108. Network security penetration test - [privilege escalation 6] - [windows kernel overflow privilege escalation]
![108. Network security penetration test - [privilege escalation 6] - [windows kernel overflow privilege escalation]](/img/c0/8a7b52c46eadd27cf4784ab2f32002.png)
In my submission , Whether studying safety or engaging in safety , More or less, I have some feelings and sense of mission List of articles One ...
2022-07-07 11:56【qwsn】
阅读更多110. Network security penetration test - [privilege promotion 8] - [windows sqlserver xp_cmdshell stored procedure authorization]
![110. Network security penetration test - [privilege promotion 8] - [windows sqlserver xp_cmdshell stored procedure authorization]](/img/62/1ec8885aaa2d4dca0e764b73a1e2df.png)
In my submission , Whether studying safety or engaging in safety , More or less, I have some feelings and sense of mission List of articles One ...
2022-07-07 11:56【qwsn】
阅读更多
边栏推荐
- 云原生存储解决方案Rook-Ceph与Rainbond结合的实践
- ArrayList线程不安全和解决方案
- Binary tree high frequency question type
- 复杂网络建模(二)
- Greenplum6.x监控软件搭建
- One click installation of highly available Nacos clusters in rainbow
- ArcGIS operation: converting DWG data to SHP data
- ORM model -- associated fields, abstract model classes
- 【istio简介、架构、组件】
- Common validation comments
猜你喜欢
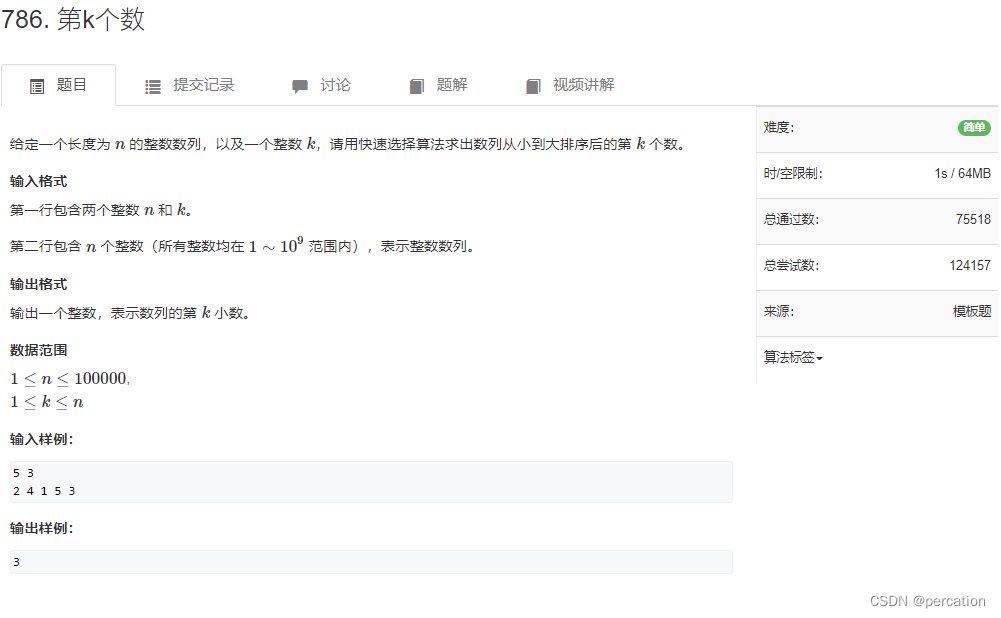
Through the tunnel https://img blog.csdnimg.cn/e9a336bc16734957bb445d07372b67cc.png / include bits/stdc++.h using namespace std; const int N = 1e...

系列文章目录 【零基础微信小程序入门开发】小程序介绍及环境搭建 35230125/article/details/125272160 【零基础微信小程序入门开发】配置小程序 35230125/article/details/125285363 【零基础微信小程序入门开发】小程序框架一 ...

问题描述 参考华为游戏多媒体服务文档,实现游戏语音相关功能,在调用 GameMediaEngine.create CreateEngineParams params, IGameMMEEventHandle eventHandler 接口创建游戏引擎实例时,游戏引擎实例创建失败,返回错误码1002...
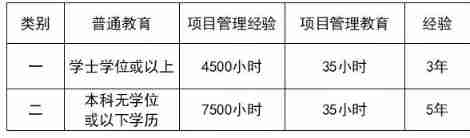
One , Enter oneself for an examination NPDP What is the condition of ? 1、 Bachelor degree or above Or equivalent : lately 4 Accumulated in 2 At l...
First, let's look at the page error https://img blog.csdnimg.cn/43088f29629446a7b6436a03f2c781e6.png?x oss process=image/watermark,type ZmFuZ3poZW5n...
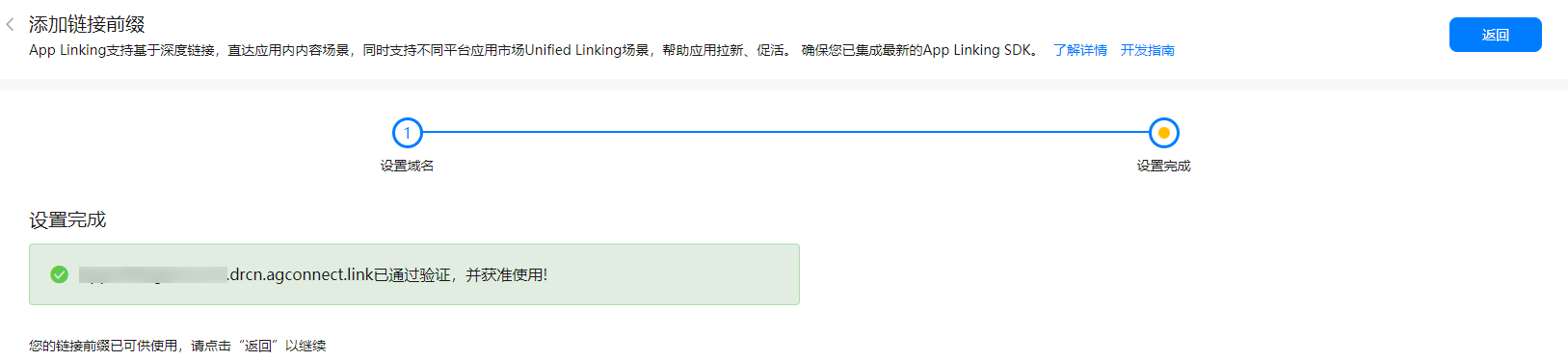
brief introduction App Linking It is a cross platform link that can work in the required way no matter whether the application has been installed ...
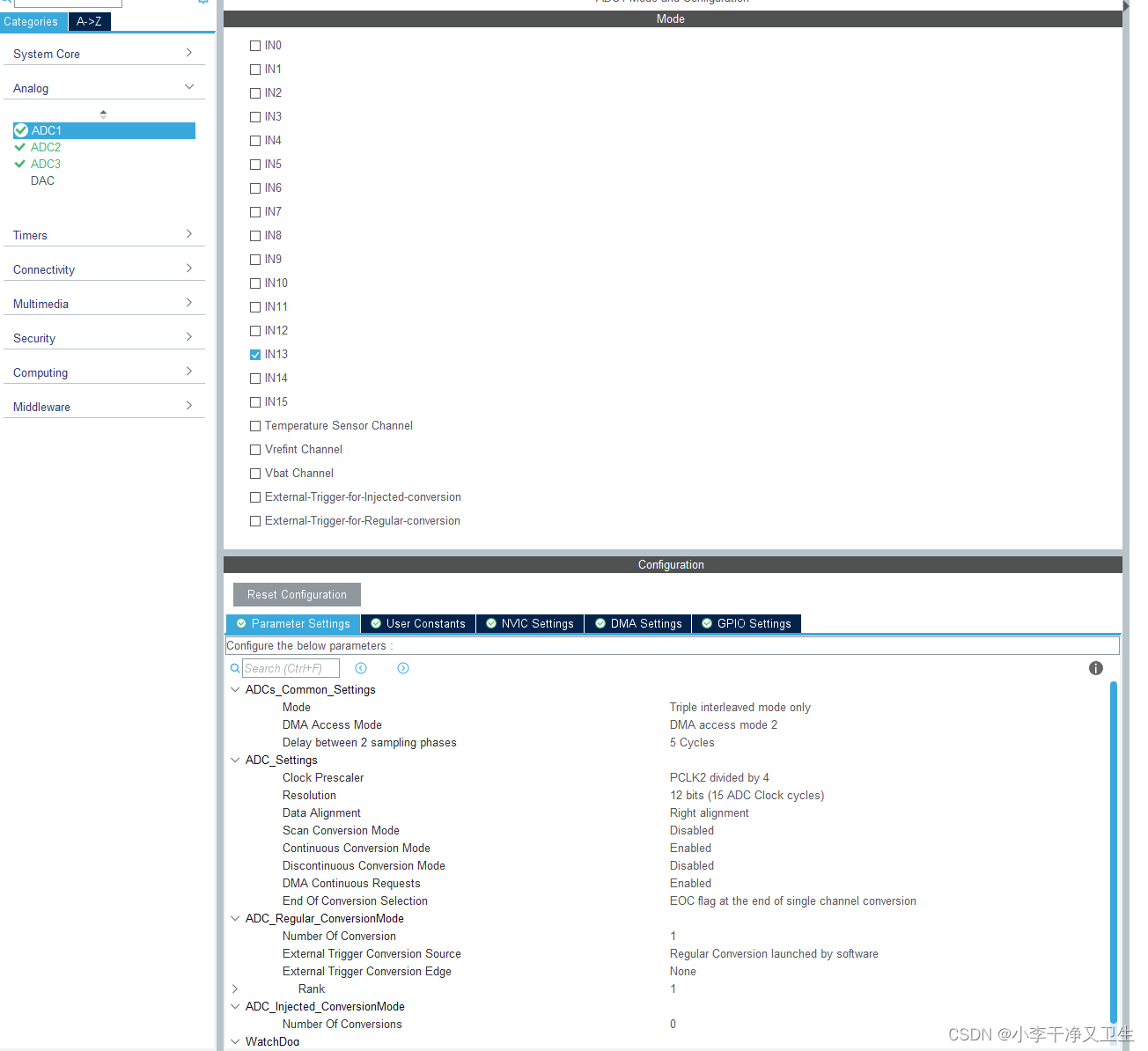
STM32 ADC and DMA Simple summary 1. brief introduction Use wildfire development board F429IGT6 ADC block diagram image 20220702105713458 https://...
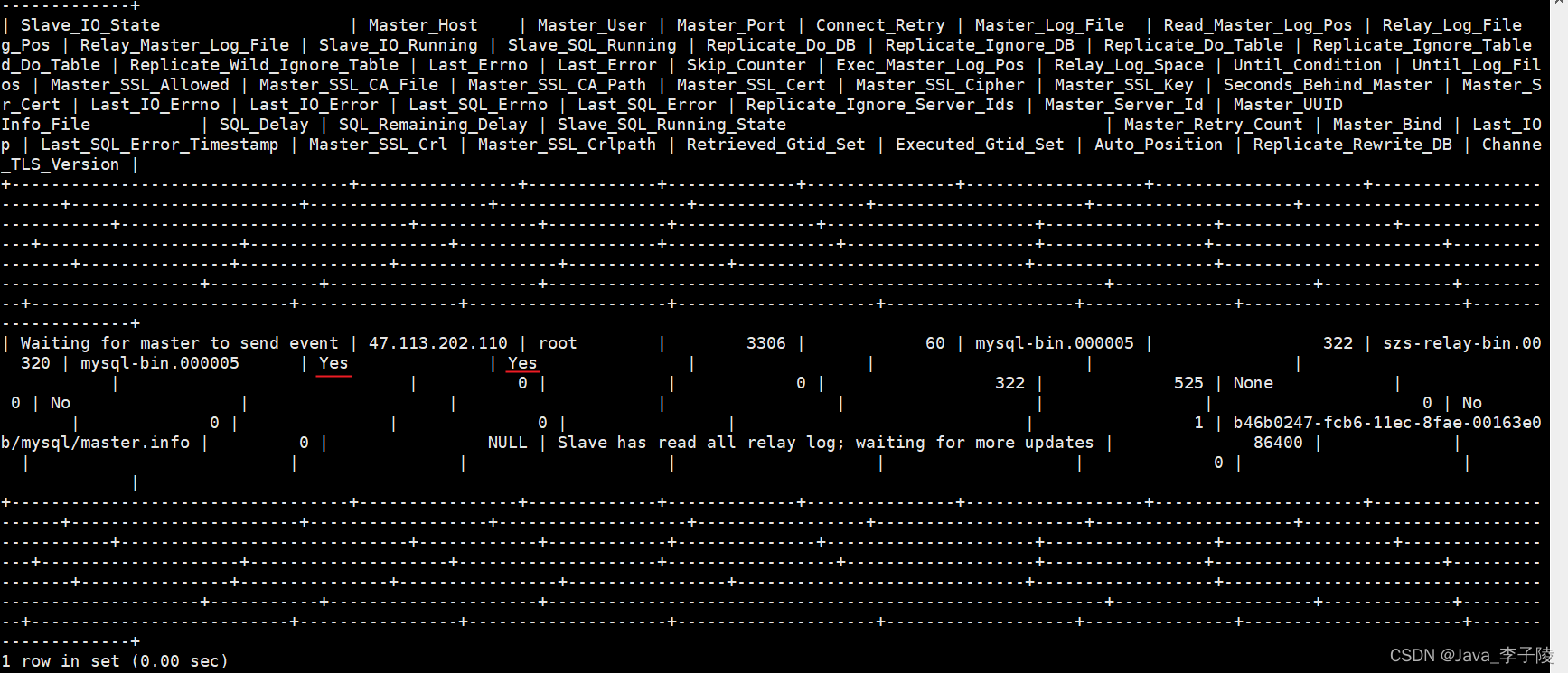
分布式数据库主从配置(MySQL) 注意:默认已经安装了mysql,安装教程详见我的另一篇博客– springboot项目部署到阿里云服务器(centos7) Java 李子陵的博客 CSDN博客 springboot部署到阿里云 51431003/article/details/1247...

Preface Brother Xu Zhu has a friend Xiao Wu , He works in a safety manufacturer company . The dean of the University Department of junior five cam...
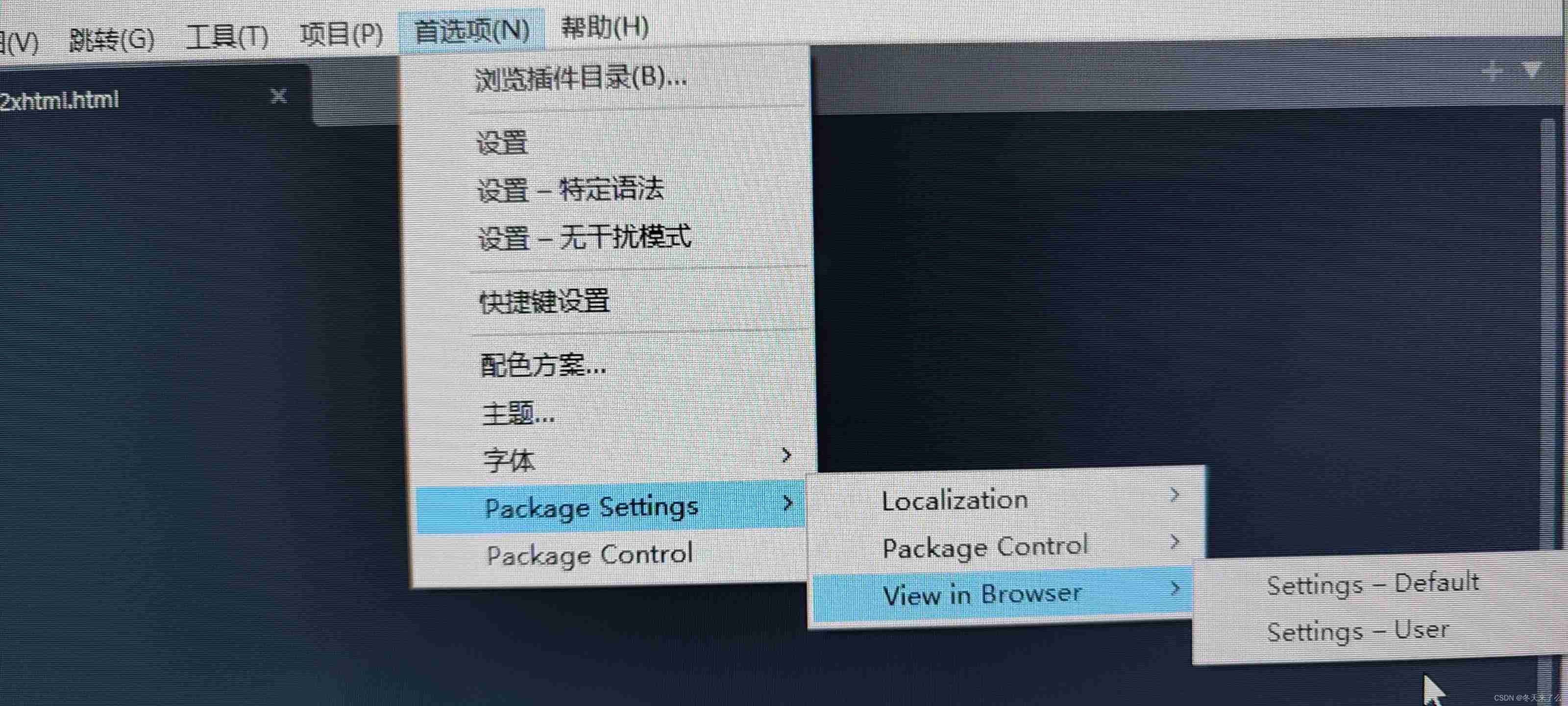
1、Ctrl + Shift + P , evoke Package Control https://img blog.csdnimg.cn/816ffbe89b9642dcaafa8d86ee39d837.png?x oss process=image/watermark,type d3F5L...